IFN648 | Applied Cryptography
VerifiedAdded on 2022/08/26
|16
|2694
|27
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: IFN648 APPLIED CRYPTOGRAPHY
IFN648 APPLIED CRYPTOGRAPHY
Name of the Student
Name of the University
Author Note
IFN648 APPLIED CRYPTOGRAPHY
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
IFN648 APPLIED CRYPTOGRAPHY 1
Ciphertext 1 – Caesar cipher:
The Caesar Cipher which is also known as shift cipher is one of the simplest and
oldest forms for encrypting and decrypting messages. The Caesar cipher is basically a
substitution cipher where each and every letters of the original message will be replaced by
another letter according to a specific letter number of shifted down or shifted up in the
alphabet. For every letters in the alphabet, the position of the letter in the alphabet will be
taken say 4 for D, and then shift the number by the key number. Say, there is a key of +4 then
D will be H as well as the similar procedure will be applied to each of the letters in the text.
1. Create a frequency analysis chart for your ciphertext (include a screenshot of this chart in
your report).
Cipher text:
pcs httbts fjxit sxhpeedxcits lwtc hwt pchltgts cd lph hwt fjxit hjgt cd bpc lxiw p igpe lwd
ldjas v
Letter table:
0 A
1 B
2 C
3 D
4 E
5 F
6 G
7 H
8 I
9 J
10 K
11 L
12 M
13 N
14 O
15 P
16 Q
17 R
18 S
Ciphertext 1 – Caesar cipher:
The Caesar Cipher which is also known as shift cipher is one of the simplest and
oldest forms for encrypting and decrypting messages. The Caesar cipher is basically a
substitution cipher where each and every letters of the original message will be replaced by
