CSG3309 IT Security Management Implementation Plan - John Dough Pizza
VerifiedAdded on 2021/04/29
|14
|3183
|452
Project
AI Summary
This document outlines a comprehensive IT security implementation plan for John Dough Pizza, addressing the company's need to improve its information security and management. The plan, intended for the Chief Technology Officer (CTO), covers a wide range of topics including the scope, goals, timeline, and associated costs. It details a Security Education, Training, and Awareness (SETA) program, an incident response plan designed to mitigate data breaches, and business continuity and disaster recovery plans. Furthermore, the report discusses organizational structure, and implementation strategies for major tasks such as database security, physical security, and the implementation of security policies like access control, two-factor authentication, and backup procedures. The plan aims to enhance the overall security posture of John Dough Pizza, ensuring the protection of customer data and business operations.

Implementation PLan
CSG3309.2020.TR1.ALL IT Security Management
Group Assignment-
Lecturer- Gaven Henry
CSG3309.2020.TR1.ALL IT Security Management
Group Assignment-
Lecturer- Gaven Henry
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Executive summary.........................................................................................................................3
SCOPE.............................................................................................................................................3
Goal..................................................................................................................................................3
Vision...........................................................................................................................................3
Timeline...........................................................................................................................................4
Costs................................................................................................................................................4
SETA program.................................................................................................................................4
Security Education.......................................................................................................................5
Training........................................................................................................................................5
Awareness....................................................................................................................................5
Incident Response Plan....................................................................................................................5
Data breach..................................................................................................................................6
Preparation...............................................................................................................................6
Identifying and Scoping...........................................................................................................6
Data Access Security...................................................................................................................6
Intelligence gathering..................................................................................................................6
Eradication...................................................................................................................................6
Recovery & review......................................................................................................................6
Continuity plan................................................................................................................................7
Business Continuity Plan.............................................................................................................7
Disaster Recovery Plan................................................................................................................8
Organizational Structure..................................................................................................................9
Implementation for major Tasks in JOHN DOUGH Pizza...........................................................10
Database.....................................................................................................................................10
Physical Security.......................................................................................................................11
Video Recording & Alert System..........................................................................................11
Maintain exterior...................................................................................................................11
Keep valuable safe.................................................................................................................11
Implementing Security Policies.................................................................................................11
Access control policy.............................................................................................................11
Two-factor authentication policy...........................................................................................12
1
Executive summary.........................................................................................................................3
SCOPE.............................................................................................................................................3
Goal..................................................................................................................................................3
Vision...........................................................................................................................................3
Timeline...........................................................................................................................................4
Costs................................................................................................................................................4
SETA program.................................................................................................................................4
Security Education.......................................................................................................................5
Training........................................................................................................................................5
Awareness....................................................................................................................................5
Incident Response Plan....................................................................................................................5
Data breach..................................................................................................................................6
Preparation...............................................................................................................................6
Identifying and Scoping...........................................................................................................6
Data Access Security...................................................................................................................6
Intelligence gathering..................................................................................................................6
Eradication...................................................................................................................................6
Recovery & review......................................................................................................................6
Continuity plan................................................................................................................................7
Business Continuity Plan.............................................................................................................7
Disaster Recovery Plan................................................................................................................8
Organizational Structure..................................................................................................................9
Implementation for major Tasks in JOHN DOUGH Pizza...........................................................10
Database.....................................................................................................................................10
Physical Security.......................................................................................................................11
Video Recording & Alert System..........................................................................................11
Maintain exterior...................................................................................................................11
Keep valuable safe.................................................................................................................11
Implementing Security Policies.................................................................................................11
Access control policy.............................................................................................................11
Two-factor authentication policy...........................................................................................12
1

Backup Policy........................................................................................................................12
Security audit policy..............................................................................................................12
Incident reports policy...........................................................................................................12
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
References.................................................................................................................................13
2
Security audit policy..............................................................................................................12
Incident reports policy...........................................................................................................12
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
References.................................................................................................................................13
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Executive summary
The report is to plan the implementation addressing to improve the Information Security
& Management issues of JOHN DOUGH pizza which is advised to CTO. Starting from the
scope and including goals of the report, timeline for implementation, costs, SETA program,
implementation for major tasks (implement security policy, etc.), incident response plan,
business continuity, disaster recovery plan and organizational structure.
SCOPE
The scope is to implement the plans with goal, time and cost. These plans contain:
-Implementation for major task in JOHN DOUGH
-Incident response plan
-Business Continuity Plan
-Disaster Recovery Plan
-Revised Organizational Structure
Implementation for major task will preventing the JOHN DOUGH from happening same fault.
Goal
JOHN DOUGH pizza planned to achieve this goal within 5 years:
- Maintain the standards chain of pizza
- To grow their business into remote geographic environment
- To apply latest technology system for the efficient pizza ordering and management
system with franchisees
- Use the social media to engage the customers interest in pizza ordering
- Boost the level of IT security for the organization and customer with IT security team and
R&D team
- Disseminate the pizza ordering service to different regions
The goal of the JOHN DOUGH pizza will be easily to implement with the well-structured
organizational structure.
Vision
- Can give number1 experience in pizza ordering online
- Become #1 name in pizza ordering
Timeline
Timeline for implementing the secure the IT system will take over 3 months. Starting
from March 10th,2020 to June 30th,2020. For the training the employees’ phase, it’s from start to
end of the implementation.
3
The report is to plan the implementation addressing to improve the Information Security
& Management issues of JOHN DOUGH pizza which is advised to CTO. Starting from the
scope and including goals of the report, timeline for implementation, costs, SETA program,
implementation for major tasks (implement security policy, etc.), incident response plan,
business continuity, disaster recovery plan and organizational structure.
