ICTNWK509 - Design and Implement a Security Perimeter for ICT Networks
VerifiedAdded on 2024/05/17
|13
|3297
|232
AI Summary
This document explores the design and implementation of a security perimeter for ICT networks. It covers various security threats, available perimeter security options, and the design of a distributed network for a company called WehostCompany. The document also includes practical labs on configuring Network Policy Server (NPS), implementing Network Access Protection (NAP), deploying Direct Access, and implementing VPN. It provides detailed explanations and answers to questions related to each lab, offering insights into the practical aspects of securing ICT networks.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

ICTNWK509 - Design and implement a security perimeter
for ICT networks
for ICT networks
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
WRITTEN ACTIVITY...................................................................................................................2
OBSERVATION/DEMONSTRATION..........................................................................................4
1. Lab: Installing and Configuring a Network Policy Server......................................................4
2. Lab: Implementing Network Access Protection......................................................................6
3. Lab A: Implementing Direct Access by Using the Getting Started Wizard............................7
4. Lab B: Deploying an Advanced DirectAccess Solution..........................................................8
5. Lab C: Implementing VPN......................................................................................................9
References......................................................................................................................................10
1
WRITTEN ACTIVITY...................................................................................................................2
OBSERVATION/DEMONSTRATION..........................................................................................4
1. Lab: Installing and Configuring a Network Policy Server......................................................4
2. Lab: Implementing Network Access Protection......................................................................6
3. Lab A: Implementing Direct Access by Using the Getting Started Wizard............................7
4. Lab B: Deploying an Advanced DirectAccess Solution..........................................................8
5. Lab C: Implementing VPN......................................................................................................9
References......................................................................................................................................10
1

WRITTEN ACTIVITY
1. Determine the level and nature of the security threat
The nature of security threats are:
Unstructured threats: (Level- moderate) - The threats are created by the inexperienced
agents and the techniques can easily be found such as password crackers. This threat
occurs in order to steal the essential data which can increase the integrity of the
WehostCompany.
Structured threats: (Level- high) - The threats developed from highly motivated people
are dangerous and they are in context to the technicalcompetence. Those agents know
very well about the vulnerabilities which they use for the exploitation.
External threats: (Level- moderate) - Some threat agents from the outside the Wehost
Company affects the Wehost Company in several ways. They can use access to any part
or they can use dial-up access servers.
Internal threats: (Level- high) - Some threats are even caused by the staff members of
the organisation itself. It may have some motive or can happen accidentally due to some
human errors. Some examples are misuse of accounts and Wi-Fi passwords (Purser,
2016).
2. Identify security threat
There are several security threats that are associated with the firewall that used in the network
system. Some of the threats that have been researched for Wehost Company in context to the
firewall are:
a. Reconnaissance: This threat is related to the stealing of data by accessing the firewall
through unauthorized discovery and maps the system to get the access to several other
devices. Examples are port scans and ping sweeps.
b. Denial of service: This threat involves the disabling and corrupting the network and
replicating it so that it becomes easy to deny the services. The effect of such threats is
that the system network speed slows down or system gets crashed.
2
1. Determine the level and nature of the security threat
The nature of security threats are:
Unstructured threats: (Level- moderate) - The threats are created by the inexperienced
agents and the techniques can easily be found such as password crackers. This threat
occurs in order to steal the essential data which can increase the integrity of the
WehostCompany.
Structured threats: (Level- high) - The threats developed from highly motivated people
are dangerous and they are in context to the technicalcompetence. Those agents know
very well about the vulnerabilities which they use for the exploitation.
External threats: (Level- moderate) - Some threat agents from the outside the Wehost
Company affects the Wehost Company in several ways. They can use access to any part
or they can use dial-up access servers.
Internal threats: (Level- high) - Some threats are even caused by the staff members of
the organisation itself. It may have some motive or can happen accidentally due to some
human errors. Some examples are misuse of accounts and Wi-Fi passwords (Purser,
2016).
2. Identify security threat
There are several security threats that are associated with the firewall that used in the network
system. Some of the threats that have been researched for Wehost Company in context to the
firewall are:
a. Reconnaissance: This threat is related to the stealing of data by accessing the firewall
through unauthorized discovery and maps the system to get the access to several other
devices. Examples are port scans and ping sweeps.
b. Denial of service: This threat involves the disabling and corrupting the network and
replicating it so that it becomes easy to deny the services. The effect of such threats is
that the system network speed slows down or system gets crashed.
