Flooding attack Detection using Anomaly Techniques with Wireshark
VerifiedAdded on 2023/06/03
|53
|13458
|342
AI Summary
This research paper discusses the detection of flooding attacks using anomaly techniques in Wireshark. It covers the types of flooding attacks, issues related to detection, attack detection techniques, and the characteristics of Wireshark in detecting flooding attacks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: DISSERTATION
Flooding attack Detection using Anomaly Techniques with Wireshark
Name of the Student-
Name of the University-
Author’s Note-
Flooding attack Detection using Anomaly Techniques with Wireshark
Name of the Student-
Name of the University-
Author’s Note-
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1DISSERTATION
Table of Contents
1. Introduction..................................................................................................................................1
1.1 Background Study.................................................................................................................1
1.2 Scope of the Research............................................................................................................3
1.3 Aim of the Research..............................................................................................................4
1.4 Objective of the Research......................................................................................................4
1.5 Research Questions................................................................................................................4
2. Literature Review........................................................................................................................5
2.1 Feature of Flood Detection System.......................................................................................5
2.2 Different Flooding attacks.....................................................................................................7
UDP Flood...............................................................................................................................7
ICMP Flood (Ping)..................................................................................................................8
SYN Flood...............................................................................................................................9
Ping of Death (POD)...............................................................................................................9
Slowloris................................................................................................................................10
NTP Amplification................................................................................................................10
HTTP Flood...........................................................................................................................11
2.3 Issues that are related with the Flooding Detection.............................................................12
Packet Classification..............................................................................................................12
Placement of Detection Mechanism......................................................................................13
Table of Contents
1. Introduction..................................................................................................................................1
1.1 Background Study.................................................................................................................1
1.2 Scope of the Research............................................................................................................3
1.3 Aim of the Research..............................................................................................................4
1.4 Objective of the Research......................................................................................................4
1.5 Research Questions................................................................................................................4
2. Literature Review........................................................................................................................5
2.1 Feature of Flood Detection System.......................................................................................5
2.2 Different Flooding attacks.....................................................................................................7
UDP Flood...............................................................................................................................7
ICMP Flood (Ping)..................................................................................................................8
SYN Flood...............................................................................................................................9
Ping of Death (POD)...............................................................................................................9
Slowloris................................................................................................................................10
NTP Amplification................................................................................................................10
HTTP Flood...........................................................................................................................11
2.3 Issues that are related with the Flooding Detection.............................................................12
Packet Classification..............................................................................................................12
Placement of Detection Mechanism......................................................................................13

2DISSERTATION
Discrepancy between SYNs and FINs...................................................................................15
2.4 Introduction of Wireshark....................................................................................................16
3. Data Evaluation.........................................................................................................................18
3.1 Using of Wireshark..............................................................................................................18
3.1.1 Process to Download and Install Wireshark.................................................................18
3.1.2 Process to Capture Data Packets...................................................................................19
3.1.3 To View and Analyze Packet Contents........................................................................20
3.1.4 Color Rules of Wireshark.............................................................................................21
3.2 Simulation of the Network Attack and using Wireshark for its Detection..........................22
3.2.1 Command used for scanning the active host in the network:.......................................22
3.2.2. Open ports of the targeted host is scanned using the following command:................25
3.2.3. For finding the service running on the port the following command is used..............26
3.2.4. In the next step the metasploitable console is started using the following command. 27
3.2.5. Brute Force attack using File Transfer protocol..........................................................31
3.2.6 Tools used for simulating the attack.............................................................................33
3.2.7 MAC flooding...............................................................................................................35
3.3 Summary..............................................................................................................................37
4. Conclusion and Recommendation.............................................................................................37
4.1 Conclusion...........................................................................................................................37
4.2 Linking with the Objective..................................................................................................39
Discrepancy between SYNs and FINs...................................................................................15
2.4 Introduction of Wireshark....................................................................................................16
3. Data Evaluation.........................................................................................................................18
3.1 Using of Wireshark..............................................................................................................18
3.1.1 Process to Download and Install Wireshark.................................................................18
3.1.2 Process to Capture Data Packets...................................................................................19
3.1.3 To View and Analyze Packet Contents........................................................................20
3.1.4 Color Rules of Wireshark.............................................................................................21
3.2 Simulation of the Network Attack and using Wireshark for its Detection..........................22
3.2.1 Command used for scanning the active host in the network:.......................................22
3.2.2. Open ports of the targeted host is scanned using the following command:................25
3.2.3. For finding the service running on the port the following command is used..............26
3.2.4. In the next step the metasploitable console is started using the following command. 27
3.2.5. Brute Force attack using File Transfer protocol..........................................................31
3.2.6 Tools used for simulating the attack.............................................................................33
3.2.7 MAC flooding...............................................................................................................35
3.3 Summary..............................................................................................................................37
4. Conclusion and Recommendation.............................................................................................37
4.1 Conclusion...........................................................................................................................37
4.2 Linking with the Objective..................................................................................................39

3DISSERTATION
4.3 Recommendations................................................................................................................40
References......................................................................................................................................42
4.3 Recommendations................................................................................................................40
References......................................................................................................................................42
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4DISSERTATION
Table of Figures
Figure 1: TCP states for establishing normal connection................................................................9
Figure 2: Packet Classification Flowchart at Leaf Routers...........................................................16
Figure 3: FDS Installation at Leaf Router.....................................................................................18
Figure 4: Command used for Scanning the Active Host in the Network......................................27
Figure 5: Open Ports of the Targeted Host is scanned..................................................................28
Figure 6: Finding the Service Running on the Port.......................................................................30
Figure 7: Starting Metasploitable Console....................................................................................34
Figure 8: Brute Force Attack.........................................................................................................36
Figure 9: Pinging the Targeted Host..............................................................................................38
Figure 10: Pinging the Targeted Host............................................................................................38
Figure 11: Using Mac Flood..........................................................................................................40
Table of Figures
Figure 1: TCP states for establishing normal connection................................................................9
Figure 2: Packet Classification Flowchart at Leaf Routers...........................................................16
Figure 3: FDS Installation at Leaf Router.....................................................................................18
Figure 4: Command used for Scanning the Active Host in the Network......................................27
Figure 5: Open Ports of the Targeted Host is scanned..................................................................28
Figure 6: Finding the Service Running on the Port.......................................................................30
Figure 7: Starting Metasploitable Console....................................................................................34
Figure 8: Brute Force Attack.........................................................................................................36
Figure 9: Pinging the Targeted Host..............................................................................................38
Figure 10: Pinging the Targeted Host............................................................................................38
Figure 11: Using Mac Flood..........................................................................................................40

5DISSERTATION
Title: Flooding attack Detection using Anomaly Techniques with Wireshark
1. Introduction
1.1 Background Study
Flooding attack can be described as assault technique on the computer network. The
assailant in a flooding attack sends different surges to the users or the administration so that they
can cut down the framework of the network (Hussain et al. 2016). There are many flooding
assaults such as UDP surges, ping surge as well as Syn surge. There are many more surges that
are a part of flooding attack. There are many challenges that describes a state of ping surge
affairs that makes use of ping order for operating the framework as well as wireshark which is to
be delivered. This also helps to setup the casualty that can be utilized which can divide quantity
of all ping parcels that got amid to a predefined period related with edge where the flooding
attack is studied.
The TCP SYN flood is commonly known as DDoS attack (Distributed Denial of Service)
which exploits the normal part of three way handshake of TCP that consumes all resources of
target server as well as render its unresponsive. With the flooding attacks, the mechanism of
three way handshake of TCP gets exploits and there are limitations to maintain the connections
that are half opened (Choi et al. 2014). That particular time when a server receives or gets a SYN
request, the server returns the packet of SYN/ACK (Known as SYN acknowledgement) back to
client. Until the client acknowledges the packet containing SYN/ACK, the connection is stated to
remain in a half open state till when the TCP connection gets timeout. This connection remains
in half open state almost for 75 seconds. Each server has a backlog queue in the memory of the
system so that it can maintain the half open connection. The backlog queue of the system has a
Title: Flooding attack Detection using Anomaly Techniques with Wireshark
1. Introduction
1.1 Background Study
Flooding attack can be described as assault technique on the computer network. The
assailant in a flooding attack sends different surges to the users or the administration so that they
can cut down the framework of the network (Hussain et al. 2016). There are many flooding
assaults such as UDP surges, ping surge as well as Syn surge. There are many more surges that
are a part of flooding attack. There are many challenges that describes a state of ping surge
affairs that makes use of ping order for operating the framework as well as wireshark which is to
be delivered. This also helps to setup the casualty that can be utilized which can divide quantity
of all ping parcels that got amid to a predefined period related with edge where the flooding
attack is studied.
The TCP SYN flood is commonly known as DDoS attack (Distributed Denial of Service)
which exploits the normal part of three way handshake of TCP that consumes all resources of
target server as well as render its unresponsive. With the flooding attacks, the mechanism of
three way handshake of TCP gets exploits and there are limitations to maintain the connections
that are half opened (Choi et al. 2014). That particular time when a server receives or gets a SYN
request, the server returns the packet of SYN/ACK (Known as SYN acknowledgement) back to
client. Until the client acknowledges the packet containing SYN/ACK, the connection is stated to
remain in a half open state till when the TCP connection gets timeout. This connection remains
in half open state almost for 75 seconds. Each server has a backlog queue in the memory of the
system so that it can maintain the half open connection. The backlog queue of the system has a

6DISSERTATION
finite size. When the queue of backlog is full, the limit of the queue is full and at that time all the
connections are dropped.
When SYN request is being spoofed, the server of the victim will not get final packet of
ACK for completing the 3-way handshake (Sahi et al. 2017). The Spoofed requests of SYN
flooding gets easily exhausted to the backlog queue of the victim server. This helps to drop all
the SYN requests. The destination and the stateless based nature of the Internet routine
infrastructure is not able to make a difference between spoofed SYN and the legitimate SYN.
TCP also do not offer very strong authentication on the SYN packets. So when there is SYN
flooding attack, the victim associated with the attack is not able to respond or find out the
legitimate SYN requests ignoring spoofed attack.
To mitigate the SYN flooding attack, there lies several mechanism that defends the
attack. The mechanism that defends the SYN flooding are Synkill, Syn proxying, SynDefender,
Syn cookies, and Syn cache. All the stated above defense mechanism are usually installed in the
firewall server of victim or may also be installed in the server of the victim (Kwon et al. 2015).
Because of these defense mechanisms, sources of SYN flooding attack cannot be detected. The
victims needs to depend on IP trace that are usually expensive for locating the sources of
flooding attack. The defense mechanism described above is stateful mechanism in which all
states are being maintained for all available TCP connection or the state might also require
computation. These solutions makes all defense mechanism exposed to attack to the SYN
attacks. There are many experiments that states the specialized firewall which resist the SYN
flood. These specialized firewall becomes futile for at least 14,000 packets of data in one second.
The stateful mechanism also degrades end – end performance of TCP by incurring the longer
delays while setting the connection of TCP. When there is no attacks of SYN flooding, the
finite size. When the queue of backlog is full, the limit of the queue is full and at that time all the
connections are dropped.
When SYN request is being spoofed, the server of the victim will not get final packet of
ACK for completing the 3-way handshake (Sahi et al. 2017). The Spoofed requests of SYN
flooding gets easily exhausted to the backlog queue of the victim server. This helps to drop all
the SYN requests. The destination and the stateless based nature of the Internet routine
infrastructure is not able to make a difference between spoofed SYN and the legitimate SYN.
TCP also do not offer very strong authentication on the SYN packets. So when there is SYN
flooding attack, the victim associated with the attack is not able to respond or find out the
legitimate SYN requests ignoring spoofed attack.
To mitigate the SYN flooding attack, there lies several mechanism that defends the
attack. The mechanism that defends the SYN flooding are Synkill, Syn proxying, SynDefender,
Syn cookies, and Syn cache. All the stated above defense mechanism are usually installed in the
firewall server of victim or may also be installed in the server of the victim (Kwon et al. 2015).
Because of these defense mechanisms, sources of SYN flooding attack cannot be detected. The
victims needs to depend on IP trace that are usually expensive for locating the sources of
flooding attack. The defense mechanism described above is stateful mechanism in which all
states are being maintained for all available TCP connection or the state might also require
computation. These solutions makes all defense mechanism exposed to attack to the SYN
attacks. There are many experiments that states the specialized firewall which resist the SYN
flood. These specialized firewall becomes futile for at least 14,000 packets of data in one second.
The stateful mechanism also degrades end – end performance of TCP by incurring the longer
delays while setting the connection of TCP. When there is no attacks of SYN flooding, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7DISSERTATION
overheads of the defense mechanism thus becomes more superfluous. To mitigate this issues,
there are also simple stateless mechanisms which helps in detecting the SYN attacks and also
helps to protect the flooding attacks. The mechanisms also can detect the attack when it is near
its source. This helps the tracer to track the flooding source easily without IP trace back that are
very expensive.
Simple methods are available for detecting the SYN flood attacks that are complementary
to defense system that are mentioned above. The simple technique for detecting the SYN attack
is the Flood Detection System (FDS). This is a statelessness as well as has very low computation
feature. The FDS is stated as by-product of the infrastructure of router which makes a difference
in the control packets of TCP from the data packets (Aborujilah and Musa 2017). With the help
of FDS, the attack of SYN flooding can be detected at the leaf routers which connects the end
hosts to Internet. This can be done in place of monitoring all ongoing traffic at the front end
same as the firewall or the proxy. Usually the FDS is deployed in the first mile or can be
deployed in the last mile of all leaf routers. The main advantages of using FDS in the first-mile
of a leaf router is mainly to gain proximity to all the flooding sources. When there is a SYN
flood in the first mile of the leaf router, all the information related to that particular location of
the flooding sources are detected as well as captured. All sources of flooding should be in subnet
where the leaf router stays connected. This helps to save all the work that is required to be done
by IP trace back.
1.2 Scope of the Research
The scope of this research study is to detect the flooding attacks that are that are possible
for online attack. The flooding attacks are detected using the anomaly techniques that are used in
Wireshark. There are many attacks that can be detected using Wireshark. Those attacks are
overheads of the defense mechanism thus becomes more superfluous. To mitigate this issues,
there are also simple stateless mechanisms which helps in detecting the SYN attacks and also
helps to protect the flooding attacks. The mechanisms also can detect the attack when it is near
its source. This helps the tracer to track the flooding source easily without IP trace back that are
very expensive.
Simple methods are available for detecting the SYN flood attacks that are complementary
to defense system that are mentioned above. The simple technique for detecting the SYN attack
is the Flood Detection System (FDS). This is a statelessness as well as has very low computation
feature. The FDS is stated as by-product of the infrastructure of router which makes a difference
in the control packets of TCP from the data packets (Aborujilah and Musa 2017). With the help
of FDS, the attack of SYN flooding can be detected at the leaf routers which connects the end
hosts to Internet. This can be done in place of monitoring all ongoing traffic at the front end
same as the firewall or the proxy. Usually the FDS is deployed in the first mile or can be
deployed in the last mile of all leaf routers. The main advantages of using FDS in the first-mile
of a leaf router is mainly to gain proximity to all the flooding sources. When there is a SYN
flood in the first mile of the leaf router, all the information related to that particular location of
the flooding sources are detected as well as captured. All sources of flooding should be in subnet
where the leaf router stays connected. This helps to save all the work that is required to be done
by IP trace back.
1.2 Scope of the Research
The scope of this research study is to detect the flooding attacks that are that are possible
for online attack. The flooding attacks are detected using the anomaly techniques that are used in
Wireshark. There are many attacks that can be detected using Wireshark. Those attacks are

8DISSERTATION
discussed in this research paper. The detection method of one such attack and the mitigation
process are also described briefly in this study.
1.3 Aim of the Research
The aim of this research paper is to study the features of Wireshark finding out the
flooding attacks. The flooding attacks are detected with the anomaly technologies that are used
in the Wireshark packet analyzer.
1.4 Objective of the Research
The objectives of the research paper are described below:
To find out the types of flooding attack that are possible for online attack.
To investigate all such issues that leads to detection of flooding attack.
To study the attack detection technique of flooding attack.
To evaluate the attack detection methodology for the anomaly detection.
To study the characteristics of Wireshark application in detecting the flooding attack.
1.5 Research Questions
The research question that will be addressed in this research paper includes
What are the types of flooding attack that are possible for online attack?
What are the issues that leads to detection of flooding attack?
How to carry out the attack detection technique of flooding attack?
What are the processes that helps to evaluate the attack detection methodology for the
anomaly detection?
discussed in this research paper. The detection method of one such attack and the mitigation
process are also described briefly in this study.
1.3 Aim of the Research
The aim of this research paper is to study the features of Wireshark finding out the
flooding attacks. The flooding attacks are detected with the anomaly technologies that are used
in the Wireshark packet analyzer.
1.4 Objective of the Research
The objectives of the research paper are described below:
To find out the types of flooding attack that are possible for online attack.
To investigate all such issues that leads to detection of flooding attack.
To study the attack detection technique of flooding attack.
To evaluate the attack detection methodology for the anomaly detection.
To study the characteristics of Wireshark application in detecting the flooding attack.
1.5 Research Questions
The research question that will be addressed in this research paper includes
What are the types of flooding attack that are possible for online attack?
What are the issues that leads to detection of flooding attack?
How to carry out the attack detection technique of flooding attack?
What are the processes that helps to evaluate the attack detection methodology for the
anomaly detection?

