ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING 27 27 ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING ICTNWK506 Student Assessment Booklet Name
VerifiedAdded on 2022/08/17
|30
|2043
|13
AI Summary
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING 27 27 ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING ICTNWK506 Student Assessment Booklet Name of the Student Name of the University Author’s Note Task 1: Initial Planning 2 Task 2: Produce a Logical Network Diagram 3 Task 3: Preparation and paper work 4 Task 4: Configure Routers, Routing protocol and WAN protocols 11 Task 5: NAT Configuration 15 Task 6: Security Access policies 16 Task 7: Troubleshooting and Documentation 17 References 29 Task 1:
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
ICTNWK506 Student Assessment Booklet
Name of the Student
Name of the University
Author’s Note
ICTNWK506 Student Assessment Booklet
Name of the Student
Name of the University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Table of Contents
Task 1: Initial Planning....................................................................................................................2
Task 2: Produce a Logical Network Diagram.................................................................................3
Task 3: Preparation and paper work................................................................................................4
Task 4: Configure Routers, Routing protocol and WAN protocols..............................................11
Task 5: NAT Configuration...........................................................................................................15
Task 6: Security Access policies...................................................................................................16
Task 7: Troubleshooting and Documentation................................................................................17
References......................................................................................................................................29
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Table of Contents
Task 1: Initial Planning....................................................................................................................2
Task 2: Produce a Logical Network Diagram.................................................................................3
Task 3: Preparation and paper work................................................................................................4
Task 4: Configure Routers, Routing protocol and WAN protocols..............................................11
Task 5: NAT Configuration...........................................................................................................15
Task 6: Security Access policies...................................................................................................16
Task 7: Troubleshooting and Documentation................................................................................17
References......................................................................................................................................29
2
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Task 1: Initial Planning
An IP addressing plan is created for IFL Delight Bread and Cake Company and given below:
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignabl
e Range
Broadcast
Product
Developme
nt Group
88 126 192.168.1.
0
/25 255.255.255.
128
192.168.1.
1 -
192.168.1.
126
192.168.1.
127
Sales &
marketing
group
33 62 192.168.1.
128
/26 255.255.255.
192
192.168.1.
129 -
192.168.1.
190
192.168.1.
191
Site
Security
group
11 14 192.168.1.
224
/28 255.255.255.
240
192.168.1.
225 -
192.168.1.
238
192.168.1.
239
Administra
tion group
17 30 192.168.1.
192
/27 255.255.255.
224
192.168.1.
193 -
192.168.1.
222
192.168.1.
223
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Task 1: Initial Planning
An IP addressing plan is created for IFL Delight Bread and Cake Company and given below:
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignabl
e Range
Broadcast
Product
Developme
nt Group
88 126 192.168.1.
0
/25 255.255.255.
128
192.168.1.
1 -
192.168.1.
126
192.168.1.
127
Sales &
marketing
group
33 62 192.168.1.
128
/26 255.255.255.
192
192.168.1.
129 -
192.168.1.
190
192.168.1.
191
Site
Security
group
11 14 192.168.1.
224
/28 255.255.255.
240
192.168.1.
225 -
192.168.1.
238
192.168.1.
239
Administra
tion group
17 30 192.168.1.
192
/27 255.255.255.
224
192.168.1.
193 -
192.168.1.
222
192.168.1.
223
3
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Production
group
132 254 192.168.0.
0
/24 255.255.255.
0
192.168.0.
1 -
192.168.0.
254
192.168.0.
255
Server
Farm
10 14 192.168.1.
240
/28 255.255.255.
240
192.168.1.
241 -
192.168.1.
254
192.168.1.
255
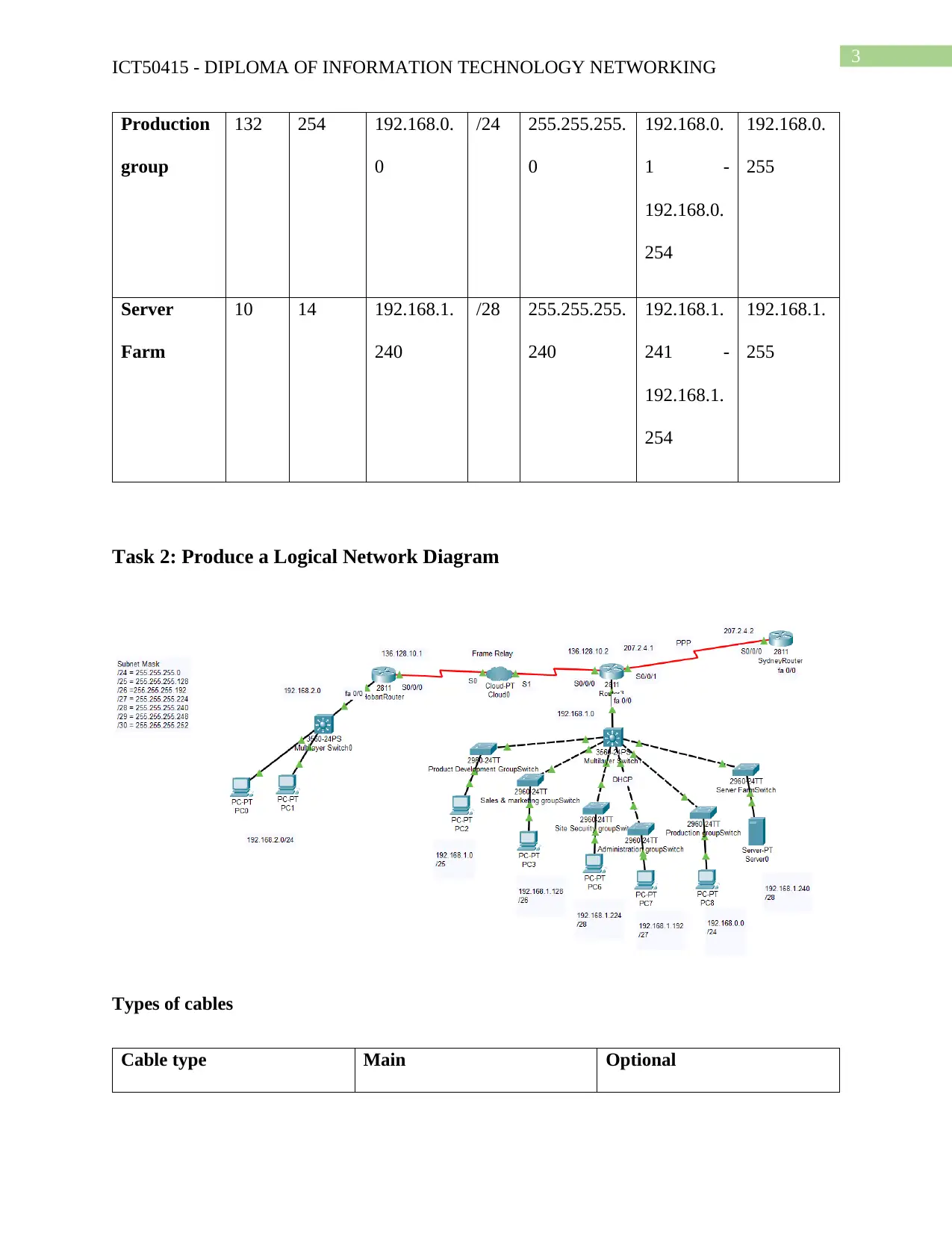
Task 2: Produce a Logical Network Diagram
Types of cables
Cable type Main Optional
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Production
group
132 254 192.168.0.
