Analyzing Security Risks & Implementation of Hybrid Cloud Architecture
VerifiedAdded on 2023/06/03
|7
|2176
|345
Report
AI Summary
This report provides a detailed analysis of hybrid cloud architectures, focusing on the implementation of Microsoft Azure and Amazon Web Services (AWS) for Smith Securities Ltd. It explores the benefits and issues associated with each platform, including application integration challenges in Azure and the shared security responsibility model in AWS. The report identifies key risks associated with hybrid cloud architecture, such as loss of control, increased integration costs, and security vulnerabilities, and proposes control measures like single sign-on accounts and easy integration security solutions. Furthermore, it outlines general precautions for information security, including strong passwords, firewalls, regular software updates, data backups, and employee education. The document emphasizes the importance of adhering to ethical guidelines and compliance regulations while implementing cloud solutions. Desklib offers a platform where students can access this and other solved assignments for academic support.
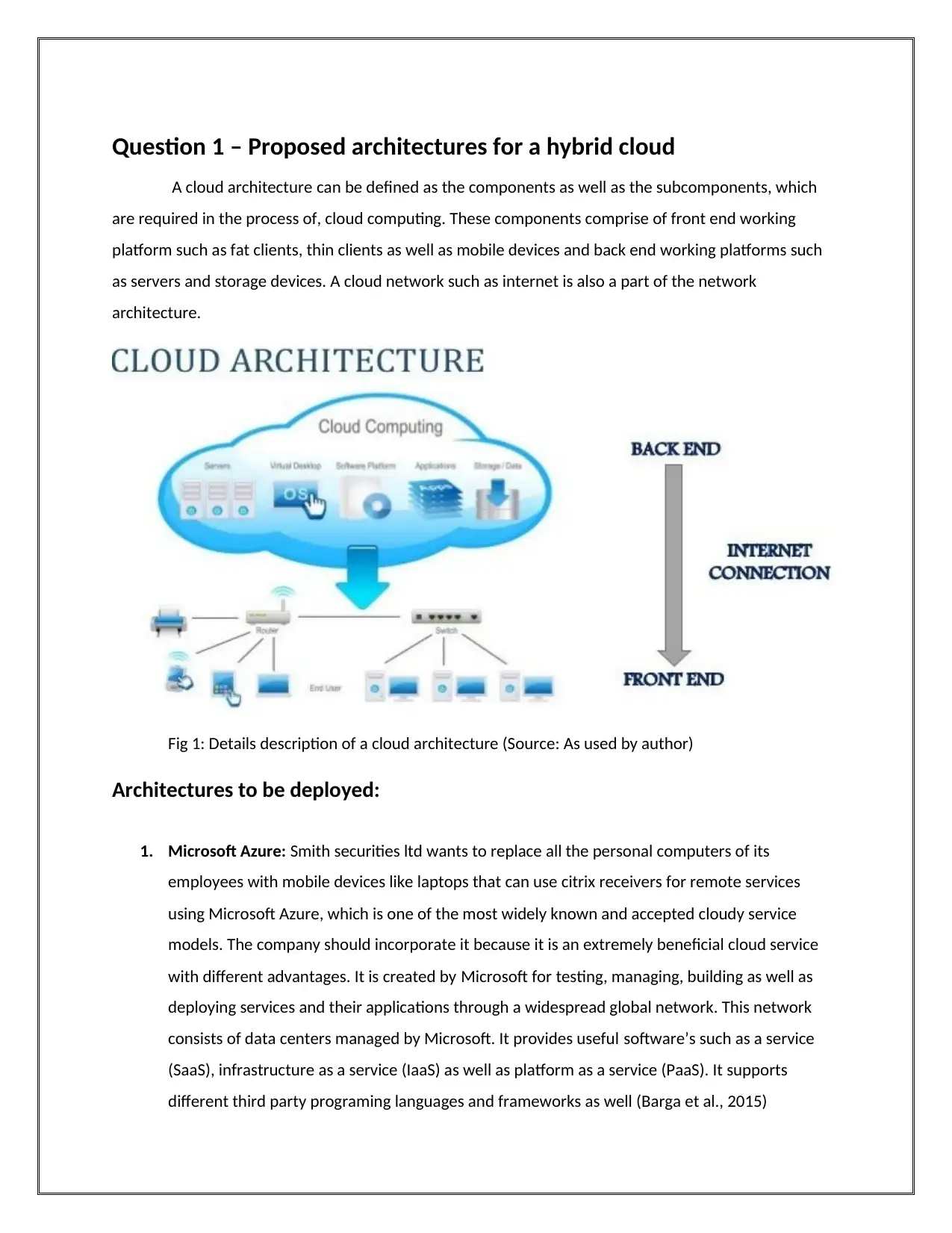
Question 1 – Proposed architectures for a hybrid cloud
A cloud architecture can be defined as the components as well as the subcomponents, which
are required in the process of, cloud computing. These components comprise of front end working
platform such as fat clients, thin clients as well as mobile devices and back end working platforms such
as servers and storage devices. A cloud network such as internet is also a part of the network
architecture.
