Healthcare Data Security
VerifiedAdded on 2022/11/02
|8
|1648
|70
AI Summary
This article discusses the recent Australian healthcare data breach, measures to avoid data breaching, loss of healthcare data, and literature review on cybersecurity in healthcare. It emphasizes the need for security risk assessment, employee education, data encryption, and modernization of IT structure to prevent healthcare data breaches.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: HEALTHCARE DATA SECURITY
Healthcare Data Security
Name of the Student:
Name of the University:
Author’s Note:
Healthcare Data Security
Name of the Student:
Name of the University:
Author’s Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1HEALTHCARE DATA SECURITY
Summary of a recent Australian Healthcare data breach
Australian Healthcare data breach occurred in Cabrini Hospital in Melbourne in the
Melbourne Heart Group department. This data breach crime occurred on 21st of February
2019. The cyber fraudsters had accessed almost 15000 medical files of patients. The medical
professionals were not able to access the files of some patients for almost three weeks. The
cyber-attack had crippled the server and corrupted the data in the system. The files were
scrambled. The records are believed to be hacked either from North Korea or Russia but it is
not fully confirmed. The server of the clinic was hacked with malware and the fraudster
demanded payment in cryptocurrency in return to share the password in order to break
encryption.
Fig 1: The probable mode of breach that occurred in Cabrini Hospital (Martin, Kinross &
Hankin, 2017)
Measures to avoid data breaching in future
The healthcare industry is indeed vulnerable to the cyber criminals hence it is important to
prevent the incidents of breaching of the healthcare data. This is because the people working
in the health care sectors are party to immense amounts of information of the patient which is
highly sensitive and may include medical records (Argaw et al., 2019). These sectors are
Summary of a recent Australian Healthcare data breach
Australian Healthcare data breach occurred in Cabrini Hospital in Melbourne in the
Melbourne Heart Group department. This data breach crime occurred on 21st of February
2019. The cyber fraudsters had accessed almost 15000 medical files of patients. The medical
professionals were not able to access the files of some patients for almost three weeks. The
cyber-attack had crippled the server and corrupted the data in the system. The files were
scrambled. The records are believed to be hacked either from North Korea or Russia but it is
not fully confirmed. The server of the clinic was hacked with malware and the fraudster
demanded payment in cryptocurrency in return to share the password in order to break
encryption.
Fig 1: The probable mode of breach that occurred in Cabrini Hospital (Martin, Kinross &
Hankin, 2017)
Measures to avoid data breaching in future
The healthcare industry is indeed vulnerable to the cyber criminals hence it is important to
prevent the incidents of breaching of the healthcare data. This is because the people working
in the health care sectors are party to immense amounts of information of the patient which is
highly sensitive and may include medical records (Argaw et al., 2019). These sectors are

2HEALTHCARE DATA SECURITY
considered to be goldmines of valuable information. Therefore, the need arises to securely
protect the information. The security measures in the healthcare industry are indeed poor and
hence breaching of these valuable data is considered as an inevitable outcome (Martin et al.,
2017).
The health care industries should conduct security risk assessment annually that should
account for the changes that occur in a healthcare in a year like introducing new systems,
enhancement of the infrastructure, restructuring the organisation as well as employee
turnover. These incidents can promote the occurrence of new vulnerabilities (Gupta, Agrawal
& Yamaguchi. 2016). The employees working in the health care sector should be educated
about the importance of data security since lack of awareness can lead to breaching of the
data. This would promote enforcement of the best practices to keep the data secure in the
workplace. The devices and records should be monitored at continuous intervals. Breaching
is often the result of stealing valuable data from home, office or vehicle (Chowdhury et al.,
2018). Encryption of the data is one of the best measures to prevent healthcare data breach.
But there are significant challenges to encryption. The access to patient information should be
restricted. Promoting subnet wireless networks also aids in preventing data breach at health
care centres. The information technology structure should also be modernized (Gupta,
Agrawal & Yamaguchi. 2016).
considered to be goldmines of valuable information. Therefore, the need arises to securely
protect the information. The security measures in the healthcare industry are indeed poor and
hence breaching of these valuable data is considered as an inevitable outcome (Martin et al.,
2017).
The health care industries should conduct security risk assessment annually that should
account for the changes that occur in a healthcare in a year like introducing new systems,
enhancement of the infrastructure, restructuring the organisation as well as employee
turnover. These incidents can promote the occurrence of new vulnerabilities (Gupta, Agrawal
& Yamaguchi. 2016). The employees working in the health care sector should be educated
about the importance of data security since lack of awareness can lead to breaching of the
data. This would promote enforcement of the best practices to keep the data secure in the
workplace. The devices and records should be monitored at continuous intervals. Breaching
is often the result of stealing valuable data from home, office or vehicle (Chowdhury et al.,
2018). Encryption of the data is one of the best measures to prevent healthcare data breach.