9DISSERTATION
2. Literature Review
2.1 Feature of Flood Detection System
According to Modi and Quadir (2014), the main feature of the FDS is utilizing inherent
behavior of TCP SYN– FIN pairs which is used for detecting flooding attack. All packets of
SYN/FIN limits starting as well as ending of the all the TCP connection. The beginning is the
SYN packet and the ending is the FIN packet. The figure below shows the TCP is borrowed from
showing the results of SYN packets. One comes from the result of SYN packet and the other
comes from FIN packet. There is a difference between SYN and the SYN/ACK packet. There is
no particular way to separate the FINs that are active from the FINs that are passive. This is
because the end host under particular leaf router might be server or a client. So, the pairs of
SYN-FIN is usually referred as (SYN, FIN) as well as (SYN/ACK, FIN). The packets of SYN
are mainly generalized so that they can be included in the pure of SYN as well as SYN/ACK
packets. The SYN-FIN pair of packet gets violated by the RST packet. Many of the RST packets
are generated to cancel the TCP connection2. But there is still a possibility to get a SYN-RST
pair.
2. Literature Review
2.1 Feature of Flood Detection System
According to Modi and Quadir (2014), the main feature of the FDS is utilizing inherent
behavior of TCP SYN– FIN pairs which is used for detecting flooding attack. All packets of
SYN/FIN limits starting as well as ending of the all the TCP connection. The beginning is the
SYN packet and the ending is the FIN packet. The figure below shows the TCP is borrowed from
showing the results of SYN packets. One comes from the result of SYN packet and the other
comes from FIN packet. There is a difference between SYN and the SYN/ACK packet. There is
no particular way to separate the FINs that are active from the FINs that are passive. This is
because the end host under particular leaf router might be server or a client. So, the pairs of
SYN-FIN is usually referred as (SYN, FIN) as well as (SYN/ACK, FIN). The packets of SYN
are mainly generalized so that they can be included in the pure of SYN as well as SYN/ACK
packets. The SYN-FIN pair of packet gets violated by the RST packet. Many of the RST packets
are generated to cancel the TCP connection2. But there is still a possibility to get a SYN-RST
pair.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10DISSERTATION
Figure 1: TCP states for establishing normal connection
(Source: Bijalwan et al. 2015)
There are packet classifications which differentiates the RST packets, TCP SYN packets
and the FIN packets at the leaf routers (Aung and Thant 2017). This classification of packet was
motivated for providing the service that differentiate the IP flows. For distinguishing the control
packets of TCP, there are packets of large scale mechanisms for controlling the TCP packets of
the routers at a very high speed.
The leaf routers particularly have no state or might have state which is used for in the
Flood Detection System. Three new variables are there at the leaf routers for measuring the total
number of SYN received, RST packets as well as FIN at inbound as well as in outbound
interface (Khandelwal, Gupta and Bhale 2016). Traffic flows from Internet to Intranet and is
known as inbound and traffic that flows from Intranet to Internet is known as outbound.
Figure 1: TCP states for establishing normal connection
(Source: Bijalwan et al. 2015)
There are packet classifications which differentiates the RST packets, TCP SYN packets
and the FIN packets at the leaf routers (Aung and Thant 2017). This classification of packet was
motivated for providing the service that differentiate the IP flows. For distinguishing the control
packets of TCP, there are packets of large scale mechanisms for controlling the TCP packets of
the routers at a very high speed.
The leaf routers particularly have no state or might have state which is used for in the
Flood Detection System. Three new variables are there at the leaf routers for measuring the total
number of SYN received, RST packets as well as FIN at inbound as well as in outbound
interface (Khandelwal, Gupta and Bhale 2016). Traffic flows from Internet to Intranet and is
known as inbound and traffic that flows from Intranet to Internet is known as outbound.

11DISSERTATION
Depending on behavior of the SYN-FIN pair, the total number of SYN as well as the FIN
packets that are modelled as stationary are different from each other, random process as well as
the FDS (Flood Detection System) is considered as an example of Sequential Change Point
Detection. For making an independent FDS all sites and for accessing the patterns, comparison
between number of SYN as well as FIN is basically normalized by an average number of RST
that is considered as estimation. A method known as CUSUM (Cumulative Sum) is applied
which is a non-parametric method for making FDS more applicable and also makes the
deployment easier (Kolias et al. 2016). There is efficacy for the detection mechanism which is
validated by the simulations that are trace driven. The results from evaluation mainly shows that
the FDS has very short time of detection and has very high accuracy detection level. Because of
the close proximity of the flooding sources as well as the detection mechanism, the SYN flood
attacks are being harmed and location of the flooding attacks are also revealed to the tracer
(Alam, Arafat and Ahmed 2015). All details of flooding attack and the detection and prevention
methods are mentioned in this study.
2.2 Different Flooding attacks
The common DDoS attacks that are used commonly are described below.
UDP Flood
The UDP flood, commonly known as User Datagram Protocol packets (UDP) packets.
The main goal of UDP attack is flooding the random ports that comes on the remote hosts. This
helps to cause host to check the application listening at the port in a repeated way (Osanaiye and
Dlodlo 2015). When application is not found, then the reply is done with ICMP packet which is
also known as Destination Unreachable. This process helps to sap the host resources that leads to
inaccessibility.
Depending on behavior of the SYN-FIN pair, the total number of SYN as well as the FIN
packets that are modelled as stationary are different from each other, random process as well as
the FDS (Flood Detection System) is considered as an example of Sequential Change Point
Detection. For making an independent FDS all sites and for accessing the patterns, comparison
between number of SYN as well as FIN is basically normalized by an average number of RST
that is considered as estimation. A method known as CUSUM (Cumulative Sum) is applied
which is a non-parametric method for making FDS more applicable and also makes the
deployment easier (Kolias et al. 2016). There is efficacy for the detection mechanism which is
validated by the simulations that are trace driven. The results from evaluation mainly shows that
the FDS has very short time of detection and has very high accuracy detection level. Because of
the close proximity of the flooding sources as well as the detection mechanism, the SYN flood
attacks are being harmed and location of the flooding attacks are also revealed to the tracer
(Alam, Arafat and Ahmed 2015). All details of flooding attack and the detection and prevention
methods are mentioned in this study.
2.2 Different Flooding attacks
The common DDoS attacks that are used commonly are described below.
UDP Flood
The UDP flood, commonly known as User Datagram Protocol packets (UDP) packets.
The main goal of UDP attack is flooding the random ports that comes on the remote hosts. This
helps to cause host to check the application listening at the port in a repeated way (Osanaiye and
Dlodlo 2015). When application is not found, then the reply is done with ICMP packet which is
also known as Destination Unreachable. This process helps to sap the host resources that leads to
inaccessibility.

12DISSERTATION
Brute Force Attack
The brute force attack is basically a trial as well as error method that is used by the
hackers for guessing the credentials or the encrypted data which includes the login, encryption
keys, as well as the passwords. The brute force attack needs an exhaustive effort. Agarwal et al.
(2016) said that this attack is one of the popular attacks for cracking the methods which is used
for hacking the WordPress now a days.
The most important advantage of the brute force attack is this attack is very simple to
perform and ample time can be taken to perform this attack. The systems that are password based
as well as has encryption key that are to be cracked by using the brute force attack. Akhtar
(2018) explained that the total amount of time that is used for brute forcing a system is done in
metric. The analyzed time to brute force the system is also mentioned in seconds in the
evaluation that is carried out. The security level of system is gauged in this way.
Mualfah and Riadi (2017) explained that the brute force attack is very slow which he
stated this as a disadvantage of brute force attack. As this attack is carried out by hit and trial
attack, so it takes time to get the combination of password for achieving the goal. This
sluggishness of this attack includes number of characters in target string to increase (Bachupally,
Yuan and Roy 2016). For instance, taking a combination of password having four characters
takes much more time to brute those compared to a password having three character. After a
certain point beyond the count of character, the brute force becomes unrealistic.
ICMP Flood (Ping)
Chen et al. (2015) explained that this principle is similar to that of UDP flood attack. In a
single ICMP flood meets the targeted resource with the ICMP Echo Request packets that are also
Brute Force Attack
The brute force attack is basically a trial as well as error method that is used by the
hackers for guessing the credentials or the encrypted data which includes the login, encryption
keys, as well as the passwords. The brute force attack needs an exhaustive effort. Agarwal et al.
(2016) said that this attack is one of the popular attacks for cracking the methods which is used
for hacking the WordPress now a days.
The most important advantage of the brute force attack is this attack is very simple to
perform and ample time can be taken to perform this attack. The systems that are password based
as well as has encryption key that are to be cracked by using the brute force attack. Akhtar
(2018) explained that the total amount of time that is used for brute forcing a system is done in
metric. The analyzed time to brute force the system is also mentioned in seconds in the
evaluation that is carried out. The security level of system is gauged in this way.
Mualfah and Riadi (2017) explained that the brute force attack is very slow which he
stated this as a disadvantage of brute force attack. As this attack is carried out by hit and trial
attack, so it takes time to get the combination of password for achieving the goal. This
sluggishness of this attack includes number of characters in target string to increase (Bachupally,
Yuan and Roy 2016). For instance, taking a combination of password having four characters
takes much more time to brute those compared to a password having three character. After a
certain point beyond the count of character, the brute force becomes unrealistic.
ICMP Flood (Ping)
Chen et al. (2015) explained that this principle is similar to that of UDP flood attack. In a
single ICMP flood meets the targeted resource with the ICMP Echo Request packets that are also
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13DISSERTATION
known as ping packets which sends packets very fast without any type of the reply from the
victim. This flood attack usually consumes incoming bandwidth as well as outgoing bandwidth.
This is because each server of the victim will respond to all packets of ICMP Echo Reply that
results in slowing down the system.
SYN Flood Attack
The SYN flood of DDoS attack mainly exploits the weakness of the TCP connection that
are also known as three way handshake attack (Hoque et al. 2014). In this attack the SYN
request will start the TCP connection along with the host that are to be answered with the SYN-
ACK packet response from a host. After that ACK response is provided from the requester
requesting the packet. A requester sends many SYN requests in a SYN flood attack. But they do
not respond to response SYN-ACK of the host. They also do not send SYN requests from the IP
address that is spoofed. Host system waits for the acknowledgement for all the requests and also
binds the resources until no connections are made and then results packet as a denial of service.
Ping of Death (POD)
Skowyra et al. (2018) stated the POD attack (Ping of Death) involves attacker to send
many malicious or malformed pings in a computer. The total length of the IP packet includes
maximum of 65,535 bytes. Data link layer of the TCP generally limits the maximum frame size
such as 1500 bytes over the Ethernet network. Total length of the IP packet along with the header
is 65,535 bytes. Data Link Layer mainly decrease the size of the frame to a certain limit. For
instance, 1500 bytes for the Ethernet network. A very large IP packet is then distributed over
many IP packets that are commonly known as fragments. Recipient hosts also reassembles the
fragments of IP in a complete packet. (Kshirsagar et al. 2016) explained in this POD scenario,
malicious manipulation is done over the fragment content and also the recipient comes to an end
known as ping packets which sends packets very fast without any type of the reply from the
victim. This flood attack usually consumes incoming bandwidth as well as outgoing bandwidth.
This is because each server of the victim will respond to all packets of ICMP Echo Reply that
results in slowing down the system.
SYN Flood Attack
The SYN flood of DDoS attack mainly exploits the weakness of the TCP connection that
are also known as three way handshake attack (Hoque et al. 2014). In this attack the SYN
request will start the TCP connection along with the host that are to be answered with the SYN-
ACK packet response from a host. After that ACK response is provided from the requester
requesting the packet. A requester sends many SYN requests in a SYN flood attack. But they do
not respond to response SYN-ACK of the host. They also do not send SYN requests from the IP
address that is spoofed. Host system waits for the acknowledgement for all the requests and also
binds the resources until no connections are made and then results packet as a denial of service.
Ping of Death (POD)
Skowyra et al. (2018) stated the POD attack (Ping of Death) involves attacker to send
many malicious or malformed pings in a computer. The total length of the IP packet includes
maximum of 65,535 bytes. Data link layer of the TCP generally limits the maximum frame size
such as 1500 bytes over the Ethernet network. Total length of the IP packet along with the header
is 65,535 bytes. Data Link Layer mainly decrease the size of the frame to a certain limit. For
instance, 1500 bytes for the Ethernet network. A very large IP packet is then distributed over
many IP packets that are commonly known as fragments. Recipient hosts also reassembles the
fragments of IP in a complete packet. (Kshirsagar et al. 2016) explained in this POD scenario,
malicious manipulation is done over the fragment content and also the recipient comes to an end

14DISSERTATION
with the IP packet that is bigger than the 65,535 bytes when they are reassembled. This helps to
overflow the memory buffer that are allocated to the packet with the denial of service attack for
the legitimate packets.
Slowloris
(Zaalouk et al. 2014) stated the next attack that is done is the Slowloris attack. This attack
enables a particular web server that takes down all other servers. This does not affects different
services or any other ports on the target network. This Slowloris attack implements the attack by
holding all connections to target the open of the web server for a longer time. Slowloris
accomplishes the connection which creates such connections to target the web server but sends
only a partial request. This attack then sends more number of HTTP headers but they cannot
complete the request. The server that is targeted mainly keeps all the false connections left open
(Alsadhan et al. 2018). The largest concurrent pool connection eventually overflows and this
denies to establish extra connections from the legitimate clients.
NTP Amplification
The next attack that is generally possible is the NTP amplification attack. In this attack,
the perpetrator helps in exploiting all the accessible servers of Network Time Protocol (NTP)
that are available publically. This is done so that the target server gets overwhelmed with the
UDP traffic. The NTP amplification type of attack is mainly known as amplification assault
(Ndatinya et al. 2015). This is due to the query as well as the response ratio in those scenarios
comes between 1:20 or may be 1:200. This defines that any attacker who obtains list of the open
NTP server can generate a great bandwidth with high volume of the DDoS attack. For example,
the NTP amplification can use a tool known as Metasploit or the data coming from Open NTP
project.
with the IP packet that is bigger than the 65,535 bytes when they are reassembled. This helps to
overflow the memory buffer that are allocated to the packet with the denial of service attack for
the legitimate packets.
Slowloris
(Zaalouk et al. 2014) stated the next attack that is done is the Slowloris attack. This attack
enables a particular web server that takes down all other servers. This does not affects different
services or any other ports on the target network. This Slowloris attack implements the attack by
holding all connections to target the open of the web server for a longer time. Slowloris
accomplishes the connection which creates such connections to target the web server but sends
only a partial request. This attack then sends more number of HTTP headers but they cannot
complete the request. The server that is targeted mainly keeps all the false connections left open
(Alsadhan et al. 2018). The largest concurrent pool connection eventually overflows and this
denies to establish extra connections from the legitimate clients.
NTP Amplification
The next attack that is generally possible is the NTP amplification attack. In this attack,
the perpetrator helps in exploiting all the accessible servers of Network Time Protocol (NTP)
that are available publically. This is done so that the target server gets overwhelmed with the
UDP traffic. The NTP amplification type of attack is mainly known as amplification assault
(Ndatinya et al. 2015). This is due to the query as well as the response ratio in those scenarios
comes between 1:20 or may be 1:200. This defines that any attacker who obtains list of the open
NTP server can generate a great bandwidth with high volume of the DDoS attack. For example,
the NTP amplification can use a tool known as Metasploit or the data coming from Open NTP
project.