Fig 1: Details description of a cloud architecture (Source: As used by author)
Architectures to be deployed:
1. Microsoft Azure: Smith securities ltd wants to replace all the personal computers of its
employees with mobile devices like laptops that can use citrix receivers for remote services
using Microsoft Azure, which is one of the most widely known and accepted cloudy service
models. The company should incorporate it because it is an extremely beneficial cloud service
with different advantages. It is created by Microsoft for testing, managing, building as well as
deploying services and their applications through a widespread global network. This network
consists of data centers managed by Microsoft. It provides useful software’s such as a service
(SaaS), infrastructure as a service (IaaS) as well as platform as a service (PaaS). It supports
different third party programing languages and frameworks as well (Barga et al., 2015)
A cloud architecture can be defined as the components as well as the subcomponents, which
are required in the process of, cloud computing. These components comprise of front end working
platform such as fat clients, thin clients as well as mobile devices and back end working platforms such
as servers and storage devices. A cloud network such as internet is also a part of the network
architecture.
Fig 1: Details description of a cloud architecture (Source: As used by author)
Architectures to be deployed:
1. Microsoft Azure: Smith securities ltd wants to replace all the personal computers of its
employees with mobile devices like laptops that can use citrix receivers for remote services
using Microsoft Azure, which is one of the most widely known and accepted cloudy service
models. The company should incorporate it because it is an extremely beneficial cloud service
with different advantages. It is created by Microsoft for testing, managing, building as well as
deploying services and their applications through a widespread global network. This network
consists of data centers managed by Microsoft. It provides useful software’s such as a service
(SaaS), infrastructure as a service (IaaS) as well as platform as a service (PaaS). It supports
different third party programing languages and frameworks as well (Barga et al., 2015)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
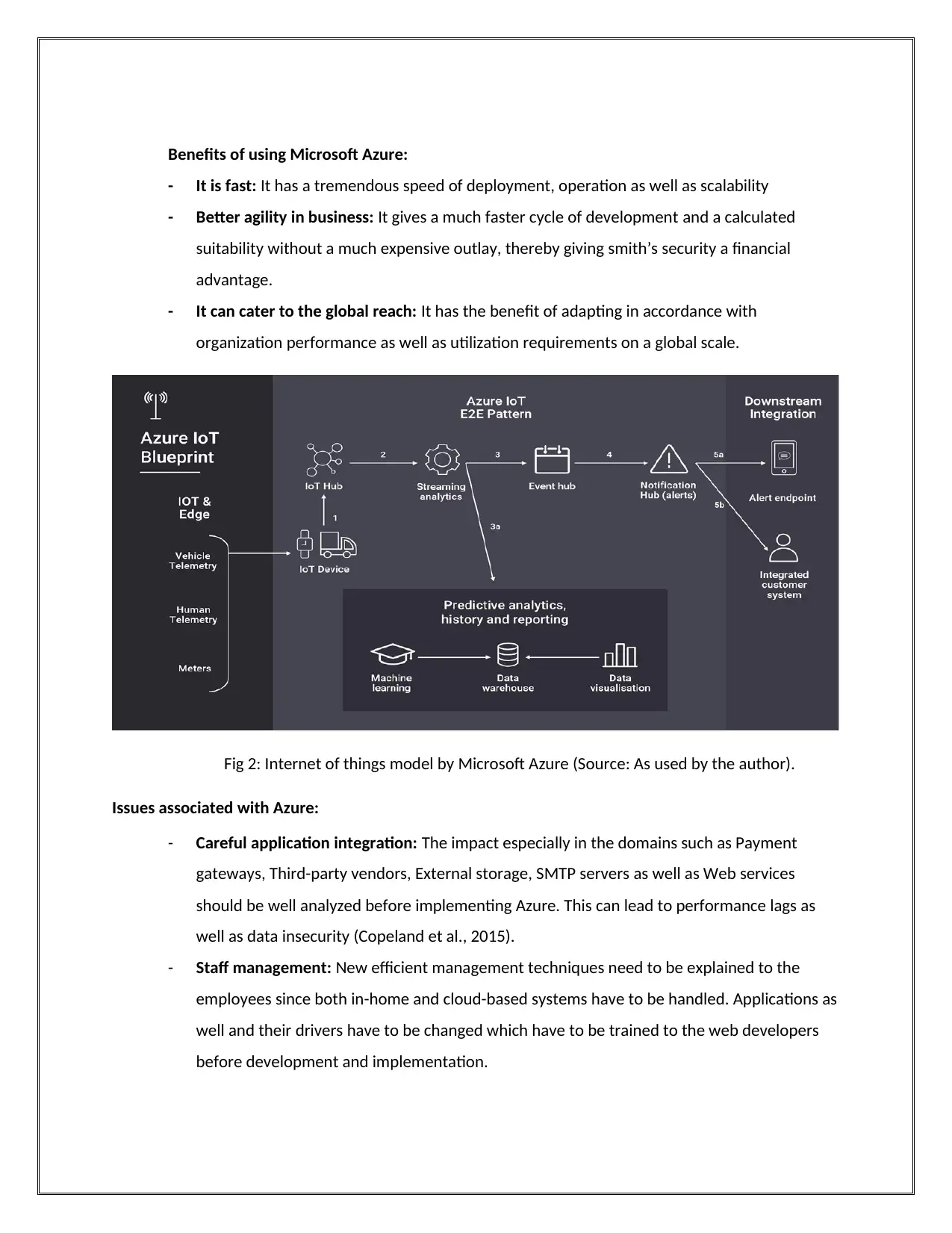
