ICTNWK506 - Configure, Verify & Troubleshoot WAN Links and IP Services
VerifiedAdded on 2024/07/12
|24
|3869
|346
Homework Assignment
AI Summary
This assignment focuses on configuring, verifying, and troubleshooting WAN links and IP services within a medium enterprise network, addressing key aspects such as pre-deployment assessments, network management, and ISP redundancy. It covers essential network services like NAT, DHCP, and ADSL, along with VPN configuration and troubleshooting, emphasizing security measures, legislative compliance, and workplace safety. The assignment includes a review of existing network designs, highlighting the need for updates to accommodate future requirements and enhance security and efficiency. Technical requirements, vendor selection, and the installation process are detailed, along with the importance of obtaining necessary approvals and security clearances. Different WAN technologies like Dark Fiber, Metro Ethernet, and MPLS are explored, and the configuration and verification steps for site-to-site VPNs and ADSL connections are provided. The document also explains the benefits of DHCP, the differences between static and dynamic IP addresses, and the operation and configuration of NAT, including verification steps. Desklib offers this student-contributed solution and many more resources to aid students in their studies.

ICTNWK506
Configure, verify and troubleshoot WAN links
and IP services in a medium enterprise network
ASSESSMENT
Configure, verify and troubleshoot WAN links
and IP services in a medium enterprise network
ASSESSMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................2
Question 3..................................................................................................................................3
Question 4..................................................................................................................................5
Question 5..................................................................................................................................5
Question 6..................................................................................................................................5
Question 7..................................................................................................................................7
Question 8..................................................................................................................................7
Question 9..................................................................................................................................7
Question 10................................................................................................................................7
Question 11................................................................................................................................8
Question 12................................................................................................................................8
Question 13................................................................................................................................8
Question 14................................................................................................................................9
Question 15................................................................................................................................9
Question 16................................................................................................................................9
Question 17..............................................................................................................................10
Question 18..............................................................................................................................10
Question 19..............................................................................................................................11
Question 20..............................................................................................................................13
Question 22..............................................................................................................................15
Question 23..............................................................................................................................15
Question 24..............................................................................................................................16
Question 25..............................................................................................................................16
Question 26..............................................................................................................................16
Question 27..............................................................................................................................17
Question 28..............................................................................................................................17
Question 29..............................................................................................................................18
Question 30..............................................................................................................................18
Question 31..............................................................................................................................19
References................................................................................................................................ 20
Question 1..................................................................................................................................2
Question 2..................................................................................................................................2
Question 3..................................................................................................................................3
Question 4..................................................................................................................................5
Question 5..................................................................................................................................5
Question 6..................................................................................................................................5
Question 7..................................................................................................................................7
Question 8..................................................................................................................................7
Question 9..................................................................................................................................7
Question 10................................................................................................................................7
Question 11................................................................................................................................8
Question 12................................................................................................................................8
Question 13................................................................................................................................8
Question 14................................................................................................................................9
Question 15................................................................................................................................9
Question 16................................................................................................................................9
Question 17..............................................................................................................................10
Question 18..............................................................................................................................10
Question 19..............................................................................................................................11
Question 20..............................................................................................................................13
Question 22..............................................................................................................................15
Question 23..............................................................................................................................15
Question 24..............................................................................................................................16
Question 25..............................................................................................................................16
Question 26..............................................................................................................................16
Question 27..............................................................................................................................17
Question 28..............................................................................................................................17
Question 29..............................................................................................................................18
Question 30..............................................................................................................................18
Question 31..............................................................................................................................19
References................................................................................................................................ 20

Question 1
In order to plan for a Wan link installation for public and private. We need to configure the
serial and passed Ethernet codes. We need to plan the security for network and the Firewalls.
There are some steps to prepare for the WAN Network.
