Foundations of Cyber Security
VerifiedAdded on 2023/04/21
|26
|5206
|328
AI Summary
This document provides an implementation of the Vigenere cipher in a C program. It explains the process of encrypting and decrypting a message using the cipher and discusses the robustness and vulnerabilities of the cipher. The document also provides recommendations for using the cipher.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

FOUNDATIONS OF CYBER SECURITY
Combined Coursework
Module: CTEC5801
Combined Coursework
Module: CTEC5801
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Question 1: Implementing the Vigenere cipher in a C program.
Below is the implementation of the cipher in C.
#include <string.h>
#include <stdio.h>
#include <ctype.h>
#include <process.h>
//functions to be used in the program
void cipher(char *,char *);
void encrypt();
void decrypt();
main()
{
int choose;
//User’s choice taken and the necessary function called.
while(1)
{
printf("Enter 1 to encrypt the Text\n");
Below is the implementation of the cipher in C.
#include <string.h>
#include <stdio.h>
#include <ctype.h>
#include <process.h>
//functions to be used in the program
void cipher(char *,char *);
void encrypt();
void decrypt();
main()
{
int choose;
//User’s choice taken and the necessary function called.
while(1)
{
printf("Enter 1 to encrypt the Text\n");

printf("Enter 2 to decrypt the Text\n");
printf("Enter 3 to exit\n");
printf("Choose one of the above :\n ");
scanf("%d",&choose); //stores the choice
fflush(stdin);//clears the screen
if(choose == 3) //selection statement
exit(0);
else if(choose == 1)
encrypt(); //calls the encryption function when the conditions
are met.
else if(choice == 2)
decrypt(); //calls the decrypt function
else
printf("Invalid choice\n");
}
return 0;
}
printf("Enter 3 to exit\n");
printf("Choose one of the above :\n ");
scanf("%d",&choose); //stores the choice
fflush(stdin);//clears the screen
if(choose == 3) //selection statement
exit(0);
else if(choose == 1)
encrypt(); //calls the encryption function when the conditions
are met.
else if(choice == 2)
decrypt(); //calls the decrypt function
else
printf("Invalid choice\n");
}
return 0;
}

void encrypt() //contents of the encrypt function
{
int a;
int b; //variable declaration
char EnteredText[100];
char keyword[27];
printf("Please input the text you want to encrypt :\n ");
gets(input);
printf("Please Enter the Encryption keyword:\n ");
gets(keyword);
for(a=0,b=0;a<strlen(EnteredText);a++,b++)
{
//The key is repeated when the end is reached.
if(b>=strlen(keyword))
{
b=0;
{
int a;
int b; //variable declaration
char EnteredText[100];
char keyword[27];
printf("Please input the text you want to encrypt :\n ");
gets(input);
printf("Please Enter the Encryption keyword:\n ");
gets(keyword);
for(a=0,b=0;a<strlen(EnteredText);a++,b++)
{
//The key is repeated when the end is reached.
if(b>=strlen(keyword))
{
b=0;
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

}
//Encryption happens by adding character from the text to the
character from the key%26
printf("%c",65+(((toupper(EnteredText[a])-65)+(toupper(keyword[b])-
65))%26));
}
}//
void decrypt()// decryption function
{
int a,b;
char EnteredText[100];
char keyword[26];
int output;//stores the value.
printf("Which text do you want to decrypt? :\n ");
gets(EnteredText);
printf("Enter Decryption Key :\n ");
gets(keyword);
//Encryption happens by adding character from the text to the
character from the key%26
printf("%c",65+(((toupper(EnteredText[a])-65)+(toupper(keyword[b])-
65))%26));
}
}//
void decrypt()// decryption function
{
int a,b;
char EnteredText[100];
char keyword[26];
int output;//stores the value.
printf("Which text do you want to decrypt? :\n ");
gets(EnteredText);
printf("Enter Decryption Key :\n ");
gets(keyword);

for(a=0,b=0;a<strlen(EnteredText);a++,b++)
{
//This loop is for repeating the keyword when the end is reached.
if(b>=strlen(keyworld))//selection statement
{
j=0;
}
//This is the same as decrypting, only that this time it is
subtraction
output = (toupper(EnteredText[a])-64)-(toupper(key[b])-64);
//Rotate the value backwards if negative and add it to 26
if( output < 0)//selection statement
{
output = 26 + value;
}
{
//This loop is for repeating the keyword when the end is reached.
if(b>=strlen(keyworld))//selection statement
{
j=0;
}
//This is the same as decrypting, only that this time it is
subtraction
output = (toupper(EnteredText[a])-64)-(toupper(key[b])-64);
//Rotate the value backwards if negative and add it to 26
if( output < 0)//selection statement
{
output = 26 + value;
}

printf("%c",65 + (output % 26));
}
}
Introduction
The program presents the user with a choice of decrypting or encrypting a message using the
Vigenere Cipher. If the user chooses to encrypt a message, the program prompts them to enter
the phrase or text they wish to encrypt. The program then asks for the keyword that users can use
to decrypt or encrypt the phrase. The program, finally, encrypts or decrypts the text and displays
the result. According to Aumasson1, it is a type of polyalphabetic cipher that works with
substitution.
Robustness of the cipher
According to Krawczyk2, the Cipher was hard to break when it first came to existence. This is
because it used all the 26 letters of the alphabet. Frequency analysis of letters is not common in
the cipher hence it offers resistance to easy deciphering. The user chooses the key used to
encrypt a message. This makes it even harder to break into the cipher since the key can be any
word.
Although the cipher is hard to break, it has some vulnerabilities:
1) Repeating the key
2) One can guess the length of the key by finding repeated words in a plain text.
3) If one finds the key, cracking the cipher becomes easy.
1 Aumasson, Serious cryptography : a practical introduction to modern encryption (No Starch
press 2018)
2 Krawczyk, Hugo, Public-key cryptography (Springer 2014)
}
}
Introduction
The program presents the user with a choice of decrypting or encrypting a message using the
Vigenere Cipher. If the user chooses to encrypt a message, the program prompts them to enter
the phrase or text they wish to encrypt. The program then asks for the keyword that users can use
to decrypt or encrypt the phrase. The program, finally, encrypts or decrypts the text and displays
the result. According to Aumasson1, it is a type of polyalphabetic cipher that works with
substitution.
Robustness of the cipher
According to Krawczyk2, the Cipher was hard to break when it first came to existence. This is
because it used all the 26 letters of the alphabet. Frequency analysis of letters is not common in
the cipher hence it offers resistance to easy deciphering. The user chooses the key used to
encrypt a message. This makes it even harder to break into the cipher since the key can be any
word.
Although the cipher is hard to break, it has some vulnerabilities:
1) Repeating the key
2) One can guess the length of the key by finding repeated words in a plain text.
3) If one finds the key, cracking the cipher becomes easy.
1 Aumasson, Serious cryptography : a practical introduction to modern encryption (No Starch
press 2018)
2 Krawczyk, Hugo, Public-key cryptography (Springer 2014)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

