University Cybersecurity Thesis: Human Behavior and Threats
VerifiedAdded on 2023/06/04
|68
|13665
|232
Thesis and Dissertation
AI Summary
This thesis paper delves into the critical intersection of human behavior and cybersecurity, examining how human factors influence the effectiveness of security practices. The research investigates the vulnerabilities introduced by human actions, particularly in the context of social engineering and manipulation. Through a mixed-methods approach, including surveys and questionnaires with a sample size of 70, the study identifies specific cybersecurity events stemming from human errors and assesses the current consideration of human behavior in security implementations. The findings highlight the need for a more comprehensive approach to cybersecurity that accounts for human reliability and data quality control, advocating for mandatory adherence to cybersecurity guidelines, robust cyber and physical asset protection, and regular security audits. The study aims to contribute to the cybersecurity field by providing recommendations for established industries to benefit from successful practices in human reliability and quality control.

Running head: HUMAN BEHAVIOUR IN CYBERSECURITY
Human Behaviour in Cybersecurity
Name of the Student:
Name of the University:
Human Behaviour in Cybersecurity
Name of the Student:
Name of the University:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1HUMAN BEHAVIOUR IN CYBERSECURITY
Abstract
The thesis paper is based on human behaviour in cybersecurity. The purpose of this thesis is to
consider issues which are affecting the human behaviour and assessing if they could better
considered in implementation of the security practices. The study is focused on human behaviour
when the employees are facing manipulation. The current security thinking is based on how to
implement object secured despite the human beings. The human activities are threats to security
chains. The research method is based on primary data collection method using surveys and
questionnaires. The selected sample is 70; these are taken to collect data. The purpose of this
research study is to identify elements of the cybersecurity which would benefit from further
research as well as development based on findings of the literature review. The result of this
study is to present need of the cybersecurity field to review in established industries to benefit
from successful practices like evaluation of human reliability and quality control of data to get
true assurance. Recommendations which are provided by the researcher to implement
cybersecurity practices in the business organizations are mandatory follow the cybersecurity
guidelines, cyber and physical asset protection and security audits.
Keywords: Cybersecurity, human behaviour, security thinking, Human reliability, Security
audits.
Abstract
The thesis paper is based on human behaviour in cybersecurity. The purpose of this thesis is to
consider issues which are affecting the human behaviour and assessing if they could better
considered in implementation of the security practices. The study is focused on human behaviour
when the employees are facing manipulation. The current security thinking is based on how to
implement object secured despite the human beings. The human activities are threats to security
chains. The research method is based on primary data collection method using surveys and
questionnaires. The selected sample is 70; these are taken to collect data. The purpose of this
research study is to identify elements of the cybersecurity which would benefit from further
research as well as development based on findings of the literature review. The result of this
study is to present need of the cybersecurity field to review in established industries to benefit
from successful practices like evaluation of human reliability and quality control of data to get
true assurance. Recommendations which are provided by the researcher to implement
cybersecurity practices in the business organizations are mandatory follow the cybersecurity
guidelines, cyber and physical asset protection and security audits.
Keywords: Cybersecurity, human behaviour, security thinking, Human reliability, Security
audits.

