NIT6130: Data Mining Methodology for Fraud and Theft Detection
VerifiedAdded on 2023/06/04
|13
|3105
|190
Report
AI Summary
This assignment provides a detailed methodology for fraud and theft detection using data mining techniques. It begins by stating the research problem, focusing on identity theft and cloning, and reorganizes collected literature based on sub-problems like skimming and financial fraud. The assignment then compares qualitative and quantitative methodologies, opting for a qualitative approach to leverage secondary data sources. Existing methodologies are reviewed, focusing on identity theft and cloning, and analyzed using the Caesar Cipher example. The relevance of the research problem is emphasized, highlighting the increasing prevalence of online data theft and the importance of fraud detection techniques. A proposed methodology is identified and justified, outlining the benefits and limitations of qualitative research. Finally, a framework is presented to illustrate the process of fraud and theft detection through data mining, including encryption, data transfer, and decryption.

NIT6130 INTRODUCTION TO RESEARCH
ASSIGNMENT 3 – METHODOLOGY
by
Rachid Hamadi
Student ID: 30099999
ASSIGNMENT 3 – METHODOLOGY
by
Rachid Hamadi
Student ID: 30099999
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Table of Contents...............................................................................................................................ii
Chapter 1 Methodology......................................................................................................................1
1.1 Research Problem and Reorganized Collected Literature.........................................................1
1.1.1 Research Problem Statement.............................................................................................1
1.1.2 Reorganized Collected Literature......................................................................................2
1.2 Types of Methodology.............................................................................................................3
1.2.1 Qualitative and Quantitative Methodologies.....................................................................3
1.2.2 Type of Chosen Methodology...........................................................................................3
1.3 Review of the Existing Methodologies.....................................................................................4
1.3.1 Selected Sub-Problem.......................................................................................................4
1.3.2 Analysis of the Selected Methodologies............................................................................4
1.3.3 Relevance of the Research Problem..................................................................................6
1.3.4 Summary of the Reviewed Methodologies........................................................................6
1.4 Proposed Methodology.............................................................................................................6
1.4.1 Identification and Justification..........................................................................................6
1.4.2 Benefits and Limitations....................................................................................................7
1.4.3 Framework and Explanation..............................................................................................8
List of References............................................................................................................................10
ii
Table of Contents...............................................................................................................................ii
Chapter 1 Methodology......................................................................................................................1
1.1 Research Problem and Reorganized Collected Literature.........................................................1
1.1.1 Research Problem Statement.............................................................................................1
1.1.2 Reorganized Collected Literature......................................................................................2
1.2 Types of Methodology.............................................................................................................3
1.2.1 Qualitative and Quantitative Methodologies.....................................................................3
1.2.2 Type of Chosen Methodology...........................................................................................3
1.3 Review of the Existing Methodologies.....................................................................................4
1.3.1 Selected Sub-Problem.......................................................................................................4
1.3.2 Analysis of the Selected Methodologies............................................................................4
1.3.3 Relevance of the Research Problem..................................................................................6
1.3.4 Summary of the Reviewed Methodologies........................................................................6
1.4 Proposed Methodology.............................................................................................................6
1.4.1 Identification and Justification..........................................................................................6
1.4.2 Benefits and Limitations....................................................................................................7
1.4.3 Framework and Explanation..............................................................................................8
List of References............................................................................................................................10
ii

Chapter 1
Methodology
This assignment focuses on the methodology of fraud and theft detection using data mining.
Fraud has been one of the greatest challenges for business organizations. This assignment deals
with the methodology followed in the study of fraud detection by data mining process.
1.1 Research Problem and Reorganized Collected Literature
1.1.1 Research Problem Statement
The enhancement of the technology have been helping in maintaining a proper data transfer
over the network. Identity crime has been one if the major fraud and theft cases in the
organizations. Fraud cases have been increasing all over the world due to the enhancement of
technology. The negative use of the technology have been creating chances for hackers to
breach into various networks for taking data form it (Odetola et al. 2018). The data theft have
been increasing over the network. Cloning has been another problem faced by the organizations
and users. These acts have been performed in credit cards and passports cloning. Data and
information regarding credit card credentials and fake passports have been created in the
market. Fraud behavior of any person need to be detected in the organizations. Fraud has been
an intentional theft act performed by any person in an organization or in the society. It has been
referred to abuse of profit of an organization in legal platform.