2

c. Malicious Software attacks: It gets inserted into the devices with the help of some
methods and this threat creates damage and corrupts the device. It also denies the access
to the device from the network. The access attacks can be in the form of password attack
and phishing.
d. Backend access: Agents gets the back-end access to the database to exploit the firewall
(Kilpatrick, 2008).
3. Research available perimeter security options
The security options for the protection of the firewall in Wehost Company include the following:
i. Validate the standard compliance: It is better to use the firewall that can determine
protocol standards used for the communication and restrict any threat. Any violation with
respect to these protocols will be an indication of the malicious traffic.
ii. Usage of validated protocols: With the increased use of protocol compliance, it must
undergo testing so that data under the protocol must be checked for expected usage.
iii. Limitation to application features: The data carried by some of the application may be
harmful and also violate the protocols of communication. This data can harm the devices
so such type of applications should be restricted from allowing the access.
iv. Control of operations in the application layer: Sometimes the application is also
responsible for the threats insertion in the network and can cause happening of hazardous
operations. So applications should be controlled during the network operations (Hogg,
2011).
4. Design Security perimeter to meet identified enterprise requirements
3
methods and this threat creates damage and corrupts the device. It also denies the access
to the device from the network. The access attacks can be in the form of password attack
and phishing.
d. Backend access: Agents gets the back-end access to the database to exploit the firewall
(Kilpatrick, 2008).
3. Research available perimeter security options
The security options for the protection of the firewall in Wehost Company include the following:
i. Validate the standard compliance: It is better to use the firewall that can determine
protocol standards used for the communication and restrict any threat. Any violation with
respect to these protocols will be an indication of the malicious traffic.
ii. Usage of validated protocols: With the increased use of protocol compliance, it must
undergo testing so that data under the protocol must be checked for expected usage.
iii. Limitation to application features: The data carried by some of the application may be
harmful and also violate the protocols of communication. This data can harm the devices
so such type of applications should be restricted from allowing the access.
iv. Control of operations in the application layer: Sometimes the application is also
responsible for the threats insertion in the network and can cause happening of hazardous
operations. So applications should be controlled during the network operations (Hogg,
2011).
4. Design Security perimeter to meet identified enterprise requirements
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
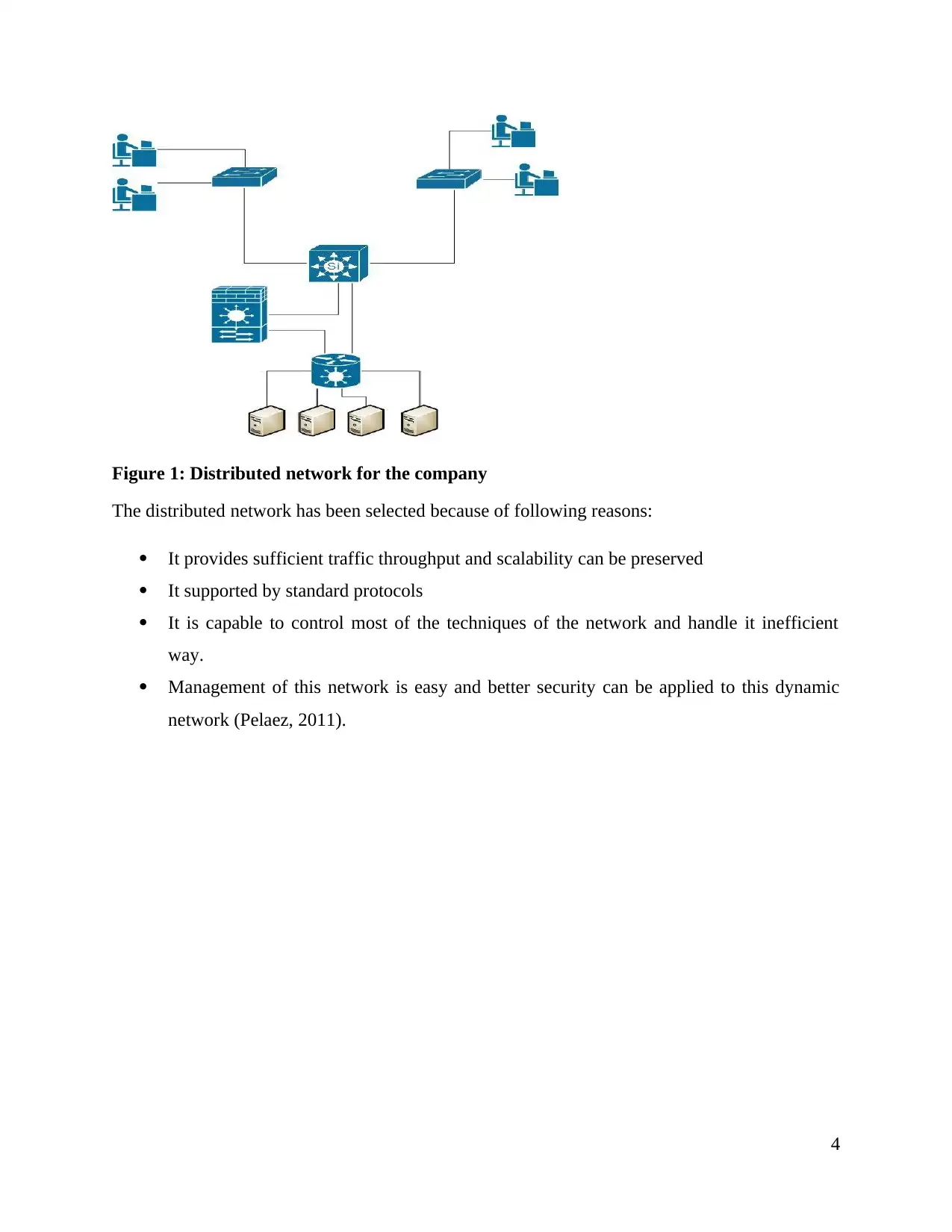
Figure 1: Distributed network for the company