For example, if we have a plaintext like “This computer is like that computer”, and the keyword
is “key”, then that means that the text has the word “computer” twice. The cipher text will also
contain the same encrypted words, only that this time, the words are 15 letters apart.
Recommendation
The cipher is recommendable because:
1) It is hard to break. This is because it uses all 26 letters of the alphabet.
2) People who are not technical savvy would not understand the encryption or break it.
3) One has to find the key in order to break the cipher. Without the key, the cipher is
unbreakable, as suggested by Eisenbarth3.
3 Eisenbarth, Thomas and Erdinç Ö ztürk, Lightweight cryptography for security and privacy
(Springer 2015)
is “key”, then that means that the text has the word “computer” twice. The cipher text will also
contain the same encrypted words, only that this time, the words are 15 letters apart.
Recommendation
The cipher is recommendable because:
1) It is hard to break. This is because it uses all 26 letters of the alphabet.
2) People who are not technical savvy would not understand the encryption or break it.
3) One has to find the key in order to break the cipher. Without the key, the cipher is
unbreakable, as suggested by Eisenbarth3.
3 Eisenbarth, Thomas and Erdinç Ö ztürk, Lightweight cryptography for security and privacy
(Springer 2015)

Question 2: Data security
Introduction
Data security is an important aspect in any organization. Securing data in an organization
involves preventing unauthorized people from accessing the organization’s computers, databases
or any other source of data. One must take certain steps to protect digital data. Complete data
erasure is the most important step. If the organization does not delete its data completely, hackers
may access the data by using certain data recovery methods. By simply deleting the data using
the delete functionality of the operating system, the computer does not delete the data
completely. This report details on how one should delete data. It also explains how malicious
people can recover data if not deleted effectively.
Normal delete function
When a user deletes a file on a computer, the computer does not delete the file completely and
securely. The file continues to exists, even after the user has removed it from the recycle bin. The
file is still stored in the hard drive. This means that anyone can recover the file that the user has
deleted.
Mauri4 suggests that, most operating systems know where a file is stored on the hard drive by the
use of pointers. Pointers are functions that tell the operating system where each file is stored in
the hard drive, that is, where the data begins and ends. Deleting functionality in most operating
systems, according to Kale5, involve removing the pointer from the data, marking the sectors that
4 Mauri, Jaime and others, Security in computing and communications (Springer 2014)
5 K Kale, S. C. Mehrotra, and R. R. Manza, Advances in computer vision and information
technology (I.K. International Pub. House 2008)
Introduction
Data security is an important aspect in any organization. Securing data in an organization
involves preventing unauthorized people from accessing the organization’s computers, databases
or any other source of data. One must take certain steps to protect digital data. Complete data
erasure is the most important step. If the organization does not delete its data completely, hackers
may access the data by using certain data recovery methods. By simply deleting the data using
the delete functionality of the operating system, the computer does not delete the data
completely. This report details on how one should delete data. It also explains how malicious
people can recover data if not deleted effectively.
Normal delete function
When a user deletes a file on a computer, the computer does not delete the file completely and
securely. The file continues to exists, even after the user has removed it from the recycle bin. The
file is still stored in the hard drive. This means that anyone can recover the file that the user has
deleted.
Mauri4 suggests that, most operating systems know where a file is stored on the hard drive by the
use of pointers. Pointers are functions that tell the operating system where each file is stored in
the hard drive, that is, where the data begins and ends. Deleting functionality in most operating
systems, according to Kale5, involve removing the pointer from the data, marking the sectors that
4 Mauri, Jaime and others, Security in computing and communications (Springer 2014)
5 K Kale, S. C. Mehrotra, and R. R. Manza, Advances in computer vision and information
technology (I.K. International Pub. House 2008)

the pointer has previously pointed to as available. The file managers of the operating systems
show the space as free and assumes that the data is not present. This means that the computer can
overwrite existing data.
Before new data overwrites the old data, one can use a recovery program to recover the data.
Recovering from the recycle bin:
The first step in restoring data is checking the deleted data in the recycle bin. One can do this in
many operating systems. In this report however, demonstration is in windows operating system.
If the files are there, then right click on the file and choose restore. The computer will restore the
data to the initial location. If the recycle bin icon does not exist on the desktop, click the start
menu and search for ‘show or hide’ and a shortcut will appear in which you can tick the recycle
bin.
However, the recycle bin is not reliable. It has a limit in size of storage. When it reaches the
limit, the computer automatically deletes the older data. If the data does not exist in the recycle
bin, then it’s time to use data recovery software to restore the data.
Using data recovery software
show the space as free and assumes that the data is not present. This means that the computer can
overwrite existing data.
Before new data overwrites the old data, one can use a recovery program to recover the data.
Recovering from the recycle bin:
The first step in restoring data is checking the deleted data in the recycle bin. One can do this in
many operating systems. In this report however, demonstration is in windows operating system.
If the files are there, then right click on the file and choose restore. The computer will restore the
data to the initial location. If the recycle bin icon does not exist on the desktop, click the start
menu and search for ‘show or hide’ and a shortcut will appear in which you can tick the recycle
bin.
However, the recycle bin is not reliable. It has a limit in size of storage. When it reaches the
limit, the computer automatically deletes the older data. If the data does not exist in the recycle
bin, then it’s time to use data recovery software to restore the data.
Using data recovery software
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