1
Methodology
This assignment focuses on the methodology of fraud and theft detection using data mining.
Fraud has been one of the greatest challenges for business organizations. This assignment deals
with the methodology followed in the study of fraud detection by data mining process.
1.1 Research Problem and Reorganized Collected Literature
1.1.1 Research Problem Statement
The enhancement of the technology have been helping in maintaining a proper data transfer
over the network. Identity crime has been one if the major fraud and theft cases in the
organizations. Fraud cases have been increasing all over the world due to the enhancement of
technology. The negative use of the technology have been creating chances for hackers to
breach into various networks for taking data form it (Odetola et al. 2018). The data theft have
been increasing over the network. Cloning has been another problem faced by the organizations
and users. These acts have been performed in credit cards and passports cloning. Data and
information regarding credit card credentials and fake passports have been created in the
market. Fraud behavior of any person need to be detected in the organizations. Fraud has been
an intentional theft act performed by any person in an organization or in the society. It has been
referred to abuse of profit of an organization in legal platform.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
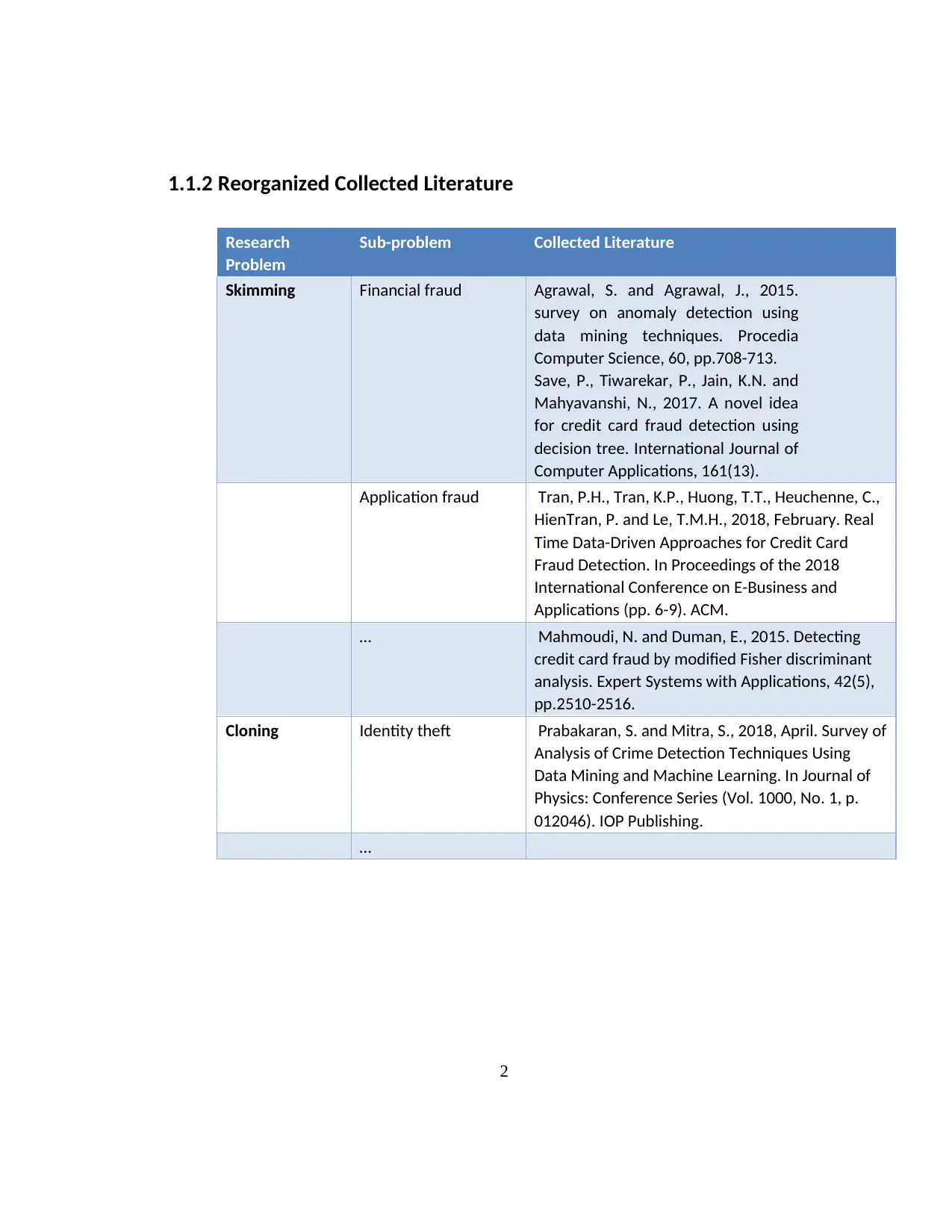
1.1.2 Reorganized Collected Literature
Research
Problem
Sub-problem Collected Literature
Skimming Financial fraud Agrawal, S. and Agrawal, J., 2015.
