ICT in Business: Collaboration Tools, Cloud Storage and Security
VerifiedAdded on 2023/06/11
|15
|4060
|53
Report
AI Summary
This report assesses the role of information and communication technologies (ICT) in business, highlighting their importance in enhancing work efficiency, data management, and accessibility. It details various collaboration tools like Monday.com and Slack, emphasizing their advantages and disadvantages in facilitating teamwork and communication. The report further explains cloud storage, its types (public, private, hybrid), and its applications in data backup and sharing, while also addressing security concerns and regulatory compliance. Cloud computing is discussed in terms of delivering computing services over the internet, including Infrastructure as a Service and Platform as a Service, underlining its cost advantages and scalability. Additionally, the report distinguishes between privacy and security, emphasizing their importance in building trust and protecting sensitive data. Finally, it touches upon the benefits and challenges of using private internet networks.

IPSDA Assignment
Report Template
Report Template
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ABSTRACT SUMMARY
This report assess about information and communication technologies as well as its
importance to businesses. It provides brief details about several collaboration tools which aids
organisation to keep connected with its employees and customers. It determines the importance
of cloud storage and cloud computing for organisation to effectively handle huge amount of data
it has collected from several sources. This report describes the difference between private and
public internet as well as benefits and challenges of using private internet.
This report assess about information and communication technologies as well as its
importance to businesses. It provides brief details about several collaboration tools which aids
organisation to keep connected with its employees and customers. It determines the importance
of cloud storage and cloud computing for organisation to effectively handle huge amount of data
it has collected from several sources. This report describes the difference between private and
public internet as well as benefits and challenges of using private internet.

Contents
INTRODUCTION...........................................................................................................................1
MAIN BODY ..................................................................................................................................1
Collaboration tools.......................................................................................................................1
Cloud storage...............................................................................................................................2
Cloud computing..........................................................................................................................4
Privacy and Security....................................................................................................................5
Discussion of collaboration tools.................................................................................................6
Privacy and security at time of pandemic....................................................................................6
Private vs Public Internet.............................................................................................................7
CONCLUSION................................................................................................................................8
REFERENCES..............................................................................................................................10
INTRODUCTION...........................................................................................................................1
MAIN BODY ..................................................................................................................................1
Collaboration tools.......................................................................................................................1
Cloud storage...............................................................................................................................2
Cloud computing..........................................................................................................................4
Privacy and Security....................................................................................................................5
Discussion of collaboration tools.................................................................................................6
Privacy and security at time of pandemic....................................................................................6
Private vs Public Internet.............................................................................................................7
CONCLUSION................................................................................................................................8
REFERENCES..............................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTRODUCTION
Information and communication technology is described as varied collection of
technological tools and resources which are used to convey, store, design, share and transact
information. These includes Internet, computers, live broadcasting technological, podcasts,
storage devices etc. These refer to technology which is utilise for routine, every day tasks like
sending an email, searching on internet and more. Role of information and communication
technology in business is that it provides better work efficiency and helps in tracking as well as
storing data effectively (Aktas, 2018). It assess organizations to have great accessibility and
collaboration with help of cloud computing. ICT enhances knowledge and information
management internally in enterprises and minimises costs of transactions as well as accelerates
speed of reliability of transactions for both business to consumer and business to business
transactions. At the time of pandemic ICT has strongly helped businesses to stay relevant and
effectively reach to its customers. It allows businesses to take online ordering which is
inexpensive and flexible. It reduces firm's overhead expenses as they started operating virtually.
Utilising online platforms facilitated business to collect data of its customers and present them
with personalised options when they were in lock down. As customers have changed their
preferences to contactless services, companies started to adopt automation which has improved
their communication with people. Pandemic assists to accelerate the digital transformation and
makes a landscape which encourages innovation and technological adoption that further helps in
moving forward.
This report covers various collaboration tools and where they are used. It explains what is
cloud storage, cloud computing, privacy & security as well as its usage, suitability and
application. It covers collaboration tools and how it helped businesses at time of pandemic. It
discusses benefits and issues of private internet local to specific nation.