0
/24 255.255.255.
0
192.168.0.
1 -
192.168.0.
254
192.168.0.
255
Server
Farm
10 14 192.168.1.
240
/28 255.255.255.
240
192.168.1.
241 -
192.168.1.
254
192.168.1.
255
Task 2: Produce a Logical Network Diagram
Types of cables
Cable type Main Optional
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
UTP 100 ohm, multipair UTP
cable used for voice graded
communication
STP 150ohm STP cable 100 ohm STP cable
Coaxial 50ohm coaxial cable 75 ohm coaxial cable
Optical Fiber 6.26/125 multimode optical
fiber
Single-mode optical fiber
Different methods for connecting to WAN
WAN can be connected using different technology such as full mesh network topology,
hub and spoke technique. For designing the network we have used hub and spoke design such
that headquarter is connected with the branch office with the use of single P2P connection. The
full mesh topology requires each of the site to be connected with each other but it is costlier to
implement and complex to connect new site with the network.
Task 3: Preparation and paper work
Prepare for given work according to legislations, work health and safety codes,
regulations and standards.
Regulation and WHS Act needs a person having duty for ensuring that health and safety
is maintained for management of risk. The code of practice is needed to be followed for the
preparation of the work following legislations, work health and safety codes, standards and
regulations. The workers are needed to be engaged for undertaking the work for finding their
influence in the works. A decision is needed to be made for finding the practicable thing that can
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
UTP 100 ohm, multipair UTP
cable used for voice graded
communication
STP 150ohm STP cable 100 ohm STP cable
Coaxial 50ohm coaxial cable 75 ohm coaxial cable
Optical Fiber 6.26/125 multimode optical
fiber
Single-mode optical fiber
Different methods for connecting to WAN
WAN can be connected using different technology such as full mesh network topology,
hub and spoke technique. For designing the network we have used hub and spoke design such
that headquarter is connected with the branch office with the use of single P2P connection. The
full mesh topology requires each of the site to be connected with each other but it is costlier to
implement and complex to connect new site with the network.
Task 3: Preparation and paper work
Prepare for given work according to legislations, work health and safety codes,
regulations and standards.
Regulation and WHS Act needs a person having duty for ensuring that health and safety
is maintained for management of risk. The code of practice is needed to be followed for the
preparation of the work following legislations, work health and safety codes, standards and
regulations. The workers are needed to be engaged for undertaking the work for finding their
influence in the works. A decision is needed to be made for finding the practicable thing that can

5
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
protect the people from getting harm and taking all the relevant matters such as hazard
likelihood, degree of harm, knowledge about the hazard and the methods for minimizing risk
(Furci and Sunindijo 2018). The extent of the risk is needed is needed to be assessed for the
elimination or minimizing the risk. The cost associated with the elimination and minimization is
also needed to be assessed such that it can be found that whether the cost is disproportionate to
the risk.
The code of practice is also needed to be applied such that it can help in understanding
the process that is needed to be followed easily. The code of practice can be referred by an
inspector for issuing improvement or creating prohibition notice. In the Work Health and Safety
Act 2011, the code of practice is followed by the court and is admissible for proceeding (Sclater
2016). It can be used as evidence for getting the details of hazards, control or risk and rely on it
for determining the ‘reasonably practicable’, for the circumstances that are related with the code.
Following the Work Health and Safety Act 2011 and Safe Work Australia can also be used as a
guidance material for achieving the standards under the WHS laws. A risk management practice
is followed and it involves the following steps that sets the code:
Identification of hazards – the cause of the harm is needed to be found
Risk assessment – the nature of the harm is needed to be found that can be caused by
hazard and the seriousness of harm could and its likelihood for happening.
Risk control – the most effective control is needed to be implemented that can be
practiced for any circumstance.
Reviewing control measures – it is needed to be ensured that the practice is working as
per the planning.
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
protect the people from getting harm and taking all the relevant matters such as hazard
likelihood, degree of harm, knowledge about the hazard and the methods for minimizing risk
(Furci and Sunindijo 2018). The extent of the risk is needed is needed to be assessed for the
elimination or minimizing the risk. The cost associated with the elimination and minimization is
also needed to be assessed such that it can be found that whether the cost is disproportionate to
the risk.
The code of practice is also needed to be applied such that it can help in understanding
the process that is needed to be followed easily. The code of practice can be referred by an
inspector for issuing improvement or creating prohibition notice. In the Work Health and Safety
Act 2011, the code of practice is followed by the court and is admissible for proceeding (Sclater
2016). It can be used as evidence for getting the details of hazards, control or risk and rely on it
for determining the ‘reasonably practicable’, for the circumstances that are related with the code.
Following the Work Health and Safety Act 2011 and Safe Work Australia can also be used as a
guidance material for achieving the standards under the WHS laws. A risk management practice
is followed and it involves the following steps that sets the code:
Identification of hazards – the cause of the harm is needed to be found
Risk assessment – the nature of the harm is needed to be found that can be caused by
hazard and the seriousness of harm could and its likelihood for happening.
Risk control – the most effective control is needed to be implemented that can be
practiced for any circumstance.
Reviewing control measures – it is needed to be ensured that the practice is working as
per the planning.
6
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Organization policy and procedure
The strategic plan of the organization is needed to be evaluated and the policy document
of the organization e.g. services provided by the company to the linguistic and cultural diverse
clients, description of jobs. For getting the access of the site the legal documents such as the
ethics in practice, care guideline duty containing confidentiality, equity and access, protection
policy for child and occupational safety and health guidelines are needed to be followed.
Development of new network design
The existing network of IFL Delight Break and Cake is outdated and is needed to be
replaced for supporting the growth of the company. Multiple sites are needed to be connected
with the help of the new network and thus two types of protocols are used for interconnecting the
different areas (Al-Hanjori, Shaath and Naser 2017). Frame relay connection is used for the site
Hobart and Melbourne and PPP connection is used between Melbourne and Sydney.
