iDevice Forensics: Data Integrity Assessment at NUST
VerifiedAdded on 2022/08/29
|6
|5310
|33
Project
AI Summary
This project, conducted at the National University of Sciences and Technology (NUST), Islamabad, Pakistan, investigates data integrity in iDevice forensics, specifically focusing on iPads. The research compares data acquired using an operating system utility (Ubuntu), a freeware tool (libimobiledevice), and a commercial tool (XRY Complete). The study aims to assess the reliability of these tools in preserving data integrity, a crucial factor for the admissibility of forensic findings. The methodology involves logical extractions using the aforementioned tools, followed by comparisons of forensic artifacts and hash values to determine data integrity. The results reveal that freeware tools can, under certain circumstances, maintain data integrity similarly to commercial tools, while commercial tools can sometimes raise doubts about data integrity. The research also explores interesting patterns in the operation of the commercial tool through consecutive extractions. The project provides recommendations for forensic examiners regarding tool selection based on specific requirements and highlights the importance of data integrity in digital forensics.

iDevice Forensics - Data Integrity
Maryam Jalees Ahmed∗
, Umar Khalid†, Baber Aslam‡
National University of Sciences and Technology, Islamabad, Pakistan
{∗
maryam.is-10, †umardar27, ‡ababer}@mcs.edu.pk
Abstract—There are different types of embedded portable
iDevices which can be used in criminal activities. The most
commonly used gadget in the field of embedded portable
iDevices is the iPad. Techniques used to acquire data from iPad
include jail breaking, using inbuilt operating system utilities
and using forensic tools (open source, freeware or commercial).
Data integrity is a vital element of digital forensics which must
be ensured for acceptability of findings (retrieved forensic
artifacts) in a court of law. In order to establish data integrity
in iDevice forensics, investigations were performed using
different techniques, specifically an operating system inbuilt
utility, a freeware tool and a commercial tool. The forensic
artifacts acquired from these tools and techniques were then
compared to ascertain their data integrity. The results have
shown that on one hand the freeware tools, under certain
circumstance, also preserve data integrity as their commercial
counterparts but on the other hand the commercial tools,
under certain circumstance, also make data integrity doubtful
as generally believed for freeware tools. Based on the results,
the research has also recommended various data acquisition
tools that the forensic examiner can select depending on the
requirement.
I. INTRODUCTION
iDevices are being used by millions of people all around
the world. These devices hold personal and organizational
data which has forensic importance. [1] iDevices are
characterized as portable devices which are generally closed
embedded systems [2, 3]. Such systems prohibit direct
access to the device’s memory when connected to a personal
computer [1, 3]. Nonetheless, there are few methods
available through which data can be collected from
iDevices. Synchronizing, jail breaking, or using
freeware/open-source tools are among free options for data
acquisition. However, data retrieved through these
techniques lack legitimacy. Conversely, commercial tools
claim to provide legitimacy but they are proprietary
software and expensive. Thus, it is tough to define that the
stated methods are reliable and preserve data integrity [2, 3].
In an effort to obtain legitimate forensic data from an
iDevice, we have used two investigation techniques. The
first investigation involves gathering data using operating
system utilities or freeware and comparing it with the data
gathered from a commercial tool. Whereas, the second
investigation involves consecutive extractions of the data
with the help of a commercial tool and comparing these
extractions with each other.
In this research work, Ubuntu - an operating system with
an inbuilt data extraction utility, libimobiledevice - a
freeware and XRY Complete - a commercial tool were used.
Analysis revealed that the Ubuntu and libimobiledevice
provide similar reliable results for the artifacts present in
Media Folder and Applications Folder of iDevice.
Moreover, libimobiledevice supports several other folders
such as Keychains, Mobile, Preferences, Root and Wireless.
While, consecutive extractions performed on iDevice using
XRY Complete brings out several interesting patterns in the
operation of closed source commercial tool. The research
methodology is described in section III.
This research will benefit investigators in selecting the
best data acquisition tool, depending upon the requirement
of iDevice forensic case. This will also help the forensic
investigator, who is interested about files associated to
location services, call history, passwords, applications,
application’s documents, cache, preferences, cookies,
webkits, system settings, system applications settings or
user data. The user data includes videos, books, downloads,
photos, purchases and music files. All these respective files
are present in user partition of iDevice. These files hold
sensitive data and can be a vital source of evidence for
crime investigation.
The paper is outlined as follows. The second section
covers the level of research already carried out on the
proposed area. The third section describes various setups
and procedures being used for each investigation. The fourth
section gives an understanding of investigation
methodology. The fifth and sixth sections provide outcome
of the investigation process. The seventh section discusses
and compares the results of the assessment and brings out
interesting facts and figures. This section also recommends
various acquisition techniques depending on forensic
investigator requirement. The eighth section concludes the
aim of this research accompanied by all executed procedures
and steps and also proposes an area for future research.
II. RELATED WORK
Different methods have been explored to acquire data
from iDevices. Most relevant work has been discussed
below:
Zdziarski [4], offered a way to gather iPhone forensic
image through Wi-Fi and serial port. Method involved few
steps like device jailbreaking, usage of SSH access and
some regular UNIX tools. Image was transferred using Wi-
Fi that was fairly slow.
Gomez [2], carried out analysis of data extraction by
connecting iPad to iTunes installed system via normal USB.
The software harmonizes current data and recovers backup
from the portable device. To synchronize, proper pairing
between the device and the software is required. The paper
also proposed a fast method of imaging an iPad directly to
the attached USB drive by using a cheap iPad accessory.
This research concluded that commercial tools can give
same imaging rate but there is no surety about data integrity.
Kubi [5], evaluated UFED and XRY tools which are
used to extract evidence from mobile devices. The paper
investigated these tools in order to provide convenience to
mobile investigator for selecting suitable tool for a particular
scenario. NIST smartphone tool specification was made the
260 ISBN: 978-1-4799-5754-5/14/$26.00 ©2014 IEEE
_____________________________________________
Maryam Jalees Ahmed∗
, Umar Khalid†, Baber Aslam‡
National University of Sciences and Technology, Islamabad, Pakistan
{∗
maryam.is-10, †umardar27, ‡ababer}@mcs.edu.pk
Abstract—There are different types of embedded portable
iDevices which can be used in criminal activities. The most
commonly used gadget in the field of embedded portable
iDevices is the iPad. Techniques used to acquire data from iPad
include jail breaking, using inbuilt operating system utilities
and using forensic tools (open source, freeware or commercial).
Data integrity is a vital element of digital forensics which must
be ensured for acceptability of findings (retrieved forensic
artifacts) in a court of law. In order to establish data integrity
in iDevice forensics, investigations were performed using
different techniques, specifically an operating system inbuilt
utility, a freeware tool and a commercial tool. The forensic
artifacts acquired from these tools and techniques were then
compared to ascertain their data integrity. The results have
shown that on one hand the freeware tools, under certain
circumstance, also preserve data integrity as their commercial
counterparts but on the other hand the commercial tools,
under certain circumstance, also make data integrity doubtful
as generally believed for freeware tools. Based on the results,
the research has also recommended various data acquisition
tools that the forensic examiner can select depending on the
requirement.
I. INTRODUCTION
iDevices are being used by millions of people all around
the world. These devices hold personal and organizational
data which has forensic importance. [1] iDevices are
characterized as portable devices which are generally closed
embedded systems [2, 3]. Such systems prohibit direct
access to the device’s memory when connected to a personal
computer [1, 3]. Nonetheless, there are few methods
available through which data can be collected from
iDevices. Synchronizing, jail breaking, or using
freeware/open-source tools are among free options for data
acquisition. However, data retrieved through these
techniques lack legitimacy. Conversely, commercial tools
claim to provide legitimacy but they are proprietary
software and expensive. Thus, it is tough to define that the
stated methods are reliable and preserve data integrity [2, 3].
In an effort to obtain legitimate forensic data from an
iDevice, we have used two investigation techniques. The
first investigation involves gathering data using operating
system utilities or freeware and comparing it with the data
gathered from a commercial tool. Whereas, the second
investigation involves consecutive extractions of the data
with the help of a commercial tool and comparing these
extractions with each other.
In this research work, Ubuntu - an operating system with
an inbuilt data extraction utility, libimobiledevice - a
freeware and XRY Complete - a commercial tool were used.
Analysis revealed that the Ubuntu and libimobiledevice
provide similar reliable results for the artifacts present in
Media Folder and Applications Folder of iDevice.
Moreover, libimobiledevice supports several other folders
such as Keychains, Mobile, Preferences, Root and Wireless.
While, consecutive extractions performed on iDevice using
XRY Complete brings out several interesting patterns in the
operation of closed source commercial tool. The research
methodology is described in section III.