MAIN BODY
Collaboration tools
Tools like software programs, applications and platforms which aid companies as well as
its people to contour the process of creativity are collaborative tools. These tools assists
managers to assigns tasks effectively, track the progress, report on results and often enhances
workflows as well as communication (Altinoz, Vasbieva and Kalugina, 2021). Efficient
1
Information and communication technology is described as varied collection of
technological tools and resources which are used to convey, store, design, share and transact
information. These includes Internet, computers, live broadcasting technological, podcasts,
storage devices etc. These refer to technology which is utilise for routine, every day tasks like
sending an email, searching on internet and more. Role of information and communication
technology in business is that it provides better work efficiency and helps in tracking as well as
storing data effectively (Aktas, 2018). It assess organizations to have great accessibility and
collaboration with help of cloud computing. ICT enhances knowledge and information
management internally in enterprises and minimises costs of transactions as well as accelerates
speed of reliability of transactions for both business to consumer and business to business
transactions. At the time of pandemic ICT has strongly helped businesses to stay relevant and
effectively reach to its customers. It allows businesses to take online ordering which is
inexpensive and flexible. It reduces firm's overhead expenses as they started operating virtually.
Utilising online platforms facilitated business to collect data of its customers and present them
with personalised options when they were in lock down. As customers have changed their
preferences to contactless services, companies started to adopt automation which has improved
their communication with people. Pandemic assists to accelerate the digital transformation and
makes a landscape which encourages innovation and technological adoption that further helps in
moving forward.
This report covers various collaboration tools and where they are used. It explains what is
cloud storage, cloud computing, privacy & security as well as its usage, suitability and
application. It covers collaboration tools and how it helped businesses at time of pandemic. It
discusses benefits and issues of private internet local to specific nation.
MAIN BODY
Collaboration tools
Tools like software programs, applications and platforms which aid companies as well as
its people to contour the process of creativity are collaborative tools. These tools assists
managers to assigns tasks effectively, track the progress, report on results and often enhances
workflows as well as communication (Altinoz, Vasbieva and Kalugina, 2021). Efficient
1
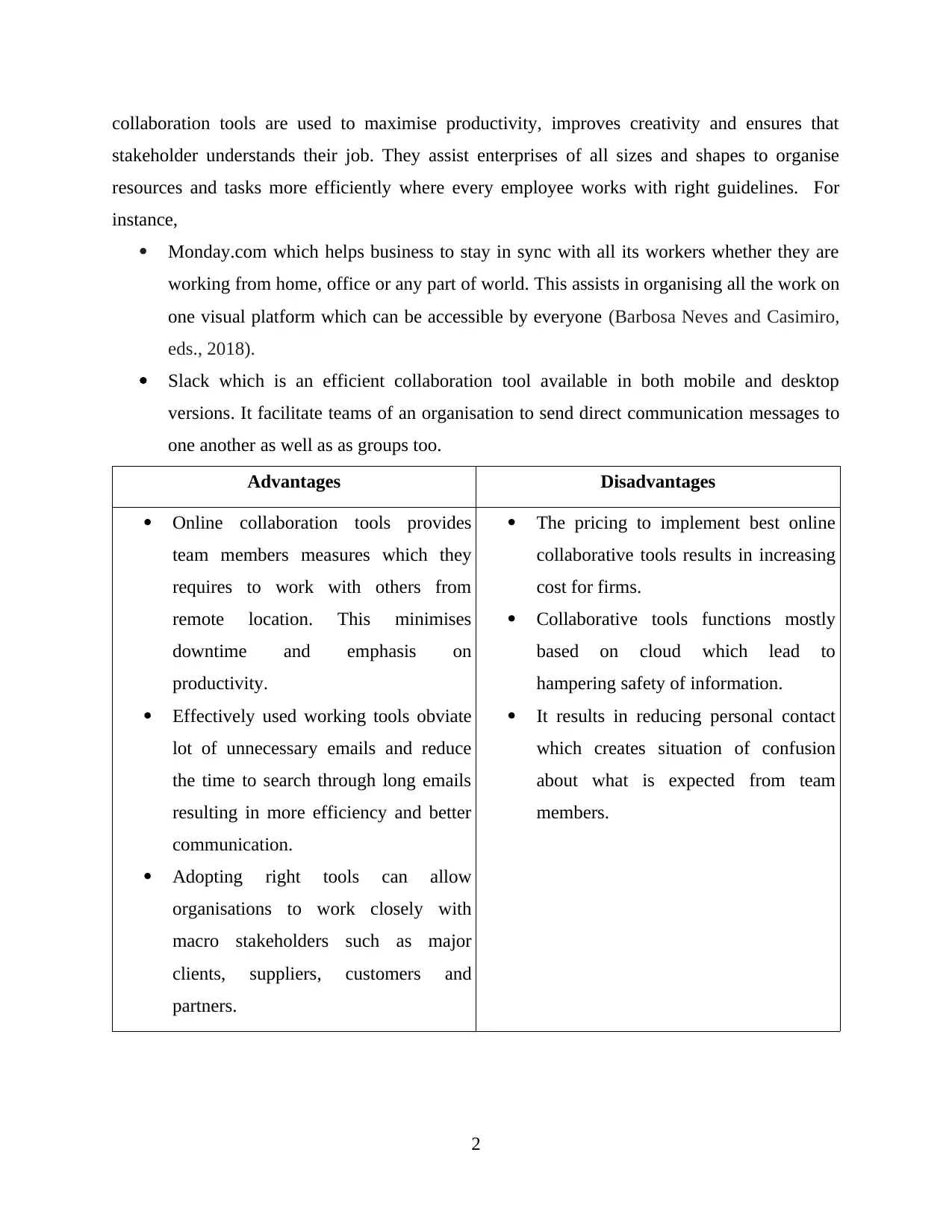
