Foreshore IT Solution Network Design: Subnetting and IP Address Allocation
VerifiedAdded on 2024/05/21
|13
|2464
|334
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

ITC542
Internetworking with TCPIP
Assessment 2
Networking Fundamentals
Student Name: Asalath Mohammed Khan
Student ID: 11619729
1
Internetworking with TCPIP
Assessment 2
Networking Fundamentals
Student Name: Asalath Mohammed Khan
Student ID: 11619729
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Contents
Question1.........................................................................................................................................3
Question 2........................................................................................................................................5
Project: 2-3...................................................................................................................................5
Project: 2-5...................................................................................................................................5
Question 3........................................................................................................................................7
Question 4........................................................................................................................................9
a....................................................................................................................................................9
b.................................................................................................................................................11
References:................................................................................................................................13
2
Question1.........................................................................................................................................3
Question 2........................................................................................................................................5
Project: 2-3...................................................................................................................................5
Project: 2-5...................................................................................................................................5
Question 3........................................................................................................................................7
Question 4........................................................................................................................................9
a....................................................................................................................................................9
b.................................................................................................................................................11
References:................................................................................................................................13
2
Question 1
Comparison of OSI reference model with TCP/IP networking model:
OSI Model: A reference model which used to know the process of communication over a
network is known as open systems interconnection (OSI) model. It is a conceptual framework
which understands the relationship. The purpose of this model is to create communication
between developers and vendors, using software programs and communication products. This
model is divided into seven layers. From layer one to four are considered as a lower layer and
five to seven areas an upper layer. OSI model is the group of seven different layers, these are the
presentation, network, physical, application, data link, transport and session (Rouse, 2014).
TCP/IP model: a conceptual model which has four layers and used to interconnect various
network devices on the internet. Transmission control protocol/Internet protocol is also a suite of
communication protocols. This model explains the process of applications that how application
use a network to create channels. TCP/IP is the combination of four layers, these are transport,
physical, application and network layer (study tonight, 2018).
Sr.No
.
OSI Model TCP/IP Model
1. This model is generic, used as a
communication gateway between the end
user and network.
Internet develop protocol and TCP/IP is
based on it. A protocol of communication
which host connection above a network.
2. Deliver the packets with the help of
transport layer.
Does not deliver any packets but more
reliable than OSI model.
3. It has a separate layer of session and
presentation and follows the vertical
approach
Does not have any separate layer and
follow horizontal approach.
4. OSI model’s transport layer is only
connection oriented.
The transport layer of TCP/IP layer is
both connectionless and oriented.
5. OSI model’s network layer is both
connectionless and oriented.
The network layer is only connectionless.
6. A reference model which used as a The way implementation of OSI model is
3
Comparison of OSI reference model with TCP/IP networking model:
OSI Model: A reference model which used to know the process of communication over a
network is known as open systems interconnection (OSI) model. It is a conceptual framework
which understands the relationship. The purpose of this model is to create communication
between developers and vendors, using software programs and communication products. This
model is divided into seven layers. From layer one to four are considered as a lower layer and
five to seven areas an upper layer. OSI model is the group of seven different layers, these are the
presentation, network, physical, application, data link, transport and session (Rouse, 2014).
TCP/IP model: a conceptual model which has four layers and used to interconnect various
network devices on the internet. Transmission control protocol/Internet protocol is also a suite of
communication protocols. This model explains the process of applications that how application
use a network to create channels. TCP/IP is the combination of four layers, these are transport,
physical, application and network layer (study tonight, 2018).
Sr.No
.
OSI Model TCP/IP Model
1. This model is generic, used as a
communication gateway between the end
user and network.
Internet develop protocol and TCP/IP is
based on it. A protocol of communication
which host connection above a network.
2. Deliver the packets with the help of
transport layer.
Does not deliver any packets but more
reliable than OSI model.
3. It has a separate layer of session and
presentation and follows the vertical
approach
Does not have any separate layer and
follow horizontal approach.
4. OSI model’s transport layer is only
connection oriented.
The transport layer of TCP/IP layer is
both connectionless and oriented.
5. OSI model’s network layer is both
connectionless and oriented.
The network layer is only connectionless.
6. A reference model which used as a The way implementation of OSI model is
3
guidance tool and networks are created
around this model.
completed by TCP/IP model.
7. This model has an issue of fitting the
protocol in the model.
It does not have any protocol to fit.
8. OSI model has hidden protocol which can
be replaced at the time of change of
technology.
It is not possible to replace the protocol in
TCP/IP model.
9. OSI model has services, protocols, and
interfaces, which clearly define the model
and it’s also a protocol-independent
model.
The services, protocols, and interfaces are
not separated by this mode. And it is the
same as OSI model with protocol
dependent.
10. The OSI model is the combination of
seven different layers.
The TCP/IP model is the collection of
four layers.