SCOPE
The scope is to implement the plans with goal, time and cost. These plans contain:
-Implementation for major task in JOHN DOUGH
-Incident response plan
-Business Continuity Plan
-Disaster Recovery Plan
-Revised Organizational Structure
Implementation for major task will preventing the JOHN DOUGH from happening same fault.
Goal
JOHN DOUGH pizza planned to achieve this goal within 5 years:
- Maintain the standards chain of pizza
- To grow their business into remote geographic environment
- To apply latest technology system for the efficient pizza ordering and management
system with franchisees
- Use the social media to engage the customers interest in pizza ordering
- Boost the level of IT security for the organization and customer with IT security team and
R&D team
- Disseminate the pizza ordering service to different regions
The goal of the JOHN DOUGH pizza will be easily to implement with the well-structured
organizational structure.
Vision
- Can give number1 experience in pizza ordering online
- Become #1 name in pizza ordering
Timeline
Timeline for implementing the secure the IT system will take over 3 months. Starting
from March 10th,2020 to June 30th,2020. For the training the employees’ phase, it’s from start to
end of the implementation.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
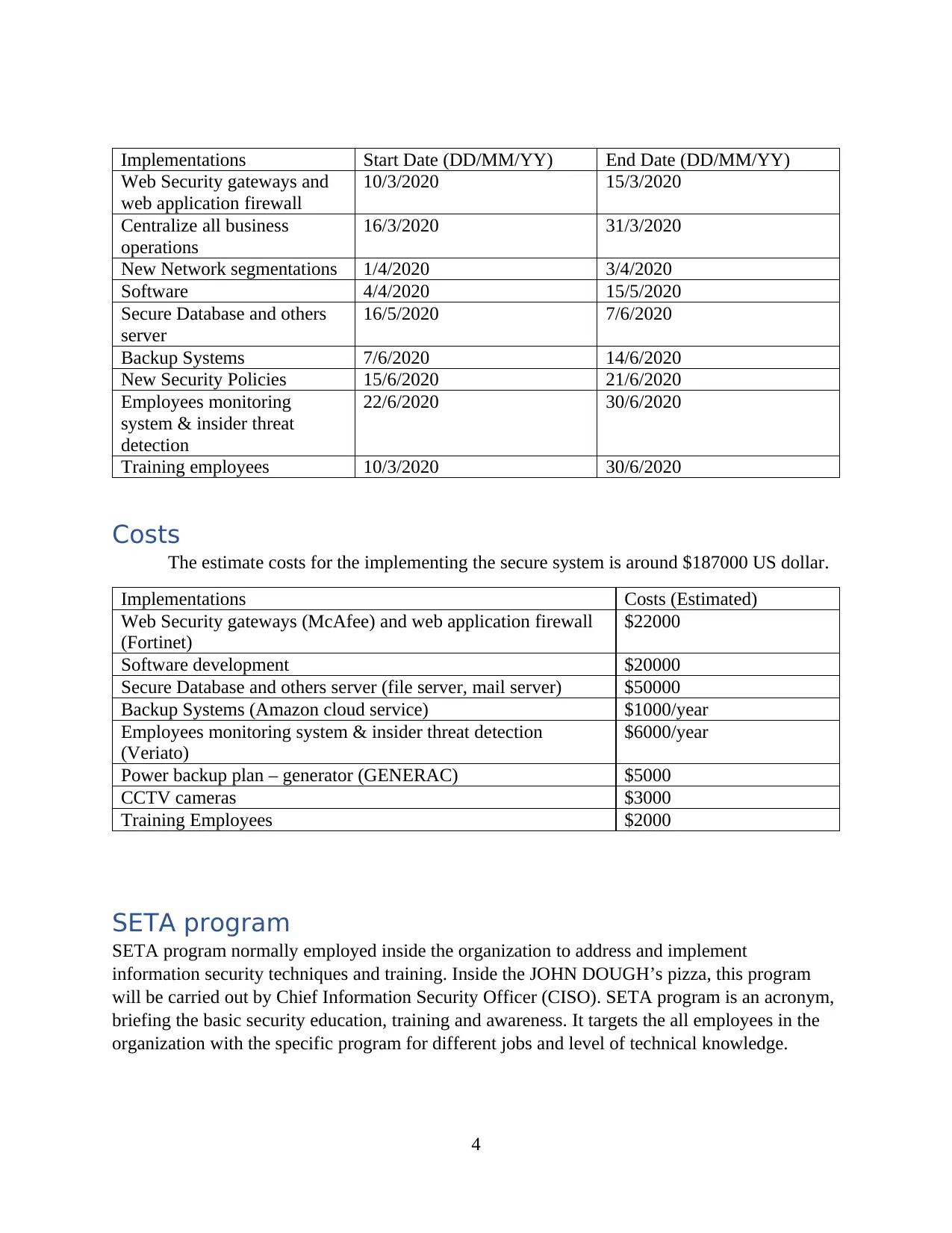
Implementations Start Date (DD/MM/YY) End Date (DD/MM/YY)
Web Security gateways and
web application firewall
10/3/2020 15/3/2020
Centralize all business
operations
16/3/2020 31/3/2020
New Network segmentations 1/4/2020 3/4/2020
Software 4/4/2020 15/5/2020
Secure Database and others
server
16/5/2020 7/6/2020
Backup Systems 7/6/2020 14/6/2020
New Security Policies 15/6/2020 21/6/2020
Employees monitoring
system & insider threat
detection
22/6/2020 30/6/2020
Training employees 10/3/2020 30/6/2020
Costs
The estimate costs for the implementing the secure system is around $187000 US dollar.