collaboration tools are used to maximise productivity, improves creativity and ensures that
stakeholder understands their job. They assist enterprises of all sizes and shapes to organise
resources and tasks more efficiently where every employee works with right guidelines. For
instance,
Monday.com which helps business to stay in sync with all its workers whether they are
working from home, office or any part of world. This assists in organising all the work on
one visual platform which can be accessible by everyone (Barbosa Neves and Casimiro,
eds., 2018).
Slack which is an efficient collaboration tool available in both mobile and desktop
versions. It facilitate teams of an organisation to send direct communication messages to
one another as well as as groups too.
Advantages Disadvantages
Online collaboration tools provides
team members measures which they
requires to work with others from
remote location. This minimises
downtime and emphasis on
productivity.
Effectively used working tools obviate
lot of unnecessary emails and reduce
the time to search through long emails
resulting in more efficiency and better
communication.
Adopting right tools can allow
organisations to work closely with
macro stakeholders such as major
clients, suppliers, customers and
partners.
The pricing to implement best online
collaborative tools results in increasing
cost for firms.
Collaborative tools functions mostly
based on cloud which lead to
hampering safety of information.
It results in reducing personal contact
which creates situation of confusion
about what is expected from team
members.
2
stakeholder understands their job. They assist enterprises of all sizes and shapes to organise
resources and tasks more efficiently where every employee works with right guidelines. For
instance,
Monday.com which helps business to stay in sync with all its workers whether they are
working from home, office or any part of world. This assists in organising all the work on
one visual platform which can be accessible by everyone (Barbosa Neves and Casimiro,
eds., 2018).
Slack which is an efficient collaboration tool available in both mobile and desktop
versions. It facilitate teams of an organisation to send direct communication messages to
one another as well as as groups too.
Advantages Disadvantages
Online collaboration tools provides
team members measures which they
requires to work with others from
remote location. This minimises
downtime and emphasis on
productivity.
Effectively used working tools obviate
lot of unnecessary emails and reduce
the time to search through long emails
resulting in more efficiency and better
communication.
Adopting right tools can allow
organisations to work closely with
macro stakeholders such as major
clients, suppliers, customers and
partners.
The pricing to implement best online
collaborative tools results in increasing
cost for firms.
