ATMC ICT301: Advanced Network Topics Report on Security
VerifiedAdded on 2022/10/19
|17
|3732
|467
Report
AI Summary
This report, prepared for the ICT301 Advanced Network Topics course, analyzes the network security of Fencing Limited, a small organization. It explores the use of firewalls, access control, and authentication methods to protect the network. The report also delves into business continuity planning, outlining the importance of a Business Continuity Plan (BCP) and the steps involved in its development, including business impact analysis, recovery strategies, and team training. Furthermore, it addresses risk management, emphasizing the need for organizations to identify, assess, and mitigate various security risks, especially those related to cybercrime. The report suggests implementing DAT security packages and outlines the benefits of a secure network for the organization, including improved operational efficiencies and better customer service. The report also highlights the importance of centralized authentication methods like RADIUS and Kerberos. The report concludes with recommendations for enhancing the network's security posture.

Running head: ICT301 ADVANCED NETWORK TOPICS
ICT301 ADVANCED NETWORK TOPICS
Name of the Student
Name of the University
Author Note:
ICT301 ADVANCED NETWORK TOPICS
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ICT301 ADVANCED NETWORK TOPICS
Table of Contents
Project Background.............................................................................................................2
Network security..................................................................................................................3
Access control and authentication.......................................................................................4
Business Continuity.............................................................................................................6
Risk management.................................................................................................................7
Conclusion.........................................................................................................................10
Recommendation...............................................................................................................11
References..........................................................................................................................13
Table of Contents
Project Background.............................................................................................................2
Network security..................................................................................................................3
Access control and authentication.......................................................................................4
Business Continuity.............................................................................................................6
Risk management.................................................................................................................7
Conclusion.........................................................................................................................10
Recommendation...............................................................................................................11
References..........................................................................................................................13

2ICT301 ADVANCED NETWORK TOPICS
Project Background
The following report is all about Fencing limited, which is a small organization based in
Wollongong, NSW. The employee strength of this organization is found to be 250 people. The
main business of this organization is all about selling various fencing materials for the
construction sites, mining and lastly manufacturing industry (Sivaraman et al. 2015). The
organization is found to be nimble which can easily move new market if there are certain number
of opportunities. Fencing limited can easily manage their inventory and allow certain customers
to buy product from the website.
Scope
To improve the network capabilities and certain initiatives for optimizing the IT
capability.
To align with the business needs which will help this organization to understand digital
transformation and providing business value.
Project Goal
The mere focus of this project is all about securing the network in the upcoming days. It
is all about keeping the whole organization information much secure (Pawar and Anuradha
2015). Most of the employees of this organization analyze that their present system is adequate
for their use. But the help of faster and agile secure network will help in facilitating business.
Project Background
The following report is all about Fencing limited, which is a small organization based in
Wollongong, NSW. The employee strength of this organization is found to be 250 people. The
main business of this organization is all about selling various fencing materials for the
construction sites, mining and lastly manufacturing industry (Sivaraman et al. 2015). The
organization is found to be nimble which can easily move new market if there are certain number
of opportunities. Fencing limited can easily manage their inventory and allow certain customers
to buy product from the website.
Scope
To improve the network capabilities and certain initiatives for optimizing the IT
capability.
To align with the business needs which will help this organization to understand digital
transformation and providing business value.
Project Goal
The mere focus of this project is all about securing the network in the upcoming days. It
is all about keeping the whole organization information much secure (Pawar and Anuradha
2015). Most of the employees of this organization analyze that their present system is adequate
for their use. But the help of faster and agile secure network will help in facilitating business.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ICT301 ADVANCED NETWORK TOPICS
Strategic alignment of Project
It will help the employee to go beyond their sales target which is the main target of
fencing limited management. The project is all about building a secure system which will
comply with the new regulation. The project comes up with high level of organizational interest
of Fencing limited in this project.
In the coming pages of the report, an idea has been provided with respect to the network
security of this organization. The next section deals with access control and authentication of this
new system. An overview has been given with respect to business continuity and risk
management for this project. The last part of the report deals with list of recommendation.
Network security
A firewall can be used for protecting the network so that all the client and organization
information is safe. Firewall is just like a filter in between two that is system and network. There
are large number of ways by which firewall can be used for filtering out information (Acemoglu,
Malekian and Ozdaglar 2016). The methods work aim to work at various layer of the network.
