QAC040X351YB - Social Engineering and Identity Theft Analysis
VerifiedAdded on 2023/06/18
|23
|8967
|161
Project
AI Summary
This project investigates identity theft using social engineering, covering its impact on socialization and society. It identifies social engineering as a form of cybercrime, examines the consequences of identity theft on students, and analyzes the effects of cyber thefts on businesses and the economy. The project also explores solutions to cybercrime and their implementation in real-world scenarios. It includes a detailed literature review, requirements analysis, design considerations, implementation and testing phases, results, and a conclusion. The research aims to raise awareness about cyber threats and provide insights into prevention and recovery strategies, addressing ethical, legal, and social aspects of identity theft.

Identity theft using
social engineering
social engineering
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Project Proposal...............................................................................................................................1
Project Objectives...................................................................................................................1
Aim................................................................................................................................1
Objectives......................................................................................................................1
Background...................................................................................................................1
Scope.............................................................................................................................2
Proposed Approach................................................................................................................2
Ways of achieving the objectives..................................................................................2
Additional needs...........................................................................................................3
Professional issues........................................................................................................3
Ethical, legal or social aspects......................................................................................4
Preliminary Plan.....................................................................................................................4
Identifying the sequence of steps..................................................................................4
Expectation of the project to be finished......................................................................4
Major computing project report.......................................................................................................5
Chapter 1: Introduction...........................................................................................................5
Research background....................................................................................................5
Summary.......................................................................................................................6
Chapter 2: Literature review...................................................................................................7
Concept of social engineering and its effect on society................................................7
Identity theft and its consequences on the students......................................................8
Issues of cyber thefts and its impact on businesses and economy..............................10
Solutions of cybercrime and implementing it in real world situations.......................12
Chapter 3: Requirements and analysis.................................................................................13
Chapter 4: Design.................................................................................................................14
Chapter 5: Implementation and testing.................................................................................15
Project Proposal...............................................................................................................................1
Project Objectives...................................................................................................................1
Aim................................................................................................................................1
Objectives......................................................................................................................1
Background...................................................................................................................1
Scope.............................................................................................................................2
Proposed Approach................................................................................................................2
Ways of achieving the objectives..................................................................................2
Additional needs...........................................................................................................3
Professional issues........................................................................................................3
Ethical, legal or social aspects......................................................................................4
Preliminary Plan.....................................................................................................................4
Identifying the sequence of steps..................................................................................4
Expectation of the project to be finished......................................................................4
Major computing project report.......................................................................................................5
Chapter 1: Introduction...........................................................................................................5
Research background....................................................................................................5
Summary.......................................................................................................................6
Chapter 2: Literature review...................................................................................................7
Concept of social engineering and its effect on society................................................7
Identity theft and its consequences on the students......................................................8
Issues of cyber thefts and its impact on businesses and economy..............................10
Solutions of cybercrime and implementing it in real world situations.......................12
Chapter 3: Requirements and analysis.................................................................................13
Chapter 4: Design.................................................................................................................14
Chapter 5: Implementation and testing.................................................................................15

Chapter 6: Results and discussion........................................................................................16
Findings.......................................................................................................................16
Goals achieved............................................................................................................17
Further work................................................................................................................18
Chapter 7: Conclusion..........................................................................................................18
References:.....................................................................................................................................19
Findings.......................................................................................................................16
Goals achieved............................................................................................................17
Further work................................................................................................................18
Chapter 7: Conclusion..........................................................................................................18
References:.....................................................................................................................................19
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Project Proposal
Project Objectives
Aim
To investigate the identity theft using social engineering and its direct impact on socialization.
Objectives
To identify the concept of social engineering as a part of cybercrime and its effect on
society
To determine the identity theft as a part of cyber theft and its consequences on the
students
To examine the issues related to the cyber thefts and its impact on businesses and
economy
To investigate the solutions regarding cybercrime and the way of implementing in real
world situations
Background
Cyber crime can be defined as the crime which includes the computer systems and
networks along with the internet. In such a crime, either computer is uses as a source of crime or
even can be the target of crime. It highly impacts negatively on the private security of someone
or can also affect the financial stability in a drastic manner. It is also called computer crime
which results in illegal nature of the situation such as commuting fraud and trafficking on child
pornography along with the intellectual property and stealing identities and also the violating the
privacy. Types of cyber thefts includes the phishing scams, website spoofing, ransomware,
malware, internet of things hacking, social engineering, virus attacks and many more types of
cyber attacks are faced by the innocent people and businesses as well (Abass, 2018). Research is
conducted on the specific topic of social engineering which involves particularly identity theft.
