Security in Healthcare Networks: Threats and Solutions
VerifiedAdded on 2023/06/04
|10
|2403
|154
AI Summary
This article discusses the security issues faced by healthcare networks, including threats from hackers, malware, and internal employees. It also explores potential solutions, such as data encryption, VPNs, and firewalls, to protect patient data and prevent security breaches.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: SECURITY IN HEALTHCARE NETWORKS
Brief explanation of the need of security in Healthcare Networks
Name of the student:
Name of the university:
Author note:
Brief explanation of the need of security in Healthcare Networks
Name of the student:
Name of the university:
Author note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1SECURITY IN HEALTHCARE NETWORKS
Table of Contents
Introduction.................................................................................................................................................2
Literature review.........................................................................................................................................2
Current and future potential threats that Healthcare networks are facing....................................................5
Threats from device compromise............................................................................................................5
Common threats faced by healthcare networks........................................................................................5
Threats from network dynamics..............................................................................................................5
Solution to one of the threats faced by healthcare networks........................................................................5
Conclusion...................................................................................................................................................6
References...................................................................................................................................................7
Table of Contents
Introduction.................................................................................................................................................2
Literature review.........................................................................................................................................2
Current and future potential threats that Healthcare networks are facing....................................................5
Threats from device compromise............................................................................................................5
Common threats faced by healthcare networks........................................................................................5
Threats from network dynamics..............................................................................................................5
Solution to one of the threats faced by healthcare networks........................................................................5
Conclusion...................................................................................................................................................6
References...................................................................................................................................................7

2SECURITY IN HEALTHCARE NETWORKS
Introduction:
This assignment will focus on the security issues that the Healthcare industry face. The industry
has adopted this new application to secure the personal data of the patients. Some of the network-
based applications that the industry is already using is the electronic medical records (EMRs). This
increases the efficiency of communication and collaboration between the patients and the healthcare
units. However, with the adoption of this new technology, security threats are also increasing in the
particular sector. The computer viruses and the hackers are posing great threats to the healthcare
networks. The security issues can be prevented and managed by the help of network security tools. To
protect the network from security breaches, healthcare organisations should frame security policies that
will help the industry to avoid the security issues.
The following paragraphs will deal with a short literature review on healthcare networks and the
critical security issues faced by the industry explaining the architecture of healthcare networks and the
solution to the security issues.
Literature review:
The network architecture consists of three important parts- (1) the Radio Frequency
Identification (RFID) wireless sensor network also called Hybrid Sensing Network (HSN), (2) interface of
the users for visualizing and management data and (3) IoT smart gateway. The network works on a
number of topologies and the gateway plays an important role in protecting the network. The network
architecture makes use of firewalls to protect the network perimeter. Along with firewall, there are
routers that has access to inspect firewall features. The Smart Hospital System (SHS) helps to collect
data regarding temperature, pressure and light conditions from the environment. The protocols that are
used to in healthcare networks are UDP, TCP and HTTP [1].
Introduction:
This assignment will focus on the security issues that the Healthcare industry face. The industry
has adopted this new application to secure the personal data of the patients. Some of the network-
based applications that the industry is already using is the electronic medical records (EMRs). This
increases the efficiency of communication and collaboration between the patients and the healthcare
units. However, with the adoption of this new technology, security threats are also increasing in the
particular sector. The computer viruses and the hackers are posing great threats to the healthcare
networks. The security issues can be prevented and managed by the help of network security tools. To
protect the network from security breaches, healthcare organisations should frame security policies that
will help the industry to avoid the security issues.
The following paragraphs will deal with a short literature review on healthcare networks and the
critical security issues faced by the industry explaining the architecture of healthcare networks and the
solution to the security issues.
Literature review:
The network architecture consists of three important parts- (1) the Radio Frequency
Identification (RFID) wireless sensor network also called Hybrid Sensing Network (HSN), (2) interface of
the users for visualizing and management data and (3) IoT smart gateway. The network works on a
number of topologies and the gateway plays an important role in protecting the network. The network
architecture makes use of firewalls to protect the network perimeter. Along with firewall, there are
routers that has access to inspect firewall features. The Smart Hospital System (SHS) helps to collect
data regarding temperature, pressure and light conditions from the environment. The protocols that are
used to in healthcare networks are UDP, TCP and HTTP [1].