But there are significant challenges to encryption. The access to patient information should be
restricted. Promoting subnet wireless networks also aids in preventing data breach at health
care centres. The information technology structure should also be modernized (Gupta,
Agrawal & Yamaguchi. 2016).
3HEALTHCARE DATA SECURITY
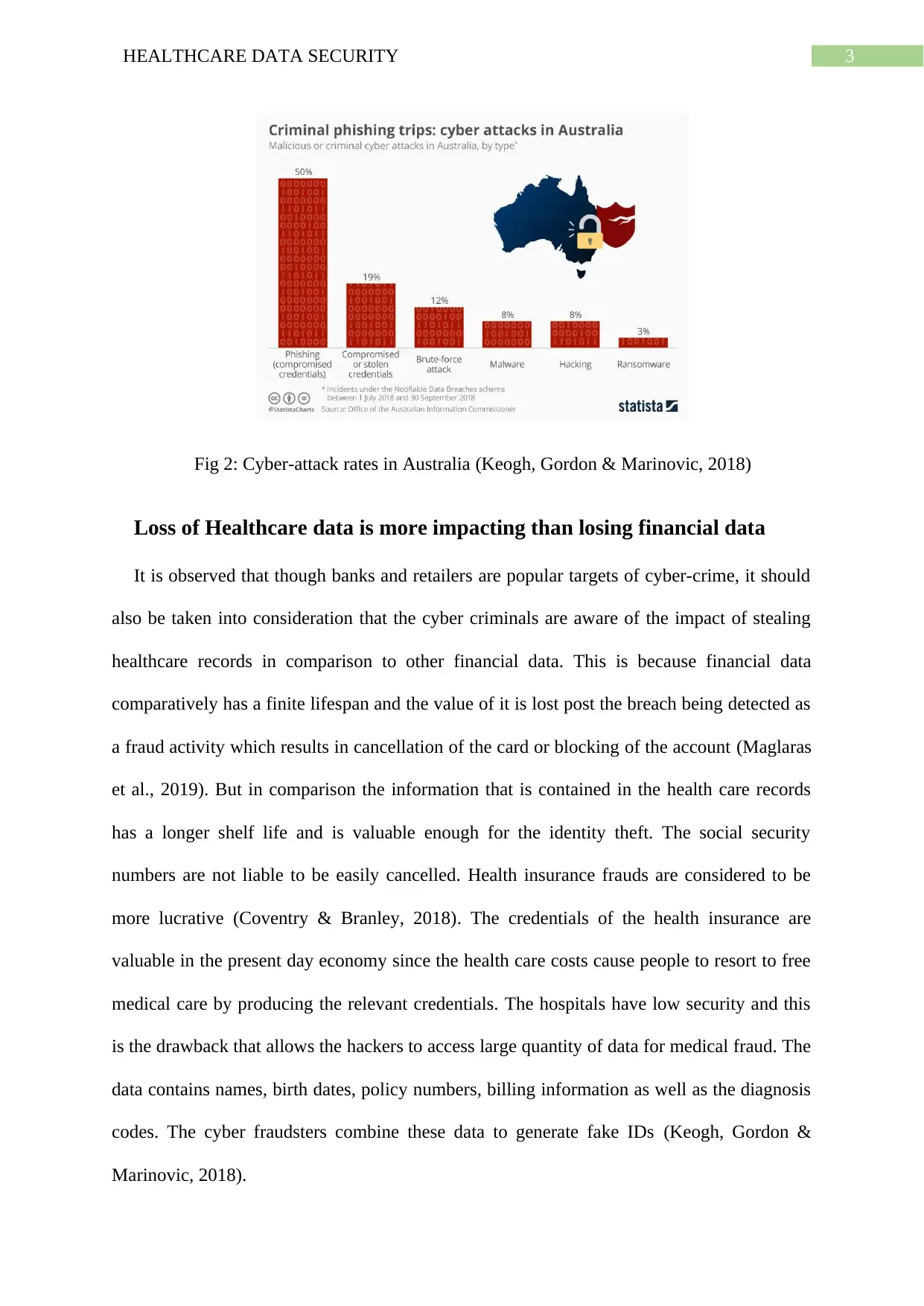
Fig 2: Cyber-attack rates in Australia (Keogh, Gordon & Marinovic, 2018)
Loss of Healthcare data is more impacting than losing financial data
It is observed that though banks and retailers are popular targets of cyber-crime, it should
also be taken into consideration that the cyber criminals are aware of the impact of stealing
healthcare records in comparison to other financial data. This is because financial data
comparatively has a finite lifespan and the value of it is lost post the breach being detected as
a fraud activity which results in cancellation of the card or blocking of the account (Maglaras
et al., 2019). But in comparison the information that is contained in the health care records
has a longer shelf life and is valuable enough for the identity theft. The social security
numbers are not liable to be easily cancelled. Health insurance frauds are considered to be
more lucrative (Coventry & Branley, 2018). The credentials of the health insurance are
valuable in the present day economy since the health care costs cause people to resort to free
medical care by producing the relevant credentials. The hospitals have low security and this
is the drawback that allows the hackers to access large quantity of data for medical fraud. The
data contains names, birth dates, policy numbers, billing information as well as the diagnosis
codes. The cyber fraudsters combine these data to generate fake IDs (Keogh, Gordon &
Marinovic, 2018).