The following investigation is performed on the identification of the concept of social
engineering as a part of cybercrime and its effect on society and determining the identity theft as
a part of cyber theft and its consequences on the students along with the examination of the
1
Project Objectives
Aim
To investigate the identity theft using social engineering and its direct impact on socialization.
Objectives
To identify the concept of social engineering as a part of cybercrime and its effect on
society
To determine the identity theft as a part of cyber theft and its consequences on the
students
To examine the issues related to the cyber thefts and its impact on businesses and
economy
To investigate the solutions regarding cybercrime and the way of implementing in real
world situations
Background
Cyber crime can be defined as the crime which includes the computer systems and
networks along with the internet. In such a crime, either computer is uses as a source of crime or
even can be the target of crime. It highly impacts negatively on the private security of someone
or can also affect the financial stability in a drastic manner. It is also called computer crime
which results in illegal nature of the situation such as commuting fraud and trafficking on child
pornography along with the intellectual property and stealing identities and also the violating the
privacy. Types of cyber thefts includes the phishing scams, website spoofing, ransomware,
malware, internet of things hacking, social engineering, virus attacks and many more types of
cyber attacks are faced by the innocent people and businesses as well (Abass, 2018). Research is
conducted on the specific topic of social engineering which involves particularly identity theft.
The following investigation is performed on the identification of the concept of social
engineering as a part of cybercrime and its effect on society and determining the identity theft as
a part of cyber theft and its consequences on the students along with the examination of the
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

issues related to the cyber thefts and its impact on businesses and economy and investigation on
the solutions regarding cybercrime and the way of implementing in real world situations (Conteh
and Schmick, 2021).
Scope
Scope of the research on identity theft using social engineering is such that it is the type
of cyber crime and it is necessary for each and every individual to get aware and gain the
knowledge about the prevention of such cyber thefts before being the victim of any cyber attacks
and major loss (Patel, 2020). Therefore, the in depth research is highly required in order to learn
the concept of identity theft using social engineering so that its impacts can be studied and their
forms as well so that it can be known that which form can be more disastrous and how can it be
prevented. Moreover, research also tells the solution after being the victim of cyber crime so that
recovery can be possible in a quick manner before any drastic happening of the incident.
Furthermore, due to greediness, people shares their private information so that they can get more
money without knowing about the sources and faces their major loss of money due to their
greedy nature. Therefore, in order to create awareness about cyber crime and social engineering
specially the identity theft, conducting research is important (Aldawood and Skinner, 2018).
Proposed Approach
Ways of achieving the objectives
There are ways in which the objectives made can be attained in an effective manner so
that the efficiency can be proved while conducting the research. First objective is to identify the
concept of social engineering as a part of cybercrime and its effect on society can be achieved by
briefly explaining the nature of social engineering and why is it relevant to study on the basis of
society along with the effects. Second objective is to determine the identity theft as a part of
cyber theft and its consequences on the students can be achieved by briefly explaining the nature
of identity theft and why is it relevant to study on the basis of students along with the
consequences. Third objective is to examine the issues related to the cyber thefts and its impact
on businesses and economy can be achieved by briefly explaining the nature of issues related to
the cyber thefts and why is it relevant to study on the basis of businesses and economy along
with its impact. Fourth objective is to investigate the solutions regarding cybercrime and the way
2
the solutions regarding cybercrime and the way of implementing in real world situations (Conteh
and Schmick, 2021).
Scope
Scope of the research on identity theft using social engineering is such that it is the type
of cyber crime and it is necessary for each and every individual to get aware and gain the
knowledge about the prevention of such cyber thefts before being the victim of any cyber attacks
and major loss (Patel, 2020). Therefore, the in depth research is highly required in order to learn
the concept of identity theft using social engineering so that its impacts can be studied and their
forms as well so that it can be known that which form can be more disastrous and how can it be
prevented. Moreover, research also tells the solution after being the victim of cyber crime so that
recovery can be possible in a quick manner before any drastic happening of the incident.
Furthermore, due to greediness, people shares their private information so that they can get more
money without knowing about the sources and faces their major loss of money due to their
greedy nature. Therefore, in order to create awareness about cyber crime and social engineering
specially the identity theft, conducting research is important (Aldawood and Skinner, 2018).
