Ethical Hacking Exploit Analysis and Pen Testing Report
VerifiedAdded on 2022/12/21
|11
|2470
|1
Report
AI Summary
This report delves into the critical realm of ICT ethical hacking, exploring the significance of penetration testing in mitigating vulnerabilities within information systems. The analysis begins by highlighting common threats, such as poor password management and user awareness, emphasizin...

Running head: ICT ETHICAL HACKING EXPLOITS 1
ICT Ethical Hacking Exploits
Student's Name
Institution Affiliation
Date of Submission
ICT Ethical Hacking Exploits
Student's Name
Institution Affiliation
Date of Submission
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ICT ETHICAL HACKING EXPLOITS 2
Inline to the dangerous vulnerabilities that most organizations are facing within their
information systems, conducting penetration test has become vital to mitigate the threats that
such businesses are facing within their networks. There are major threats that organizations are
facing are due to numerous reasons. Such reasons include poor management of passwords and
accounts, poor user awareness on information securities issues, poor access control, among
others (Hoffmann, 2015). Pen testing refers to the assessments of the risks of specific
application, system, or even environment by use of known and reliable techniques.
There are numerous case study involving pen-testing. My analysis will take into account
the first scenario known as remote access interfaces that mitigate passwords attack. Due to poor
configuration and control access, ethical hacking has been a predominant scenario within the
business systems (Najera-Gutierrez & Ansari, 2018). In a keen analysis of the present case study,
it is profound to create intense attention on the fact that system administrators should make good
use of various protocols to minimize ethical hacking. A protocol such as RDP would create a
remote connection that makes filtering for the IDs connection possible. Such kind of process
should be adapted to mitigate the adverse effects.
There are various scopes and phases of examination of the remote access control. Such
stages involve creating of nodes on the network perimeters, filtering of connection by the IP
address, strengthening the available network nodes and mitigating telnet access such as root:
root. Concerning the test based provided, the black box is availed to support the key-based
authentication (Chen et al., 2018). Through this, a private key is created that highly mitigate
chances of hacking. There are numerous ethical considerations taken into account during the
development of the pen test.
Inline to the dangerous vulnerabilities that most organizations are facing within their
information systems, conducting penetration test has become vital to mitigate the threats that
such businesses are facing within their networks. There are major threats that organizations are
facing are due to numerous reasons. Such reasons include poor management of passwords and
accounts, poor user awareness on information securities issues, poor access control, among
others (Hoffmann, 2015). Pen testing refers to the assessments of the risks of specific
application, system, or even environment by use of known and reliable techniques.
There are numerous case study involving pen-testing. My analysis will take into account
the first scenario known as remote access interfaces that mitigate passwords attack. Due to poor
configuration and control access, ethical hacking has been a predominant scenario within the
business systems (Najera-Gutierrez & Ansari, 2018). In a keen analysis of the present case study,
it is profound to create intense attention on the fact that system administrators should make good
use of various protocols to minimize ethical hacking. A protocol such as RDP would create a
remote connection that makes filtering for the IDs connection possible. Such kind of process
should be adapted to mitigate the adverse effects.
There are various scopes and phases of examination of the remote access control. Such
stages involve creating of nodes on the network perimeters, filtering of connection by the IP
address, strengthening the available network nodes and mitigating telnet access such as root:
root. Concerning the test based provided, the black box is availed to support the key-based
authentication (Chen et al., 2018). Through this, a private key is created that highly mitigate
chances of hacking. There are numerous ethical considerations taken into account during the
development of the pen test.

ICT ETHICAL HACKING EXPLOITS 3
One key consideration is the developing of the administration of secure VPN connection,
which does not violate that set ethical principles and codes of conduct. Another key one is the
creation of reliable nodes via remote access that does not infringe the right of access to the right
users (Pozzobon et al., 2018). In developing this pen test, software application and programs will
be vital to take into account. Hardware components of computers can’t be left out in this
particular analysis. Developing this kind of test can take around two months to ensure that the
system is fully secure. Penetration testing is a practice of computer systems testing and web
applications used to check for areas that might be weak, and hackers could use them as entry
points to destroy or steal data. The process involves collecting data about the system and trying
to enter the system through the weak areas. The pen test will be used to check for flaws in the
company’s computer system and the effectiveness of the corporation’s security guiding principle.