15DISSERTATION
MAC flooding Attack
According to Kaur (2018), a computer network, the MAC flooding is considered as a
technique that is employed for compromising the switches security in the network. The switches
are maintained in a list. The list showing the switches are known as CAM table. This helps to
map the individual MAC address that are on the network for the physical ports that are the
switch.
This helps in sending the data out in the physical port where the victim computer is
situated. This attack does not indiscriminate the data broadcasting of all ports like that of a hub
(Gupta and Badve 2017). The main advantage that the MAC flood presents is that the data is
routed to network the segment that contains computer in which data are particularly designed.
Paharia and Bhushan (2018) said in MAC flooding attack, a particular switch is mainly
flooded with packets of data that contains different MAC addresses usually from different
sources. This helps in consuming a limited memory aside in which the switch stores all the
addresses of MAC translated to physical port. This table is known as transition table. The result
that is obtained with the MAC flood. After performing this MAC flood attack, the switch enters a
state known as the failopen mode. In this mode, all the packets that are broadcasted out similar to
a hub. The broadcast are done on all ports rather than broadcasting the incoming packets on a
particular port.
In a MAC flood, malicious user can also use a packet sniffer by running promiscuous
mode for capturing the sensitive data that comes from all other computers. Sensitive data
includes e-mails, messaging conversations, or unencrypted passwords (Rai and Haldkar 2015).
These sensitive data will not be working if they were only working on a switch normally.
MAC flooding Attack
According to Kaur (2018), a computer network, the MAC flooding is considered as a
technique that is employed for compromising the switches security in the network. The switches
are maintained in a list. The list showing the switches are known as CAM table. This helps to
map the individual MAC address that are on the network for the physical ports that are the
switch.
This helps in sending the data out in the physical port where the victim computer is
situated. This attack does not indiscriminate the data broadcasting of all ports like that of a hub
(Gupta and Badve 2017). The main advantage that the MAC flood presents is that the data is
routed to network the segment that contains computer in which data are particularly designed.
Paharia and Bhushan (2018) said in MAC flooding attack, a particular switch is mainly
flooded with packets of data that contains different MAC addresses usually from different
sources. This helps in consuming a limited memory aside in which the switch stores all the
addresses of MAC translated to physical port. This table is known as transition table. The result
that is obtained with the MAC flood. After performing this MAC flood attack, the switch enters a
state known as the failopen mode. In this mode, all the packets that are broadcasted out similar to
a hub. The broadcast are done on all ports rather than broadcasting the incoming packets on a
particular port.
In a MAC flood, malicious user can also use a packet sniffer by running promiscuous
mode for capturing the sensitive data that comes from all other computers. Sensitive data
includes e-mails, messaging conversations, or unencrypted passwords (Rai and Haldkar 2015).
These sensitive data will not be working if they were only working on a switch normally.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16DISSERTATION
HTTP Flood
Shamshirband et al. (2015) said that in HTTP DDoS flood attack, an attacker exploits all
legitimate HTTP Post as well as Get requests that are available to attack web application or web
server. The HTTP flood mostly do not use any malformed packets, reflection techniques as well
as spoofing and also requires low bandwidth compared to all other attacks for bringing down all
the targeted server or the site. This attack becomes most effective attack when this forces the
application or the server for allocating maximum resources that are possible in response of a
single packet.
2.3 Issues that are related with the Flooding Detection
There are many issues that are faced while detecting the flooding attack. The issues that
are related with Flooding detection attack are described below.
Packet Classification
Singh, Singh and De (2016) said for identifying the TCP SYNs, RSTs and FINs, the
header of TCP are accessed. The identifications are generally from many trusted entities for all
clients connected in the same intranet. There is a multi-layer protocol known as IPSec that is
proposed and allows all trusted routers for accessing transport layer information. So, for securing
the IPSec at the network level, there should not be any type of obstacle for identifying as well as
counting the TCP SYNs, RSTs and FINs in the leaf routers. There is a detailed description
algorithm of classification of packet in the figure given below. In Figure 2, the starting two steps
mainly guarantees the IP packet that has a TCP header. IP packet has a TCP header should has
offset of zero fragmentation. Most of the IP options are available for the testing the network or
for the debugging the network (Noman, Abdullah and Mohammed 2015). This is done to
pinpoint offset of the TCP CODE BITs accurately in a particular IP packet. A header length of 4-
HTTP Flood
Shamshirband et al. (2015) said that in HTTP DDoS flood attack, an attacker exploits all
legitimate HTTP Post as well as Get requests that are available to attack web application or web
server. The HTTP flood mostly do not use any malformed packets, reflection techniques as well
as spoofing and also requires low bandwidth compared to all other attacks for bringing down all
the targeted server or the site. This attack becomes most effective attack when this forces the
application or the server for allocating maximum resources that are possible in response of a
single packet.
2.3 Issues that are related with the Flooding Detection
There are many issues that are faced while detecting the flooding attack. The issues that
are related with Flooding detection attack are described below.
Packet Classification
Singh, Singh and De (2016) said for identifying the TCP SYNs, RSTs and FINs, the
header of TCP are accessed. The identifications are generally from many trusted entities for all
clients connected in the same intranet. There is a multi-layer protocol known as IPSec that is
proposed and allows all trusted routers for accessing transport layer information. So, for securing
the IPSec at the network level, there should not be any type of obstacle for identifying as well as
counting the TCP SYNs, RSTs and FINs in the leaf routers. There is a detailed description
algorithm of classification of packet in the figure given below. In Figure 2, the starting two steps
mainly guarantees the IP packet that has a TCP header. IP packet has a TCP header should has
offset of zero fragmentation. Most of the IP options are available for the testing the network or
for the debugging the network (Noman, Abdullah and Mohammed 2015). This is done to
pinpoint offset of the TCP CODE BITs accurately in a particular IP packet. A header length of 4-
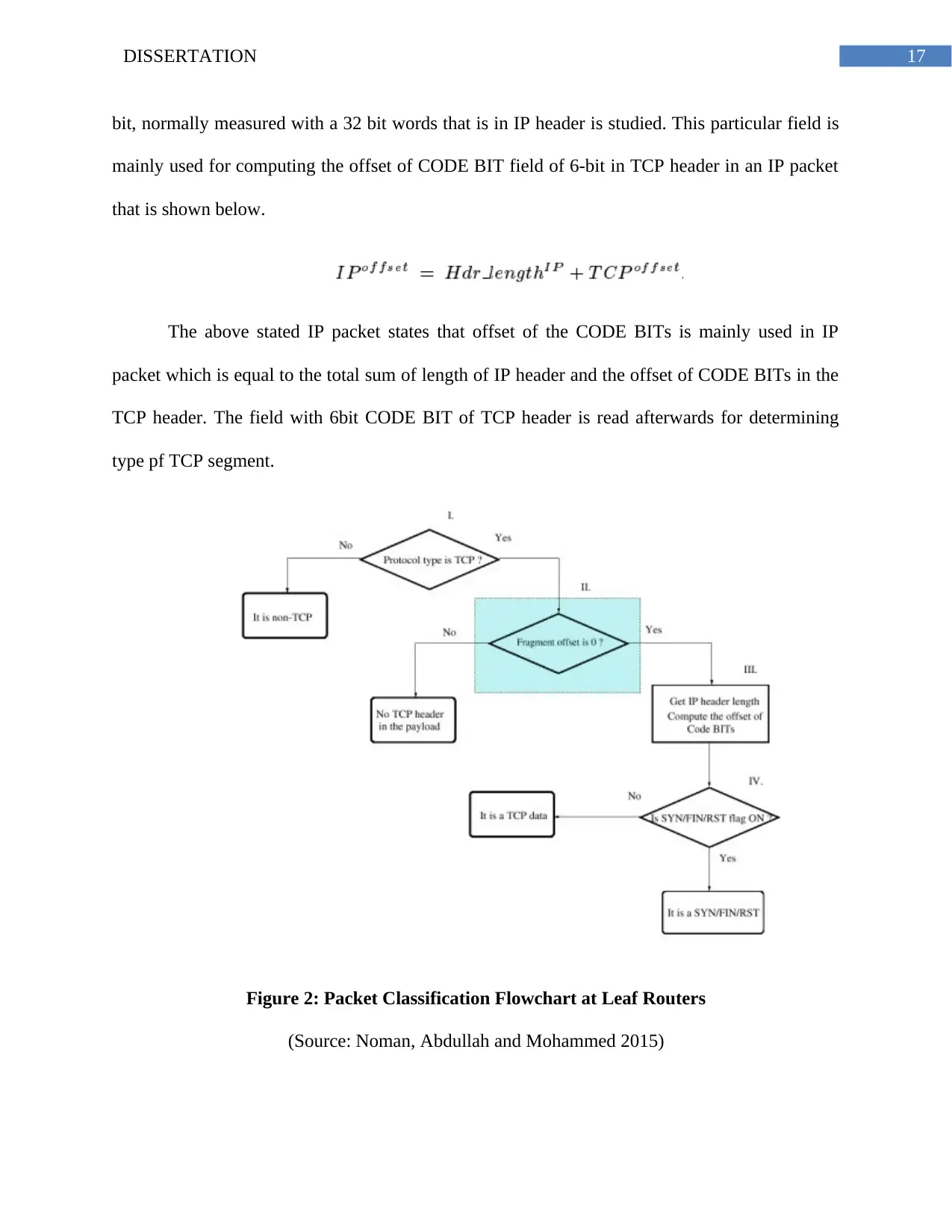
17DISSERTATION
bit, normally measured with a 32 bit words that is in IP header is studied. This particular field is
mainly used for computing the offset of CODE BIT field of 6-bit in TCP header in an IP packet
that is shown below.
The above stated IP packet states that offset of the CODE BITs is mainly used in IP
packet which is equal to the total sum of length of IP header and the offset of CODE BITs in the
TCP header. The field with 6bit CODE BIT of TCP header is read afterwards for determining
type pf TCP segment.
Figure 2: Packet Classification Flowchart at Leaf Routers
(Source: Noman, Abdullah and Mohammed 2015)
bit, normally measured with a 32 bit words that is in IP header is studied. This particular field is
mainly used for computing the offset of CODE BIT field of 6-bit in TCP header in an IP packet
that is shown below.
The above stated IP packet states that offset of the CODE BITs is mainly used in IP
packet which is equal to the total sum of length of IP header and the offset of CODE BITs in the
TCP header. The field with 6bit CODE BIT of TCP header is read afterwards for determining
type pf TCP segment.
Figure 2: Packet Classification Flowchart at Leaf Routers
(Source: Noman, Abdullah and Mohammed 2015)

18DISSERTATION
Placement of the Detection Mechanism
As discussed above, the Flood Detection System (FDS) that are to be installed in the first
mile or in the last mile of the lead router (Yusof, Ali and Darus 2017). All the leaf router can be
implemented in first mile or in the router of last mile. The implementation of FDS mainly
depends on direction where network traffic flows in between the Internet and the Intranet. For all
packets that are going out of intranet, leaf router is considered to as the first mile router. Whereas
for all incoming packets that comes in the intranet, leaf router is the last mile as well. For getting
a secured connection, deploying FDS (Flood Detection System) is done at the inbound interface
as well as in the outbound interfaces. The FDS that is installed in the outbound is known as the
first mile of FDS and the FDS which is installed at the inbound interface is the last mile of FDS.
The below stated figure 3 shows installation of the FDS at leaf router. Both the FDS at
each interface co-ordinates with each other through some shared memory or through the IPC that
is implemented inside the router (Robinson and Thomas 2015). First mile FDS in a leaf router
mainly has the primary role for detecting the flooding attack because of the proximity to all
sources included in the flooding attack. Detection of sensitivity mainly declines with increasing
the size of the attack group. Basically in a large scale DDoS attack, the flooding sources are
orchestrated. This is done so that the flooding traffic done individually causes some significant
difference from traffic pattern that happens normally. Karami and Guerrero-Zapata (2015) said
that the last mile of FDS on the other hand detects flooding attack very quickly because all
flooding traffic is summed up in the last mile router. But this FDS detection cannot guess the
sources of flooding attack. There is a particular defense system known as SynDefender which are
triggered for protecting the network of the victim. This makes flooding attack harder to succeed
in doing the successful attack. To protect the network of the victim, the flooding rates of the
Placement of the Detection Mechanism
As discussed above, the Flood Detection System (FDS) that are to be installed in the first
mile or in the last mile of the lead router (Yusof, Ali and Darus 2017). All the leaf router can be
implemented in first mile or in the router of last mile. The implementation of FDS mainly
depends on direction where network traffic flows in between the Internet and the Intranet. For all
packets that are going out of intranet, leaf router is considered to as the first mile router. Whereas
for all incoming packets that comes in the intranet, leaf router is the last mile as well. For getting
a secured connection, deploying FDS (Flood Detection System) is done at the inbound interface
as well as in the outbound interfaces. The FDS that is installed in the outbound is known as the
first mile of FDS and the FDS which is installed at the inbound interface is the last mile of FDS.
The below stated figure 3 shows installation of the FDS at leaf router. Both the FDS at
each interface co-ordinates with each other through some shared memory or through the IPC that
is implemented inside the router (Robinson and Thomas 2015). First mile FDS in a leaf router
mainly has the primary role for detecting the flooding attack because of the proximity to all
sources included in the flooding attack. Detection of sensitivity mainly declines with increasing
the size of the attack group. Basically in a large scale DDoS attack, the flooding sources are
orchestrated. This is done so that the flooding traffic done individually causes some significant
difference from traffic pattern that happens normally. Karami and Guerrero-Zapata (2015) said
that the last mile of FDS on the other hand detects flooding attack very quickly because all
flooding traffic is summed up in the last mile router. But this FDS detection cannot guess the
sources of flooding attack. There is a particular defense system known as SynDefender which are
triggered for protecting the network of the victim. This makes flooding attack harder to succeed
in doing the successful attack. To protect the network of the victim, the flooding rates of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19DISSERTATION
flooding sources are to be increased. But, with the increase in flooding traffic, it is easy to detect
flooding attack and all the sources that are in the first mile router (Salunkhe, Jadhav and Bhosale
2017). The FDS (Flood Detection Systems) are not recommended for installing in core routers
because of two main reason. Firstly, FDS is not close to the flooding system or to the victim.
Secondly, the packets in same flow can traverse in all different paths.
Figure 3: FDS Installation at Leaf Router
(Source: Salunkhe, Jadhav and Bhosale 2017)
Discrepancy between SYNs and FINs
Pacheco and Hariri (2016) stated in a normal condition, the semantics of TCP mainly
requires one to one match in between the FINs and the SYNs. In reality, there always remains a
discrepancy in between the total number of FINs and SYNs. Along with the small number of
long TCP sessions, there are also other major cause of difference that lies in RST packets. There
are single RST packets those are capable of terminating TCP session even without generating
FIN packet. Single RST violates the behavior of SYN and FIN pair (Sharma et al. 2015). There
are two reasons for generating the RSTs. One of those reasons for generating RSTs is that it is
passive. This is because that the RST gets transmitted when there is response to arrival of packet
which is attached to closed port. (Anbar et al. 2018) stated the second reason for using the RST
flooding sources are to be increased. But, with the increase in flooding traffic, it is easy to detect
flooding attack and all the sources that are in the first mile router (Salunkhe, Jadhav and Bhosale
2017). The FDS (Flood Detection Systems) are not recommended for installing in core routers
because of two main reason. Firstly, FDS is not close to the flooding system or to the victim.
Secondly, the packets in same flow can traverse in all different paths.
Figure 3: FDS Installation at Leaf Router
(Source: Salunkhe, Jadhav and Bhosale 2017)
Discrepancy between SYNs and FINs
Pacheco and Hariri (2016) stated in a normal condition, the semantics of TCP mainly
requires one to one match in between the FINs and the SYNs. In reality, there always remains a
discrepancy in between the total number of FINs and SYNs. Along with the small number of
long TCP sessions, there are also other major cause of difference that lies in RST packets. There
are single RST packets those are capable of terminating TCP session even without generating
FIN packet. Single RST violates the behavior of SYN and FIN pair (Sharma et al. 2015). There
are two reasons for generating the RSTs. One of those reasons for generating RSTs is that it is
passive. This is because that the RST gets transmitted when there is response to arrival of packet
which is attached to closed port. (Anbar et al. 2018) stated the second reason for using the RST

20DISSERTATION
is that it is very active. The RST gets started while aborting TCP connection. The active RST is
then associated with SYN from that session because both session are seen by same FDS. The
RST those are passive cannot associated with SYN in the same FDS. This is because the passive
RST and the corresponding SYN goes through various FDSs. The passive RSTs actually has
nothing to do with a SYN. For example, arrival of data packet lately to a port that is already
closed leads to transmission of the RST. The passive RTS are generally treated as the
background noise.
From the above discussion, it can be stated that the FDS is not accurate for detecting
flood attack. There are three different SYN pairs that are considered as normal behavior of the
TCP. Three types of SYN pairs are (SYN, FIN), (SYN/ACK, FIN). FDS cannot differentiate
between the active RSTs and the passive RSTs. Two simple ways can be used for solving this
problem of FDS. The first resolution is to treat all the RSTs as an active packet and second is
also to treat the RSTs as a passive packet. The first way of considering the RST packets as active
packets helps in reducing FDS detection in a sensitive way (Bandara et al. 2016). The second
way helps in rising FDS alarm rate when it is false. For making trade-off between the detection
sensitivity as well as detect the false alarm rate, it is very important setting proper threshold so
that they can filter maximum of background noise. Observing this condition under normally,
firstly it can be summarized that SYN and the RSTs have very strong correlation between them.
The second observation is that the difference in between total number of SYN and the FIN is
very similar to RSTs. The total passive RSTs are very small in percentage out of the total number
of RSTs. So, the threshold is set to be 75% (Fleming and Wilander 2018). This implies that three
RSTs out of 4 RSTs are considered as an active one. The FDS also has a negative impact on all
the passive RSTs which are not correctly stated as the active RST one. In the CUSUM algorithm,
is that it is very active. The RST gets started while aborting TCP connection. The active RST is
then associated with SYN from that session because both session are seen by same FDS. The
RST those are passive cannot associated with SYN in the same FDS. This is because the passive
RST and the corresponding SYN goes through various FDSs. The passive RSTs actually has
nothing to do with a SYN. For example, arrival of data packet lately to a port that is already
closed leads to transmission of the RST. The passive RTS are generally treated as the
background noise.
From the above discussion, it can be stated that the FDS is not accurate for detecting
flood attack. There are three different SYN pairs that are considered as normal behavior of the
TCP. Three types of SYN pairs are (SYN, FIN), (SYN/ACK, FIN). FDS cannot differentiate
between the active RSTs and the passive RSTs. Two simple ways can be used for solving this
problem of FDS. The first resolution is to treat all the RSTs as an active packet and second is
also to treat the RSTs as a passive packet. The first way of considering the RST packets as active
packets helps in reducing FDS detection in a sensitive way (Bandara et al. 2016). The second
way helps in rising FDS alarm rate when it is false. For making trade-off between the detection
sensitivity as well as detect the false alarm rate, it is very important setting proper threshold so
that they can filter maximum of background noise. Observing this condition under normally,
firstly it can be summarized that SYN and the RSTs have very strong correlation between them.
The second observation is that the difference in between total number of SYN and the FIN is
very similar to RSTs. The total passive RSTs are very small in percentage out of the total number
of RSTs. So, the threshold is set to be 75% (Fleming and Wilander 2018). This implies that three
RSTs out of 4 RSTs are considered as an active one. The FDS also has a negative impact on all
the passive RSTs which are not correctly stated as the active RST one. In the CUSUM algorithm,