Proposed Approach
Ways of achieving the objectives
There are ways in which the objectives made can be attained in an effective manner so
that the efficiency can be proved while conducting the research. First objective is to identify the
concept of social engineering as a part of cybercrime and its effect on society can be achieved by
briefly explaining the nature of social engineering and why is it relevant to study on the basis of
society along with the effects. Second objective is to determine the identity theft as a part of
cyber theft and its consequences on the students can be achieved by briefly explaining the nature
of identity theft and why is it relevant to study on the basis of students along with the
consequences. Third objective is to examine the issues related to the cyber thefts and its impact
on businesses and economy can be achieved by briefly explaining the nature of issues related to
the cyber thefts and why is it relevant to study on the basis of businesses and economy along
with its impact. Fourth objective is to investigate the solutions regarding cybercrime and the way
2

of implementing in real world situations can be achieved by briefly explaining the nature of
solutions regarding cyber crime and why is it relevant to study on the basis of its implementation
in real time circumstances (Bansla, Kunwar and Gupta, 2019).
Additional needs
The research report on identity thefts using social engineering requires basic resources
such as to develop the report, it is important to have the in depth knowledge about the computing
and its associated technologies so that the safety and security needs can be identifies easily in an
in depth manner. Proper data and information is required having the facts of cyber crime and its
various types written by reliable and relevant authors so that it can be justify with an appropriate
evidence. Moreover, data from books and journals along with the internet sources are highly
required because the factual information can be attained with such sources of information.
Furthermore, the additional needs are the suitable aspects of the research area because anything
written cannot look vague but appears qualitative and qualitative along with the research
methods used and literature review along with the recommendation.
Professional issues
Professional issues regarding the identity thefts using social engineering are such that
organization who uses technology on large basis with excellent level and operate it by providing
the services of investments or credit card services and many more have a higher risk of social
engineering because many hackers in the name of such organizations contacts the customers and
extracts the private information of their credit and debit cards along with the personal
identification also and steals the money from them, customers ultimately blames the
organizations for stealing the money and demands for recovery. This is the professional issues
for such organizations because any how they have to tackle such cyber crimes with their
customer in the name of their own. They needs to investigate about it and finds out the culprit so
that next time it won't happen again, this whole situation takes a lot of expenses of the
organization, thereby, they are considered as the professional issues (Conteh and Staton, 2021).
3
solutions regarding cyber crime and why is it relevant to study on the basis of its implementation
in real time circumstances (Bansla, Kunwar and Gupta, 2019).
Additional needs
The research report on identity thefts using social engineering requires basic resources
such as to develop the report, it is important to have the in depth knowledge about the computing
and its associated technologies so that the safety and security needs can be identifies easily in an
in depth manner. Proper data and information is required having the facts of cyber crime and its
various types written by reliable and relevant authors so that it can be justify with an appropriate
evidence. Moreover, data from books and journals along with the internet sources are highly
required because the factual information can be attained with such sources of information.
Furthermore, the additional needs are the suitable aspects of the research area because anything
written cannot look vague but appears qualitative and qualitative along with the research
methods used and literature review along with the recommendation.
Professional issues
Professional issues regarding the identity thefts using social engineering are such that
organization who uses technology on large basis with excellent level and operate it by providing
the services of investments or credit card services and many more have a higher risk of social
engineering because many hackers in the name of such organizations contacts the customers and
extracts the private information of their credit and debit cards along with the personal
identification also and steals the money from them, customers ultimately blames the
organizations for stealing the money and demands for recovery. This is the professional issues
for such organizations because any how they have to tackle such cyber crimes with their
customer in the name of their own. They needs to investigate about it and finds out the culprit so
that next time it won't happen again, this whole situation takes a lot of expenses of the
organization, thereby, they are considered as the professional issues (Conteh and Staton, 2021).
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Ethical, legal or social aspects
Ethical aspects of the identity thefts are such that in the organization there are many
people who are against the management and tries to spoil the functioning of the organization,
such people are reason where they try to destroy the ethics by revealing the confidential
information and using the social engineering as well. People outside the organization can also
performs this by hacking the accession of the data of the company. Legal issues arises when the
company identifies the theft and the criminal who are responsible for it runs away, this results in
the legal issues in professionalism. Moreover, social aspects are such that the employees who are
working in the organization tries to spoil their own colleagues by data breaching their
information due to some personal conflicts which can directly raise the social issues in
professionalism (Aldawood and Skinner, 2019).
Preliminary Plan
Identifying the sequence of steps
This research report is conducted with having the whole plan for completing the project
which includes the research proposal and major computing project report. Research proposal
includes the project objectives and proposed approach along with the preliminary plan which
contains various other steps such as aim and objectives along with the background and scope
which is followed by the ways of achieving the objectives and additional needs and also the
professional issues relating ethical, legal or social aspects. Major computing project report
includes different chapters from one to seven contains the introduction and literature review
along with the requirements and analysis which is followed by the design and implementation
and testing and also the results and discussion along with the findings and conclusion. These are
the sequencing of steps which are followed in order to complete the research report identity theft
using social engineering.