Collaborative tools functions mostly
based on cloud which lead to
hampering safety of information.
It results in reducing personal contact
which creates situation of confusion
about what is expected from team
members.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cloud storage
The model of computer data storage where digital data is stocked in pools called as cloud
is known as cloud storage. It provides quick, low cost and extremely durable storage for data
approached less than once a month. It is used to retrieve, store and share data which is both
scalable and reliable. Cloud storage facilitates organisations to save files and information in an
off site platform which they can access by network connection. It is used when users runs out of
storage, thus the need to transfer documents to external storage arises. Cloud storage is
appropriate choice for development of application and its testing. It involves zero capital and low
operation cost which assist in helping firm of any type and size to fasten its prototype and
development (Bon, 2019). Applications of cloud storage contains data backup, resource service
and data sharing. It also assist in providing interface which are standardised to support other
services of network. Cloud storage can be of various types such as: Public cloud storage- These cloud services are owned by third party, a firm who deals in
cloud services and then they make it available to public or a huge group of industry.
Users of public cloud are often the residential users and they can access to it using
internet services (Camacho, Hassanein and Head, 2018). Examples of public cloud
storage are Google, Amazon, IBM etc. Private cloud storage- This system is designed for private firms and operated entirely for
the users. Its purpose is to form cloud storage which can be accessed only by the
employees of enterprise or by third parties with due permission but on by general public
(Khakimov, Karlinskiy and Rakhmatullin, 2018). It has extra security and organisation as
well as it users can personalise it as per their preferences.
Hybrid cloud storage- It is the system which contains more than two clouds for instance
community cloud, private or public cloud. Often, each cloud includes at least one public
and one private cloud. In hybrid cloud, a firm gives and manages their resources both in
out and in house (Khodjayev, 2021). For example, it is used by banking industry where
they allowed its users to store their data in public cloud and details which are confidential
in nature are stored in private cloud.
Advantages Disadvantages
It helps in freeing workforce with
activities of storation such as
Security is the major concern with
cloud storage services. It sometimes
3
The model of computer data storage where digital data is stocked in pools called as cloud
is known as cloud storage. It provides quick, low cost and extremely durable storage for data
approached less than once a month. It is used to retrieve, store and share data which is both
scalable and reliable. Cloud storage facilitates organisations to save files and information in an
off site platform which they can access by network connection. It is used when users runs out of
storage, thus the need to transfer documents to external storage arises. Cloud storage is
appropriate choice for development of application and its testing. It involves zero capital and low
operation cost which assist in helping firm of any type and size to fasten its prototype and
development (Bon, 2019). Applications of cloud storage contains data backup, resource service
and data sharing. It also assist in providing interface which are standardised to support other
services of network. Cloud storage can be of various types such as: Public cloud storage- These cloud services are owned by third party, a firm who deals in
cloud services and then they make it available to public or a huge group of industry.
Users of public cloud are often the residential users and they can access to it using
internet services (Camacho, Hassanein and Head, 2018). Examples of public cloud
storage are Google, Amazon, IBM etc. Private cloud storage- This system is designed for private firms and operated entirely for
the users. Its purpose is to form cloud storage which can be accessed only by the
employees of enterprise or by third parties with due permission but on by general public
(Khakimov, Karlinskiy and Rakhmatullin, 2018). It has extra security and organisation as
well as it users can personalise it as per their preferences.
Hybrid cloud storage- It is the system which contains more than two clouds for instance
community cloud, private or public cloud. Often, each cloud includes at least one public
and one private cloud. In hybrid cloud, a firm gives and manages their resources both in
out and in house (Khodjayev, 2021). For example, it is used by banking industry where
they allowed its users to store their data in public cloud and details which are confidential
in nature are stored in private cloud.
Advantages Disadvantages
It helps in freeing workforce with
activities of storation such as
Security is the major concern with
cloud storage services. It sometimes
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

installation, acquiring, administration
and fixation. It takes away the
responsibilities of maintaining and
securing the stored data.
Adopting cloud storage services speeds
up process of initiation and adds to
storage capabilities of firm.