survey on anomaly detection using
data mining techniques. Procedia
Computer Science, 60, pp.708-713.
Save, P., Tiwarekar, P., Jain, K.N. and
Mahyavanshi, N., 2017. A novel idea
for credit card fraud detection using
decision tree. International Journal of
Computer Applications, 161(13).
Application fraud Tran, P.H., Tran, K.P., Huong, T.T., Heuchenne, C.,
HienTran, P. and Le, T.M.H., 2018, February. Real
Time Data-Driven Approaches for Credit Card
Fraud Detection. In Proceedings of the 2018
International Conference on E-Business and
Applications (pp. 6-9). ACM.
… Mahmoudi, N. and Duman, E., 2015. Detecting
credit card fraud by modified Fisher discriminant
analysis. Expert Systems with Applications, 42(5),
pp.2510-2516.
Cloning Identity theft Prabakaran, S. and Mitra, S., 2018, April. Survey of
Analysis of Crime Detection Techniques Using
Data Mining and Machine Learning. In Journal of
Physics: Conference Series (Vol. 1000, No. 1, p.
012046). IOP Publishing.
…
2
Research
Problem
Sub-problem Collected Literature
Skimming Financial fraud Agrawal, S. and Agrawal, J., 2015.
survey on anomaly detection using
data mining techniques. Procedia
Computer Science, 60, pp.708-713.
Save, P., Tiwarekar, P., Jain, K.N. and
Mahyavanshi, N., 2017. A novel idea
for credit card fraud detection using
decision tree. International Journal of
Computer Applications, 161(13).
Application fraud Tran, P.H., Tran, K.P., Huong, T.T., Heuchenne, C.,
HienTran, P. and Le, T.M.H., 2018, February. Real
Time Data-Driven Approaches for Credit Card
Fraud Detection. In Proceedings of the 2018
International Conference on E-Business and
Applications (pp. 6-9). ACM.
… Mahmoudi, N. and Duman, E., 2015. Detecting
credit card fraud by modified Fisher discriminant
analysis. Expert Systems with Applications, 42(5),
pp.2510-2516.
Cloning Identity theft Prabakaran, S. and Mitra, S., 2018, April. Survey of
Analysis of Crime Detection Techniques Using
Data Mining and Machine Learning. In Journal of
Physics: Conference Series (Vol. 1000, No. 1, p.
012046). IOP Publishing.
…
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.2 Types of Methodology
1.2.1 Qualitative and Quantitative Methodologies
Quantitative and Qualitative strategies are the two kinds of procedures in the research.
Qualitative research systems centers on the nature of things and parts of information.
Qualitative research help in investigating associations with the segments of research. Qualitative
research centers on the secondary methodologies of the information accumulation (Agrawal
and Agrawal 2015). Information gathering should be finished utilizing the secondary sources
including on the web diaries, articles and books (Zissis and Lekkas 2012). The sample size of the
Qualitative research should be high to accumulate more pertinent data with respect to the
research theme. The example should be enormous that hemps in guaranteeing consideration of
all discernments incorporated into the research theme. The utilization of online review helps in
gathering enormous measure of information and data with respect to the subject (Jokar,
Arianpoo and Leung 2016). Irregular examining strategy has been utilized for choosing taking
part for the study in quantitative methodology. Measurable strategies are utilized in
investigating quantitative information in a research.
1.2.2 Type of Chosen Methodology
In this research, the researcher has chosen qualitative research approach. The qualitative
research approach manages the secondary wellsprings of information and data identified with
the fraud detection techniques using data mining process (Save, Tiwarekar Jain and
Mahyavanshi 2017). The utilization of qualitative research strategies have been helping in
keeping up a sharp way to deal with the points of interest of the fraud detections in
organizations. The qualitative methodology has helped in gathering information from online
diaries and articles.