2HUMAN BEHAVIOUR IN CYBERSECURITY
Table of Contents
1.0 Introduction................................................................................................................................4
1.1 Background of the research study..........................................................................................4
1.2 Research aim and objectives..................................................................................................4
1.3 Research question..................................................................................................................5
1.4 Purpose of the research..........................................................................................................5
1.5 Overview of the research.......................................................................................................5
2.0 Proposed methodology..............................................................................................................6
2.1 Introduction............................................................................................................................6
2.2 Research philosophy..............................................................................................................6
2.3 Research approach.................................................................................................................7
2.4 Research design.....................................................................................................................8
2.5 Data collection procedures and techniques............................................................................8
2.6 Ethical considerations..........................................................................................................10
2.7 Research limitations.............................................................................................................10
2.8 Time horizon........................................................................................................................11
3.0 Findings from research............................................................................................................11
3.1 Introduction..........................................................................................................................11
3.2 Quantitative data analysis....................................................................................................12
4.0 Discussion of findings.............................................................................................................41
Table of Contents
1.0 Introduction................................................................................................................................4
1.1 Background of the research study..........................................................................................4
1.2 Research aim and objectives..................................................................................................4
1.3 Research question..................................................................................................................5
1.4 Purpose of the research..........................................................................................................5
1.5 Overview of the research.......................................................................................................5
2.0 Proposed methodology..............................................................................................................6
2.1 Introduction............................................................................................................................6
2.2 Research philosophy..............................................................................................................6
2.3 Research approach.................................................................................................................7
2.4 Research design.....................................................................................................................8
2.5 Data collection procedures and techniques............................................................................8
2.6 Ethical considerations..........................................................................................................10
2.7 Research limitations.............................................................................................................10
2.8 Time horizon........................................................................................................................11
3.0 Findings from research............................................................................................................11
3.1 Introduction..........................................................................................................................11
3.2 Quantitative data analysis....................................................................................................12
4.0 Discussion of findings.............................................................................................................41
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3HUMAN BEHAVIOUR IN CYBERSECURITY
4.1 Relation to research problem...............................................................................................41
4.2 Relation to literature............................................................................................................42
5.0 Conclusion and recommendations...........................................................................................44
5.1 Conclusion from data presented..........................................................................................44
5.2 Link with aim and objectives...............................................................................................45
5.3 Recommendations................................................................................................................46
5.4 Future research.....................................................................................................................47
5.5 Critical review of completed work......................................................................................47
References......................................................................................................................................49
Bibliography..................................................................................................................................50
Appendix........................................................................................................................................51
1. Literature Review..................................................................................................................51
2. Ethics form.............................................................................................................................66
4.1 Relation to research problem...............................................................................................41
4.2 Relation to literature............................................................................................................42
5.0 Conclusion and recommendations...........................................................................................44
5.1 Conclusion from data presented..........................................................................................44
5.2 Link with aim and objectives...............................................................................................45
5.3 Recommendations................................................................................................................46
5.4 Future research.....................................................................................................................47
5.5 Critical review of completed work......................................................................................47
References......................................................................................................................................49
Bibliography..................................................................................................................................50
Appendix........................................................................................................................................51
1. Literature Review..................................................................................................................51
2. Ethics form.............................................................................................................................66
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4HUMAN BEHAVIOUR IN CYBERSECURITY
1.0 Introduction
1.1 Background of the research study
Danks and Danks (2016) stated that cybersecurity is extremely important in modern
society. With the technical attacks, criminals are benefitting from the information they have
received. The criminals get access to credit information, business secrets, passwords, account
and personal information of victims. This stolen information is used to blackmail and sell
information to the victim himself. For example, a hard disk is encrypted and then the encryption
key is sold back tothe victim. Gutzwiller et al. (2015) argued that social engineering is uncertain
is the modern world where humans are more aware and more suspicious about securing their
personal information.
1.2 Research aim and objectives
This research study is based on exploring the relationship between human behaviour and
cybersecurity and examining the impact of human factors on the security of data. The research
work is based on identifying the elements of cybersecurity which would benefit from further
study and development based on the literature findings. Following are the research objectives
such as:
To identify cybersecurity events caused due to human errors
To assess human behaviour considered in the implementation of the security practices
To identify the significance of human behaviour on the cybersecurity assurance
1.0 Introduction
1.1 Background of the research study
Danks and Danks (2016) stated that cybersecurity is extremely important in modern
society. With the technical attacks, criminals are benefitting from the information they have
received. The criminals get access to credit information, business secrets, passwords, account
and personal information of victims. This stolen information is used to blackmail and sell
information to the victim himself. For example, a hard disk is encrypted and then the encryption
key is sold back tothe victim. Gutzwiller et al. (2015) argued that social engineering is uncertain
is the modern world where humans are more aware and more suspicious about securing their
personal information.