According to Foley6, Data recovery is the process of retrieving data that had been previously
deleted, damaged or formatted. Data recovery is not always possible as the data new data may
have overwritten previous data. If not, then one can delete the data. Since data technically still
exists on a hard drive, one can restore it. The data however, is stored as several disconnected
fragments. Data recovery on solid state drives however is not possible. This is because the SSD
deleted the data completely making it unrecoverable.
Effective data erasure
This is the action of removing data from a storage device. Data clearing, wiping or cleaning
means the same thing as deletion or erasure. The process is software based. This means that it
relies on computer software. Data in an organization should be disposed-off safely so as to avoid
future conflicts and to comply with the law.
Safe data deletion is possible by using a dedicated software or by overwriting the data manually.
However, one should make sure that the data intended for deletion does not contain personal or
sensitive information. Always consider if you will need that data again if deleted completely
with safe procedures. The data deleted should be such that no one can use it against you.
Data erasure using a software is an effective process. It aims at overwriting the data on the
device that holds the data. It completely destroys all the data available by overwriting using zeros
and ones. This makes the data unrecoverable and sanitizes it.
6 Foley, Simon N., Dieter Gollmann, and Einar Snekkenes. Computer security -- ESORICS 2017
(Springer 2017)
deleted, damaged or formatted. Data recovery is not always possible as the data new data may
have overwritten previous data. If not, then one can delete the data. Since data technically still
exists on a hard drive, one can restore it. The data however, is stored as several disconnected
fragments. Data recovery on solid state drives however is not possible. This is because the SSD
deleted the data completely making it unrecoverable.
Effective data erasure
This is the action of removing data from a storage device. Data clearing, wiping or cleaning
means the same thing as deletion or erasure. The process is software based. This means that it
relies on computer software. Data in an organization should be disposed-off safely so as to avoid
future conflicts and to comply with the law.
Safe data deletion is possible by using a dedicated software or by overwriting the data manually.
However, one should make sure that the data intended for deletion does not contain personal or
sensitive information. Always consider if you will need that data again if deleted completely
with safe procedures. The data deleted should be such that no one can use it against you.
Data erasure using a software is an effective process. It aims at overwriting the data on the
device that holds the data. It completely destroys all the data available by overwriting using zeros
and ones. This makes the data unrecoverable and sanitizes it.
6 Foley, Simon N., Dieter Gollmann, and Einar Snekkenes. Computer security -- ESORICS 2017
(Springer 2017)

Unlike physical destruction of the storage device (known as degaussing) the software removes
the data completely while leaving the disk in a good condition. To comply with the law, most
software overwrites twice. According to Qing7, this makes the data fully unrecoverable.
However, one should only use the software that offer complete data erasure.
The deletion software should have the following characteristics:
1) Comply with data deletion standards
2) Verify the success of the data erasure process after finishing.
Encryption is a dated method that aids in data erasure. When one uses encrypted drives and
storage devices, the chances of recovering data after deletion are minimal. This is because
encryption empowers data erasure in crypto-shredding. This is where the software deleted the
encryption keys in place of the data itself. Nowadays, computer hardware can delete data faster
than a hard drive can write data. These are drives that can encrypt themselves. Changing the
cryptographic keys becomes a very efficient method of complete data erasure as the keys cannot
be guesses easily.
Importance of good data erasure methods
Breach of data – Technology changes rapidly. There is need for newer models of computers and
electronics daily. This has led to refurbished asset sale. This is the sale of previously owned
computers or mobile phones. Since they are not new, it means that they contain the user’s data
that may be sensitive. This means that complete data erasure of the owner’s data is important, so
that the new owner will not access the previous sensitive data. An organization may be willing to
sell their computers for upgrade purposes. This means that they must erase the data completely
before sale. If they do not take into consideration the complete erasure process, their data may
7 Qing and Sihan. Information and communications security (Springer 2005)
the data completely while leaving the disk in a good condition. To comply with the law, most
software overwrites twice. According to Qing7, this makes the data fully unrecoverable.
However, one should only use the software that offer complete data erasure.
The deletion software should have the following characteristics:
1) Comply with data deletion standards
2) Verify the success of the data erasure process after finishing.
Encryption is a dated method that aids in data erasure. When one uses encrypted drives and
storage devices, the chances of recovering data after deletion are minimal. This is because
encryption empowers data erasure in crypto-shredding. This is where the software deleted the
encryption keys in place of the data itself. Nowadays, computer hardware can delete data faster
than a hard drive can write data. These are drives that can encrypt themselves. Changing the
cryptographic keys becomes a very efficient method of complete data erasure as the keys cannot
be guesses easily.
Importance of good data erasure methods
Breach of data – Technology changes rapidly. There is need for newer models of computers and
electronics daily. This has led to refurbished asset sale. This is the sale of previously owned
computers or mobile phones. Since they are not new, it means that they contain the user’s data
that may be sensitive. This means that complete data erasure of the owner’s data is important, so
that the new owner will not access the previous sensitive data. An organization may be willing to
sell their computers for upgrade purposes. This means that they must erase the data completely
before sale. If they do not take into consideration the complete erasure process, their data may
7 Qing and Sihan. Information and communications security (Springer 2005)

