IFN503 Fundamentals of Computer System Report, QUT, 2019
VerifiedAdded on 2022/10/01
|11
|2375
|26
Report
AI Summary
This report delves into the fundamentals of computer systems, addressing key aspects of networking and information security. Part 1 of the report examines the characteristics and layered protocol stack design of TCP/IP protocols. It then contrasts IPv4 and IPv6, covering differences in packet format, a...

Running head: FUNDAMENTALS OF COMPUTER SYSTEM
Fundamentals of Computer System
Name of the Student
Name of the University
Author Note
Fundamentals of Computer System
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
FUNDAMENTALS OF COMPUTER SYSTEM 1
Part 1
Answer to question number 1:
A TCP link defines the link of the endpoints, which is involved with the connection
(Comer, 2013). The socket number is the combination of the port number and IP address that
can identify any connection uniquely. TCP (Transmission Control Protocol) has various
characteristics.
An idealized communication of network with the protocol family is described in the
OSI model. TCP / IP do not immediately match with this model. TCP / IP either mix multiple
OSI layers into one part or use no components at all (Fu et al., 2013). The chart below
indicates the levels of TCP / IP Solaris application.
Answer to question number 2:
IPv4 IPv6
Address Space IPv4 utilizes 32-bit
instructions limited to
4294967296 applications.
IPv4 supplies unique address
blocks that is equivalent to
18 million handles) and
multicast handles that is
equivalent to 270 million
handles for private networks.
The length of IPv6 is 128 bit
opposed to IPv4's 32 pieces.
Therefore, the address space
has roughly 3.4×1038
addresses that is equivalent
to 340 undecillion addresses.
Address Representation IPv4 involves an answering
scheme using 32-bit
An address of IPv6 is
depicted as eight rows of four
Part 1
Answer to question number 1:
A TCP link defines the link of the endpoints, which is involved with the connection
(Comer, 2013). The socket number is the combination of the port number and IP address that
can identify any connection uniquely. TCP (Transmission Control Protocol) has various
characteristics.
An idealized communication of network with the protocol family is described in the
OSI model. TCP / IP do not immediately match with this model. TCP / IP either mix multiple
OSI layers into one part or use no components at all (Fu et al., 2013). The chart below
indicates the levels of TCP / IP Solaris application.
Answer to question number 2:
IPv4 IPv6
Address Space IPv4 utilizes 32-bit
instructions limited to
4294967296 applications.
IPv4 supplies unique address
blocks that is equivalent to
18 million handles) and
multicast handles that is
equivalent to 270 million
handles for private networks.
The length of IPv6 is 128 bit
opposed to IPv4's 32 pieces.
Therefore, the address space
has roughly 3.4×1038
addresses that is equivalent
to 340 undecillion addresses.
Address Representation IPv4 involves an answering
scheme using 32-bit
An address of IPv6 is
depicted as eight rows of four
2FUNDAMENTALS OF COMPUTER SYSTEM
numerical identifiers.
Typically, these addresses
are represented as decimal
numbers of four bytes in
quad-noted format, each in
the spectrum 0 to 255, or 8
pieces per digit.
hexadecimal numbers (Karir
et al., 2013). Each set of 16
pieces or two bytes, and
sometimes it is called a
hextet as well.
Packet Format The IPv4 datagram is
the packet of variable lengths
consisting of the header of 20
bytes and the data up to
65,536 together with header.
The header includes vital
routing and distribution data
(Bosshart et al., 2014).
Each packet consists of a
compulsory foundation
header that the payload
succeeds. The payload
consists of two components,
which is voluntary expansion
headers and bottom level
information. The original
header consumes nearly 40
bytes, while the expansion
headers and upper-level data
typically retain up to 65,535
bytes of data.
Answer to question number 3:
An IPv6 host receives an application on the Internet to the IPv4 activated
server, which is comprehended to the IPv6 address. The system can assist them to interact in
the network. When the IPv6 recipient gives an IPv4 client demand signal, the router or device
numerical identifiers.
Typically, these addresses
are represented as decimal
numbers of four bytes in
quad-noted format, each in
the spectrum 0 to 255, or 8
pieces per digit.
hexadecimal numbers (Karir
et al., 2013). Each set of 16
pieces or two bytes, and
sometimes it is called a
hextet as well.
Packet Format The IPv4 datagram is
the packet of variable lengths
consisting of the header of 20
bytes and the data up to
65,536 together with header.