Expectation of the project to be finished
4
Ethical aspects of the identity thefts are such that in the organization there are many
people who are against the management and tries to spoil the functioning of the organization,
such people are reason where they try to destroy the ethics by revealing the confidential
information and using the social engineering as well. People outside the organization can also
performs this by hacking the accession of the data of the company. Legal issues arises when the
company identifies the theft and the criminal who are responsible for it runs away, this results in
the legal issues in professionalism. Moreover, social aspects are such that the employees who are
working in the organization tries to spoil their own colleagues by data breaching their
information due to some personal conflicts which can directly raise the social issues in
professionalism (Aldawood and Skinner, 2019).
Preliminary Plan
Identifying the sequence of steps
This research report is conducted with having the whole plan for completing the project
which includes the research proposal and major computing project report. Research proposal
includes the project objectives and proposed approach along with the preliminary plan which
contains various other steps such as aim and objectives along with the background and scope
which is followed by the ways of achieving the objectives and additional needs and also the
professional issues relating ethical, legal or social aspects. Major computing project report
includes different chapters from one to seven contains the introduction and literature review
along with the requirements and analysis which is followed by the design and implementation
and testing and also the results and discussion along with the findings and conclusion. These are
the sequencing of steps which are followed in order to complete the research report identity theft
using social engineering.
Expectation of the project to be finished
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
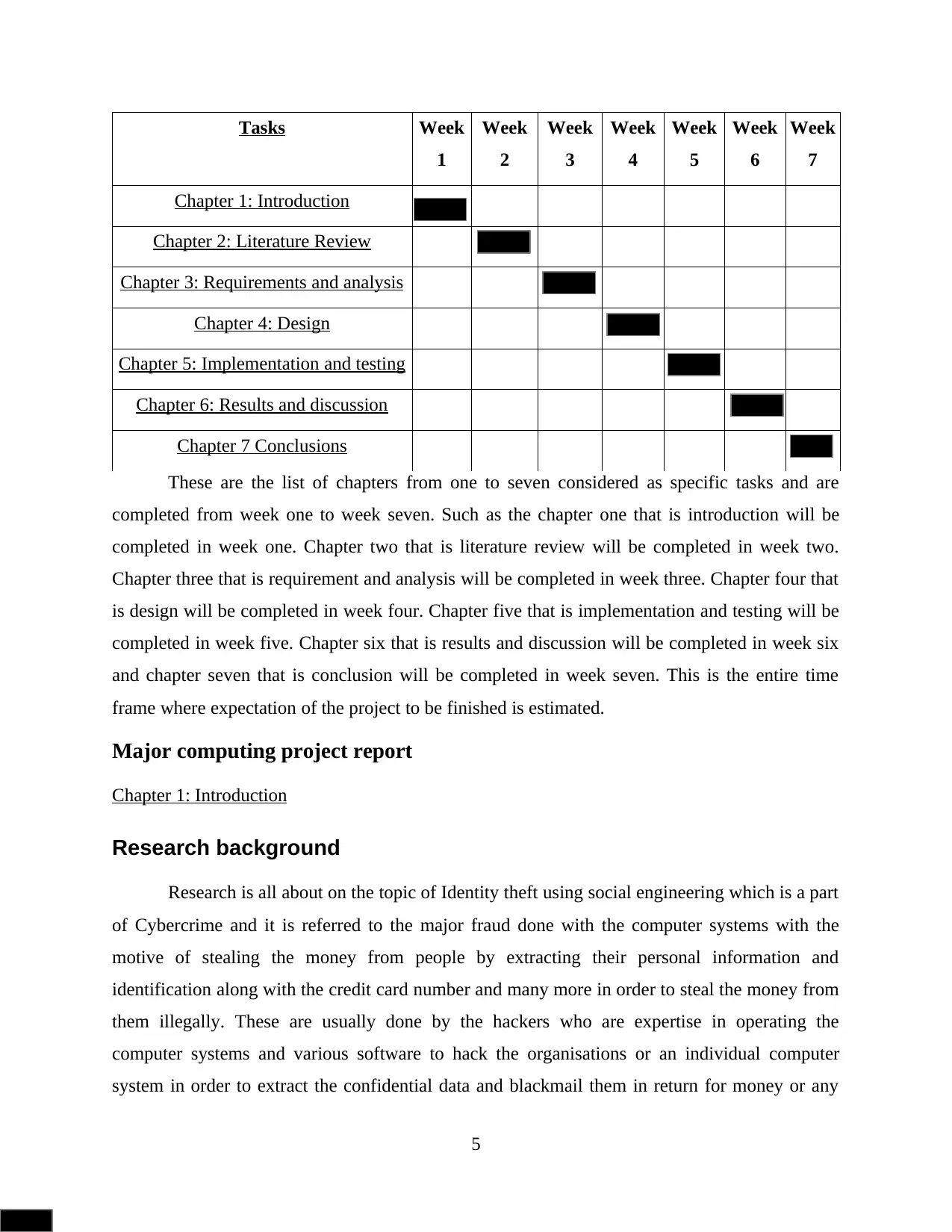
Tasks Week
1
Week
2
Week
3
Week
4
Week
5
Week
6
Week
7
Chapter 1: Introduction
Chapter 2: Literature Review
Chapter 3: Requirements and analysis
Chapter 4: Design
Chapter 5: Implementation and testing
Chapter 6: Results and discussion
Chapter 7 Conclusions
These are the list of chapters from one to seven considered as specific tasks and are
completed from week one to week seven. Such as the chapter one that is introduction will be
completed in week one. Chapter two that is literature review will be completed in week two.