21DISSERTATION
there is a way to reset the value to zero for the negative difference that comes between total
number of the SYNs and total number of FINs by eliminating cumulative effects. As a result
there is a spike on the background noise which degrades sensitive detection in one observation
period.
2.4 Introduction of Wireshark
(Zhang et al. 2016) introduced the wireshark is considered as a tool that is open source
which help in profiling the network traffic as well as analyzing all the packets. The wireshark is a
tool of network analyzer, a protocol analyzer of network or a sniffer. The wireshark is formerly
described as Ethereal (Liu, Lai and Zhang 2017). This is use for examining all the details of
traffic at different levels that ranges from the information of connection level to bits which are
responsible for making single packet. The packet capture helps in providing network
administrator all necessary information related to the individual packets including transmit time,
destination, header data, and protocol type and source data. The information are mainly used for
evaluating the security events and helps in troubleshooting the issues of network security device.
Shaik et al. (2015) said that wireshark mainly display the information usually in three
different panels. The top panels lists all the frames that works individually with the key data on a
single line. A particular single frame is then selected in the top pane which is explained further in
middle panel tool. In the display section, the Wireshark shows all the packet details which
explains the important aspects of frame that are considered as the belonging of data link layer,
application layer, transport layer, and network layer (Kaur et al. 2015). The bottom pane of the
Wireshark displays the raw frame with the hexadecimal rendition on left and their corresponding
ASCII values on right. The wireshark is mainly used for eavesdropping. It is an organizational
tool in which the privacy policy are defined clearly. The privacy policy states the right of the
there is a way to reset the value to zero for the negative difference that comes between total
number of the SYNs and total number of FINs by eliminating cumulative effects. As a result
there is a spike on the background noise which degrades sensitive detection in one observation
period.
2.4 Introduction of Wireshark
(Zhang et al. 2016) introduced the wireshark is considered as a tool that is open source
which help in profiling the network traffic as well as analyzing all the packets. The wireshark is a
tool of network analyzer, a protocol analyzer of network or a sniffer. The wireshark is formerly
described as Ethereal (Liu, Lai and Zhang 2017). This is use for examining all the details of
traffic at different levels that ranges from the information of connection level to bits which are
responsible for making single packet. The packet capture helps in providing network
administrator all necessary information related to the individual packets including transmit time,
destination, header data, and protocol type and source data. The information are mainly used for
evaluating the security events and helps in troubleshooting the issues of network security device.
Shaik et al. (2015) said that wireshark mainly display the information usually in three
different panels. The top panels lists all the frames that works individually with the key data on a
single line. A particular single frame is then selected in the top pane which is explained further in
middle panel tool. In the display section, the Wireshark shows all the packet details which
explains the important aspects of frame that are considered as the belonging of data link layer,
application layer, transport layer, and network layer (Kaur et al. 2015). The bottom pane of the
Wireshark displays the raw frame with the hexadecimal rendition on left and their corresponding
ASCII values on right. The wireshark is mainly used for eavesdropping. It is an organizational
tool in which the privacy policy are defined clearly. The privacy policy states the right of the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22DISSERTATION
individuals which uses the network, gives permission to the sniff traffic for troubleshooting and
security issues (Bhuyan, Bhattacharyya and Kalita 2017). The privacy policy also states the
policy of the organization that helps in obtaining, retaining, as well as analyzing the traffic
samples.
3. Data Evaluation
3.1 Using of Wireshark
The Wireshark that is used for detecting the anomaly that comes from flooding attack.
The wireshark is basically a free application that is used in capturing or viewing all data that
travels to and fro in a network (Safoine, Mounir and Farchi 2018). The wireshark helps in
drilling down as well as reading all contents of the packets that comes to them and those packets
are filtered so that they can meet the specific needs. The wireshark is used in troubleshooting
network problems and also helps in developing as well as testing the software. The wireshark is
an analyzer that is open sourced which is accepted widely as industry standard, as winning the
fair share over years.
The wireshark was mainly famous as Ethereal and has a user friendly interface which
displays data from various protocols on all types of network. All data packets are mostly viewed
in real time or can be analyzed offline (Rehman and Manickam 2016). The wireshark supports
many captures of file formats that are supported by ERF and CAP. The tool of integrated
decryption mainly allows a user to view the encrypted packets for protocols that includes
WPA/WPA2 and the WEP protocols.
individuals which uses the network, gives permission to the sniff traffic for troubleshooting and
security issues (Bhuyan, Bhattacharyya and Kalita 2017). The privacy policy also states the
policy of the organization that helps in obtaining, retaining, as well as analyzing the traffic
samples.
3. Data Evaluation
3.1 Using of Wireshark
The Wireshark that is used for detecting the anomaly that comes from flooding attack.
The wireshark is basically a free application that is used in capturing or viewing all data that
travels to and fro in a network (Safoine, Mounir and Farchi 2018). The wireshark helps in
drilling down as well as reading all contents of the packets that comes to them and those packets
are filtered so that they can meet the specific needs. The wireshark is used in troubleshooting
network problems and also helps in developing as well as testing the software. The wireshark is
an analyzer that is open sourced which is accepted widely as industry standard, as winning the
fair share over years.
The wireshark was mainly famous as Ethereal and has a user friendly interface which
displays data from various protocols on all types of network. All data packets are mostly viewed
in real time or can be analyzed offline (Rehman and Manickam 2016). The wireshark supports
many captures of file formats that are supported by ERF and CAP. The tool of integrated
decryption mainly allows a user to view the encrypted packets for protocols that includes
WPA/WPA2 and the WEP protocols.

23DISSERTATION
3.1.1 Process to Download and Install Wireshark
The wireshark software can be downloaded without any cost from the official website of
Wireshark Foundation. This software is working for both the operating systems that is for
macOS and for Windows. To use the latest release of the software is always recommended to the
user. For setting up the process of Windows Operating, the user should install the WinPcap
which includes library that is required for capturing the data live (Cheong 2017). The application
or the software of Wireshark is available for Linux as well as other UNIX platform systems as
well. This includes Red Hat, FreeBSD, and Solaris.
3.1.2 Process to Capture Data Packets
When the Wireshark is launched first, there appears a welcome screen that contains list of
all the networks that are available for the network connections that are available on the current
device (AlEroud and Alsmadi 2017). There are many connection types such as Bluetooth
Network Connection, Wi-Fi, Virtual Box Network, and Ethernet. In the right, there is a EKG
style line graph which represents all live traffic that are on that particular network.
For start with the capturing packet, more than one network is selected by clicking a
particular choice of the user and with the help of the Ctrl and the Shift keys the user can record
the data from different networks one after another (Meidan et al. 2018). After selecting a
particular connection type to capture all the purposes, the background is then shaded with blue or
gray color. Then the Capture button is clicked in main menu that is located on the top of the
screen in the interface of Wireshark. When drop down option appears on the screen, then the user
needs to select Start button.
The user using the Wireshark can also process the capturing of packets through some
shortcuts. The shortcuts are described below.
3.1.1 Process to Download and Install Wireshark
The wireshark software can be downloaded without any cost from the official website of
Wireshark Foundation. This software is working for both the operating systems that is for
macOS and for Windows. To use the latest release of the software is always recommended to the
user. For setting up the process of Windows Operating, the user should install the WinPcap
which includes library that is required for capturing the data live (Cheong 2017). The application
or the software of Wireshark is available for Linux as well as other UNIX platform systems as
well. This includes Red Hat, FreeBSD, and Solaris.
3.1.2 Process to Capture Data Packets
When the Wireshark is launched first, there appears a welcome screen that contains list of
all the networks that are available for the network connections that are available on the current
device (AlEroud and Alsmadi 2017). There are many connection types such as Bluetooth
Network Connection, Wi-Fi, Virtual Box Network, and Ethernet. In the right, there is a EKG
style line graph which represents all live traffic that are on that particular network.
For start with the capturing packet, more than one network is selected by clicking a
particular choice of the user and with the help of the Ctrl and the Shift keys the user can record
the data from different networks one after another (Meidan et al. 2018). After selecting a
particular connection type to capture all the purposes, the background is then shaded with blue or
gray color. Then the Capture button is clicked in main menu that is located on the top of the
screen in the interface of Wireshark. When drop down option appears on the screen, then the user
needs to select Start button.
The user using the Wireshark can also process the capturing of packets through some
shortcuts. The shortcuts are described below.

24DISSERTATION
Mouse: For beginning to capture the packets from a single network, double click is to be
done on the name of the network.
Keyboard: With the keyboard, the user needs to press Ctrl + E.
Toolbar: Clicking on the button showing blue shark fin that is located on left side of
Wireshark toolbar.
After performing all the shortcuts in proper way, live capturing of the process begins. The
wireshark then displays all packets in details simultaneously as recorded (Bhattacharyya and
Kalita 2016). To stop the capturing process, the following process are to be carried out:
Keyboard: Press the Ctrl + E from keyboard.
Toolbar: To stop the capturing process, the red button beside the shark fin button on
Wireshark toolbar to be clicked.
3.1.3 To View and Analyze Packet Contents
After recording all the network data, the packets that are captured are to be looked. The
data interface that are captured during the capturing process, there are particularly three main
sections. The first section is the list of packet pane, the second section shows the details of
packet pane and the third section shows the bytes of the packet pane. All three sections are
described briefly in the following sections.
Packet List:
The pane consisting the packet list is located on top of screen or the window. The pane
show all the packets that are found active while capturing the file. Each of the packet has own
row as well as has a corresponding quantity that is assigned to the packet (Bhattacharyya and
Mouse: For beginning to capture the packets from a single network, double click is to be
done on the name of the network.
Keyboard: With the keyboard, the user needs to press Ctrl + E.
Toolbar: Clicking on the button showing blue shark fin that is located on left side of
Wireshark toolbar.
After performing all the shortcuts in proper way, live capturing of the process begins. The
wireshark then displays all packets in details simultaneously as recorded (Bhattacharyya and
Kalita 2016). To stop the capturing process, the following process are to be carried out:
Keyboard: Press the Ctrl + E from keyboard.
Toolbar: To stop the capturing process, the red button beside the shark fin button on
Wireshark toolbar to be clicked.
3.1.3 To View and Analyze Packet Contents
After recording all the network data, the packets that are captured are to be looked. The
data interface that are captured during the capturing process, there are particularly three main
sections. The first section is the list of packet pane, the second section shows the details of
packet pane and the third section shows the bytes of the packet pane. All three sections are
described briefly in the following sections.
Packet List:
The pane consisting the packet list is located on top of screen or the window. The pane
show all the packets that are found active while capturing the file. Each of the packet has own
row as well as has a corresponding quantity that is assigned to the packet (Bhattacharyya and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25DISSERTATION
Kalita 2016). These numbers are assigned with the packets along with the data points. The
packet list contains the following list that are described below:
Time: The total time taken by wireshark to capture the packet is basically displayed in
this particular column. The format that is set by default as the total number of seconds or
the partial seconds (Rehman and Manickam 2016). This is done because a particular file
capture was done previously. For modifying the file format to something else, that may
include the actual time. This can be selected in another option that is in the Time Display
Format in the time pane of the wireshark menu. This is located on the top of the interface
of the wireshark.
Source: The source column in the packet list pane mainly contains the IP address of the
packet from it has originated.
Destination: This particular column in the pane list mainly contains address to where the
packet is being sent. The destination address of the packet is shown in this destination
column.
Protocol: The protocol name of the packet which includes the TCP is mainly found in
protocol column.
Length: The total length of the packet is shown in length column. The length of the
packet is shown in bytes in pane list.
Info: All the extra details related to the packets are detailed in this info column. The
details of this particular column mainly differs depending on the contents of the packets.
When the packet is selected form top pane, there may be more than one symbol that will
appear in first column. The symbols such as open brackets or closed brackets or straight
horizontal line mainly indicates if the packet or the group of packets will be same part of the
Kalita 2016). These numbers are assigned with the packets along with the data points. The
packet list contains the following list that are described below:
Time: The total time taken by wireshark to capture the packet is basically displayed in
this particular column. The format that is set by default as the total number of seconds or
the partial seconds (Rehman and Manickam 2016). This is done because a particular file
capture was done previously. For modifying the file format to something else, that may
include the actual time. This can be selected in another option that is in the Time Display
Format in the time pane of the wireshark menu. This is located on the top of the interface
of the wireshark.
Source: The source column in the packet list pane mainly contains the IP address of the
packet from it has originated.
Destination: This particular column in the pane list mainly contains address to where the
packet is being sent. The destination address of the packet is shown in this destination
column.
Protocol: The protocol name of the packet which includes the TCP is mainly found in
protocol column.
Length: The total length of the packet is shown in length column. The length of the
packet is shown in bytes in pane list.
Info: All the extra details related to the packets are detailed in this info column. The
details of this particular column mainly differs depending on the contents of the packets.
When the packet is selected form top pane, there may be more than one symbol that will
appear in first column. The symbols such as open brackets or closed brackets or straight
horizontal line mainly indicates if the packet or the group of packets will be same part of the

26DISSERTATION
conversation that are to and fro on that particular network (Safoine, Mounir and Farchi 2018).
There is another system shown as broken horizontal line that signifies that the captured packet is
not the part of the conversation.
3.1.4 Color Rules of Wireshark
While capturing the packets in Wireshark and displaying the filters mainly allows the
user to make a limit where the packets are generally recorded as well as shown on window
screen. There are certain colorization functions in the wireshark that helps in analyzing the
packet of data further to the next process. The colorization helps to make a difference between
the packets received differentiating individual hue. This feature of colorization in Wireshark
helps in locating the packets quickly by setting a different color in the pane of packet list.
The application of Wireshark mainly comes with 20 default color rules that are in built in
the application itself. Each of the colors that are present in the color pane of Wireshark can be
edited, deleted or can be disabled if the user wishes to. The user is also able to add new shades of
color from the filter with all coloring rules that are present in the interface. The color options is
accessible to the user from View menu (Safoine, Mounir and Farchi 2018). Along with a name
and a filter with each of the rule, the user is also asked to give a background color along with a
text color or the packets. The colorization of the packets can also be turned off by the user or the
user can also turn off the option of Colorize Packet List that is available in the view menu list.
The following section shows the details of evaluating the packets using the wireshark
application. The attacks that were carried out for analyzing the packets were the Brute Force
flood attack, Ping flood attack, and the metasploit flood attack (Bhuyan, Bhattacharyya and
Kalita 2017). The first step that is carried out to find out all the ports that are open. Then the
conversation that are to and fro on that particular network (Safoine, Mounir and Farchi 2018).
There is another system shown as broken horizontal line that signifies that the captured packet is
not the part of the conversation.
3.1.4 Color Rules of Wireshark
While capturing the packets in Wireshark and displaying the filters mainly allows the
user to make a limit where the packets are generally recorded as well as shown on window
screen. There are certain colorization functions in the wireshark that helps in analyzing the
packet of data further to the next process. The colorization helps to make a difference between
the packets received differentiating individual hue. This feature of colorization in Wireshark
helps in locating the packets quickly by setting a different color in the pane of packet list.
The application of Wireshark mainly comes with 20 default color rules that are in built in
the application itself. Each of the colors that are present in the color pane of Wireshark can be
edited, deleted or can be disabled if the user wishes to. The user is also able to add new shades of
color from the filter with all coloring rules that are present in the interface. The color options is
accessible to the user from View menu (Safoine, Mounir and Farchi 2018). Along with a name
and a filter with each of the rule, the user is also asked to give a background color along with a
text color or the packets. The colorization of the packets can also be turned off by the user or the
user can also turn off the option of Colorize Packet List that is available in the view menu list.
The following section shows the details of evaluating the packets using the wireshark
application. The attacks that were carried out for analyzing the packets were the Brute Force
flood attack, Ping flood attack, and the metasploit flood attack (Bhuyan, Bhattacharyya and
Kalita 2017). The first step that is carried out to find out all the ports that are open. Then the

27DISSERTATION
three attacks that are mentioned above are performed simultaneously. Wireshark will be used for
processing the attacks that were performed for carrying out this study.
3.2 Simulation of the Network Attack and using Wireshark for its Detection
3.2.1 Command used for scanning the active host in the network:
root@kali:~# nmap -sP 192.168.90.0/24
Starting Nmap 7.50 ( https://nmap.org ) at 2018-11-13 17:10 AWST
Nmap scan report for 192.168.90.1
Host is up (0.00016s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.90.2
Host is up (0.00017s latency).
MAC Address: 00:50:56:F4:66:30 (VMware)
Nmap scan report for 192.168.90.131
Host is up (-0.10s latency).
MAC Address: 00:0C:29:58:0F:F4 (VMware)
Nmap scan report for 192.168.90.254
Host is up (-0.10s latency).
MAC Address: 00:50:56:EC:04:3E (VMware)
Nmap scan report for 192.168.90.128
three attacks that are mentioned above are performed simultaneously. Wireshark will be used for
processing the attacks that were performed for carrying out this study.
3.2 Simulation of the Network Attack and using Wireshark for its Detection
3.2.1 Command used for scanning the active host in the network:
root@kali:~# nmap -sP 192.168.90.0/24
Starting Nmap 7.50 ( https://nmap.org ) at 2018-11-13 17:10 AWST
Nmap scan report for 192.168.90.1
Host is up (0.00016s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.90.2
Host is up (0.00017s latency).
MAC Address: 00:50:56:F4:66:30 (VMware)
Nmap scan report for 192.168.90.131
Host is up (-0.10s latency).
MAC Address: 00:0C:29:58:0F:F4 (VMware)
Nmap scan report for 192.168.90.254
Host is up (-0.10s latency).
MAC Address: 00:50:56:EC:04:3E (VMware)
Nmap scan report for 192.168.90.128
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
28DISSERTATION
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 5.39 seconds
Figure 4: Command used for Scanning the Active Host in the Network
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 5.39 seconds
Figure 4: Command used for Scanning the Active Host in the Network
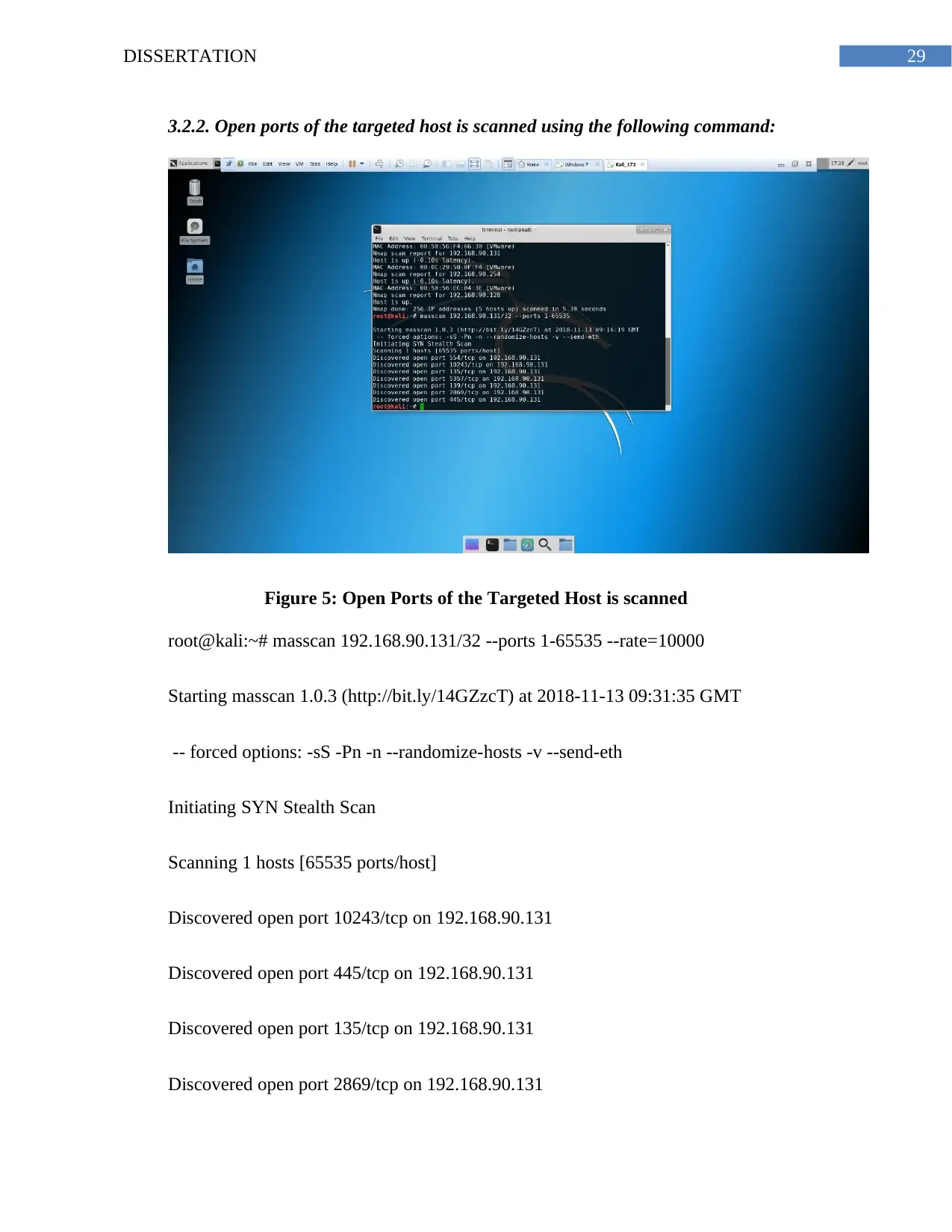
29DISSERTATION
3.2.2. Open ports of the targeted host is scanned using the following command:
Figure 5: Open Ports of the Targeted Host is scanned
root@kali:~# masscan 192.168.90.131/32 --ports 1-65535 --rate=10000
Starting masscan 1.0.3 (http://bit.ly/14GZzcT) at 2018-11-13 09:31:35 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 10243/tcp on 192.168.90.131
Discovered open port 445/tcp on 192.168.90.131
Discovered open port 135/tcp on 192.168.90.131
Discovered open port 2869/tcp on 192.168.90.131
3.2.2. Open ports of the targeted host is scanned using the following command:
Figure 5: Open Ports of the Targeted Host is scanned
root@kali:~# masscan 192.168.90.131/32 --ports 1-65535 --rate=10000
Starting masscan 1.0.3 (http://bit.ly/14GZzcT) at 2018-11-13 09:31:35 GMT
-- forced options: -sS -Pn -n --randomize-hosts -v --send-eth
Initiating SYN Stealth Scan
Scanning 1 hosts [65535 ports/host]
Discovered open port 10243/tcp on 192.168.90.131
Discovered open port 445/tcp on 192.168.90.131
Discovered open port 135/tcp on 192.168.90.131
Discovered open port 2869/tcp on 192.168.90.131