The header includes vital
routing and distribution data
(Bosshart et al., 2014).
Each packet consists of a
compulsory foundation
header that the payload
succeeds. The payload
consists of two components,
which is voluntary expansion
headers and bottom level
information. The original
header consumes nearly 40
bytes, while the expansion
headers and upper-level data
typically retain up to 65,535
bytes of data.
Answer to question number 3:
An IPv6 host receives an application on the Internet to the IPv4 activated
server, which is comprehended to the IPv6 address. The system can assist them to interact in
the network. When the IPv6 recipient gives an IPv4 client demand signal, the router or device
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3FUNDAMENTALS OF COMPUTER SYSTEM
strips the IPv6 signal, takes the IPv6 protocol, provides the IPv4 protocol and transfers it over
the Internet. The router does the vice versa when an IPv4 server reaction goes to the IPv6
host.
Answer to question number 4:
The dual stack network is the network, where both IPv6 and IPv4 are allowed for all
the nodes. This is particularly crucial for the router, as a router is usually the first node to
the obtain requests from the outside of the network on the particular network. If data is
received by a node in the dual stack network and it is programmed for preferring the IPv6 to
IPv4 transport.
The network infrastructure can change from IPv4 to IPv6 for providing more space
for the addresses and represent increasing worldwide connectivity. One of the IPv4 to IPv6
transition approaches described in the latest years is dual stack networks in the IP addresses
transition.
Part 2
Answer to question number 1:
All the measures of information security try to address the three goals such as:
Protect confidentiality of the information
Preserve integrity of the information
Promote availability of the information for the authorized used
Three goals form the CIA triad (Confidentiality, integrity and availability), which are base of
all the security programs (Samonas & Coss, 2014).
strips the IPv6 signal, takes the IPv6 protocol, provides the IPv4 protocol and transfers it over
the Internet. The router does the vice versa when an IPv4 server reaction goes to the IPv6
host.
Answer to question number 4:
The dual stack network is the network, where both IPv6 and IPv4 are allowed for all
the nodes. This is particularly crucial for the router, as a router is usually the first node to
the obtain requests from the outside of the network on the particular network. If data is
received by a node in the dual stack network and it is programmed for preferring the IPv6 to
IPv4 transport.
The network infrastructure can change from IPv4 to IPv6 for providing more space
for the addresses and represent increasing worldwide connectivity. One of the IPv4 to IPv6
transition approaches described in the latest years is dual stack networks in the IP addresses
transition.
Part 2
Answer to question number 1:
All the measures of information security try to address the three goals such as:
Protect confidentiality of the information
Preserve integrity of the information
Promote availability of the information for the authorized used
Three goals form the CIA triad (Confidentiality, integrity and availability), which are base of
all the security programs (Samonas & Coss, 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4FUNDAMENTALS OF COMPUTER SYSTEM
Fig 1: CIA Triad (Source: Created by author)
Confidentiality: The confidentiality is equivalent to the privacy of the data. The
measures are undertaken for ensuring the confidentiality for preventing the
confidential data from reaching to the wrong person (Von Solms & Van Niekerk,
2013). It is needed to ensure the right people are accessing the data. The access to the
data needs to be restricted for the authorized for viewing the data. For the data for
being categorized as per the type and amount of the damage can be done and fall into
the unintended hands. Less or more the rigorous measures can be implemented as the
categories.
Integrity: The integrity model keeps the data trustworthy and pure by securing the
data from the sudden or intentional changes. Integrity model prevent the unauthorized
users from making the change to the programs or data. It prevents the authorized user
from making the unauthorized or improper change to the data. It also maintains the
external and internal consistency of the programs and the data.
Availability: Availability keeps the resources and the data available for the authorized
access and mainly for the disasters and the emergencies. Professional of the
Information Security addresses the common challenges to the availability. It addresses
Fig 1: CIA Triad (Source: Created by author)
Confidentiality: The confidentiality is equivalent to the privacy of the data. The
measures are undertaken for ensuring the confidentiality for preventing the
confidential data from reaching to the wrong person (Von Solms & Van Niekerk,
2013). It is needed to ensure the right people are accessing the data. The access to the
data needs to be restricted for the authorized for viewing the data. For the data for
being categorized as per the type and amount of the damage can be done and fall into
the unintended hands. Less or more the rigorous measures can be implemented as the
categories.