It is cost effective as it facilitates firms
to treat cloud storage cost as existing
operating expenses and not as capital
expenses associated with investments
and tax (Kosyakova, Zhilyunov and
Astashev, 2020).
Cloud storage maximises scalability of
storage for organisation as they are
restrained with limited storage
facilitates.
Storing information on cloud helps in
continuity of business in case of natural
disaster or any other uncertainty.
have occasional breaches resulting in
theft of users data.
It can pose certain limit on control of
users data.
In some cases, delays in information
transmission to and from the cloud
server happens due to traffic congestion
mostly when working on public
network.
Regulatory compliance posed by
certain industry such as finance or
healthcare prevents firms to use cloud
storage for specific kinds of files such
as investment or medical records.
Cloud computing
Cloud computing is referred as activities of delivering computing services consisting
databases, networking, servers, storage, analytics etc. over internet in order to improve
innovation, flexible resources and achieve economies of scale. Its major purpose is to share data,
software and resources. In cloud computing internet perform as hidden cable which links
everything including all virtual and physical servers al around world. It is used by organisations
to store data and provides remote access to any data that is related to work. It is use to speed to
market by enabling users to provide their applications to market rapidly. Major suitability of
cloud computing for organisation is that it provides cost advantage and simpler process of
deployment (Lediga and Fombad, 2018). It allows to easily access to trending information,
automatic updates, huge scalability and effective communication technologies. Examples of
4
and fixation. It takes away the
responsibilities of maintaining and
securing the stored data.
Adopting cloud storage services speeds
up process of initiation and adds to
storage capabilities of firm.
It is cost effective as it facilitates firms
to treat cloud storage cost as existing
operating expenses and not as capital
expenses associated with investments
and tax (Kosyakova, Zhilyunov and
Astashev, 2020).
Cloud storage maximises scalability of
storage for organisation as they are
restrained with limited storage
facilitates.
Storing information on cloud helps in
continuity of business in case of natural
disaster or any other uncertainty.
have occasional breaches resulting in
theft of users data.
It can pose certain limit on control of
users data.
In some cases, delays in information
transmission to and from the cloud
server happens due to traffic congestion
mostly when working on public
network.
Regulatory compliance posed by
certain industry such as finance or
healthcare prevents firms to use cloud
storage for specific kinds of files such
as investment or medical records.
Cloud computing
Cloud computing is referred as activities of delivering computing services consisting
databases, networking, servers, storage, analytics etc. over internet in order to improve
innovation, flexible resources and achieve economies of scale. Its major purpose is to share data,
software and resources. In cloud computing internet perform as hidden cable which links
everything including all virtual and physical servers al around world. It is used by organisations
to store data and provides remote access to any data that is related to work. It is use to speed to
market by enabling users to provide their applications to market rapidly. Major suitability of
cloud computing for organisation is that it provides cost advantage and simpler process of
deployment (Lediga and Fombad, 2018). It allows to easily access to trending information,
automatic updates, huge scalability and effective communication technologies. Examples of
4

applications of cloud computing are Dropbox, Salesforce, Google App engine, Apache Stratos
and Amazon Web Services. Various types of cloud computing are as follows: Infrastructure as a Service- It is a kind of cloud computing where a service provider is
liable to offer servers, networking and storage over virtual interface. In this type, users do
not have to manage cloud infrastructure as they have full power over operating systems,
storage and deployed applications (Neidhardt and Wörndl, 2020). A third party hosts
servers, software, hardware and other infrastructure attributes as well as maintains
backup of users data.
Platform as a service- This type offers environment of development and positioning in
cloud which allows users to create and run applications without complexity of keeping
infrastructure. In this type, users buys resources from third party which can be accessed
by secure network and pay on regular basis.
Advantages Disadvantages
Cloud computing infrastructure allows
to maximise scale of demand which
backs up fluctuating workloads.
Firms can evaluate their degree of
control on its servers with range of
options of as a service.
Virtual private cloud and encryption of
information helps in keeping data
secure.