Implementations Costs (Estimated)
Web Security gateways (McAfee) and web application firewall
(Fortinet)
$22000
Software development $20000
Secure Database and others server (file server, mail server) $50000
Backup Systems (Amazon cloud service) $1000/year
Employees monitoring system & insider threat detection
(Veriato)
$6000/year
Power backup plan – generator (GENERAC) $5000
CCTV cameras $3000
Training Employees $2000
SETA program
SETA program normally employed inside the organization to address and implement
information security techniques and training. Inside the JOHN DOUGH’s pizza, this program
will be carried out by Chief Information Security Officer (CISO). SETA program is an acronym,
briefing the basic security education, training and awareness. It targets the all employees in the
organization with the specific program for different jobs and level of technical knowledge.
4
Web Security gateways and
web application firewall
10/3/2020 15/3/2020
Centralize all business
operations
16/3/2020 31/3/2020
New Network segmentations 1/4/2020 3/4/2020
Software 4/4/2020 15/5/2020
Secure Database and others
server
16/5/2020 7/6/2020
Backup Systems 7/6/2020 14/6/2020
New Security Policies 15/6/2020 21/6/2020
Employees monitoring
system & insider threat
detection
22/6/2020 30/6/2020
Training employees 10/3/2020 30/6/2020
Costs
The estimate costs for the implementing the secure system is around $187000 US dollar.
Implementations Costs (Estimated)
Web Security gateways (McAfee) and web application firewall
(Fortinet)
$22000
Software development $20000
Secure Database and others server (file server, mail server) $50000
Backup Systems (Amazon cloud service) $1000/year
Employees monitoring system & insider threat detection
(Veriato)
$6000/year
Power backup plan – generator (GENERAC) $5000
CCTV cameras $3000
Training Employees $2000
SETA program
SETA program normally employed inside the organization to address and implement
information security techniques and training. Inside the JOHN DOUGH’s pizza, this program
will be carried out by Chief Information Security Officer (CISO). SETA program is an acronym,
briefing the basic security education, training and awareness. It targets the all employees in the
organization with the specific program for different jobs and level of technical knowledge.
4

Purpose of the SETA program is to enhance the level of the security by educating the employee
with detailed knowledge. The SETA program will be boosted to implementing the goal the and
security needs.
CISO will be responsible for this program and can be done by doing three steps:
1. Security Education
2. Training
3. Awareness
Security Education
The basic requirement for the technology used organization is Security Education. All the
employees and employers need to understand clearly about the basic security measure. This
branch of the SETA program is designed to educate members of the organization about why the
organization is preparing in the way it has and why the organization responding in the way it
does. Members of the organization can gain sight on how the process develops and achieve
continuous improvement.
Training
The training aims to train the member of the organization on how to react and respond to threats
in specific situations. All the employees and employees including manager should be trained
well because one of the managers in JOHN DOUGH pizza sent an email to entire customers
address book without using BCC. Should train them well about cyber security awareness
priority, password security training & best practices and train them to recognize phishing and
awareness of social engineering and so on.
Awareness
This section aims to teach the member of organization what is security and what employees
should be aware of certain situations. This section offers information about threats and
responses.
Incident Response Plan
Incident response (IR) is the systematic approach to prepare for, detection of incident, incident
occurrence, and recovery from a suspected and experienced cybersecurity breach. Incident
response plan helps to ensure the effective countermeasure to incidents which can help to protect
JOHN DOUGH’s data and reputation. The plan will be estimating the worst from occurring and
if happened it will be helping to reduce the damage of incident. The effective incident response
plan must be placed to prevent and respond to incident.
To act quickly and professionally while incident is unfolding. We need to implement the
response plan with the IR team. IR team must be cross sectionally connected with business and
technical experts to be informational and take action on the possible incidents.
5
with detailed knowledge. The SETA program will be boosted to implementing the goal the and
security needs.
CISO will be responsible for this program and can be done by doing three steps:
1. Security Education
2. Training
3. Awareness
Security Education
The basic requirement for the technology used organization is Security Education. All the
employees and employers need to understand clearly about the basic security measure. This
branch of the SETA program is designed to educate members of the organization about why the
organization is preparing in the way it has and why the organization responding in the way it
does. Members of the organization can gain sight on how the process develops and achieve
continuous improvement.
Training
The training aims to train the member of the organization on how to react and respond to threats
in specific situations. All the employees and employees including manager should be trained
well because one of the managers in JOHN DOUGH pizza sent an email to entire customers
address book without using BCC. Should train them well about cyber security awareness
priority, password security training & best practices and train them to recognize phishing and
awareness of social engineering and so on.
Awareness
This section aims to teach the member of organization what is security and what employees
should be aware of certain situations. This section offers information about threats and
responses.
Incident Response Plan
Incident response (IR) is the systematic approach to prepare for, detection of incident, incident
occurrence, and recovery from a suspected and experienced cybersecurity breach. Incident
response plan helps to ensure the effective countermeasure to incidents which can help to protect
JOHN DOUGH’s data and reputation. The plan will be estimating the worst from occurring and
if happened it will be helping to reduce the damage of incident. The effective incident response
plan must be placed to prevent and respond to incident.
To act quickly and professionally while incident is unfolding. We need to implement the
response plan with the IR team. IR team must be cross sectionally connected with business and
technical experts to be informational and take action on the possible incidents.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Data breach
Preparation
This phase needs to ensure the employees to be well-trained and the important
(necessary) technology need to be implemented. Data Backup plans must be taken, and the data
breaches also must be conducted and evaluate the effectiveness of plan and Computer Incident
Response Team (CIRT).