30DISSERTATION
Discovered open port 139/tcp on 192.168.90.131
Discovered open port 5357/tcp on 192.168.90.131
Discovered open port 554/tcp on 192.168.90.131
3.2.3. For finding the service running on the port the following command is used
root@kali:~# nmap -sV -p10243,445,135,2869,139,5357,554,21,20 192.168.90.131
Starting Nmap 7.50 ( https://nmap.org ) at 2018-11-13 18:18 AWST
Nmap scan report for 192.168.90.131
Host is up (-0.18s latency).
PORT STATE SERVICE VERSION
20/tcp filtered ftp-data
21/tcp filtered ftp
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
554/tcp filtered rtsp
2869/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
5357/tcp filtered wsdapi
10243/tcp filtered unknown
MAC Address: 00:0C:29:58:0F:F4 (VMware)
Discovered open port 139/tcp on 192.168.90.131
Discovered open port 5357/tcp on 192.168.90.131
Discovered open port 554/tcp on 192.168.90.131
3.2.3. For finding the service running on the port the following command is used
root@kali:~# nmap -sV -p10243,445,135,2869,139,5357,554,21,20 192.168.90.131
Starting Nmap 7.50 ( https://nmap.org ) at 2018-11-13 18:18 AWST
Nmap scan report for 192.168.90.131
Host is up (-0.18s latency).
PORT STATE SERVICE VERSION
20/tcp filtered ftp-data
21/tcp filtered ftp
135/tcp filtered msrpc
139/tcp filtered netbios-ssn
445/tcp filtered microsoft-ds
554/tcp filtered rtsp
2869/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
5357/tcp filtered wsdapi
10243/tcp filtered unknown
MAC Address: 00:0C:29:58:0F:F4 (VMware)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
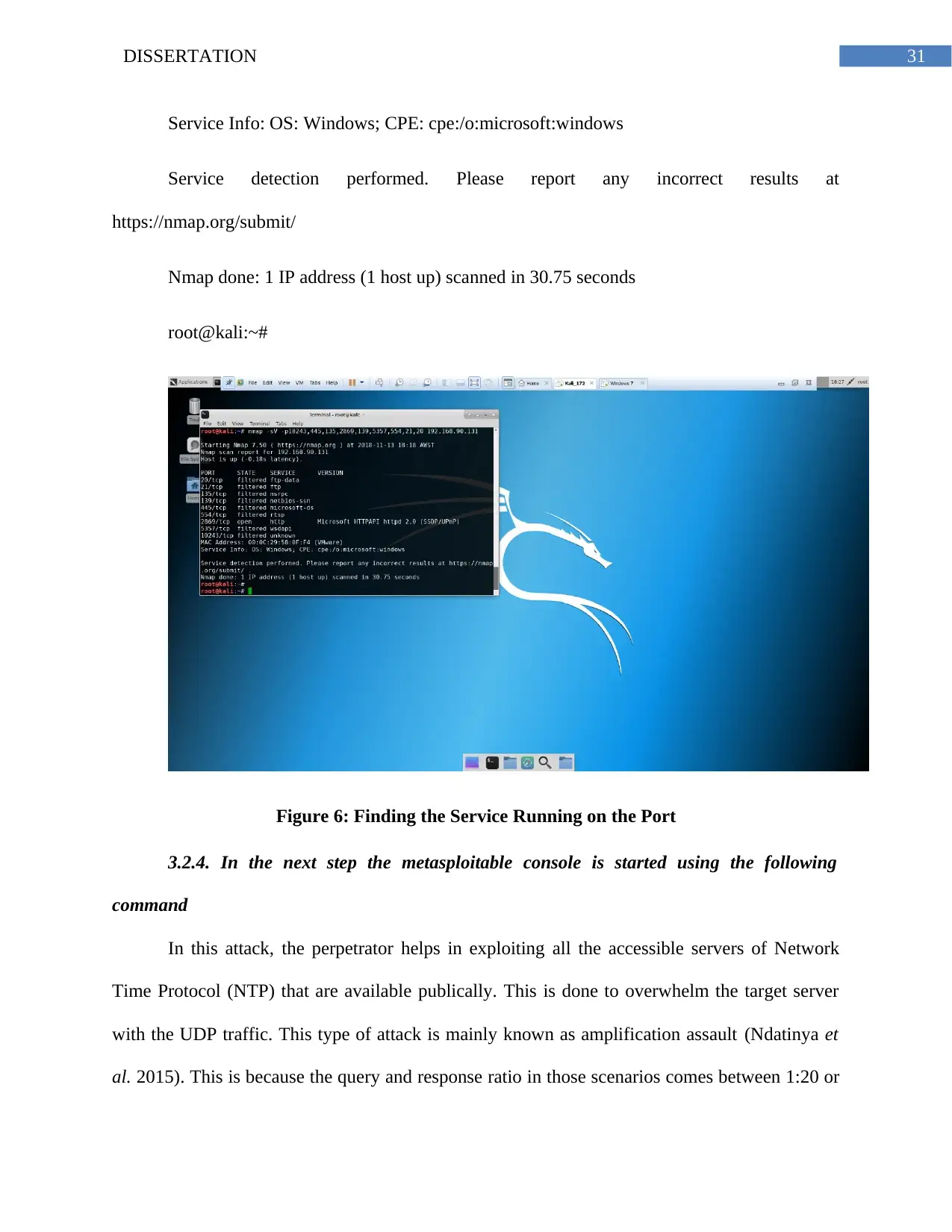
31DISSERTATION
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at
https://nmap.org/submit/
Nmap done: 1 IP address (1 host up) scanned in 30.75 seconds
root@kali:~#
Figure 6: Finding the Service Running on the Port
3.2.4. In the next step the metasploitable console is started using the following
command
In this attack, the perpetrator helps in exploiting all the accessible servers of Network
Time Protocol (NTP) that are available publically. This is done to overwhelm the target server
with the UDP traffic. This type of attack is mainly known as amplification assault (Ndatinya et
al. 2015). This is because the query and response ratio in those scenarios comes between 1:20 or
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at
https://nmap.org/submit/
Nmap done: 1 IP address (1 host up) scanned in 30.75 seconds
root@kali:~#
Figure 6: Finding the Service Running on the Port
3.2.4. In the next step the metasploitable console is started using the following
command
In this attack, the perpetrator helps in exploiting all the accessible servers of Network
Time Protocol (NTP) that are available publically. This is done to overwhelm the target server
with the UDP traffic. This type of attack is mainly known as amplification assault (Ndatinya et
al. 2015). This is because the query and response ratio in those scenarios comes between 1:20 or

32DISSERTATION
may be 1:200. This defines that any attacker who obtains list of the open NTP server can
generate a great bandwidth with high volume of the DDoS attack.
root@kali:~# msfconsole
.~+P``````-o+:. -o+:.
.+oooyysyyssyyssyddh++os-````` ``````````````` `
+++++++++++++++++++++++sydhyoyso/:.````...`...-///::+ohhyosyyosyy/+om++:ooo///o
++++///////~~~~///////++++++++++++++++ooyysoyysosso+++++++++++++++++++///
oossosy
--.` .-.-...-////+++++++++++++++////////~~//////++++++++++++///
`...............` `...-/////...`
.::::::::::-. .::::::-
.hmMMMMMMMMMMNddds\...//M\\.../hddddmMMMMMMNo
:Nm-/NMMMMMMMMMMMMM$
$NMMMMm&&MMMMMMMMMMMMMMy
.sm/`-yMMMMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMMMMh`
-Nd` :MMMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMMMh`
-Nh` .yMMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMMm/
may be 1:200. This defines that any attacker who obtains list of the open NTP server can
generate a great bandwidth with high volume of the DDoS attack.
root@kali:~# msfconsole
.~+P``````-o+:. -o+:.
.+oooyysyyssyyssyddh++os-````` ``````````````` `
+++++++++++++++++++++++sydhyoyso/:.````...`...-///::+ohhyosyyosyy/+om++:ooo///o
++++///////~~~~///////++++++++++++++++ooyysoyysosso+++++++++++++++++++///
oossosy
--.` .-.-...-////+++++++++++++++////////~~//////++++++++++++///
`...............` `...-/////...`
.::::::::::-. .::::::-
.hmMMMMMMMMMMNddds\...//M\\.../hddddmMMMMMMNo
:Nm-/NMMMMMMMMMMMMM$
$NMMMMm&&MMMMMMMMMMMMMMy
.sm/`-yMMMMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMMMMh`
-Nd` :MMMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMMMh`
-Nh` .yMMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMMm/

33DISSERTATION
`oo/``-hd: `` .sNd :MMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMm/
.yNmMMh//+syysso-`````` -mh` :MMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMd
.shMMMMN//dmNMMMMMMMMMMMMs` `:```-o++++oooo+:/ooooo+:+o++
+oooo++/
`///omh//dMMMMMMMMMMMMMMMN/:::::/+ooso--/ydh//+s+/ossssso:--syN///os:
/MMMMMMMMMMMMMMMMMMd. `/++-.-yy/...osydh/-+oo:-`o//...oyodh+
-hMMmssddd+:dMMmNMMh. `.-=mmk.//^^^\\.^^`:++:^^o://^^^\\`::
.sMMmo. -dMd--:mN/` ||--X--|| ||--X--||
........../yddy/:...+hmo-...hdd:............\\=v=//............\\=v=//.........
===============================================================
=================
=====================+--------------------------------
+=========================
=====================| Session one died of dysentery. |
=========================
=====================+--------------------------------
+=========================
`oo/``-hd: `` .sNd :MMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMm/
.yNmMMh//+syysso-`````` -mh` :MMMMMMMMMM$
$MMMMMN&&MMMMMMMMMMd
.shMMMMN//dmNMMMMMMMMMMMMs` `:```-o++++oooo+:/ooooo+:+o++
+oooo++/
`///omh//dMMMMMMMMMMMMMMMN/:::::/+ooso--/ydh//+s+/ossssso:--syN///os:
/MMMMMMMMMMMMMMMMMMd. `/++-.-yy/...osydh/-+oo:-`o//...oyodh+
-hMMmssddd+:dMMmNMMh. `.-=mmk.//^^^\\.^^`:++:^^o://^^^\\`::
.sMMmo. -dMd--:mN/` ||--X--|| ||--X--||
........../yddy/:...+hmo-...hdd:............\\=v=//............\\=v=//.........
===============================================================
=================
=====================+--------------------------------
+=========================
=====================| Session one died of dysentery. |
=========================
=====================+--------------------------------
+=========================
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

34DISSERTATION
===============================================================
=================
Press ENTER to size up the situation
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Date: April 25, 1848 %%%
%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%% Weather: It's always cool in the lab
%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Health: Overweight %%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%% Caffeine: 12975 mg %%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Hacked: All the things %%%%
%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
Press SPACE BAR to continue
=[ metasploit v4.14.28-dev ]
+ -- --=[ 1662 exploits - 951 auxiliary - 293 post ]
===============================================================
=================
Press ENTER to size up the situation
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%% Date: April 25, 1848 %%%
%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%% Weather: It's always cool in the lab
%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Health: Overweight %%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%% Caffeine: 12975 mg %%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%% Hacked: All the things %%%%
%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%%
Press SPACE BAR to continue
=[ metasploit v4.14.28-dev ]
+ -- --=[ 1662 exploits - 951 auxiliary - 293 post ]
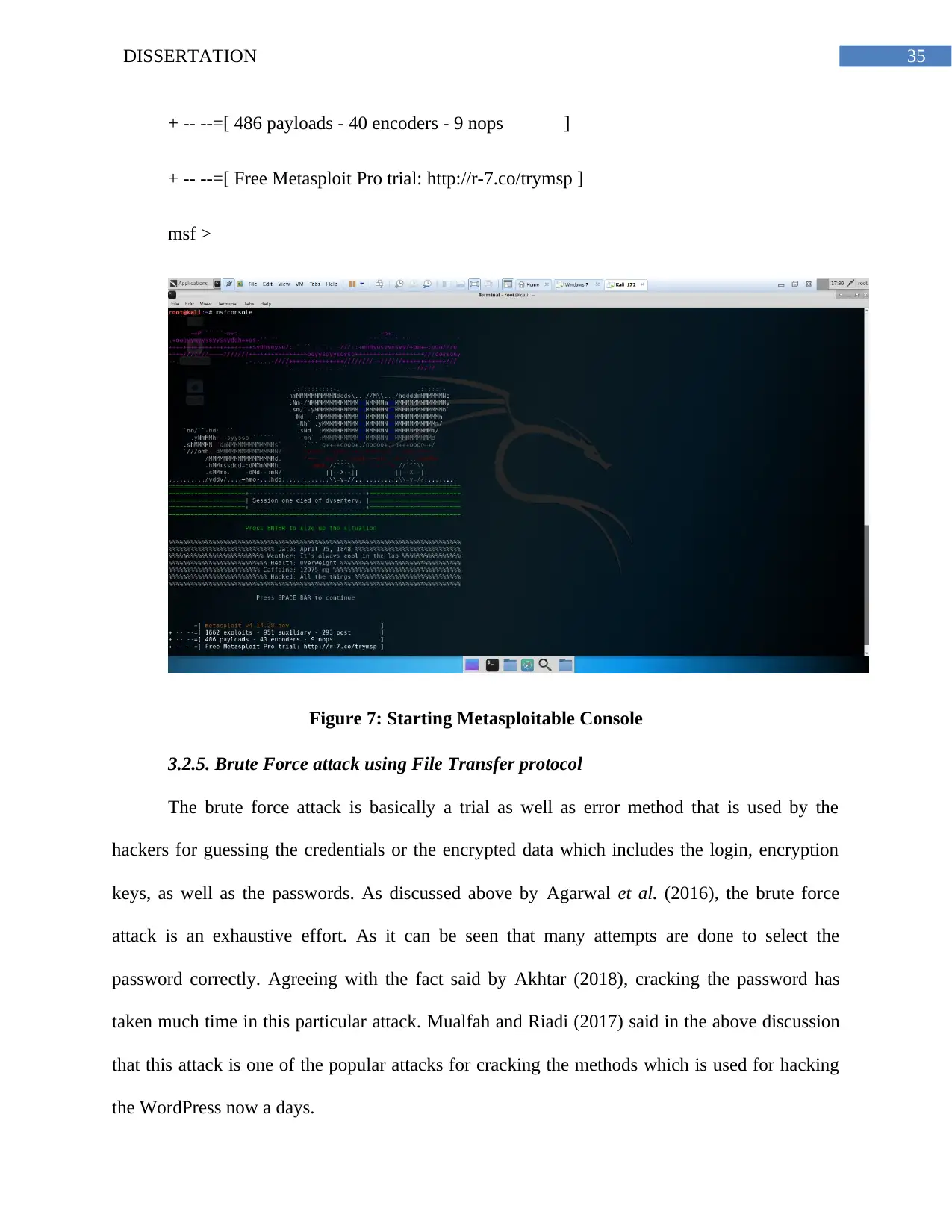
35DISSERTATION
+ -- --=[ 486 payloads - 40 encoders - 9 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf >
Figure 7: Starting Metasploitable Console
3.2.5. Brute Force attack using File Transfer protocol
The brute force attack is basically a trial as well as error method that is used by the
hackers for guessing the credentials or the encrypted data which includes the login, encryption
keys, as well as the passwords. As discussed above by Agarwal et al. (2016), the brute force
attack is an exhaustive effort. As it can be seen that many attempts are done to select the
password correctly. Agreeing with the fact said by Akhtar (2018), cracking the password has
taken much time in this particular attack. Mualfah and Riadi (2017) said in the above discussion
that this attack is one of the popular attacks for cracking the methods which is used for hacking
the WordPress now a days.
+ -- --=[ 486 payloads - 40 encoders - 9 nops ]
+ -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ]
msf >
Figure 7: Starting Metasploitable Console
3.2.5. Brute Force attack using File Transfer protocol
The brute force attack is basically a trial as well as error method that is used by the
hackers for guessing the credentials or the encrypted data which includes the login, encryption
keys, as well as the passwords. As discussed above by Agarwal et al. (2016), the brute force
attack is an exhaustive effort. As it can be seen that many attempts are done to select the
password correctly. Agreeing with the fact said by Akhtar (2018), cracking the password has
taken much time in this particular attack. Mualfah and Riadi (2017) said in the above discussion
that this attack is one of the popular attacks for cracking the methods which is used for hacking
the WordPress now a days.