Benefits of using Microsoft Azure:
- It is fast: It has a tremendous speed of deployment, operation as well as scalability
- Better agility in business: It gives a much faster cycle of development and a calculated
suitability without a much expensive outlay, thereby giving smith’s security a financial
advantage.
- It can cater to the global reach: It has the benefit of adapting in accordance with
organization performance as well as utilization requirements on a global scale.
Fig 2: Internet of things model by Microsoft Azure (Source: As used by the author).
Issues associated with Azure:
- Careful application integration: The impact especially in the domains such as Payment
gateways, Third-party vendors, External storage, SMTP servers as well as Web services
should be well analyzed before implementing Azure. This can lead to performance lags as
well as data insecurity (Copeland et al., 2015).
- Staff management: New efficient management techniques need to be explained to the
employees since both in-home and cloud-based systems have to be handled. Applications as
well and their drivers have to be changed which have to be trained to the web developers
before development and implementation.
- It is fast: It has a tremendous speed of deployment, operation as well as scalability
- Better agility in business: It gives a much faster cycle of development and a calculated
suitability without a much expensive outlay, thereby giving smith’s security a financial
advantage.
- It can cater to the global reach: It has the benefit of adapting in accordance with
organization performance as well as utilization requirements on a global scale.
Fig 2: Internet of things model by Microsoft Azure (Source: As used by the author).
Issues associated with Azure:
- Careful application integration: The impact especially in the domains such as Payment
gateways, Third-party vendors, External storage, SMTP servers as well as Web services
should be well analyzed before implementing Azure. This can lead to performance lags as
well as data insecurity (Copeland et al., 2015).
- Staff management: New efficient management techniques need to be explained to the
employees since both in-home and cloud-based systems have to be handled. Applications as
well and their drivers have to be changed which have to be trained to the web developers
before development and implementation.