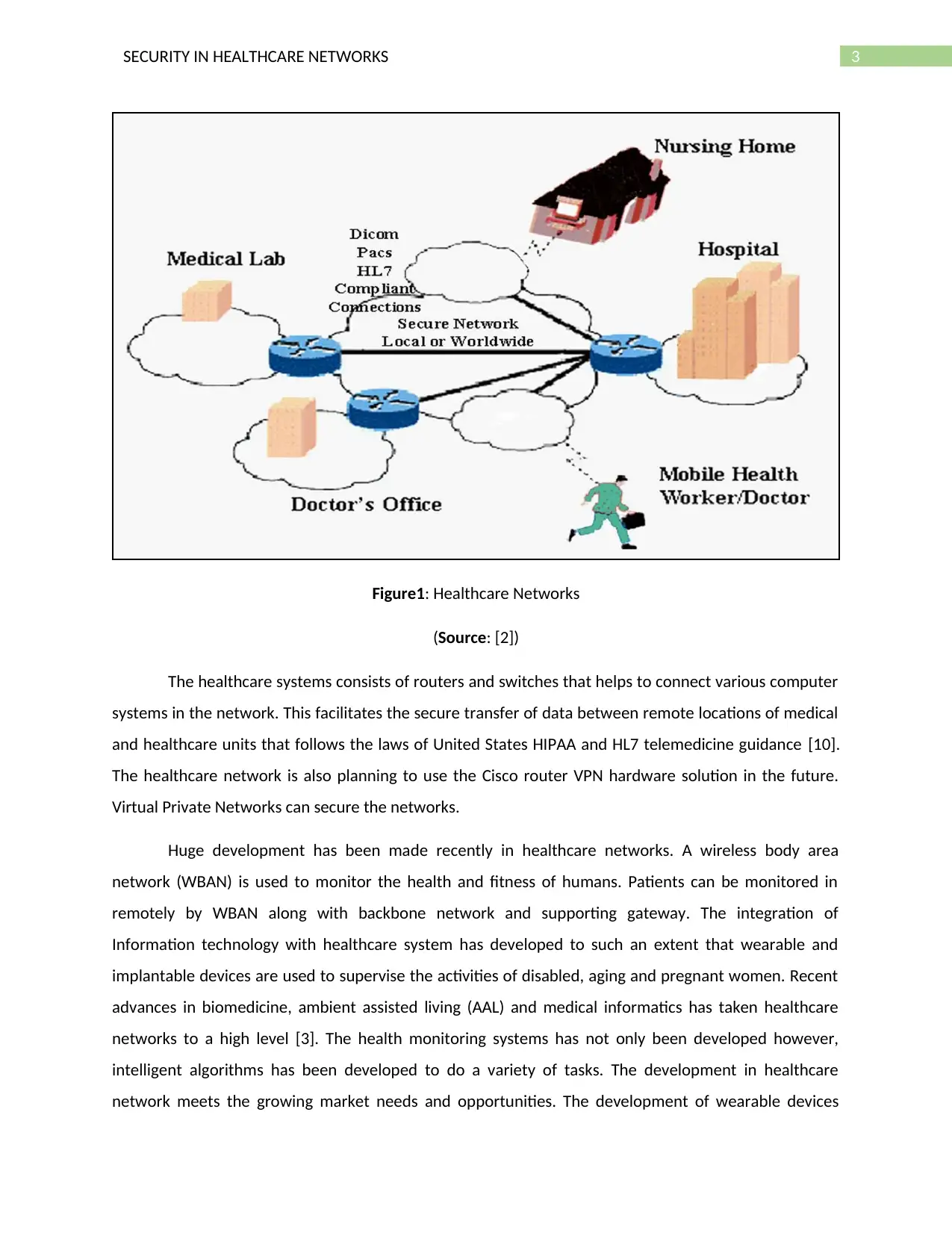
3SECURITY IN HEALTHCARE NETWORKS
Figure1: Healthcare Networks
(Source: [2])
The healthcare systems consists of routers and switches that helps to connect various computer
systems in the network. This facilitates the secure transfer of data between remote locations of medical
and healthcare units that follows the laws of United States HIPAA and HL7 telemedicine guidance [10].
The healthcare network is also planning to use the Cisco router VPN hardware solution in the future.
Virtual Private Networks can secure the networks.