The distributed network has been selected because of following reasons:
It provides sufficient traffic throughput and scalability can be preserved
It supported by standard protocols
It is capable to control most of the techniques of the network and handle it inefficient
way.
Management of this network is easy and better security can be applied to this dynamic
network (Pelaez, 2011).
4
The distributed network has been selected because of following reasons:
It provides sufficient traffic throughput and scalability can be preserved
It supported by standard protocols
It is capable to control most of the techniques of the network and handle it inefficient
way.
Management of this network is easy and better security can be applied to this dynamic
network (Pelaez, 2011).
4

OBSERVATION/DEMONSTRATION
1. Lab: Installing and Configuring a Network Policy Server
Question 1: What does a RADIUS proxy provide?
NPS is the Network Policy Server requires RADIUS proxy for its deployments. RADIUS stands
for Remote Authentication Dial-In User Service. It helps the NPD in getting the connection
requests from the clients of the RADIUS. After getting the access, RADIUS forwards the
requests to the server having NPS. NPS can perform several functions such as authentication,
authorization and so on with the help of RADIUS. This proxy needs to register in the active
directory of the user accounts. The communication of NPS with the RADIUS client is preceded
with the help of RADIUS protocols and the servers associated with this communication are
named as network access servers (Poggemeyer and McIllece, 2017).
Question 2: What is a RADIUS client, and what are some examples of RADIUS clients?
Radius Client is a device which is RADIUS-enabled used at the perimeter of the network. It
helps in enforcing the access control to the persons who are trying to access the network
resources. Client usually sends a request to the server that makes it forward to the network. There
are several examples of RADIUS client and they are VPN server, Wireless Access Point, Dial-in
modem and so on. When the request related to the authentication is sent, the client accepts it and
can also reject it according to the assigned authentication agent. The client has the IP address that
is being used to recognize it in the network system (RSA, 2017).
Question3: How can you make the most effective use of the NPS logging features?
The most effective use of NPS logging feature can be made in following way:
Loginto the account by authenticating the system and then apply appropriate changes to
the selections for the network
It must be ensured that the logging should be done in sufficient capacity so that logs can
be maintained
Data files should be regularly back up so that accidentally deleted files can be retrieved
Track the data usage and identify which department is accessing which data and this
helps in getting records from the system (Microsoft, 2012).
Question 4: What consideration must you follow if you choose to use a nonstandard port
assignment for RADIUS traffic?
The following consideration must be followed while using RADIUS:
5
1. Lab: Installing and Configuring a Network Policy Server
Question 1: What does a RADIUS proxy provide?