(Studytonight, 2018)
After comparison and study of both models, I’ll prefer to work with TCP/IP model over OSI
model. The OSI model has a bad implementation with less timing and bad technology with bad
politics. The bad timing is related to the just finishing of this model after the research and the
waste of money. The bad technology relates to empty of two layers presentation and session
whereas data link is overfull. TCP/IP model has reliable implementation compare than OSI
model (learning network, 2014).
4
around this model.
completed by TCP/IP model.
7. This model has an issue of fitting the
protocol in the model.
It does not have any protocol to fit.
8. OSI model has hidden protocol which can
be replaced at the time of change of
technology.
It is not possible to replace the protocol in
TCP/IP model.
9. OSI model has services, protocols, and
interfaces, which clearly define the model
and it’s also a protocol-independent
model.
The services, protocols, and interfaces are
not separated by this mode. And it is the
same as OSI model with protocol
dependent.
10. The OSI model is the combination of
seven different layers.
The TCP/IP model is the collection of
four layers.
(Studytonight, 2018)
After comparison and study of both models, I’ll prefer to work with TCP/IP model over OSI
model. The OSI model has a bad implementation with less timing and bad technology with bad
politics. The bad timing is related to the just finishing of this model after the research and the
waste of money. The bad technology relates to empty of two layers presentation and session
whereas data link is overfull. TCP/IP model has reliable implementation compare than OSI
model (learning network, 2014).
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Question 2
Project: 2-3
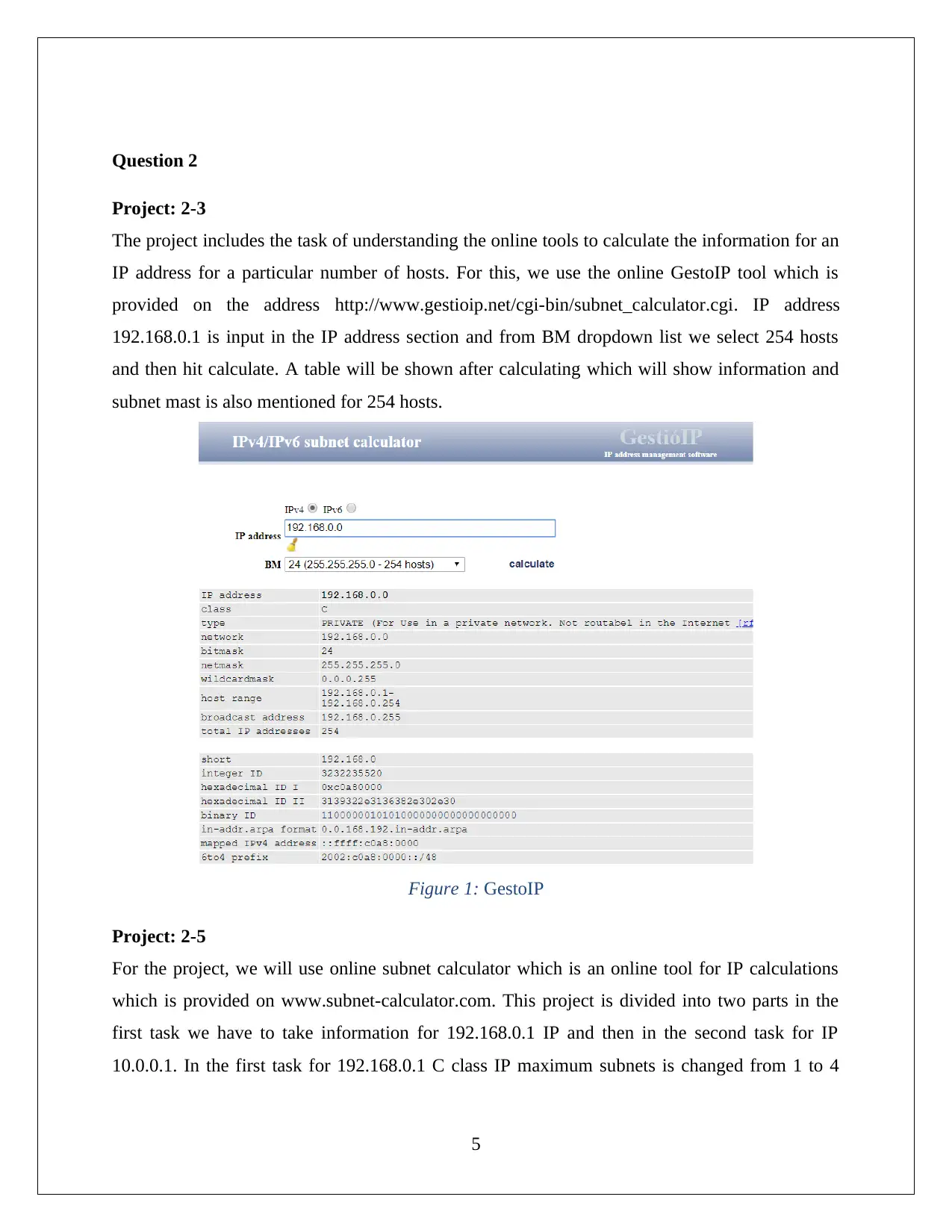
The project includes the task of understanding the online tools to calculate the information for an
IP address for a particular number of hosts. For this, we use the online GestoIP tool which is
provided on the address http://www.gestioip.net/cgi-bin/subnet_calculator.cgi. IP address
192.168.0.1 is input in the IP address section and from BM dropdown list we select 254 hosts
and then hit calculate. A table will be shown after calculating which will show information and
subnet mast is also mentioned for 254 hosts.