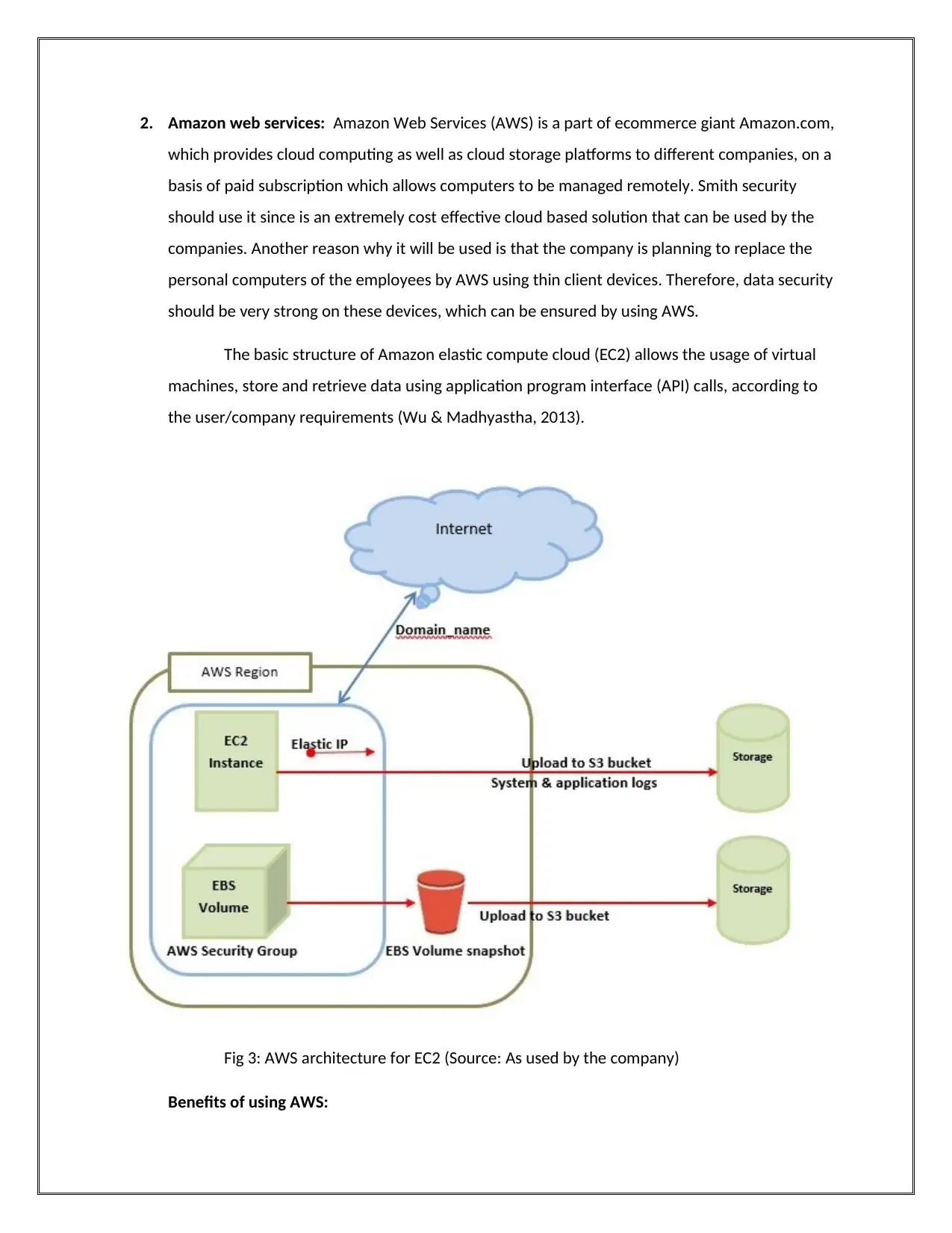
2. Amazon web services: Amazon Web Services (AWS) is a part of ecommerce giant Amazon.com,
which provides cloud computing as well as cloud storage platforms to different companies, on a
basis of paid subscription which allows computers to be managed remotely. Smith security
should use it since is an extremely cost effective cloud based solution that can be used by the
companies. Another reason why it will be used is that the company is planning to replace the
personal computers of the employees by AWS using thin client devices. Therefore, data security
should be very strong on these devices, which can be ensured by using AWS.
The basic structure of Amazon elastic compute cloud (EC2) allows the usage of virtual
machines, store and retrieve data using application program interface (API) calls, according to
the user/company requirements (Wu & Madhyastha, 2013).
Fig 3: AWS architecture for EC2 (Source: As used by the company)
Benefits of using AWS:
which provides cloud computing as well as cloud storage platforms to different companies, on a
basis of paid subscription which allows computers to be managed remotely. Smith security
should use it since is an extremely cost effective cloud based solution that can be used by the
companies. Another reason why it will be used is that the company is planning to replace the
personal computers of the employees by AWS using thin client devices. Therefore, data security
should be very strong on these devices, which can be ensured by using AWS.
The basic structure of Amazon elastic compute cloud (EC2) allows the usage of virtual
machines, store and retrieve data using application program interface (API) calls, according to
the user/company requirements (Wu & Madhyastha, 2013).