Several strategies can be used to conduct a penetration test. Examples of these strategies
include battered testing, peripheral testing mechanisms, internal testing, black-box testing, as
well as white-box testing (Rouse, 2019). All these strategies are based on the key intention of the
test and the information available for the test to be conducted. For the penetration test to be
carried out for this company, blind testing will be used. Blind testing is done to assess the weak
points of a computer system that can be used by real external hackers to penetrate the computer
system and identify how much the hacker can access (Rouse, 2019). For blind testing, the hacker
is provided which as minimal information as possible about the company's computer system then
he or she is supposed to find his way into the system.
Penetration Testing - Method
One key consideration is the developing of the administration of secure VPN connection,
which does not violate that set ethical principles and codes of conduct. Another key one is the
creation of reliable nodes via remote access that does not infringe the right of access to the right
users (Pozzobon et al., 2018). In developing this pen test, software application and programs will
be vital to take into account. Hardware components of computers can’t be left out in this
particular analysis. Developing this kind of test can take around two months to ensure that the
system is fully secure. Penetration testing is a practice of computer systems testing and web
applications used to check for areas that might be weak, and hackers could use them as entry
points to destroy or steal data. The process involves collecting data about the system and trying
to enter the system through the weak areas. The pen test will be used to check for flaws in the
company’s computer system and the effectiveness of the corporation’s security guiding principle.
Several strategies can be used to conduct a penetration test. Examples of these strategies
include battered testing, peripheral testing mechanisms, internal testing, black-box testing, as
well as white-box testing (Rouse, 2019). All these strategies are based on the key intention of the
test and the information available for the test to be conducted. For the penetration test to be
carried out for this company, blind testing will be used. Blind testing is done to assess the weak
points of a computer system that can be used by real external hackers to penetrate the computer
system and identify how much the hacker can access (Rouse, 2019). For blind testing, the hacker
is provided which as minimal information as possible about the company's computer system then
he or she is supposed to find his way into the system.
Penetration Testing - Method
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
ICT ETHICAL HACKING EXPLOITS 4
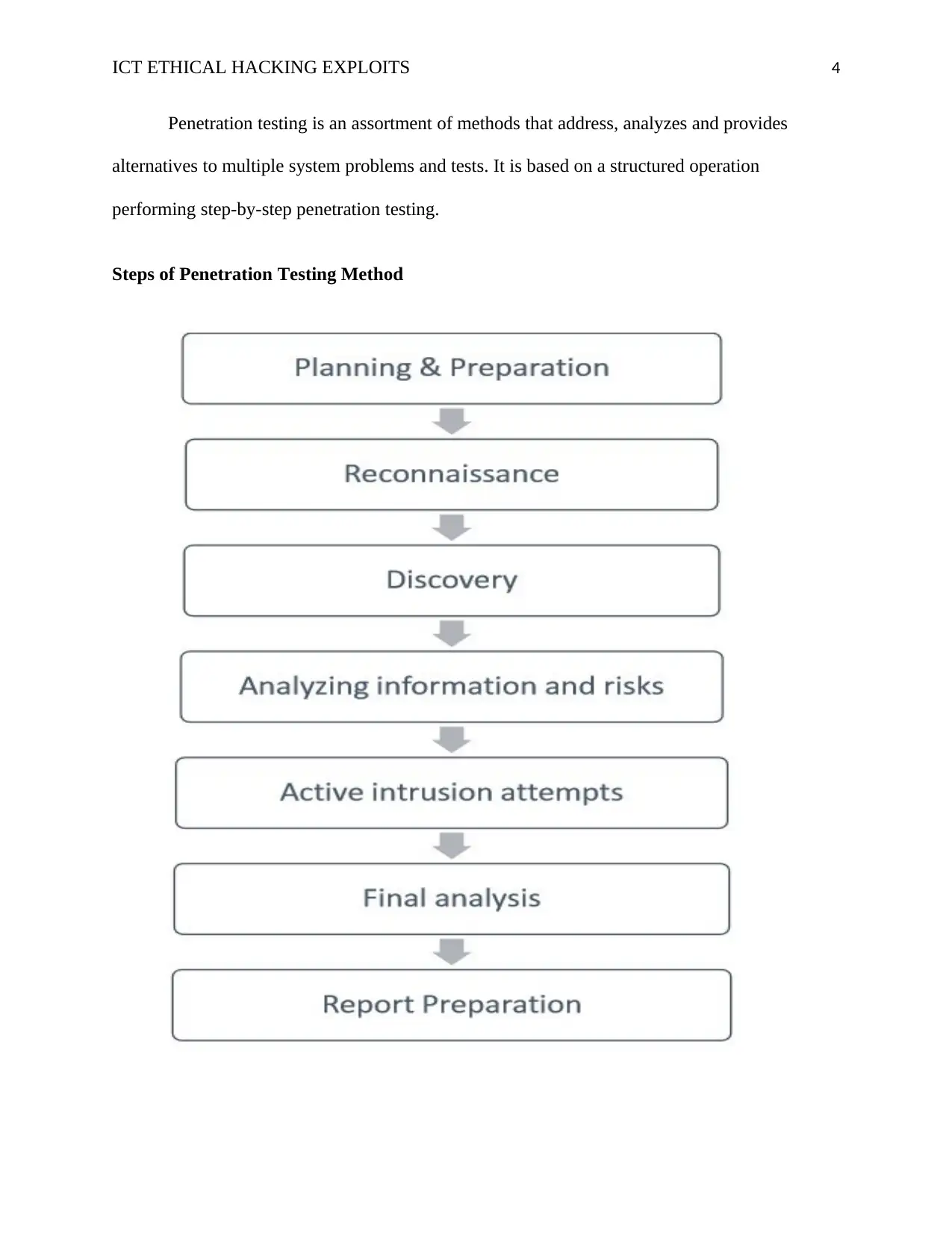
Penetration testing is an assortment of methods that address, analyzes and provides
alternatives to multiple system problems and tests. It is based on a structured operation
performing step-by-step penetration testing.
Steps of Penetration Testing Method
Penetration testing is an assortment of methods that address, analyzes and provides