Cloud computing adopts resources
which are remote that helps in saving
firm's costs and other tools.
Providers of service frequently updates
offerings to provides users with
trending and up to date technologies.
Biggest challenge in cloud computing
is outage and downtime as service
providers offers services to large
number of clients on daily basis.
Lack of good internet connection do
not enable users to access their data on
cloud. In addition to that, using open
wifi to access information on cloud can
risk data on servers.
In case when service provider owns and
manages infrastructure, a user may
have little control over their cloud
server.
5
and Amazon Web Services. Various types of cloud computing are as follows: Infrastructure as a Service- It is a kind of cloud computing where a service provider is
liable to offer servers, networking and storage over virtual interface. In this type, users do
not have to manage cloud infrastructure as they have full power over operating systems,
storage and deployed applications (Neidhardt and Wörndl, 2020). A third party hosts
servers, software, hardware and other infrastructure attributes as well as maintains
backup of users data.
Platform as a service- This type offers environment of development and positioning in
cloud which allows users to create and run applications without complexity of keeping
infrastructure. In this type, users buys resources from third party which can be accessed
by secure network and pay on regular basis.
Advantages Disadvantages
Cloud computing infrastructure allows
to maximise scale of demand which
backs up fluctuating workloads.
Firms can evaluate their degree of
control on its servers with range of
options of as a service.
Virtual private cloud and encryption of
information helps in keeping data
secure.
Cloud computing adopts resources
which are remote that helps in saving
firm's costs and other tools.
Providers of service frequently updates
offerings to provides users with
trending and up to date technologies.
Biggest challenge in cloud computing
is outage and downtime as service
providers offers services to large
number of clients on daily basis.
Lack of good internet connection do
not enable users to access their data on
cloud. In addition to that, using open
wifi to access information on cloud can
risk data on servers.
In case when service provider owns and
manages infrastructure, a user may
have little control over their cloud
server.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Privacy and Security
Privacy is described as the control users have on their personal information and how their
data can be used. It enable users to form barriers and maintain boundaries to protect themselves
from unwanted interferences. It is a fundamental right which is crucial for autonomy and protects
dignity of users. Whereas, security determines how protected is users or firms information. It
helps in protection against unauthorised access to information or data. Data security and privacy
is crucial for building trust between users and organisations (IPeraković, Periša and Sente, 2018).
It is important as lack of security and privacy can lead to breach as well as theft of data of
company and its users which can lead to disclosing their strategies, customer information, future
plans etc. It provides protection to companies from any type of misuse of data from others. Data
privacy saves businesses information from cyber crime, fraud or corruption. There are various
challenges faced by businesses in relation to privacy and security such as the data is growing at
an exponential rate which makes it difficult for firms to effectively maintain it. The cost of
maintaining privacy of data is increasing constantly resulting in adding up to overhead expenses
of businesses.
Discussion of collaboration tools
One of the significant collaboration tool is Zoom which is a web software program
utilised for video conferencing. It is a free account which allows users to add up to hundred
people at once and facilitates users to make unlimited phone calls and hold unlimited meetings. It
helps business to host meetings with its remote workers and clients. It is known for its ease and
high quality video collaboration facilitates (Rojas, 2018). At the time of pandemic, most
companies switch to Zoom as it is simple to use and provides best quality. As people were in
lock down they needed tools to connect with people, Zoom emerged as strong app which helps
businesses to keep in touch with its employees.
Another collaboration tool is Trello which enable users to organise tasks, projects and
activities associated with them into boards. It provides a portal where everyday tasks can be
tracked and shared within team mates. With the help of Trello, users can find information like
what work is being done by whom and its progress. It is used as a project management hub to
manage teams of hundreds which drives their productivity (Tay, Tay and Klainin‐Yobas, 2018).
During pandemic, Trello helps in fostering purposeful collaboration for remote workforce and
resulting in reducing security risks. It assists businesses to encourage cross team participation by
6
Privacy is described as the control users have on their personal information and how their
data can be used. It enable users to form barriers and maintain boundaries to protect themselves
from unwanted interferences. It is a fundamental right which is crucial for autonomy and protects
dignity of users. Whereas, security determines how protected is users or firms information. It
helps in protection against unauthorised access to information or data. Data security and privacy
is crucial for building trust between users and organisations (IPeraković, Periša and Sente, 2018).