Figure 1: GestoIP
Project: 2-5
For the project, we will use online subnet calculator which is an online tool for IP calculations
which is provided on www.subnet-calculator.com. This project is divided into two parts in the
first task we have to take information for 192.168.0.1 IP and then in the second task for IP
10.0.0.1. In the first task for 192.168.0.1 C class IP maximum subnets is changed from 1 to 4
5
Project: 2-3
The project includes the task of understanding the online tools to calculate the information for an
IP address for a particular number of hosts. For this, we use the online GestoIP tool which is
provided on the address http://www.gestioip.net/cgi-bin/subnet_calculator.cgi. IP address
192.168.0.1 is input in the IP address section and from BM dropdown list we select 254 hosts
and then hit calculate. A table will be shown after calculating which will show information and
subnet mast is also mentioned for 254 hosts.
Figure 1: GestoIP
Project: 2-5
For the project, we will use online subnet calculator which is an online tool for IP calculations
which is provided on www.subnet-calculator.com. This project is divided into two parts in the
first task we have to take information for 192.168.0.1 IP and then in the second task for IP
10.0.0.1. In the first task for 192.168.0.1 C class IP maximum subnets is changed from 1 to 4
5
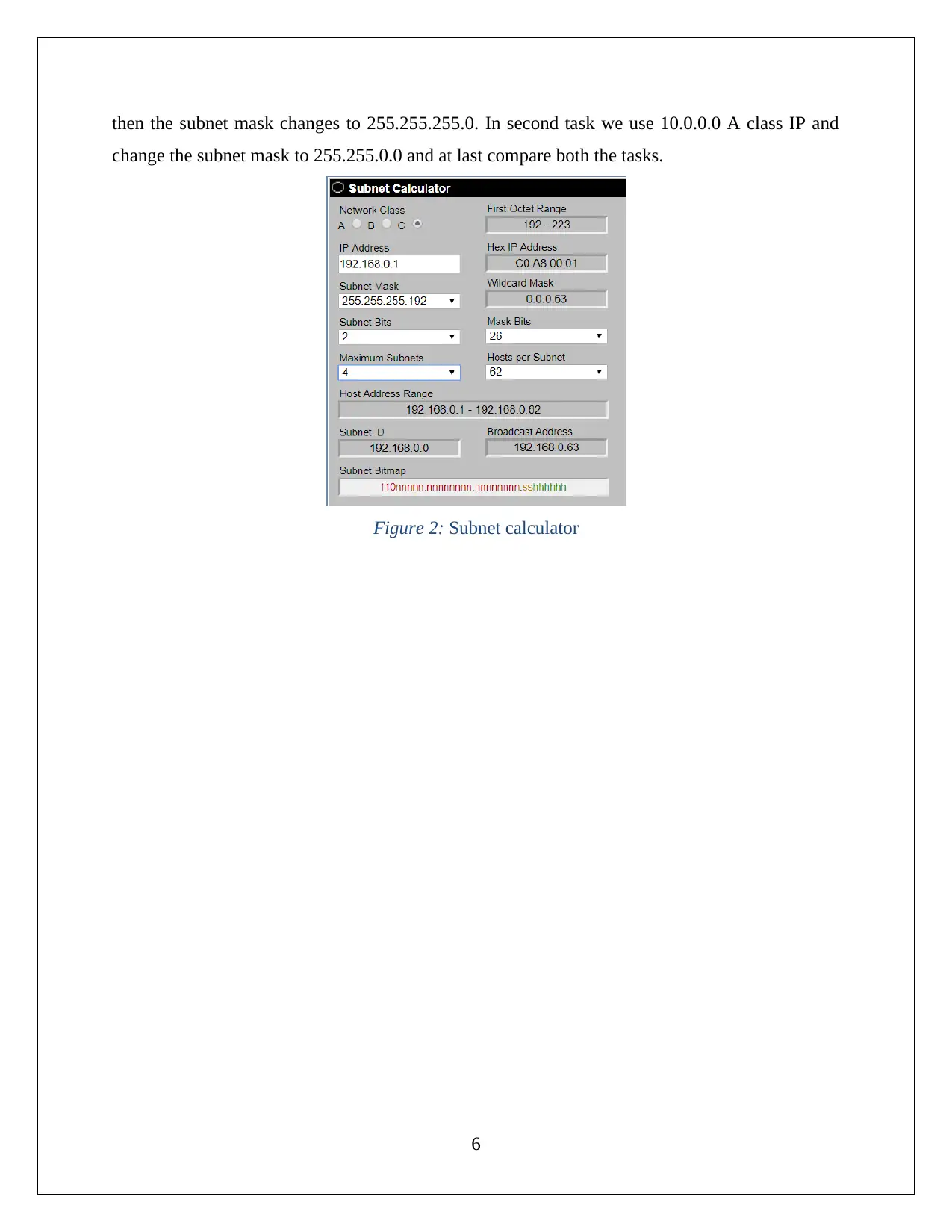
then the subnet mask changes to 255.255.255.0. In second task we use 10.0.0.0 A class IP and
change the subnet mask to 255.255.0.0 and at last compare both the tasks.