(a) Conduct Pre-Deployment and Readiness Assessments
(b) Shift the Network Management Focus
(c) Determine Priorities
(d) Consider ISP Redundancy
Question 2
In order to plan for a Wan link installation for public and private. We need to configure the
serial and passed Ethernet codes. We need to plan the security for network and the Firewalls.
There are some steps to prepare for the WAN Network.
(a) Conduct Pre-Deployment and Readiness Assessments
(b) Shift the Network Management Focus
(c) Determine Priorities
(d) Consider ISP Redundancy
Question 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 3
a) Network address translation (NAT)
b) Dynamic host configuration protocol (DHCP)
c) Access control lists (ACLs)
a) Network address translation (NAT)
b) Dynamic host configuration protocol (DHCP)
c) Access control lists (ACLs)
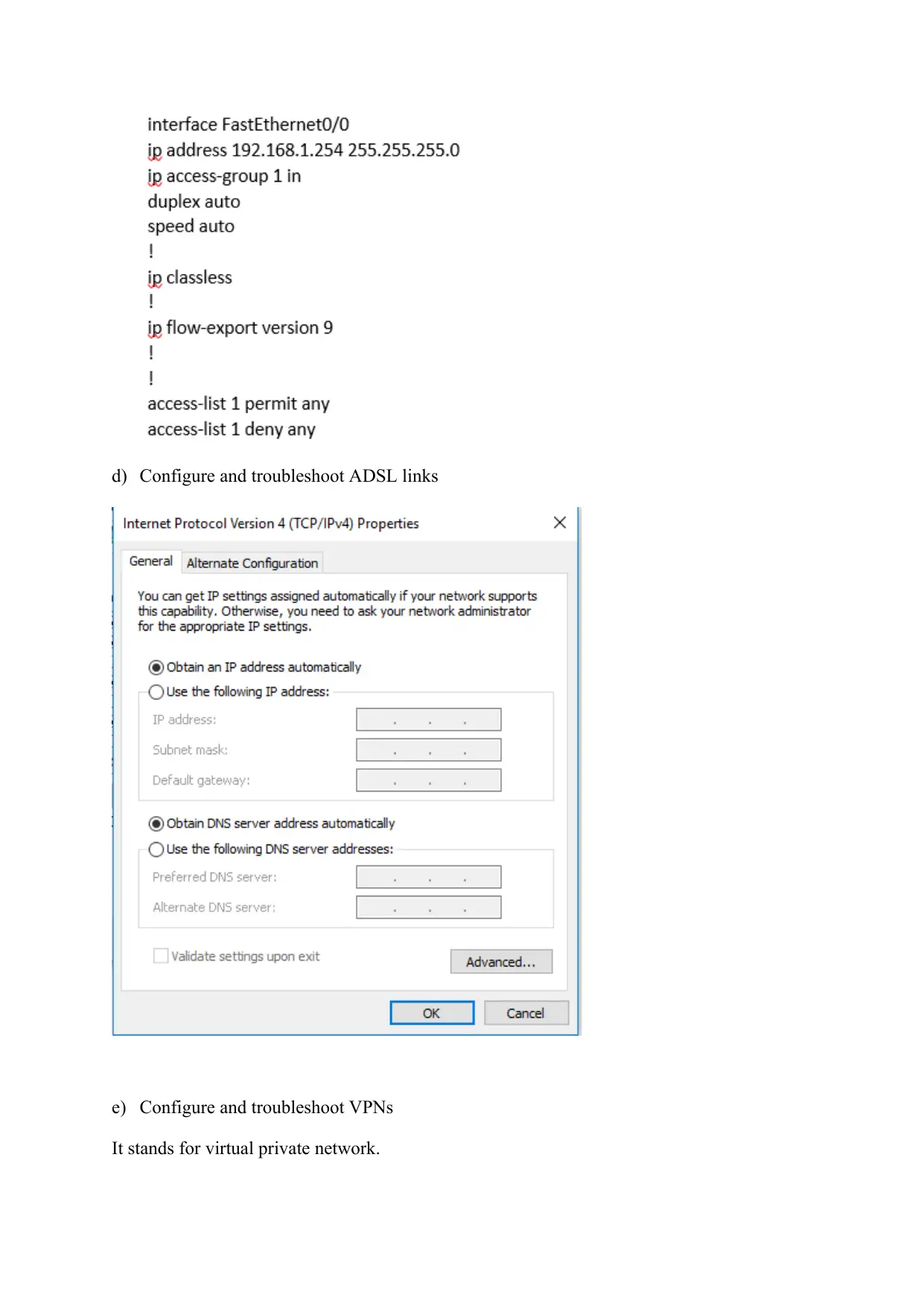
d) Configure and troubleshoot ADSL links
e) Configure and troubleshoot VPNs
It stands for virtual private network.