Some of the basic function of a firewall is discussed below like
Packet filtering: All the basic firewall software makes use of earlier-defined security
rules which is needed for creating filters. If the incoming packet data containing information is
anyhow flagged by this filter, then it is not completely allowed through it (Duffield 2017).
Packets which passes through the filter are send to the system and all other packets are
completely discarded.
Strategic alignment of Project
It will help the employee to go beyond their sales target which is the main target of
fencing limited management. The project is all about building a secure system which will
comply with the new regulation. The project comes up with high level of organizational interest
of Fencing limited in this project.
In the coming pages of the report, an idea has been provided with respect to the network
security of this organization. The next section deals with access control and authentication of this
new system. An overview has been given with respect to business continuity and risk
management for this project. The last part of the report deals with list of recommendation.
Network security
A firewall can be used for protecting the network so that all the client and organization
information is safe. Firewall is just like a filter in between two that is system and network. There
are large number of ways by which firewall can be used for filtering out information (Acemoglu,
Malekian and Ozdaglar 2016). The methods work aim to work at various layer of the network.
Some of the basic function of a firewall is discussed below like
Packet filtering: All the basic firewall software makes use of earlier-defined security
rules which is needed for creating filters. If the incoming packet data containing information is
anyhow flagged by this filter, then it is not completely allowed through it (Duffield 2017).
Packets which passes through the filter are send to the system and all other packets are
completely discarded.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ICT301 ADVANCED NETWORK TOPICS
Proxy Service: Proxy server of firewall is considered to be an application which works in
between the given system. All the required information is collected from internet are sent to
firewall and sent to required system. It generally operates in the application layer of firewall
where connection in between the two ends is required to conduct session by the help of proxy
(Chen et al. 2015). It merely operates by setting and running a given process on firewall if it is
running on the end host. All the centralized information is transferred for any activity like
firewall scanning.
Stateful inspection: It is the updated method of scanning firewall which does not depend
on intensive examination of packets. It aims to hold certain number of attributes for each
connection for database that has trusted information. The given attributes are defined as state of
connection which includes the detail of IP addresses and Port (Aljuhani and Alharbi 2017). It
merely includes connection and sequence number for packet which is being sent. The firewall
merely compares that information is being sent for copying relevant and transfer of required
information from databases.
Outdoor cameras can be great initiative for keeping a track of person that are visiting the
main office of Fencing limited on Prince Highway. But most of the burglars do not come from
the front door instead of that they make use of blind spot for entering into the building (Yu et al.,
2015). The organization should go for DAT security packages which has been designed for
securing offices. The system provides a wide range of option like basic bells and whistles for
customizing a system which will help in protecting the system. The system aims to provide a
range of benefits like
Monitoring on 24/7 basis.
Equipment’s for security monitoring
Proxy Service: Proxy server of firewall is considered to be an application which works in
between the given system. All the required information is collected from internet are sent to
firewall and sent to required system. It generally operates in the application layer of firewall
where connection in between the two ends is required to conduct session by the help of proxy
(Chen et al. 2015). It merely operates by setting and running a given process on firewall if it is
running on the end host. All the centralized information is transferred for any activity like
firewall scanning.
Stateful inspection: It is the updated method of scanning firewall which does not depend
on intensive examination of packets. It aims to hold certain number of attributes for each
connection for database that has trusted information. The given attributes are defined as state of
connection which includes the detail of IP addresses and Port (Aljuhani and Alharbi 2017). It
merely includes connection and sequence number for packet which is being sent. The firewall
merely compares that information is being sent for copying relevant and transfer of required
information from databases.
Outdoor cameras can be great initiative for keeping a track of person that are visiting the
main office of Fencing limited on Prince Highway. But most of the burglars do not come from
the front door instead of that they make use of blind spot for entering into the building (Yu et al.,
2015). The organization should go for DAT security packages which has been designed for
securing offices. The system provides a wide range of option like basic bells and whistles for
customizing a system which will help in protecting the system. The system aims to provide a
range of benefits like
Monitoring on 24/7 basis.
Equipment’s for security monitoring

5ICT301 ADVANCED NETWORK TOPICS
Installation by professionals
Remote alarm and disarm
Customizable alerts, automation and schedules
Security cameras
Live stream from mobile devices
Recording and saving video clips.