Figure 2: Subnet calculator
6
change the subnet mask to 255.255.0.0 and at last compare both the tasks.
Figure 2: Subnet calculator
6

Question 3
Describe the Address resolution protocol (ARP). What is the purpose of ARP cache:
A communication protocol which used to find the address of link layer, like MAC address, and
the given address associated with network layer address, like as IPv4 address. This protocol is
also used to mapping the (IP Address) internet protocol address of a machine in a local network.
The example is IP version 4. Four types of IP address used today which are 32 bits long. The
Ethernet, which represents the address for devices in a local area network is 48 bits long. The
table which is called Address resolution protocol cache has represented the relation between
MAC address and its related IP address.
The address resolution term has represented the procedure to find a computer system’s address in
a network. The network of Ethernet used the hardware to identify the frame’s source and
destination. The address of hardware is also called as Medium access control (MAC) address.
During the manufacturing process of the card in a factory which stores in PROM, the network
interface card of a computer system is allocated a six-byte link address. This link is a simple link
source address which used by the interface. A computer system used to send and receive the
packets with its hardware. It sends the own creates packets with source link address of its
hardware. And receive the packets which match with its hardware address.
The link layer address is called Ethernet address which dependent on the interface card. The
network layer is operated by IP operates. Address resolution protocol is used to communicate
between two different types of address. IP is used to operate all computer’s server process and
address resolution protocol client over the Ethernet. These processes are implemented as the part
of software drivers and these software drivers drive the NIC (network interface card).
The four types of messages which sent by the address resolution protocol. These messages are
identified as values of the operation of address resolution protocol message. These messages are:
ARP Request
ARP Reply
RARP Request
RARP Reply
The purpose of Address resolution protocol cache is to resolve the address for a short time to
decrease the number of request for resolution. The address resolution cache has a finite size and
7
Describe the Address resolution protocol (ARP). What is the purpose of ARP cache:
A communication protocol which used to find the address of link layer, like MAC address, and
the given address associated with network layer address, like as IPv4 address. This protocol is
also used to mapping the (IP Address) internet protocol address of a machine in a local network.
The example is IP version 4. Four types of IP address used today which are 32 bits long. The
Ethernet, which represents the address for devices in a local area network is 48 bits long. The
table which is called Address resolution protocol cache has represented the relation between
MAC address and its related IP address.
The address resolution term has represented the procedure to find a computer system’s address in
a network. The network of Ethernet used the hardware to identify the frame’s source and
destination. The address of hardware is also called as Medium access control (MAC) address.
During the manufacturing process of the card in a factory which stores in PROM, the network
interface card of a computer system is allocated a six-byte link address. This link is a simple link
source address which used by the interface. A computer system used to send and receive the
packets with its hardware. It sends the own creates packets with source link address of its
hardware. And receive the packets which match with its hardware address.
The link layer address is called Ethernet address which dependent on the interface card. The
network layer is operated by IP operates. Address resolution protocol is used to communicate
between two different types of address. IP is used to operate all computer’s server process and
address resolution protocol client over the Ethernet. These processes are implemented as the part
of software drivers and these software drivers drive the NIC (network interface card).
The four types of messages which sent by the address resolution protocol. These messages are
identified as values of the operation of address resolution protocol message. These messages are:
ARP Request
ARP Reply
RARP Request
RARP Reply
The purpose of Address resolution protocol cache is to resolve the address for a short time to
decrease the number of request for resolution. The address resolution cache has a finite size and
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

full of obsolete and incomplete entries which are not allowed in a computer system without
check. The cache is flushed all the entries of the computer system. The unused entries are deleted
from the computer and make free space in the cache of address resolution protocol. Some
contacts are not running all time in a computer system so it deletes these unsuccessful contacts.