Integrity: The integrity model keeps the data trustworthy and pure by securing the
data from the sudden or intentional changes. Integrity model prevent the unauthorized
users from making the change to the programs or data. It prevents the authorized user
from making the unauthorized or improper change to the data. It also maintains the
external and internal consistency of the programs and the data.
Availability: Availability keeps the resources and the data available for the authorized
access and mainly for the disasters and the emergencies. Professional of the
Information Security addresses the common challenges to the availability. It addresses
5FUNDAMENTALS OF COMPUTER SYSTEM
the DoS (Denial of service) because of the intentional attacks in the implementation
when the programmer is unaware of the flow, which can crash the system.
Availability model addresses the loss of the capabilities of the information system
because of the natural disaster or the human actions. It also addresses the failures of
the equipment during the use.
Answer to question number 2:
The three goals of the information security CIA triad (confidentiality, integrity, and the
availability) may be threatened by the security attacks.
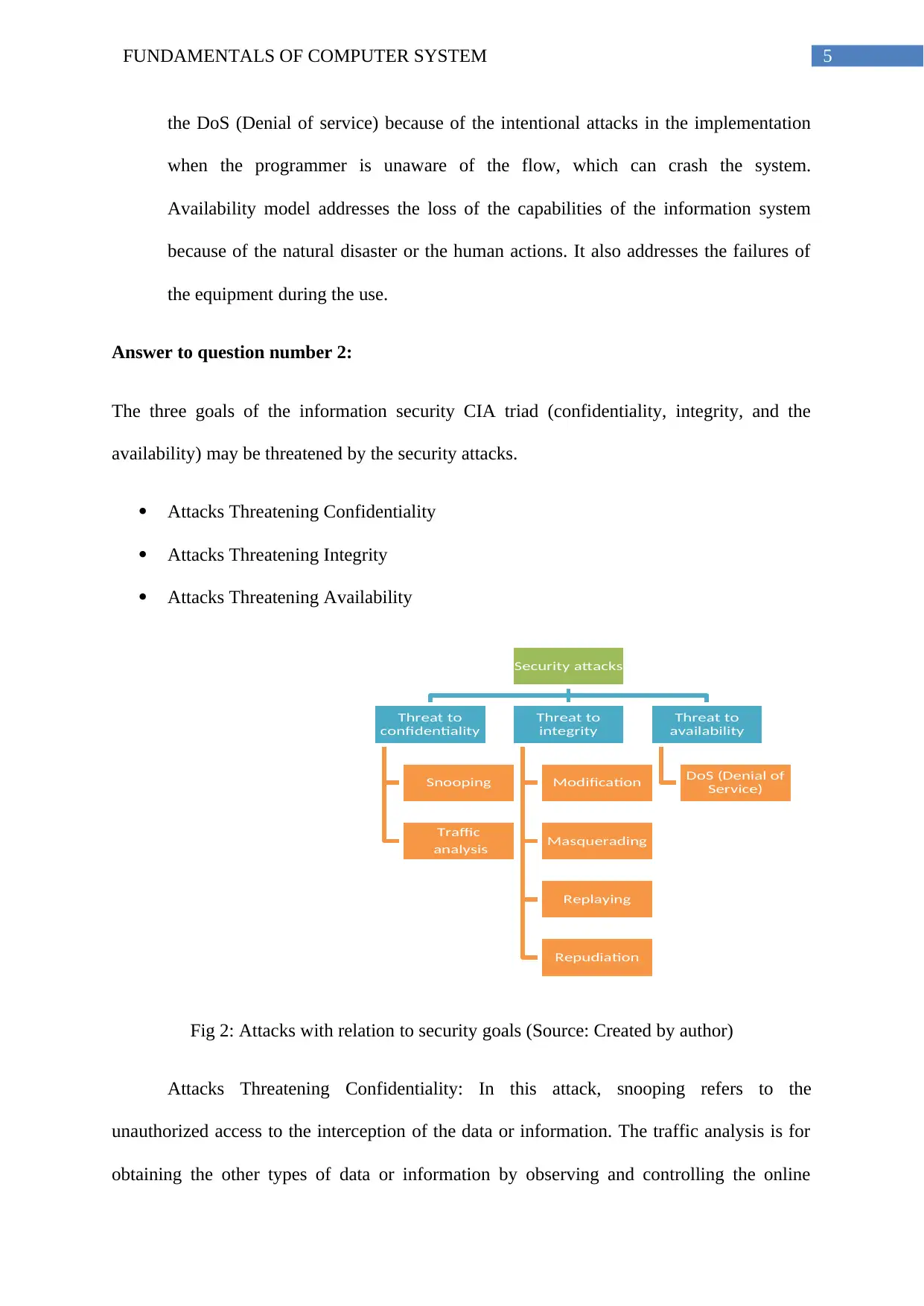
Attacks Threatening Confidentiality
Attacks Threatening Integrity
Attacks Threatening Availability
Fig 2: Attacks with relation to security goals (Source: Created by author)
Attacks Threatening Confidentiality: In this attack, snooping refers to the
unauthorized access to the interception of the data or information. The traffic analysis is for
obtaining the other types of data or information by observing and controlling the online
Security attacks
Threat to
confidentiality
Snooping
Traffic
analysis
Threat to
integrity
Modification
Masquerading
Replaying
Repudiation
Threat to
availability
DoS (Denial of
Service)
the DoS (Denial of service) because of the intentional attacks in the implementation
when the programmer is unaware of the flow, which can crash the system.