This research will benefit investigators in selecting the
best data acquisition tool, depending upon the requirement
of iDevice forensic case. This will also help the forensic
investigator, who is interested about files associated to
location services, call history, passwords, applications,
application’s documents, cache, preferences, cookies,
webkits, system settings, system applications settings or
user data. The user data includes videos, books, downloads,
photos, purchases and music files. All these respective files
are present in user partition of iDevice. These files hold
sensitive data and can be a vital source of evidence for
crime investigation.
The paper is outlined as follows. The second section
covers the level of research already carried out on the
proposed area. The third section describes various setups
and procedures being used for each investigation. The fourth
section gives an understanding of investigation
methodology. The fifth and sixth sections provide outcome
of the investigation process. The seventh section discusses
and compares the results of the assessment and brings out
interesting facts and figures. This section also recommends
various acquisition techniques depending on forensic
investigator requirement. The eighth section concludes the
aim of this research accompanied by all executed procedures
and steps and also proposes an area for future research.
II. RELATED WORK
Different methods have been explored to acquire data
from iDevices. Most relevant work has been discussed
below:
Zdziarski [4], offered a way to gather iPhone forensic
image through Wi-Fi and serial port. Method involved few
steps like device jailbreaking, usage of SSH access and
some regular UNIX tools. Image was transferred using Wi-
Fi that was fairly slow.
Gomez [2], carried out analysis of data extraction by
connecting iPad to iTunes installed system via normal USB.
The software harmonizes current data and recovers backup
from the portable device. To synchronize, proper pairing
between the device and the software is required. The paper
also proposed a fast method of imaging an iPad directly to
the attached USB drive by using a cheap iPad accessory.
This research concluded that commercial tools can give
same imaging rate but there is no surety about data integrity.
Kubi [5], evaluated UFED and XRY tools which are
used to extract evidence from mobile devices. The paper
investigated these tools in order to provide convenience to
mobile investigator for selecting suitable tool for a particular
scenario. NIST smartphone tool specification was made the
260 ISBN: 978-1-4799-5754-5/14/$26.00 ©2014 IEEE
_____________________________________________
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

base for this evaluation. Results of the evaluation were
represented graphically showing that XRY outdid UFED in
many circumstances.
Sigwald [6, 7], discussed a tool for automatic SSH
ramdisk creation and loading. Suggested method supported
devices with A4 chips and lower. Required files from Apple
were automatically downloaded by the tool and SSH client
was used to run different commands. The tool performed
DD and NAND dump.
Iqbal [1], developed a technique to gather records
without jailbreaking the iDevices. Focus of the proposed
technique was to provide data extraction in less than half an
hour while preserving integrity of the evidence. The paper
explains that to get a root access, weakness was exploited in
the booting phase. Tool for analysis of extracted data was
also developed. The paper also discussed that integrity
factor is doubtful when a device is jailbreaked or a
commercial tool is used for data mining
Abalenkovs [3], discussed the security features of two
operating systems i.e. iOS and Android in detail. The paper
compared the existing techniques on data retrieval and
presented a way to examine extracted data. Various open
source and closed source tools were also discussed. The
paper also concluded that integrity factor is doubtful when a
device is jailbroken or rooted.
The above mentioned studies conclude that many
techniques and tools have been suggested for extracting data
from iDevices, but ensuring data integrity is still very
challenging. Open source tools are freely available but do
not provide any assurance about data validity. On the other
hand, commercial tools claim to provide reliability but are
expensive.
Despite the importance of data integrity in the digital
forensic, there is no study available in the literature that has
compared the validity of data extracted from open source
tools with the data obtained from commercial tools. The
proposed work will establish the validity (and its extent) of
data that is obtained from open source tools thus enabling
the use of open source tools for iPad forensics.
III. MOTIVATION
In early 2010, Apple launched its first tablet and named
it iPad [2]. With the passage of time its various models were
introduced and it became very popular [8, 9]. From
storage/data point of view, an iPad comprises of system-
partition and data-partition. System partition holds operating
system and factory installed applications, while user’s data
and applications installed by the consumer are stored in data
partition. As the system partition cannot be modified by user
so it makes it non-evidential. Conversely, user partition has
user specific data and hence assists the forensic investigator.
[1]
User partition contains various folders such as
Keychains, Mobile, Preferences, Root and Wireless.
Keychains folder stores the passwords used within iOS.
Mobile folder comprises of three subfolders: Application,
Library and Media. Application subfolder contains Cache,
Preferences, Cookies, Webkits and applications itself.
Library subfolder holds data like settings for system and
system applications (Safari, Maps, Mail, Notes, Calendars,
Address Book and Voicemail). Media subfolder holds user’s
Video’s, Podcast’s, Book’s, Download’s, Photo’s, iTunes
Data, Purchase’s and Music data [1]. Preferences folder
contains files related to system configuration, power
management, network interfaces and wifi. Data related to
location services is located in Root folder. Whereas, call
history records from MobilePhone.app reside in Wireless
folder. These folders are important for forensic investigator.
Idiosyncrasies of the embedded portable devices like
iPad, hinders access to its partitions without using forensic
softwares. To access the significant files without using
commercial tools, two detailed investigations were
performed on iPad 1, version 5.1.1, thus aiding the forensic
analysis of data without spending on a costly commercial
tool. To ascertain the integrity of the extracted data from
open source tool, first investigation was used and it was
established that the data thus obtained was authentic and
therefore, open source tools can be used for iPad forensics.
In the first investigation, the iPad was mounted to Windows
7 and Ubuntu machine separately. Appearance of an iPad on
each operating system was different as shown in Table I.
The logical extraction was then performed on iPad with the
help of libimobiledevice and XRY. Table II illustrates the
two forensic tools used in this experiment with different
operating systems.
TABLE I.
IPAD IDENTITY ON DIFFERENT OS PLATFORM
Operating Sytem Platform Identity Status
Microsoft Windows 7 – 32 bit Portable Device
Ubuntu 12.04.3 LTS MJ’s iPad
Documents on MJ’s iPad
TABLE II.
FORENSIC TOOL BREAKDOWN BY OS AND TYPE
Tools Operating System
Requirements
Type
XRY Complete Microsoft Windows 7 Commercial Tool
libimobiledevice Linux Free Software
The research work also focused on understanding the
interesting forensic patterns in the operations of closed
source commercial tool using second investigation
technique. As far as the authors can tell, no research exists
where unique facts and figures in commercial forensic tool
operations are identified. Five consecutive logical and
physical extractions were performed on an iPad using XRY
Complete. The files thus generated were compared for
changes in the file size and hash values. This difference in
file sizes and hashes aids the analyst to figure out the
modifications in each of the created XRY file.
IV. INVESTIGATION METHODOLOGY
The main purpose of this research was to compare
validity of data obtained from the operating system utility
and freewares to the data obtained from the commercial
tool. Another aspect of this research was to identify
interesting patterns in consecutive extractions. These
consecutive extractions were performed on iDevice using a
commercial tool.
This research involved three data acquisition tools, i.e.,
Ubuntu, libimobiledevice and XRY Complete. Ubuntu is a
Debian-based Linux operating system, made-up of
numerous software packages. Most of the packages are
freeware. Till date many Ubuntu versions have been
released. [10] libimobiledevice is a free software library
261
represented graphically showing that XRY outdid UFED in
many circumstances.
Sigwald [6, 7], discussed a tool for automatic SSH
ramdisk creation and loading. Suggested method supported
devices with A4 chips and lower. Required files from Apple
were automatically downloaded by the tool and SSH client
was used to run different commands. The tool performed
DD and NAND dump.
Iqbal [1], developed a technique to gather records
without jailbreaking the iDevices. Focus of the proposed
technique was to provide data extraction in less than half an
hour while preserving integrity of the evidence. The paper
explains that to get a root access, weakness was exploited in
the booting phase. Tool for analysis of extracted data was
also developed. The paper also discussed that integrity
factor is doubtful when a device is jailbreaked or a
commercial tool is used for data mining
Abalenkovs [3], discussed the security features of two
operating systems i.e. iOS and Android in detail. The paper
compared the existing techniques on data retrieval and
presented a way to examine extracted data. Various open
source and closed source tools were also discussed. The
paper also concluded that integrity factor is doubtful when a
device is jailbroken or rooted.
The above mentioned studies conclude that many
techniques and tools have been suggested for extracting data
from iDevices, but ensuring data integrity is still very
challenging. Open source tools are freely available but do
not provide any assurance about data validity. On the other
hand, commercial tools claim to provide reliability but are
expensive.
Despite the importance of data integrity in the digital
forensic, there is no study available in the literature that has
compared the validity of data extracted from open source
tools with the data obtained from commercial tools. The
proposed work will establish the validity (and its extent) of
data that is obtained from open source tools thus enabling
the use of open source tools for iPad forensics.