alternatives to multiple system problems and tests. It is based on a structured operation
performing step-by-step penetration testing.
Steps of Penetration Testing Method
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ICT ETHICAL HACKING EXPLOITS 5
The blind penetration test will include five stages. The first stage will be the planning and
reconnaissance stage. In this stage, the tester will be provided with any information an outsider
may have concerning the subject, not all information about the system is provided for blind
testing. Sometimes only the company's name is provided. The second stage is the scanning stage,
where the tester analyses how the system is likely to respond to the external intrusion. The third
step is gaining access to the system. In this stage, different software will be used to gain
accessibility to the whole system through the weak points. The fourth stage is maintaining the
entrance to find out if the hacker can manage access long enough to exploit the company's data.
The final step will be an analysis of the findings. In this stage, the results of the penetration tests
are analyzed by the company's security personnel to come up with an improvement or
completely change the security of the computer system (Imperva, 2019).
Before the pen test can begin a written contract must be written between the tester and the
company (Rasch, 2019). The written agreement ensures that the tester does not take advantage of
the test and gain access to data that he or she was not supposed. For example, a tester may take
advantage of the medical records of a company and use them to blackmail employees. By
signing a contract, this is prevented. A non-disclosure agreement also has to be signed to ensure
that confidential information is not leaked.
For the successful completion of this task, pen-test software will be required to scan the
computer network for holes and weaknesses (Nickel, 2019). The tester will choose the software
which he or she feels comfortable using. Examples of this software’s include net-sparker,
acunetix, probely, and immune-web. The task is expected to take at least three working days
because the hacker has very little information about the system. The first day will cover the early
The blind penetration test will include five stages. The first stage will be the planning and
reconnaissance stage. In this stage, the tester will be provided with any information an outsider
may have concerning the subject, not all information about the system is provided for blind
testing. Sometimes only the company's name is provided. The second stage is the scanning stage,
where the tester analyses how the system is likely to respond to the external intrusion. The third
step is gaining access to the system. In this stage, different software will be used to gain
accessibility to the whole system through the weak points. The fourth stage is maintaining the
entrance to find out if the hacker can manage access long enough to exploit the company's data.
The final step will be an analysis of the findings. In this stage, the results of the penetration tests
are analyzed by the company's security personnel to come up with an improvement or
completely change the security of the computer system (Imperva, 2019).