Network devices needed for installation
No. of device Device Name Model Series Number of
Ports
3 Cisco 2800
Router
Cisco 2800
Integrated
Services Router
2800 Series ISR 1 auxiliary
port
1 Console port
2 USB port
3 Cisco Catalyst
WS-C2960S-
WS-C2960S-
24TS layer 2
WS-C2960S- 24 nos. LAN
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Organization policy and procedure
The strategic plan of the organization is needed to be evaluated and the policy document
of the organization e.g. services provided by the company to the linguistic and cultural diverse
clients, description of jobs. For getting the access of the site the legal documents such as the
ethics in practice, care guideline duty containing confidentiality, equity and access, protection
policy for child and occupational safety and health guidelines are needed to be followed.
Development of new network design
The existing network of IFL Delight Break and Cake is outdated and is needed to be
replaced for supporting the growth of the company. Multiple sites are needed to be connected
with the help of the new network and thus two types of protocols are used for interconnecting the
different areas (Al-Hanjori, Shaath and Naser 2017). Frame relay connection is used for the site
Hobart and Melbourne and PPP connection is used between Melbourne and Sydney.
Network devices needed for installation
No. of device Device Name Model Series Number of
Ports
3 Cisco 2800
Router
Cisco 2800
Integrated
Services Router
2800 Series ISR 1 auxiliary
port
1 Console port
2 USB port
3 Cisco Catalyst
WS-C2960S-
WS-C2960S-
24TS layer 2
WS-C2960S- 24 nos. LAN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
24TS-S 24-port
10/100/1000
switch
switch 24TS-S port
Action plan for installation of components
Task Name Duration Start Finish Predecessors
Resource
Names
Network development for IFL
Delight Bread and Cake
Company
32 days
Thu
1/10/19
Fri
2/22/19
Identification of the project
scope
5.5 days
Thu
1/10/19
Thu
1/17/19
Requirement analysis 2 days
Thu
1/10/19
Fri 1/11/19
Network
Manager ,Proje
ct manager
Feasibility study 1.5 days
Mon
1/14/19
Tue
1/15/19
2
Project
manager
Selection of the technology 2 days
Tue
1/15/19
Thu
1/17/19
3
Network
Manager ,Serv
er Manager
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
24TS-S 24-port
10/100/1000
switch
switch 24TS-S port
Action plan for installation of components
Task Name Duration Start Finish Predecessors
Resource
Names
Network development for IFL
Delight Bread and Cake
Company
32 days
Thu
1/10/19
Fri
2/22/19
Identification of the project
scope
5.5 days
Thu
1/10/19
Thu
1/17/19
Requirement analysis 2 days
Thu
1/10/19
Fri 1/11/19
Network
Manager ,Proje
ct manager
Feasibility study 1.5 days
Mon
1/14/19
Tue
1/15/19
2
Project
manager
Selection of the technology 2 days
Tue
1/15/19
Thu
1/17/19
3
Network
Manager ,Serv
er Manager
8
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Identification of network
device and equipment
26.5 days
Thu
1/17/19
Fri 2/22/19
Site survey 1.5 days
Thu
1/17/19
Fri 1/18/19 4
Project
manager
Analysis of list of hardware 2 days
Mon
1/21/19
Tue
1/22/19
6
Network
Manager
Development of a network
design
1 day
Wed
1/23/19
Wed
1/23/19
7
Network
Manager
Configuration of the
Network
12 days
Thu
1/24/19
Fri 2/8/19
Identification of number of
users
2 days
Thu
1/24/19