NPS is the Network Policy Server requires RADIUS proxy for its deployments. RADIUS stands
for Remote Authentication Dial-In User Service. It helps the NPD in getting the connection
requests from the clients of the RADIUS. After getting the access, RADIUS forwards the
requests to the server having NPS. NPS can perform several functions such as authentication,
authorization and so on with the help of RADIUS. This proxy needs to register in the active
directory of the user accounts. The communication of NPS with the RADIUS client is preceded
with the help of RADIUS protocols and the servers associated with this communication are
named as network access servers (Poggemeyer and McIllece, 2017).
Question 2: What is a RADIUS client, and what are some examples of RADIUS clients?
Radius Client is a device which is RADIUS-enabled used at the perimeter of the network. It
helps in enforcing the access control to the persons who are trying to access the network
resources. Client usually sends a request to the server that makes it forward to the network. There
are several examples of RADIUS client and they are VPN server, Wireless Access Point, Dial-in
modem and so on. When the request related to the authentication is sent, the client accepts it and
can also reject it according to the assigned authentication agent. The client has the IP address that
is being used to recognize it in the network system (RSA, 2017).
Question3: How can you make the most effective use of the NPS logging features?
The most effective use of NPS logging feature can be made in following way:
Loginto the account by authenticating the system and then apply appropriate changes to
the selections for the network
It must be ensured that the logging should be done in sufficient capacity so that logs can
be maintained
Data files should be regularly back up so that accidentally deleted files can be retrieved
Track the data usage and identify which department is accessing which data and this
helps in getting records from the system (Microsoft, 2012).
Question 4: What consideration must you follow if you choose to use a nonstandard port
assignment for RADIUS traffic?
The following consideration must be followed while using RADIUS:
5

Proper encryption passwords should be applied so that communication can be secured and
standard configurations can be installed
Usernames must be encrypted and this enables encryption of the request. This makes the
information secure with respect to the destination address
Generation of warning during any violation of the standard protocol with respect to the proxy
servers (Causer, 2015).
6
standard configurations can be installed
Usernames must be encrypted and this enables encryption of the request. This makes the
information secure with respect to the destination address
Generation of warning during any violation of the standard protocol with respect to the proxy
servers (Causer, 2015).
6
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2. Lab: Implementing Network Access Protection
Question1: The DHCP NAP enforcement method is the weakest enforcement method in
Windows Server 2012. Why is it a less preferable enforcement method than other available
methods?
DHCP or Dynamic Host Configuration Protocol is used for configuring the IP network in
automatic manner. It eliminates the intervention of human and apply checks to the computers so
that they cannot have same IP address. It is weakest enforcement technique in Windows Server
2012 due to some of the reasons and the reasons are:
There is some serious risk issue when server is installed. This makes the violation of data
which will affect the privacy of the user and security of the network
During the case of single DHCP server, the connected computer fails with the failure of
the server and if the computer don’t have IP address then they will surely lost the
connection
For the case of multiple sub-networks, the single DHCP server is insufficient to manage.
This can be done by fulfilling additional requirement as each segment requires its own
server which increases the cost and makes the network complex (Laverty, 2015).
Question 2: Could you use the remote access NAP solution alongside the IPsec NAP solution?
What benefit would this scenario provide?
There are several benefits that have been found when the remote access NAP solution in addition
to the IPsec NAP solution. The benefits are:
It helps in making the device mobile so that the staff members use the network
efficiently and helps in managing the personal computers
The major benefit for having this is to provide IP address and Protocol port number to
establish a better connection
It can be automatic which provides necessary updates when required so that a computer
can become a complaint (Craig, 2016).
Question 3: Could you have used DHCP NAP enforcement for the client? Why or why not?
NAP or Network Access Protection provides services to validate the associated clients. As the
client starts accessing the service installed at the NAP server, the status is checked by the NAP
service agent. DHCP is the services that have well integrated server and specific and distinct IP
address to each device. This is weakest enforcement method so I will not use this method for the
enforcement. It is associated to several security issues which occur during the installation of the
server in the NAP. This protocol makes the server to get easily bypassed and client is avoided
with the use of dynamic IP address configuration (Sarabadani, 2011).
7
Question1: The DHCP NAP enforcement method is the weakest enforcement method in
Windows Server 2012. Why is it a less preferable enforcement method than other available
methods?