36DISSERTATION
The most important advantage of the brute force attack is this attack is very simple to
perform and ample time can be taken to perform this attack. The systems that are password based
as well as has encryption key that are to be cracked by using the brute force attack. (Bachupally,
Yuan and Roy 2016) explained that the total amount of time that is used for brute forcing a
system is done in metric. The analyzed time to brute force the system is mentioned in seconds in
the evaluation that is carried out. This helps to gauge the security level of the system.
Agarwal et al. (2016) explained that the brute force attack is very slow which he stated
this as a disadvantage of brute force attack. As this attack is carried out by hit and trial attack, so
it takes time to get the combination of password for achieving the goal.
The process of attack is defined below:
root@kali:~# nmap -p 21 --script=ftp-brute 192.168.90.131
Starting Nmap 7.50 ( https://nmap.org ) at 2018-11-13 18:43 AWST
Nmap scan report for 192.168.90.131
Host is up (-0.20s latency).
PORT STATE SERVICE
21/tcp filtered ftp
MAC Address: 00:0C:29:58:0F:F4 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.62 seconds
root@kali:~#
The most important advantage of the brute force attack is this attack is very simple to
perform and ample time can be taken to perform this attack. The systems that are password based
as well as has encryption key that are to be cracked by using the brute force attack. (Bachupally,
Yuan and Roy 2016) explained that the total amount of time that is used for brute forcing a
system is done in metric. The analyzed time to brute force the system is mentioned in seconds in
the evaluation that is carried out. This helps to gauge the security level of the system.
Agarwal et al. (2016) explained that the brute force attack is very slow which he stated
this as a disadvantage of brute force attack. As this attack is carried out by hit and trial attack, so
it takes time to get the combination of password for achieving the goal.
The process of attack is defined below:
root@kali:~# nmap -p 21 --script=ftp-brute 192.168.90.131
Starting Nmap 7.50 ( https://nmap.org ) at 2018-11-13 18:43 AWST
Nmap scan report for 192.168.90.131
Host is up (-0.20s latency).
PORT STATE SERVICE
21/tcp filtered ftp
MAC Address: 00:0C:29:58:0F:F4 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.62 seconds
root@kali:~#
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
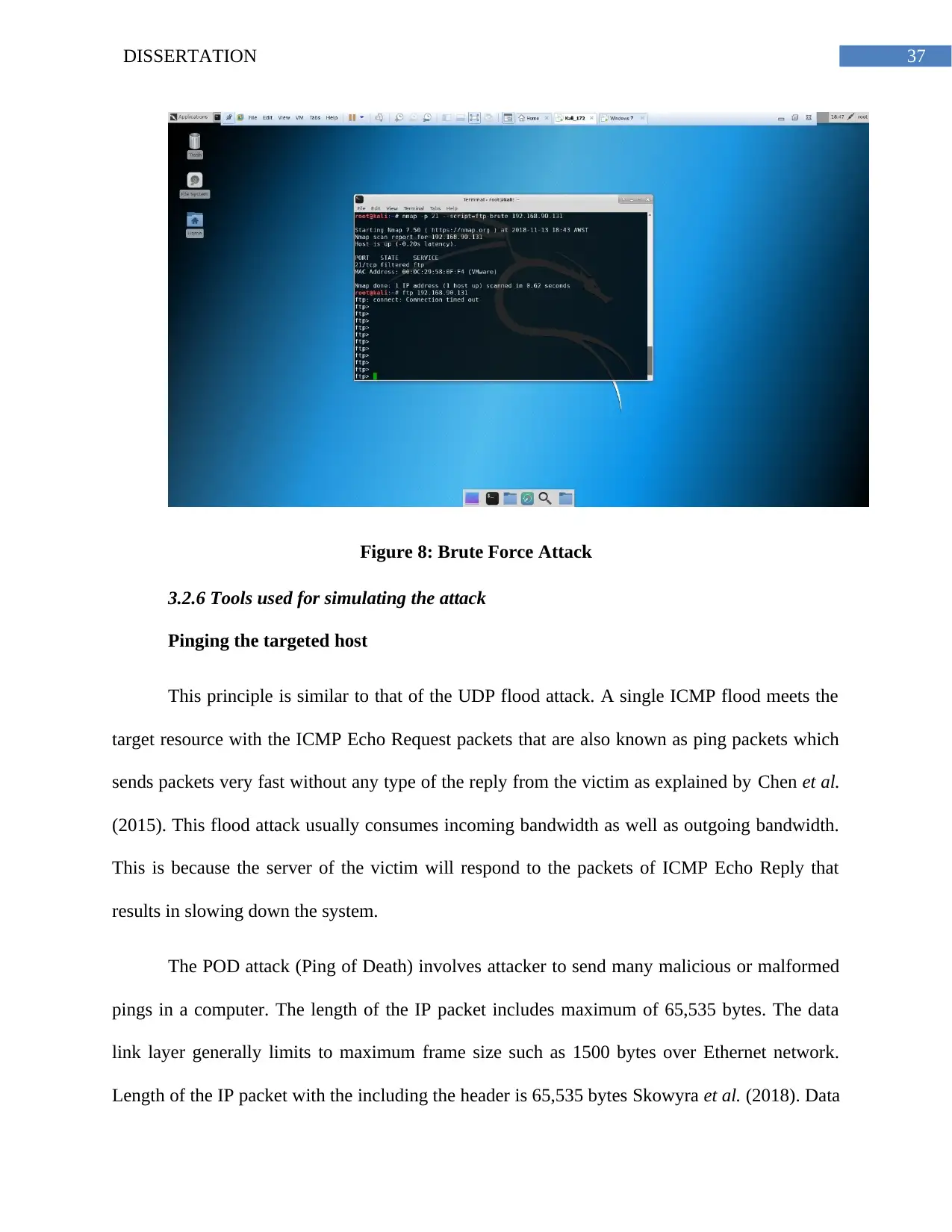
37DISSERTATION
Figure 8: Brute Force Attack
3.2.6 Tools used for simulating the attack
Pinging the targeted host
This principle is similar to that of the UDP flood attack. A single ICMP flood meets the
target resource with the ICMP Echo Request packets that are also known as ping packets which
sends packets very fast without any type of the reply from the victim as explained by Chen et al.
(2015). This flood attack usually consumes incoming bandwidth as well as outgoing bandwidth.
This is because the server of the victim will respond to the packets of ICMP Echo Reply that
results in slowing down the system.
The POD attack (Ping of Death) involves attacker to send many malicious or malformed
pings in a computer. The length of the IP packet includes maximum of 65,535 bytes. The data
link layer generally limits to maximum frame size such as 1500 bytes over Ethernet network.
Length of the IP packet with the including the header is 65,535 bytes Skowyra et al. (2018). Data
Figure 8: Brute Force Attack
3.2.6 Tools used for simulating the attack
Pinging the targeted host
This principle is similar to that of the UDP flood attack. A single ICMP flood meets the
target resource with the ICMP Echo Request packets that are also known as ping packets which
sends packets very fast without any type of the reply from the victim as explained by Chen et al.
(2015). This flood attack usually consumes incoming bandwidth as well as outgoing bandwidth.
This is because the server of the victim will respond to the packets of ICMP Echo Reply that
results in slowing down the system.
The POD attack (Ping of Death) involves attacker to send many malicious or malformed
pings in a computer. The length of the IP packet includes maximum of 65,535 bytes. The data
link layer generally limits to maximum frame size such as 1500 bytes over Ethernet network.
Length of the IP packet with the including the header is 65,535 bytes Skowyra et al. (2018). Data
38DISSERTATION
Link Layer mainly limits to the frame size. For instance, 1500 bytes for the Ethernet network. A
large IP packet is then distributed over many IP packets that are commonly known as fragments.
Recipient hosts also reassembles the fragments of IP in a complete packet. In this POD scenario,
malicious manipulation is done over the fragment content and also the recipient comes to an end
with the IP packet that is bigger than the 65,535 bytes when they are reassembled. This helps to
overflow the memory buffer that are allocated to the packet with the denial of service attack for
the legitimate packets.
Hping
hping3 --rand-source 192.168.90.131 --flood -S -L 0 -p 2869
Link Layer mainly limits to the frame size. For instance, 1500 bytes for the Ethernet network. A
large IP packet is then distributed over many IP packets that are commonly known as fragments.
Recipient hosts also reassembles the fragments of IP in a complete packet. In this POD scenario,
malicious manipulation is done over the fragment content and also the recipient comes to an end
with the IP packet that is bigger than the 65,535 bytes when they are reassembled. This helps to
overflow the memory buffer that are allocated to the packet with the denial of service attack for
the legitimate packets.
Hping
hping3 --rand-source 192.168.90.131 --flood -S -L 0 -p 2869
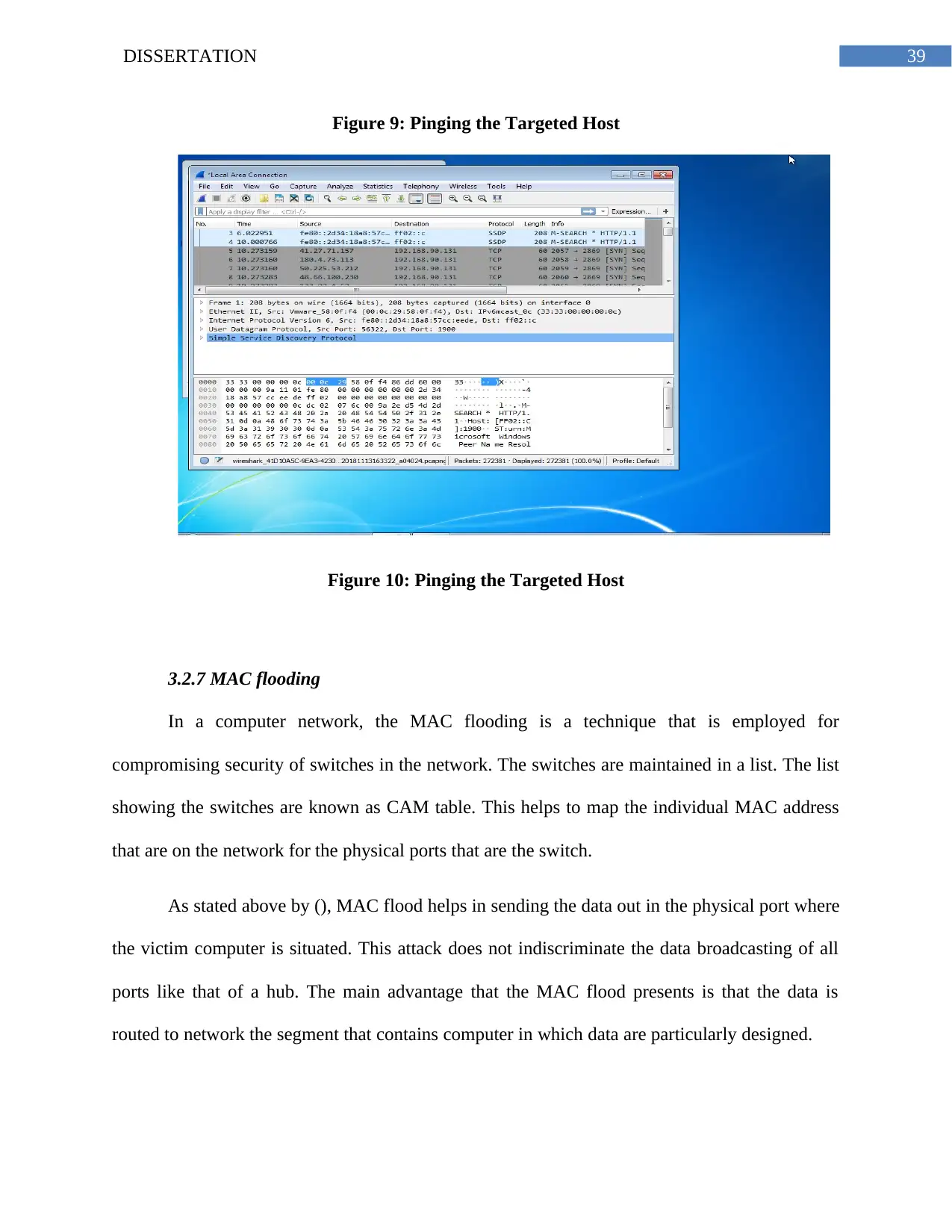
39DISSERTATION
Figure 9: Pinging the Targeted Host
Figure 10: Pinging the Targeted Host
3.2.7 MAC flooding
In a computer network, the MAC flooding is a technique that is employed for
compromising security of switches in the network. The switches are maintained in a list. The list
showing the switches are known as CAM table. This helps to map the individual MAC address
that are on the network for the physical ports that are the switch.
As stated above by (), MAC flood helps in sending the data out in the physical port where
the victim computer is situated. This attack does not indiscriminate the data broadcasting of all
ports like that of a hub. The main advantage that the MAC flood presents is that the data is
routed to network the segment that contains computer in which data are particularly designed.
Figure 9: Pinging the Targeted Host
Figure 10: Pinging the Targeted Host
3.2.7 MAC flooding
In a computer network, the MAC flooding is a technique that is employed for
compromising security of switches in the network. The switches are maintained in a list. The list
showing the switches are known as CAM table. This helps to map the individual MAC address
that are on the network for the physical ports that are the switch.
As stated above by (), MAC flood helps in sending the data out in the physical port where
the victim computer is situated. This attack does not indiscriminate the data broadcasting of all
ports like that of a hub. The main advantage that the MAC flood presents is that the data is
routed to network the segment that contains computer in which data are particularly designed.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

40DISSERTATION
In a MAC flooding attack, a particular switch is mainly flooded with packets of data that
contains different MAC addresses usually from different sources. This helps in consuming a
limited memory aside in which the switch stores all the addresses of MAC translated to physical
port. This table is known as transition table. The result that is obtained with the MAC flood is
shown below in figure 11. After performing this MAC flood attack, the switch enters a state
known as the failopen mode. In this mode, all the packets that are broadcasted out similar to a
hub. The broadcast are done on all ports rather than broadcasting the incoming packets on a
particular port.
In a MAC flood, malicious user can also use a packet sniffer by running promiscuous
mode for capturing the sensitive data that comes from all other computers. Sensitive data
includes e-mails, messaging conversations, or unencrypted passwords. These sensitive data will
not be working if they were only working on a switch normally.
In a MAC flooding attack, a particular switch is mainly flooded with packets of data that
contains different MAC addresses usually from different sources. This helps in consuming a
limited memory aside in which the switch stores all the addresses of MAC translated to physical
port. This table is known as transition table. The result that is obtained with the MAC flood is
shown below in figure 11. After performing this MAC flood attack, the switch enters a state
known as the failopen mode. In this mode, all the packets that are broadcasted out similar to a
hub. The broadcast are done on all ports rather than broadcasting the incoming packets on a
particular port.
In a MAC flood, malicious user can also use a packet sniffer by running promiscuous
mode for capturing the sensitive data that comes from all other computers. Sensitive data
includes e-mails, messaging conversations, or unencrypted passwords. These sensitive data will
not be working if they were only working on a switch normally.
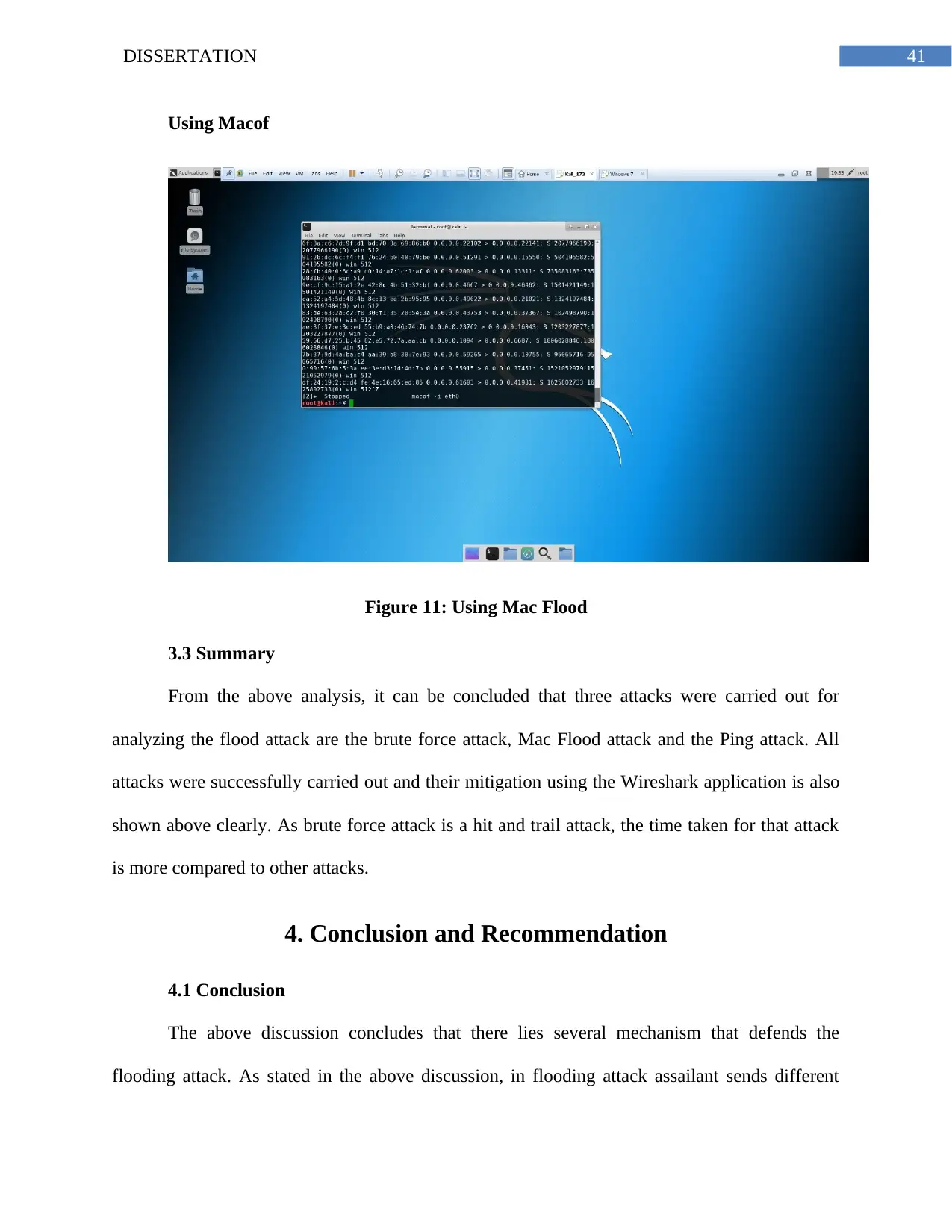
41DISSERTATION
Using Macof
Figure 11: Using Mac Flood
3.3 Summary
From the above analysis, it can be concluded that three attacks were carried out for
analyzing the flood attack are the brute force attack, Mac Flood attack and the Ping attack. All
attacks were successfully carried out and their mitigation using the Wireshark application is also
shown above clearly. As brute force attack is a hit and trail attack, the time taken for that attack
is more compared to other attacks.
4. Conclusion and Recommendation
4.1 Conclusion
The above discussion concludes that there lies several mechanism that defends the
flooding attack. As stated in the above discussion, in flooding attack assailant sends different
Using Macof
Figure 11: Using Mac Flood
3.3 Summary
From the above analysis, it can be concluded that three attacks were carried out for
analyzing the flood attack are the brute force attack, Mac Flood attack and the Ping attack. All
attacks were successfully carried out and their mitigation using the Wireshark application is also
shown above clearly. As brute force attack is a hit and trail attack, the time taken for that attack
is more compared to other attacks.
4. Conclusion and Recommendation
4.1 Conclusion
The above discussion concludes that there lies several mechanism that defends the
flooding attack. As stated in the above discussion, in flooding attack assailant sends different