In some conditions, the host changes the address of MAC when it was using and this host is
deleted by another host after deleted the entry of cache and a fresh message of address resolution
protocol is established for a new connection.
Gratuitous ARP:
The gratuitous term is used after the selection of IP address by a node and this IP address defend
its selected address on local area network. Node’s IP addresses common view can be a force
after the change of IP address.
Proxy ARP:
A node responds to the request on the place of another node. This term is also used to redirect the
traffic when it sent an IP address to another system (Fairhurst, 2005).
8
check. The cache is flushed all the entries of the computer system. The unused entries are deleted
from the computer and make free space in the cache of address resolution protocol. Some
contacts are not running all time in a computer system so it deletes these unsuccessful contacts.
In some conditions, the host changes the address of MAC when it was using and this host is
deleted by another host after deleted the entry of cache and a fresh message of address resolution
protocol is established for a new connection.
Gratuitous ARP:
The gratuitous term is used after the selection of IP address by a node and this IP address defend
its selected address on local area network. Node’s IP addresses common view can be a force
after the change of IP address.
Proxy ARP:
A node responds to the request on the place of another node. This term is also used to redirect the
traffic when it sent an IP address to another system (Fairhurst, 2005).
8
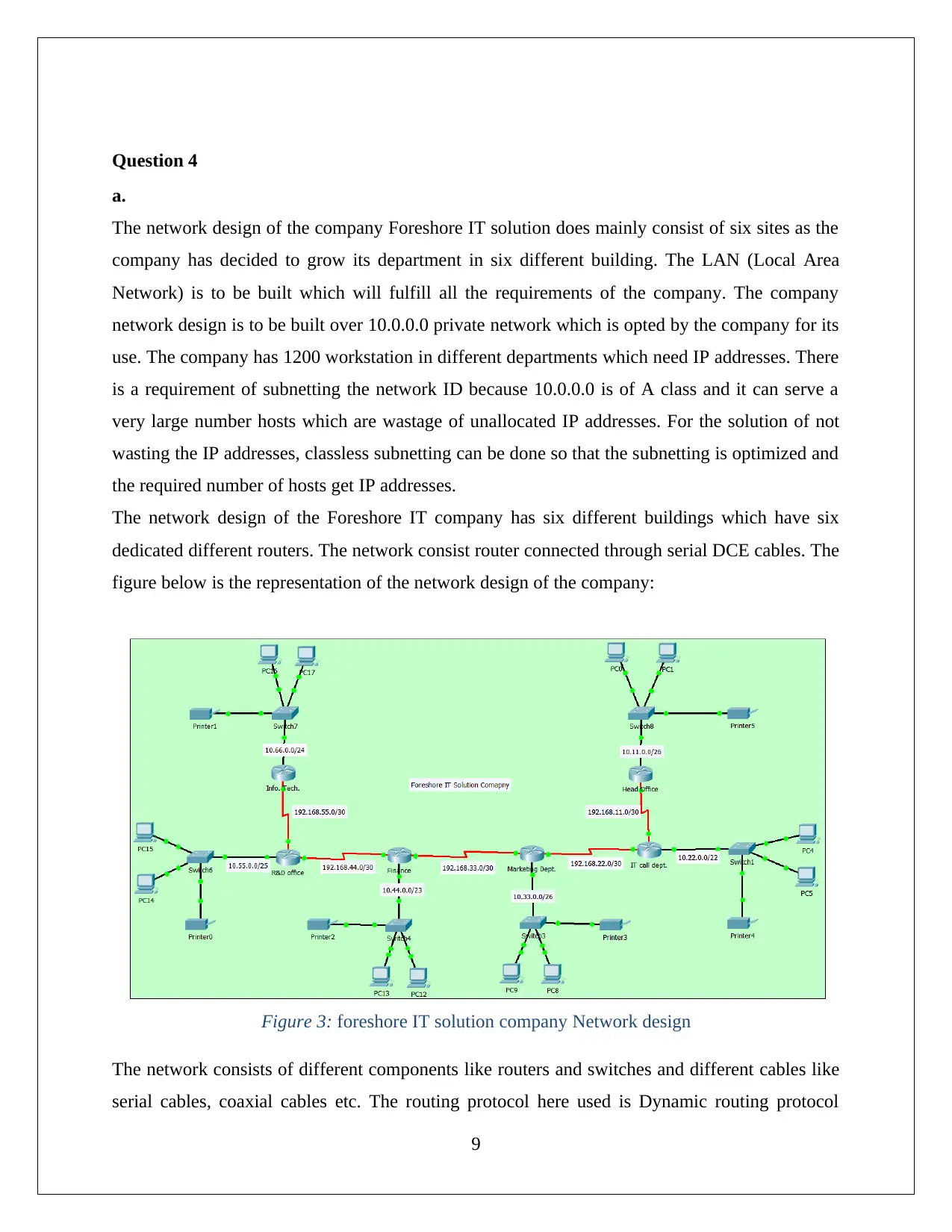
Question 4
a.