e) Configure and troubleshoot VPNs
It stands for virtual private network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Question 4
For NAT Configuration we configure the interface – of Nat on either interface enabling the
network security. We can have multiple computers on the internal network connected to a
public IP address and vice versa. In DHCP we configure the services on server creating
pools with different subnets for IP address, each range is different and helps in creating
redundancy. ADSL – Asymmetric subscriber line is used to connect the internet, we could
use PPPoE or IP address format to connect internet. VPN can be configured on routing and
remote access on the server and each server will have access to the network moreover some
of the features chaps is the protocol and connection is made to establish connection remotely
Question 5
Security passes, login details, network resources shared, IP configuration map, for NAT we
needed to get IP address tables for connection and translation, On VPN we need the server to
connect the server and connections, ADSL we need to configure the phone ADSL, pope
connections, and others.
Question 6
Legislations: There are various rules that are applied to the networks and computers. The
acts under this are as under:
For NAT Configuration we configure the interface – of Nat on either interface enabling the
network security. We can have multiple computers on the internal network connected to a
public IP address and vice versa. In DHCP we configure the services on server creating
pools with different subnets for IP address, each range is different and helps in creating
redundancy. ADSL – Asymmetric subscriber line is used to connect the internet, we could
use PPPoE or IP address format to connect internet. VPN can be configured on routing and
remote access on the server and each server will have access to the network moreover some
of the features chaps is the protocol and connection is made to establish connection remotely
Question 5
Security passes, login details, network resources shared, IP configuration map, for NAT we
needed to get IP address tables for connection and translation, On VPN we need the server to
connect the server and connections, ADSL we need to configure the phone ADSL, pope
connections, and others.
Question 6
Legislations: There are various rules that are applied to the networks and computers. The
acts under this are as under:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Communications (2003): This rule protects the improper or illegal use of the services of
public communications.
Computer Misuse (1990): This rule protects the computers and data from any interference
and unauthorized access.
Investigatory Power (2016): This rule controls the traffic interception occurring on the
networks. It provides powers to investigating authorities and police to obtain information
about their users and usage.
Data Protection (2018): It establishes the requirements to the person that have personal
data on any system.
Police and Justice (2006): This rule has created various new types of offences related to
obtaining, supplying and making of tools that are used in the computer misuse rule of
1990 (Jisc, 2015).
Work Health and Safety codes: There are obligations for ensuring the safety and health of
the employees working. For this, certain standards and regulations are needed for the
workplace.
Ensure handling of hazardous materials safely at the workplace. For this, learn using,
storing, handling, labelling and disposing of them correctly.
Use tools and resources that help the company to comply with the health and safety
requirements of the workplace.
Regulations and Standards used: In this, we have used network codes and regulations for
the networking. They are as under:
Network Codes: These are the Industry codes. Some of the codes are as
under:
1. Billing Accuracy and Call Charging
2. Deployment rules of Local Loop service, etc
Network Standards: There are standards set by the government related to
the interconnection facilities in the telecommunications (Acme, 2017).
public communications.
Computer Misuse (1990): This rule protects the computers and data from any interference
and unauthorized access.