1.2 Research aim and objectives
This research study is based on exploring the relationship between human behaviour and
cybersecurity and examining the impact of human factors on the security of data. The research
work is based on identifying the elements of cybersecurity which would benefit from further
study and development based on the literature findings. Following are the research objectives
such as:
To identify cybersecurity events caused due to human errors
To assess human behaviour considered in the implementation of the security practices
To identify the significance of human behaviour on the cybersecurity assurance

5HUMAN BEHAVIOUR IN CYBERSECURITY
1.3 Research question
The selected research questions based on the research topic are:
1. What are possible cybersecurity breaches and thesignificance of human behaviour on the
cybersecurity assurance?
2. How is it assessed that human behaviour isconsidered inthe implementation of the
security practices?
3. What are possible security incidents because of human behaviour?
1.4 Purpose of the research
The purpose of this research is to consider thecauses of human behaviour and assess
whether it is better taken for theimplementation of security practices. The study is focused on
human behaviour plus social engineering. The activities of humans are always a threat
towardsthe security chain. The cybersecurity events are discussed in the study so that humans are
aware of the attacks caused due to human errors.
1.5 Overview of the research
The research discussed the series of events which are focused on how the social engineers
are taking advantage of human behaviour. The first section describes the background of the
research. It provides research aims, objectives and questions on whichthe entireresearch study is
based. The next chapter is focused on the term social engineering andthe impact of human
behaviour on cybersecurity. The third chapter consists of the methods and techniques which are
used to collect data for this research study. This section deals with how collected information
canbe used to allow the social engineer to identify the cybersecurity threats due to human errors.
1.3 Research question
The selected research questions based on the research topic are:
1. What are possible cybersecurity breaches and thesignificance of human behaviour on the
cybersecurity assurance?
2. How is it assessed that human behaviour isconsidered inthe implementation of the
security practices?
3. What are possible security incidents because of human behaviour?
1.4 Purpose of the research
The purpose of this research is to consider thecauses of human behaviour and assess
whether it is better taken for theimplementation of security practices. The study is focused on
human behaviour plus social engineering. The activities of humans are always a threat
towardsthe security chain. The cybersecurity events are discussed in the study so that humans are
aware of the attacks caused due to human errors.
1.5 Overview of the research
The research discussed the series of events which are focused on how the social engineers
are taking advantage of human behaviour. The first section describes the background of the
research. It provides research aims, objectives and questions on whichthe entireresearch study is
based. The next chapter is focused on the term social engineering andthe impact of human
behaviour on cybersecurity. The third chapter consists of the methods and techniques which are
used to collect data for this research study. This section deals with how collected information
canbe used to allow the social engineer to identify the cybersecurity threats due to human errors.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6HUMAN BEHAVIOUR IN CYBERSECURITY
The fifth section provides an analysis of collected data where social engineering is an action. It is
focused on the events against the social engineering throughout security thinking to prevent the
cybersecurity events. The sixth section summarises the events due to which research goals are
achieved. It provides a discussion about if the study is meeting with its aims and objectives.
2.0 Proposed methodology
2.1 Introduction
Gast and Ledford (2014) stated that the research methodology is utilised to introduce
statistical tools for analysing the data to the researcher. It is used to introduce concepts related to
the scientific research and methods which are conducted for scientific inquiry. The research
methods and techniques are used to adopt and conduct the study related to human behaviours in
cybersecurity. The methods as well as techniques are used to solve the research related problems.
2.2 Research philosophy
Creswell (2013) discussed that research philosophy deals with nature and development of
the knowledge. The concept related to the philosophy collects primary and secondary data to
create new knowledge related to the thesis work. There are three types of research philosophy
which are termed as positivism, realism and interpretivism. This method is used to determine
hidden facts related to selected research philosophy. The research philosophy is belief about
ways in which the data about research phenomenon should gather and analyses.
After analysing the selected topic “Human behaviour in cybersecurity”,it was determined
that positivism would be selected as the research method. All the hidden facts were being
evaluated in scientific manner with an application of the particular philosophy. This method is
The fifth section provides an analysis of collected data where social engineering is an action. It is
focused on the events against the social engineering throughout security thinking to prevent the
cybersecurity events. The sixth section summarises the events due to which research goals are
achieved. It provides a discussion about if the study is meeting with its aims and objectives.