Fri 1/25/19 8
Project
manager
IP addressing plan 1.5 days
Mon
1/28/19
Tue
1/29/19
10
Network
Manager
Configuring router and
switches
2.5 days
Tue
1/29/19
Thu
1/31/19
11
Network
Manager
Network cabling 3 days Fri 2/1/19 Tue 2/5/19 12
Network
Manager
Connecting the device 3 days Wed 2/6/19 Fri 2/8/19 13 Network
Manager ,Serv
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Identification of network
device and equipment
26.5 days
Thu
1/17/19
Fri 2/22/19
Site survey 1.5 days
Thu
1/17/19
Fri 1/18/19 4
Project
manager
Analysis of list of hardware 2 days
Mon
1/21/19
Tue
1/22/19
6
Network
Manager
Development of a network
design
1 day
Wed
1/23/19
Wed
1/23/19
7
Network
Manager
Configuration of the
Network
12 days
Thu
1/24/19
Fri 2/8/19
Identification of number of
users
2 days
Thu
1/24/19
Fri 1/25/19 8
Project
manager
IP addressing plan 1.5 days
Mon
1/28/19
Tue
1/29/19
10
Network
Manager
Configuring router and
switches
2.5 days
Tue
1/29/19
Thu
1/31/19
11
Network
Manager
Network cabling 3 days Fri 2/1/19 Tue 2/5/19 12
Network
Manager
Connecting the device 3 days Wed 2/6/19 Fri 2/8/19 13 Network
Manager ,Serv
9
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
er Manager
Configuration of the Server 4 days
Mon
2/11/19
Thu
2/14/19
Configuring print server 2 days
Mon
2/11/19
Tue
2/12/19
14
Server
Manager
Configuring file server 2 days
Wed
2/13/19
Thu
2/14/19
16
Server
Manager
Project closure 6 days Fri 2/15/19 Fri 2/22/19
Testing the configuration 2.5 days Fri 2/15/19
Tue
2/19/19
17 Tester
Review of the requirement 1.5 days
Tue
2/19/19
Wed
2/20/19
19 Tester
Stakeholder sign off 2 days
Thu
2/21/19
Fri 2/22/19 20
Network
Manager ,Proje
ct
manager ,Serve
r
Manager ,Test
er
Approval of the Plan
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
er Manager
Configuration of the Server 4 days
Mon
2/11/19
Thu
2/14/19
Configuring print server 2 days
Mon
2/11/19
Tue
2/12/19
14
Server
Manager
Configuring file server 2 days
Wed
2/13/19
Thu
2/14/19
16
Server
Manager
Project closure 6 days Fri 2/15/19 Fri 2/22/19
Testing the configuration 2.5 days Fri 2/15/19
Tue
2/19/19
17 Tester
Review of the requirement 1.5 days
Tue
2/19/19
Wed
2/20/19
19 Tester
Stakeholder sign off 2 days
Thu
2/21/19
Fri 2/22/19 20
Network
Manager ,Proje
ct
manager ,Serve
r
Manager ,Test
er
Approval of the Plan
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Stakeholder engaged in project approval Signature
Project Manager <please fill>
Sponsor <please fill>
Head of the organization <please fill>
Task 4: Configure Routers, Routing protocol and WAN protocols
Internal network address: 192.168.0.0/18
Router serial interface: 136.128.10.0/30
NAT pool public address: 178.4.0.0/23
ISP network connection address: 207.2.4.0/30
Configuration and verification of router serial interfaces
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Stakeholder engaged in project approval Signature
Project Manager <please fill>
Sponsor <please fill>
Head of the organization <please fill>
Task 4: Configure Routers, Routing protocol and WAN protocols
Internal network address: 192.168.0.0/18
Router serial interface: 136.128.10.0/30
NAT pool public address: 178.4.0.0/23
ISP network connection address: 207.2.4.0/30
Configuration and verification of router serial interfaces

11
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