Huge development has been made recently in healthcare networks. A wireless body area
network (WBAN) is used to monitor the health and fitness of humans. Patients can be monitored in
remotely by WBAN along with backbone network and supporting gateway. The integration of
Information technology with healthcare system has developed to such an extent that wearable and
implantable devices are used to supervise the activities of disabled, aging and pregnant women. Recent
advances in biomedicine, ambient assisted living (AAL) and medical informatics has taken healthcare
networks to a high level [3]. The health monitoring systems has not only been developed however,
intelligent algorithms has been developed to do a variety of tasks. The development in healthcare
network meets the growing market needs and opportunities. The development of wearable devices
Figure1: Healthcare Networks
(Source: [2])
The healthcare systems consists of routers and switches that helps to connect various computer
systems in the network. This facilitates the secure transfer of data between remote locations of medical
and healthcare units that follows the laws of United States HIPAA and HL7 telemedicine guidance [10].
The healthcare network is also planning to use the Cisco router VPN hardware solution in the future.
Virtual Private Networks can secure the networks.
Huge development has been made recently in healthcare networks. A wireless body area
network (WBAN) is used to monitor the health and fitness of humans. Patients can be monitored in
remotely by WBAN along with backbone network and supporting gateway. The integration of
Information technology with healthcare system has developed to such an extent that wearable and
implantable devices are used to supervise the activities of disabled, aging and pregnant women. Recent
advances in biomedicine, ambient assisted living (AAL) and medical informatics has taken healthcare
networks to a high level [3]. The health monitoring systems has not only been developed however,
intelligent algorithms has been developed to do a variety of tasks. The development in healthcare
network meets the growing market needs and opportunities. The development of wearable devices
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
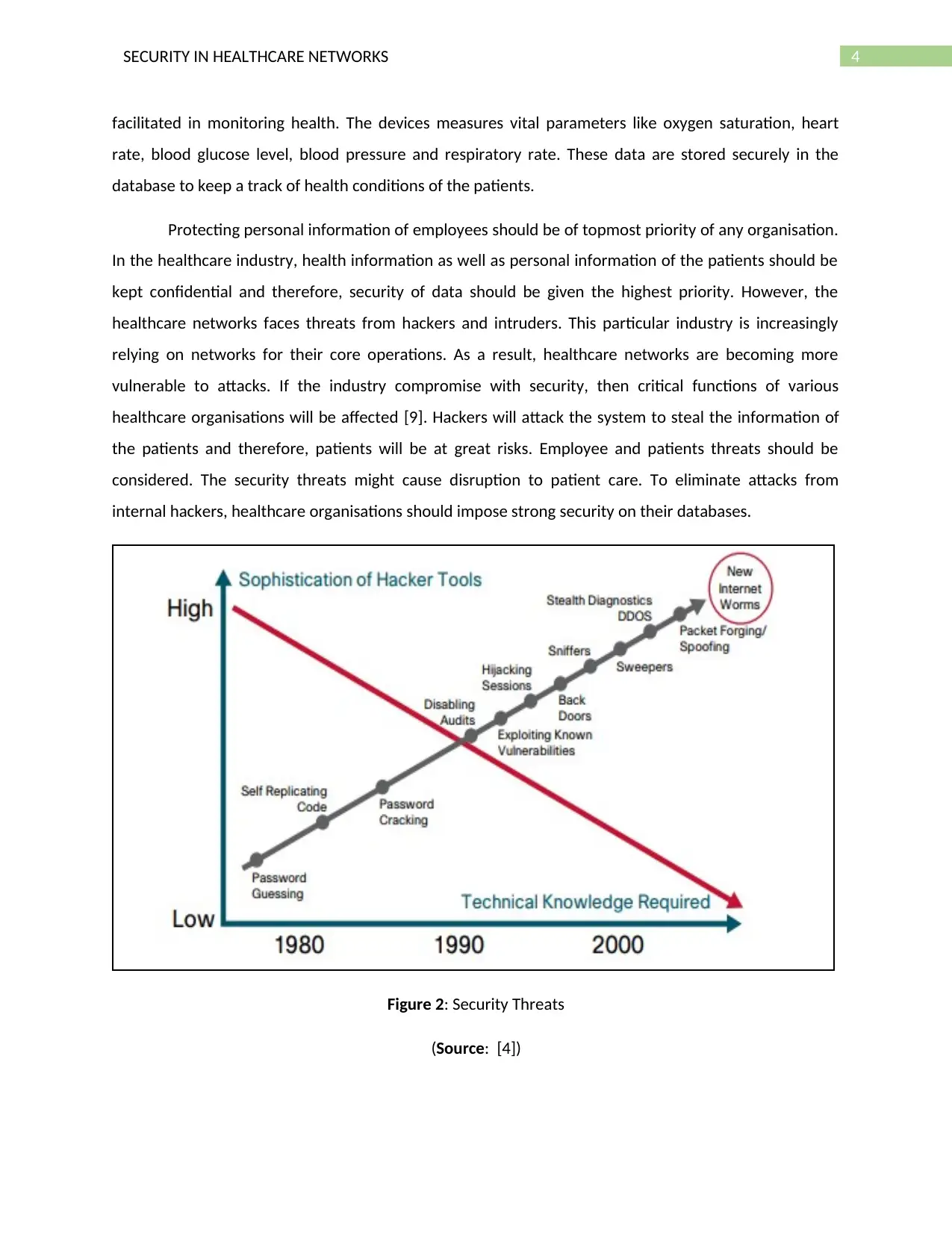
4SECURITY IN HEALTHCARE NETWORKS
facilitated in monitoring health. The devices measures vital parameters like oxygen saturation, heart
rate, blood glucose level, blood pressure and respiratory rate. These data are stored securely in the
database to keep a track of health conditions of the patients.
Protecting personal information of employees should be of topmost priority of any organisation.
In the healthcare industry, health information as well as personal information of the patients should be
kept confidential and therefore, security of data should be given the highest priority. However, the
healthcare networks faces threats from hackers and intruders. This particular industry is increasingly
relying on networks for their core operations. As a result, healthcare networks are becoming more
vulnerable to attacks. If the industry compromise with security, then critical functions of various
healthcare organisations will be affected [9]. Hackers will attack the system to steal the information of
the patients and therefore, patients will be at great risks. Employee and patients threats should be
considered. The security threats might cause disruption to patient care. To eliminate attacks from