2.0 Proposed methodology
2.1 Introduction
Gast and Ledford (2014) stated that the research methodology is utilised to introduce
statistical tools for analysing the data to the researcher. It is used to introduce concepts related to
the scientific research and methods which are conducted for scientific inquiry. The research
methods and techniques are used to adopt and conduct the study related to human behaviours in
cybersecurity. The methods as well as techniques are used to solve the research related problems.
2.2 Research philosophy
Creswell (2013) discussed that research philosophy deals with nature and development of
the knowledge. The concept related to the philosophy collects primary and secondary data to
create new knowledge related to the thesis work. There are three types of research philosophy
which are termed as positivism, realism and interpretivism. This method is used to determine
hidden facts related to selected research philosophy. The research philosophy is belief about
ways in which the data about research phenomenon should gather and analyses.
After analysing the selected topic “Human behaviour in cybersecurity”,it was determined
that positivism would be selected as the research method. All the hidden facts were being
evaluated in scientific manner with an application of the particular philosophy. This method is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7HUMAN BEHAVIOUR IN CYBERSECURITY
used as it is believed that reality is stable and observes and describe from the viewpoint of
research objectives. It involved manipulation of reality with the variations into single
independent variables to form relationships between elements into the social world. In this study,
predictions are made based on previously observed as well as explained realities and
interrelationships.
2.3 Research approach
The research approach is selected to determine the research aim as well as objectives so
thatthe selected topic is analysed critically. There are two types of research approaches,
deductive as well as inductive. Mackey and Gass (2015) stated that the inductive approach is
used as a study to learn the selected topic at the time when proper data is not available.
Observation is used as a technique to get related data so that the research path is built based on
the method. In order to build theories related to the selected topic,the inductive approach is
suitable. The deductive approach is selected as a method which can describe the practical
applications related to the theories which are required to get access related tothe content of data
investigations.
In order to investigate details related to human behaviour in cybersecurity, the most
suitable approach wasdeductive. The results obtained from this approach provided a clear
understanding of the human errors which occurred due to cybersecurity threats in particular
behaviour. In this case,the inductive approach failed to meet with the research objectives as the
researchers failed to highlight innovative concepts as well as theories based on the human
behaviour. The human behaviour in cybersecurity helped to recognise the comprehensive
thoughts in precise way.
used as it is believed that reality is stable and observes and describe from the viewpoint of
research objectives. It involved manipulation of reality with the variations into single
independent variables to form relationships between elements into the social world. In this study,
predictions are made based on previously observed as well as explained realities and
interrelationships.
2.3 Research approach
The research approach is selected to determine the research aim as well as objectives so
thatthe selected topic is analysed critically. There are two types of research approaches,
deductive as well as inductive. Mackey and Gass (2015) stated that the inductive approach is
used as a study to learn the selected topic at the time when proper data is not available.
Observation is used as a technique to get related data so that the research path is built based on
the method. In order to build theories related to the selected topic,the inductive approach is
suitable. The deductive approach is selected as a method which can describe the practical
applications related to the theories which are required to get access related tothe content of data
investigations.
In order to investigate details related to human behaviour in cybersecurity, the most
suitable approach wasdeductive. The results obtained from this approach provided a clear
understanding of the human errors which occurred due to cybersecurity threats in particular
behaviour. In this case,the inductive approach failed to meet with the research objectives as the
researchers failed to highlight innovative concepts as well as theories based on the human
behaviour. The human behaviour in cybersecurity helped to recognise the comprehensive
thoughts in precise way.

8HUMAN BEHAVIOUR IN CYBERSECURITY
2.4 Research design
Maxwell (2012) determined that the research design will help the researcher to select the
issues in the research work. It aims to combinethe significance of the purpose of this research
study. It will also draw out the processthe researcher performs in terms of the hypothesis
equippedsuggestions and completed data analysis. There are three types of research
design:descriptive, exploratory and explanatory for analysing the selected topic. Exploratory
design is used to prepare research issues for in-detail investigation for the prepared aspects
(Silverman 2016). It is flexible for permitting different scopes of the issues under the research
study. Explanatory research design is utilised to find explanations to carry out the research
related study. Descriptive design is used to describethe characteristicsof aspecific individual. It is
suitable to protect data against the bias and raise reliability to finish the research work in a
financial way.