3
1.2.1 Qualitative and Quantitative Methodologies
Quantitative and Qualitative strategies are the two kinds of procedures in the research.
Qualitative research systems centers on the nature of things and parts of information.
Qualitative research help in investigating associations with the segments of research. Qualitative
research centers on the secondary methodologies of the information accumulation (Agrawal
and Agrawal 2015). Information gathering should be finished utilizing the secondary sources
including on the web diaries, articles and books (Zissis and Lekkas 2012). The sample size of the
Qualitative research should be high to accumulate more pertinent data with respect to the
research theme. The example should be enormous that hemps in guaranteeing consideration of
all discernments incorporated into the research theme. The utilization of online review helps in
gathering enormous measure of information and data with respect to the subject (Jokar,
Arianpoo and Leung 2016). Irregular examining strategy has been utilized for choosing taking
part for the study in quantitative methodology. Measurable strategies are utilized in
investigating quantitative information in a research.
1.2.2 Type of Chosen Methodology
In this research, the researcher has chosen qualitative research approach. The qualitative
research approach manages the secondary wellsprings of information and data identified with
the fraud detection techniques using data mining process (Save, Tiwarekar Jain and
Mahyavanshi 2017). The utilization of qualitative research strategies have been helping in
keeping up a sharp way to deal with the points of interest of the fraud detections in
organizations. The qualitative methodology has helped in gathering information from online
diaries and articles.
3

1.3 Review of the Existing Methodologies
1.3.1 Selected Sub-Problem
The research has focused on the identity theft using cloning method. Information started from
Qualitative data has been kept up and checked appropriately. The legitimacy and dependability
factors in information accumulation should be finished. However, this compose information are
taken from distributed journals and articles. Qualitative research helps in getting top to bottom
points of interest of the research theme including fraud detection (Jain 2017). The validity of
data collected has been properly maintained. Data has been collected from secondary sources
including books, journals and articles. Journals have been taken from 2012 published journals.
The view of the members have been thought about appropriately. This sort of methodology
causes in comprehensive way to deal with the segments of fraud detection.
1.3.2 Analysis of the Selected Methodologies
We should take a plain : "DOTNETSPIDER IS A LEADING FOR DOT NET COMMUNITY" and we
need to scramble the plain utilizing "Caesar Cipher", utilizing key/secret word as "9". Caesar
Cipher just takes numeric secret key, and just between 0-25.
So our plain's figure/encoded will progress toward becoming: "MXCWNCBYRMNA RB J
UNJMRWP FNKBRCN OXA MXC WNC LXVVDWRCH".
So how could we land at the figure/scrambled ?
Presently take a word from the plain , for instance: "DOTNETSPIDER"
It is a kind of supplant figure in which each letter in the plaintext is supplanted by a letter with a
settled position isolated by a numerical esteem utilized as a "key".
So we need to take each letter or character,In instance of "DOTNETSPIDER": the estimation of
'D' is 3, so include 3 by 9 (since we have utilized '9' as our key/secret phrase)
4
1.3.1 Selected Sub-Problem
The research has focused on the identity theft using cloning method. Information started from
Qualitative data has been kept up and checked appropriately. The legitimacy and dependability
factors in information accumulation should be finished. However, this compose information are
taken from distributed journals and articles. Qualitative research helps in getting top to bottom
points of interest of the research theme including fraud detection (Jain 2017). The validity of
data collected has been properly maintained. Data has been collected from secondary sources
including books, journals and articles. Journals have been taken from 2012 published journals.
The view of the members have been thought about appropriately. This sort of methodology
causes in comprehensive way to deal with the segments of fraud detection.
1.3.2 Analysis of the Selected Methodologies
We should take a plain : "DOTNETSPIDER IS A LEADING FOR DOT NET COMMUNITY" and we
need to scramble the plain utilizing "Caesar Cipher", utilizing key/secret word as "9". Caesar
Cipher just takes numeric secret key, and just between 0-25.
So our plain's figure/encoded will progress toward becoming: "MXCWNCBYRMNA RB J
UNJMRWP FNKBRCN OXA MXC WNC LXVVDWRCH".
So how could we land at the figure/scrambled ?
Presently take a word from the plain , for instance: "DOTNETSPIDER"
It is a kind of supplant figure in which each letter in the plaintext is supplanted by a letter with a
settled position isolated by a numerical esteem utilized as a "key".