III. MOTIVATION
In early 2010, Apple launched its first tablet and named
it iPad [2]. With the passage of time its various models were
introduced and it became very popular [8, 9]. From
storage/data point of view, an iPad comprises of system-
partition and data-partition. System partition holds operating
system and factory installed applications, while user’s data
and applications installed by the consumer are stored in data
partition. As the system partition cannot be modified by user
so it makes it non-evidential. Conversely, user partition has
user specific data and hence assists the forensic investigator.
[1]
User partition contains various folders such as
Keychains, Mobile, Preferences, Root and Wireless.
Keychains folder stores the passwords used within iOS.
Mobile folder comprises of three subfolders: Application,
Library and Media. Application subfolder contains Cache,
Preferences, Cookies, Webkits and applications itself.
Library subfolder holds data like settings for system and
system applications (Safari, Maps, Mail, Notes, Calendars,
Address Book and Voicemail). Media subfolder holds user’s
Video’s, Podcast’s, Book’s, Download’s, Photo’s, iTunes
Data, Purchase’s and Music data [1]. Preferences folder
contains files related to system configuration, power
management, network interfaces and wifi. Data related to
location services is located in Root folder. Whereas, call
history records from MobilePhone.app reside in Wireless
folder. These folders are important for forensic investigator.
Idiosyncrasies of the embedded portable devices like
iPad, hinders access to its partitions without using forensic
softwares. To access the significant files without using
commercial tools, two detailed investigations were
performed on iPad 1, version 5.1.1, thus aiding the forensic
analysis of data without spending on a costly commercial
tool. To ascertain the integrity of the extracted data from
open source tool, first investigation was used and it was
established that the data thus obtained was authentic and
therefore, open source tools can be used for iPad forensics.
In the first investigation, the iPad was mounted to Windows
7 and Ubuntu machine separately. Appearance of an iPad on
each operating system was different as shown in Table I.
The logical extraction was then performed on iPad with the
help of libimobiledevice and XRY. Table II illustrates the
two forensic tools used in this experiment with different
operating systems.
TABLE I.
IPAD IDENTITY ON DIFFERENT OS PLATFORM
Operating Sytem Platform Identity Status
Microsoft Windows 7 – 32 bit Portable Device
Ubuntu 12.04.3 LTS MJ’s iPad
Documents on MJ’s iPad
TABLE II.
FORENSIC TOOL BREAKDOWN BY OS AND TYPE
Tools Operating System
Requirements
Type
XRY Complete Microsoft Windows 7 Commercial Tool
libimobiledevice Linux Free Software
The research work also focused on understanding the
interesting forensic patterns in the operations of closed
source commercial tool using second investigation
technique. As far as the authors can tell, no research exists
where unique facts and figures in commercial forensic tool
operations are identified. Five consecutive logical and
physical extractions were performed on an iPad using XRY
Complete. The files thus generated were compared for
changes in the file size and hash values. This difference in
file sizes and hashes aids the analyst to figure out the
modifications in each of the created XRY file.
IV. INVESTIGATION METHODOLOGY
The main purpose of this research was to compare
validity of data obtained from the operating system utility
and freewares to the data obtained from the commercial
tool. Another aspect of this research was to identify
interesting patterns in consecutive extractions. These
consecutive extractions were performed on iDevice using a
commercial tool.
This research involved three data acquisition tools, i.e.,
Ubuntu, libimobiledevice and XRY Complete. Ubuntu is a
Debian-based Linux operating system, made-up of
numerous software packages. Most of the packages are
freeware. Till date many Ubuntu versions have been
released. [10] libimobiledevice is a free software library
261
which communicates to Apple devices nat
file system without jail breaking a devic
XRY Complete is a commercial hardwa
tool manufactured by Micro Systemat
recovers live and deleted data from mo
forensically secure manner [12, 13].
Before moving towards investiga
following categories of iPad were popul
test data: Safari, Messages, Calendar, N
Videos, iTunes, Music, Photos, Mail, Co
few other applications such as Adobe
FileManager, and Temple Run. The purpo
was to locate the files containing artifacts
folders when the specific investigation was
In order to check data validity, hashe
for the data acquired from various tools. M
to birthday attack which makes it less secu
high probability that two different inputs c
values in our research. To complement
MD5, we have also used SHA-256. SHA-2
and collision resistant.
V. INVESTIGATION 1: DATA INTEGR
The first step in any forensic investig
evidence. Evidence is acceptable in court
integrity of data is preserved during the a
[1]. This investigation was carried to pro
acquisition techniques are reliable and
commercial tools. For the analysis and test
paper) a forensics workstation, data acquis
iPad were used.
A. Microsoft Windows 7 - 32 bit
In this investigation, iPad was first att a
Windows 7 machine. It was recognized as
Only the DCIM folder was visible to
Windows platform. DCIM folder contain s
the iPad. These pictures were acquired an
each picture were recorded.
B. Ubuntu 12.04.3 LTS
The iPad was mounted in a default op
mode to Ubuntu 12.04.3 LTS operati
different volumes were displayed: first v
iPad’ and second volume was ‘Documents
actual practice data resides in various i
One such directory which holds
/var/mobile/Media. Another directory
application.documents.is./var/mobile/Appl
er}/Documents. Artifacts associated w
directories were found when iPad was m
machine. User’s Video’s, Podcast’s, Boo
Photo’s, iTunes Data, Purchase’s and
/var/mobile/Media directory. Documen
applications like Adobe Reader and
applications.resides.in /var/mobile/Applica
/Documents. All these artifacts are a va
evidence for forensic examination.
Ubuntu gave access to many folder s
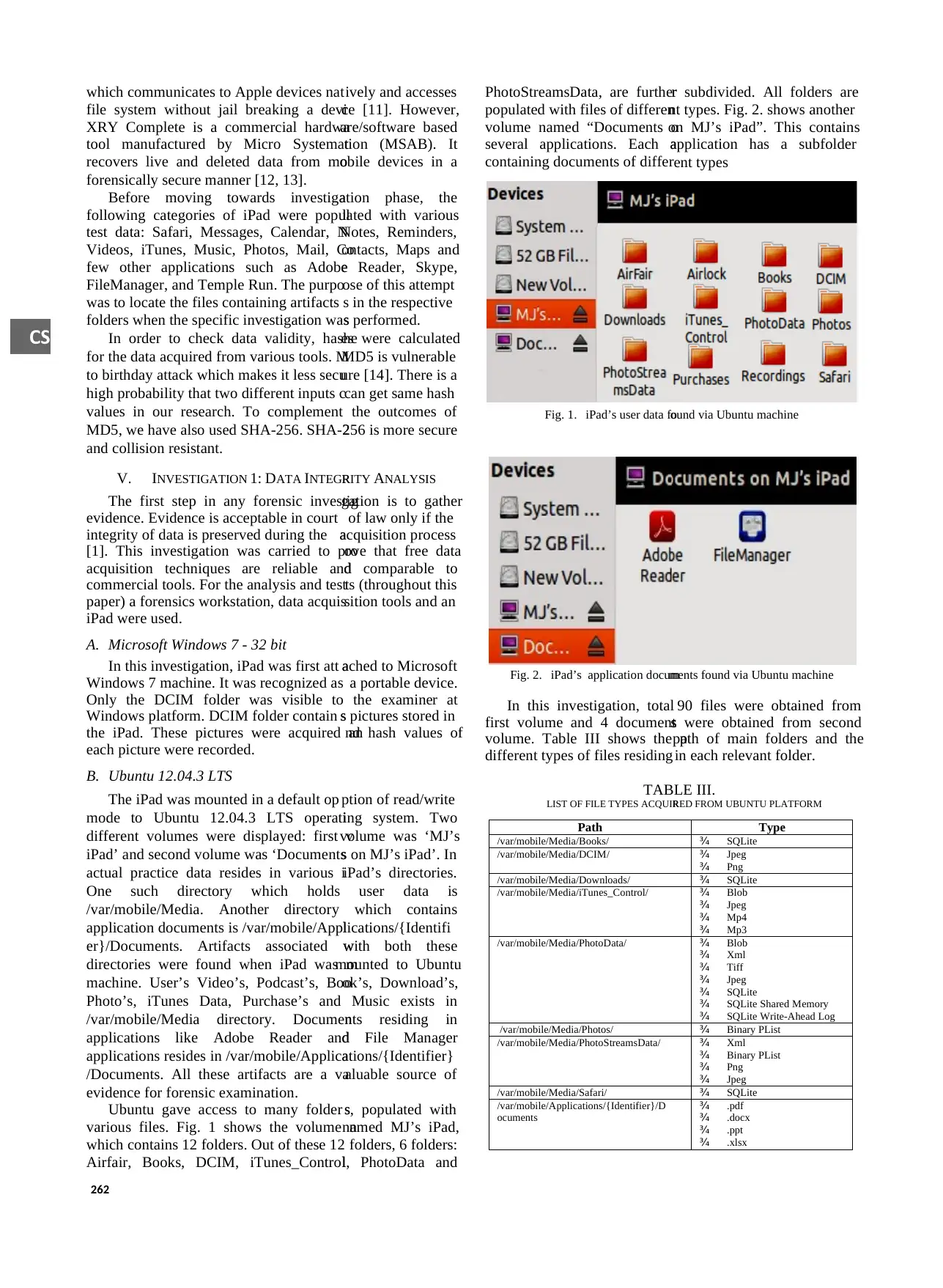
various files. Fig. 1 shows the volume n
which contains 12 folders. Out of these 12
Airfair, Books, DCIM, iTunes_Control
ively and accesses
ce [11]. However,
are/software based
tion (MSAB). It
obile devices in a
ation phase, the
lated with various
Notes, Reminders,
ontacts, Maps and
e Reader, Skype,
ose of this attempt
s in the respective
s performed.