Access control and authentication
Network access control is the way of improving the overall security of Fencing limited
private organization. This is mainly done by limiting the overall availability to network-based
resources which can comply with security policy of Fencing limited (Joshi and Karkade 2015). A
network access control scheme merely consists of two important aspects that is restricted the
access and providing network boundary protection. It is gained by the help of user
authentication and proper authorization control. It is solely responsible for analyzing and
identifying various user of network system. Authorization is just a new a method of providing
access to permission for protected resources (Gupta and Misra 2016). Network boundary
protection aims to provide logical control for establishing connection in and out of the network.
By the help of firewalls any kind of unauthorized access to the network system of fencing limited
can be blocked. In addition, intrusion detection and certain preventive technologies can be
employed for defending the network from any kind of attack.
Restricting the access to certain number of devices on this network is an important step
for providing security to network. Most of the network devices consist of both communication
and computing technologies (Luong et al. 2017). It comes up with the potential of bringing down
Installation by professionals
Remote alarm and disarm
Customizable alerts, automation and schedules
Security cameras
Live stream from mobile devices
Recording and saving video clips.
Access control and authentication
Network access control is the way of improving the overall security of Fencing limited
private organization. This is mainly done by limiting the overall availability to network-based
resources which can comply with security policy of Fencing limited (Joshi and Karkade 2015). A
network access control scheme merely consists of two important aspects that is restricted the
access and providing network boundary protection. It is gained by the help of user
authentication and proper authorization control. It is solely responsible for analyzing and
identifying various user of network system. Authorization is just a new a method of providing
access to permission for protected resources (Gupta and Misra 2016). Network boundary
protection aims to provide logical control for establishing connection in and out of the network.
By the help of firewalls any kind of unauthorized access to the network system of fencing limited
can be blocked. In addition, intrusion detection and certain preventive technologies can be
employed for defending the network from any kind of attack.
Restricting the access to certain number of devices on this network is an important step
for providing security to network. Most of the network devices consist of both communication
and computing technologies (Luong et al. 2017). It comes up with the potential of bringing down
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ICT301 ADVANCED NETWORK TOPICS
the whole network and its resources. One of the major point of network device security is all
about having proper access control and authorization. Various protocols have been design and
developed for addressing each of the two requirement and improving the network security to
next level.
User authentication is important for gaining control on the network system and related
devices. Authentication comes up with two aspects like general access authentication and proper
functional authorization (Satasiya, Raviya and Kumar 2016). Authorization mainly deals with
the individual rights for getting access to the system. User authentication depends on certain
number of factors like password, cryptographic token and lastly biometrics.
Individual device-based authentication aims to provide access control measure.
Authentication method is known to be an effective and efficient way when the network makes
use large number of devices and user for accessing the devices (Adao et al. 2016). Centralized
authentication is mainly used for solving the issues in remote network access. In this, the
administer of user (employees) on network devices are not practical. Keeping all the information
in single device and all the required information updated is considered to be administrative
nightmare. Some of centralized authentication like RADIUS and Kerberos can tackle this
particular issue (ALAmri and Guan 2016). The system will allow the user information to be
easily stored and managed at a single platform. Most of the RADIUS servers can easily
communicate with some of the network devices and after that it can securely access the account
information.
Most of the network devices come up with configured access list which defines both
hostname and IP address. It is generally authorized for access the network. There can be
restriction with respect to network equipment for IP from the administrator end (Khosroshahi
the whole network and its resources. One of the major point of network device security is all
about having proper access control and authorization. Various protocols have been design and
developed for addressing each of the two requirement and improving the network security to
next level.
User authentication is important for gaining control on the network system and related
devices. Authentication comes up with two aspects like general access authentication and proper
functional authorization (Satasiya, Raviya and Kumar 2016). Authorization mainly deals with
the individual rights for getting access to the system. User authentication depends on certain
number of factors like password, cryptographic token and lastly biometrics.
Individual device-based authentication aims to provide access control measure.
Authentication method is known to be an effective and efficient way when the network makes
use large number of devices and user for accessing the devices (Adao et al. 2016). Centralized
authentication is mainly used for solving the issues in remote network access. In this, the
administer of user (employees) on network devices are not practical. Keeping all the information
in single device and all the required information updated is considered to be administrative
nightmare. Some of centralized authentication like RADIUS and Kerberos can tackle this
particular issue (ALAmri and Guan 2016). The system will allow the user information to be
easily stored and managed at a single platform. Most of the RADIUS servers can easily
communicate with some of the network devices and after that it can securely access the account
information.