DHCP or Dynamic Host Configuration Protocol is used for configuring the IP network in
automatic manner. It eliminates the intervention of human and apply checks to the computers so
that they cannot have same IP address. It is weakest enforcement technique in Windows Server
2012 due to some of the reasons and the reasons are:
There is some serious risk issue when server is installed. This makes the violation of data
which will affect the privacy of the user and security of the network
During the case of single DHCP server, the connected computer fails with the failure of
the server and if the computer don’t have IP address then they will surely lost the
connection
For the case of multiple sub-networks, the single DHCP server is insufficient to manage.
This can be done by fulfilling additional requirement as each segment requires its own
server which increases the cost and makes the network complex (Laverty, 2015).
Question 2: Could you use the remote access NAP solution alongside the IPsec NAP solution?
What benefit would this scenario provide?
There are several benefits that have been found when the remote access NAP solution in addition
to the IPsec NAP solution. The benefits are:
It helps in making the device mobile so that the staff members use the network
efficiently and helps in managing the personal computers
The major benefit for having this is to provide IP address and Protocol port number to
establish a better connection
It can be automatic which provides necessary updates when required so that a computer
can become a complaint (Craig, 2016).
Question 3: Could you have used DHCP NAP enforcement for the client? Why or why not?
NAP or Network Access Protection provides services to validate the associated clients. As the
client starts accessing the service installed at the NAP server, the status is checked by the NAP
service agent. DHCP is the services that have well integrated server and specific and distinct IP
address to each device. This is weakest enforcement method so I will not use this method for the
enforcement. It is associated to several security issues which occur during the installation of the
server in the NAP. This protocol makes the server to get easily bypassed and client is avoided
with the use of dynamic IP address configuration (Sarabadani, 2011).
7

3. Lab A: Implementing Direct Access by Using the Getting Started Wizard
Question 1: Why did you create the DA_Clients group?
The need of creating the DA Client is to configure the windows server and client to provide a
complex integration. It simplifies the process which handles the background operations of the
networking system. It also enables the enabling of alternate solution for the configuration of the
networking system. Step by step instructions were created to introduce the reliable system which
includes the error-free system. The error free system can be configured by identifying the root
causes. Extensive servers are installed with the direct access and client groups are created for
better network environment with the help of virtual private network (Fullmer, 2014).
Question 2: How will you configure IPv6 addresses for client computers running the
Windows® 8 operating system to use DirectAccess?
Configuration of the direct access helps in facilitating the operation of implementation so that
password expiration can be restricted and policy can be changed. The VPN connection can be
eliminated with the elimination of the need of the end user. There are several steps that can be
used for the configuration IPv6 address for client computers and the steps are:
1. Initially create the virtual machine for the windows server
2. External DNS record should be set up
3. Firewall should be configured for DA
4. Prepare and install the certificate for DA server
5. Active directory should be created for security group
6. Verify the windows client OS
7. Now install and configure DA (Chukwudozi, 2016).
8
Question 1: Why did you create the DA_Clients group?
The need of creating the DA Client is to configure the windows server and client to provide a
complex integration. It simplifies the process which handles the background operations of the
networking system. It also enables the enabling of alternate solution for the configuration of the
networking system. Step by step instructions were created to introduce the reliable system which
includes the error-free system. The error free system can be configured by identifying the root
causes. Extensive servers are installed with the direct access and client groups are created for
better network environment with the help of virtual private network (Fullmer, 2014).
Question 2: How will you configure IPv6 addresses for client computers running the
Windows® 8 operating system to use DirectAccess?
Configuration of the direct access helps in facilitating the operation of implementation so that
password expiration can be restricted and policy can be changed. The VPN connection can be
eliminated with the elimination of the need of the end user. There are several steps that can be
used for the configuration IPv6 address for client computers and the steps are:
1. Initially create the virtual machine for the windows server
2. External DNS record should be set up
3. Firewall should be configured for DA
4. Prepare and install the certificate for DA server
5. Active directory should be created for security group
6. Verify the windows client OS
7. Now install and configure DA (Chukwudozi, 2016).
8

4. Lab B: Deploying an Advanced Direct Access Solution
Question 1: Why did you make the CRL available on the edge server?
Edge server is used as it helps in granting access to users for the network. The users are of
several types such as mobile, remote, federated and so on. With this, users at the external side
are able to send and receive network request. It act as intermediary IP which translates the
external IP address into internal address so that a better communication can be set up for user
connections. It needs the routable Public IPs for assigning the server to the system. Edge server
is enough in handling various users as it has ability to develop and deploy different topologies. It
provides remainder when any mobile user initiates to access it (Williams, 2017).