fall into wrong hands. Issues like identity theft, data compromise, financial impacts and loss of
an organization’s reputation may occur.
Complying with the law – Tryfonas8 says that there are strict laws by the government that force
all organizations to comply with the standards of data privacy. They make the organization
secure their data and the government’s data. The government may impose fines may on those
organizations that do not practice safe data disposal.
Environment issues - Degaussing or physical destruction of the storage devices is a data disposal
method that is not environmental friendly. The electronic waste is one of the environmental
hazards. Usage of software methods however, do not destroy the storage media and hence. One
should use them whenever possible. In case of degaussing, one should make sure they recycle
the storage devices like hard disks.
Limitations of software based methods
The data erasure software may not completely wipe some types of storage devices like solid state
drives and Universal serial buses. This is because they remain with data of which the software
cannot delete it normally. One can still recover the data from the chips of the USB devices inside
the drives. Drives that have some bad sectors may not be erasable through overwriting. The
software cannot overwrite bad sectors of the drives. Malicious code can also compromise the
data deletion process.
The Erasure process
8 Tryfonas and Theodore, Human aspects of information security, privacy and trust (Springer
2017)
an organization’s reputation may occur.
Complying with the law – Tryfonas8 says that there are strict laws by the government that force
all organizations to comply with the standards of data privacy. They make the organization
secure their data and the government’s data. The government may impose fines may on those
organizations that do not practice safe data disposal.
Environment issues - Degaussing or physical destruction of the storage devices is a data disposal
method that is not environmental friendly. The electronic waste is one of the environmental
hazards. Usage of software methods however, do not destroy the storage media and hence. One
should use them whenever possible. In case of degaussing, one should make sure they recycle
the storage devices like hard disks.
Limitations of software based methods
The data erasure software may not completely wipe some types of storage devices like solid state
drives and Universal serial buses. This is because they remain with data of which the software
cannot delete it normally. One can still recover the data from the chips of the USB devices inside
the drives. Drives that have some bad sectors may not be erasable through overwriting. The
software cannot overwrite bad sectors of the drives. Malicious code can also compromise the
data deletion process.
The Erasure process
8 Tryfonas and Theodore, Human aspects of information security, privacy and trust (Springer
2017)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Software that perform erasure do so by writing a combination of zeros and ones or alpha numeric
characters to each sector of the hard disk. The software first scans the sectors of the hard drive
for any errors and abnormalities before the data erasure can begin. This is pre testing. This is to
determine that the drive is in a good working condition.
There are many software programs that offer data erasure. However, only those that erase the full
disk have full security. The software chosen for the process should be able to access all the areas
of the drive. Such areas include hidden areas, Host protected areas and remapped sectors. This
makes sure that no data remains intact. Lewis9 suggests that the software should also be able to
bypass operating systems. This is because most operating systems cannot allow any software to
delete its system files.
Data erasure in a network is possible. Chebbi10 says that the first step is to identify the target
computers in a network. Data erasure software based on the Linux operating system offer server
storage network environments that support the process. DOS based programs may fail in
detecting the computers in the network.
Conclusion
9 Lewis, and others, The effect of encryption on lawful access to communications and data
(Center for Strategic & International Studies Rowman & Littlefield 2017)
10 Chebbi, Chebbi, Advanced infrastructure penetration testing : defend your systems from
methodized and proficient attackers (Packt Publishing 2018)
characters to each sector of the hard disk. The software first scans the sectors of the hard drive
for any errors and abnormalities before the data erasure can begin. This is pre testing. This is to
determine that the drive is in a good working condition.
There are many software programs that offer data erasure. However, only those that erase the full
disk have full security. The software chosen for the process should be able to access all the areas
of the drive. Such areas include hidden areas, Host protected areas and remapped sectors. This
makes sure that no data remains intact. Lewis9 suggests that the software should also be able to
bypass operating systems. This is because most operating systems cannot allow any software to
delete its system files.
Data erasure in a network is possible. Chebbi10 says that the first step is to identify the target
computers in a network. Data erasure software based on the Linux operating system offer server
storage network environments that support the process. DOS based programs may fail in
detecting the computers in the network.
Conclusion
9 Lewis, and others, The effect of encryption on lawful access to communications and data
(Center for Strategic & International Studies Rowman & Littlefield 2017)
10 Chebbi, Chebbi, Advanced infrastructure penetration testing : defend your systems from
methodized and proficient attackers (Packt Publishing 2018)

It is clear that the computer does not delete the data fully when one uses the delete functionality
of the operating system. Data is still present until the computer writes new data over the initial
data. The operating systems use pointers to show the location of a file on the storage device.
When one deletes the data, the pointers stop pointing to the data, making it seem like the data
does not exist.
One can delete data safely by using data deletion software. The software overwrites the data in
question with a stream of ones and zeros, making the data go away completely. Some software
overwrite twice, making sure that no one can recover the data.
of the operating system. Data is still present until the computer writes new data over the initial
data. The operating systems use pointers to show the location of a file on the storage device.
When one deletes the data, the pointers stop pointing to the data, making it seem like the data
does not exist.
One can delete data safely by using data deletion software. The software overwrites the data in
question with a stream of ones and zeros, making the data go away completely. Some software
overwrite twice, making sure that no one can recover the data.