Most of the network devices come up with configured access list which defines both
hostname and IP address. It is generally authorized for access the network. There can be
restriction with respect to network equipment for IP from the administrator end (Khosroshahi
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ICT301 ADVANCED NETWORK TOPICS
and Shahinzadeh 2016). It can be used for protecting the network for any kind of unauthorized
access.
Account Administrator: Employees have complete access to official websites which
provides them the capability of creating new account administration. In addition, it provides
account access for both ad manager and administrator.
Manager: User will have access to the official website and can easily make changes in
the campaign. Manager cannot allow any kind of access to accounts or make modification to
information available on website.
Business Continuity
Business continuity plan (BCP) is a method of creating system for prevention and
recovery form any kind of threat to organization. The plan aims to highlights that both personnel
and assets are completely protected. It is merely highlights quick functioning in case of disaster.
BCP of Fencing limited is completely advanced and requires involvement from various
stakeholders (Sahebjamnia, Torabi and Mansouri 2015). BCP is all about defining various risk
which impact the overall operation of the organization. It is considered to be important aspect for
managing organization risk. BCP is considered to be an important aspect of this organization.
Both threats and disruption can result in loss in revenue and even much higher cost. Fencing
Limited is very much prone to disaster which are catastrophic in nature. Business continuity plan
will help this organization to easily operate even in case of cyber-attacks (Podaras, Antlová and
Motejlek 2016). Considering this organization, BCP is completely put into plan by back up of
important data and client information. If something happens to the main office of fencing
limited, then all the data can be easily retrieved.
and Shahinzadeh 2016). It can be used for protecting the network for any kind of unauthorized
access.
Account Administrator: Employees have complete access to official websites which
provides them the capability of creating new account administration. In addition, it provides
account access for both ad manager and administrator.
Manager: User will have access to the official website and can easily make changes in
the campaign. Manager cannot allow any kind of access to accounts or make modification to
information available on website.
Business Continuity
Business continuity plan (BCP) is a method of creating system for prevention and
recovery form any kind of threat to organization. The plan aims to highlights that both personnel
and assets are completely protected. It is merely highlights quick functioning in case of disaster.
BCP of Fencing limited is completely advanced and requires involvement from various
stakeholders (Sahebjamnia, Torabi and Mansouri 2015). BCP is all about defining various risk
which impact the overall operation of the organization. It is considered to be important aspect for
managing organization risk. BCP is considered to be an important aspect of this organization.
Both threats and disruption can result in loss in revenue and even much higher cost. Fencing
Limited is very much prone to disaster which are catastrophic in nature. Business continuity plan
will help this organization to easily operate even in case of cyber-attacks (Podaras, Antlová and
Motejlek 2016). Considering this organization, BCP is completely put into plan by back up of
important data and client information. If something happens to the main office of fencing
limited, then all the data can be easily retrieved.

8ICT301 ADVANCED NETWORK TOPICS
BCP for fencing limited will be developed by using following steps like:
Business Impact analysis: In this point, the organization will look for function and
related resources which are merely time-sensitive.
Recovery: In this point, the organization will look for identifying and implementing
certain steps for recovery of some important business function.
Organization: There is need of building a continuity team for managing any kind of
disruption.
Training: The continuity team needs to be completely trained and tested. All the
members of this team should be given exercise for going over the plan and strategy.
There is an important aspect for developing a BCP is all about creating a business
continuity impact analysis. It mere identifies any kind of effect of disruption to business function
and related process (Järveläinen 2016). The required information is required for decision making
and recovery of strategy.
Peter Smith the owner of this organization have planned to invest $300 000 in next three
years. The suggested system can easily improve the overall importance of information system in
organization like
It will provide operational efficiencies
Reducing overall cost
Better customer service
Development of community capabilities and methods.
The new system will provide real-time data for any fast action.
BCP for fencing limited will be developed by using following steps like:
Business Impact analysis: In this point, the organization will look for function and
related resources which are merely time-sensitive.
Recovery: In this point, the organization will look for identifying and implementing
certain steps for recovery of some important business function.
Organization: There is need of building a continuity team for managing any kind of
disruption.
Training: The continuity team needs to be completely trained and tested. All the
members of this team should be given exercise for going over the plan and strategy.