Fig 3: AWS architecture for EC2 (Source: As used by the company)
Benefits of using AWS:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
- Security: It has tight security guards across all its data centers 24/7 and an excellent disaster
management system in case of system failures as well as natural disasters. It also exerts a
strict Identity & Access Management (IAM) & Cloud audit Trail to keep a track of all the
activities and who accessed what (Newcombe et al., 2015).
- Flexibility: New infrastructure for self-managing can be built by automatically scaling
aligning closely with the specific need of the organization by effectively managing resource
traffic. Amazon machine images (AMIs) in circulating different clones in multiple geographic
locations in fraction s of seconds, eliminating the need to repeat the same task repeatedly.
Issues associated with AWS:
- The path of learning for a data center which is software based is sometimes difficult for
organizations to follow (Amazon, 2015).
- Billing structure is very confusing as recommended by National Products Inc (NPI). It
recommends users to consult get a reseller involved in order to receive a more detailed
invoice.
- Recently, high profile AWS web server outages have been experienced worldwide.
Question 2 – Risks associated to hybrid cloud architecture:
Multiple risks are associated with a hybrid cloud architecture. They can be classified as:
Risks (in reference to
Desktop as a service DaaS)
Description Control Measures
Microsoft Azure:
1. Loss of control on
accounts
2. Increase in
integration costs
By using Microsoft Azure, Microsoft
reserves the rights to maintain
considerable control over the accounts
and data stored by the companies in
order to ensure optimum data security, as
it mentions in its initial agreement with
the different
Companies (Dinh et al., 2015). It also
causes has the risk of increased charges of
- Utilization of
‘single sign on
(SSO)’ within the
organization that
utilize DaaS cloud
computing.
management system in case of system failures as well as natural disasters. It also exerts a
strict Identity & Access Management (IAM) & Cloud audit Trail to keep a track of all the
activities and who accessed what (Newcombe et al., 2015).
- Flexibility: New infrastructure for self-managing can be built by automatically scaling
aligning closely with the specific need of the organization by effectively managing resource
traffic. Amazon machine images (AMIs) in circulating different clones in multiple geographic
locations in fraction s of seconds, eliminating the need to repeat the same task repeatedly.
Issues associated with AWS:
- The path of learning for a data center which is software based is sometimes difficult for
organizations to follow (Amazon, 2015).
- Billing structure is very confusing as recommended by National Products Inc (NPI). It