internal hackers, healthcare organisations should impose strong security on their databases.
Figure 2: Security Threats
(Source: [4])
facilitated in monitoring health. The devices measures vital parameters like oxygen saturation, heart
rate, blood glucose level, blood pressure and respiratory rate. These data are stored securely in the
database to keep a track of health conditions of the patients.
Protecting personal information of employees should be of topmost priority of any organisation.
In the healthcare industry, health information as well as personal information of the patients should be
kept confidential and therefore, security of data should be given the highest priority. However, the
healthcare networks faces threats from hackers and intruders. This particular industry is increasingly
relying on networks for their core operations. As a result, healthcare networks are becoming more
vulnerable to attacks. If the industry compromise with security, then critical functions of various
healthcare organisations will be affected [9]. Hackers will attack the system to steal the information of
the patients and therefore, patients will be at great risks. Employee and patients threats should be
considered. The security threats might cause disruption to patient care. To eliminate attacks from
internal hackers, healthcare organisations should impose strong security on their databases.
Figure 2: Security Threats
(Source: [4])

5SECURITY IN HEALTHCARE NETWORKS
Therefore, the healthcare providers should undertake proper IP implementation that involves practices
ensuring network security, services and products. This will help them to deal with the potential risks
associated with the use of healthcare networks.
Current and future potential threats that Healthcare networks are facing:
The three security issues that Healthcare networks are facing today and the potential threats in
the future are as follows:
Threats from device compromise: Wireless body area networks (WBANs) are being used for e-
healthcare systems. The network operates in an environment that allows open access to various number
of people that includes attackers. According to some researchers the main device in the network that
are subjected to compromise in security are the WBAN nodes [5]. When the whole data is encrypted
and stored in the node with its encryption key, then data will be disclosed to the hackers. The local
servers that provides networking facilities might not be trustworthy and the malicious people might
break into the network to obtain personal information of patients [7]. A number of research argues that
the attackers might obtain information directly through the internet or from the patient’s room by
physically entering into it and compromising with the local servers. This makes the patient’s vulnerable
to attacks.
Common threats faced by healthcare networks: The common security threats faced by
healthcare networks are packet sniffers, denial of service (DoS), defacing, spam, man-in-the-middle
attack and attacks by viruses, Trojan horses and worms [6]. Research reveals that these attacks mainly
aim at hacking the usernames and passwords of the network devices to gain access to network
information. The threats might reduce the confidence of the patients on the healthcare organisation’s
ability to protect confidential data. Another emerging threat to healthcare networks is spam that affects
the mail servers.