Fig 2: Cyber-attack rates in Australia (Keogh, Gordon & Marinovic, 2018)
Loss of Healthcare data is more impacting than losing financial data
It is observed that though banks and retailers are popular targets of cyber-crime, it should
also be taken into consideration that the cyber criminals are aware of the impact of stealing
healthcare records in comparison to other financial data. This is because financial data
comparatively has a finite lifespan and the value of it is lost post the breach being detected as
a fraud activity which results in cancellation of the card or blocking of the account (Maglaras
et al., 2019). But in comparison the information that is contained in the health care records
has a longer shelf life and is valuable enough for the identity theft. The social security
numbers are not liable to be easily cancelled. Health insurance frauds are considered to be
more lucrative (Coventry & Branley, 2018). The credentials of the health insurance are
valuable in the present day economy since the health care costs cause people to resort to free
medical care by producing the relevant credentials. The hospitals have low security and this
is the drawback that allows the hackers to access large quantity of data for medical fraud. The
data contains names, birth dates, policy numbers, billing information as well as the diagnosis
codes. The cyber fraudsters combine these data to generate fake IDs (Keogh, Gordon &
Marinovic, 2018).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4HEALTHCARE DATA SECURITY
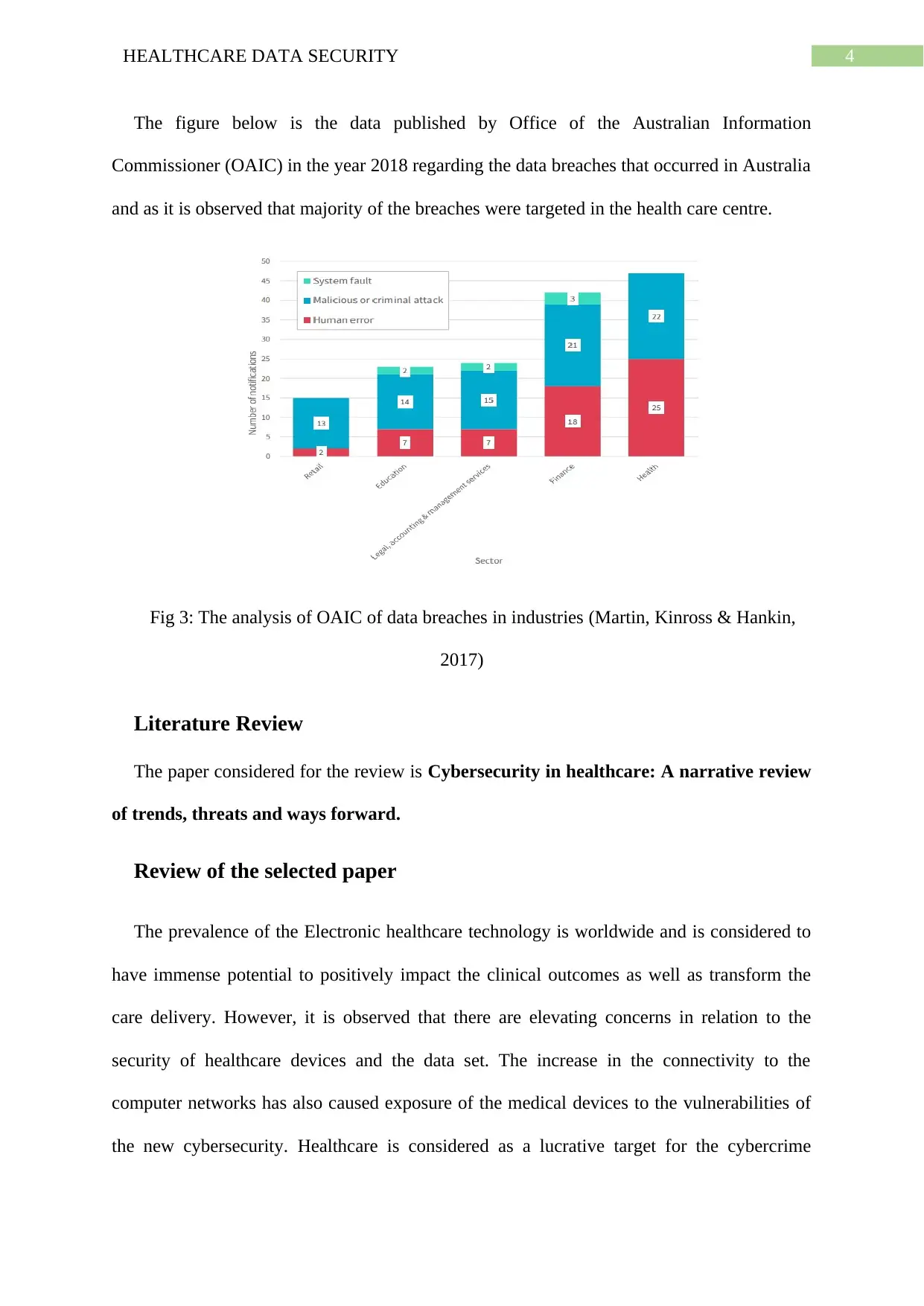
The figure below is the data published by Office of the Australian Information
Commissioner (OAIC) in the year 2018 regarding the data breaches that occurred in Australia
and as it is observed that majority of the breaches were targeted in the health care centre.
Fig 3: The analysis of OAIC of data breaches in industries (Martin, Kinross & Hankin,
2017)
Literature Review
The paper considered for the review is Cybersecurity in healthcare: A narrative review
of trends, threats and ways forward.
Review of the selected paper
The prevalence of the Electronic healthcare technology is worldwide and is considered to
have immense potential to positively impact the clinical outcomes as well as transform the
care delivery. However, it is observed that there are elevating concerns in relation to the