So we need to take each letter or character,In instance of "DOTNETSPIDER": the estimation of
'D' is 3, so include 3 by 9 (since we have utilized '9' as our key/secret phrase)
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Along these lines, 3 + 9 = 12
Presently allude to the table above, now whose esteem is 12, its 'M'.
So here „D‟ gets supplanted by „M‟
Let‟s take another incentive from "DOTNETSPIDER" ? „T‟: the estimation of „T‟ is 19, so include
19 by 9 (since we have utilized „9‟ as our key/secret word)
Along these lines, 19 + 9 = 28,
Here you can see the esteem isn't on the rundown.
So at whatever point the esteem is more prominent than „25‟, simply subtract the incentive
with „26‟.
Along these lines, 19 + 9 = 28, and now the esteem is more prominent than 25, in this way, 28 –
26 = 2.
Presently allude to the table above, now whose esteem is 2, its „C‟. So here „T‟ gets supplanted
by „C‟
Additionally,
O (14) + 9 = 23(X)
T (19) + 9 = 28 – 26 = 2(C)
N (13) + 9 = 22(W)
E (4) + 9 = 13(N)
T (19) + 9 = 28 – 26 = 2(C)
5
Presently allude to the table above, now whose esteem is 12, its 'M'.
So here „D‟ gets supplanted by „M‟
Let‟s take another incentive from "DOTNETSPIDER" ? „T‟: the estimation of „T‟ is 19, so include
19 by 9 (since we have utilized „9‟ as our key/secret word)
Along these lines, 19 + 9 = 28,
Here you can see the esteem isn't on the rundown.
So at whatever point the esteem is more prominent than „25‟, simply subtract the incentive
with „26‟.
Along these lines, 19 + 9 = 28, and now the esteem is more prominent than 25, in this way, 28 –
26 = 2.
Presently allude to the table above, now whose esteem is 2, its „C‟. So here „T‟ gets supplanted
by „C‟
Additionally,
O (14) + 9 = 23(X)
T (19) + 9 = 28 – 26 = 2(C)
N (13) + 9 = 22(W)
E (4) + 9 = 13(N)
T (19) + 9 = 28 – 26 = 2(C)
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.3.3 Relevance of the Research Problem
The research refers to the methodology used in the fraud detection by data mining
process. Data has been collected form qualitative method and data text have been taken from
various online journals and books. The research has been relevant and reliable to its objectives
and aim (Tran et al. 2018). The research has focused on fraud and theft detection using data
mining techniques. Major problems of the data mining has been the theft and fraud cases. Fraud
can be of different forms including bribery, securities fraud, theft, mortgage and scams. Online
data theft has been one of the major problems over the internet. Fraud detection techniques
have been used in the methodology for ensuring security (Hines and Youssef 2018). The validity
of data collected has been properly maintained. Data has been collected from secondary
sources including books, journals and articles. Journals have been taken from 2012 published
journals. The view of the members have been thought about appropriately. All the journals have
its proper author name and publishing house. This verifies the reliability and validity of data and
information collected from various sources.
1.3.4 Summary of the Reviewed Methodologies
Literature # Research Problem Methodology Your Sub-problem Relevance
Literature1 Skimming Qualitative Financial Fraud Valid
Literature2 Cloning Qualitative Identity theft Valid
1.4 Proposed Methodology
1.4.1 Identification and Justification
Quantitative research manages the amount of the information assembled. Quantitative research
strategy manages crude information gathered from members. By and large, online overviews
are best to gather quantitative information and data with respect to the research theme (Ristov,
6
The research refers to the methodology used in the fraud detection by data mining
process. Data has been collected form qualitative method and data text have been taken from
various online journals and books. The research has been relevant and reliable to its objectives
and aim (Tran et al. 2018). The research has focused on fraud and theft detection using data
mining techniques. Major problems of the data mining has been the theft and fraud cases. Fraud
can be of different forms including bribery, securities fraud, theft, mortgage and scams. Online
data theft has been one of the major problems over the internet. Fraud detection techniques
have been used in the methodology for ensuring security (Hines and Youssef 2018). The validity
of data collected has been properly maintained. Data has been collected from secondary
sources including books, journals and articles. Journals have been taken from 2012 published
journals. The view of the members have been thought about appropriately. All the journals have
its proper author name and publishing house. This verifies the reliability and validity of data and
information collected from various sources.