Question 2: Why did you install a certificate on the client computer?
Installation of certificate is necessary step in order to provide better authentication to the client
computers. It is better to decide which certificate based authentication is better for the current
networking system. There are several benefits for installation of the certificate which are
described below:
There is less requirement of involvement of end users because certificate installation can
provide the security related to the authentication of the devices. Less training is required
for the maintenance.
There is no extra requirement of the hardware and provides several solutions such as one
time password and biometrics. With this, back-up plan is not required for the forgotten
tokens
The management of the certificate solutions is easy for the authentication. The platform
becomes easy to configure for administrators. Support should be provided for the internal
resources and provides easy scalability for the business growth
Organisation should support the standard certificates trusted by large enterprise and they
require minimal configuration. Two factor authentications are enabled to support the
remote workforce (Olenski, 2014).
9
Question 1: Why did you make the CRL available on the edge server?
Edge server is used as it helps in granting access to users for the network. The users are of
several types such as mobile, remote, federated and so on. With this, users at the external side
are able to send and receive network request. It act as intermediary IP which translates the
external IP address into internal address so that a better communication can be set up for user
connections. It needs the routable Public IPs for assigning the server to the system. Edge server
is enough in handling various users as it has ability to develop and deploy different topologies. It
provides remainder when any mobile user initiates to access it (Williams, 2017).
Question 2: Why did you install a certificate on the client computer?
Installation of certificate is necessary step in order to provide better authentication to the client
computers. It is better to decide which certificate based authentication is better for the current
networking system. There are several benefits for installation of the certificate which are
described below:
There is less requirement of involvement of end users because certificate installation can
provide the security related to the authentication of the devices. Less training is required
for the maintenance.
There is no extra requirement of the hardware and provides several solutions such as one
time password and biometrics. With this, back-up plan is not required for the forgotten
tokens
The management of the certificate solutions is easy for the authentication. The platform
becomes easy to configure for administrators. Support should be provided for the internal
resources and provides easy scalability for the business growth
Organisation should support the standard certificates trusted by large enterprise and they
require minimal configuration. Two factor authentications are enabled to support the
remote workforce (Olenski, 2014).
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5. Lab C: Implementing VPN
Question 1: In the lab, you configured the VPN server to allocate an IP address configuration by
using a static pool of addresses. Is there a way to automate IP configuration?
IP configuration can be automated by configuring the DHHCP that can automatically assign with
IP address even in case of unavailability of the server. This can happen when the server is down
for some-time and maintenance is required always for proper automation. It becomes important
to back-up the registry before any modifications are done. The automatic IP addressing should be
provided so that there will be less conflict between various routers. When the network adapter
gets its IP address, computer system uses other IP address for the communication with other
systems. It also includes the connection with the LAN network. The address range should be set
up with subnet mask. In some of the systems, there may be private IP addressing having default
conditions. Restart the system to see the applied changes on the devices (Support.microsoft,
2017).
Question2: Why was DirectAccess not working when we removed LON-CL1 from the
Adatum.com domain?
When LON-CL1 is removed from the domain, DA is not working properly due to many reasons.
The working is stopped due to the following reasons:
Unable to restore missing configuration
Failure of the configuration
Unable of making connection with the client groups
Connection failure due to limited internet access
Change in default settings of the configuration
Modification of IP address of existing devices
Insufficient security at the firewalls (McIllece and Poggemeyer, 2017).
10
Question 1: In the lab, you configured the VPN server to allocate an IP address configuration by
using a static pool of addresses. Is there a way to automate IP configuration?
IP configuration can be automated by configuring the DHHCP that can automatically assign with
IP address even in case of unavailability of the server. This can happen when the server is down
for some-time and maintenance is required always for proper automation. It becomes important
to back-up the registry before any modifications are done. The automatic IP addressing should be
provided so that there will be less conflict between various routers. When the network adapter
gets its IP address, computer system uses other IP address for the communication with other
systems. It also includes the connection with the LAN network. The address range should be set
up with subnet mask. In some of the systems, there may be private IP addressing having default
conditions. Restart the system to see the applied changes on the devices (Support.microsoft,
2017).
Question2: Why was DirectAccess not working when we removed LON-CL1 from the
Adatum.com domain?
When LON-CL1 is removed from the domain, DA is not working properly due to many reasons.