Question 3: Encrypted emails
Introduction
The word email denotes “Electronic mail”. It one of the most helpful technologies in the
communication world. Organizations as well as personal users use them. The internet allows
transfer of emails. According to Lin11, this makes them vulnerable to intrusion by hackers and
unauthorized people. Organizations have to secure their emails and that gave rise to email
encryption. It is the encryption of email messages to prevent the content of the email from being
read or accessed by people other than the intended recipients. However, malicious hackers can
extract emails. This is because they are public. Encryption is disguising the contents of the email
messages. The encryption methods are suitable for small businesses as well as individuals and
large organizations, as suggested by Pardo12.
The email threat
Emails act on a point to point communication. For example, if user 1 sends an Email to user2,
the user1’s computer connects with user2’s computer virtually. That is known as
synchronization. SMTP (Simple mail transfer protocol) is a means of transferring messages
between the two computers. If user2 cannot receive the message at the moment, the message is
stored in a server called Post office protocol server. When user2 is online, they can download the
message from the server and read it. The message belongs to user2 but since it is on the server,
the public can view it. When transmitting the files over the internet, hackers can be intercept
them. If they are, encrypting the emails will hide the information in the emails.
11 Lin, Xiaodong, and others, Security and privacy in communication networks (Springer 2018)
12 Pardo, José L. Introduction to cryptography with Maple (Springer-Verlag 2013)
Introduction
The word email denotes “Electronic mail”. It one of the most helpful technologies in the
communication world. Organizations as well as personal users use them. The internet allows
transfer of emails. According to Lin11, this makes them vulnerable to intrusion by hackers and
unauthorized people. Organizations have to secure their emails and that gave rise to email
encryption. It is the encryption of email messages to prevent the content of the email from being
read or accessed by people other than the intended recipients. However, malicious hackers can
extract emails. This is because they are public. Encryption is disguising the contents of the email
messages. The encryption methods are suitable for small businesses as well as individuals and
large organizations, as suggested by Pardo12.
The email threat
Emails act on a point to point communication. For example, if user 1 sends an Email to user2,
the user1’s computer connects with user2’s computer virtually. That is known as
synchronization. SMTP (Simple mail transfer protocol) is a means of transferring messages
between the two computers. If user2 cannot receive the message at the moment, the message is
stored in a server called Post office protocol server. When user2 is online, they can download the
message from the server and read it. The message belongs to user2 but since it is on the server,
the public can view it. When transmitting the files over the internet, hackers can be intercept
them. If they are, encrypting the emails will hide the information in the emails.
11 Lin, Xiaodong, and others, Security and privacy in communication networks (Springer 2018)
12 Pardo, José L. Introduction to cryptography with Maple (Springer-Verlag 2013)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

How email works
Loshin13 defines protocols as a set of rules and standards in a network that determine how
communication happens between two processes. In Email, there are the most commonly used
protocols. It is essential to understand them so that one can understand email encryption, as the
protocols facilitate the transfer of the encrypted mail from computer to computer.
The protocols include:
1) IMAP
2) POP
3) SMTP
IMAP
Lucas14 defines it as the Internet Mail Access Protocol. The protocol is useful for receiving email
messages. It works in such a way that the email messages received are not stored on a local
computer. They are stored on the server and one can retrieve them anytime, saving the local
computer’s memory.
POP
It is a protocol called Post Office. It is useful email reception also. POP differs from IMAP in
that the former sends the email data into the user’s computer, removing the email from the
server, increasing server memory.
SMPT
It is the Simple Mail Transfer Protocol. It is useful for sending emails.
13 Loshin, Peter, Simple steps to data encryption : a practical guide to secure computing (Elsevier Science 2013)
14 Lucas, W Michael, PGP & GPG : email for the practical paranoid (No Starch Press 2006)
Loshin13 defines protocols as a set of rules and standards in a network that determine how
communication happens between two processes. In Email, there are the most commonly used
protocols. It is essential to understand them so that one can understand email encryption, as the
protocols facilitate the transfer of the encrypted mail from computer to computer.
The protocols include:
1) IMAP
2) POP
3) SMTP
IMAP
Lucas14 defines it as the Internet Mail Access Protocol. The protocol is useful for receiving email
messages. It works in such a way that the email messages received are not stored on a local
computer. They are stored on the server and one can retrieve them anytime, saving the local
computer’s memory.
POP
It is a protocol called Post Office. It is useful email reception also. POP differs from IMAP in
that the former sends the email data into the user’s computer, removing the email from the
server, increasing server memory.
SMPT
It is the Simple Mail Transfer Protocol. It is useful for sending emails.
13 Loshin, Peter, Simple steps to data encryption : a practical guide to secure computing (Elsevier Science 2013)
14 Lucas, W Michael, PGP & GPG : email for the practical paranoid (No Starch Press 2006)

For a successful email transfer to occur, there needs to be the sender, the receiver, the protocol
and the DNS. DNS (Domain name system) converts the names of the recipients into IP addresses
and also the other way. The senders and receivers must do so through mail servers. They are
computer systems that receive and send emails. Orman15 suggests that MTAs are those servers
used to send emails and MDAs are those used to receive emails.
The email sender uses an application tailored for sending emails to send an email to a particular
email address. Once the user sends the email, it goes though the MTA. The transfer is made
through the SMTP protocol.
Email encryption
Avoine16 says that encryption of emails involve preventing other people than the original
recipient to view the content. Encryption can happen by each user having two keys: public and
private key. With their public key, anyone can send messages to the user, but the only the user
can decrypt the messages using their private key. One can use certain protocols to enable secure
communication of encrypted mails. They include Transport level and end to end encryption
solutions.
Transport level encryption
STARTTLS is a secure socket layer that exists over plaintext message communication,
according to Martin17. It gives a chance to email servers, allowing them to encrypt their plaintext
15 Orman and Hilarie, Encrypted email : the history and technology of message privacy (Springer
2015)
16 Avoine and others, Lightweight Cryptography for Security and Privacy (Heidelberg: Springer
2013)
and the DNS. DNS (Domain name system) converts the names of the recipients into IP addresses
and also the other way. The senders and receivers must do so through mail servers. They are
computer systems that receive and send emails. Orman15 suggests that MTAs are those servers
used to send emails and MDAs are those used to receive emails.
The email sender uses an application tailored for sending emails to send an email to a particular
email address. Once the user sends the email, it goes though the MTA. The transfer is made
through the SMTP protocol.
Email encryption
Avoine16 says that encryption of emails involve preventing other people than the original
recipient to view the content. Encryption can happen by each user having two keys: public and
private key. With their public key, anyone can send messages to the user, but the only the user
can decrypt the messages using their private key. One can use certain protocols to enable secure
communication of encrypted mails. They include Transport level and end to end encryption
solutions.
Transport level encryption
STARTTLS is a secure socket layer that exists over plaintext message communication,
according to Martin17. It gives a chance to email servers, allowing them to encrypt their plaintext
15 Orman and Hilarie, Encrypted email : the history and technology of message privacy (Springer
2015)
16 Avoine and others, Lightweight Cryptography for Security and Privacy (Heidelberg: Springer
2013)