Before the pen test can begin a written contract must be written between the tester and the
company (Rasch, 2019). The written agreement ensures that the tester does not take advantage of
the test and gain access to data that he or she was not supposed. For example, a tester may take
advantage of the medical records of a company and use them to blackmail employees. By
signing a contract, this is prevented. A non-disclosure agreement also has to be signed to ensure
that confidential information is not leaked.
For the successful completion of this task, pen-test software will be required to scan the
computer network for holes and weaknesses (Nickel, 2019). The tester will choose the software
which he or she feels comfortable using. Examples of this software’s include net-sparker,
acunetix, probely, and immune-web. The task is expected to take at least three working days
because the hacker has very little information about the system. The first day will cover the early
ICT ETHICAL HACKING EXPLOITS 6
two stages, which are planning reconnaissance and scanning. The second day will include
gaining access and maintaining access while the third day will cover analyzing the results and
coming up with conclusions.
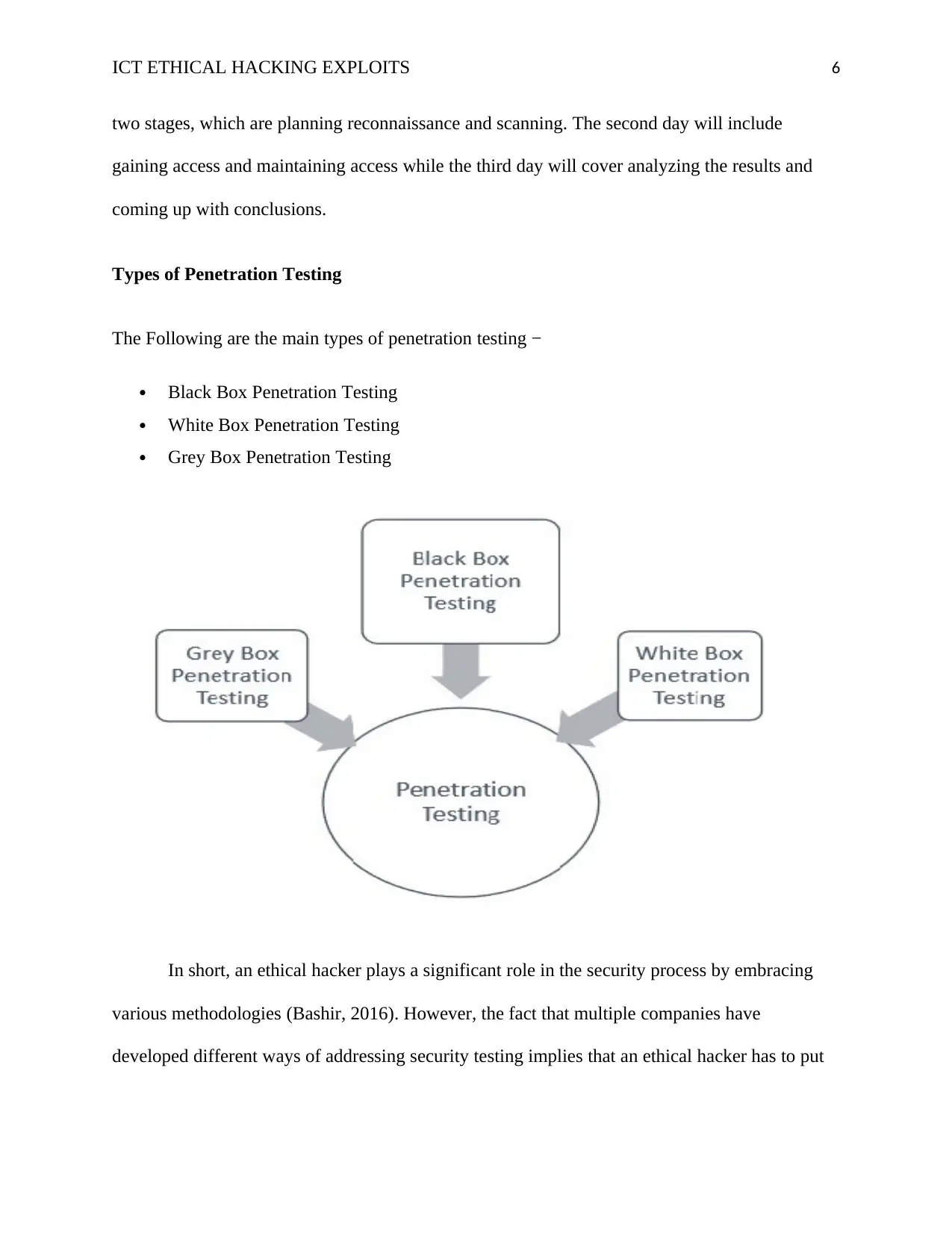
Types of Penetration Testing
The Following are the main types of penetration testing −
Black Box Penetration Testing
White Box Penetration Testing
Grey Box Penetration Testing
In short, an ethical hacker plays a significant role in the security process by embracing
various methodologies (Bashir, 2016). However, the fact that multiple companies have
developed different ways of addressing security testing implies that an ethical hacker has to put
two stages, which are planning reconnaissance and scanning. The second day will include
gaining access and maintaining access while the third day will cover analyzing the results and
coming up with conclusions.