Investigatory Power (2016): This rule controls the traffic interception occurring on the
networks. It provides powers to investigating authorities and police to obtain information
about their users and usage.
Data Protection (2018): It establishes the requirements to the person that have personal
data on any system.
Police and Justice (2006): This rule has created various new types of offences related to
obtaining, supplying and making of tools that are used in the computer misuse rule of
1990 (Jisc, 2015).
Work Health and Safety codes: There are obligations for ensuring the safety and health of
the employees working. For this, certain standards and regulations are needed for the
workplace.
Ensure handling of hazardous materials safely at the workplace. For this, learn using,
storing, handling, labelling and disposing of them correctly.
Use tools and resources that help the company to comply with the health and safety
requirements of the workplace.
Regulations and Standards used: In this, we have used network codes and regulations for
the networking. They are as under:
Network Codes: These are the Industry codes. Some of the codes are as
under:
1. Billing Accuracy and Call Charging
2. Deployment rules of Local Loop service, etc
Network Standards: There are standards set by the government related to
the interconnection facilities in the telecommunications (Acme, 2017).

Question 7
The procedures and workplace policies used are a risk assessment, information sensitivity,
audit policy, request for account access, email policy, spam policy etc (Paquet, 2013).
Question 8
On reviewing the existing document of network design it was found that it was difficult to
foresee the requirements of the future, security, growth, efficiency, and capacity. Also, they
have squeezed many computers and another network device into a single logical network. SO
the current network design was incomplete and needs to be updated (Partsenidis, 2003).
Question 9
Technical requirements needed to be the internet connection, Diagnostic tools for network,
bandwidth, software for local caching, Firewalls, filters etc (Bird and Harwood, 2002).
Question 10
a)
For this, we have contacted vendors who sell modem, routers, bridges, hubs, switches,
gateways etc.
b)
The network elements needed for the networking purpose are as under:
S. No Element Specification
1. Modem BCM63168
2. Routers 802.11 a/b/g/n/ac
3. Bridges Quadro M32X
4. Hubs Cisco 1538 Series 10 100 Micro Hub
5. Switches Cisco Catalyst 2960S-24TS-L
6. Wireless Access Points Aironet 1815 Series
7. Gateways Cisco 2900
The procedures and workplace policies used are a risk assessment, information sensitivity,
audit policy, request for account access, email policy, spam policy etc (Paquet, 2013).
Question 8
On reviewing the existing document of network design it was found that it was difficult to
foresee the requirements of the future, security, growth, efficiency, and capacity. Also, they
have squeezed many computers and another network device into a single logical network. SO
the current network design was incomplete and needs to be updated (Partsenidis, 2003).
Question 9
Technical requirements needed to be the internet connection, Diagnostic tools for network,
bandwidth, software for local caching, Firewalls, filters etc (Bird and Harwood, 2002).
Question 10
a)
For this, we have contacted vendors who sell modem, routers, bridges, hubs, switches,
gateways etc.
b)
The network elements needed for the networking purpose are as under:
S. No Element Specification
1. Modem BCM63168
2. Routers 802.11 a/b/g/n/ac
3. Bridges Quadro M32X
4. Hubs Cisco 1538 Series 10 100 Micro Hub
5. Switches Cisco Catalyst 2960S-24TS-L
6. Wireless Access Points Aironet 1815 Series
7. Gateways Cisco 2900
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Question 11
For installation, there requires a class installer and co-installer, INF files and notify objects.
a)
Identify the elements needed according to technical requirements of the network.
Priorities tasks that are needed & contingency plans so as to achieve the goal.
Identify the human requirement and retrieve the approval for the plans.
b)
No, there was no disruption to clients.
Question 12
a)
The approval was obtained from the CITC. The CITC hold the power of approving. They
approve the LAN usage rules.
b)
The security clearance will be required for the purpose of preventing the access of security
concerns so that they do not gain access to any sensitive assets of government, information,
location etc.