Identifying and Scoping
The company need to be detecting the security incidents that require the CIRT as soon as
possible during the incident by implementing and using the right technologies and tools (e.g.
should use Network Traffic Analysis and Endpoint detection of response to detect the suspicious
behaviors.)
Data Access Security
The company also need to find and identify the person who has accessed the sensitive
data or critical data and assets, need to know where those data are located and when the data and
assets are being accessed. For example, LepideAuditor suite in file server provides the real time
information of who has accessed to which data, and what time and changes.
Intelligence gathering
Intelligence gathering contains threats to prevent the damage and gather the information
about the incidents as much as possible. As mentioned above about the LepideAuditor suite, it
shows the history of events which took place before incidents and generates several reports and
that can use for the legal satisfy compliance requirements and potential legal proceedings.
Eradication
After the threats to the system has been identified, contained, analyzed and broke down,
need to remove the actual threat/s from the network system and reestablish the system
framework to a functional. All compromised credentials must be investigated, reviewed and
reset.
Recovery & review
In this phase, all the frameworks and systems are reestablished in the production and
need to monitor which they are working functional and showing no signs about the system
compromises. Computer Incident Response Team (CIRT) must review overall and documents all
the issues during the incidents also include the suggestions for the incident and how to resolve
the future incidents.
6
Preparation
This phase needs to ensure the employees to be well-trained and the important
(necessary) technology need to be implemented. Data Backup plans must be taken, and the data
breaches also must be conducted and evaluate the effectiveness of plan and Computer Incident
Response Team (CIRT).
Identifying and Scoping
The company need to be detecting the security incidents that require the CIRT as soon as
possible during the incident by implementing and using the right technologies and tools (e.g.
should use Network Traffic Analysis and Endpoint detection of response to detect the suspicious
behaviors.)
Data Access Security
The company also need to find and identify the person who has accessed the sensitive
data or critical data and assets, need to know where those data are located and when the data and
assets are being accessed. For example, LepideAuditor suite in file server provides the real time
information of who has accessed to which data, and what time and changes.
Intelligence gathering
Intelligence gathering contains threats to prevent the damage and gather the information
about the incidents as much as possible. As mentioned above about the LepideAuditor suite, it
shows the history of events which took place before incidents and generates several reports and
that can use for the legal satisfy compliance requirements and potential legal proceedings.
Eradication
After the threats to the system has been identified, contained, analyzed and broke down,
need to remove the actual threat/s from the network system and reestablish the system
framework to a functional. All compromised credentials must be investigated, reviewed and
reset.
Recovery & review
In this phase, all the frameworks and systems are reestablished in the production and
need to monitor which they are working functional and showing no signs about the system
compromises. Computer Incident Response Team (CIRT) must review overall and documents all
the issues during the incidents also include the suggestions for the incident and how to resolve
the future incidents.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
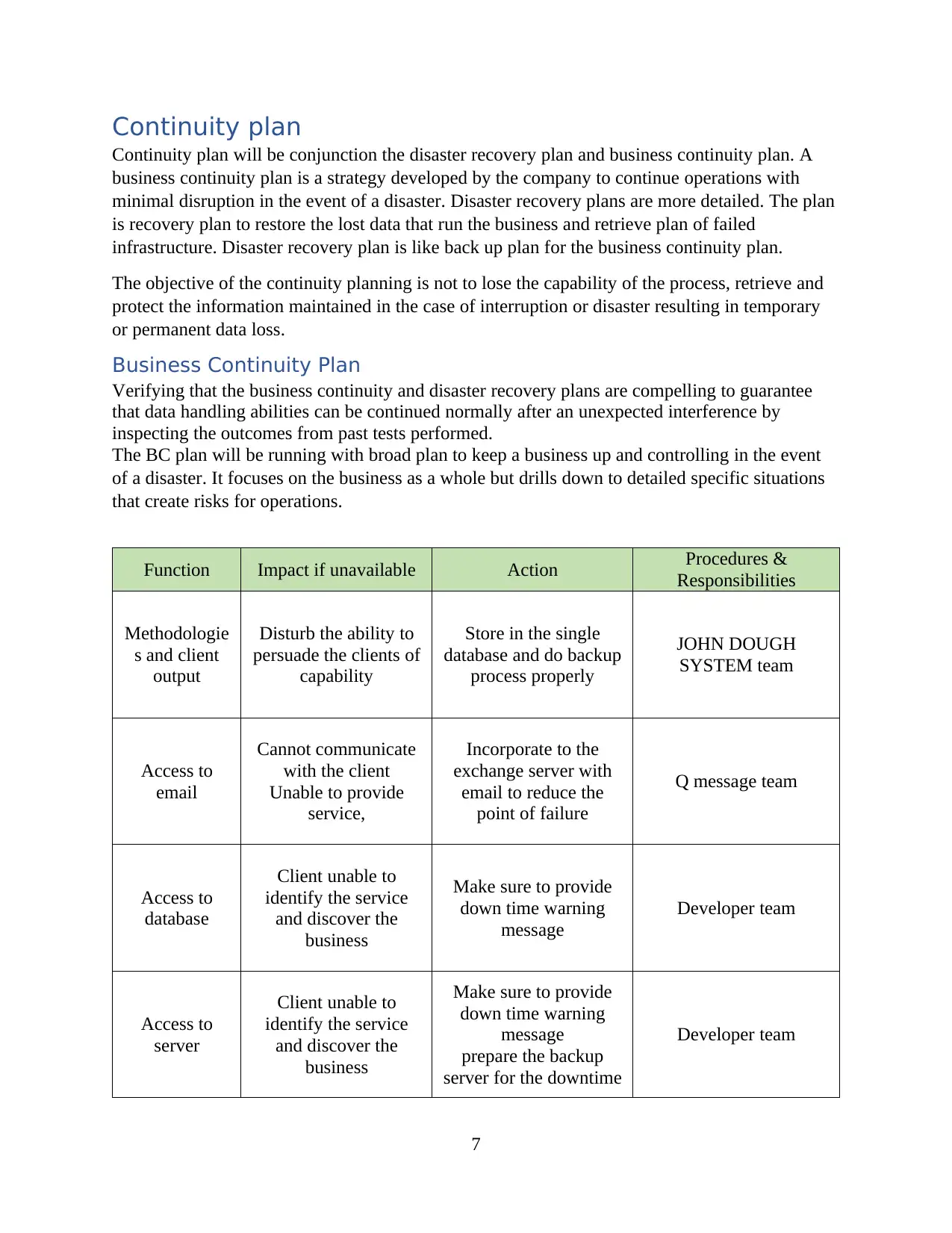
Continuity plan
Continuity plan will be conjunction the disaster recovery plan and business continuity plan. A
business continuity plan is a strategy developed by the company to continue operations with
minimal disruption in the event of a disaster. Disaster recovery plans are more detailed. The plan
is recovery plan to restore the lost data that run the business and retrieve plan of failed
infrastructure. Disaster recovery plan is like back up plan for the business continuity plan.