42DISSERTATION
surges to the users or the administration so that they can cut down the framework of the network.
There are many flooding assaults such as UDP surges, ping surge as well as Syn surge. This
technique of attack is commonly known as assault technique. In this research, three such
flooding attacks were taken for carrying out the attack process. As it is known that TCP SYN
flood is commonly known as DDoS attack (Distributed Denial of Service) which exploits the
normal part of three way handshake of TCP that consumes all resources of target server as well
as render its unresponsive. With the flooding attacks, the mechanism of three way handshake of
TCP gets exploits and there are limitations to maintain the connections that are half opened. All
the three attacks including the Brute Force attack, Mac Flood attack as well as Ping attack
(ICMP attack) are detected using the wireshark application. From the above study, it can be
analyzed that the TCP SYN flood is commonly known as DDoS attack (Distributed Denial of
Service) which exploits the normal part of three way handshake of TCP that consumes all
resources of target server as well as render its unresponsive. With the flooding attacks, the
mechanism of three way handshake of TCP gets exploits and there are limitations to maintain the
connections that are half opened. When a particular server receives or gets a SYN request, then
the server returns a packet of SYN/ACK (Known as SYN acknowledgement) back to client.
Detailed study of wireshark is also described in this research paper. As stated above in
this research paper, wireshark is a tool that is used to refer a network analyzer, protocol analyzer
of network or sniffer. This is used for examining all the details of traffic at different levels that
ranges from the information of connection level to bits which are responsible for making single
packet. The packet capture helps in providing network administrator all necessary information
related to the individual packets including transmit time, destination, header data, and protocol
type and source data. The using process of wireshark is also explained in the research paper
surges to the users or the administration so that they can cut down the framework of the network.
There are many flooding assaults such as UDP surges, ping surge as well as Syn surge. This
technique of attack is commonly known as assault technique. In this research, three such
flooding attacks were taken for carrying out the attack process. As it is known that TCP SYN
flood is commonly known as DDoS attack (Distributed Denial of Service) which exploits the
normal part of three way handshake of TCP that consumes all resources of target server as well
as render its unresponsive. With the flooding attacks, the mechanism of three way handshake of
TCP gets exploits and there are limitations to maintain the connections that are half opened. All
the three attacks including the Brute Force attack, Mac Flood attack as well as Ping attack
(ICMP attack) are detected using the wireshark application. From the above study, it can be
analyzed that the TCP SYN flood is commonly known as DDoS attack (Distributed Denial of
Service) which exploits the normal part of three way handshake of TCP that consumes all
resources of target server as well as render its unresponsive. With the flooding attacks, the
mechanism of three way handshake of TCP gets exploits and there are limitations to maintain the
connections that are half opened. When a particular server receives or gets a SYN request, then
the server returns a packet of SYN/ACK (Known as SYN acknowledgement) back to client.
Detailed study of wireshark is also described in this research paper. As stated above in
this research paper, wireshark is a tool that is used to refer a network analyzer, protocol analyzer
of network or sniffer. This is used for examining all the details of traffic at different levels that
ranges from the information of connection level to bits which are responsible for making single
packet. The packet capture helps in providing network administrator all necessary information
related to the individual packets including transmit time, destination, header data, and protocol
type and source data. The using process of wireshark is also explained in the research paper
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

43DISSERTATION
which details about how to use the wireshark, the process that is to be carried out for
downloading the wireshark and the process of installing the wireshark. A detailed discussion is
also provided about the process to capture the data packets and the way to view as well as
analyze the packet contents are also described in this research paper. The wireshark works with
some color rules which are stated in the research paper describing the details about how to
choose color while detecting the packets of data.
Proper evaluation of the packets using the wireshark application. The attacks that were
carried out for analyzing the packets were the Brute Force flood attack, Ping flood attack, and the
metasploit flood attack. The first step that is carried out to find out all the ports that are open.
Then the three attacks that are mentioned above are performed simultaneously. At last Wireshark
will be used for detecting the attacks that were performed for analyzing the attacks.
4.2 Linking with the Objective
The objectives that were stated in the beginning while carrying out the research study is
to find out the types of flooding attack that are possible for online attack. All the attacks that
were possible for the online attacks are stated clearly in literature review section of this research
paper. The second objective was to investigate all the issues that are related with the flooding
attacks. All such issues are clearly described that are used in the flooding attack. Detection
method of flooding attacks are also described clearly in this research paper to address the
objective that were stated in the beginning of the research study. Details of wireshark application
are also stated in this paper which states the involvement of wireshark while carrying out
flooding attack. The characteristics of wireshark application are also described briefly in this
research paper addressing the objective of the research paper.
which details about how to use the wireshark, the process that is to be carried out for
downloading the wireshark and the process of installing the wireshark. A detailed discussion is
also provided about the process to capture the data packets and the way to view as well as
analyze the packet contents are also described in this research paper. The wireshark works with
some color rules which are stated in the research paper describing the details about how to
choose color while detecting the packets of data.
Proper evaluation of the packets using the wireshark application. The attacks that were
carried out for analyzing the packets were the Brute Force flood attack, Ping flood attack, and the
metasploit flood attack. The first step that is carried out to find out all the ports that are open.
Then the three attacks that are mentioned above are performed simultaneously. At last Wireshark
will be used for detecting the attacks that were performed for analyzing the attacks.
4.2 Linking with the Objective
The objectives that were stated in the beginning while carrying out the research study is
to find out the types of flooding attack that are possible for online attack. All the attacks that
were possible for the online attacks are stated clearly in literature review section of this research
paper. The second objective was to investigate all the issues that are related with the flooding
attacks. All such issues are clearly described that are used in the flooding attack. Detection
method of flooding attacks are also described clearly in this research paper to address the
objective that were stated in the beginning of the research study. Details of wireshark application
are also stated in this paper which states the involvement of wireshark while carrying out
flooding attack. The characteristics of wireshark application are also described briefly in this
research paper addressing the objective of the research paper.

44DISSERTATION
4.3 Recommendations
Some of the recommendation that can be provided for the preventing the flooding attacks
are stated below:
For preventing Brute Force attacks the recommendations that can be provided are:
To implement lockout policy of an account. For example, when there are three attempts
of login, the account gets locked. This is a disadvantage of this attack as many of the
accounts can get locked when it attacker fails. This cause denial of services for victims.
The second method that is recommended is the progressive delays. With this delay, the
account of the user remains locked out for some time after some failed login attempts.
The time for the lock out tends to increase gradually with more number of failed
attempts. This helps in preventing the automated tools to perform the brute force attack
on a network.
The third recommended technique is using challenge response test. This helps in
preventing automated submission of login pages. Tools which includes reCAPTCHA can
be used to provide a better security.
The users are also recommended to use strong passwords for an account so that the
malicious users cannot attack their accounts.
For preventing Mac Flood attacks the recommendations that can be provided are:
First recommendation that is given to the users is to secure the port. All the ports must be
closed with proper firewall implementation. The port security is often measured as a
counter measure of the flooding attack. There should be switches that are to be
4.3 Recommendations
Some of the recommendation that can be provided for the preventing the flooding attacks
are stated below:
For preventing Brute Force attacks the recommendations that can be provided are:
To implement lockout policy of an account. For example, when there are three attempts
of login, the account gets locked. This is a disadvantage of this attack as many of the
accounts can get locked when it attacker fails. This cause denial of services for victims.
The second method that is recommended is the progressive delays. With this delay, the
account of the user remains locked out for some time after some failed login attempts.
The time for the lock out tends to increase gradually with more number of failed
attempts. This helps in preventing the automated tools to perform the brute force attack
on a network.
The third recommended technique is using challenge response test. This helps in
preventing automated submission of login pages. Tools which includes reCAPTCHA can
be used to provide a better security.
The users are also recommended to use strong passwords for an account so that the
malicious users cannot attack their accounts.
For preventing Mac Flood attacks the recommendations that can be provided are:
First recommendation that is given to the users is to secure the port. All the ports must be
closed with proper firewall implementation. The port security is often measured as a
counter measure of the flooding attack. There should be switches that are to be

45DISSERTATION
configured for limiting the total number of MAC addresses that are connected with end
stations.
There should be authentication using the AAA server. The MAC address that is
discovered are to be authenticated against the authentication.
Take proper security measures for preventing the ARP Spoofing or the IP Spoofing. The
security measures for preventing should perform the additional MAC addresses for
filtering the unicast packets.
Implementing IEEE 802.1X that allows the rules of packet filtering that are needed to be
explicitly installed by the AAA server that are based on the information of the clients,
which includes the MAC address.
For preventing Ping attacks the recommendations that can be provided are:
To disable the ping attacks, the ICMP functionality on the targeted router is main
disabled on the computer device. Network administrator can mainly access administrative
interface of device and thus disable the ability for sending as well as receiving the requests using
the ICMP. This helps is eliminating the processing of request as well as echo reply effectively
form the network. All the consequences of this attack is that all network activities that are
involved in the ICMP are to be disabled which makes device unresponsive to ping the requests,
trace route the requests involved and also trace routes all other network activities.
configured for limiting the total number of MAC addresses that are connected with end
stations.
There should be authentication using the AAA server. The MAC address that is
discovered are to be authenticated against the authentication.
Take proper security measures for preventing the ARP Spoofing or the IP Spoofing. The
security measures for preventing should perform the additional MAC addresses for
filtering the unicast packets.
Implementing IEEE 802.1X that allows the rules of packet filtering that are needed to be
explicitly installed by the AAA server that are based on the information of the clients,
which includes the MAC address.
For preventing Ping attacks the recommendations that can be provided are:
To disable the ping attacks, the ICMP functionality on the targeted router is main
disabled on the computer device. Network administrator can mainly access administrative
interface of device and thus disable the ability for sending as well as receiving the requests using
the ICMP. This helps is eliminating the processing of request as well as echo reply effectively
form the network. All the consequences of this attack is that all network activities that are
involved in the ICMP are to be disabled which makes device unresponsive to ping the requests,
trace route the requests involved and also trace routes all other network activities.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

46DISSERTATION
References
Aborujilah, A. and Musa, S., 2017. Cloud-Based DDoS HTTP Attack Detection Using
Covariance Matrix Approach. Journal of Computer Networks and Communications, 2017.
Agarwal, M., Pasumarthi, D., Biswas, S. and Nandi, S., 2016. Machine learning approach for
detection of flooding DoS attacks in 802.11 networks and attacker localization. International
Journal of Machine Learning and Cybernetics, 7(6), pp.1035-1051.
Akhtar, F., 2018. Distributed denial of service attack detection using flow based detection
techniques. MCS.
Alam, M.M., Arafat, M.Y. and Ahmed, F., 2015. Study on auto detecting defence mechanisms
against application layer Ddos attacks in SIP server. Journal of Networks, 10(6), p.344.
AlEroud, A. and Alsmadi, I., 2017. Identifying cyber-attacks on software defined networks: An
inference-based intrusion detection approach. Journal of Network and Computer
Applications, 80, pp.152-164.
Alsadhan, A.A., Hussain, A., Baker, T. and Alfandi, O., 2018, August. Detecting Distributed
Denial of Service Attacks in Neighbour Discovery Protocol Using Machine Learning Algorithm
Based on Streams Representation. In International Conference on Intelligent Computing (pp.
551-563). Springer, Cham.
Anbar, M., Abdullah, R., Al-Tamimi, B.N. and Hussain, A., 2018. A Machine Learning
Approach to Detect Router Advertisement Flooding Attacks in Next-Generation IPv6
Networks. Cognitive Computation, 10(2), pp.201-214.
References
Aborujilah, A. and Musa, S., 2017. Cloud-Based DDoS HTTP Attack Detection Using
Covariance Matrix Approach. Journal of Computer Networks and Communications, 2017.
Agarwal, M., Pasumarthi, D., Biswas, S. and Nandi, S., 2016. Machine learning approach for
detection of flooding DoS attacks in 802.11 networks and attacker localization. International
Journal of Machine Learning and Cybernetics, 7(6), pp.1035-1051.
Akhtar, F., 2018. Distributed denial of service attack detection using flow based detection
techniques. MCS.
Alam, M.M., Arafat, M.Y. and Ahmed, F., 2015. Study on auto detecting defence mechanisms
against application layer Ddos attacks in SIP server. Journal of Networks, 10(6), p.344.
AlEroud, A. and Alsmadi, I., 2017. Identifying cyber-attacks on software defined networks: An
inference-based intrusion detection approach. Journal of Network and Computer
Applications, 80, pp.152-164.
Alsadhan, A.A., Hussain, A., Baker, T. and Alfandi, O., 2018, August. Detecting Distributed
Denial of Service Attacks in Neighbour Discovery Protocol Using Machine Learning Algorithm
Based on Streams Representation. In International Conference on Intelligent Computing (pp.
551-563). Springer, Cham.
Anbar, M., Abdullah, R., Al-Tamimi, B.N. and Hussain, A., 2018. A Machine Learning
Approach to Detect Router Advertisement Flooding Attacks in Next-Generation IPv6
Networks. Cognitive Computation, 10(2), pp.201-214.

47DISSERTATION
Aung, M.A.C. and Thant, K.P., 2017, February. Proposed Framework for Link Layer Attack
Detection System in Wireless Network. In 15th International Conference on Computer
Applications (ICCA), Yangon, Myanmar, 16th-17th February(pp. 169-175).
Bachupally, Y.R., Yuan, X. and Roy, K., 2016, March. Network security analysis using Big Data
technology. In SoutheastCon, 2016 (pp. 1-4). IEEE.
Bandara, K.R.W.V., Abeysinghe, T.S., Hijaz, A.J.M., Darshana, D.G.T., Aneez, H.,
Kaluarachchi, S.J., Sulochana, K.V.D.L. and DhishanDhammearatchi, M., 2016. Preventing
DDoS Attack Using Data Mining Algorithms. International Journal of Scientific and Research
Publications, 6(10), p.390.
Bhattacharyya, D.K. and Kalita, J.K., 2016. Ddos attacks: Evolution, detection, prevention,
reaction, and tolerance. Chapman and Hall/CRC.
Bhuyan, M.H., Bhattacharyya, D.K. and Kalita, J.K., 2017. Practical Tools for Attackers and
Defenders. In Network Traffic Anomaly Detection and Prevention (pp. 201-242). Springer,
Cham.
Bijalwan, A., Wazid, M., Pilli, E.S. and Joshi, R.C., 2015. forensics of random-UDP flooding
attacks. Journal of Networks, 10(5), p.287.
Chen, B., Pattanaik, N., Goulart, A., Butler-Purry, K.L. and Kundur, D., 2015, May.
Implementing attacks for modbus/TCP protocol in a real-time cyber physical system test bed.
In Communications Quality and Reliability (CQR), 2015 IEEE International Workshop
Technical Committee on (pp. 1-6). IEEE.
Aung, M.A.C. and Thant, K.P., 2017, February. Proposed Framework for Link Layer Attack
Detection System in Wireless Network. In 15th International Conference on Computer
Applications (ICCA), Yangon, Myanmar, 16th-17th February(pp. 169-175).
Bachupally, Y.R., Yuan, X. and Roy, K., 2016, March. Network security analysis using Big Data
technology. In SoutheastCon, 2016 (pp. 1-4). IEEE.
Bandara, K.R.W.V., Abeysinghe, T.S., Hijaz, A.J.M., Darshana, D.G.T., Aneez, H.,
Kaluarachchi, S.J., Sulochana, K.V.D.L. and DhishanDhammearatchi, M., 2016. Preventing
DDoS Attack Using Data Mining Algorithms. International Journal of Scientific and Research
Publications, 6(10), p.390.
Bhattacharyya, D.K. and Kalita, J.K., 2016. Ddos attacks: Evolution, detection, prevention,
reaction, and tolerance. Chapman and Hall/CRC.
Bhuyan, M.H., Bhattacharyya, D.K. and Kalita, J.K., 2017. Practical Tools for Attackers and
Defenders. In Network Traffic Anomaly Detection and Prevention (pp. 201-242). Springer,
Cham.
Bijalwan, A., Wazid, M., Pilli, E.S. and Joshi, R.C., 2015. forensics of random-UDP flooding
attacks. Journal of Networks, 10(5), p.287.
Chen, B., Pattanaik, N., Goulart, A., Butler-Purry, K.L. and Kundur, D., 2015, May.
Implementing attacks for modbus/TCP protocol in a real-time cyber physical system test bed.
In Communications Quality and Reliability (CQR), 2015 IEEE International Workshop
Technical Committee on (pp. 1-6). IEEE.