security of healthcare devices and the data set. The increase in the connectivity to the
computer networks has also caused exposure of the medical devices to the vulnerabilities of
the new cybersecurity. Healthcare is considered as a lucrative target for the cybercrime
The figure below is the data published by Office of the Australian Information
Commissioner (OAIC) in the year 2018 regarding the data breaches that occurred in Australia
and as it is observed that majority of the breaches were targeted in the health care centre.
Fig 3: The analysis of OAIC of data breaches in industries (Martin, Kinross & Hankin,
2017)
Literature Review
The paper considered for the review is Cybersecurity in healthcare: A narrative review
of trends, threats and ways forward.
Review of the selected paper
The prevalence of the Electronic healthcare technology is worldwide and is considered to
have immense potential to positively impact the clinical outcomes as well as transform the
care delivery. However, it is observed that there are elevating concerns in relation to the
security of healthcare devices and the data set. The increase in the connectivity to the
computer networks has also caused exposure of the medical devices to the vulnerabilities of
the new cybersecurity. Healthcare is considered as a lucrative target for the cybercrime

5HEALTHCARE DATA SECURITY
essentially because of two fundamental reasons which are healthcare is an excellent source of
valuable data and the defences of the healthcare sector is weak (Martin, Kinross & Hankin,
2017). Cybersecurity breaches consists stealing information on health of the patients as well
as ransomware attacks on hospitals, it can also include attacks on medical devices that are
implanted. Breaches decrease the trust of the clients that is the patient, it can cripple the
health systems and impose a threat to human life. Cybersecurity is also considered critical in
relation to the safety of the patient, even though it has still been lax. New legislation as well
as the regulations are expected to promote change. Hence cybersecurity is becoming an
integral part of the safety of the patient with respect to data breaching but there are changes
that are required in the process flow, human behaviour as well as technology to ensure a
holistic measure to prevent the breaching of data at health care sector (Coventry & Branley,
2018).