In this particular study to analyse the selected topic, descriptive research design was
selected to finish off theframework of this research study. This selected research design wasused
to gain details on characteristics of the individuals who carried out the critical analysis of
selected thesis work. Using this research method, various project factors were understandable.
The detailed human errors involved in cybersecurity threats are efficiently determined by means
ofa descriptive research design method.
2.5 Data collection procedures and techniques
In order to conducta study on the human behaviour errors which lead to cyber threats,
thedata collection method is used to gather data for getting better research outcomes. The data
iscollected from the factors which are used in the literature study relevant tothis thesis topic. The
data collection is used to collect data and this data is analysed to get proper project related
2.4 Research design
Maxwell (2012) determined that the research design will help the researcher to select the
issues in the research work. It aims to combinethe significance of the purpose of this research
study. It will also draw out the processthe researcher performs in terms of the hypothesis
equippedsuggestions and completed data analysis. There are three types of research
design:descriptive, exploratory and explanatory for analysing the selected topic. Exploratory
design is used to prepare research issues for in-detail investigation for the prepared aspects
(Silverman 2016). It is flexible for permitting different scopes of the issues under the research
study. Explanatory research design is utilised to find explanations to carry out the research
related study. Descriptive design is used to describethe characteristicsof aspecific individual. It is
suitable to protect data against the bias and raise reliability to finish the research work in a
financial way.
In this particular study to analyse the selected topic, descriptive research design was
selected to finish off theframework of this research study. This selected research design wasused
to gain details on characteristics of the individuals who carried out the critical analysis of
selected thesis work. Using this research method, various project factors were understandable.
The detailed human errors involved in cybersecurity threats are efficiently determined by means
ofa descriptive research design method.
2.5 Data collection procedures and techniques
In order to conducta study on the human behaviour errors which lead to cyber threats,
thedata collection method is used to gather data for getting better research outcomes. The data
iscollected from the factors which are used in the literature study relevant tothis thesis topic. The
data collection is used to collect data and this data is analysed to get proper project related
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9HUMAN BEHAVIOUR IN CYBERSECURITY
decisions (Smith 2015). The data collection method is divided into two forms: data sources and
data analysis.
For thespecific selected thesis topic “Human behaviour in cybersecurity”, primary data
sources were used for gatheringthe required information. In order to get data based on thesis
needs, selection of proper data sources was vital. Suitable data sources provided helpful
materials and information regarding the research topic. In order to gather raw data on the survey
questions based on the selected research questions, objectives and literature study, primary data
sources were helpful to widen the topic towards statistical level. The primary data were collected
bythe researcher based on the research needs. Primary data was used to clarifythe reliability and
validity of collected raw data. The primary data sources included proper interaction with the
individuals in terms ofthe surveymethod. The participants took part in the survey were selected
on a random basis to perform the primary research.
In order to analyse collected raw data, quantitative data analysis techniques were used to
add practical and statistical concepts to the selected thesis topic. The practical concepts related to
the human errors and threats thatlead to cybersecurity issues were understood in a better way
withthe help of quantitative data analysis. It helped to record statistical data even if the selected
sample size was 70. On a random basis, the individuals selected were those facing cyberthreats
and usinga computer for their daily working life. The individuals were asked to participate in the
survey throughan online method where the survey link was provided they had to provide their
responses based on the cyberthreats they were facing due to human faults. This data technique
was being applied bythe researcher to collect and analyse human behaviour in cyberthreats.
decisions (Smith 2015). The data collection method is divided into two forms: data sources and
data analysis.
For thespecific selected thesis topic “Human behaviour in cybersecurity”, primary data
sources were used for gatheringthe required information. In order to get data based on thesis
needs, selection of proper data sources was vital. Suitable data sources provided helpful
materials and information regarding the research topic. In order to gather raw data on the survey
questions based on the selected research questions, objectives and literature study, primary data
sources were helpful to widen the topic towards statistical level. The primary data were collected
bythe researcher based on the research needs. Primary data was used to clarifythe reliability and
validity of collected raw data. The primary data sources included proper interaction with the
individuals in terms ofthe surveymethod. The participants took part in the survey were selected
on a random basis to perform the primary research.