48DISSERTATION
Cheong, P.Z.Q., 2017. Proof of Concept: Network Vulnerability through Wi-Fi
Spoofing (Doctoral dissertation, UTAR).
Choi, J., Choi, C., Ko, B. and Kim, P., 2014. A method of DDoS attack detection using HTTP
packet pattern and rule engine in cloud computing environment. Soft Computing, 18(9), pp.1697-
1703.
Fleming, T. and Wilander, H., 2018. Network Intrusion and Detection: An evaluation of
SNORT.
Gupta, B.B. and Badve, O.P., 2017. Taxonomy of DoS and DDoS attacks and desirable defense
mechanism in a cloud computing environment. Neural Computing and Applications, 28(12),
pp.3655-3682.
Hoque, N., Bhuyan, M.H., Baishya, R.C., Bhattacharyya, D.K. and Kalita, J.K., 2014. Network
attacks: Taxonomy, tools and systems. Journal of Network and Computer Applications, 40,
pp.307-324.
Hussain, K., Hussain, S.J., Dillshad, V., Nafees, M. and Azeem, M.A., 2016. An Adaptive SYN
Flooding attack Mitigation in DDOS Environment. International Journal of Computer Science
and Network Security (IJCSNS), 16(7), p.27.
Karami, A. and Guerrero-Zapata, M., 2015. A fuzzy anomaly detection system based on hybrid
PSO-Kmeans algorithm in content-centric networks. Neurocomputing, 149, pp.1253-1269.
Kaur, J., 2018. Wired LAN and Wireless LAN Attack Detection Using Signature Based and
Machine Learning Tools. In Networking Communication and Data Knowledge Engineering(pp.
15-24). Springer, Singapore.
Cheong, P.Z.Q., 2017. Proof of Concept: Network Vulnerability through Wi-Fi
Spoofing (Doctoral dissertation, UTAR).
Choi, J., Choi, C., Ko, B. and Kim, P., 2014. A method of DDoS attack detection using HTTP
packet pattern and rule engine in cloud computing environment. Soft Computing, 18(9), pp.1697-
1703.
Fleming, T. and Wilander, H., 2018. Network Intrusion and Detection: An evaluation of
SNORT.
Gupta, B.B. and Badve, O.P., 2017. Taxonomy of DoS and DDoS attacks and desirable defense
mechanism in a cloud computing environment. Neural Computing and Applications, 28(12),
pp.3655-3682.
Hoque, N., Bhuyan, M.H., Baishya, R.C., Bhattacharyya, D.K. and Kalita, J.K., 2014. Network
attacks: Taxonomy, tools and systems. Journal of Network and Computer Applications, 40,
pp.307-324.
Hussain, K., Hussain, S.J., Dillshad, V., Nafees, M. and Azeem, M.A., 2016. An Adaptive SYN
Flooding attack Mitigation in DDOS Environment. International Journal of Computer Science
and Network Security (IJCSNS), 16(7), p.27.
Karami, A. and Guerrero-Zapata, M., 2015. A fuzzy anomaly detection system based on hybrid
PSO-Kmeans algorithm in content-centric networks. Neurocomputing, 149, pp.1253-1269.
Kaur, J., 2018. Wired LAN and Wireless LAN Attack Detection Using Signature Based and
Machine Learning Tools. In Networking Communication and Data Knowledge Engineering(pp.
15-24). Springer, Singapore.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

49DISSERTATION
Kaur, J., Tonejc, J., Wendzel, S. and Meier, M., 2015, May. Securing BACnet’s pitfalls. In IFIP
International Information Security Conference (pp. 616-629). Springer, Cham.
Khandelwal, M., Gupta, D.K. and Bhale, P., 2016, September. DoS attack detection technique
using back propagation neural network. In Advances in Computing, Communications and
Informatics (ICACCI), 2016 International Conference on (pp. 1064-1068). IEEE.
Kolias, C., Kambourakis, G., Stavrou, A. and Gritzalis, S., 2016. Intrusion detection in 802.11
networks: empirical evaluation of threats and a public dataset. IEEE Communications Surveys &
Tutorials, 18(1), pp.184-208.
Kshirsagar, D., Sawant, S., Rathod, A. and Wathore, S., 2016. CPU load analysis &
minimization for TCP SYN flood detection. Procedia Computer Science, 85, pp.626-633.
Kwon, Y., Kim, H.K., Lim, Y.H. and Lim, J.I., 2015, June. A behavior-based intrusion detection
technique for smart grid infrastructure. In PowerTech, 2015 IEEE Eindhoven (pp. 1-6). IEEE.
Liu, J., Lai, Y. and Zhang, S., 2017, March. FL-GUARD: A Detection and Defense System for
DDoS Attack in SDN. In Proceedings of the 2017 International Conference on Cryptography,
Security and Privacy (pp. 107-111). ACM.
Meidan, Y., Bohadana, M., Mathov, Y., Mirsky, Y., Shabtai, A., Breitenbacher, D. and Elovici,
Y., 2018. N-BaIoT—Network-Based Detection of IoT Botnet Attacks Using Deep
Autoencoders. IEEE Pervasive Computing, 17(3), pp.12-22.
Modi, K. and Quadir, A., 2014. Detection and Prevention of DDoS Attacks on the Cloud using
Double-Tcp Mechanism and HMM-based Architecture. International Journal of Cloud
Computing and Services Science, 3(2), p.113.
Kaur, J., Tonejc, J., Wendzel, S. and Meier, M., 2015, May. Securing BACnet’s pitfalls. In IFIP
International Information Security Conference (pp. 616-629). Springer, Cham.
Khandelwal, M., Gupta, D.K. and Bhale, P., 2016, September. DoS attack detection technique
using back propagation neural network. In Advances in Computing, Communications and
Informatics (ICACCI), 2016 International Conference on (pp. 1064-1068). IEEE.
Kolias, C., Kambourakis, G., Stavrou, A. and Gritzalis, S., 2016. Intrusion detection in 802.11
networks: empirical evaluation of threats and a public dataset. IEEE Communications Surveys &
Tutorials, 18(1), pp.184-208.
Kshirsagar, D., Sawant, S., Rathod, A. and Wathore, S., 2016. CPU load analysis &
minimization for TCP SYN flood detection. Procedia Computer Science, 85, pp.626-633.
Kwon, Y., Kim, H.K., Lim, Y.H. and Lim, J.I., 2015, June. A behavior-based intrusion detection
technique for smart grid infrastructure. In PowerTech, 2015 IEEE Eindhoven (pp. 1-6). IEEE.
Liu, J., Lai, Y. and Zhang, S., 2017, March. FL-GUARD: A Detection and Defense System for
DDoS Attack in SDN. In Proceedings of the 2017 International Conference on Cryptography,
Security and Privacy (pp. 107-111). ACM.
Meidan, Y., Bohadana, M., Mathov, Y., Mirsky, Y., Shabtai, A., Breitenbacher, D. and Elovici,
Y., 2018. N-BaIoT—Network-Based Detection of IoT Botnet Attacks Using Deep
Autoencoders. IEEE Pervasive Computing, 17(3), pp.12-22.
Modi, K. and Quadir, A., 2014. Detection and Prevention of DDoS Attacks on the Cloud using
Double-Tcp Mechanism and HMM-based Architecture. International Journal of Cloud
Computing and Services Science, 3(2), p.113.

50DISSERTATION
Mualfah, D. and Riadi, I., 2017. Network Forensics For Detecting Flooding Attack On Web
Server. International Journal of Computer Science and Information Security, 15(2), p.326.
Ndatinya, V., Xiao, Z., Manepalli, V.R., Meng, K. and Xiao, Y., 2015. Network forensics
analysis using Wireshark. International Journal of Security and Networks, 10(2), pp.91-106.
Noman, H.A., Abdullah, S.M. and Mohammed, H.I., 2015. An Automated Approach to Detect
Deauthentication and Disassociation Dos Attacks on Wireless 802.11 Networks. International
Journal of Computer Science Issues (IJCSI), 12(4), p.107.
Osanaiye, O.A. and Dlodlo, M., 2015, September. TCP/IP header classification for detecting
spoofed DDoS attack in Cloud environment. In EUROCON 2015-International Conference on
Computer as a Tool (EUROCON), IEEE (pp. 1-6). IEEE.
Pacheco, J. and Hariri, S., 2016, September. IoT security framework for smart cyber
infrastructures. In Foundations and Applications of Self* Systems, IEEE International
Workshops on (pp. 242-247). IEEE.
Paharia, B. and Bhushan, K., 2018, July. DDoS Detection and Mitigation in Cloud Via FogFiter:
A Defence Mechanism. In 2018 9th International Conference on Computing, Communication
and Networking Technologies (ICCCNT) (pp. 1-7). IEEE.
Rai, M.K. and Haldkar, G., 2015. Mitigation of Intruders and TCP bad Connection Detection in
WAN Environment using Wireshark.
Rehman, S.U. and Manickam, S., 2016. Denial of Service Attack in IPv6 Duplicate Address
Detection Process. International Journal of Advanced Computer Science & Applications, 7,
pp.232-8.
Mualfah, D. and Riadi, I., 2017. Network Forensics For Detecting Flooding Attack On Web
Server. International Journal of Computer Science and Information Security, 15(2), p.326.
Ndatinya, V., Xiao, Z., Manepalli, V.R., Meng, K. and Xiao, Y., 2015. Network forensics
analysis using Wireshark. International Journal of Security and Networks, 10(2), pp.91-106.
Noman, H.A., Abdullah, S.M. and Mohammed, H.I., 2015. An Automated Approach to Detect
Deauthentication and Disassociation Dos Attacks on Wireless 802.11 Networks. International
Journal of Computer Science Issues (IJCSI), 12(4), p.107.
Osanaiye, O.A. and Dlodlo, M., 2015, September. TCP/IP header classification for detecting
spoofed DDoS attack in Cloud environment. In EUROCON 2015-International Conference on
Computer as a Tool (EUROCON), IEEE (pp. 1-6). IEEE.
Pacheco, J. and Hariri, S., 2016, September. IoT security framework for smart cyber
infrastructures. In Foundations and Applications of Self* Systems, IEEE International
Workshops on (pp. 242-247). IEEE.
Paharia, B. and Bhushan, K., 2018, July. DDoS Detection and Mitigation in Cloud Via FogFiter:
A Defence Mechanism. In 2018 9th International Conference on Computing, Communication
and Networking Technologies (ICCCNT) (pp. 1-7). IEEE.
Rai, M.K. and Haldkar, G., 2015. Mitigation of Intruders and TCP bad Connection Detection in
WAN Environment using Wireshark.
Rehman, S.U. and Manickam, S., 2016. Denial of Service Attack in IPv6 Duplicate Address
Detection Process. International Journal of Advanced Computer Science & Applications, 7,
pp.232-8.

51DISSERTATION
Robinson, R.R. and Thomas, C., 2015, December. Ranking of machine learning algorithms
based on the performance in classifying DDoS attacks. In Intelligent Computational Systems
(RAICS), 2015 IEEE Recent Advances in (pp. 185-190). IEEE.
Safoine, R., Mounir, S. and Farchi, A., 2018, May. Comparative study on DOS attacks Detection
Techniques in SIP-based VOIP networks. In 2018 6th International Conference on Multimedia
Computing and Systems (ICMCS)(pp. 1-5). IEEE.
Sahi, A., Lai, D., Li, Y. and Diykh, M., 2017. An efficient DDoS TCP flood attack detection and
prevention system in a cloud environment. IEEE Access, 5, pp.6036-6048.
Salunkhe, H., Jadhav, S. and Bhosale, V., 2017. Analysis and review of TCP SYN flood attack
on network with its detection and performance metrics. IJERT, 6(1), pp.250-256.
Shaik, A., Borgaonkar, R., Asokan, N., Niemi, V. and Seifert, J.P., 2015. Practical attacks
against privacy and availability in 4G/LTE mobile communication systems. arXiv preprint
arXiv:1510.07563.
Shamshirband, S., Daghighi, B., Anuar, N.B., Kiah, M.L.M., Patel, A. and Abraham, A., 2015.
Co-FQL: Anomaly detection using cooperative fuzzy Q-learning in network. Journal of
Intelligent & Fuzzy Systems, 28(3), pp.1345-1357.
Sharma, P., Sharma, R., Pilli, E.S. and Mishra, A.K., 2015, October. A detection algorithm for
DoS attack in the cloud environment. In Proceedings of the 8th Annual ACM India
Conference (pp. 107-110). ACM.
Robinson, R.R. and Thomas, C., 2015, December. Ranking of machine learning algorithms
based on the performance in classifying DDoS attacks. In Intelligent Computational Systems
(RAICS), 2015 IEEE Recent Advances in (pp. 185-190). IEEE.
Safoine, R., Mounir, S. and Farchi, A., 2018, May. Comparative study on DOS attacks Detection
Techniques in SIP-based VOIP networks. In 2018 6th International Conference on Multimedia
Computing and Systems (ICMCS)(pp. 1-5). IEEE.
Sahi, A., Lai, D., Li, Y. and Diykh, M., 2017. An efficient DDoS TCP flood attack detection and
prevention system in a cloud environment. IEEE Access, 5, pp.6036-6048.
Salunkhe, H., Jadhav, S. and Bhosale, V., 2017. Analysis and review of TCP SYN flood attack
on network with its detection and performance metrics. IJERT, 6(1), pp.250-256.
Shaik, A., Borgaonkar, R., Asokan, N., Niemi, V. and Seifert, J.P., 2015. Practical attacks
against privacy and availability in 4G/LTE mobile communication systems. arXiv preprint
arXiv:1510.07563.
Shamshirband, S., Daghighi, B., Anuar, N.B., Kiah, M.L.M., Patel, A. and Abraham, A., 2015.
Co-FQL: Anomaly detection using cooperative fuzzy Q-learning in network. Journal of
Intelligent & Fuzzy Systems, 28(3), pp.1345-1357.
Sharma, P., Sharma, R., Pilli, E.S. and Mishra, A.K., 2015, October. A detection algorithm for
DoS attack in the cloud environment. In Proceedings of the 8th Annual ACM India
Conference (pp. 107-110). ACM.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

52DISSERTATION
Singh, N.A., Singh, K.J. and De, T., 2016, August. Distributed denial of service attack detection
using naive Bayes classifier through info gain feature selection. In Proceedings of the
International Conference on Informatics and Analytics (p. 54). ACM.
Skowyra, R., Xu, L., Gu, G., Dedhia, V., Hobson, T., Okhravi, H. and Landry, J., 2018, June.
Effective topology tampering attacks and defenses in software-defined networks. In 2018 48th
Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN) (pp.
374-385). IEEE.
Yusof, M.A.M., Ali, F.H.M. and Darus, M.Y., 2017, November. Detection and Defense
Algorithms of Different Types of DDoS Attacks Using Machine Learning. In International
Conference on Computational Science and Technology (pp. 370-379). Springer, Singapore.
Zaalouk, A., Khondoker, R., Marx, R. and Bayarou, K., 2014, May. Orchsec: An orchestrator-
based architecture for enhancing network-security using network monitoring and sdn control
functions. In Network Operations and Management Symposium (NOMS), 2014 IEEE (pp. 1-9).
IEEE.
Zhang, J., Zhang, Y., Liu, P. and He, J., 2016, November. A spark-based DDoS attack detection
model in cloud services. In International Conference on Information Security Practice and
Experience (pp. 48-64). Springer, Cham.
Singh, N.A., Singh, K.J. and De, T., 2016, August. Distributed denial of service attack detection
using naive Bayes classifier through info gain feature selection. In Proceedings of the
International Conference on Informatics and Analytics (p. 54). ACM.
Skowyra, R., Xu, L., Gu, G., Dedhia, V., Hobson, T., Okhravi, H. and Landry, J., 2018, June.
Effective topology tampering attacks and defenses in software-defined networks. In 2018 48th
Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN) (pp.
374-385). IEEE.
Yusof, M.A.M., Ali, F.H.M. and Darus, M.Y., 2017, November. Detection and Defense
Algorithms of Different Types of DDoS Attacks Using Machine Learning. In International
Conference on Computational Science and Technology (pp. 370-379). Springer, Singapore.
Zaalouk, A., Khondoker, R., Marx, R. and Bayarou, K., 2014, May. Orchsec: An orchestrator-
based architecture for enhancing network-security using network monitoring and sdn control
functions. In Network Operations and Management Symposium (NOMS), 2014 IEEE (pp. 1-9).
IEEE.
Zhang, J., Zhang, Y., Liu, P. and He, J., 2016, November. A spark-based DDoS attack detection
model in cloud services. In International Conference on Information Security Practice and
Experience (pp. 48-64). Springer, Cham.
1 out of 53
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.