It is important as lack of security and privacy can lead to breach as well as theft of data of
company and its users which can lead to disclosing their strategies, customer information, future
plans etc. It provides protection to companies from any type of misuse of data from others. Data
privacy saves businesses information from cyber crime, fraud or corruption. There are various
challenges faced by businesses in relation to privacy and security such as the data is growing at
an exponential rate which makes it difficult for firms to effectively maintain it. The cost of
maintaining privacy of data is increasing constantly resulting in adding up to overhead expenses
of businesses.
Discussion of collaboration tools
One of the significant collaboration tool is Zoom which is a web software program
utilised for video conferencing. It is a free account which allows users to add up to hundred
people at once and facilitates users to make unlimited phone calls and hold unlimited meetings. It
helps business to host meetings with its remote workers and clients. It is known for its ease and
high quality video collaboration facilitates (Rojas, 2018). At the time of pandemic, most
companies switch to Zoom as it is simple to use and provides best quality. As people were in
lock down they needed tools to connect with people, Zoom emerged as strong app which helps
businesses to keep in touch with its employees.
Another collaboration tool is Trello which enable users to organise tasks, projects and
activities associated with them into boards. It provides a portal where everyday tasks can be
tracked and shared within team mates. With the help of Trello, users can find information like
what work is being done by whom and its progress. It is used as a project management hub to
manage teams of hundreds which drives their productivity (Tay, Tay and Klainin‐Yobas, 2018).
During pandemic, Trello helps in fostering purposeful collaboration for remote workforce and
resulting in reducing security risks. It assists businesses to encourage cross team participation by
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

use of shared resources. Trello has proved to be great tool which effectively manage connections
and arranges check ins and community.
Privacy and security at time of pandemic
At time of pandemic, businesses faces various threats in terms of privacy and security. As
the whole world was in lock down which encourages workforce to work from home. As a result,
technology has become more essential in working lives. But the increase in hybrid working leads
to rise in risks of cybersecurity also. The unsecured network of remote workers resulted in
breaching company's privacy by hackers. Companies have started to implement more artificial
intelligence as it maximises their efficiency but also expose firm to cyber crimes. Businesses
faced several phishing attacks as hackers sometimes pose as important persons and ends up
breaching privacy over emails. Rupture of security involves risks like malware, spam,
compromised business email, malicious link or domains (Warshawski, Itzhaki and Barnoy,
2019). Employees were connected only through the information and communication
technologies, thus the situations of privacy breach from third party or hackers take place
frequently. Potential risk from these breaches were stolen company's data or exposure to its
strategies. During pandemic, companies made communication with its customer only through
information and communication technologies, hence at time when of downtime or internet
outage, firms ended up losing major business opportunities.
Businesses can take several measures to protect themselves from risks associated with
privacy and security which are described underneath:
All employees of firm should be provided with proper antivirus program and malware
software especially if they are remote workers. It can help in eliminate attacks of low to
medium level attacks.
Workforce of companies should be provided with effective training about best practices
and processes to regulate emails and cloud storage. This increase awareness will help
them to determine malicious links in emails.
Businesses must use secure network in their premises and encourages its remote
employees to not connect to any public wifi for work. Robust security of network will
assists firms to protect their data and have strong privacy which could not be breached by
hackers.
7
and arranges check ins and community.
Privacy and security at time of pandemic
At time of pandemic, businesses faces various threats in terms of privacy and security. As
the whole world was in lock down which encourages workforce to work from home. As a result,
technology has become more essential in working lives. But the increase in hybrid working leads
to rise in risks of cybersecurity also. The unsecured network of remote workers resulted in
breaching company's privacy by hackers. Companies have started to implement more artificial
intelligence as it maximises their efficiency but also expose firm to cyber crimes. Businesses
faced several phishing attacks as hackers sometimes pose as important persons and ends up
breaching privacy over emails. Rupture of security involves risks like malware, spam,
compromised business email, malicious link or domains (Warshawski, Itzhaki and Barnoy,
2019). Employees were connected only through the information and communication
technologies, thus the situations of privacy breach from third party or hackers take place
frequently. Potential risk from these breaches were stolen company's data or exposure to its
strategies. During pandemic, companies made communication with its customer only through
information and communication technologies, hence at time when of downtime or internet
outage, firms ended up losing major business opportunities.