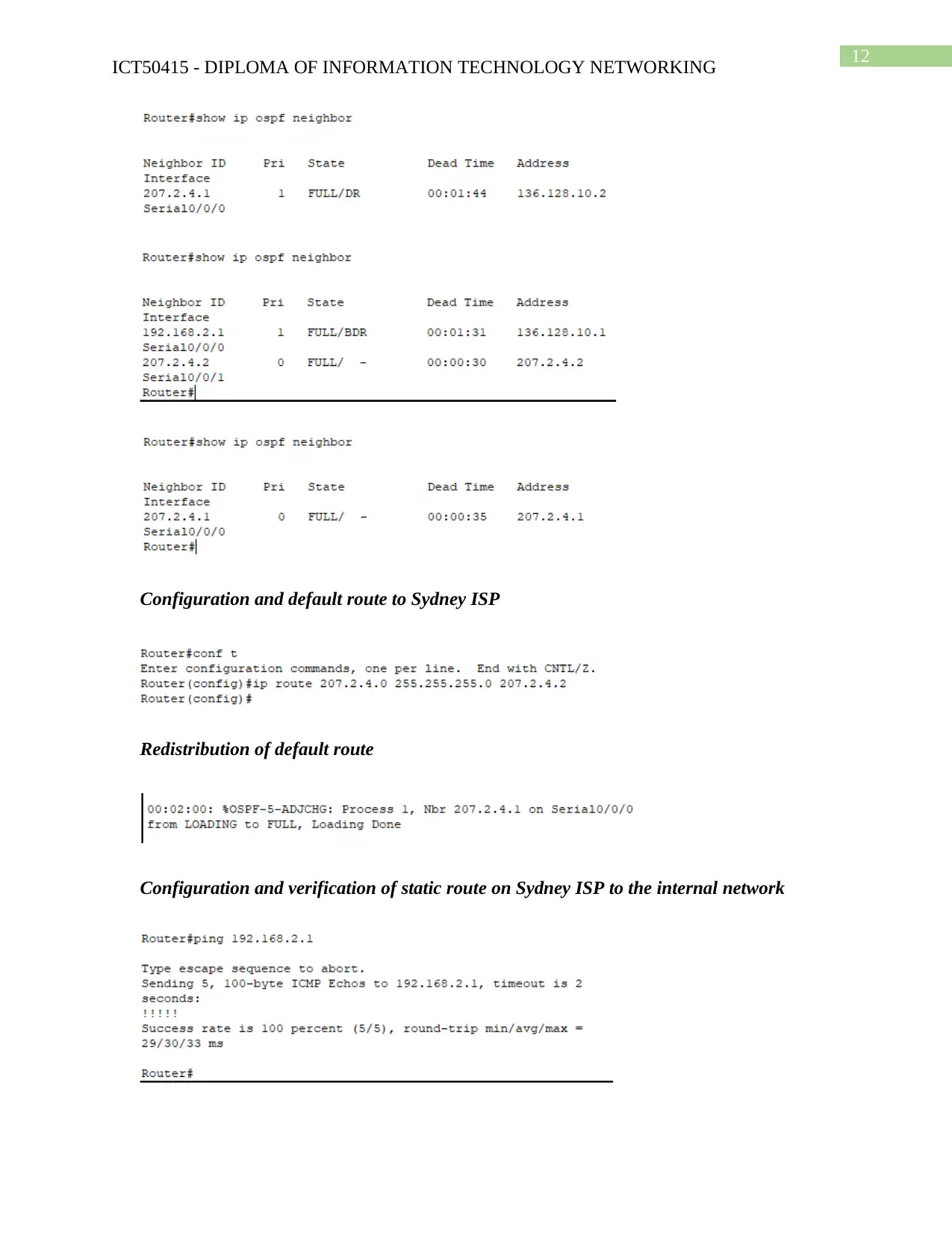
Configuration and verification of routing protocol OSPF
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Configuration and verification of routing protocol OSPF
12
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Configuration and default route to Sydney ISP
Redistribution of default route
Configuration and verification of static route on Sydney ISP to the internal network
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Configuration and default route to Sydney ISP
Redistribution of default route
Configuration and verification of static route on Sydney ISP to the internal network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
13
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
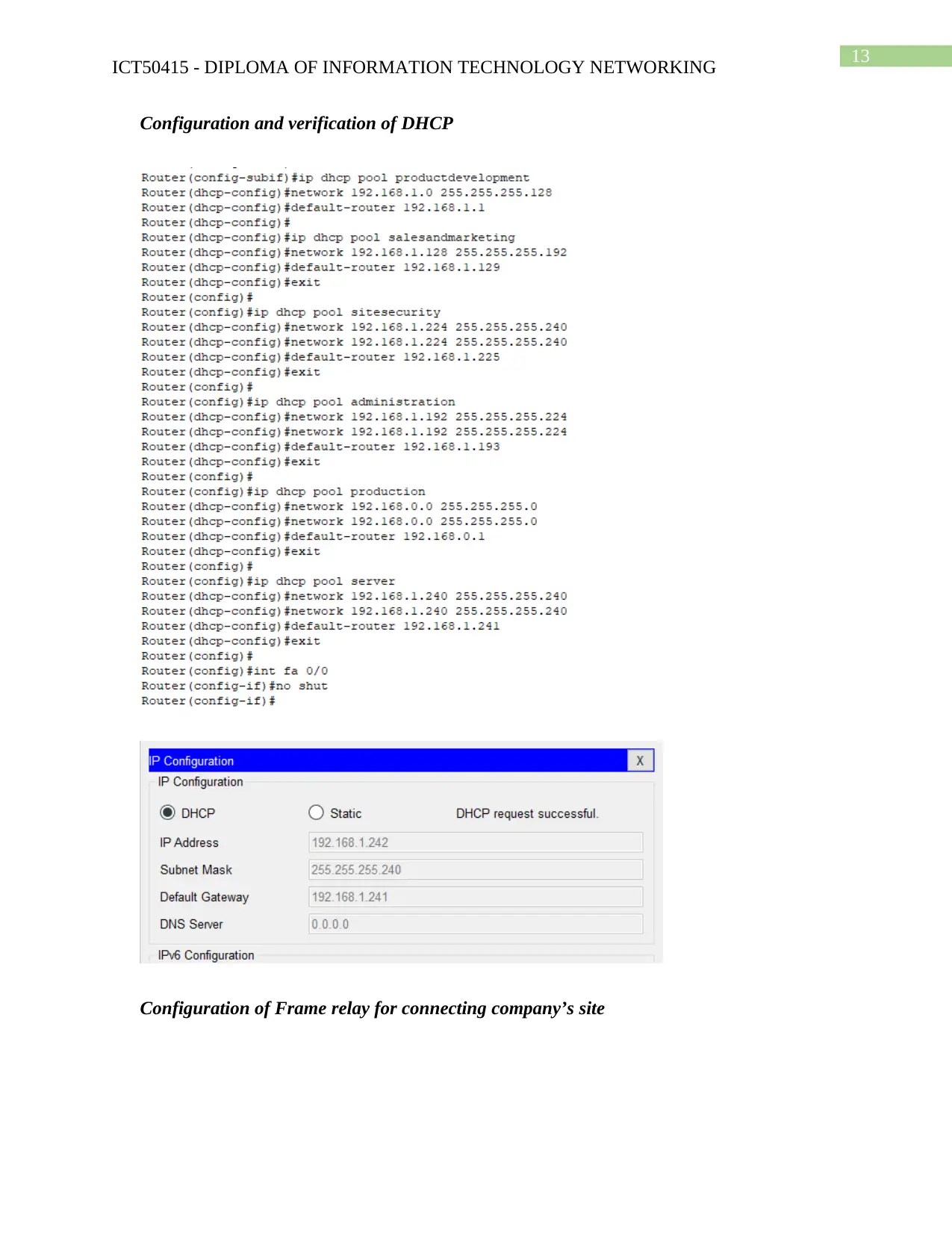
Configuration and verification of DHCP
Configuration of Frame relay for connecting company’s site
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Configuration and verification of DHCP
Configuration of Frame relay for connecting company’s site

14
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Configuration and verification of PPP and CHAP authentication
Task 5: NAT Configuration
Defining NAT pool
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Configuration and verification of PPP and CHAP authentication
Task 5: NAT Configuration
Defining NAT pool

15
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Defining access control list
Testing of NAT
NAT translation table
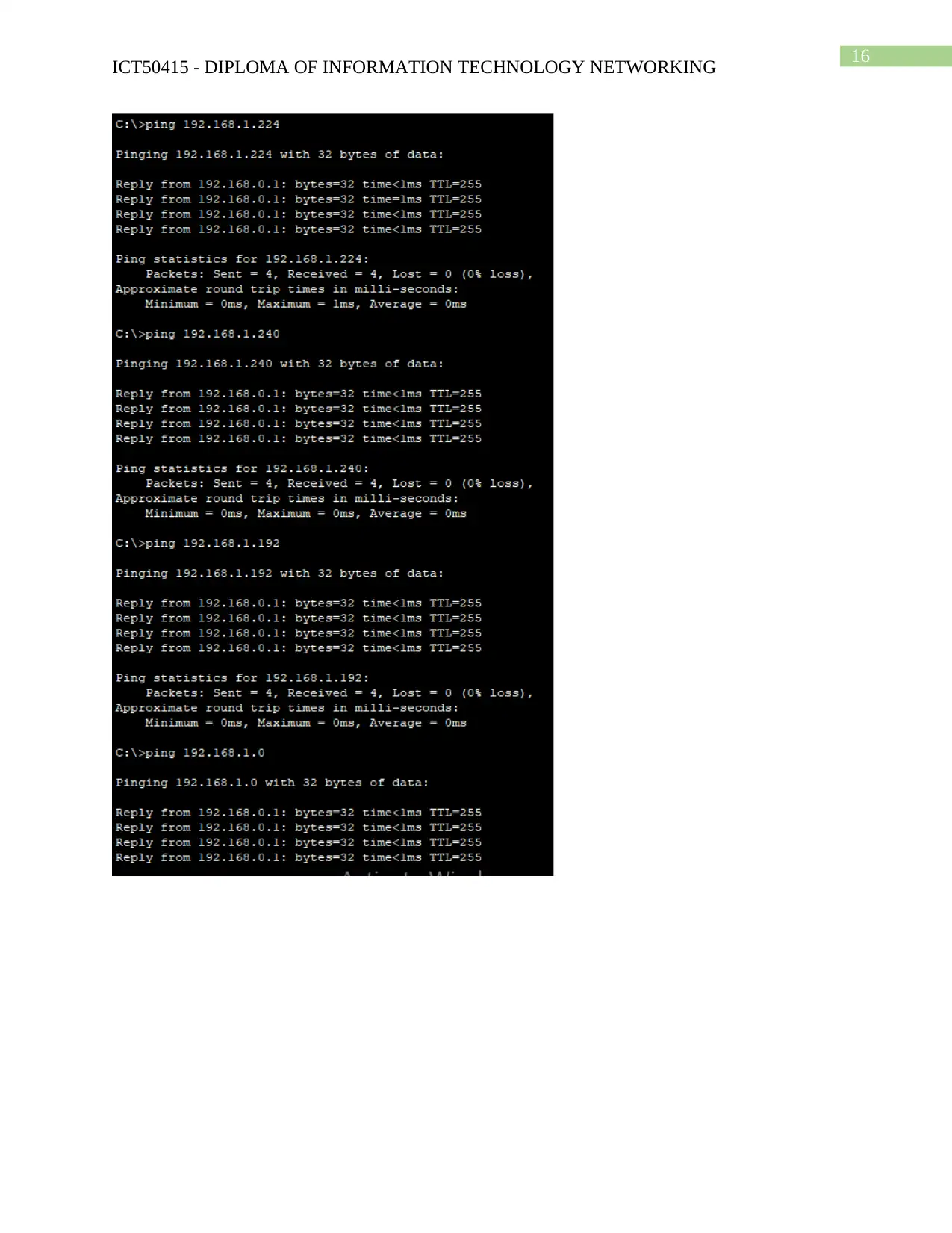
Task 6: Security Access policies
Ping Test
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Defining access control list
Testing of NAT
NAT translation table
Task 6: Security Access policies
Ping Test
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
16
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
17
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
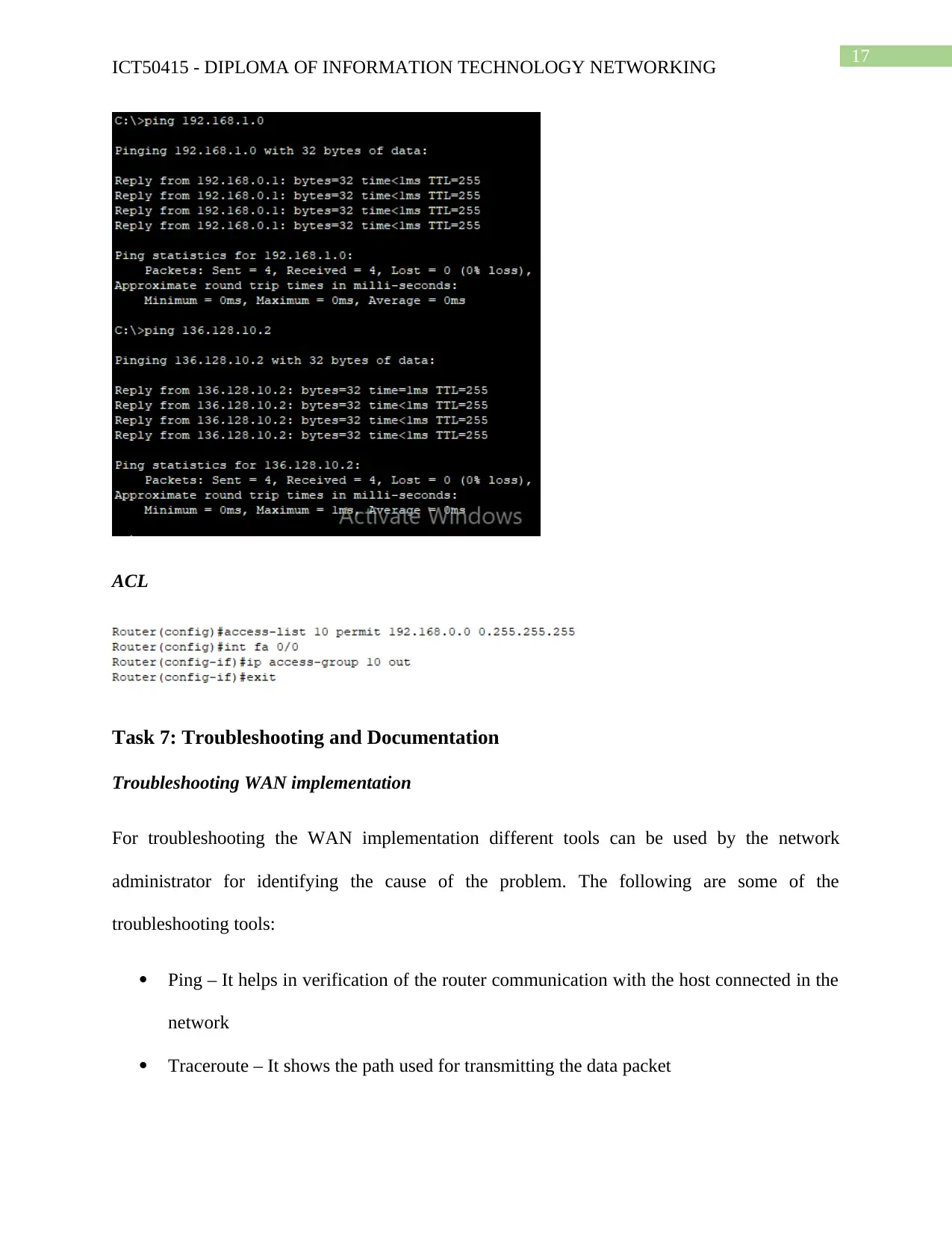
ACL
Task 7: Troubleshooting and Documentation
Troubleshooting WAN implementation
For troubleshooting the WAN implementation different tools can be used by the network
administrator for identifying the cause of the problem. The following are some of the
troubleshooting tools:
Ping – It helps in verification of the router communication with the host connected in the
network
Traceroute – It shows the path used for transmitting the data packet
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
ACL
Task 7: Troubleshooting and Documentation
Troubleshooting WAN implementation
For troubleshooting the WAN implementation different tools can be used by the network
administrator for identifying the cause of the problem. The following are some of the
troubleshooting tools:
Ping – It helps in verification of the router communication with the host connected in the
network
Traceroute – It shows the path used for transmitting the data packet

18
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Netstat – It shows the network connection for TCP protocol, routing table and interface
of the netwok
Ipconfig – It displays the configuration of the network device
Description and justification of design
The routes of each of the sites are configured with DHCP pool and the network is
subnetted according to the number of departments in that office. A layer three switching device