Types of Penetration Testing
The Following are the main types of penetration testing −
Black Box Penetration Testing
White Box Penetration Testing
Grey Box Penetration Testing
In short, an ethical hacker plays a significant role in the security process by embracing
various methodologies (Bashir, 2016). However, the fact that multiple companies have
developed different ways of addressing security testing implies that an ethical hacker has to put
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ICT ETHICAL HACKING EXPLOITS 7
into consideration some basic variations such as Open Source Security Testing Methodology
Manual, Asset, and Operational Critical Threat among others.
Sensitive Data Exposure is another visible vulnerability that is evident to have happened
after an attacker has gained control of the system in case the data was not sufficiently protected.
For this attack to occur, it is possible that the company had adopted weak primary and
management as well as weak algorithm usage (Rao, 2014). Broken Authentication flaw is likely
to occur where the attacker uses leaks in authenticating procedures in impersonating other users.
When the company system or flaw has been exploited, it is easier for the attacker to impersonate
the employee in case permission from the account has been granted. As a common but dangerous
category of vulnerability, security misconfiguration is possible when the company uses outdated
software, runs an unnecessary service on its system or even forgetting to change factory settings.
Once an attacker realizes the target is using flawed database management systems, he or she can
use automated scanners to detect these systems that are not well patched; hence, carry out the
attack or the mission.
Vulnerability Assessment
The vulnerability assessment method is the identification (discovery) and measurement
(scanning) of vulnerabilities in a specified setting. It is a thorough evaluation of the situation of
data safety (analysis of results). It also defines prospective weaknesses and offers the appropriate
mitigation (remediation) steps to either eliminate those weaknesses or decrease them below the
point of danger.
into consideration some basic variations such as Open Source Security Testing Methodology
Manual, Asset, and Operational Critical Threat among others.
Sensitive Data Exposure is another visible vulnerability that is evident to have happened
after an attacker has gained control of the system in case the data was not sufficiently protected.
For this attack to occur, it is possible that the company had adopted weak primary and
management as well as weak algorithm usage (Rao, 2014). Broken Authentication flaw is likely
to occur where the attacker uses leaks in authenticating procedures in impersonating other users.
When the company system or flaw has been exploited, it is easier for the attacker to impersonate
the employee in case permission from the account has been granted. As a common but dangerous
category of vulnerability, security misconfiguration is possible when the company uses outdated
software, runs an unnecessary service on its system or even forgetting to change factory settings.
Once an attacker realizes the target is using flawed database management systems, he or she can
use automated scanners to detect these systems that are not well patched; hence, carry out the
attack or the mission.
Vulnerability Assessment
The vulnerability assessment method is the identification (discovery) and measurement
(scanning) of vulnerabilities in a specified setting. It is a thorough evaluation of the situation of
data safety (analysis of results). It also defines prospective weaknesses and offers the appropriate
mitigation (remediation) steps to either eliminate those weaknesses or decrease them below the
point of danger.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ICT ETHICAL HACKING EXPLOITS 8
Common security misconfigurations are the most common form of vulnerabilities that
any company can face. From the VM image provided, it is visible that the company's software is
not up to date hence the default system credentials like user accounts and passwords were not
secured and the reason why the hacker was connected to another user to gain access into the
system. It is a fact that the company's computer system is multi-layered, thus implying that if the
layers are not securely assembled, then it is possible for the system to be infiltrated leading to
data being compromised like what happened in the company (Thomas, 2018). Arguably, security
misconfiguration vulnerability evident in the VM image imply that there are routers on the
market that have hardcoded credentials and even network appliances that use default SSH keys
that allows the attacker to gain connection into the system without authorization successfully.