Businesses can take several measures to protect themselves from risks associated with
privacy and security which are described underneath:
All employees of firm should be provided with proper antivirus program and malware
software especially if they are remote workers. It can help in eliminate attacks of low to
medium level attacks.
Workforce of companies should be provided with effective training about best practices
and processes to regulate emails and cloud storage. This increase awareness will help
them to determine malicious links in emails.
Businesses must use secure network in their premises and encourages its remote
employees to not connect to any public wifi for work. Robust security of network will
assists firms to protect their data and have strong privacy which could not be breached by
hackers.
7

Implementing virtual private network helps in adding an extra layer of security to internet
use from home. These can be proved as useful tool against security breach.
Companies need to ensure that its personal devices have appropriate anti virus software
installed. For this, they should make its security team a part of crisis management.
To effectively cope with traffic on network, firms must invest in working in their own
websites with private connections so they do not lose any business due to downtime.
Private vs Public Internet
Private internet is termed as personal virtual private network which facilitates users to
connect to several locations. It provides safe VPN option with proper encryption protocols and
results in more security. It gives users online privacy and anonymity as it forms personal private
connection as its access its restricted. Whereas, public internet allows everyone to connect to
network and its access is not tightly controlled (Zheng and Wang, 2021). The major differences
between public and private internet is the addressing of appliances on public internet should be
evaluated properly but on private internet it is little liberal.
Benefits of private internet:
In UK, usage of private network provides better control over internet congestion and
ensures adequate capacity for effective communication.
It maximises security of both users and organisation's data as its access is restricted. In
addition to that, utilities control network access which increase level of security in the
grid.
Private internet do not involve any monthly fees since it is privately owned and run. This
assists in saving additional cost of users and firms.
It is more customisable, provides strong technology with network availability to form
extensive over plus and backup power.
It allows to repair the system as and when needed as well as facilitates strong hybrid
coverage with access to long range.
Challenges of private internet:
As private internet exists inside a physical network, there are high chances of slowdown
in speed of internet. Maintaining a VPN takes specific quantity of bandwidth which
reduces pace of connections.
8
use from home. These can be proved as useful tool against security breach.
Companies need to ensure that its personal devices have appropriate anti virus software
installed. For this, they should make its security team a part of crisis management.
To effectively cope with traffic on network, firms must invest in working in their own
websites with private connections so they do not lose any business due to downtime.
Private vs Public Internet
Private internet is termed as personal virtual private network which facilitates users to
connect to several locations. It provides safe VPN option with proper encryption protocols and
results in more security. It gives users online privacy and anonymity as it forms personal private
connection as its access its restricted. Whereas, public internet allows everyone to connect to
network and its access is not tightly controlled (Zheng and Wang, 2021). The major differences
between public and private internet is the addressing of appliances on public internet should be
evaluated properly but on private internet it is little liberal.
Benefits of private internet:
In UK, usage of private network provides better control over internet congestion and
ensures adequate capacity for effective communication.
It maximises security of both users and organisation's data as its access is restricted. In
addition to that, utilities control network access which increase level of security in the
grid.
Private internet do not involve any monthly fees since it is privately owned and run. This
assists in saving additional cost of users and firms.
It is more customisable, provides strong technology with network availability to form
extensive over plus and backup power.
It allows to repair the system as and when needed as well as facilitates strong hybrid
coverage with access to long range.
Challenges of private internet:
As private internet exists inside a physical network, there are high chances of slowdown
in speed of internet. Maintaining a VPN takes specific quantity of bandwidth which
reduces pace of connections.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