1.3.4 Summary of the Reviewed Methodologies
Literature # Research Problem Methodology Your Sub-problem Relevance
Literature1 Skimming Qualitative Financial Fraud Valid
Literature2 Cloning Qualitative Identity theft Valid
1.4 Proposed Methodology
1.4.1 Identification and Justification
Quantitative research manages the amount of the information assembled. Quantitative research
strategy manages crude information gathered from members. By and large, online overviews
are best to gather quantitative information and data with respect to the research theme (Ristov,
6

Gusev and Kostoska 2012). The research has been focused on the fraud and theft detection. The
use of various journals and articles have been helping in collecting in the data and information.
The fraud and theft detection have been a major problems for the organization in the market.
The use of the data mining techniques have been helping in providing solutions to the fraud
cases (Prabakaran and Mitra 2018). Data and information has been helping in performing
analysis method of the fraud detection techniques. Data has been collected from secondary
sources including books, journals and articles. Journals have been taken from 2012 published
journals. This has been a great factor in order to maintain a keen approach in the fraud
detection techniques. Various research journals and articles have been used in order to collect
data and information.
1.4.2 Benefits and Limitations
There are different advantages of utilizing a Qualitative strategies and methodologies. This
methodology helps in giving a detailed data about the research point. Qualitative methodology
helps in characterizing relationship among data preparing with execution. It helps in giving a
more profound methodology about the remarks of the research that aides in keeping up sharp
way to deal with the improvement of the theory of the research (Zhou et al. 2018). Fraud
detection techniques have been used in the methodology for ensuring security. All the journals
have its proper author name and publishing house. This verifies the reliability and validity of
data and information collected from various sources. Qualitative research concedes about
finding members and experience to pick up learning with respect to look into theme (Xiao and
Xiao 2013). It has an adaptable structure that may help in keeping up guide way to deal with
information gathering from interviews and online sources.
Past these favorable circumstances, there are some e constraints of the Qualitative
methodology. This methodology does not give data of some logical sensitive and spotlights on
encounters (Gray, and Debreceny 2014). Nonetheless, different researchers have less need to
the Qualitative methodologies because of low believability (Luna et al. 2012). The example size
7
use of various journals and articles have been helping in collecting in the data and information.
The fraud and theft detection have been a major problems for the organization in the market.
The use of the data mining techniques have been helping in providing solutions to the fraud
cases (Prabakaran and Mitra 2018). Data and information has been helping in performing
analysis method of the fraud detection techniques. Data has been collected from secondary
sources including books, journals and articles. Journals have been taken from 2012 published
journals. This has been a great factor in order to maintain a keen approach in the fraud
detection techniques. Various research journals and articles have been used in order to collect
data and information.
1.4.2 Benefits and Limitations
There are different advantages of utilizing a Qualitative strategies and methodologies. This
methodology helps in giving a detailed data about the research point. Qualitative methodology
helps in characterizing relationship among data preparing with execution. It helps in giving a
more profound methodology about the remarks of the research that aides in keeping up sharp
way to deal with the improvement of the theory of the research (Zhou et al. 2018). Fraud
detection techniques have been used in the methodology for ensuring security. All the journals
have its proper author name and publishing house. This verifies the reliability and validity of
data and information collected from various sources. Qualitative research concedes about
finding members and experience to pick up learning with respect to look into theme (Xiao and
Xiao 2013). It has an adaptable structure that may help in keeping up guide way to deal with
information gathering from interviews and online sources.
Past these favorable circumstances, there are some e constraints of the Qualitative
methodology. This methodology does not give data of some logical sensitive and spotlights on
encounters (Gray, and Debreceny 2014). Nonetheless, different researchers have less need to
the Qualitative methodologies because of low believability (Luna et al. 2012). The example size
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
of the Qualitative methodology is little contrast with quantitative methodology. Consequently,
the legitimacy of the information has been constantly flawed.