Chapter three that is requirement and analysis will be completed in week three. Chapter four that
is design will be completed in week four. Chapter five that is implementation and testing will be
completed in week five. Chapter six that is results and discussion will be completed in week six
and chapter seven that is conclusion will be completed in week seven. This is the entire time
frame where expectation of the project to be finished is estimated.
Major computing project report
Chapter 1: Introduction
Research background
Research is all about on the topic of Identity theft using social engineering which is a part
of Cybercrime and it is referred to the major fraud done with the computer systems with the
motive of stealing the money from people by extracting their personal information and
identification along with the credit card number and many more in order to steal the money from
them illegally. These are usually done by the hackers who are expertise in operating the
computer systems and various software to hack the organisations or an individual computer
system in order to extract the confidential data and blackmail them in return for money or any
5
1
Week
2
Week
3
Week
4
Week
5
Week
6
Week
7
Chapter 1: Introduction
Chapter 2: Literature Review
Chapter 3: Requirements and analysis
Chapter 4: Design
Chapter 5: Implementation and testing
Chapter 6: Results and discussion
Chapter 7 Conclusions
These are the list of chapters from one to seven considered as specific tasks and are
completed from week one to week seven. Such as the chapter one that is introduction will be
completed in week one. Chapter two that is literature review will be completed in week two.
Chapter three that is requirement and analysis will be completed in week three. Chapter four that
is design will be completed in week four. Chapter five that is implementation and testing will be
completed in week five. Chapter six that is results and discussion will be completed in week six
and chapter seven that is conclusion will be completed in week seven. This is the entire time
frame where expectation of the project to be finished is estimated.
Major computing project report
Chapter 1: Introduction
Research background
Research is all about on the topic of Identity theft using social engineering which is a part
of Cybercrime and it is referred to the major fraud done with the computer systems with the
motive of stealing the money from people by extracting their personal information and
identification along with the credit card number and many more in order to steal the money from
them illegally. These are usually done by the hackers who are expertise in operating the
computer systems and various software to hack the organisations or an individual computer
system in order to extract the confidential data and blackmail them in return for money or any
5

other purposes. The reason behind conducting research on identity theft is because it is not
specific to any organisation but it is particular to one individual who doesn't have any knowledge
about cyber-crimes happening in the world and how they can prevent and fight against such
crimes. The open best dishes are conducted in order to reduce such illegal forms of crimes in
terms of computers and technologies. Social engineering is not only specific to the computers but
it can also be conducted with the help of fraud calls to any of the random individuals and
extracting their personal information but it is majorly conducted with the help of networks and
the internet by hacking the systems or any other. The following discussion contains the aims and
objectives of the research along with the discussions and results with proper findings and
conclusion in order to have the strategic investigation on a particular topic and cover the topic in
every aspect such as in the form of professional issues or personal as well along with the societal
and student issues also.