Threats from network dynamics: The healthcare networks are dynamic in nature and therefore,
are vulnerable to malware attacks. Healthcare networks face network jamming, Distributed Denial of
Services and other attacks. The malicious attacks mostly takes place in electronic health records (EHRs)
[8]. Databases of healthcare organisation faces maximum threats, as the data is stored here.
Solution to one of the threats faced by healthcare networks:
Therefore, the healthcare providers should undertake proper IP implementation that involves practices
ensuring network security, services and products. This will help them to deal with the potential risks
associated with the use of healthcare networks.
Current and future potential threats that Healthcare networks are facing:
The three security issues that Healthcare networks are facing today and the potential threats in
the future are as follows:
Threats from device compromise: Wireless body area networks (WBANs) are being used for e-
healthcare systems. The network operates in an environment that allows open access to various number
of people that includes attackers. According to some researchers the main device in the network that
are subjected to compromise in security are the WBAN nodes [5]. When the whole data is encrypted
and stored in the node with its encryption key, then data will be disclosed to the hackers. The local
servers that provides networking facilities might not be trustworthy and the malicious people might
break into the network to obtain personal information of patients [7]. A number of research argues that
the attackers might obtain information directly through the internet or from the patient’s room by
physically entering into it and compromising with the local servers. This makes the patient’s vulnerable
to attacks.
Common threats faced by healthcare networks: The common security threats faced by
healthcare networks are packet sniffers, denial of service (DoS), defacing, spam, man-in-the-middle
attack and attacks by viruses, Trojan horses and worms [6]. Research reveals that these attacks mainly
aim at hacking the usernames and passwords of the network devices to gain access to network
information. The threats might reduce the confidence of the patients on the healthcare organisation’s
ability to protect confidential data. Another emerging threat to healthcare networks is spam that affects
the mail servers.
Threats from network dynamics: The healthcare networks are dynamic in nature and therefore,
are vulnerable to malware attacks. Healthcare networks face network jamming, Distributed Denial of
Services and other attacks. The malicious attacks mostly takes place in electronic health records (EHRs)
[8]. Databases of healthcare organisation faces maximum threats, as the data is stored here.
Solution to one of the threats faced by healthcare networks:

6SECURITY IN HEALTHCARE NETWORKS
One of the most severe threat faced by healthcare networks is from the network devices.
Therefore, to mitigate this risk, physical and commutation privacy should be provided to the devices.
They should be monitored frequently to avoid device theft or data being leaked out of the device. The
integrity and availability of the devices highly affects the security of the network. As a solution to the
above problem, networking experts have suggested the use of antiviruses that will protect the
computing systems from malware attacks. Data encryption is another way to deal with the security
issues. Encrypting data will cover the information with an encrypted code [11]. This will become difficult
for the hackers to read the encrypted data and therefore, the information remains secured and
confidential.
Using firewalls is another solution to the attacks that the healthcare system is facing. Firewalls
act as a filter between the network and the network devices [12]. Any exchange in information between
devices and the network will have to pass through firewalls that will kill security breaks and make the
network secured. Research reveals that these attacks mainly aim at hacking the usernames and
passwords of the network devices to gain access to network information. A number of research argues
that the attackers might obtain information directly through the internet or from the patient’s room by
physically entering into it and compromising with the local servers. Therefore, strong security checks
should be imposed in the healthcare organisation such that the medical information as well as the
personal information of the patients are kept secured and personal. Antiviruses can be implemented in
each system such that the security can be checked in every step.
Conclusion:
From the above discussions, it can be concluded that healthcare industry is increasingly
depending on Internet of things and networks for carrying out various operations. This increases the
efficiency of communication and collaboration between the patients and the healthcare units. The
applications of IoT that are being used by this sector are electronic medical records (EMRs), biomedical
information, imaging, patient accounting and online claims submissions. All the mentioned application
will require security of data. However, healthcare sector is facing a number of security issues including
attacks from hackers and intruders, malicious software as well as from the internal employees. The
human errors re posing great threats to the healthcare networks and has become the main concern
today. The solution to these problems that should be used by healthcare companies are encryption of
data, using VPNs (Virtual Private Networks) and firewalls. Setting a strong monitoring team might also
prove beneficial for the industry. Firewalls act as a filter between the network and the network devices.