The anonymous attacker gains free entry into the company's system by using another users
account and through generating another password of his own, he or she compromises the system
Common security misconfigurations are the most common form of vulnerabilities that
any company can face. From the VM image provided, it is visible that the company's software is
not up to date hence the default system credentials like user accounts and passwords were not
secured and the reason why the hacker was connected to another user to gain access into the
system. It is a fact that the company's computer system is multi-layered, thus implying that if the
layers are not securely assembled, then it is possible for the system to be infiltrated leading to
data being compromised like what happened in the company (Thomas, 2018). Arguably, security
misconfiguration vulnerability evident in the VM image imply that there are routers on the
market that have hardcoded credentials and even network appliances that use default SSH keys
that allows the attacker to gain connection into the system without authorization successfully.
The anonymous attacker gains free entry into the company's system by using another users
account and through generating another password of his own, he or she compromises the system

ICT ETHICAL HACKING EXPLOITS 9
(Baloch, 2017). This form of vulnerabilities is evident to have negatively impacted on the
paradigm of the internet of things, in the sense that devices that are not well configured are easily
exploited by hackers who have the potential to compromise the system.
Needless to say, after the hackers or a hacker has gained access to the target system, most
of them consider sustainment or in simple terms, staying in place without being noticed. In this
case, the hackers maintain access through secretly installing programs that are malicious such as
rootkits in the system. The fact is so since the hackers can compromise the company's system yet
cover their activities. It, therefore, implies that the hackers had to carefully choose the technique
that best accomplishes their malicious motives and still maintain access to the system without
being noticed.
Penetration Testing - Legal Issues (Disclosure/Non-disclosure agreement)
Here are some of the problems that may occur between a tester and his customer; the
tester is unknown to his customer − so on what ground should he be given access to delicate
information who will take the safety assurance of the lost information? The customer may blame
tester for data loss or confidentiality Penetration testing may impact system efficiency and may
increase confidentiality and integrity problems; hence, this is very crucial, even in an inner
penetration test conducted by inner employees to obtain written approval. Before any testing
project, a declaration of intent should be drawn up and duly signed by both sides. It should be
stated that the scope of the work and that while performing vulnerability tests, you may and may
not be doing it. It is essential for the tester to understand who owns the company or systems that
are required to operate on, and the infrastructure between testing schemes and their objectives
that could be impacted by pen-testing.
(Baloch, 2017). This form of vulnerabilities is evident to have negatively impacted on the
paradigm of the internet of things, in the sense that devices that are not well configured are easily
exploited by hackers who have the potential to compromise the system.
Needless to say, after the hackers or a hacker has gained access to the target system, most
of them consider sustainment or in simple terms, staying in place without being noticed. In this
case, the hackers maintain access through secretly installing programs that are malicious such as
rootkits in the system. The fact is so since the hackers can compromise the company's system yet
cover their activities. It, therefore, implies that the hackers had to carefully choose the technique
that best accomplishes their malicious motives and still maintain access to the system without
being noticed.
Penetration Testing - Legal Issues (Disclosure/Non-disclosure agreement)
Here are some of the problems that may occur between a tester and his customer; the
tester is unknown to his customer − so on what ground should he be given access to delicate
information who will take the safety assurance of the lost information? The customer may blame
tester for data loss or confidentiality Penetration testing may impact system efficiency and may
increase confidentiality and integrity problems; hence, this is very crucial, even in an inner
penetration test conducted by inner employees to obtain written approval. Before any testing
project, a declaration of intent should be drawn up and duly signed by both sides. It should be
stated that the scope of the work and that while performing vulnerability tests, you may and may
not be doing it. It is essential for the tester to understand who owns the company or systems that
are required to operate on, and the infrastructure between testing schemes and their objectives
that could be impacted by pen-testing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ICT ETHICAL HACKING EXPLOITS 10
References
Bashir, B., & Khalique, A. (2016). A Review on Security versus ethics. International Journal of
Computer Applications, 151(11).