There is an important aspect for developing a BCP is all about creating a business
continuity impact analysis. It mere identifies any kind of effect of disruption to business function
and related process (Järveläinen 2016). The required information is required for decision making
and recovery of strategy.
Peter Smith the owner of this organization have planned to invest $300 000 in next three
years. The suggested system can easily improve the overall importance of information system in
organization like
It will provide operational efficiencies
Reducing overall cost
Better customer service
Development of community capabilities and methods.
The new system will provide real-time data for any fast action.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ICT301 ADVANCED NETWORK TOPICS
Custom of data for decision making
Achieving data for business analysis
Risk management
Information technology risk management merely requires certain organization to easily
plan, monitor, track and manage various security risk. Organization like Fencing limited which
are connected to internet are easily exposed to cyber-crime (Haidzir, Othman and Mammi 2018).
Cyber-criminals come up with variety of methods for get into a system. They can get in through
an employee or any weak link into the system. This is mainly done so that they can steal some of
the vital information. There is a list of steps which should be taken by Fencing limited like
Avoiding risk by removing the possibility of any attack
Reduction of exposure to some of the attacks.
Retaining and managing risk each and every time.
Considering the cyber-crime, there is various kind of risk. Risk management should come
into picture by analyzing the wide picture. Then the mere focus is all about reducing the overall
amount of risk. The overall success of most of the organization is all about analyzing various
kind of risk factors followed by ranking them (Mattos and Duarte 2016). Risk factor can easily
range from hacker getting money transferring system to employee who have lost their mobile
devices. The very next stage is all about creating methods for prioritized task. Some of the
methods will require technical knowledge while other can be handled by the help of training.
Security areas to be considered Potential Security Measures
Physical Safeguards Facilities and other Building an alarm
Custom of data for decision making
Achieving data for business analysis
Risk management
Information technology risk management merely requires certain organization to easily
plan, monitor, track and manage various security risk. Organization like Fencing limited which
are connected to internet are easily exposed to cyber-crime (Haidzir, Othman and Mammi 2018).