One of the most severe threat faced by healthcare networks is from the network devices.
Therefore, to mitigate this risk, physical and commutation privacy should be provided to the devices.
They should be monitored frequently to avoid device theft or data being leaked out of the device. The
integrity and availability of the devices highly affects the security of the network. As a solution to the
above problem, networking experts have suggested the use of antiviruses that will protect the
computing systems from malware attacks. Data encryption is another way to deal with the security
issues. Encrypting data will cover the information with an encrypted code [11]. This will become difficult
for the hackers to read the encrypted data and therefore, the information remains secured and
confidential.
Using firewalls is another solution to the attacks that the healthcare system is facing. Firewalls
act as a filter between the network and the network devices [12]. Any exchange in information between
devices and the network will have to pass through firewalls that will kill security breaks and make the
network secured. Research reveals that these attacks mainly aim at hacking the usernames and
passwords of the network devices to gain access to network information. A number of research argues
that the attackers might obtain information directly through the internet or from the patient’s room by
physically entering into it and compromising with the local servers. Therefore, strong security checks
should be imposed in the healthcare organisation such that the medical information as well as the
personal information of the patients are kept secured and personal. Antiviruses can be implemented in
each system such that the security can be checked in every step.
Conclusion:
From the above discussions, it can be concluded that healthcare industry is increasingly
depending on Internet of things and networks for carrying out various operations. This increases the
efficiency of communication and collaboration between the patients and the healthcare units. The
applications of IoT that are being used by this sector are electronic medical records (EMRs), biomedical
information, imaging, patient accounting and online claims submissions. All the mentioned application
will require security of data. However, healthcare sector is facing a number of security issues including
attacks from hackers and intruders, malicious software as well as from the internal employees. The
human errors re posing great threats to the healthcare networks and has become the main concern
today. The solution to these problems that should be used by healthcare companies are encryption of
data, using VPNs (Virtual Private Networks) and firewalls. Setting a strong monitoring team might also
prove beneficial for the industry. Firewalls act as a filter between the network and the network devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SECURITY IN HEALTHCARE NETWORKS
Any exchange in information between devices and the network will have to pass through firewalls that
will kill security breaks and make the network secured.
Any exchange in information between devices and the network will have to pass through firewalls that
will kill security breaks and make the network secured.

8SECURITY IN HEALTHCARE NETWORKS
References:
[1] Catarinucci, Luca, Danilo De Donno, Luca Mainetti, Luca Palano, Luigi Patrono, Maria Laura Stefanizzi,
and Luciano Tarricone. "An IoT-aware architecture for smart healthcare systems." IEEE Internet of
Things Journal 2, no. 6 (2015): 515-526.
[2] "Telemedicine, Telehealth, Distance Learning medical solutions to equalize healthcare access, to
eliminate suffering, improve the quality of life, and to brighten lives", First-worldwide-internet.com,
2018. [Online]. Available: http://www.first-worldwide-internet.com/telemedical-telehealth-hipaa-
dicom-hL7-pacs-network.html. [Accessed: 24- Sep- 2018].
[3] Chen, Min, Jiafu Wan, Sergio González-Valenzuela, Xiaofei Liao, and Victor CM Leung. "A Survey of
Recent Developments in Home M2M Networks." IEEE Communications Surveys and Tutorials 16, no. 1
(2014): 98-114.
[4] Zafar, Humayun, Myung S. Ko, and Jan G. Clark. "Security Risk Management in Health Care: A Case
Study." CAIS 34 (2014): 37.
[5] Rushanan, Michael, Aviel D. Rubin, Denis Foo Kune, and Colleen M. Swanson. "Sok: Security and
privacy in implantable medical devices and body area networks." In 2014 IEEE Symposium on Security
and Privacy (SP), pp. 524-539. IEEE, 2014.
[6] Abomhara, Mohamed, and Geir M. Køien. "Cyber security and the internet of things: vulnerabilities,
threats, intruders and attacks." Journal of Cyber Security 4, no. 1 (2015): 65-88.
[7] Zhang, Meng, Anand Raghunathan, and Niraj K. Jha. "Trustworthiness of Medical Devices and Body
Area Networks." Proceedings of the IEEE 102, no. 8 (2014): 1174-1188.