Availability model addresses the loss of the capabilities of the information system
because of the natural disaster or the human actions. It also addresses the failures of
the equipment during the use.
Answer to question number 2:
The three goals of the information security CIA triad (confidentiality, integrity, and the
availability) may be threatened by the security attacks.
Attacks Threatening Confidentiality
Attacks Threatening Integrity
Attacks Threatening Availability
Fig 2: Attacks with relation to security goals (Source: Created by author)
Attacks Threatening Confidentiality: In this attack, snooping refers to the
unauthorized access to the interception of the data or information. The traffic analysis is for
obtaining the other types of data or information by observing and controlling the online
Security attacks
Threat to
confidentiality
Snooping
Traffic
analysis
Threat to
integrity
Modification
Masquerading
Replaying
Repudiation
Threat to
availability
DoS (Denial of
Service)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6FUNDAMENTALS OF COMPUTER SYSTEM
traffic. For an instance, while transferring any data, data interruption can occur by the cut of
wire line, jamming the wireless signals or drop packets. Thus any data interception can occur
by wiring eavesdrops by the hackers.
Attacks Threatening Integrity: Modification of threat to integrity means that the
hacker intercepts the data of the message and modifies it. Masquerading occurs when the
hacker impersonates other person (Nawir et al., 2016). Replaying means that the hacker
obtains the copy of the data of the message, which is sent by the user and then the hacker tries
to replay the message. Repudiation means that the sender of the sent message can deny that
he or she has not send the message. Then the receiver can deny later that he or she has not
received the message. For an instance, while the message transferring, the hacker intercepts
the message and replace the information of the message. Then the impersonation occurs.
Attacks Threatening Availability: Very common attack of the availability is the DoS
(Denial of service) (Park et al., 2014). DoS can slow down the service of the system or totally
interrupt the system.
Part 3
CPU management
The operating frequency of the device of CPU can scale according to the user or
system requirement. When the full resources of the process are not required, the system may
reduce the overall operating temperature and power consumption (Valentini et al., 2013). The
API allows disabling and enabling the available cores of CPU. IT provides the access to a
complete method list, which is available in the API. All the API methods of CPU need the
permission to access into them. If the application does not have the permission, the
traffic. For an instance, while transferring any data, data interruption can occur by the cut of
wire line, jamming the wireless signals or drop packets. Thus any data interception can occur
by wiring eavesdrops by the hackers.
Attacks Threatening Integrity: Modification of threat to integrity means that the
hacker intercepts the data of the message and modifies it. Masquerading occurs when the
hacker impersonates other person (Nawir et al., 2016). Replaying means that the hacker
obtains the copy of the data of the message, which is sent by the user and then the hacker tries
to replay the message. Repudiation means that the sender of the sent message can deny that
he or she has not send the message. Then the receiver can deny later that he or she has not
received the message. For an instance, while the message transferring, the hacker intercepts
the message and replace the information of the message. Then the impersonation occurs.
Attacks Threatening Availability: Very common attack of the availability is the DoS
(Denial of service) (Park et al., 2014). DoS can slow down the service of the system or totally
interrupt the system.