The network design of the company Foreshore IT solution does mainly consist of six sites as the
company has decided to grow its department in six different building. The LAN (Local Area
Network) is to be built which will fulfill all the requirements of the company. The company
network design is to be built over 10.0.0.0 private network which is opted by the company for its
use. The company has 1200 workstation in different departments which need IP addresses. There
is a requirement of subnetting the network ID because 10.0.0.0 is of A class and it can serve a
very large number hosts which are wastage of unallocated IP addresses. For the solution of not
wasting the IP addresses, classless subnetting can be done so that the subnetting is optimized and
the required number of hosts get IP addresses.
The network design of the Foreshore IT company has six different buildings which have six
dedicated different routers. The network consist router connected through serial DCE cables. The
figure below is the representation of the network design of the company:
Figure 3: foreshore IT solution company Network design
The network consists of different components like routers and switches and different cables like
serial cables, coaxial cables etc. The routing protocol here used is Dynamic routing protocol
9
a.
The network design of the company Foreshore IT solution does mainly consist of six sites as the
company has decided to grow its department in six different building. The LAN (Local Area
Network) is to be built which will fulfill all the requirements of the company. The company
network design is to be built over 10.0.0.0 private network which is opted by the company for its
use. The company has 1200 workstation in different departments which need IP addresses. There
is a requirement of subnetting the network ID because 10.0.0.0 is of A class and it can serve a
very large number hosts which are wastage of unallocated IP addresses. For the solution of not
wasting the IP addresses, classless subnetting can be done so that the subnetting is optimized and
the required number of hosts get IP addresses.
The network design of the Foreshore IT company has six different buildings which have six
dedicated different routers. The network consist router connected through serial DCE cables. The
figure below is the representation of the network design of the company:
Figure 3: foreshore IT solution company Network design
The network consists of different components like routers and switches and different cables like
serial cables, coaxial cables etc. The routing protocol here used is Dynamic routing protocol
9

which provides independent routing practice over the network. For interconnection between
routers, different private networks are used so that routing can be performed. For like connection
between Head office and IT call department 192.168.11.0/30 IP is used, here 30 defines network
bits which provide only two hosts.
The provided IP 10.0.0.0 has 8 network bits and rest 24 bits are for hosts. But we are going to
subnet the IP according to the number of hosts included in the departments. Example of
calculation for classless subnetting is performed below –
The network ID provided is 10.0.0.0, the Head Office of the company has 60 workstations which
is the number of hosts. IP address consists 32 bits' binary value which is then converted to the
decimal value. For 60 hosts the nearest binary value will be 111111 which is equal to 26 = 64
(neglecting network IP and broadcast IP). The number of hosts 60 must be equal to or smaller
(nearest value) to its binary. So for Head Office number of hosts will be treated as 62 and host
bits = 6
H = 6
The network is of A class so the initial 8 bits are for the network only, so,
Network bits of the IP, N = 8
Now for subnet mask bits, we have to first find the subnet bits. To calculate subnet bits following
method is applied:
2Subnet mask bits + host bits (H) = 232
2subnet mask bits + 6 = 232, from this it can be calculated that: subnet mask bits + host bits = 32
Subnet mask bits = 32 – host bits (H) = 32 – 6 = 26
So for 26 subnet mask bits, the relevant subnet mask will be 255.255.255.192 which will make
the 10.0.0.0 IP address to be subnetted to provide IP address to 62 hosts which will precisely
handle the Head Office needs. We will take 10.11.0.0 as the subnetted IP.
Network ID 10.11.0.0
Subnet mask 255.255.255.192
10
routers, different private networks are used so that routing can be performed. For like connection
between Head office and IT call department 192.168.11.0/30 IP is used, here 30 defines network
bits which provide only two hosts.
The provided IP 10.0.0.0 has 8 network bits and rest 24 bits are for hosts. But we are going to
subnet the IP according to the number of hosts included in the departments. Example of
calculation for classless subnetting is performed below –
The network ID provided is 10.0.0.0, the Head Office of the company has 60 workstations which
is the number of hosts. IP address consists 32 bits' binary value which is then converted to the
decimal value. For 60 hosts the nearest binary value will be 111111 which is equal to 26 = 64
(neglecting network IP and broadcast IP). The number of hosts 60 must be equal to or smaller
(nearest value) to its binary. So for Head Office number of hosts will be treated as 62 and host
bits = 6
H = 6
The network is of A class so the initial 8 bits are for the network only, so,
Network bits of the IP, N = 8
Now for subnet mask bits, we have to first find the subnet bits. To calculate subnet bits following
method is applied:
2Subnet mask bits + host bits (H) = 232
2subnet mask bits + 6 = 232, from this it can be calculated that: subnet mask bits + host bits = 32
Subnet mask bits = 32 – host bits (H) = 32 – 6 = 26
So for 26 subnet mask bits, the relevant subnet mask will be 255.255.255.192 which will make
the 10.0.0.0 IP address to be subnetted to provide IP address to 62 hosts which will precisely
handle the Head Office needs. We will take 10.11.0.0 as the subnetted IP.