Question 13
a)
Dark Fiber
Metro Ethernet
Broadband
MPLS
Legacy T1 (Froehlich, 2017)
For installation, there requires a class installer and co-installer, INF files and notify objects.
a)
Identify the elements needed according to technical requirements of the network.
Priorities tasks that are needed & contingency plans so as to achieve the goal.
Identify the human requirement and retrieve the approval for the plans.
b)
No, there was no disruption to clients.
Question 12
a)
The approval was obtained from the CITC. The CITC hold the power of approving. They
approve the LAN usage rules.
b)
The security clearance will be required for the purpose of preventing the access of security
concerns so that they do not gain access to any sensitive assets of government, information,
location etc.
Question 13
a)
Dark Fiber
Metro Ethernet
Broadband
MPLS
Legacy T1 (Froehlich, 2017)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
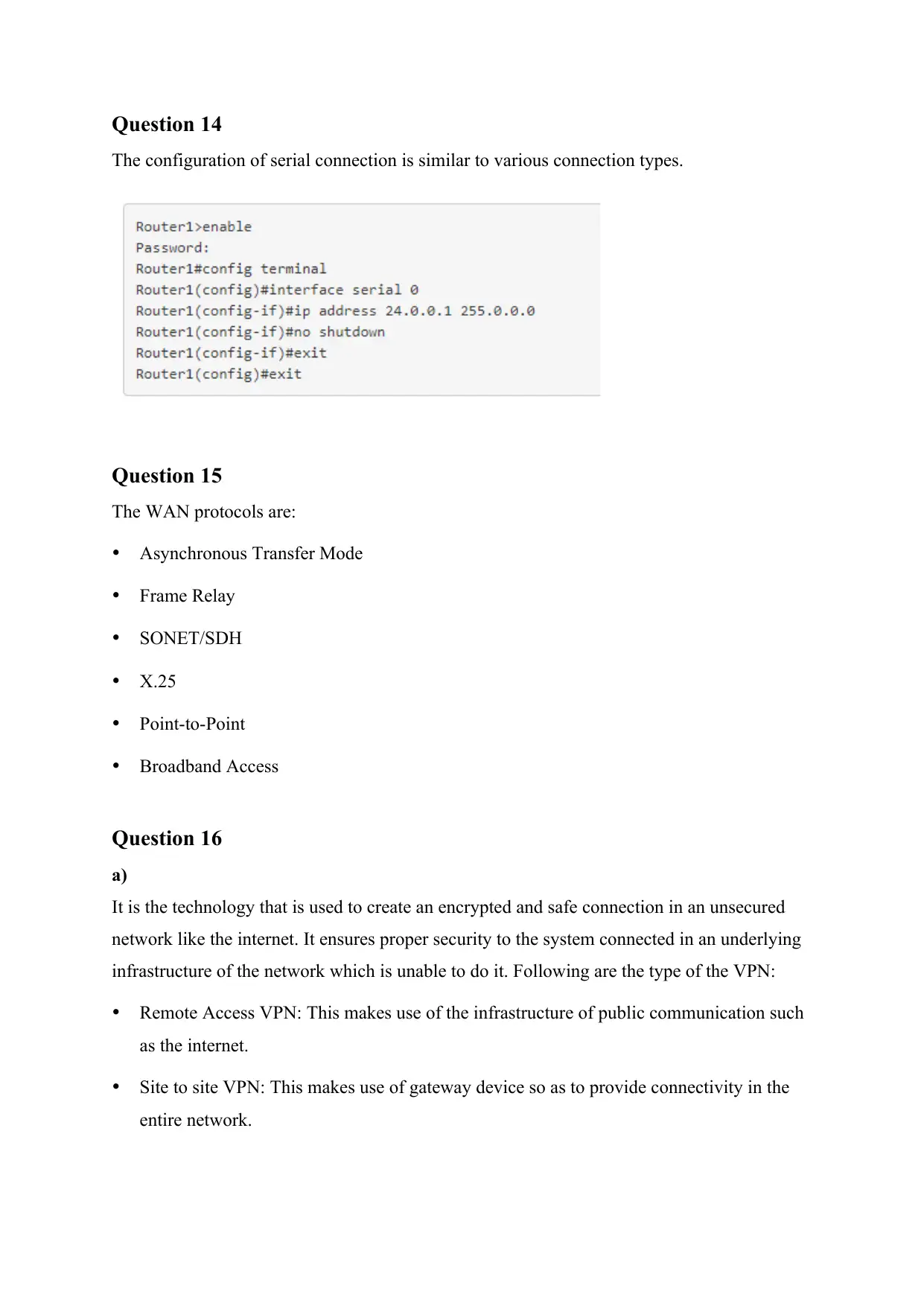
Question 14
The configuration of serial connection is similar to various connection types.