es were calculated
MD5 is vulnerable
ure [14]. There is a
can get same hash
the outcomes of
256 is more secure
RITY ANALYSIS
gation is to gather
of law only if the
acquisition process
ove that free data
d comparable to
ts (throughout this
sition tools and an
ached to Microsoft
a portable device.
the examiner at
s pictures stored in
nd hash values of
ption of read/write
ing system. Two
volume was ‘MJ’s
s on MJ’s iPad’. In
iPad’s directories.
user data is
which contains
lications/{Identifi
with both these
mounted to Ubuntu
ok’s, Download’s,
Music exists in
nts residing in
d File Manager
ations/{Identifier}
aluable source of
s, populated with
named MJ’s iPad,
folders, 6 folders:
l, PhotoData and
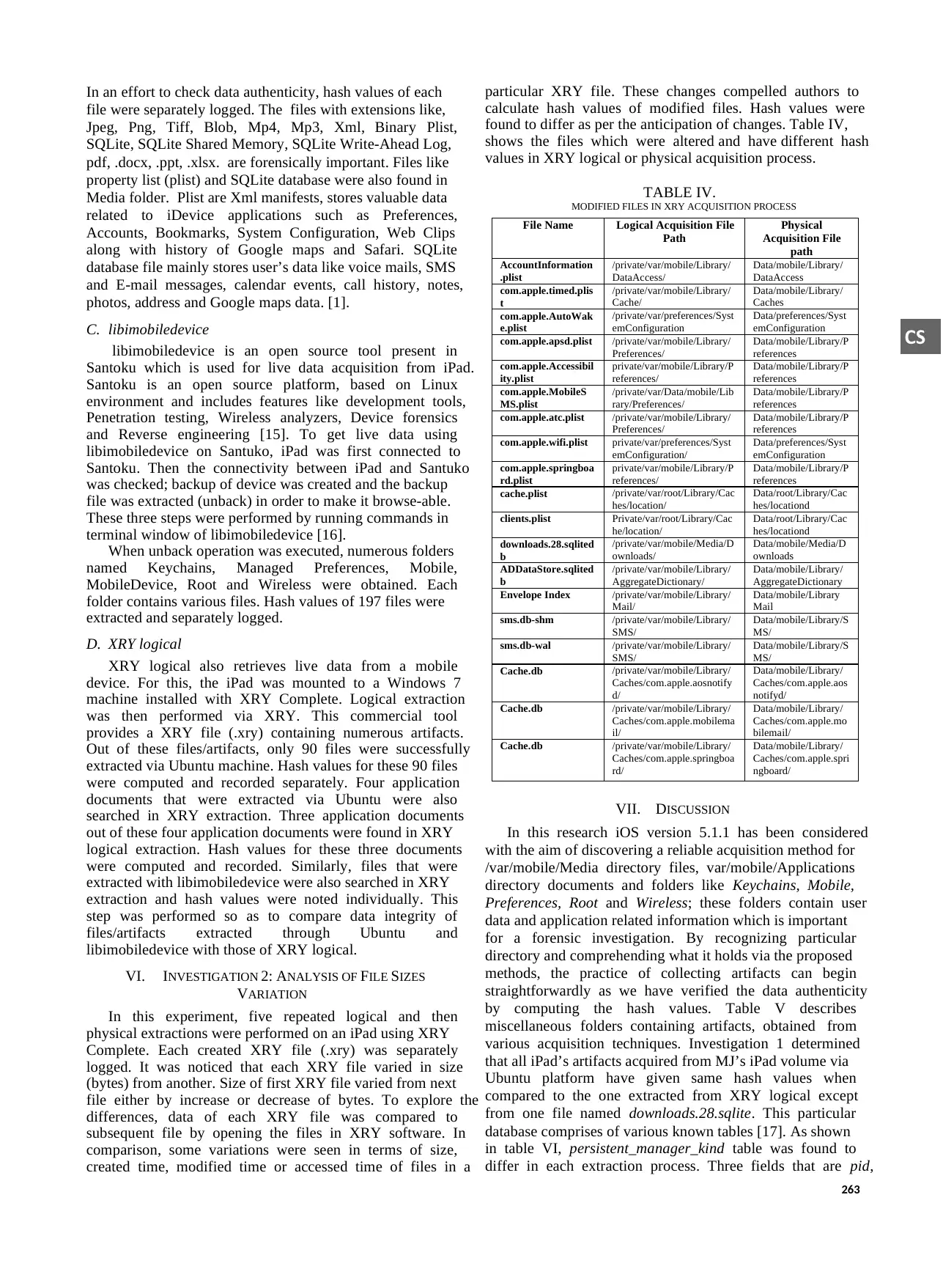
PhotoStreamsData, are further
populated with files of differen
volume named “Documents o
several applications. Each a
containing documents of differ
Fig. 1. iPad’s user data fo
Fig. 2. iPad’s application docum
In this investigation, total
first volume and 4 documents
volume. Table III shows the p
different types of files residing
TAB
LIST OF FILE TYPES ACQUIR
Path
/var/mobile/Media/Books/
/var/mobile/Media/DCIM/
/var/mobile/Media/Downloads/
/var/mobile/Media/iTunes_Control/
/var/mobile/Media/PhotoData/
/var/mobile/Media/Photos/
/var/mobile/Media/PhotoStreamsData/
/var/mobile/Media/Safari/
/var/mobile/Applications/{Identifier}/D
ocuments
r subdivided. All folders are
nt types. Fig. 2. shows another
on MJ’s iPad”. This contains
application has a subfolder
ent types
ound via Ubuntu machine
ments found via Ubuntu machine
90 files were obtained from
s were obtained from second
path of main folders and the
in each relevant folder.
LE III.
RED FROM UBUNTU PLATFORM
Type
¾ SQLite
¾ Jpeg
¾ Png
¾ SQLite
¾ Blob
¾ Jpeg
¾ Mp4
¾ Mp3
¾ Blob
¾ Xml
¾ Tiff
¾ Jpeg
¾ SQLite
¾ SQLite Shared Memory
¾ SQLite Write-Ahead Log
¾ Binary PList
¾ Xml
¾ Binary PList
¾ Png
¾ Jpeg
¾ SQLite
¾ .pdf
¾ .docx
¾ .ppt
¾ .xlsx
262
file system without jail breaking a devic
XRY Complete is a commercial hardwa
tool manufactured by Micro Systemat
recovers live and deleted data from mo
forensically secure manner [12, 13].
Before moving towards investiga
following categories of iPad were popul
test data: Safari, Messages, Calendar, N
Videos, iTunes, Music, Photos, Mail, Co
few other applications such as Adobe
FileManager, and Temple Run. The purpo
was to locate the files containing artifacts
folders when the specific investigation was
In order to check data validity, hashe
for the data acquired from various tools. M
to birthday attack which makes it less secu
high probability that two different inputs c
values in our research. To complement
MD5, we have also used SHA-256. SHA-2
and collision resistant.
V. INVESTIGATION 1: DATA INTEGR
The first step in any forensic investig
evidence. Evidence is acceptable in court
integrity of data is preserved during the a
[1]. This investigation was carried to pro
acquisition techniques are reliable and
commercial tools. For the analysis and test
paper) a forensics workstation, data acquis
iPad were used.
A. Microsoft Windows 7 - 32 bit
In this investigation, iPad was first att a
Windows 7 machine. It was recognized as
Only the DCIM folder was visible to
Windows platform. DCIM folder contain s
the iPad. These pictures were acquired an
each picture were recorded.