Network ID 10.11.0.0
Subnet mask 255.255.255.192
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
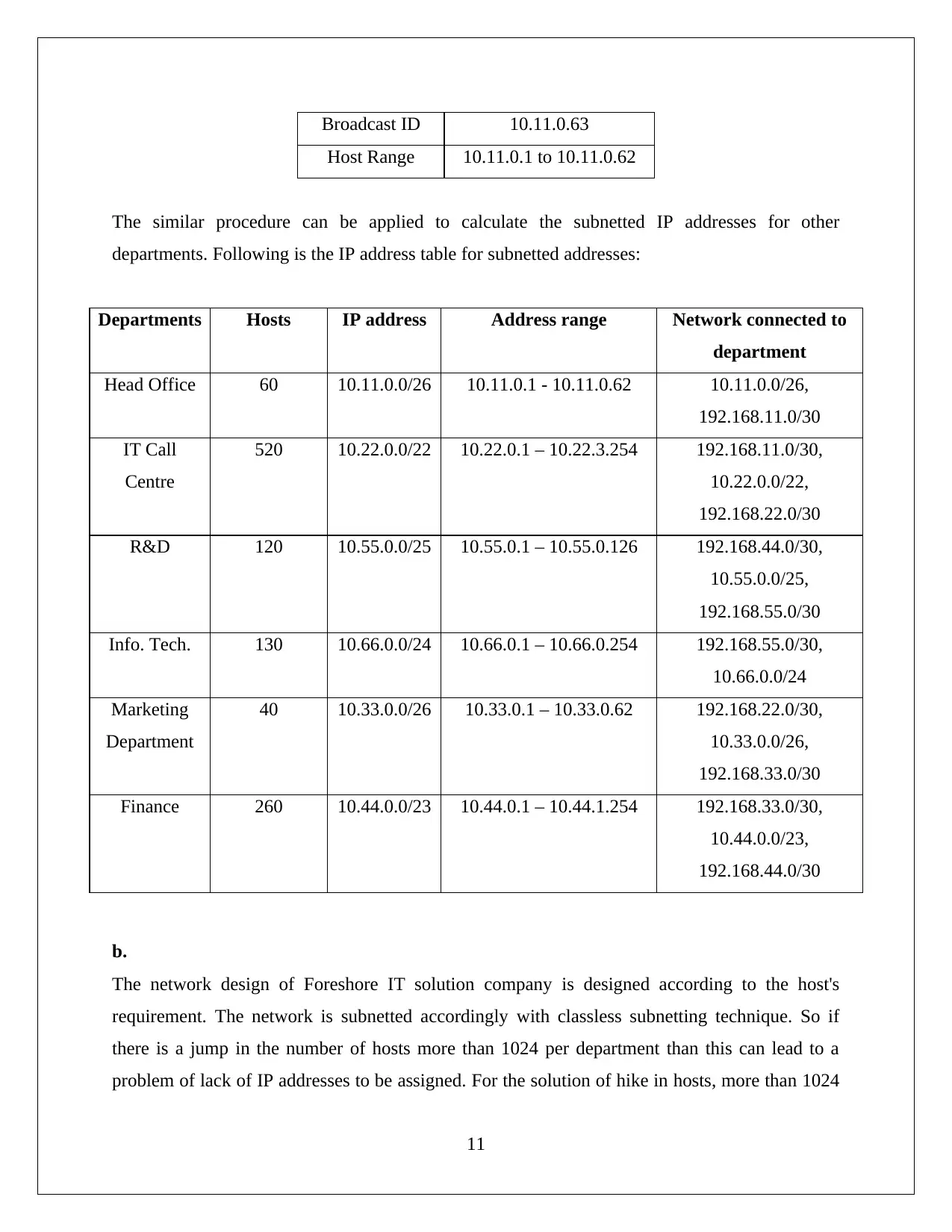
Broadcast ID 10.11.0.63
Host Range 10.11.0.1 to 10.11.0.62
The similar procedure can be applied to calculate the subnetted IP addresses for other
departments. Following is the IP address table for subnetted addresses:
Departments Hosts IP address Address range Network connected to
department
Head Office 60 10.11.0.0/26 10.11.0.1 - 10.11.0.62 10.11.0.0/26,
192.168.11.0/30
IT Call
Centre
520 10.22.0.0/22 10.22.0.1 – 10.22.3.254 192.168.11.0/30,
10.22.0.0/22,
192.168.22.0/30
R&D 120 10.55.0.0/25 10.55.0.1 – 10.55.0.126 192.168.44.0/30,
10.55.0.0/25,
192.168.55.0/30
Info. Tech. 130 10.66.0.0/24 10.66.0.1 – 10.66.0.254 192.168.55.0/30,
10.66.0.0/24
Marketing
Department
40 10.33.0.0/26 10.33.0.1 – 10.33.0.62 192.168.22.0/30,
10.33.0.0/26,
192.168.33.0/30
Finance 260 10.44.0.0/23 10.44.0.1 – 10.44.1.254 192.168.33.0/30,
10.44.0.0/23,
192.168.44.0/30
b.