Cyber-criminals come up with variety of methods for get into a system. They can get in through
an employee or any weak link into the system. This is mainly done so that they can steal some of
the vital information. There is a list of steps which should be taken by Fencing limited like
Avoiding risk by removing the possibility of any attack
Reduction of exposure to some of the attacks.
Retaining and managing risk each and every time.
Considering the cyber-crime, there is various kind of risk. Risk management should come
into picture by analyzing the wide picture. Then the mere focus is all about reducing the overall
amount of risk. The overall success of most of the organization is all about analyzing various
kind of risk factors followed by ranking them (Mattos and Duarte 2016). Risk factor can easily
range from hacker getting money transferring system to employee who have lost their mobile
devices. The very next stage is all about creating methods for prioritized task. Some of the
methods will require technical knowledge while other can be handled by the help of training.
Security areas to be considered Potential Security Measures
Physical Safeguards Facilities and other Building an alarm
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
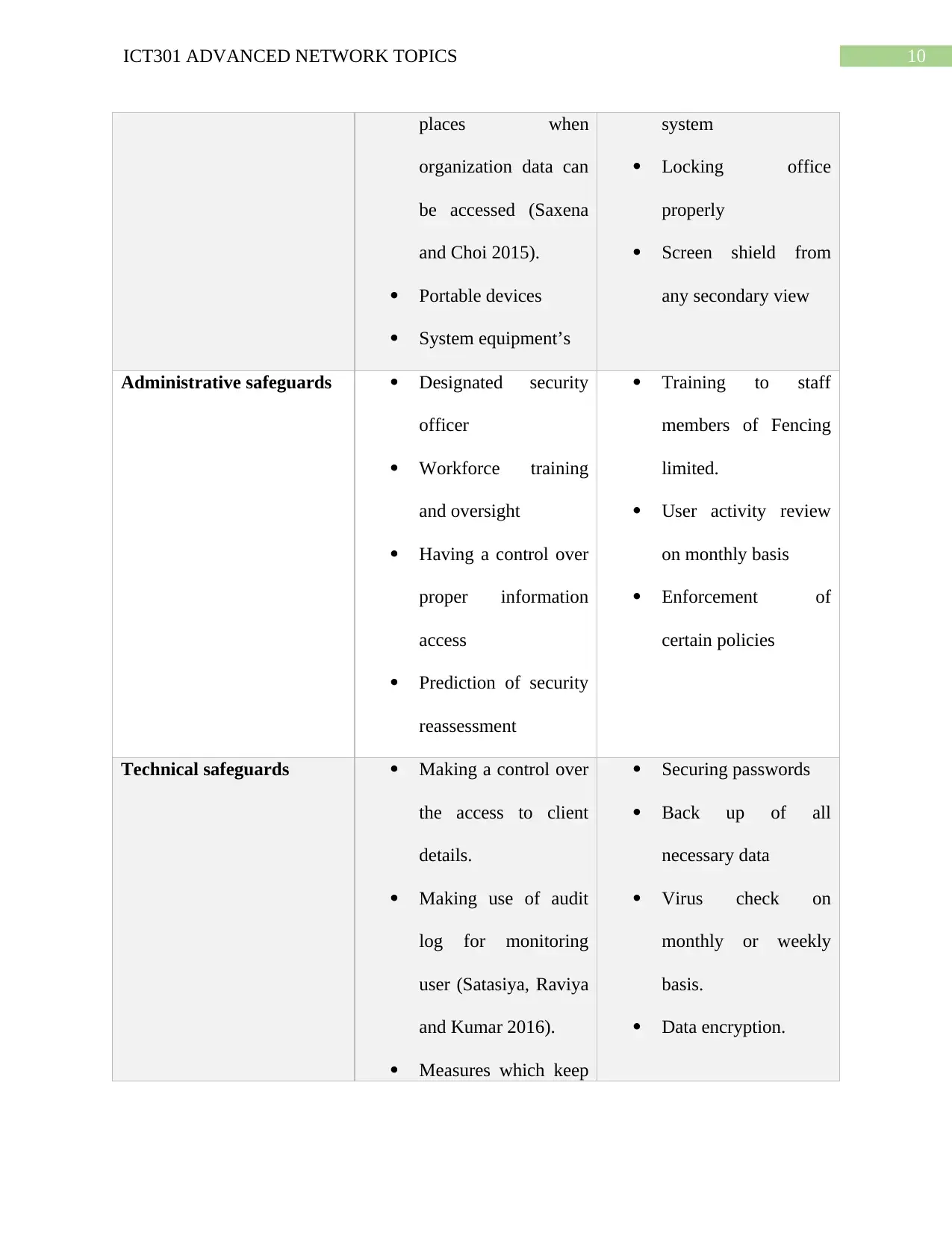
10ICT301 ADVANCED NETWORK TOPICS
places when
organization data can
be accessed (Saxena
and Choi 2015).
Portable devices
System equipment’s
system
Locking office
properly
Screen shield from
any secondary view
Administrative safeguards Designated security
officer
Workforce training
and oversight
Having a control over
proper information
access
Prediction of security
reassessment
Training to staff
members of Fencing
limited.
User activity review
on monthly basis
Enforcement of
certain policies
Technical safeguards Making a control over
the access to client
details.
Making use of audit
log for monitoring
user (Satasiya, Raviya
and Kumar 2016).
Measures which keep
Securing passwords
Back up of all
necessary data
Virus check on
monthly or weekly
basis.
Data encryption.
places when
organization data can
be accessed (Saxena
and Choi 2015).
Portable devices
System equipment’s
system
Locking office
properly
Screen shield from
any secondary view
Administrative safeguards Designated security
officer
Workforce training
and oversight
Having a control over
proper information
access
Prediction of security
reassessment
Training to staff
members of Fencing
limited.
User activity review
on monthly basis
Enforcement of
certain policies
Technical safeguards Making a control over
the access to client
details.
Making use of audit
log for monitoring
user (Satasiya, Raviya
and Kumar 2016).
Measures which keep
Securing passwords
Back up of all
necessary data
Virus check on
monthly or weekly
basis.
Data encryption.