is introduced for management of VLAN and the subnet and it is configured as VTP server such
that the changes can be managed at a small time and the network can support the growth for the
coming three years.
Implementation of:
WAN Protocol – Point to point protocol is used for establish connecting between two
routers without the involvement of any host. It is used for authentication, transmission
encryption and compression. The protocol is applied for serial cables, trunk lines, fiber
optics links etc. DHCP Service – It is used for sending broadcasts and asking for an IP address and the
router picks the packets and relays it to the DHCP server for allocating an IP address to
the host. A range of IP address is used and it is reserved by the administrator for
allocation. NAT Service – It is used to remap the IP address with other by modifying the address
information that transmit between the routing devices.
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Netstat – It shows the network connection for TCP protocol, routing table and interface
of the netwok
Ipconfig – It displays the configuration of the network device
Description and justification of design
The routes of each of the sites are configured with DHCP pool and the network is
subnetted according to the number of departments in that office. A layer three switching device
is introduced for management of VLAN and the subnet and it is configured as VTP server such
that the changes can be managed at a small time and the network can support the growth for the
coming three years.
Implementation of:
WAN Protocol – Point to point protocol is used for establish connecting between two
routers without the involvement of any host. It is used for authentication, transmission
encryption and compression. The protocol is applied for serial cables, trunk lines, fiber
optics links etc. DHCP Service – It is used for sending broadcasts and asking for an IP address and the
router picks the packets and relays it to the DHCP server for allocating an IP address to
the host. A range of IP address is used and it is reserved by the administrator for
allocation. NAT Service – It is used to remap the IP address with other by modifying the address
information that transmit between the routing devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Security Access policies – It is used for restricting unauthorized access and minimizing
risk with the organization. It performs authorization, authentication and other security
controls. Troubleshooting and verification strategy – the network configuration is needed to be
documented and an information is needed to be collected for the identification of the
symptoms. Then the problem is needed to be defined and the severity is needed to be
assigned (Al-Hanjori, Shaath and Naser 2017). The system or subsystems involved is also
needed to be identified for the development of a hypothesis table. A solution to the
problem is created and it is needed to be implemented and evaluated. Asymmetric digital subscriber line – The technology is used for enabling faster
transmission of data using copper telephone lines. The bit rate and bandwidth is
asymmetric that means greater for downstream than upstream. DSL isolates the
frequency bands and thus allows the telephone lines to carry both voice and data service.