The objective of the continuity planning is not to lose the capability of the process, retrieve and
protect the information maintained in the case of interruption or disaster resulting in temporary
or permanent data loss.
Business Continuity Plan
Verifying that the business continuity and disaster recovery plans are compelling to guarantee
that data handling abilities can be continued normally after an unexpected interference by
inspecting the outcomes from past tests performed.
The BC plan will be running with broad plan to keep a business up and controlling in the event
of a disaster. It focuses on the business as a whole but drills down to detailed specific situations
that create risks for operations.
Function Impact if unavailable Action Procedures &
Responsibilities
Methodologie
s and client
output
Disturb the ability to
persuade the clients of
capability
Store in the single
database and do backup
process properly
JOHN DOUGH
SYSTEM team
Access to
email
Cannot communicate
with the client
Unable to provide
service,
Incorporate to the
exchange server with
email to reduce the
point of failure
Q message team
Access to
database
Client unable to
identify the service
and discover the
business
Make sure to provide
down time warning
message
Developer team
Access to
server
Client unable to
identify the service
and discover the
business
Make sure to provide
down time warning
message
prepare the backup
server for the downtime
Developer team
7
Continuity plan will be conjunction the disaster recovery plan and business continuity plan. A
business continuity plan is a strategy developed by the company to continue operations with
minimal disruption in the event of a disaster. Disaster recovery plans are more detailed. The plan
is recovery plan to restore the lost data that run the business and retrieve plan of failed
infrastructure. Disaster recovery plan is like back up plan for the business continuity plan.
The objective of the continuity planning is not to lose the capability of the process, retrieve and
protect the information maintained in the case of interruption or disaster resulting in temporary
or permanent data loss.
Business Continuity Plan
Verifying that the business continuity and disaster recovery plans are compelling to guarantee
that data handling abilities can be continued normally after an unexpected interference by
inspecting the outcomes from past tests performed.
The BC plan will be running with broad plan to keep a business up and controlling in the event
of a disaster. It focuses on the business as a whole but drills down to detailed specific situations
that create risks for operations.
Function Impact if unavailable Action Procedures &
Responsibilities
Methodologie
s and client
output
Disturb the ability to
persuade the clients of
capability
Store in the single
database and do backup
process properly
JOHN DOUGH
SYSTEM team
Access to
Cannot communicate
with the client