Baloch, R. (2017). Ethical hacking and penetration testing guide. Auerbach Publications.
Chen, C. K., Zhang, Z. K., Lee, S. H., & Shieh, S. (2018). Penetration Testing in the IoT
age. Computer, 51(4), 82-85.
Hoffmann, J. (2015, April). Simulated Penetration Testing: From" Dijkstra" to" Turing Test++."
In Twenty-Fifth International Conference on Automated Planning and Scheduling.
Imperva. (2019). What is Penetration Testing | Step-By-Step Process & Methods | Imperva?
Retrieved 2 September 2019, from
https://www.imperva.com/learn/application-security/penetration-testing/
Najera-Gutierrez, G., & Ansari, J. A. (2018). Web Penetration Testing with Kali Linux: Explore
the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Nickel, A. (2019). 3 Things You Need in a Penetration Testing Tool. Retrieved 2 September
2019, from https://www.coresecurity.com/node/28478
Pozzobon, E., Weiss, N., Renner, S., & Hackenberg, R. (2018). A Survey on Media Access
Solutions for CAN Penetration Testing.
Rasch, M. (2019). Legal Issues in Penetration Testing - SecurityCurrent. Retrieved 2 September
2019, from https://securitycurrent.com/legal-issues-in-penetration-testing/
References
Bashir, B., & Khalique, A. (2016). A Review on Security versus ethics. International Journal of
Computer Applications, 151(11).
Baloch, R. (2017). Ethical hacking and penetration testing guide. Auerbach Publications.
Chen, C. K., Zhang, Z. K., Lee, S. H., & Shieh, S. (2018). Penetration Testing in the IoT
age. Computer, 51(4), 82-85.
Hoffmann, J. (2015, April). Simulated Penetration Testing: From" Dijkstra" to" Turing Test++."
In Twenty-Fifth International Conference on Automated Planning and Scheduling.
Imperva. (2019). What is Penetration Testing | Step-By-Step Process & Methods | Imperva?
Retrieved 2 September 2019, from
https://www.imperva.com/learn/application-security/penetration-testing/
Najera-Gutierrez, G., & Ansari, J. A. (2018). Web Penetration Testing with Kali Linux: Explore
the methods and tools of ethical hacking with Kali Linux. Packt Publishing Ltd.
Nickel, A. (2019). 3 Things You Need in a Penetration Testing Tool. Retrieved 2 September
2019, from https://www.coresecurity.com/node/28478
Pozzobon, E., Weiss, N., Renner, S., & Hackenberg, R. (2018). A Survey on Media Access
Solutions for CAN Penetration Testing.
Rasch, M. (2019). Legal Issues in Penetration Testing - SecurityCurrent. Retrieved 2 September
2019, from https://securitycurrent.com/legal-issues-in-penetration-testing/
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ICT ETHICAL HACKING EXPLOITS 11
Rao, G. S., Kumar, P. N., Swetha, P., & BhanuKiran, G. (2014, December). Security assessment
of computer networks-an ethical hacker's perspective. In International Conference on
Computing and Communication Technologies (pp. 1-5). IEEE.
Rouse, M. (2019). What is a pen test (penetration testing)? - Definition from WhatIs.com.
Retrieved 2 September 2019, from
https://searchsecurity.techtarget.com/definition/penetration-testing
Thomas, G., Burmeister, O., & Low, G. (2018). Issues of Implied Trust in Ethical
Hacking. ORBIT Journal, 2(1).
Rao, G. S., Kumar, P. N., Swetha, P., & BhanuKiran, G. (2014, December). Security assessment
of computer networks-an ethical hacker's perspective. In International Conference on
Computing and Communication Technologies (pp. 1-5). IEEE.
Rouse, M. (2019). What is a pen test (penetration testing)? - Definition from WhatIs.com.
Retrieved 2 September 2019, from
https://searchsecurity.techtarget.com/definition/penetration-testing
Thomas, G., Burmeister, O., & Low, G. (2018). Issues of Implied Trust in Ethical
Hacking. ORBIT Journal, 2(1).
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