Summary
The following discussion is based on the different chapters with the help of which the
research is undertaken. Chapter 1 is itself the introduction which specifies the background of the
information with relevant information and data along with the summary of different chapters and
overview of the content they will be specifying in the further research. Chapter 2 will cover the
information of literature review in which the various objectives are described in a detailed
manner such as the concept of social engineering and its effect on society, identity theft and its
consequences on the students, issues of Cyber threats and its impact on businesses and economy
and solutions of Cyber-crime and its implementation in the real world situations. Under all these
objectives, literature review covers the purpose of each and every chapter with the reliable and
relevant investigation conducted on the specific objective with the help of the content of various
authors and sources of recent years and moreover the relationship has been created among the
research outputs and the student's own work. Furthermore, identification of the gaps is also
covered along with the applications and its new research context. Chapter 3 covers the
requirements and analysis section of the entire research report on identity theft which includes
the detailed discussion on the different types of data and software along with the hardware
required in order to conduct the investigation which is basically followed by by the kind of
analysis undertaken to complete the whole report so that its aims and objectives can be fulfilled
6
specific to any organisation but it is particular to one individual who doesn't have any knowledge
about cyber-crimes happening in the world and how they can prevent and fight against such
crimes. The open best dishes are conducted in order to reduce such illegal forms of crimes in
terms of computers and technologies. Social engineering is not only specific to the computers but
it can also be conducted with the help of fraud calls to any of the random individuals and
extracting their personal information but it is majorly conducted with the help of networks and
the internet by hacking the systems or any other. The following discussion contains the aims and
objectives of the research along with the discussions and results with proper findings and
conclusion in order to have the strategic investigation on a particular topic and cover the topic in
every aspect such as in the form of professional issues or personal as well along with the societal
and student issues also.
Summary
The following discussion is based on the different chapters with the help of which the
research is undertaken. Chapter 1 is itself the introduction which specifies the background of the
information with relevant information and data along with the summary of different chapters and
overview of the content they will be specifying in the further research. Chapter 2 will cover the
information of literature review in which the various objectives are described in a detailed
manner such as the concept of social engineering and its effect on society, identity theft and its
consequences on the students, issues of Cyber threats and its impact on businesses and economy
and solutions of Cyber-crime and its implementation in the real world situations. Under all these
objectives, literature review covers the purpose of each and every chapter with the reliable and
relevant investigation conducted on the specific objective with the help of the content of various
authors and sources of recent years and moreover the relationship has been created among the
research outputs and the student's own work. Furthermore, identification of the gaps is also
covered along with the applications and its new research context. Chapter 3 covers the
requirements and analysis section of the entire research report on identity theft which includes
the detailed discussion on the different types of data and software along with the hardware
required in order to conduct the investigation which is basically followed by by the kind of
analysis undertaken to complete the whole report so that its aims and objectives can be fulfilled
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

in an effective and efficient manner. Chapter 4 will cover the design of the entire report which
explains what type of design technique is selected from various other alternatives so that careful
attention could be paid on controlling the conditions for example sampling of the data chosen
along with the coding methods which are used in the report. Chapter 5 will cover the
implementation and testing part which has the discussion about the testing as per the needs and
requirements of the scheme presented in the chapter of analysis and requirements because the
usage of both functional and user acceptance testing was proper in the implementation process.
This is a type of project which is investigative and the techniques used have to be evaluated
according to the standard result set for better calibration along with the live data set. Chapter 6
full cover the results and discussion part which demonstrates the major results of the entire
investigation done so that the critical evaluation can be conducted because this chapter mainly
covers the three basic themes for better understanding such as findings and goals achieved along
with the further work in order to have the better future considerations and decision making for
future research and improvements. Chapter 7 will cover the conclusion of the whole report which
basically summarises about the succession or failure of the research as per the needs and
requirements of aims and objectives so that the amendments can be performed accordingly. All
these chapters are covered in the following discussion for better research and presentation of the
investigation conducted on the topic of Identity theft using social engineering.
Chapter 2: Literature review
Concept of social engineering and its effect on society
Concept of social engineering states that it is related to crime and illegal nature in the
context of information security because it is defined as the psychological influence of an
individual so that an individual can perform such actions which can spoil their life. It is basically
the extracting of confidential information from the people and using it to steal the money such as
credit card number or any identification card. It is a term which is broadly used in terms of
malicious actions which is completed with the help of human communications (Kagita,
Thilakarathne, Gadekallu and Singh, 2020). People who are involved in such crimes use that
trick to manipulate an individual so that they can easily provide that information to them and
even the security mistakes along with the sensitive information. This type of attack happens in
various steps. People who are into the social engineering crime performance stages in the form of
7
explains what type of design technique is selected from various other alternatives so that careful
attention could be paid on controlling the conditions for example sampling of the data chosen
along with the coding methods which are used in the report. Chapter 5 will cover the
implementation and testing part which has the discussion about the testing as per the needs and
requirements of the scheme presented in the chapter of analysis and requirements because the
usage of both functional and user acceptance testing was proper in the implementation process.