Unable to provide
service,
Incorporate to the
exchange server with
email to reduce the
point of failure
Q message team
Access to
database
Client unable to
identify the service
and discover the
business
Make sure to provide
down time warning
message
Developer team
Access to
server
Client unable to
identify the service
and discover the
business
Make sure to provide
down time warning
message
prepare the backup
server for the downtime
Developer team
7
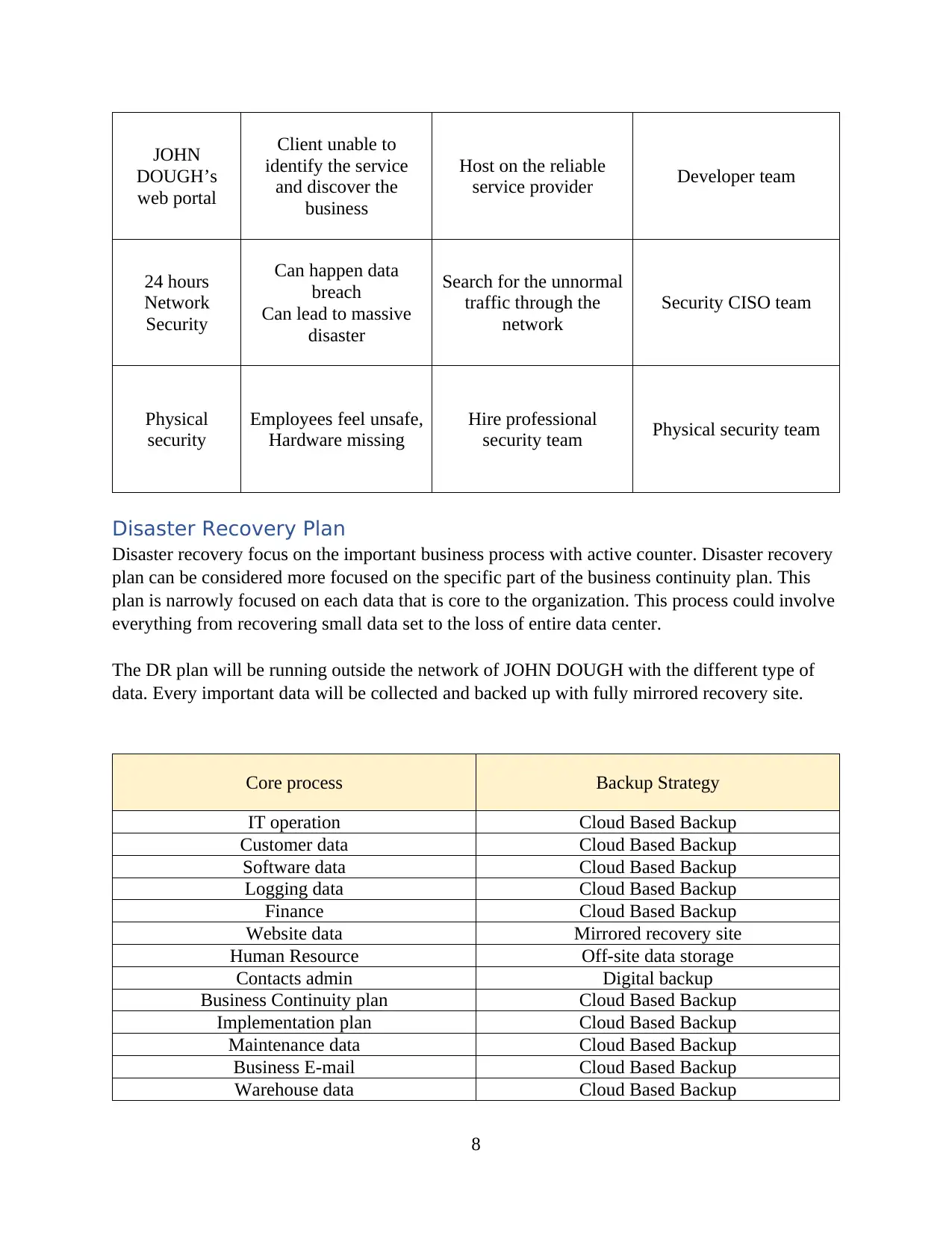
JOHN
DOUGH’s
web portal
Client unable to
identify the service
and discover the
business
Host on the reliable
service provider Developer team
24 hours
Network
Security
Can happen data
breach
Can lead to massive
disaster
Search for the unnormal
traffic through the
network
Security CISO team
Physical
security
Employees feel unsafe,
Hardware missing
Hire professional
security team Physical security team
Disaster Recovery Plan
Disaster recovery focus on the important business process with active counter. Disaster recovery
plan can be considered more focused on the specific part of the business continuity plan. This
plan is narrowly focused on each data that is core to the organization. This process could involve
everything from recovering small data set to the loss of entire data center.
The DR plan will be running outside the network of JOHN DOUGH with the different type of
data. Every important data will be collected and backed up with fully mirrored recovery site.
Core process Backup Strategy
IT operation Cloud Based Backup
Customer data Cloud Based Backup
Software data Cloud Based Backup
Logging data Cloud Based Backup
Finance Cloud Based Backup
Website data Mirrored recovery site
Human Resource Off-site data storage
Contacts admin Digital backup
Business Continuity plan Cloud Based Backup
Implementation plan Cloud Based Backup
Maintenance data Cloud Based Backup
Business E-mail Cloud Based Backup
Warehouse data Cloud Based Backup
8
DOUGH’s
web portal
Client unable to
identify the service
and discover the
business
Host on the reliable
service provider Developer team
24 hours
Network
Security
Can happen data
breach
Can lead to massive
disaster
Search for the unnormal
traffic through the
network
Security CISO team
Physical
security
Employees feel unsafe,
Hardware missing
Hire professional
security team Physical security team
Disaster Recovery Plan
Disaster recovery focus on the important business process with active counter. Disaster recovery
plan can be considered more focused on the specific part of the business continuity plan. This
plan is narrowly focused on each data that is core to the organization. This process could involve
everything from recovering small data set to the loss of entire data center.
The DR plan will be running outside the network of JOHN DOUGH with the different type of
data. Every important data will be collected and backed up with fully mirrored recovery site.