The working is stopped due to the following reasons:
Unable to restore missing configuration
Failure of the configuration
Unable of making connection with the client groups
Connection failure due to limited internet access
Change in default settings of the configuration
Modification of IP address of existing devices
Insufficient security at the firewalls (McIllece and Poggemeyer, 2017).
10

References
Causer, C. (2015). Linux and eduroam: RADIUS. [online] Network Development Team.
Available at: https://blogs.it.ox.ac.uk/networks/2015/02/16/linux-and-eduroam-radius/
[Accessed 7 Mar. 2018].
Chukwudozi, C. (2016). My Step-by-Step DirectAccess Configuration on Windows Server
2012 R2. [online] ChinnyChukwudozie. Available at:
https://chinnychukwudozie.com/2016/08/22/my-step-by-step-directaccess-configuration-on-
windows-server-2012-r2/ [Accessed 7 Mar. 2018].
Craig, M. (2016). Module 8: Configuring Network Access Protection. [online] Slideplayer.
Available at: http://slideplayer.com/slide/7645966/ [Accessed 7 Mar. 2018].
Fullmer, S. (2014). Correcting Direct Access Configuration Errors. [online] Interface
Technical Training. Available at: https://www.interfacett.com/blogs/correcting-direct-access-
configuration-errors/ [Accessed 7 Mar. 2018].
Hogg, S. (2011). Firewall Administration Techniques and Tools. [online] Network World.
Available at: https://www.networkworld.com/article/2220307/cisco-subnet/cisco-subnet-
firewall-administration-techniques-and-tools.html [Accessed 7 Mar. 2018].
Kilpatrick, I. (2008). What Firewall Do And What Firewalls Don't Do. [online] IT Pro Portal.
Available at: https://www.itproportal.com/2008/03/26/what-firewall-do-and-what-firewalls-
dont-do/ [Accessed 7 Mar. 2018].
Laverty, S. (2015). The Disadvantages of DHCP. [online] Techwalla. Available at:
https://www.techwalla.com/articles/the-disadvantages-of-dhcp [Accessed 7 Mar. 2018].
McIllece, J. and Poggemeyer, L. (2017). Troubleshooting DirectAccess. [online]
Docs.microsoft. Available at:
https://docs.microsoft.com/en-us/windows-server/remote/remote-access/directaccess/
troubleshooting-directaccess [Accessed 7 Mar. 2018].
Microsoft. (2012). Best Practices for NPS. [online] Available at:
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-
R2-and-2008/cc771746(v=ws.10) [Accessed 7 Mar. 2018].
Olenski, J. (2014). 4 Benefits of Certificate-Based Authentication. [online] Globalsign.
Available at: https://www.globalsign.com/en/blog/4-benefits-of-certificate-based-
authentication/ [Accessed 7 Mar. 2018].
Pelaez, M. (2011). Network Security Perimeter: How to choose the correct firewall and IPS
for your environment?. [online] SANS Internet Storm Center. Available at:
https://isc.sans.edu/diary/Network+Security+Perimeter:
+How+to+choose+the+correct+firewall+and+IPS+for+your+environment?/9901 [Accessed
7 Mar. 2018].
Poggemeyer, L. and McIllece, J. (2017). Plan NPS as a RADIUS proxy. [online] Microsoft.
Available at: https://docs.microsoft.com/en-us/windows-server/networking/technologies/
nps/nps-plan-proxy [Accessed 7 Mar. 2018].
Purser, L. (2016). Chapter One Modern Network Security Threats. [online] Slideplayer.
Available at: http://slideplayer.com/slide/4146490/ [Accessed 7 Mar. 2018].
RSA (2017). RADIUS Clients. [online] Community. Available at:
https://community.rsa.com/docs/DOC-77224 [Accessed 7 Mar. 2018].
11
Causer, C. (2015). Linux and eduroam: RADIUS. [online] Network Development Team.
Available at: https://blogs.it.ox.ac.uk/networks/2015/02/16/linux-and-eduroam-radius/
[Accessed 7 Mar. 2018].
Chukwudozi, C. (2016). My Step-by-Step DirectAccess Configuration on Windows Server
2012 R2. [online] ChinnyChukwudozie. Available at:
https://chinnychukwudozie.com/2016/08/22/my-step-by-step-directaccess-configuration-on-
windows-server-2012-r2/ [Accessed 7 Mar. 2018].
Craig, M. (2016). Module 8: Configuring Network Access Protection. [online] Slideplayer.