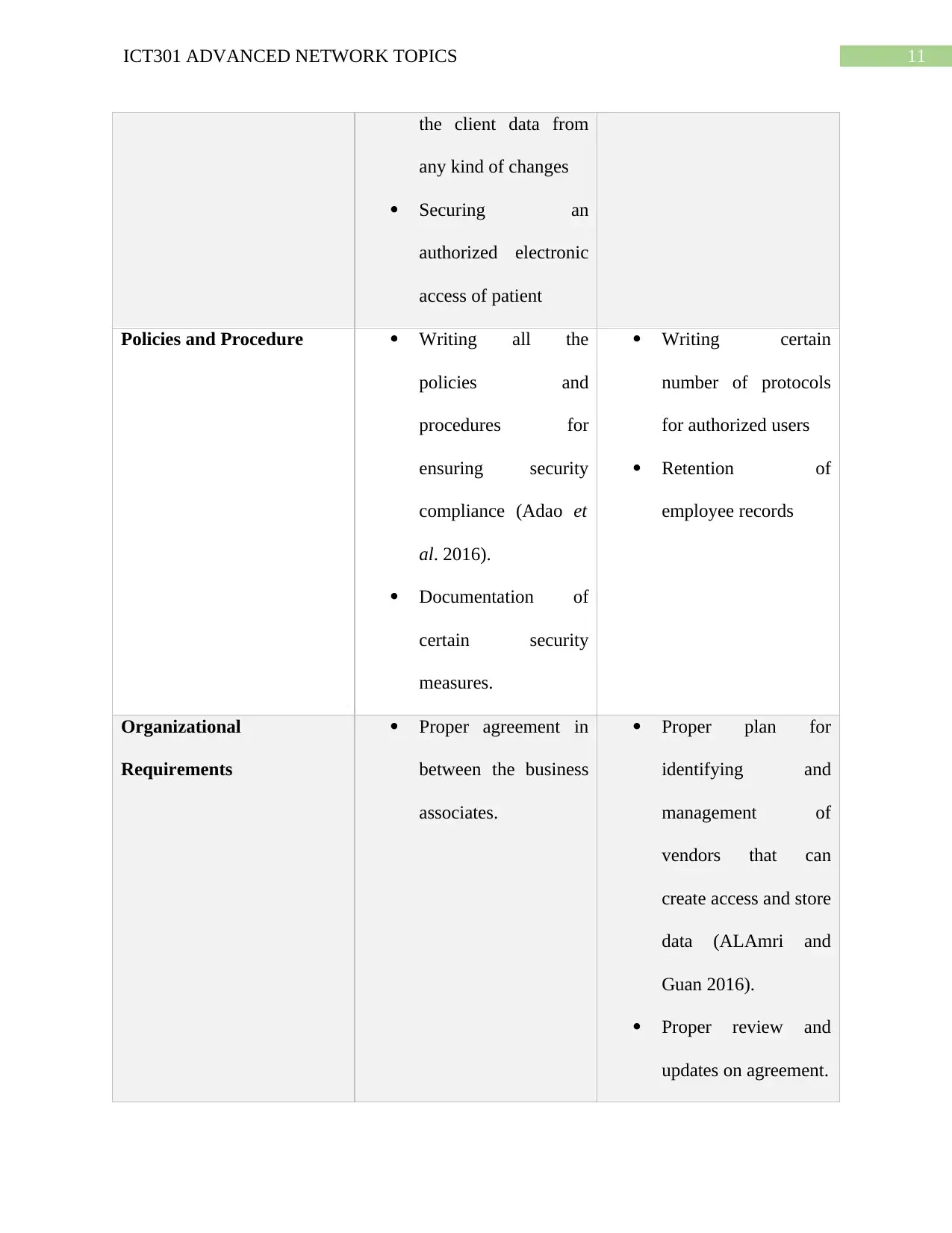
11ICT301 ADVANCED NETWORK TOPICS
the client data from
any kind of changes
Securing an
authorized electronic
access of patient
Policies and Procedure Writing all the
policies and
procedures for
ensuring security
compliance (Adao et
al. 2016).
Documentation of
certain security
measures.
Writing certain
number of protocols
for authorized users
Retention of
employee records
Organizational
Requirements
Proper agreement in
between the business
associates.
Proper plan for
identifying and
management of
vendors that can
create access and store
data (ALAmri and
Guan 2016).
Proper review and
updates on agreement.
the client data from
any kind of changes
Securing an
authorized electronic
access of patient
Policies and Procedure Writing all the
policies and
procedures for
ensuring security
compliance (Adao et
al. 2016).
Documentation of
certain security
measures.
Writing certain
number of protocols
for authorized users
Retention of
employee records
Organizational
Requirements
Proper agreement in
between the business
associates.
Proper plan for
identifying and
management of
vendors that can
create access and store
data (ALAmri and
Guan 2016).
Proper review and
updates on agreement.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