B. Ubuntu 12.04.3 LTS
The iPad was mounted in a default op
mode to Ubuntu 12.04.3 LTS operati
different volumes were displayed: first v
iPad’ and second volume was ‘Documents
actual practice data resides in various i
One such directory which holds
/var/mobile/Media. Another directory
application.documents.is./var/mobile/Appl
er}/Documents. Artifacts associated w
directories were found when iPad was m
machine. User’s Video’s, Podcast’s, Boo
Photo’s, iTunes Data, Purchase’s and
/var/mobile/Media directory. Documen
applications like Adobe Reader and
applications.resides.in /var/mobile/Applica
/Documents. All these artifacts are a va
evidence for forensic examination.
Ubuntu gave access to many folder s
various files. Fig. 1 shows the volume n
which contains 12 folders. Out of these 12
Airfair, Books, DCIM, iTunes_Control
ively and accesses
ce [11]. However,
are/software based
tion (MSAB). It
obile devices in a
ation phase, the
lated with various
Notes, Reminders,
ontacts, Maps and
e Reader, Skype,
ose of this attempt
s in the respective
s performed.
es were calculated
MD5 is vulnerable
ure [14]. There is a
can get same hash
the outcomes of
256 is more secure
RITY ANALYSIS
gation is to gather
of law only if the
acquisition process
ove that free data
d comparable to
ts (throughout this
sition tools and an
ached to Microsoft
a portable device.
the examiner at
s pictures stored in
nd hash values of
ption of read/write
ing system. Two
volume was ‘MJ’s
s on MJ’s iPad’. In
iPad’s directories.
user data is
which contains
lications/{Identifi
with both these
mounted to Ubuntu
ok’s, Download’s,
Music exists in
nts residing in
d File Manager
ations/{Identifier}
aluable source of
s, populated with
named MJ’s iPad,
folders, 6 folders:
l, PhotoData and
PhotoStreamsData, are further
populated with files of differen
volume named “Documents o
several applications. Each a
containing documents of differ
Fig. 1. iPad’s user data fo
Fig. 2. iPad’s application docum
In this investigation, total
first volume and 4 documents
volume. Table III shows the p
different types of files residing
TAB
LIST OF FILE TYPES ACQUIR
Path
/var/mobile/Media/Books/
/var/mobile/Media/DCIM/
/var/mobile/Media/Downloads/
/var/mobile/Media/iTunes_Control/
/var/mobile/Media/PhotoData/
/var/mobile/Media/Photos/
/var/mobile/Media/PhotoStreamsData/
/var/mobile/Media/Safari/
/var/mobile/Applications/{Identifier}/D
ocuments
r subdivided. All folders are
nt types. Fig. 2. shows another
on MJ’s iPad”. This contains
application has a subfolder
ent types
ound via Ubuntu machine
ments found via Ubuntu machine
90 files were obtained from
s were obtained from second
path of main folders and the
in each relevant folder.
LE III.
RED FROM UBUNTU PLATFORM
Type
¾ SQLite
¾ Jpeg
¾ Png
¾ SQLite
¾ Blob
¾ Jpeg
¾ Mp4
¾ Mp3
¾ Blob
¾ Xml
¾ Tiff
¾ Jpeg
¾ SQLite
¾ SQLite Shared Memory
¾ SQLite Write-Ahead Log
¾ Binary PList
¾ Xml
¾ Binary PList
¾ Png
¾ Jpeg
¾ SQLite
¾ .pdf
¾ .docx
¾ .ppt
¾ .xlsx
262
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
In an effort to check data authenticity, hash values of each
file were separately logged. The files with extensions like,
Jpeg, Png, Tiff, Blob, Mp4, Mp3, Xml, Binary Plist,
SQLite, SQLite Shared Memory, SQLite Write-Ahead Log,
pdf, .docx, .ppt, .xlsx. are forensically important. Files like
property list (plist) and SQLite database were also found in
Media folder. Plist are Xml manifests, stores valuable data
related to iDevice applications such as Preferences,
Accounts, Bookmarks, System Configuration, Web Clips
along with history of Google maps and Safari. SQLite
database file mainly stores user’s data like voice mails, SMS
and E-mail messages, calendar events, call history, notes,
photos, address and Google maps data. [1].
C. libimobiledevice
libimobiledevice is an open source tool present in
Santoku which is used for live data acquisition from iPad.
Santoku is an open source platform, based on Linux
environment and includes features like development tools,
Penetration testing, Wireless analyzers, Device forensics
and Reverse engineering [15]. To get live data using
libimobiledevice on Santuko, iPad was first connected to
Santoku. Then the connectivity between iPad and Santuko
was checked; backup of device was created and the backup
file was extracted (unback) in order to make it browse-able.
These three steps were performed by running commands in
terminal window of libimobiledevice [16].
When unback operation was executed, numerous folders
named Keychains, Managed Preferences, Mobile,
MobileDevice, Root and Wireless were obtained. Each
folder contains various files. Hash values of 197 files were
extracted and separately logged.
D. XRY logical
XRY logical also retrieves live data from a mobile
device. For this, the iPad was mounted to a Windows 7
machine installed with XRY Complete. Logical extraction
was then performed via XRY. This commercial tool
provides a XRY file (.xry) containing numerous artifacts.
Out of these files/artifacts, only 90 files were successfully
extracted via Ubuntu machine. Hash values for these 90 files
were computed and recorded separately. Four application
documents that were extracted via Ubuntu were also
searched in XRY extraction. Three application documents
out of these four application documents were found in XRY
logical extraction. Hash values for these three documents
were computed and recorded. Similarly, files that were
extracted with libimobiledevice were also searched in XRY
extraction and hash values were noted individually. This
step was performed so as to compare data integrity of
files/artifacts extracted through Ubuntu and
libimobiledevice with those of XRY logical.
VI. INVESTIGATION 2: ANALYSIS OF FILE SIZES
VARIATION
In this experiment, five repeated logical and then
physical extractions were performed on an iPad using XRY
Complete. Each created XRY file (.xry) was separately
logged. It was noticed that each XRY file varied in size
(bytes) from another. Size of first XRY file varied from next
file either by increase or decrease of bytes. To explore the
differences, data of each XRY file was compared to
subsequent file by opening the files in XRY software. In
comparison, some variations were seen in terms of size,
created time, modified time or accessed time of files in a
particular XRY file. These changes compelled authors to
calculate hash values of modified files. Hash values were
found to differ as per the anticipation of changes. Table IV,
shows the files which were altered and have different hash
values in XRY logical or physical acquisition process.
TABLE IV.
MODIFIED FILES IN XRY ACQUISITION PROCESS
VII. DISCUSSION
In this research iOS version 5.1.1 has been considered
with the aim of discovering a reliable acquisition method for
/var/mobile/Media directory files, var/mobile/Applications
directory documents and folders like Keychains, Mobile,
Preferences, Root and Wireless; these folders contain user
data and application related information which is important
for a forensic investigation. By recognizing particular
directory and comprehending what it holds via the proposed
methods, the practice of collecting artifacts can begin
straightforwardly as we have verified the data authenticity
by computing the hash values. Table V describes
miscellaneous folders containing artifacts, obtained from
various acquisition techniques. Investigation 1 determined
that all iPad’s artifacts acquired from MJ’s iPad volume via
Ubuntu platform have given same hash values when
compared to the one extracted from XRY logical except
from one file named downloads.28.sqlite. This particular
database comprises of various known tables [17]. As shown
in table VI, persistent_manager_kind table was found to
differ in each extraction process. Three fields that are pid,
File Name Logical Acquisition File
Path
Physical
Acquisition File
path
AccountInformation
.plist
/private/var/mobile/Library/
DataAccess/
Data/mobile/Library/
DataAccess
com.apple.timed.plis
t
/private/var/mobile/Library/
Cache/
Data/mobile/Library/
Caches
com.apple.AutoWak
e.plist
/private/var/preferences/Syst
emConfiguration
Data/preferences/Syst
emConfiguration
com.apple.apsd.plist /private/var/mobile/Library/
Preferences/
Data/mobile/Library/P
references
com.apple.Accessibil
ity.plist
private/var/mobile/Library/P
references/
Data/mobile/Library/P
references
com.apple.MobileS
MS.plist
/private/var/Data/mobile/Lib
rary/Preferences/
Data/mobile/Library/P
references
com.apple.atc.plist /private/var/mobile/Library/
Preferences/
Data/mobile/Library/P
references
com.apple.wifi.plist private/var/preferences/Syst
emConfiguration/
Data/preferences/Syst
emConfiguration
com.apple.springboa
rd.plist
private/var/mobile/Library/P
references/
Data/mobile/Library/P
references
cache.plist /private/var/root/Library/Cac
hes/location/
Data/root/Library/Cac
hes/locationd
clients.plist Private/var/root/Library/Cac
he/location/
Data/root/Library/Cac
hes/locationd
downloads.28.sqlited
b
/private/var/mobile/Media/D
ownloads/
Data/mobile/Media/D
ownloads
ADDataStore.sqlited
b
/private/var/mobile/Library/
AggregateDictionary/
Data/mobile/Library/
AggregateDictionary
Envelope Index /private/var/mobile/Library/
Mail/
Data/mobile/Library
Mail
sms.db-shm /private/var/mobile/Library/
SMS/
Data/mobile/Library/S
MS/
sms.db-wal /private/var/mobile/Library/
SMS/
Data/mobile/Library/S
MS/
Cache.db /private/var/mobile/Library/
Caches/com.apple.aosnotify
d/
Data/mobile/Library/
Caches/com.apple.aos
notifyd/
Cache.db /private/var/mobile/Library/
Caches/com.apple.mobilema
il/
Data/mobile/Library/
Caches/com.apple.mo
bilemail/
Cache.db /private/var/mobile/Library/
Caches/com.apple.springboa
rd/
Data/mobile/Library/
Caches/com.apple.spri
ngboard/
263
file were separately logged. The files with extensions like,
Jpeg, Png, Tiff, Blob, Mp4, Mp3, Xml, Binary Plist,
SQLite, SQLite Shared Memory, SQLite Write-Ahead Log,
pdf, .docx, .ppt, .xlsx. are forensically important. Files like
property list (plist) and SQLite database were also found in
Media folder. Plist are Xml manifests, stores valuable data
related to iDevice applications such as Preferences,
Accounts, Bookmarks, System Configuration, Web Clips
along with history of Google maps and Safari. SQLite
database file mainly stores user’s data like voice mails, SMS
and E-mail messages, calendar events, call history, notes,
photos, address and Google maps data. [1].