This is a type of project which is investigative and the techniques used have to be evaluated
according to the standard result set for better calibration along with the live data set. Chapter 6
full cover the results and discussion part which demonstrates the major results of the entire
investigation done so that the critical evaluation can be conducted because this chapter mainly
covers the three basic themes for better understanding such as findings and goals achieved along
with the further work in order to have the better future considerations and decision making for
future research and improvements. Chapter 7 will cover the conclusion of the whole report which
basically summarises about the succession or failure of the research as per the needs and
requirements of aims and objectives so that the amendments can be performed accordingly. All
these chapters are covered in the following discussion for better research and presentation of the
investigation conducted on the topic of Identity theft using social engineering.
Chapter 2: Literature review
Concept of social engineering and its effect on society
Concept of social engineering states that it is related to crime and illegal nature in the
context of information security because it is defined as the psychological influence of an
individual so that an individual can perform such actions which can spoil their life. It is basically
the extracting of confidential information from the people and using it to steal the money such as
credit card number or any identification card. It is a term which is broadly used in terms of
malicious actions which is completed with the help of human communications (Kagita,
Thilakarathne, Gadekallu and Singh, 2020). People who are involved in such crimes use that
trick to manipulate an individual so that they can easily provide that information to them and
even the security mistakes along with the sensitive information. This type of attack happens in
various steps. People who are into the social engineering crime performance stages in the form of
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

cybercrime such as first is the research which means that people first investigate about the
individual from home they want to extract information and who can be easily manipulated or
influenced and also have a good amount in their bank account. All these investigations are made
by the hacker so that they can target the particular number of people for their crime (van de
Weijer, Leukfeldt and Bernasco, 2019). Second is planning which means that after the collection
of all the data in the research stage then planning is done accordingly because they make the
strategies that how they can use the data and in what manner along with the time duration so that
the proper feasibility study could be undertaken. Third stage is the contact which means that after
the proper planning is done, hackers start contacting the people who they have targeted in the
previous stages one by one by using all the tricks of manipulation and influencing them in order
to extract their confidential information (Yar and Steinmetz, 2019). Hackers generally target with
the help of fraud phone calls and can be the internet and networking which is also called the
cybercrime and cyber theft. Fourth stage is the execution which means that after extracting all
the information they start the process of stealing the money out from the confidential information
with their own software because they have the expertise in doing this and have a special
knowledge so they operate their software and extract along with the stealing of money of an
individual. Social engineering affects the society in a very drastic manner such as it has a
negative impact on the society because society faces the mental stress and financial loss due to
social engineering because the main purpose of social engineering is to steal the money which
majorly results in the loss of money which leads to the mental stress in a person and due to this
person attempts suicide or any other dangerous act. There is only the negative aspect of social
engineering in society, this is because it is very well known that the people are for the family and
if another person steals all their savings then it can also result in the mental trauma of a person
which ends the willingness to live as an individual. This is the impact of social engineering on
society (Kizza, 2020).
Identity theft and its consequences on the students
Concept of Identity Theft States that is the part of the social engineering and which is a
part of the cybercrime or cyber theft. Identity theft is referred to the using of personal
information of someone else for the personal use of one's own specially in the form of
identification number or in the form of credit card number so that the stealing of money can be
8
individual from home they want to extract information and who can be easily manipulated or
influenced and also have a good amount in their bank account. All these investigations are made
by the hacker so that they can target the particular number of people for their crime (van de
Weijer, Leukfeldt and Bernasco, 2019). Second is planning which means that after the collection
of all the data in the research stage then planning is done accordingly because they make the
strategies that how they can use the data and in what manner along with the time duration so that
the proper feasibility study could be undertaken. Third stage is the contact which means that after
the proper planning is done, hackers start contacting the people who they have targeted in the
previous stages one by one by using all the tricks of manipulation and influencing them in order
to extract their confidential information (Yar and Steinmetz, 2019). Hackers generally target with
the help of fraud phone calls and can be the internet and networking which is also called the
cybercrime and cyber theft. Fourth stage is the execution which means that after extracting all
the information they start the process of stealing the money out from the confidential information
with their own software because they have the expertise in doing this and have a special
knowledge so they operate their software and extract along with the stealing of money of an
individual. Social engineering affects the society in a very drastic manner such as it has a
negative impact on the society because society faces the mental stress and financial loss due to
social engineering because the main purpose of social engineering is to steal the money which
majorly results in the loss of money which leads to the mental stress in a person and due to this
person attempts suicide or any other dangerous act. There is only the negative aspect of social
engineering in society, this is because it is very well known that the people are for the family and
if another person steals all their savings then it can also result in the mental trauma of a person
which ends the willingness to live as an individual. This is the impact of social engineering on
society (Kizza, 2020).