recommends users to consult get a reseller involved in order to receive a more detailed
invoice.
- Recently, high profile AWS web server outages have been experienced worldwide.
Question 2 – Risks associated to hybrid cloud architecture:
Multiple risks are associated with a hybrid cloud architecture. They can be classified as:
Risks (in reference to
Desktop as a service DaaS)
Description Control Measures
Microsoft Azure:
1. Loss of control on
accounts
2. Increase in
integration costs
By using Microsoft Azure, Microsoft
reserves the rights to maintain
considerable control over the accounts
and data stored by the companies in
order to ensure optimum data security, as
it mentions in its initial agreement with
the different
Companies (Dinh et al., 2015). It also
causes has the risk of increased charges of
- Utilization of
‘single sign on
(SSO)’ within the
organization that
utilize DaaS cloud
computing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
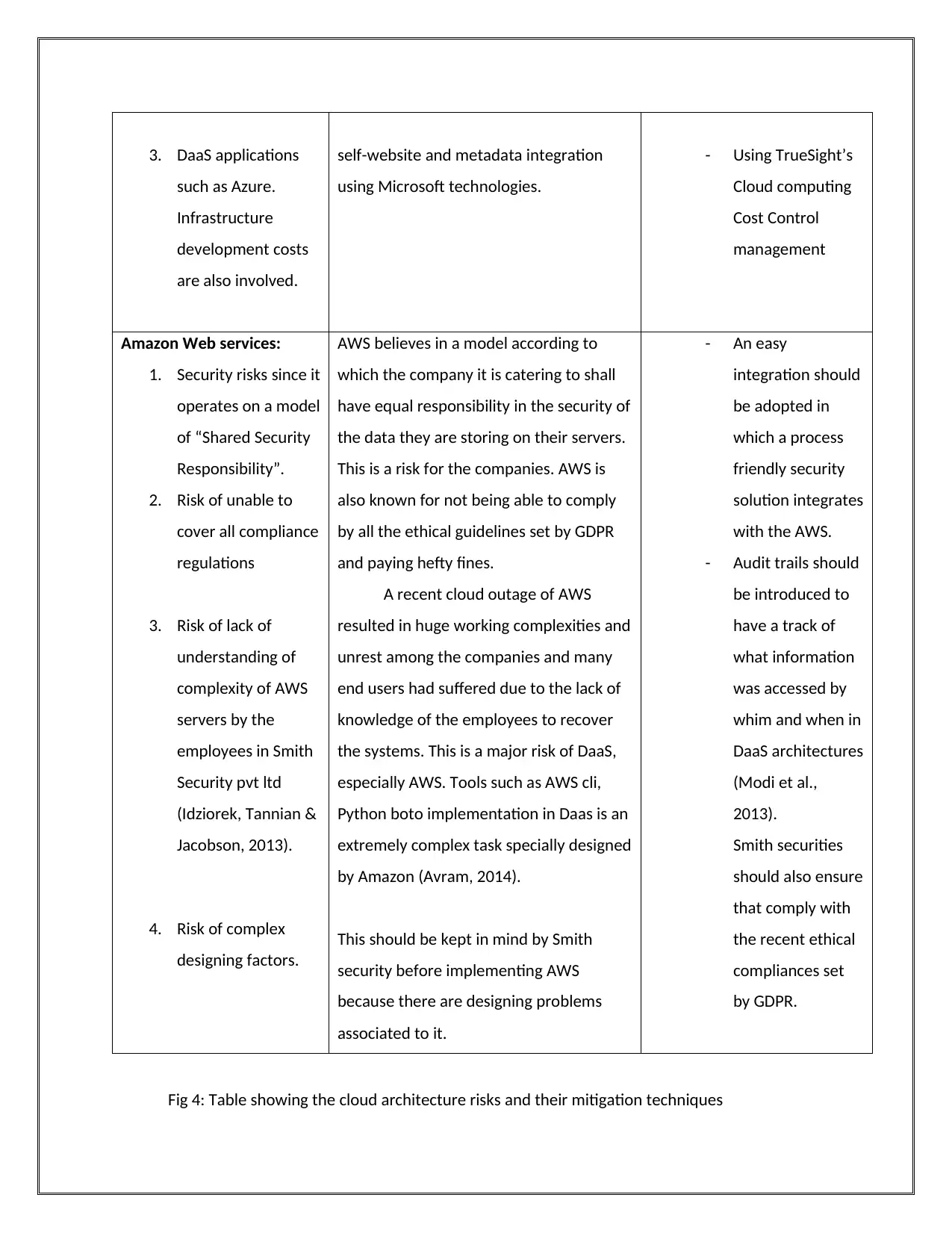
3. DaaS applications
such as Azure.
Infrastructure
development costs
are also involved.
self-website and metadata integration
using Microsoft technologies.
- Using TrueSight’s
Cloud computing
Cost Control
management
Amazon Web services:
1. Security risks since it
operates on a model
of “Shared Security
Responsibility”.
2. Risk of unable to
cover all compliance
regulations
3. Risk of lack of
understanding of
complexity of AWS
servers by the
employees in Smith
Security pvt ltd
(Idziorek, Tannian &
Jacobson, 2013).
4. Risk of complex
designing factors.
AWS believes in a model according to
which the company it is catering to shall
have equal responsibility in the security of
the data they are storing on their servers.
This is a risk for the companies. AWS is
also known for not being able to comply
by all the ethical guidelines set by GDPR
and paying hefty fines.
A recent cloud outage of AWS
resulted in huge working complexities and
unrest among the companies and many
end users had suffered due to the lack of
knowledge of the employees to recover
the systems. This is a major risk of DaaS,
especially AWS. Tools such as AWS cli,
Python boto implementation in Daas is an
extremely complex task specially designed
by Amazon (Avram, 2014).
This should be kept in mind by Smith
security before implementing AWS
because there are designing problems
associated to it.
- An easy
integration should
be adopted in
which a process
friendly security
solution integrates
with the AWS.
- Audit trails should
be introduced to
have a track of
what information
was accessed by
whim and when in
DaaS architectures
(Modi et al.,
2013).
Smith securities
should also ensure
that comply with
the recent ethical
compliances set
by GDPR.
Fig 4: Table showing the cloud architecture risks and their mitigation techniques
such as Azure.
Infrastructure
development costs
are also involved.
self-website and metadata integration
using Microsoft technologies.