C. libimobiledevice
libimobiledevice is an open source tool present in
Santoku which is used for live data acquisition from iPad.
Santoku is an open source platform, based on Linux
environment and includes features like development tools,
Penetration testing, Wireless analyzers, Device forensics
and Reverse engineering [15]. To get live data using
libimobiledevice on Santuko, iPad was first connected to
Santoku. Then the connectivity between iPad and Santuko
was checked; backup of device was created and the backup
file was extracted (unback) in order to make it browse-able.
These three steps were performed by running commands in
terminal window of libimobiledevice [16].
When unback operation was executed, numerous folders
named Keychains, Managed Preferences, Mobile,
MobileDevice, Root and Wireless were obtained. Each
folder contains various files. Hash values of 197 files were
extracted and separately logged.
D. XRY logical
XRY logical also retrieves live data from a mobile
device. For this, the iPad was mounted to a Windows 7
machine installed with XRY Complete. Logical extraction
was then performed via XRY. This commercial tool
provides a XRY file (.xry) containing numerous artifacts.
Out of these files/artifacts, only 90 files were successfully
extracted via Ubuntu machine. Hash values for these 90 files
were computed and recorded separately. Four application
documents that were extracted via Ubuntu were also
searched in XRY extraction. Three application documents
out of these four application documents were found in XRY
logical extraction. Hash values for these three documents
were computed and recorded. Similarly, files that were
extracted with libimobiledevice were also searched in XRY
extraction and hash values were noted individually. This
step was performed so as to compare data integrity of
files/artifacts extracted through Ubuntu and
libimobiledevice with those of XRY logical.
VI. INVESTIGATION 2: ANALYSIS OF FILE SIZES
VARIATION
In this experiment, five repeated logical and then
physical extractions were performed on an iPad using XRY
Complete. Each created XRY file (.xry) was separately
logged. It was noticed that each XRY file varied in size
(bytes) from another. Size of first XRY file varied from next
file either by increase or decrease of bytes. To explore the
differences, data of each XRY file was compared to
subsequent file by opening the files in XRY software. In
comparison, some variations were seen in terms of size,
created time, modified time or accessed time of files in a
particular XRY file. These changes compelled authors to
calculate hash values of modified files. Hash values were
found to differ as per the anticipation of changes. Table IV,
shows the files which were altered and have different hash
values in XRY logical or physical acquisition process.
TABLE IV.
MODIFIED FILES IN XRY ACQUISITION PROCESS
VII. DISCUSSION
In this research iOS version 5.1.1 has been considered
with the aim of discovering a reliable acquisition method for
/var/mobile/Media directory files, var/mobile/Applications
directory documents and folders like Keychains, Mobile,
Preferences, Root and Wireless; these folders contain user
data and application related information which is important
for a forensic investigation. By recognizing particular
directory and comprehending what it holds via the proposed
methods, the practice of collecting artifacts can begin
straightforwardly as we have verified the data authenticity
by computing the hash values. Table V describes
miscellaneous folders containing artifacts, obtained from
various acquisition techniques. Investigation 1 determined
that all iPad’s artifacts acquired from MJ’s iPad volume via
Ubuntu platform have given same hash values when
compared to the one extracted from XRY logical except
from one file named downloads.28.sqlite. This particular
database comprises of various known tables [17]. As shown
in table VI, persistent_manager_kind table was found to
differ in each extraction process. Three fields that are pid,
File Name Logical Acquisition File
Path
Physical
Acquisition File
path
AccountInformation
.plist
/private/var/mobile/Library/
DataAccess/
Data/mobile/Library/
DataAccess
com.apple.timed.plis
t
/private/var/mobile/Library/
Cache/
Data/mobile/Library/
Caches
com.apple.AutoWak
e.plist
/private/var/preferences/Syst
emConfiguration
Data/preferences/Syst
emConfiguration
com.apple.apsd.plist /private/var/mobile/Library/
Preferences/
Data/mobile/Library/P
references
com.apple.Accessibil
ity.plist
private/var/mobile/Library/P
references/
Data/mobile/Library/P
references
com.apple.MobileS
MS.plist
/private/var/Data/mobile/Lib
rary/Preferences/
Data/mobile/Library/P
references
com.apple.atc.plist /private/var/mobile/Library/
Preferences/
Data/mobile/Library/P
references
com.apple.wifi.plist private/var/preferences/Syst
emConfiguration/
Data/preferences/Syst
emConfiguration
com.apple.springboa
rd.plist
private/var/mobile/Library/P
references/
Data/mobile/Library/P
references
cache.plist /private/var/root/Library/Cac
hes/location/
Data/root/Library/Cac
hes/locationd
clients.plist Private/var/root/Library/Cac
he/location/
Data/root/Library/Cac
hes/locationd
downloads.28.sqlited
b
/private/var/mobile/Media/D
ownloads/
Data/mobile/Media/D
ownloads
ADDataStore.sqlited
b
/private/var/mobile/Library/
AggregateDictionary/
Data/mobile/Library/
AggregateDictionary
Envelope Index /private/var/mobile/Library/
Mail/
Data/mobile/Library
sms.db-shm /private/var/mobile/Library/
SMS/
Data/mobile/Library/S
MS/
sms.db-wal /private/var/mobile/Library/
SMS/
Data/mobile/Library/S
MS/
Cache.db /private/var/mobile/Library/
Caches/com.apple.aosnotify
d/
Data/mobile/Library/
Caches/com.apple.aos
notifyd/
Cache.db /private/var/mobile/Library/
Caches/com.apple.mobilema
il/
Data/mobile/Library/
Caches/com.apple.mo
bilemail/
Cache.db /private/var/mobile/Library/
Caches/com.apple.springboa
rd/
Data/mobile/Library/
Caches/com.apple.spri
ngboard/
263
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
manager_id and download_kind reside within
persistent_manager_kind table.
TABLE V.
COMPARISON OF FOLDERS OBTAINED FROM VARIOUS ACQUISITION
METHODS.
Device Microsoft
Windows 7
Ubuntu 12.04.3 LTS Libimobiledevice
iPad 1 - DCIM - AirFair
- AirLock
- Books
- DCIM
- Downloads
- iTunes_Controls
- PhotoData
- Photos
- PhotoStreamsData
- Purchases
- Recordings
- Safari
-Application
Documents.
- Keychains
-Managed
Preferences
- Mobile
- MobileDevice
- Root
- wireless
Analysis determined that integrity of downloads.28.sqlite
file was compromised because of the changes in data entry of
certain fields that are pid and download_kind. Table VI
shows that in every extraction two changes were observed.
One is that a new pid was assigned against each
download_kind data entry. Second, same thirteen data entries
in download_kind field randomly changed position in each
extraction process. It was thus concluded that whichever
method is adopted, integrity of this file will certainly be
compromised.
Evaluating the results of libimobiledevice, 8 files out of
197 files have given different hash values from logical and
physical XRY files. The 8 files are:
com.apple.itunesstored.2.sqlitedb,.sms.db,.applicationstate.p
list,.com.apple.Accessibility.plist,.com.apple.wifi.plist,.clien
ts.plist,.com.apple.MobileSMS.plist,.com.apple.springboard.
plist. libimobiledevice compromised integrity of 3 files i.e.
com.apple.itunesstored.2.sqlitedb,.sms.db.and.applicationsta
te.plist. However, XRY maintained integrity of these files.