Available at: http://slideplayer.com/slide/7645966/ [Accessed 7 Mar. 2018].
Fullmer, S. (2014). Correcting Direct Access Configuration Errors. [online] Interface
Technical Training. Available at: https://www.interfacett.com/blogs/correcting-direct-access-
configuration-errors/ [Accessed 7 Mar. 2018].
Hogg, S. (2011). Firewall Administration Techniques and Tools. [online] Network World.
Available at: https://www.networkworld.com/article/2220307/cisco-subnet/cisco-subnet-
firewall-administration-techniques-and-tools.html [Accessed 7 Mar. 2018].
Kilpatrick, I. (2008). What Firewall Do And What Firewalls Don't Do. [online] IT Pro Portal.
Available at: https://www.itproportal.com/2008/03/26/what-firewall-do-and-what-firewalls-
dont-do/ [Accessed 7 Mar. 2018].
Laverty, S. (2015). The Disadvantages of DHCP. [online] Techwalla. Available at:
https://www.techwalla.com/articles/the-disadvantages-of-dhcp [Accessed 7 Mar. 2018].
McIllece, J. and Poggemeyer, L. (2017). Troubleshooting DirectAccess. [online]
Docs.microsoft. Available at:
https://docs.microsoft.com/en-us/windows-server/remote/remote-access/directaccess/
troubleshooting-directaccess [Accessed 7 Mar. 2018].
Microsoft. (2012). Best Practices for NPS. [online] Available at:
https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-
R2-and-2008/cc771746(v=ws.10) [Accessed 7 Mar. 2018].
Olenski, J. (2014). 4 Benefits of Certificate-Based Authentication. [online] Globalsign.
Available at: https://www.globalsign.com/en/blog/4-benefits-of-certificate-based-
authentication/ [Accessed 7 Mar. 2018].
Pelaez, M. (2011). Network Security Perimeter: How to choose the correct firewall and IPS
for your environment?. [online] SANS Internet Storm Center. Available at:
https://isc.sans.edu/diary/Network+Security+Perimeter:
+How+to+choose+the+correct+firewall+and+IPS+for+your+environment?/9901 [Accessed
7 Mar. 2018].
Poggemeyer, L. and McIllece, J. (2017). Plan NPS as a RADIUS proxy. [online] Microsoft.
Available at: https://docs.microsoft.com/en-us/windows-server/networking/technologies/
nps/nps-plan-proxy [Accessed 7 Mar. 2018].
Purser, L. (2016). Chapter One Modern Network Security Threats. [online] Slideplayer.
Available at: http://slideplayer.com/slide/4146490/ [Accessed 7 Mar. 2018].
RSA (2017). RADIUS Clients. [online] Community. Available at:
https://community.rsa.com/docs/DOC-77224 [Accessed 7 Mar. 2018].
11

Sarabadani, E. (2011). Network Access Protection with DHCP Step-By-Step Guide. [online]
An Illusion Called Security. Available at:
http://blog.windowsserversecurity.com/2011/04/18/network-access-protection-with-dhcp-
step-by-step-guide/ [Accessed 7 Mar. 2018].
Support.microsoft. (2017). How to use automatic TCP/IP addressing without a DHCP server.
[online] Available at: https://support.microsoft.com/en-in/help/220874/how-to-use-
automatic-tcp-ip-addressing-without-a-dhcp-server [Accessed 7 Mar. 2018].
Williams, C. (2017). How the Edge Server Fits into Skype for Business. [online] The Skype
for Business Insider. Available at: http://skype4businessinsider.com/reference/edge-server-
fits-skype-business/ [Accessed 7 Mar. 2018].
12
An Illusion Called Security. Available at:
http://blog.windowsserversecurity.com/2011/04/18/network-access-protection-with-dhcp-
step-by-step-guide/ [Accessed 7 Mar. 2018].
Support.microsoft. (2017). How to use automatic TCP/IP addressing without a DHCP server.
[online] Available at: https://support.microsoft.com/en-in/help/220874/how-to-use-
automatic-tcp-ip-addressing-without-a-dhcp-server [Accessed 7 Mar. 2018].
Williams, C. (2017). How the Edge Server Fits into Skype for Business. [online] The Skype
for Business Insider. Available at: http://skype4businessinsider.com/reference/edge-server-
fits-skype-business/ [Accessed 7 Mar. 2018].
12
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