The network design of Foreshore IT solution company is designed according to the host's
requirement. The network is subnetted accordingly with classless subnetting technique. So if
there is a jump in the number of hosts more than 1024 per department than this can lead to a
problem of lack of IP addresses to be assigned. For the solution of hike in hosts, more than 1024
11
Host Range 10.11.0.1 to 10.11.0.62
The similar procedure can be applied to calculate the subnetted IP addresses for other
departments. Following is the IP address table for subnetted addresses:
Departments Hosts IP address Address range Network connected to
department
Head Office 60 10.11.0.0/26 10.11.0.1 - 10.11.0.62 10.11.0.0/26,
192.168.11.0/30
IT Call
Centre
520 10.22.0.0/22 10.22.0.1 – 10.22.3.254 192.168.11.0/30,
10.22.0.0/22,
192.168.22.0/30
R&D 120 10.55.0.0/25 10.55.0.1 – 10.55.0.126 192.168.44.0/30,
10.55.0.0/25,
192.168.55.0/30
Info. Tech. 130 10.66.0.0/24 10.66.0.1 – 10.66.0.254 192.168.55.0/30,
10.66.0.0/24
Marketing
Department
40 10.33.0.0/26 10.33.0.1 – 10.33.0.62 192.168.22.0/30,
10.33.0.0/26,
192.168.33.0/30
Finance 260 10.44.0.0/23 10.44.0.1 – 10.44.1.254 192.168.33.0/30,
10.44.0.0/23,
192.168.44.0/30
b.
The network design of Foreshore IT solution company is designed according to the host's
requirement. The network is subnetted accordingly with classless subnetting technique. So if
there is a jump in the number of hosts more than 1024 per department than this can lead to a
problem of lack of IP addresses to be assigned. For the solution of hike in hosts, more than 1024
11

the current scheme will be changed. Like for example in Head office the total hosts provided by
the IP address 10.11.0.0/26 is 62 if there are more than 1024 hosts than the subnet mask will be
changed 255.255.255.192 to 255.255.248.0 which can provide IP addresses to about 2046 hosts.
12
the IP address 10.11.0.0/26 is 62 if there are more than 1024 hosts than the subnet mask will be
changed 255.255.255.192 to 255.255.248.0 which can provide IP addresses to about 2046 hosts.
12

References:
Fairhurst, G. (2005). Address Resolution Protocol (arp). Retrieved from
http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/arp.html
Learningnetwork. (2014). Why is TCP/IP used rather than OSI? - 77624 - The Cisco
Learning Network. Retrieved from https://learningnetwork.cisco.com/thread/77624
Rouse, M. (2014). What is OSI reference model (Open Systems Interconnection)? -
Definition from WhatIs.com. Retrieved from
https://searchnetworking.techtarget.com/definition/OSI
Studytonight. (2018). Difference between OSI Reference Model and TCP/IP Reference
Model | Study tonight. Retrieved from
https://www.studytonight.com/computer-networks/comparison-osi-tcp-model
Studytonight. (2018). Introduction to TCP/IP Reference Model | Study tonight. Retrieved
from https://www.studytonight.com/computer-networks/tcp-ip-reference-model
13
Fairhurst, G. (2005). Address Resolution Protocol (arp). Retrieved from
http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/arp.html
Learningnetwork. (2014). Why is TCP/IP used rather than OSI? - 77624 - The Cisco
Learning Network. Retrieved from https://learningnetwork.cisco.com/thread/77624
Rouse, M. (2014). What is OSI reference model (Open Systems Interconnection)? -
Definition from WhatIs.com. Retrieved from
https://searchnetworking.techtarget.com/definition/OSI
Studytonight. (2018). Difference between OSI Reference Model and TCP/IP Reference
Model | Study tonight. Retrieved from
https://www.studytonight.com/computer-networks/comparison-osi-tcp-model
Studytonight. (2018). Introduction to TCP/IP Reference Model | Study tonight. Retrieved
from https://www.studytonight.com/computer-networks/tcp-ip-reference-model
13
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