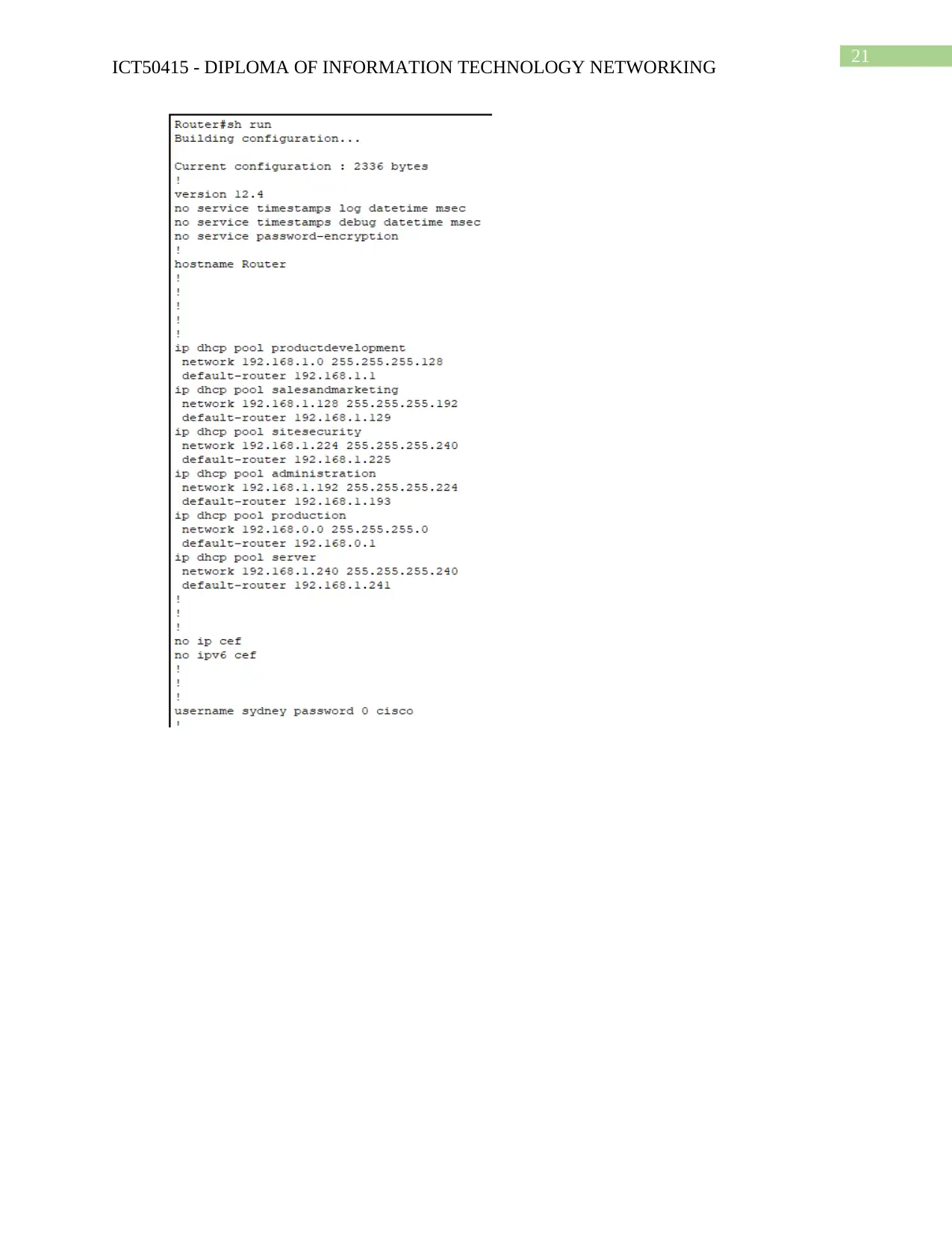
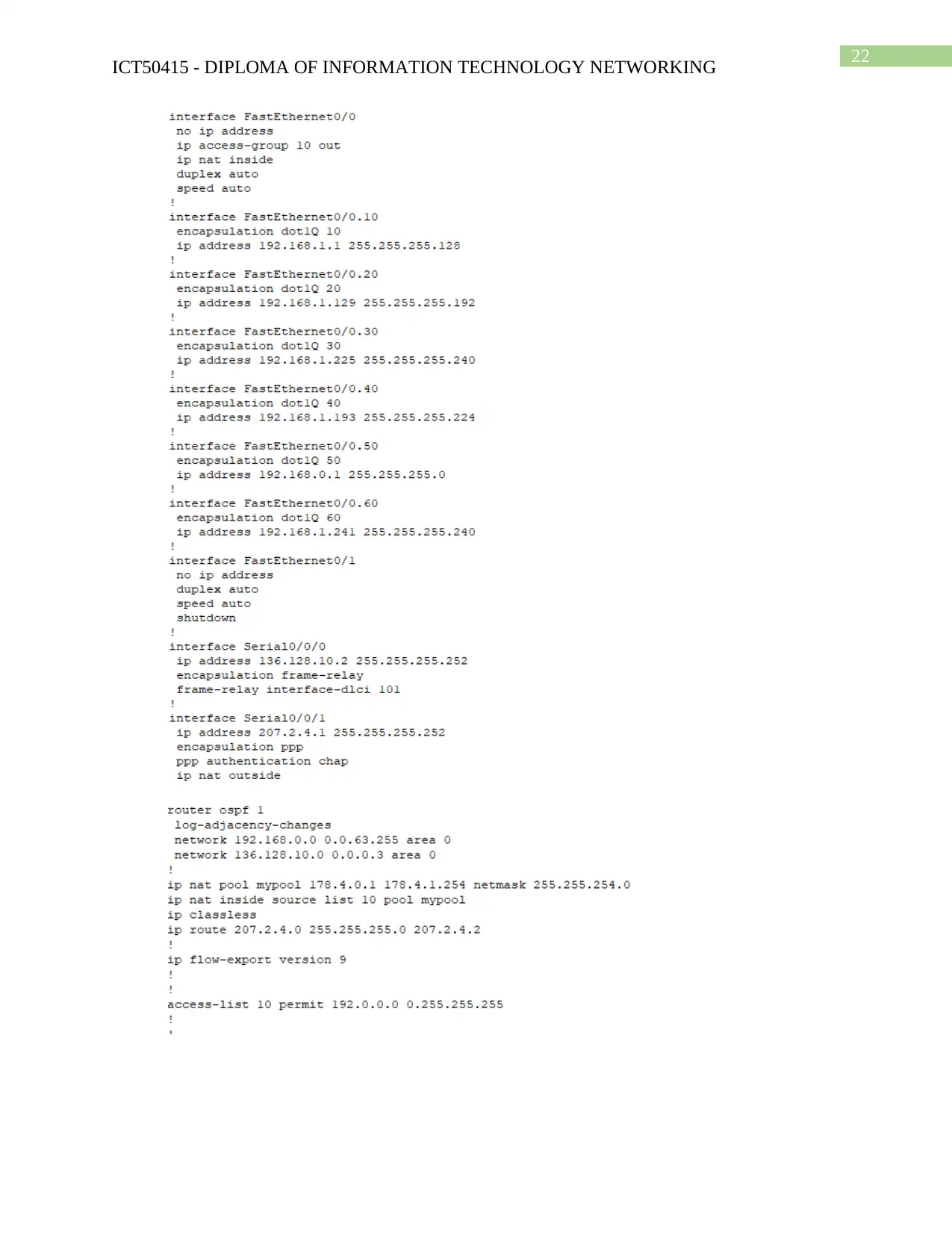
Router Configuration
Show run
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Security Access policies – It is used for restricting unauthorized access and minimizing
risk with the organization. It performs authorization, authentication and other security
controls. Troubleshooting and verification strategy – the network configuration is needed to be
documented and an information is needed to be collected for the identification of the
symptoms. Then the problem is needed to be defined and the severity is needed to be
assigned (Al-Hanjori, Shaath and Naser 2017). The system or subsystems involved is also
needed to be identified for the development of a hypothesis table. A solution to the
problem is created and it is needed to be implemented and evaluated. Asymmetric digital subscriber line – The technology is used for enabling faster
transmission of data using copper telephone lines. The bit rate and bandwidth is
asymmetric that means greater for downstream than upstream. DSL isolates the
frequency bands and thus allows the telephone lines to carry both voice and data service.