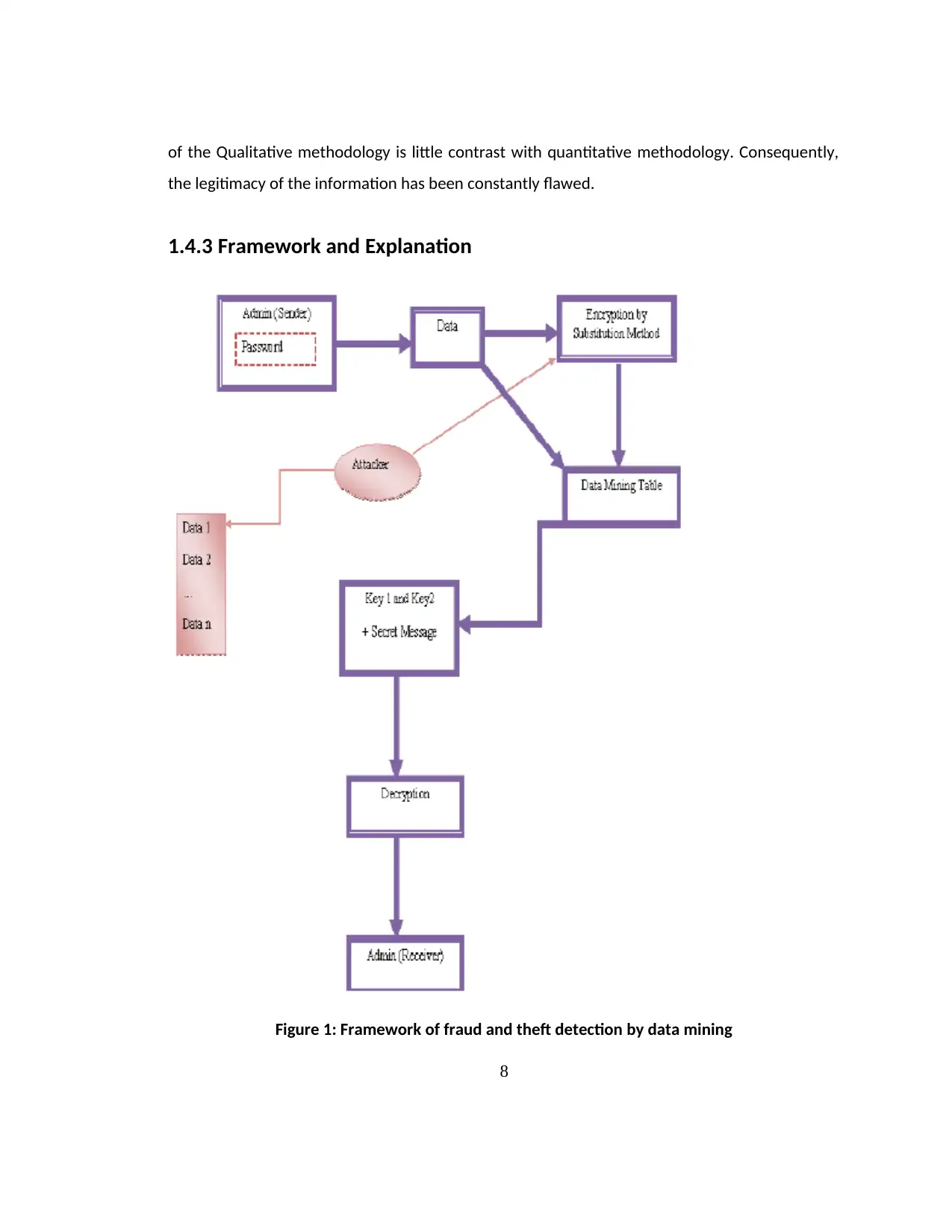
1.4.3 Framework and Explanation
Figure 1: Framework of fraud and theft detection by data mining
8
the legitimacy of the information has been constantly flawed.
1.4.3 Framework and Explanation
Figure 1: Framework of fraud and theft detection by data mining
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

(Source: Created by Author)
The above figure describes about a framework of the fraud and theft detection technique. This
figure contains eight components including attacker. The attacker directly attacks the encryption
by substitution method that can be controlled by enhancing security in encrypting technology.
After that, data is transferred n the data mining table where proper allocation of the data has
been done (Dutta, Gupta and Narayan 2017). The data is secured by allocating keys including
private and public keys. After allocating keys, data is transferred to the receiver end. The data is
decrypted in the received end with the help of private and public keys. This help in maintaining
a secured approached to the data transfer in the network. After decrypting, data is received at
the receiver end.
9
The above figure describes about a framework of the fraud and theft detection technique. This
figure contains eight components including attacker. The attacker directly attacks the encryption
by substitution method that can be controlled by enhancing security in encrypting technology.