Core process Backup Strategy
IT operation Cloud Based Backup
Customer data Cloud Based Backup
Software data Cloud Based Backup
Logging data Cloud Based Backup
Finance Cloud Based Backup
Website data Mirrored recovery site
Human Resource Off-site data storage
Contacts admin Digital backup
Business Continuity plan Cloud Based Backup
Implementation plan Cloud Based Backup
Maintenance data Cloud Based Backup
Business E-mail Cloud Based Backup
Warehouse data Cloud Based Backup
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
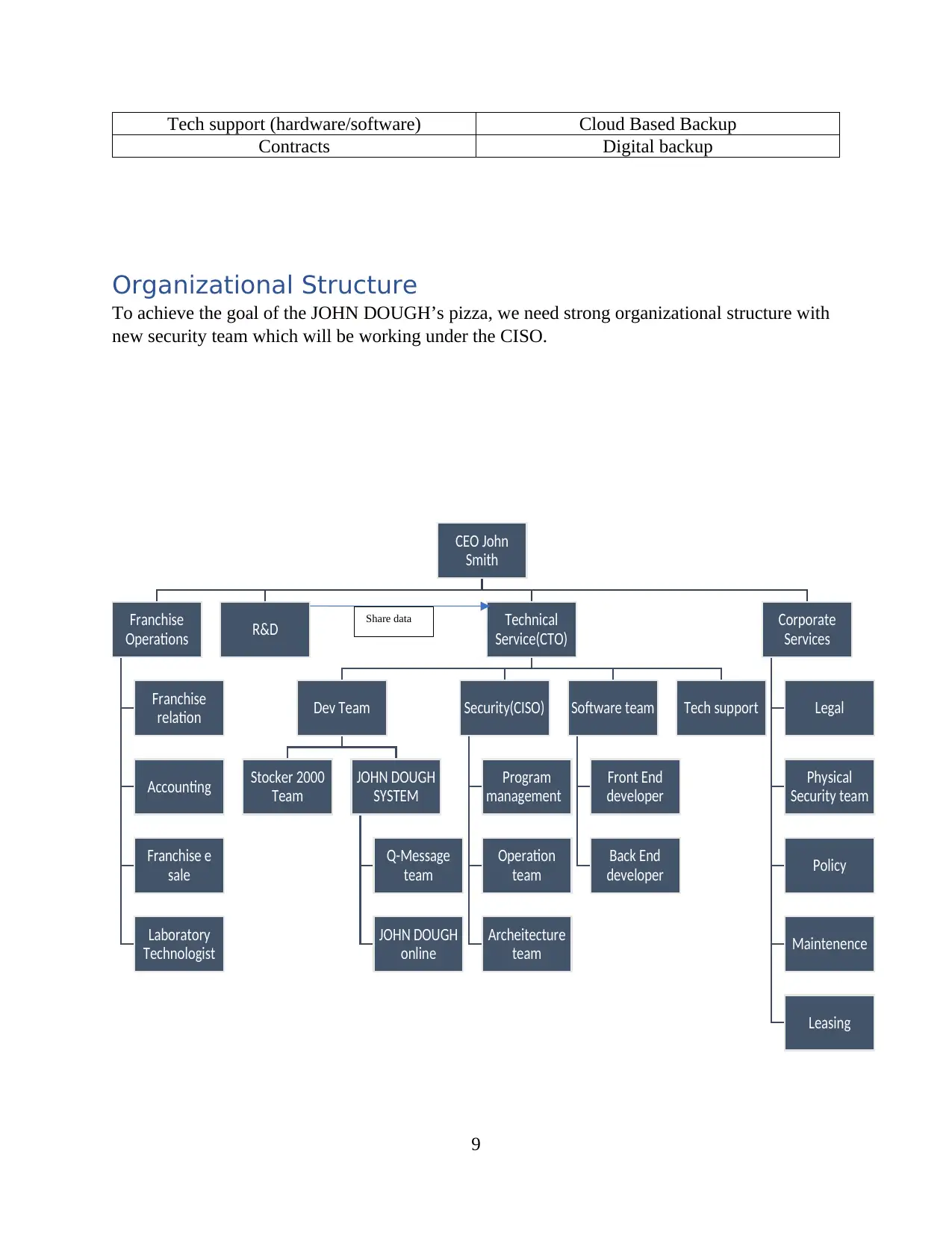
Tech support (hardware/software) Cloud Based Backup
Contracts Digital backup
Organizational Structure
To achieve the goal of the JOHN DOUGH’s pizza, we need strong organizational structure with
new security team which will be working under the CISO.
9
CEO John
Smith
Franchise
Operations
Franchise
relation
Accounting
Franchise e
sale
Laboratory
Technologist
R&D Technical
Service(CTO)
Dev Team
Stocker 2000
Team
JOHN DOUGH
SYSTEM
Q-Message
team
JOHN DOUGH
online
Security(CISO)
Program
management
Operation
team
Archeitecture
team
Software team
Front End
developer
Back End
developer
Tech support
Corporate
Services
Legal
Physical
Security team
Policy
Maintenence
Leasing
Share data
Contracts Digital backup
Organizational Structure
To achieve the goal of the JOHN DOUGH’s pizza, we need strong organizational structure with
new security team which will be working under the CISO.
9
CEO John
Smith
Franchise
Operations
Franchise
relation
Accounting
Franchise e
sale
Laboratory
Technologist
R&D Technical
Service(CTO)
Dev Team
Stocker 2000
Team
JOHN DOUGH
SYSTEM
Q-Message
team
JOHN DOUGH
online
Security(CISO)
Program
management
Operation
team
Archeitecture
team
Software team
Front End
developer
Back End
developer
Tech support
Corporate
Services
Legal
Physical
Security team
Policy
Maintenence
Leasing
Share data
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Implementation for major Tasks in JOHN DOUGH Pizza
Database
Database protection & security plays as an important role in a company. Since Database
was breached at John Dough Pizza company in 2012 and all the customers’ orders and sale
histories, this make the company more challenge regarding to increase the security of database.
Implementation steps for MSSQL database are as follow.
- Put the server in restricted network segment (using VLAN) so that only authorized
network traffic can pass to the database server.
- Correct DB installation: MSSQL offers a lot of additional features. By removing the
features that don’t need for current system, can reduce the possibility of exploitations.
- Keep updated: MSSQL regularly patch the vulnerabilities and the administrator must
always keep updated. This way can prevent most vulnerabilities to attack.
- Restrict DB processes and traffic: MSSQL is sometimes run as an administrator
account or local system that allows the database processes which includes full access
and command shell interfaces (e.g. xp_cmdshell). It should be run with non-
administrator account with only few privileges. Allow only the SQL traffic to and
from designated IPs so that malicious users cannot harm the server and they will need
to connect directly to the server from the secure client front end web application.
- Set strong(unpredictable) admin password, monitor the login logging audits, secure
the backup data,
Physical Security
A burglary case was happened, and PC of franchise was stolen in 2012 at JOHN DOUGH
Pizza. This phase is also quite important and big challenge to the company. Here are some ways
to preventing burglaries.