Part 3
CPU management
The operating frequency of the device of CPU can scale according to the user or
system requirement. When the full resources of the process are not required, the system may
reduce the overall operating temperature and power consumption (Valentini et al., 2013). The
API allows disabling and enabling the available cores of CPU. IT provides the access to a
complete method list, which is available in the API. All the API methods of CPU need the
permission to access into them. If the application does not have the permission, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7FUNDAMENTALS OF COMPUTER SYSTEM
application will not allow to access to the feature of CPU service. For working with the API
and managing the device, instantiation of the CPU management object is the first step.
Memory management
Memory management always coordinates with the management of the RAM or
physical memory of the computer (Comer, 2015). Each computer system has the preinstalled
main memory that is used for the running process of the service or the application. However,
the huge memory capacity cannot accommodate with the running process or the programs
simultaneously. In this way, the memory management allocates the required memory space
for the process by moving in between the memory and hard drive. Then it assigns priorities to
the entire organization of the process or programs. Memory management is managed and
performed by the OS host. Memory management encompasses the non-volatile memories in
the system like virtual memory and cache memory.
Process management
Without any instruction by the CPU, a program does not execute anything. Process is
execution of the program. For accomplishing the task, process requires the resources of
computer. There can have more than one process of the system that can require the previous
resource (Silberschatz, Gagne & Galvin, 2018). Therefore, the OS manages all the resources
and processes in the efficient and convenient way. Some of the computer resources can be
required for being executed by any one process for maintaining the consistency. Otherwise,
system will become inconsistent and the deadlock can occur. OS is responsible for the below
mentioned activities in the connection with the process management.
Scheduling the threads and processes on the CPU
Creating and deleting the system processes and the user.
application will not allow to access to the feature of CPU service. For working with the API
and managing the device, instantiation of the CPU management object is the first step.
Memory management
Memory management always coordinates with the management of the RAM or
physical memory of the computer (Comer, 2015). Each computer system has the preinstalled
main memory that is used for the running process of the service or the application. However,
the huge memory capacity cannot accommodate with the running process or the programs
simultaneously. In this way, the memory management allocates the required memory space
for the process by moving in between the memory and hard drive. Then it assigns priorities to
the entire organization of the process or programs. Memory management is managed and
performed by the OS host. Memory management encompasses the non-volatile memories in
the system like virtual memory and cache memory.
Process management
Without any instruction by the CPU, a program does not execute anything. Process is
execution of the program. For accomplishing the task, process requires the resources of
computer. There can have more than one process of the system that can require the previous
resource (Silberschatz, Gagne & Galvin, 2018). Therefore, the OS manages all the resources
and processes in the efficient and convenient way. Some of the computer resources can be
required for being executed by any one process for maintaining the consistency. Otherwise,
system will become inconsistent and the deadlock can occur. OS is responsible for the below
mentioned activities in the connection with the process management.
Scheduling the threads and processes on the CPU
Creating and deleting the system processes and the user.

8FUNDAMENTALS OF COMPUTER SYSTEM
Resuming and suspending the processes.
Providing mechanisms for the process of synchronization
Secondary storage management
The secondary storage management is the transcendent feature of the database
management system (Micheloni, Crippa & Picca, 2013). It is supported by the mechanism
set. The mechanism set is included with the index management, buffering of data, clustering
of data, access path selection and the query optimization. These indices are invisible to users.
They are the performance feature. However, in terms of performance the indices are very
critical that the system will keep performing in their absence as they take much time to
perform. The essential point is the indices are not visible. The programmer may not have to
write the code for program for maintaining the indices for allocating the disk storage or for
moving the data between the main memory and disk. In this way, there needs to be a
independence within the physical and logical level of the device or the system.
Resuming and suspending the processes.
Providing mechanisms for the process of synchronization
Secondary storage management
The secondary storage management is the transcendent feature of the database
management system (Micheloni, Crippa & Picca, 2013). It is supported by the mechanism
set. The mechanism set is included with the index management, buffering of data, clustering
of data, access path selection and the query optimization. These indices are invisible to users.
They are the performance feature. However, in terms of performance the indices are very
critical that the system will keep performing in their absence as they take much time to
perform. The essential point is the indices are not visible. The programmer may not have to
write the code for program for maintaining the indices for allocating the disk storage or for
moving the data between the main memory and disk. In this way, there needs to be a
independence within the physical and logical level of the device or the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9FUNDAMENTALS OF COMPUTER SYSTEM
References
Bosshart, P., Daly, D., Gibb, G., Izzard, M., McKeown, N., Rexford, J., ... & Walker, D.