Router Configuration
Show run

20
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
21
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
22
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING

23
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Show ip interface brief
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Show ip interface brief

24
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Show access-lists
Show ip route
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Show access-lists
Show ip route
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING

26
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
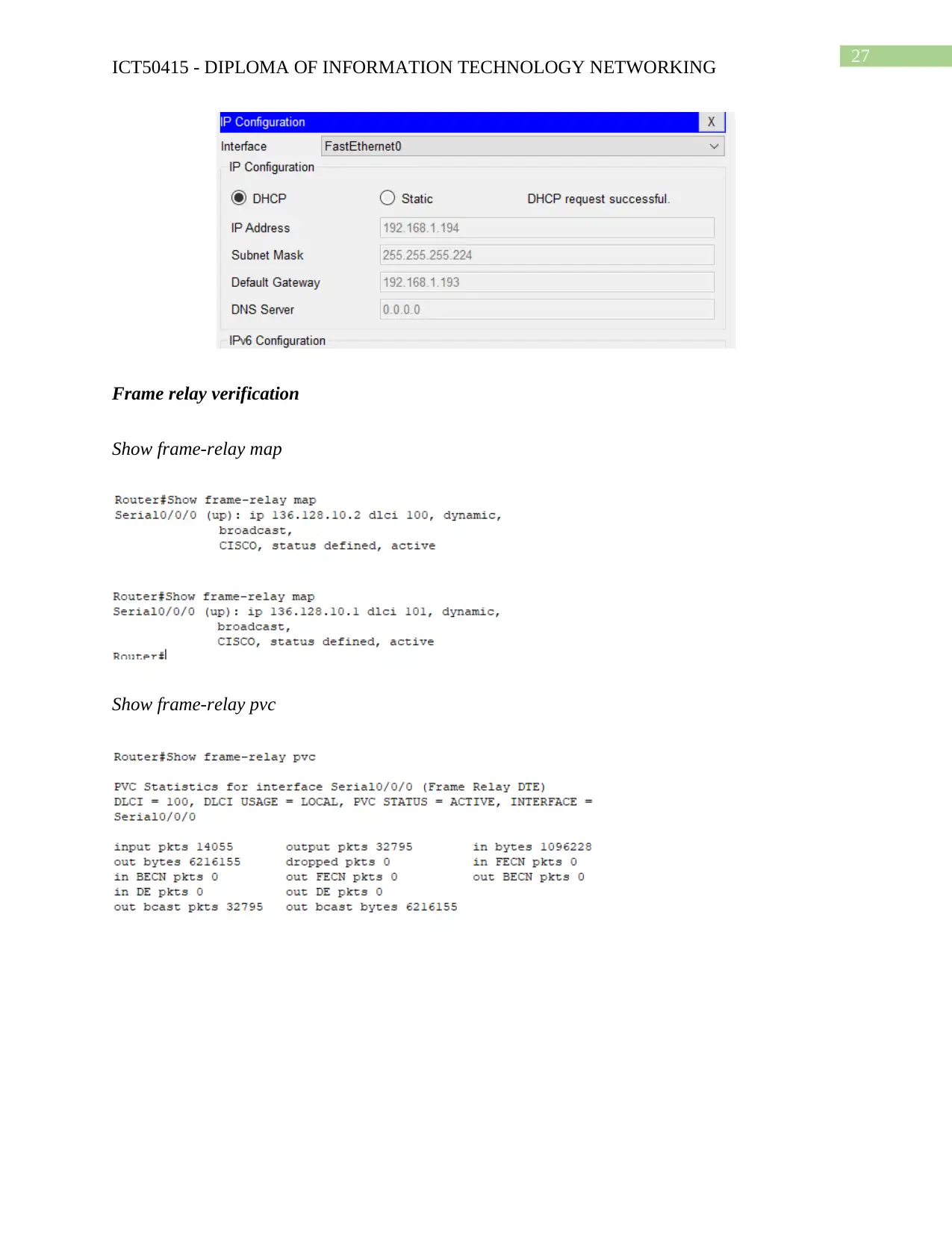
NAT Output
Show ip nat translation
DHCP Output
Show dhcp bindings
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
NAT Output
Show ip nat translation
DHCP Output
Show dhcp bindings
27
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Frame relay verification
Show frame-relay map
Show frame-relay pvc
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Frame relay verification
Show frame-relay map
Show frame-relay pvc
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

28
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Show frame-relay lmi
Packet tracer file of the network
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
Show frame-relay lmi
Packet tracer file of the network

29
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
References
Al-Hanjori, M.M., Shaath, M.Z. and Naser, S.S.A., 2017. Learning computer networks using
intelligent tutoring system.
Furci, J. and Sunindijo, R.Y., 2018. Impacts of the WHS Act 2011 on safety management in
small and medium construction companies. International Journal of Construction Management,
pp.1-11.
Sclater, N., 2016. Developing a code of practice for learning analytics. Journal of Learning
Analytics, 3(1), pp.16-42.
ICT50415 - DIPLOMA OF INFORMATION TECHNOLOGY NETWORKING
References
Al-Hanjori, M.M., Shaath, M.Z. and Naser, S.S.A., 2017. Learning computer networks using
intelligent tutoring system.
Furci, J. and Sunindijo, R.Y., 2018. Impacts of the WHS Act 2011 on safety management in
small and medium construction companies. International Journal of Construction Management,
pp.1-11.
Sclater, N., 2016. Developing a code of practice for learning analytics. Journal of Learning
Analytics, 3(1), pp.16-42.
1 out of 30
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.