In order to analyse collected raw data, quantitative data analysis techniques were used to
add practical and statistical concepts to the selected thesis topic. The practical concepts related to
the human errors and threats thatlead to cybersecurity issues were understood in a better way
withthe help of quantitative data analysis. It helped to record statistical data even if the selected
sample size was 70. On a random basis, the individuals selected were those facing cyberthreats
and usinga computer for their daily working life. The individuals were asked to participate in the
survey throughan online method where the survey link was provided they had to provide their
responses based on the cyberthreats they were facing due to human faults. This data technique
was being applied bythe researcher to collect and analyse human behaviour in cyberthreats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10HUMAN BEHAVIOUR IN CYBERSECURITY
2.6 Ethical considerations
Following are the ethical considerations which are required to follow to conduct this
research study such as:
a. The researcher is required to maintain a code of conduct to help the participants to
recognise right and wrong behavioural sets. In order to analyse human behaviours
in cyberthreats, the data gathered is vital.
b. Based on following the code of conduct, the findings for this research study will
be used for academic purposes only.
c. The researcher should respect anonymity as well as confidentiality of collected
data which is closely connected with rights of beneficence. The researcher should
ensure that there is no physical as well as mental harassment of the respondents
taking part in the study.
d. When the researcher is not promise of anonymity, then they have to address
confidentiality that is management of the private information by the researcher for
protection of subject’s identity.
e. The researcher should also respect about privacy of the data. Without prior
knowledge and consent of the participants, their information, opinions and records
are not shared with others. All the research methodologies are discussed with
prospective subjects, and then the researcher is prior to the investigations.
2.7 Research limitations
The participants involved in the survey are not forced and influenced to provide their
feedback. The issues related to reliability provide negative impact on the research work. Due to
lack of budget, SPSS analysis is not conducted; therefore sometimes there is low validity to
2.6 Ethical considerations
Following are the ethical considerations which are required to follow to conduct this
research study such as:
a. The researcher is required to maintain a code of conduct to help the participants to
recognise right and wrong behavioural sets. In order to analyse human behaviours
in cyberthreats, the data gathered is vital.
b. Based on following the code of conduct, the findings for this research study will
be used for academic purposes only.
c. The researcher should respect anonymity as well as confidentiality of collected
data which is closely connected with rights of beneficence. The researcher should
ensure that there is no physical as well as mental harassment of the respondents
taking part in the study.
d. When the researcher is not promise of anonymity, then they have to address
confidentiality that is management of the private information by the researcher for
protection of subject’s identity.
e. The researcher should also respect about privacy of the data. Without prior
knowledge and consent of the participants, their information, opinions and records
are not shared with others. All the research methodologies are discussed with
prospective subjects, and then the researcher is prior to the investigations.
2.7 Research limitations
The participants involved in the survey are not forced and influenced to provide their
feedback. The issues related to reliability provide negative impact on the research work. Due to
lack of budget, SPSS analysis is not conducted; therefore sometimes there is low validity to
11HUMAN BEHAVIOUR IN CYBERSECURITY
check raw data. The researcher faced issues of lack of time as this study is cross sectional in
nature. As this research study is cross sectional, therefore in-depth analysis is to be eliminated in
this case.