messages. The servers on both sides should support the encryption. This prevents snoopers from
sniffing into the contents of the email messages.
The encryption does not happen between the recipient and the sender. It happens between the
SMTP relays, as suggested by Nagelhout18. The relays are the only ones that can read or alter the
messages. An advantage of the transport level encryption is that users do not have to change
anything. They do not need to perform any actions. The encryption happens as soon as the sender
sends the message, as suggested by Davies19. This makes it possible to run scanners and spam
filter on the emails by the receiver, since the receiver does not need to cooperate with the sender
in order to view the messages. It has a disadvantage however, that anyone on the receiving
organization’s side can read and alter the messages if no further steps occur.
End to end encryption
In this type of encryption, data encryption and decryption happens only at each end, according to
Kohno20. This means that when a sender sends the message, the computer encrypts it before
sending. Email sending services will not be able to view the content of the email message. The
receiving computer the decrypts the message at the receiving point.
Some protocols that support end to end encryption are
1) Bitmessage
17 Martin and M Keith, Everyday cryptography : fundamental principles and applications
(Oxford University Press 2017)
18 Nagelhout, Ryan, Digital era encryption and decryption (Rosen Publishing 2017)
19 Davies and A Joshua, Implementing SSL/TLS using cryptography and PKI (Wiley John Wiley
distributor 2011)
20 Kohno, Tadayoshi, Niels Ferguson, and Bruce Schneier, Cryptography engineering : design
principles and practical applications ( Wiley Pub Inc 2010)
sniffing into the contents of the email messages.
The encryption does not happen between the recipient and the sender. It happens between the
SMTP relays, as suggested by Nagelhout18. The relays are the only ones that can read or alter the
messages. An advantage of the transport level encryption is that users do not have to change
anything. They do not need to perform any actions. The encryption happens as soon as the sender
sends the message, as suggested by Davies19. This makes it possible to run scanners and spam
filter on the emails by the receiver, since the receiver does not need to cooperate with the sender
in order to view the messages. It has a disadvantage however, that anyone on the receiving
organization’s side can read and alter the messages if no further steps occur.
End to end encryption
In this type of encryption, data encryption and decryption happens only at each end, according to
Kohno20. This means that when a sender sends the message, the computer encrypts it before
sending. Email sending services will not be able to view the content of the email message. The
receiving computer the decrypts the message at the receiving point.
Some protocols that support end to end encryption are
1) Bitmessage
17 Martin and M Keith, Everyday cryptography : fundamental principles and applications
(Oxford University Press 2017)
18 Nagelhout, Ryan, Digital era encryption and decryption (Rosen Publishing 2017)
19 Davies and A Joshua, Implementing SSL/TLS using cryptography and PKI (Wiley John Wiley
distributor 2011)
20 Kohno, Tadayoshi, Niels Ferguson, and Bruce Schneier, Cryptography engineering : design
principles and practical applications ( Wiley Pub Inc 2010)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2) GPG (GNU privacy guard)
3) Pretty good privacy
4) S/MIME
Open PGP, as suggested by Garfinkel21, is an example of a good encryption protocol. According
to Kotulski22, it allows users to encrypt the contents of an email by the use of the recipient’s key
that is public. It uses public key cryptography that involves associating every email address with
a private and public key.
The users do not need server support to encrypt data. The protocol requires email users to create
key pairs and avail them widely. The protocol protects the contents of the email only, not the
metadata, according to Stallings23. One can still know who sent the message.
This method of encryption ensures that the emails are secure from intrusion. Only the recipient
can view the contents of emails and attachments. Even hackers who eavesdrop in a network
cannot hold the data transfer.
Current research areas
S/MIME and OpenPGP are areas in which researchers are currently working on. They have
found errors and vulnerabilities on the protocols. They have described the vulnerability as
EFAIL. They have stated that the vulnerability can cause encrypted data to be exposed. This
21 Garfinkel and Simson, PGP: pretty good privacy (O'Reilly & Associates 1995)
22 Kotulski, Zbigniew, Bogdan Ksie̜żopolski, and Katarzyna Mazur, Cryptography and security
systems (Springer 2014)
23 Stallings and William. Cryptography and network security : principles and practice. (Prentice
Hall 2011)
3) Pretty good privacy
4) S/MIME
Open PGP, as suggested by Garfinkel21, is an example of a good encryption protocol. According
to Kotulski22, it allows users to encrypt the contents of an email by the use of the recipient’s key
that is public. It uses public key cryptography that involves associating every email address with
a private and public key.
The users do not need server support to encrypt data. The protocol requires email users to create
key pairs and avail them widely. The protocol protects the contents of the email only, not the
metadata, according to Stallings23. One can still know who sent the message.
This method of encryption ensures that the emails are secure from intrusion. Only the recipient
can view the contents of emails and attachments. Even hackers who eavesdrop in a network
cannot hold the data transfer.
Current research areas
S/MIME and OpenPGP are areas in which researchers are currently working on. They have
found errors and vulnerabilities on the protocols. They have described the vulnerability as
EFAIL. They have stated that the vulnerability can cause encrypted data to be exposed. This
21 Garfinkel and Simson, PGP: pretty good privacy (O'Reilly & Associates 1995)
22 Kotulski, Zbigniew, Bogdan Ksie̜żopolski, and Katarzyna Mazur, Cryptography and security
systems (Springer 2014)
23 Stallings and William. Cryptography and network security : principles and practice. (Prentice
Hall 2011)