- Using TrueSight’s
Cloud computing
Cost Control
management
Amazon Web services:
1. Security risks since it
operates on a model
of “Shared Security
Responsibility”.
2. Risk of unable to
cover all compliance
regulations
3. Risk of lack of
understanding of
complexity of AWS
servers by the
employees in Smith
Security pvt ltd
(Idziorek, Tannian &
Jacobson, 2013).
4. Risk of complex
designing factors.
AWS believes in a model according to
which the company it is catering to shall
have equal responsibility in the security of
the data they are storing on their servers.
This is a risk for the companies. AWS is
also known for not being able to comply
by all the ethical guidelines set by GDPR
and paying hefty fines.
A recent cloud outage of AWS
resulted in huge working complexities and
unrest among the companies and many
end users had suffered due to the lack of
knowledge of the employees to recover
the systems. This is a major risk of DaaS,
especially AWS. Tools such as AWS cli,
Python boto implementation in Daas is an
extremely complex task specially designed
by Amazon (Avram, 2014).
This should be kept in mind by Smith
security before implementing AWS
because there are designing problems
associated to it.
- An easy
integration should
be adopted in
which a process
friendly security
solution integrates
with the AWS.
- Audit trails should
be introduced to
have a track of
what information
was accessed by
whim and when in
DaaS architectures
(Modi et al.,
2013).
Smith securities
should also ensure
that comply with
the recent ethical
compliances set
by GDPR.
Fig 4: Table showing the cloud architecture risks and their mitigation techniques

Question 3 – General precautions for information security:
Some of the general data security measures can be summarized below as:
- Establishing very strong passwords: An ideal password is a combination of upper and lower
case letters, numbers as well as symbols, making it 8-12 characters long. In addition, it
should be made sure that all employees have their separate unique username and password
and not a single common password, which can be accessible, by all.
- Setting up a strong firewall: A firewall is a computer program that protects the organization
network by managing and controlling the inward and outward internet traffic. They are
standardized across the board and should be commonly implemented across each devices
to the same priority levels by the system administrators. They also prevent malicious attacks
by hackers and protect the systems from virus attacks. Some of the popular enterprise
firewall protection packages are Kaspersky internet security, Fortigate, Pfsense etc
(Fernando, Loke & Rahayu, 2013).
- Programs should be updated regularly: The programs that run in the laptops and
workstations should be regularly updated and update patches should be regularly installed
in all systems to ensure updated security engines within the systems and servers of the
organization. If software’s are not properly maintained including the security software’s,
they are of no good. It also helps the admins to stay updated on any recent bugs or issues
fixed by the application developers.
- Regular back up and diligent monitoring: All the important files and data should be
regularly backed up in secure spaces to eliminate the risk of data loss in case of system
failures or even natural disasters. Scheduled back up cycles such complete weekly data
backup as well as incremental data backups on every night should be implemented. There
should be a dedicated team for risk management that will monitor all the important internal
tasks.
- Employee education: All employees should be well informed and trained on the
implementation of any new technology as well as cloud computing architectures and their
working (Lakshminarayanan, Kumar & Raju, 2013).
Some of the general data security measures can be summarized below as:
- Establishing very strong passwords: An ideal password is a combination of upper and lower
case letters, numbers as well as symbols, making it 8-12 characters long. In addition, it
should be made sure that all employees have their separate unique username and password
and not a single common password, which can be accessible, by all.
- Setting up a strong firewall: A firewall is a computer program that protects the organization
network by managing and controlling the inward and outward internet traffic. They are
standardized across the board and should be commonly implemented across each devices
to the same priority levels by the system administrators. They also prevent malicious attacks
by hackers and protect the systems from virus attacks. Some of the popular enterprise
firewall protection packages are Kaspersky internet security, Fortigate, Pfsense etc
(Fernando, Loke & Rahayu, 2013).
- Programs should be updated regularly: The programs that run in the laptops and
workstations should be regularly updated and update patches should be regularly installed
in all systems to ensure updated security engines within the systems and servers of the
organization. If software’s are not properly maintained including the security software’s,
they are of no good. It also helps the admins to stay updated on any recent bugs or issues
fixed by the application developers.
- Regular back up and diligent monitoring: All the important files and data should be
regularly backed up in secure spaces to eliminate the risk of data loss in case of system
failures or even natural disasters. Scheduled back up cycles such complete weekly data
backup as well as incremental data backups on every night should be implemented. There
should be a dedicated team for risk management that will monitor all the important internal
tasks.