As all consecutive XRY extractions gave same hash values
for these 3 files.
Further,.plists.named.com.apple.Accessibility,.com.appl
e.wifi,.clients,.com.apple.MobileSMS,.com.apple.springboa
rd were found to give same hash values in every alternate
extraction. This was observed for both, the freeware and the
commercial tool. Hence, concluding that integrity was not
preserved for commercial tool as well as freeware.
Another significant thing was observed regarding the
commercial tool. XRY logical failed to read the PDF
document which was easily accessed from “Documents on
MJ’s iPad” volume via Ubuntu platform.
Investigation 2 provided some interesting results. 19
files have not maintained data integrity during five
consecutive XRY logical and physical extractions as shown
in Table IV. These were database files and plist. Databases
integrity was compromised due to alteration of data residing
in various fields of tables. On the other hand some changes
were observed in sizes of files e.g. in fifth physical
extraction, com.apple.apsd.plist size fluctuated from 497
Bytes to 473 Bytes due to change in date. Though, the data
residing in the file was same as in previous four extractions.
But somehow data integrity was not preserved.
TABLE VI.
DIFFERENCES IN PERSISTENT_MANAGER_KIND TABLE.
Moreover, each XRY file contained one additional file as
compared from the previous extracted XRY file. However
there was no such file found in first created XRY file. This
file.is.a.ResetCounter.plist.found.at./private/var/logs/CrashR
eporter/ or Data/logs/CrashReporter. Difference in hash
values was detected, which was the consequence of different
string value assigned to Incident Identifier preset in
ResetCounter.plist file. The ResetCounter.plist was created
on a specific location each and every time the iPad was
restarted after XRY extraction. E.g. ResetCounter-2014-02-
01-160422 was found in second logical extraction. This
means that the file was created when the iPad was restarted
after the completion of first XRY logical extraction. 2014-
02-01 represents the creation date and 160422 is some
random number assigned to the file.
The results show that hundred percent data integrity is
not guaranteed whether free tool or commercial tool is used.
However, depending on the need (files to be extracted)
different extraction tools may be used.
The findings of our two investigations suggest that
investigator who is just interested in camera picture can
simply use Windows 7 operating system utility. As Ubuntu
platform and libimobiledevice methods provide subset of
similar reliable results comparable to XRY logical, so these
two free available tools can be used for live data extraction.
However, if investigator is interested in recovery of deleted
data, then XRY physical (or logical) can be utilized for
better results.
Artifacts Acquired from Ubuntu Platform
pid manager_id download_kind
-8697013296067968042 -3079926881866431783 videoPodcast
-7402569617997322243 -3079926881866431783 Book
-7329431502199691124 -3079926881866431783 Song
-6103358376161157882 -3079926881866431783 feature-movie
-1926500322170101766 -3079926881866431783 tv-episode
-843140266838312323 -3079926881866431783 Ebook
380133384971333366 6359578672334592279 Software
1965503006134192909 -3079926881866431783 Podcast
5210172721110099699 -3079926881866431783 Tone
5857462790415292211 -3079926881866431783 Ringtone
7441660511175830427 -3079926881866431783 Software
7875068394866816547 -3079926881866431783 music-video
7947198972459445051 -6895534963590278926 com.apple.MobileAsset
Artifacts Acquired from XRY
pid manager_id download_kind
-5096606683834414342 -3079926881866431783 tv-episode
-4519809471157545230 -3079926881866431783 videoPodcast
-4159226675442296094 -3079926881866431783 music-video
2396457548417753381 -3079926881866431783 Podcast
3765671117134938152 -3079926881866431783 feature-movie
3983873152646791978 -3079926881866431783 Software
5497865317862532018 6359578672334592279 Software
7155669364744334388 -3079926881866431783 Book
7514104786197330003 -3079926881866431783 Ringtone
7947198972459445051 -6895534963590278926 com.apple.MobileAsset
8304865426285548539 -3079926881866431783 Ebook
8884606758783125398 -3079926881866431783 Tone
9028490395618818294 -3079926881866431783 Song
264
persistent_manager_kind table.
TABLE V.
COMPARISON OF FOLDERS OBTAINED FROM VARIOUS ACQUISITION
METHODS.
Device Microsoft
Windows 7
Ubuntu 12.04.3 LTS Libimobiledevice
iPad 1 - DCIM - AirFair
- AirLock
- Books
- DCIM
- Downloads
- iTunes_Controls
- PhotoData
- Photos
- PhotoStreamsData
- Purchases
- Recordings
- Safari
-Application
Documents.
- Keychains
-Managed
Preferences
- Mobile
- MobileDevice
- Root
- wireless
Analysis determined that integrity of downloads.28.sqlite
file was compromised because of the changes in data entry of
certain fields that are pid and download_kind. Table VI
shows that in every extraction two changes were observed.
One is that a new pid was assigned against each
download_kind data entry. Second, same thirteen data entries
in download_kind field randomly changed position in each
extraction process. It was thus concluded that whichever
method is adopted, integrity of this file will certainly be
compromised.
Evaluating the results of libimobiledevice, 8 files out of
197 files have given different hash values from logical and
physical XRY files. The 8 files are:
com.apple.itunesstored.2.sqlitedb,.sms.db,.applicationstate.p
list,.com.apple.Accessibility.plist,.com.apple.wifi.plist,.clien
ts.plist,.com.apple.MobileSMS.plist,.com.apple.springboard.
plist. libimobiledevice compromised integrity of 3 files i.e.
com.apple.itunesstored.2.sqlitedb,.sms.db.and.applicationsta
te.plist. However, XRY maintained integrity of these files.
As all consecutive XRY extractions gave same hash values
for these 3 files.
Further,.plists.named.com.apple.Accessibility,.com.appl
e.wifi,.clients,.com.apple.MobileSMS,.com.apple.springboa
rd were found to give same hash values in every alternate
extraction. This was observed for both, the freeware and the
commercial tool. Hence, concluding that integrity was not
preserved for commercial tool as well as freeware.
Another significant thing was observed regarding the
commercial tool. XRY logical failed to read the PDF
document which was easily accessed from “Documents on
MJ’s iPad” volume via Ubuntu platform.
Investigation 2 provided some interesting results. 19
files have not maintained data integrity during five
consecutive XRY logical and physical extractions as shown
in Table IV. These were database files and plist. Databases
integrity was compromised due to alteration of data residing
in various fields of tables. On the other hand some changes
were observed in sizes of files e.g. in fifth physical
extraction, com.apple.apsd.plist size fluctuated from 497
Bytes to 473 Bytes due to change in date. Though, the data
residing in the file was same as in previous four extractions.
But somehow data integrity was not preserved.
TABLE VI.
DIFFERENCES IN PERSISTENT_MANAGER_KIND TABLE.
Moreover, each XRY file contained one additional file as
compared from the previous extracted XRY file. However
there was no such file found in first created XRY file. This
file.is.a.ResetCounter.plist.found.at./private/var/logs/CrashR
eporter/ or Data/logs/CrashReporter. Difference in hash
values was detected, which was the consequence of different
string value assigned to Incident Identifier preset in
ResetCounter.plist file. The ResetCounter.plist was created
on a specific location each and every time the iPad was
restarted after XRY extraction. E.g. ResetCounter-2014-02-
01-160422 was found in second logical extraction. This
means that the file was created when the iPad was restarted
after the completion of first XRY logical extraction. 2014-
02-01 represents the creation date and 160422 is some
random number assigned to the file.
The results show that hundred percent data integrity is
not guaranteed whether free tool or commercial tool is used.
However, depending on the need (files to be extracted)
different extraction tools may be used.
The findings of our two investigations suggest that
investigator who is just interested in camera picture can
simply use Windows 7 operating system utility. As Ubuntu
platform and libimobiledevice methods provide subset of
similar reliable results comparable to XRY logical, so these
two free available tools can be used for live data extraction.
However, if investigator is interested in recovery of deleted
data, then XRY physical (or logical) can be utilized for
better results.