After that, data is transferred n the data mining table where proper allocation of the data has
been done (Dutta, Gupta and Narayan 2017). The data is secured by allocating keys including
private and public keys. After allocating keys, data is transferred to the receiver end. The data is
decrypted in the received end with the help of private and public keys. This help in maintaining
a secured approached to the data transfer in the network. After decrypting, data is received at
the receiver end.
9

List of References
Agrawal, S. and Agrawal, J., 2015. Survey on anomaly detection using data mining
techniques. Procedia Computer Science, 60, pp.708-713.
Ahmad, T., Chen, H., Wang, J. and Guo, Y., 2017. Review of various modeling techniques for the
detection of electricity theft in smart grid environment. Renewable and Sustainable Energy
Reviews.
Baesens, B., Van Vlasselaer, V. and Verbeke, W., 2015. Fraud analytics using descriptive,
predictive, and social network techniques: a guide to data science for fraud detection. John Wiley
& Sons.
Dutta, S., Gupta, A.K. and Narayan, N., 2017, October. Identity Crime Detection Using Data
Mining. In Computational Intelligence and Networks (CINE), 2017 3rd International Conference
on (pp. 1-5). IEEE.
Gray, G.L. and Debreceny, R.S., 2014. A taxonomy to guide research on the application of data
mining to fraud detection in financial statement audits. International Journal of Accounting
Information Systems, 15(4), pp.357-380.
Hines, C. and Youssef, A., 2018, April. Machine Learning Applied to Rotating Check Fraud
Detection. In Data Intelligence and Security (ICDIS), 2018 1st International Conference on (pp.
32-35). IEEE.
Jain, V., 2017. Perspective analysis of telecommunication fraud detection using data stream
analytics and neural network classification based data mining. International Journal of
Information Technology, 9(3), pp.303-310.
Jeong, S.H., Kim, H., Shin, Y., Lee, T. and Kim, H.K., 2015. A Survey of Fraud Detection Research
based on Transaction Analysis and Data Mining Technique. Journal of the Korea Institute of
Information Security and Cryptology, 25(6), pp.1525-1540.
Jokar, P., Arianpoo, N. and Leung, V.C., 2016. Electricity Theft Detection in AMI Using Customers'
Consumption Patterns. IEEE Trans. Smart Grid, 7(1), pp.216-226.
10
Agrawal, S. and Agrawal, J., 2015. Survey on anomaly detection using data mining
techniques. Procedia Computer Science, 60, pp.708-713.
Ahmad, T., Chen, H., Wang, J. and Guo, Y., 2017. Review of various modeling techniques for the
detection of electricity theft in smart grid environment. Renewable and Sustainable Energy
Reviews.
Baesens, B., Van Vlasselaer, V. and Verbeke, W., 2015. Fraud analytics using descriptive,
predictive, and social network techniques: a guide to data science for fraud detection. John Wiley
& Sons.
Dutta, S., Gupta, A.K. and Narayan, N., 2017, October. Identity Crime Detection Using Data
Mining. In Computational Intelligence and Networks (CINE), 2017 3rd International Conference
on (pp. 1-5). IEEE.
Gray, G.L. and Debreceny, R.S., 2014. A taxonomy to guide research on the application of data
mining to fraud detection in financial statement audits. International Journal of Accounting
Information Systems, 15(4), pp.357-380.
Hines, C. and Youssef, A., 2018, April. Machine Learning Applied to Rotating Check Fraud
Detection. In Data Intelligence and Security (ICDIS), 2018 1st International Conference on (pp.
32-35). IEEE.
Jain, V., 2017. Perspective analysis of telecommunication fraud detection using data stream
analytics and neural network classification based data mining. International Journal of
Information Technology, 9(3), pp.303-310.
Jeong, S.H., Kim, H., Shin, Y., Lee, T. and Kim, H.K., 2015. A Survey of Fraud Detection Research
based on Transaction Analysis and Data Mining Technique. Journal of the Korea Institute of
Information Security and Cryptology, 25(6), pp.1525-1540.
Jokar, P., Arianpoo, N. and Leung, V.C., 2016. Electricity Theft Detection in AMI Using Customers'
Consumption Patterns. IEEE Trans. Smart Grid, 7(1), pp.216-226.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