- Employee education: All employees should be well informed and trained on the
implementation of any new technology as well as cloud computing architectures and their
working (Lakshminarayanan, Kumar & Raju, 2013).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References:
Amazon, E. C. (2015). Amazon web services. Available in: http://aws. amazon. com/es/ec2/(November
2012).
Avram, M. G. (2014). Advantages and challenges of adopting cloud computing from an enterprise
perspective. Procedia Technology, 12, 529-534.
Barga, R., Fontama, V., Tok, W. H., & Cabrera-Cordon, L. (2015). Predictive analytics with Microsoft Azure
machine learning. Apress.
Copeland, M., Soh, J., Puca, A., Manning, M., & Gollob, D. (2015). Microsoft azure and cloud computing.
In Microsoft Azure (pp. 3-26). Apress, Berkeley, CA.
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud computing: architecture,
applications, and approaches. Wireless communications and mobile computing, 13(18), 1587-1611.
Fernando, N., Loke, S. W., & Rahayu, W. (2013). Mobile cloud computing: A survey. Future generation
computer systems, 29(1), 84-106.
Idziorek, J., Tannian, M. F., & Jacobson, D. (2013). The insecurity of cloud utility models. IT
Professional, 15(2), 22-27.
Lakshminarayanan, R., Kumar, B., & Raju, M. (2013). Cloud computing benefits for educational
institutions. arXiv preprint arXiv:1305.2616.
Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (2013). A survey on security issues and
solutions at different layers of Cloud computing. The journal of supercomputing, 63(2), 561-592.
Modi, C., Patel, D., Borisaniya, B., Patel, H., Patel, A., & Rajarajan, M. (2013). A survey of intrusion
detection techniques in cloud. Journal of network and computer applications, 36(1), 42-57.
Newcombe, C., Rath, T., Zhang, F., Munteanu, B., Brooker, M., & Deardeuff, M. (2015). How Amazon
web services uses formal methods. Communications of the ACM, 58(4), 66-73.
Wu, Z., & Madhyastha, H. V. (2013). Understanding the latency benefits of multi-cloud webservice
deployments. ACM SIGCOMM Computer Communication Review, 43(2), 13-20.
Amazon, E. C. (2015). Amazon web services. Available in: http://aws. amazon. com/es/ec2/(November
2012).
Avram, M. G. (2014). Advantages and challenges of adopting cloud computing from an enterprise
perspective. Procedia Technology, 12, 529-534.
Barga, R., Fontama, V., Tok, W. H., & Cabrera-Cordon, L. (2015). Predictive analytics with Microsoft Azure
machine learning. Apress.
Copeland, M., Soh, J., Puca, A., Manning, M., & Gollob, D. (2015). Microsoft azure and cloud computing.
In Microsoft Azure (pp. 3-26). Apress, Berkeley, CA.
Dinh, H. T., Lee, C., Niyato, D., & Wang, P. (2013). A survey of mobile cloud computing: architecture,
applications, and approaches. Wireless communications and mobile computing, 13(18), 1587-1611.
Fernando, N., Loke, S. W., & Rahayu, W. (2013). Mobile cloud computing: A survey. Future generation
computer systems, 29(1), 84-106.
Idziorek, J., Tannian, M. F., & Jacobson, D. (2013). The insecurity of cloud utility models. IT
Professional, 15(2), 22-27.
Lakshminarayanan, R., Kumar, B., & Raju, M. (2013). Cloud computing benefits for educational
institutions. arXiv preprint arXiv:1305.2616.
Modi, C., Patel, D., Borisaniya, B., Patel, A., & Rajarajan, M. (2013). A survey on security issues and
solutions at different layers of Cloud computing. The journal of supercomputing, 63(2), 561-592.
Modi, C., Patel, D., Borisaniya, B., Patel, H., Patel, A., & Rajarajan, M. (2013). A survey of intrusion
detection techniques in cloud. Journal of network and computer applications, 36(1), 42-57.
Newcombe, C., Rath, T., Zhang, F., Munteanu, B., Brooker, M., & Deardeuff, M. (2015). How Amazon
web services uses formal methods. Communications of the ACM, 58(4), 66-73.
Wu, Z., & Madhyastha, H. V. (2013). Understanding the latency benefits of multi-cloud webservice
deployments. ACM SIGCOMM Computer Communication Review, 43(2), 13-20.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