Identity theft and its consequences on the students
Concept of Identity Theft States that is the part of the social engineering and which is a
part of the cybercrime or cyber theft. Identity theft is referred to the using of personal
information of someone else for the personal use of one's own specially in the form of
identification number or in the form of credit card number so that the stealing of money can be
8

done and this is performed without any permission in order to commit the fraud and crimes. It
was first conducted in 1964 (Singh and Rastogi, 2018). This is a term which describes all types
of crimes and illegal actions in which the person wrongfully extracts and uses the other
individual Private data which is considered as fraud and deception. The motive of such crime is
basically to take revenge from the person or to simply steal the money for their own luxurious
life. There are different types of Identity theft which the hackers used to attack the people such as
account takeover fraud which means that hackers hack the account of an individual and access
the account as per the needs and requirements and specifically attack those people who have a
good amount in their bank account. Debit card and credit card fraud which means that hackers
steal the information from an individual of the personal number which is printed on the debit and
credit card so that they can steal the money and access the bank accounts of the person
(Alshammari and Singh, 2018). Drivers licence identity theft which means that hackers hack the
driving licence of the person so that the information can be extracted and use the information in
their illegal activities which majorly turns into cybercrime. Mail identity theft which means that
hackers use the email spoofing to contact the person and send the satisfying mail so that the
person can easily provide the bank accounts information to them and the reason being the
greediness of a person. Online shopping fraud which means that hackers access the account of a
person through the applications through which the person conducts the online shopping and
through which we can extract the bank account details and can also make their shopping fraud
from the fraud websites. Social security number identity theft which is one of the identification
number of every individual who lives in the nation and it is important to link it with every bank
account so that the online transactions can be possible and therefore identity theft is also
performed on the social security number so that the hackers can easily access the bank accounts
of an individual. Another minor identity theft includes the senior identity theft and scams along
with the child identity theft and text identity theft which is followed by the biometric
identification theft and synthetic identity theft and also the medical identity theft (Wang, Hsieh,
Chang and Dallier, 2021). Moreover, the mortgage fraud and home title fraud along with the lost
or stolen passport and internet of things identity fraud. Identity theft is majorly impacting the
students because nowadays students are willing to earn because of the increasing opportunity for
the students to earn in the small age only and therefore they find their job opportunities on the
Internet specially on the job applications which is connected directly to the internet and therefore
9
was first conducted in 1964 (Singh and Rastogi, 2018). This is a term which describes all types
of crimes and illegal actions in which the person wrongfully extracts and uses the other
individual Private data which is considered as fraud and deception. The motive of such crime is
basically to take revenge from the person or to simply steal the money for their own luxurious
life. There are different types of Identity theft which the hackers used to attack the people such as
account takeover fraud which means that hackers hack the account of an individual and access
the account as per the needs and requirements and specifically attack those people who have a
good amount in their bank account. Debit card and credit card fraud which means that hackers
steal the information from an individual of the personal number which is printed on the debit and
credit card so that they can steal the money and access the bank accounts of the person
(Alshammari and Singh, 2018). Drivers licence identity theft which means that hackers hack the
driving licence of the person so that the information can be extracted and use the information in
their illegal activities which majorly turns into cybercrime. Mail identity theft which means that
hackers use the email spoofing to contact the person and send the satisfying mail so that the
person can easily provide the bank accounts information to them and the reason being the
greediness of a person. Online shopping fraud which means that hackers access the account of a
person through the applications through which the person conducts the online shopping and
through which we can extract the bank account details and can also make their shopping fraud
from the fraud websites. Social security number identity theft which is one of the identification
number of every individual who lives in the nation and it is important to link it with every bank
account so that the online transactions can be possible and therefore identity theft is also
performed on the social security number so that the hackers can easily access the bank accounts
of an individual. Another minor identity theft includes the senior identity theft and scams along
with the child identity theft and text identity theft which is followed by the biometric
identification theft and synthetic identity theft and also the medical identity theft (Wang, Hsieh,
Chang and Dallier, 2021). Moreover, the mortgage fraud and home title fraud along with the lost
or stolen passport and internet of things identity fraud. Identity theft is majorly impacting the
students because nowadays students are willing to earn because of the increasing opportunity for
the students to earn in the small age only and therefore they find their job opportunities on the
Internet specially on the job applications which is connected directly to the internet and therefore
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