includes emails that the users had sent in the past. The vulnerability affects those clients that use
the S/MIME and OpenPGP protocols, according to Nemati24.
This shows how important good email security practices are. Users should create strong
passwords that are combinations of digits, alphanumeric characters and characters. Two factor
authentication is also a good way of improving email security. Screening of locations and
freezing accounts that have failed authentication also serves as a good way of preventing email
attacks.
Conclusion
Security of emails is important in an organization. This is why the organization should secure the
sensitive data transmitted through emails. Methods of encryption such as end to end and
transport layer encryption exist. In end to end encryption, the computer encrypts the message at
the sending point and decrypts it at the receiving point. This makes it safe from man in the
middle attack. The transport layer encrypts the data at the relays and not at the user’s ends. This
makes it insecure as the relays can view and alter the message. One should take encryption
strategies into consideration to secure email messaging and preventing wrong hands from getting
access to the data. The email protocols such as POP and IMAP as well as SMTP are useful in
email data transfer. When combined with the encryption methods, they become effective in
email data security.
24 Nemati, Hamid R., and Li Yang, Applied cryptography for cyber security and defense :
information encryption and cyphering (Information Science Reference 2011)
the S/MIME and OpenPGP protocols, according to Nemati24.
This shows how important good email security practices are. Users should create strong
passwords that are combinations of digits, alphanumeric characters and characters. Two factor
authentication is also a good way of improving email security. Screening of locations and
freezing accounts that have failed authentication also serves as a good way of preventing email
attacks.
Conclusion
Security of emails is important in an organization. This is why the organization should secure the
sensitive data transmitted through emails. Methods of encryption such as end to end and
transport layer encryption exist. In end to end encryption, the computer encrypts the message at
the sending point and decrypts it at the receiving point. This makes it safe from man in the
middle attack. The transport layer encrypts the data at the relays and not at the user’s ends. This
makes it insecure as the relays can view and alter the message. One should take encryption
strategies into consideration to secure email messaging and preventing wrong hands from getting
access to the data. The email protocols such as POP and IMAP as well as SMTP are useful in
email data transfer. When combined with the encryption methods, they become effective in
email data security.
24 Nemati, Hamid R., and Li Yang, Applied cryptography for cyber security and defense :
information encryption and cyphering (Information Science Reference 2011)
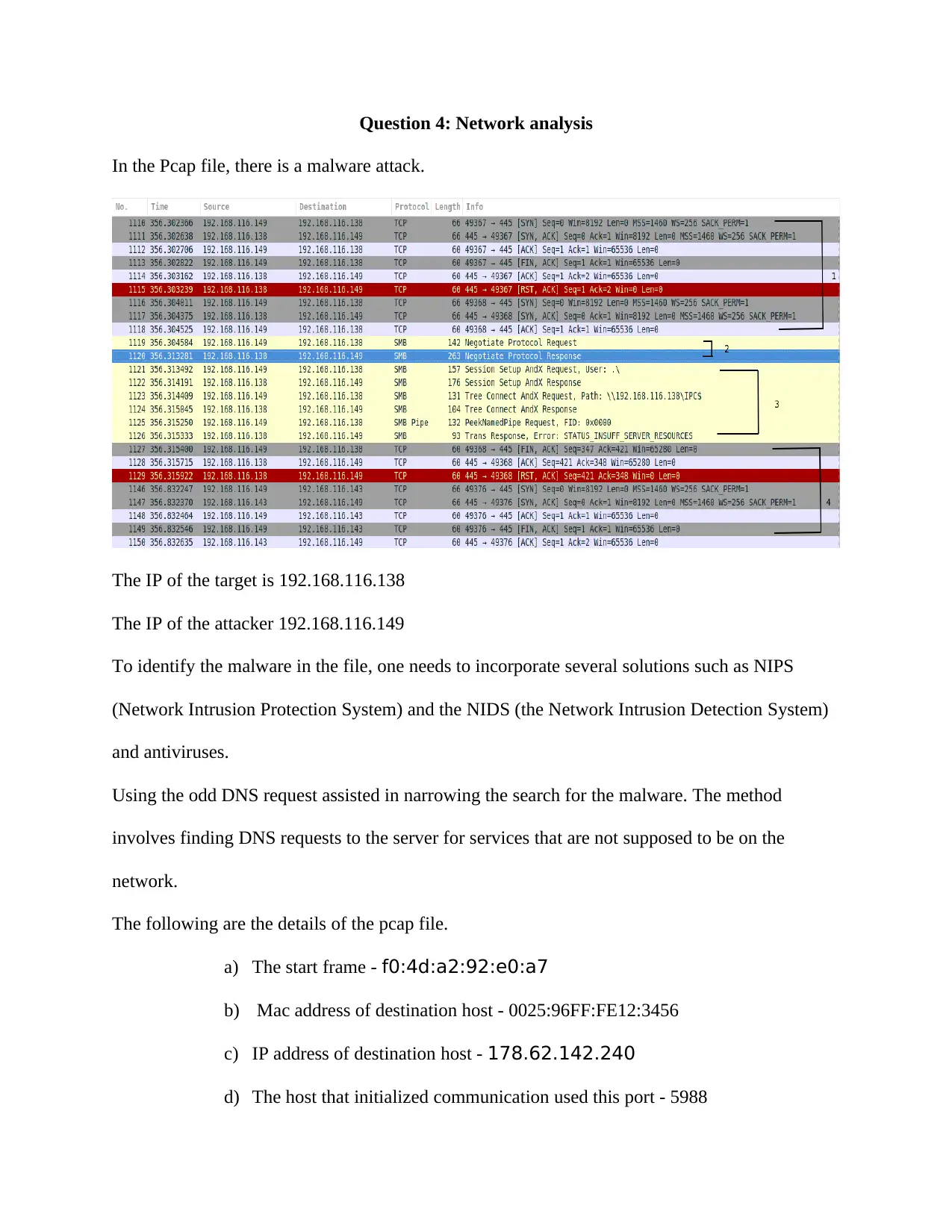
Question 4: Network analysis
In the Pcap file, there is a malware attack.
The IP of the target is 192.168.116.138
The IP of the attacker 192.168.116.149
To identify the malware in the file, one needs to incorporate several solutions such as NIPS
(Network Intrusion Protection System) and the NIDS (the Network Intrusion Detection System)
and antiviruses.
Using the odd DNS request assisted in narrowing the search for the malware. The method
involves finding DNS requests to the server for services that are not supposed to be on the
network.
The following are the details of the pcap file.
a) The start frame - f0:4d:a2:92:e0:a7
b) Mac address of destination host - 0025:96FF:FE12:3456
c) IP address of destination host - 178.62.142.240
d) The host that initialized communication used this port - 5988
In the Pcap file, there is a malware attack.
The IP of the target is 192.168.116.138
The IP of the attacker 192.168.116.149
To identify the malware in the file, one needs to incorporate several solutions such as NIPS
(Network Intrusion Protection System) and the NIDS (the Network Intrusion Detection System)
and antiviruses.
Using the odd DNS request assisted in narrowing the search for the malware. The method
involves finding DNS requests to the server for services that are not supposed to be on the
network.
The following are the details of the pcap file.
a) The start frame - f0:4d:a2:92:e0:a7
b) Mac address of destination host - 0025:96FF:FE12:3456
c) IP address of destination host - 178.62.142.240
d) The host that initialized communication used this port - 5988
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