[8] Glisson, William Bradley, Todd Andel, Todd McDonald, Mike Jacobs, Matt Campbell, and Johnny
Mayr. "Compromising a medical mannequin." arXiv preprint arXiv:1509.00065 (2015).
[9] Waring, Justin, Fiona Marshall, and Simon Bishop. "Understanding the occupational and
organizational boundaries to safe hospital discharge." Journal of health services research & policy 20, no.
1_suppl (2015): 35-44.
[10] Baig, Mirza Mansoor, Hamid GholamHosseini, and Martin J. Connolly. "Mobile healthcare
applications: system design review, critical issues and challenges." Australasian physical & engineering
sciences in medicine 38, no. 1 (2015): 23-38.
References:
[1] Catarinucci, Luca, Danilo De Donno, Luca Mainetti, Luca Palano, Luigi Patrono, Maria Laura Stefanizzi,
and Luciano Tarricone. "An IoT-aware architecture for smart healthcare systems." IEEE Internet of
Things Journal 2, no. 6 (2015): 515-526.
[2] "Telemedicine, Telehealth, Distance Learning medical solutions to equalize healthcare access, to
eliminate suffering, improve the quality of life, and to brighten lives", First-worldwide-internet.com,
2018. [Online]. Available: http://www.first-worldwide-internet.com/telemedical-telehealth-hipaa-
dicom-hL7-pacs-network.html. [Accessed: 24- Sep- 2018].
[3] Chen, Min, Jiafu Wan, Sergio González-Valenzuela, Xiaofei Liao, and Victor CM Leung. "A Survey of
Recent Developments in Home M2M Networks." IEEE Communications Surveys and Tutorials 16, no. 1
(2014): 98-114.
[4] Zafar, Humayun, Myung S. Ko, and Jan G. Clark. "Security Risk Management in Health Care: A Case
Study." CAIS 34 (2014): 37.
[5] Rushanan, Michael, Aviel D. Rubin, Denis Foo Kune, and Colleen M. Swanson. "Sok: Security and
privacy in implantable medical devices and body area networks." In 2014 IEEE Symposium on Security
and Privacy (SP), pp. 524-539. IEEE, 2014.
[6] Abomhara, Mohamed, and Geir M. Køien. "Cyber security and the internet of things: vulnerabilities,
threats, intruders and attacks." Journal of Cyber Security 4, no. 1 (2015): 65-88.
[7] Zhang, Meng, Anand Raghunathan, and Niraj K. Jha. "Trustworthiness of Medical Devices and Body
Area Networks." Proceedings of the IEEE 102, no. 8 (2014): 1174-1188.
[8] Glisson, William Bradley, Todd Andel, Todd McDonald, Mike Jacobs, Matt Campbell, and Johnny
Mayr. "Compromising a medical mannequin." arXiv preprint arXiv:1509.00065 (2015).
[9] Waring, Justin, Fiona Marshall, and Simon Bishop. "Understanding the occupational and
organizational boundaries to safe hospital discharge." Journal of health services research & policy 20, no.
1_suppl (2015): 35-44.
[10] Baig, Mirza Mansoor, Hamid GholamHosseini, and Martin J. Connolly. "Mobile healthcare
applications: system design review, critical issues and challenges." Australasian physical & engineering
sciences in medicine 38, no. 1 (2015): 23-38.

9SECURITY IN HEALTHCARE NETWORKS
[11] Naik, Aanand D., Lindsey A. Martin, Jennifer Moye, and Michele J. Karel. "Health values and
treatment goals of older, multimorbid adults facing life threatening illness."‐ Journal of the American
Geriatrics Society 64, no. 3 (2016): 625-631.
[12] Lee, Jay, Behrad Bagheri, and Hung-An Kao. "A cyber-physical systems architecture for industry 4.0-
based manufacturing systems." Manufacturing Letters 3 (2015): 18-23.
[11] Naik, Aanand D., Lindsey A. Martin, Jennifer Moye, and Michele J. Karel. "Health values and
treatment goals of older, multimorbid adults facing life threatening illness."‐ Journal of the American
Geriatrics Society 64, no. 3 (2016): 625-631.
[12] Lee, Jay, Behrad Bagheri, and Hung-An Kao. "A cyber-physical systems architecture for industry 4.0-
based manufacturing systems." Manufacturing Letters 3 (2015): 18-23.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