Reflection and critic of the chosen article
The journal enforces on the fact that cybersecurity of the hospitals should be a concern of
multidisciplinary groups and also the fact that the security cannot be efficacious without
active involvement of the of different professionals in the hospital. This paper descriptively
discusses the causes of the cyber attack and also suggests several methods by which the
fraudsters can be avoided. The journal had also investigated the funding sources in order to
explore the influence of the companies and the conflicts of interest. The literature study
remains restricted in number with respect to the articles selected. Some of the important
aspects of the cybersecurity like the cloud storage as well as access management has also
been neglected in this journal. The recommendations are indeed available but the journal
lacks standardised best practice methods as well as comprehensive guidelines.
essentially because of two fundamental reasons which are healthcare is an excellent source of
valuable data and the defences of the healthcare sector is weak (Martin, Kinross & Hankin,
2017). Cybersecurity breaches consists stealing information on health of the patients as well
as ransomware attacks on hospitals, it can also include attacks on medical devices that are
implanted. Breaches decrease the trust of the clients that is the patient, it can cripple the
health systems and impose a threat to human life. Cybersecurity is also considered critical in
relation to the safety of the patient, even though it has still been lax. New legislation as well
as the regulations are expected to promote change. Hence cybersecurity is becoming an
integral part of the safety of the patient with respect to data breaching but there are changes
that are required in the process flow, human behaviour as well as technology to ensure a
holistic measure to prevent the breaching of data at health care sector (Coventry & Branley,
2018).
Reflection and critic of the chosen article
The journal enforces on the fact that cybersecurity of the hospitals should be a concern of
multidisciplinary groups and also the fact that the security cannot be efficacious without
active involvement of the of different professionals in the hospital. This paper descriptively
discusses the causes of the cyber attack and also suggests several methods by which the
fraudsters can be avoided. The journal had also investigated the funding sources in order to
explore the influence of the companies and the conflicts of interest. The literature study
remains restricted in number with respect to the articles selected. Some of the important
aspects of the cybersecurity like the cloud storage as well as access management has also
been neglected in this journal. The recommendations are indeed available but the journal
lacks standardised best practice methods as well as comprehensive guidelines.

6HEALTHCARE DATA SECURITY
Reference style: APA
Argaw, S. T., Bempong, N. E., Eshaya-Chauvin, B., & Flahault, A. (2019). The state of
research on cyberattacks against hospitals and available best practice recommendations:
a scoping review. BMC medical informatics and decision making, 19(1), 10.
Chowdhury, M., Jahan, S., Islam, R., & Gao, J. (2018, August). Malware Detection for
Healthcare Data Security. In International Conference on Security and Privacy in
Communication Systems (pp. 407-416). Springer, Cham.
Coventry, L., & Branley, D. (2018). Cybersecurity in healthcare: A narrative review of
trends, threats and ways forward. Maturitas, 113, 48-52.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
Keogh, K., Gordon, C., & Marinovic, P. (2018). Cyber security: Global developments in
cyber security law: is Australia keeping pace?. LSJ: Law Society of NSW Journal, (42),
82.
Maglaras, L., Ferrag, M. A., Derhab, A., Mukherjee, M., Janicke, H., & Rallis, S. (2019).
Threats, Protection and Attribution of Cyber Attacks on Critical Infrastructures. arXiv
preprint arXiv:1901.03899.
Martin, G., Kinross, J., & Hankin, C. (2017). Effective cybersecurity is fundamental to
patient safety. BMJ 2017;357:j2375
Martin, G., Martin, P., Hankin, C., Darzi, A., & Kinross, J. (2017). Cybersecurity and
healthcare: how safe are we?. Bmj, 358, j3179.
Reference style: APA
Argaw, S. T., Bempong, N. E., Eshaya-Chauvin, B., & Flahault, A. (2019). The state of
research on cyberattacks against hospitals and available best practice recommendations:
a scoping review. BMC medical informatics and decision making, 19(1), 10.
Chowdhury, M., Jahan, S., Islam, R., & Gao, J. (2018, August). Malware Detection for
Healthcare Data Security. In International Conference on Security and Privacy in
Communication Systems (pp. 407-416). Springer, Cham.
Coventry, L., & Branley, D. (2018). Cybersecurity in healthcare: A narrative review of
trends, threats and ways forward. Maturitas, 113, 48-52.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
Keogh, K., Gordon, C., & Marinovic, P. (2018). Cyber security: Global developments in
cyber security law: is Australia keeping pace?. LSJ: Law Society of NSW Journal, (42),
82.
Maglaras, L., Ferrag, M. A., Derhab, A., Mukherjee, M., Janicke, H., & Rallis, S. (2019).
Threats, Protection and Attribution of Cyber Attacks on Critical Infrastructures. arXiv
preprint arXiv:1901.03899.
Martin, G., Kinross, J., & Hankin, C. (2017). Effective cybersecurity is fundamental to
patient safety. BMJ 2017;357:j2375
Martin, G., Martin, P., Hankin, C., Darzi, A., & Kinross, J. (2017). Cybersecurity and
healthcare: how safe are we?. Bmj, 358, j3179.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7HEALTHCARE DATA SECURITY
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.