Artifacts Acquired from Ubuntu Platform
pid manager_id download_kind
-8697013296067968042 -3079926881866431783 videoPodcast
-7402569617997322243 -3079926881866431783 Book
-7329431502199691124 -3079926881866431783 Song
-6103358376161157882 -3079926881866431783 feature-movie
-1926500322170101766 -3079926881866431783 tv-episode
-843140266838312323 -3079926881866431783 Ebook
380133384971333366 6359578672334592279 Software
1965503006134192909 -3079926881866431783 Podcast
5210172721110099699 -3079926881866431783 Tone
5857462790415292211 -3079926881866431783 Ringtone
7441660511175830427 -3079926881866431783 Software
7875068394866816547 -3079926881866431783 music-video
7947198972459445051 -6895534963590278926 com.apple.MobileAsset
Artifacts Acquired from XRY
pid manager_id download_kind
-5096606683834414342 -3079926881866431783 tv-episode
-4519809471157545230 -3079926881866431783 videoPodcast
-4159226675442296094 -3079926881866431783 music-video
2396457548417753381 -3079926881866431783 Podcast
3765671117134938152 -3079926881866431783 feature-movie
3983873152646791978 -3079926881866431783 Software
5497865317862532018 6359578672334592279 Software
7155669364744334388 -3079926881866431783 Book
7514104786197330003 -3079926881866431783 Ringtone
7947198972459445051 -6895534963590278926 com.apple.MobileAsset
8304865426285548539 -3079926881866431783 Ebook
8884606758783125398 -3079926881866431783 Tone
9028490395618818294 -3079926881866431783 Song
264

VIII. CONCLUSION
iDevices have achieved great success and gained
widespread popularity in short period of time. These devices
contain plenty of data which has forensic value. Preserving
the integrity of data throughout the acquisition process is an
important step in any digital forensic investigation. This
paper has discussed simple techniques to attain same subset
of iDevice’s artifacts which we can acquire from a
commercial tool. To assure authenticity of the proposed
methods, hashes of related files acquired from different
tools were calculated and compared. Furthermore, various
files, which were altered in consecutive XRY extractions,
have been identified and analyzed. The results can be used
by a forensic examiner to choose the appropriate tool for
data extraction keeping in view the requirements.
This research did not analyze jail breaking procedure. It
will be interesting to perform a jail breaking acquisition
technique on an iPad and compare this with a commercial
tool to determine what level of data integrity can be
obtained via jail breaking technique.
REFERENCES
[1] B. Iqbal, A. Iqbal and H. A. Obaid “A Novel Method of
iDevice(iPhone,iPad,iPod) Forensics without Jailbreaking,”
International Conference on Innovations in Information
Technology (IIT), 2012
[2] L. Gomez and J. Arnedo, “Universal, fast method for iPad
forensics imaging via USB adapter,” Fifth International
Conference on Innovative Mobile and Internet Services in
Ubiquitous Computing, 2011
[3] D. Abalenkovs et al., “Mobile Forensics: Comparison of
extraction and analyzing methods of iOS and Android,” 2012
[4] J. Zdziarski, iPhone Forensics: Recovering Evidence,Personal
Data, and Corporate Assets.: O’Reilly, 2008.
[5] A. K. Kubi, S. Saleem, and O. Popov, "Evaluation of Some
Tools for Extracting e-Evidence from Mobile Devices," 5th
International Conference on Application of Information and
Communication Technologies (AICT), Baku, 2011.
[6] J. Sigwald, “iphone-dataprotection,” http://code.google.com/
p/iphone-dataprotection/wiki/README (Current May 5,
2014)
[7] J. Sigwald, “Automatic SSH ramdisk creation and loading,”
http://msftguy.blogspot.com (Current May 5, 2014)
[8] E. Slivka, “Android and iOS Continue to Dominate
Smartphone Market as Windows Phone Shows Signs of Life,”
http://www.macrumors.com/2013/05/16/android-and-ios-
continue-to-dominate-smartphone-market-as-windows-phone-
shows-signs-of-life/ (Current May 5, 2014)
[9] D. Graziano, “Apple continues to make gains on Android,”
http://bgr.com/2013/06/04/ios-android-market-share-april-
2013/ (Current May 5, 2014)
[10] “What is Ubuntu?,” https://help.ubuntu.com/12.04/
installation-guide/powerpc/what-is-ubuntu.html (Current May
5, 2014)
[11] J. Auzu. “How to Manage iPhone/iPod/iPad on Linux,”
http://www.junauza.com/2012/07/how-to-manage-
iphoneipodipad-on-linux.html (Current May 5, 2014)
[12] MicroSystemation, “XRY COMPLETE,” http://www.msab.
com/xry/xry-complete (Current May 5, 2014)
[13] MicroSystemation, “USEFUL LINKS,” http://www.msab.
com/support/useful-links (Current May 5, 2014)
[14] B. D. Boer and A. Bosselaers “Collisions for the compression
function of MD5, Advances in Cryptology,” EUROCRYPT
’93. LNCS 765; p. 293-304, 1994
[15] “About Santuko,” https://santoku-linux.com/about-santoku
(Current May 5, 2014)
[16] “About Santuko,” https://santoku-linux.com/howto/mobile-
forensics/howto-create-a-logical-backup-of-an-ios-device-
using-libimobiledevice-on-santoku-linux (Current May 5,
2014)
[17] “downloads.28.sqlitedb - SQLite Database Catalog,” http://
www.filesig.co.uk/sqlitedatabasecatalog/downloads.28.sqlited
b%20SQLite%20Database%20%5b00001%5d.html (Current
May 5, 2014)
265
iDevices have achieved great success and gained
widespread popularity in short period of time. These devices
contain plenty of data which has forensic value. Preserving
the integrity of data throughout the acquisition process is an
important step in any digital forensic investigation. This
paper has discussed simple techniques to attain same subset
of iDevice’s artifacts which we can acquire from a
commercial tool. To assure authenticity of the proposed
methods, hashes of related files acquired from different
tools were calculated and compared. Furthermore, various
files, which were altered in consecutive XRY extractions,
have been identified and analyzed. The results can be used
by a forensic examiner to choose the appropriate tool for
data extraction keeping in view the requirements.
This research did not analyze jail breaking procedure. It
will be interesting to perform a jail breaking acquisition
technique on an iPad and compare this with a commercial
tool to determine what level of data integrity can be
obtained via jail breaking technique.
REFERENCES
[1] B. Iqbal, A. Iqbal and H. A. Obaid “A Novel Method of
iDevice(iPhone,iPad,iPod) Forensics without Jailbreaking,”
International Conference on Innovations in Information
Technology (IIT), 2012
[2] L. Gomez and J. Arnedo, “Universal, fast method for iPad
forensics imaging via USB adapter,” Fifth International
Conference on Innovative Mobile and Internet Services in
Ubiquitous Computing, 2011
[3] D. Abalenkovs et al., “Mobile Forensics: Comparison of
extraction and analyzing methods of iOS and Android,” 2012
[4] J. Zdziarski, iPhone Forensics: Recovering Evidence,Personal
Data, and Corporate Assets.: O’Reilly, 2008.
[5] A. K. Kubi, S. Saleem, and O. Popov, "Evaluation of Some
Tools for Extracting e-Evidence from Mobile Devices," 5th
International Conference on Application of Information and
Communication Technologies (AICT), Baku, 2011.
[6] J. Sigwald, “iphone-dataprotection,” http://code.google.com/
p/iphone-dataprotection/wiki/README (Current May 5,
2014)
[7] J. Sigwald, “Automatic SSH ramdisk creation and loading,”
http://msftguy.blogspot.com (Current May 5, 2014)
[8] E. Slivka, “Android and iOS Continue to Dominate
Smartphone Market as Windows Phone Shows Signs of Life,”
http://www.macrumors.com/2013/05/16/android-and-ios-
continue-to-dominate-smartphone-market-as-windows-phone-
shows-signs-of-life/ (Current May 5, 2014)
[9] D. Graziano, “Apple continues to make gains on Android,”
http://bgr.com/2013/06/04/ios-android-market-share-april-
2013/ (Current May 5, 2014)
[10] “What is Ubuntu?,” https://help.ubuntu.com/12.04/
installation-guide/powerpc/what-is-ubuntu.html (Current May
5, 2014)
[11] J. Auzu. “How to Manage iPhone/iPod/iPad on Linux,”
http://www.junauza.com/2012/07/how-to-manage-
iphoneipodipad-on-linux.html (Current May 5, 2014)
[12] MicroSystemation, “XRY COMPLETE,” http://www.msab.
com/xry/xry-complete (Current May 5, 2014)
[13] MicroSystemation, “USEFUL LINKS,” http://www.msab.
com/support/useful-links (Current May 5, 2014)
[14] B. D. Boer and A. Bosselaers “Collisions for the compression
function of MD5, Advances in Cryptology,” EUROCRYPT
’93. LNCS 765; p. 293-304, 1994
[15] “About Santuko,” https://santoku-linux.com/about-santoku
(Current May 5, 2014)
[16] “About Santuko,” https://santoku-linux.com/howto/mobile-
forensics/howto-create-a-logical-backup-of-an-ios-device-
using-libimobiledevice-on-santoku-linux (Current May 5,
2014)
[17] “downloads.28.sqlitedb - SQLite Database Catalog,” http://
www.filesig.co.uk/sqlitedatabasecatalog/downloads.28.sqlited
b%20SQLite%20Database%20%5b00001%5d.html (Current
May 5, 2014)
265
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