Video Recording & Alert System
This is the best way to protect the company property against burglary. Alarm & CCTV
camera systems involve the protection of perimeter and area of important objects. Perimeter
covers the outside the surface of the building and area protection covers the entire objects inside
the building. CCTV technologies are keep improving and can help to record the videos digitally
to hard drive and it helps to catch the thief of burglary and may retrieve the properties.
Maintain exterior
Thieves and burglaries like to work under the darkness, one of the most effective way to
deterrence against crime. Trash dumpsters, vehicles and overgrown grass or shrubbery near the
building may provide good cover for them. Keeping the tress away from the doors and windows
can minimize the hiding places around the buildings.
10
Database
Database protection & security plays as an important role in a company. Since Database
was breached at John Dough Pizza company in 2012 and all the customers’ orders and sale
histories, this make the company more challenge regarding to increase the security of database.
Implementation steps for MSSQL database are as follow.
- Put the server in restricted network segment (using VLAN) so that only authorized
network traffic can pass to the database server.
- Correct DB installation: MSSQL offers a lot of additional features. By removing the
features that don’t need for current system, can reduce the possibility of exploitations.
- Keep updated: MSSQL regularly patch the vulnerabilities and the administrator must
always keep updated. This way can prevent most vulnerabilities to attack.
- Restrict DB processes and traffic: MSSQL is sometimes run as an administrator
account or local system that allows the database processes which includes full access
and command shell interfaces (e.g. xp_cmdshell). It should be run with non-
administrator account with only few privileges. Allow only the SQL traffic to and
from designated IPs so that malicious users cannot harm the server and they will need
to connect directly to the server from the secure client front end web application.
- Set strong(unpredictable) admin password, monitor the login logging audits, secure
the backup data,
Physical Security
A burglary case was happened, and PC of franchise was stolen in 2012 at JOHN DOUGH
Pizza. This phase is also quite important and big challenge to the company. Here are some ways
to preventing burglaries.
Video Recording & Alert System
This is the best way to protect the company property against burglary. Alarm & CCTV
camera systems involve the protection of perimeter and area of important objects. Perimeter
covers the outside the surface of the building and area protection covers the entire objects inside
the building. CCTV technologies are keep improving and can help to record the videos digitally
to hard drive and it helps to catch the thief of burglary and may retrieve the properties.
Maintain exterior
Thieves and burglaries like to work under the darkness, one of the most effective way to
deterrence against crime. Trash dumpsters, vehicles and overgrown grass or shrubbery near the
building may provide good cover for them. Keeping the tress away from the doors and windows
can minimize the hiding places around the buildings.
10

Keep valuable safe
Put the large amount of money in bank as soon as possible or in safe deposit box. High
value or important merchandise should not be left in the unsecure place during the non-business
hour.
Implementing Security Policies
Access control policy
Access control policy is one of the most significant policy for every business. To know
who access should has to what comes under this strategy or policy. This turns out to be
considerably increasingly significant because of the human element who often make intentional
or unintentional to occur data breaches. Social Engineering is the biggest threat that organization
face today. Role based access control is regularly employed and utilized in enterprises where
many roles are only required to have access to functionality which is related to their works or
jobs.
Two-factor authentication policy
By using two-factor authentication in IT system, it can mitigate the security risks of data
breach because it denies all the illegal account access. Nowadays, SMS two-factor authentication
is not that much secure in many cases. Using TOPT (Time-based One Time Password) & HOPT
(HMAC-Based One Time Password) are better options for OPT based two-factor authentication.
Backup Policy
Periodic Backup whether using Cloud service or External HDDs is very important.
Ransomware like Wannacry can encrypt entire data on the infected machines. Most of the people
who didn’t do backup would lose all the data and effect the negative impacts for them.
Security audit policy
Security Events such as account logon, directory service access, account management,
policy change, privilege use, process tracking, etc. can be audited. If there is no auditors in
JOHN DOUGH pizza company, there are some experts auditors available for hire.
Incident reports policy
Incident report is used to rescue in the disaster management. JOHN DOUGH pizza
company should make the detailed policies about the incident reports and the employees also
know how to prevent and handle the threats and situation if happens again.
11
Put the large amount of money in bank as soon as possible or in safe deposit box. High
value or important merchandise should not be left in the unsecure place during the non-business
hour.
Implementing Security Policies
Access control policy
Access control policy is one of the most significant policy for every business. To know
who access should has to what comes under this strategy or policy. This turns out to be
considerably increasingly significant because of the human element who often make intentional
or unintentional to occur data breaches. Social Engineering is the biggest threat that organization
face today. Role based access control is regularly employed and utilized in enterprises where
many roles are only required to have access to functionality which is related to their works or
jobs.
Two-factor authentication policy
By using two-factor authentication in IT system, it can mitigate the security risks of data
breach because it denies all the illegal account access. Nowadays, SMS two-factor authentication
is not that much secure in many cases. Using TOPT (Time-based One Time Password) & HOPT
(HMAC-Based One Time Password) are better options for OPT based two-factor authentication.
Backup Policy
Periodic Backup whether using Cloud service or External HDDs is very important.
Ransomware like Wannacry can encrypt entire data on the infected machines. Most of the people
who didn’t do backup would lose all the data and effect the negative impacts for them.
Security audit policy
Security Events such as account logon, directory service access, account management,
policy change, privilege use, process tracking, etc. can be audited. If there is no auditors in
JOHN DOUGH pizza company, there are some experts auditors available for hire.
Incident reports policy
Incident report is used to rescue in the disaster management. JOHN DOUGH pizza
company should make the detailed policies about the incident reports and the employees also
know how to prevent and handle the threats and situation if happens again.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