e) The host at the destination used this port - 546

BIBLIOGRAPHY
Aumasson, Serious cryptography : a practical introduction to modern encryption (No Starch
press 2018)
Avoine and others, Lightweight Cryptography for Security and Privacy (Heidelberg: Springer
2013)
Chebbi, Chebbi, Advanced infrastructure penetration testing : defend your systems from
methodized and proficient attackers (Packt Publishing 2018)
Davies and A Joshua, Implementing SSL/TLS using cryptography and PKI (Wiley John Wiley
distributor 2011)
Eisenbarth, Thomas and Erdinç Ö ztürk, Lightweight cryptography for security and privacy
(Springer 2015)
Foley, Simon N., Dieter Gollmann, and Einar Snekkenes. Computer security -- ESORICS 2017
(Springer 2017)
Garfinkel and Simson, PGP: pretty good privacy (O'Reilly & Associates 1995)
K Kale, S. C. Mehrotra, and R. R. Manza, Advances in computer vision and information
technology (I.K. International Pub. House 2008)
Aumasson, Serious cryptography : a practical introduction to modern encryption (No Starch
press 2018)
Avoine and others, Lightweight Cryptography for Security and Privacy (Heidelberg: Springer
2013)
Chebbi, Chebbi, Advanced infrastructure penetration testing : defend your systems from
methodized and proficient attackers (Packt Publishing 2018)
Davies and A Joshua, Implementing SSL/TLS using cryptography and PKI (Wiley John Wiley
distributor 2011)
Eisenbarth, Thomas and Erdinç Ö ztürk, Lightweight cryptography for security and privacy
(Springer 2015)
Foley, Simon N., Dieter Gollmann, and Einar Snekkenes. Computer security -- ESORICS 2017
(Springer 2017)
Garfinkel and Simson, PGP: pretty good privacy (O'Reilly & Associates 1995)
K Kale, S. C. Mehrotra, and R. R. Manza, Advances in computer vision and information
technology (I.K. International Pub. House 2008)

Kohno, Tadayoshi, Niels Ferguson, and Bruce Schneier, Cryptography engineering : design
principles and practical applications ( Wiley Pub Inc 2010)
Kotulski, Zbigniew, Bogdan Ksie̜żopolski, and Katarzyna Mazur, Cryptography and security
systems (Springer 2014)
Krawczyk, Hugo, Public-key cryptography (Springer 2014)
Lewis, and others, The effect of encryption on lawful access to communications and data (Center
for Strategic & International Studies Rowman & Littlefield 2017)
Lin, Xiaodong, and others, Security and privacy in communication networks (Springer 2018)
Loshin, Peter, Simple steps to data encryption : a practical guide to secure computing (Elsevier
Science 2013)
Lucas, W Michael, PGP & GPG : email for the practical paranoid (No Starch Press 2006)
Martin and M Keith, Everyday cryptography : fundamental principles and applications (Oxford
University Press 2017)
Mauri, Jaime and others, Security in computing and communications (Springer 2014)
Nagelhout, Ryan, Digital era encryption and decryption (Rosen Publishing 2017)
principles and practical applications ( Wiley Pub Inc 2010)
Kotulski, Zbigniew, Bogdan Ksie̜żopolski, and Katarzyna Mazur, Cryptography and security
systems (Springer 2014)
Krawczyk, Hugo, Public-key cryptography (Springer 2014)
Lewis, and others, The effect of encryption on lawful access to communications and data (Center
for Strategic & International Studies Rowman & Littlefield 2017)
Lin, Xiaodong, and others, Security and privacy in communication networks (Springer 2018)
Loshin, Peter, Simple steps to data encryption : a practical guide to secure computing (Elsevier
Science 2013)
Lucas, W Michael, PGP & GPG : email for the practical paranoid (No Starch Press 2006)
Martin and M Keith, Everyday cryptography : fundamental principles and applications (Oxford
University Press 2017)
Mauri, Jaime and others, Security in computing and communications (Springer 2014)
Nagelhout, Ryan, Digital era encryption and decryption (Rosen Publishing 2017)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Nemati, Hamid R., and Li Yang, Applied cryptography for cyber security and defense :
information encryption and cyphering (Information Science Reference 2011)
Orman and Hilarie, Encrypted email : the history and technology of message privacy (Springer
2015)
Pardo, José L. Introduction to cryptography with Maple (Springer-Verlag 2013)
Qing and Sihan. Information and communications security (Springer 2005)
Stallings and William. Cryptography and network security : principles and practice. (Prentice
Hall 2011)
Tryfonas and Theodore, Human aspects of information security, privacy and trust (Springer
2017)
information encryption and cyphering (Information Science Reference 2011)
Orman and Hilarie, Encrypted email : the history and technology of message privacy (Springer
2015)
Pardo, José L. Introduction to cryptography with Maple (Springer-Verlag 2013)
Qing and Sihan. Information and communications security (Springer 2005)
Stallings and William. Cryptography and network security : principles and practice. (Prentice
Hall 2011)
Tryfonas and Theodore, Human aspects of information security, privacy and trust (Springer
2017)
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