Question 15
The WAN protocols are:
Asynchronous Transfer Mode
Frame Relay
SONET/SDH
X.25
Point-to-Point
Broadband Access
Question 16
a)
It is the technology that is used to create an encrypted and safe connection in an unsecured
network like the internet. It ensures proper security to the system connected in an underlying
infrastructure of the network which is unable to do it. Following are the type of the VPN:
Remote Access VPN: This makes use of the infrastructure of public communication such
as the internet.
Site to site VPN: This makes use of gateway device so as to provide connectivity in the
entire network.
The configuration of serial connection is similar to various connection types.
Question 15
The WAN protocols are:
Asynchronous Transfer Mode
Frame Relay
SONET/SDH
X.25
Point-to-Point
Broadband Access
Question 16
a)
It is the technology that is used to create an encrypted and safe connection in an unsecured
network like the internet. It ensures proper security to the system connected in an underlying
infrastructure of the network which is unable to do it. Following are the type of the VPN:
Remote Access VPN: This makes use of the infrastructure of public communication such
as the internet.
Site to site VPN: This makes use of gateway device so as to provide connectivity in the
entire network.

Question 17
Configuration step of a site-to-site VPN.
Verify the connectivity through LAN.
Allow the IKE policies.
Configure policies of ISAKMP.
Arrange pre-shared keys.
Configure the transform set of IPsec.
Configure the interesting traffic.
Configure the crypto map.
Verify step of a site-to-site VPN.
Verify the configuration of the IPsec.
Show isakmp security.
Show IPsec security.
Produce some boring test traffic & detect the result.
Produce some exciting test traffic & detect the result (Bipin, 2015).
Question 18
Asymmetric digital subscriber line is the internet connection’s type. Nowadays it is used for
streaming multimedia, moderating game, downloading bulky files, and computer design. It
provides a facility that the users can easily use the internet when they are talking to someone
on phone call. It is also used for receiving the faxes and emails. It is the replacement of dial-
up modems. It is also available online. So there is no need of waiting for a connection
(Soffar, 2015).
Configuration step of a site-to-site VPN.
Verify the connectivity through LAN.
Allow the IKE policies.
Configure policies of ISAKMP.
Arrange pre-shared keys.
Configure the transform set of IPsec.
Configure the interesting traffic.
Configure the crypto map.
Verify step of a site-to-site VPN.
Verify the configuration of the IPsec.
Show isakmp security.
Show IPsec security.
Produce some boring test traffic & detect the result.
Produce some exciting test traffic & detect the result (Bipin, 2015).
Question 18
Asymmetric digital subscriber line is the internet connection’s type. Nowadays it is used for
streaming multimedia, moderating game, downloading bulky files, and computer design. It
provides a facility that the users can easily use the internet when they are talking to someone
on phone call. It is also used for receiving the faxes and emails. It is the replacement of dial-
up modems. It is also available online. So there is no need of waiting for a connection
(Soffar, 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