(2014). P4: Programming protocol-independent packet processors. ACM SIGCOMM
Computer Communication Review, 44(3), 87-95.
Comer, D. (2015). Operating system design: the XINU approach. Chapman and Hall/CRC.
Comer, D. E. (2013). Internetworking with TCP/IP. Addison-Wesley Professional.
Fu, B., Xiao, Y., Deng, H. J., & Zeng, H. (2013). A survey of cross-layer designs in wireless
networks. IEEE Communications Surveys & Tutorials, 16(1), 110-126.
Karir, M., Huston, G., Michaelson, G., & Bailey, M. (2013, March). Understanding IPv6
populations in the wild. In International Conference on Passive and Active Network
Measurement (pp. 256-259). Springer, Berlin, Heidelberg.
Micheloni, R., Crippa, L., & Picca, M. (2013). Hybrid storage. In Inside solid state drives
(SSDs) (pp. 61-77). Springer, Dordrecht.
Nawir, M., Amir, A., Yaakob, N., & Lynn, O. B. (2016, August). Internet of Things (IoT):
Taxonomy of security attacks. In 2016 3rd International Conference on Electronic
Design (ICED) (pp. 321-326). IEEE.
Park, J., Iwai, K., Tanaka, H., & Kurokawa, T. (2014, October). Analysis of slow read DoS
attack. In 2014 International Symposium on Information Theory and its
Applications (pp. 60-64). IEEE.
Samonas, S., & Coss, D. (2014). THE CIA STRIKES BACK: REDEFINING
CONFIDENTIALITY, INTEGRITY AND AVAILABILITY IN
SECURITY. Journal of Information System Security, 10(3).
References
Bosshart, P., Daly, D., Gibb, G., Izzard, M., McKeown, N., Rexford, J., ... & Walker, D.
(2014). P4: Programming protocol-independent packet processors. ACM SIGCOMM
Computer Communication Review, 44(3), 87-95.
Comer, D. (2015). Operating system design: the XINU approach. Chapman and Hall/CRC.
Comer, D. E. (2013). Internetworking with TCP/IP. Addison-Wesley Professional.
Fu, B., Xiao, Y., Deng, H. J., & Zeng, H. (2013). A survey of cross-layer designs in wireless
networks. IEEE Communications Surveys & Tutorials, 16(1), 110-126.
Karir, M., Huston, G., Michaelson, G., & Bailey, M. (2013, March). Understanding IPv6
populations in the wild. In International Conference on Passive and Active Network
Measurement (pp. 256-259). Springer, Berlin, Heidelberg.
Micheloni, R., Crippa, L., & Picca, M. (2013). Hybrid storage. In Inside solid state drives
(SSDs) (pp. 61-77). Springer, Dordrecht.
Nawir, M., Amir, A., Yaakob, N., & Lynn, O. B. (2016, August). Internet of Things (IoT):
Taxonomy of security attacks. In 2016 3rd International Conference on Electronic
Design (ICED) (pp. 321-326). IEEE.
Park, J., Iwai, K., Tanaka, H., & Kurokawa, T. (2014, October). Analysis of slow read DoS
attack. In 2014 International Symposium on Information Theory and its
Applications (pp. 60-64). IEEE.
Samonas, S., & Coss, D. (2014). THE CIA STRIKES BACK: REDEFINING
CONFIDENTIALITY, INTEGRITY AND AVAILABILITY IN
SECURITY. Journal of Information System Security, 10(3).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10FUNDAMENTALS OF COMPUTER SYSTEM
Silberschatz, A., Gagne, G., & Galvin, P. B. (2018). Operating system concepts. Wiley.
Valentini, G. L., Lassonde, W., Khan, S. U., Min-Allah, N., Madani, S. A., Li, J., ... & Li, H.
(2013). An overview of energy efficiency techniques in cluster computing
systems. Cluster Computing, 16(1), 3-15.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Silberschatz, A., Gagne, G., & Galvin, P. B. (2018). Operating system concepts. Wiley.
Valentini, G. L., Lassonde, W., Khan, S. U., Min-Allah, N., Madani, S. A., Li, J., ... & Li, H.
(2013). An overview of energy efficiency techniques in cluster computing
systems. Cluster Computing, 16(1), 3-15.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