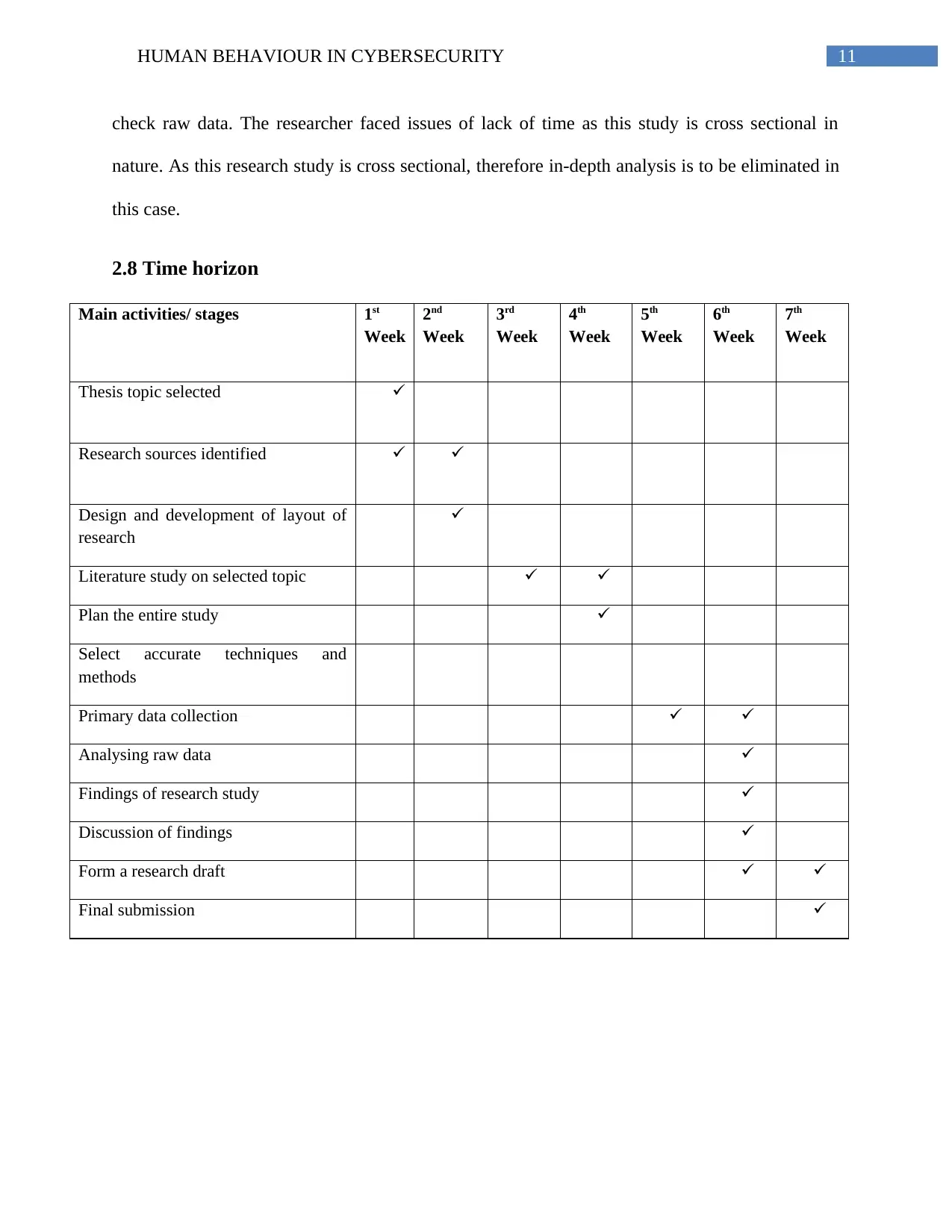
2.8 Time horizon
Main activities/ stages 1st
Week
2nd
Week
3rd
Week
4th
Week
5th
Week
6th
Week
7th
Week
Thesis topic selected
Research sources identified
Design and development of layout of
research
Literature study on selected topic
Plan the entire study
Select accurate techniques and
methods
Primary data collection
Analysing raw data
Findings of research study
Discussion of findings
Form a research draft
Final submission
check raw data. The researcher faced issues of lack of time as this study is cross sectional in
nature. As this research study is cross sectional, therefore in-depth analysis is to be eliminated in
this case.
2.8 Time horizon
Main activities/ stages 1st
Week
2nd
Week
3rd
Week
4th
Week
5th
Week
6th
Week
7th
Week
Thesis topic selected
Research sources identified
Design and development of layout of
research
Literature study on selected topic
Plan the entire study
Select accurate techniques and
methods
Primary data collection
Analysing raw data
Findings of research study
Discussion of findings
Form a research draft
Final submission
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 68
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