another letter according to a specific letter number of shifted down or shifted up in the
alphabet. For every letters in the alphabet, the position of the letter in the alphabet will be
taken say 4 for D, and then shift the number by the key number. Say, there is a key of +4 then
D will be H as well as the similar procedure will be applied to each of the letters in the text.
1. Create a frequency analysis chart for your ciphertext (include a screenshot of this chart in
your report).
Cipher text:
pcs httbts fjxit sxhpeedxcits lwtc hwt pchltgts cd lph hwt fjxit hjgt cd bpc lxiw p igpe lwd
ldjas v
Letter table:
0 A
1 B
2 C
3 D
4 E
5 F
6 G
7 H
8 I
9 J
10 K
11 L
12 M
13 N
14 O
15 P
16 Q
17 R
18 S
2IFN648 APPLIED CRYPTOGRAPHY
19 T
20 U
21 V
22 W
23 X
24 Y
25 Z
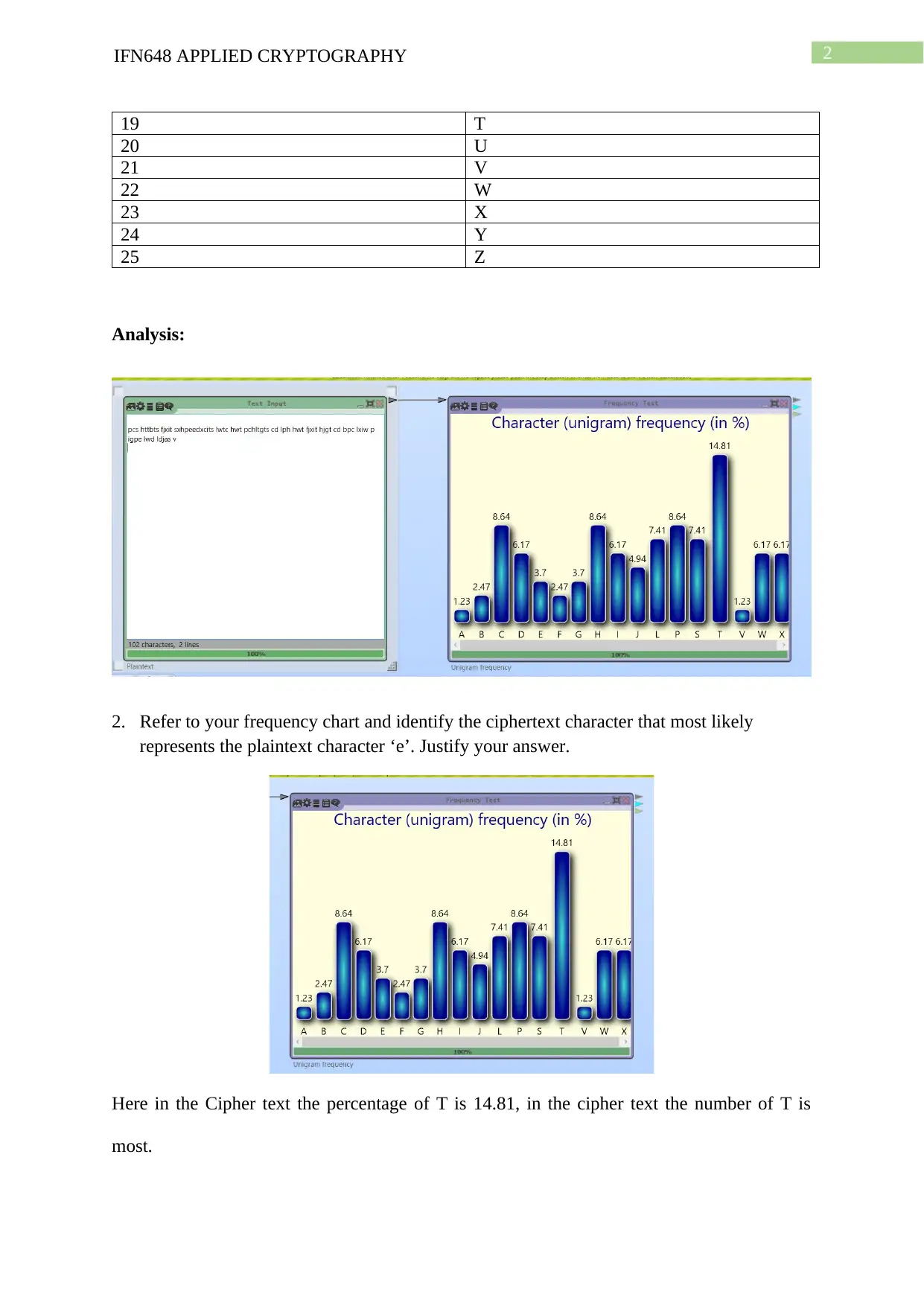
Analysis:
2. Refer to your frequency chart and identify the ciphertext character that most likely
represents the plaintext character ‘e’. Justify your answer.
Here in the Cipher text the percentage of T is 14.81, in the cipher text the number of T is
most.
19 T
20 U
21 V
22 W
23 X
24 Y
25 Z
Analysis:
2. Refer to your frequency chart and identify the ciphertext character that most likely
represents the plaintext character ‘e’. Justify your answer.
Here in the Cipher text the percentage of T is 14.81, in the cipher text the number of T is
most.
3IFN648 APPLIED CRYPTOGRAPHY
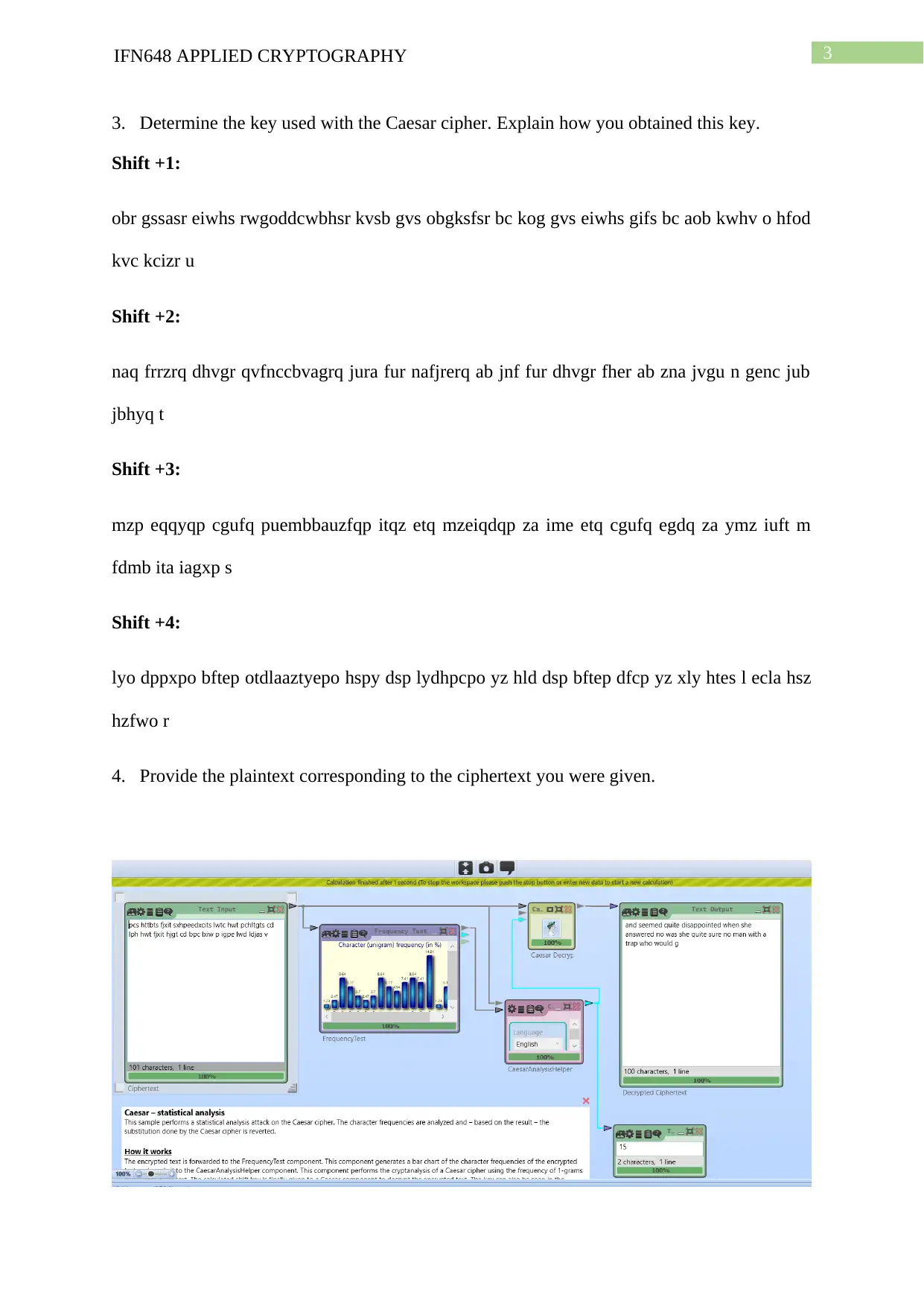
3. Determine the key used with the Caesar cipher. Explain how you obtained this key.
Shift +1:
obr gssasr eiwhs rwgoddcwbhsr kvsb gvs obgksfsr bc kog gvs eiwhs gifs bc aob kwhv o hfod
kvc kcizr u
Shift +2:
naq frrzrq dhvgr qvfnccbvagrq jura fur nafjrerq ab jnf fur dhvgr fher ab zna jvgu n genc jub
jbhyq t
Shift +3:
mzp eqqyqp cgufq puembbauzfqp itqz etq mzeiqdqp za ime etq cgufq egdq za ymz iuft m
fdmb ita iagxp s
Shift +4:
lyo dppxpo bftep otdlaaztyepo hspy dsp lydhpcpo yz hld dsp bftep dfcp yz xly htes l ecla hsz
hzfwo r
4. Provide the plaintext corresponding to the ciphertext you were given.
3. Determine the key used with the Caesar cipher. Explain how you obtained this key.
Shift +1:
obr gssasr eiwhs rwgoddcwbhsr kvsb gvs obgksfsr bc kog gvs eiwhs gifs bc aob kwhv o hfod
kvc kcizr u
Shift +2:
naq frrzrq dhvgr qvfnccbvagrq jura fur nafjrerq ab jnf fur dhvgr fher ab zna jvgu n genc jub
jbhyq t
Shift +3:
mzp eqqyqp cgufq puembbauzfqp itqz etq mzeiqdqp za ime etq cgufq egdq za ymz iuft m
fdmb ita iagxp s
Shift +4:
lyo dppxpo bftep otdlaaztyepo hspy dsp lydhpcpo yz hld dsp bftep dfcp yz xly htes l ecla hsz
hzfwo r
4. Provide the plaintext corresponding to the ciphertext you were given.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4IFN648 APPLIED CRYPTOGRAPHY
Using shift +15:
and seemed quite disappointed when she answered no was she quite sure no man with a trap
who would g
Plain text:
and seemed quite disappointed when she answered no was she quite sure no man with a trap
who would g
Row/column Transposition Cipher:
Unlike the Caesar cipher (simple substitution cipher) that switches each and every
letters of messages around, the transposition cipher works instead by messing with letter
orders for hiding the messages those have been sent. There are two types of transposition
cipher. One is column transposition cipher and the other one is row transposition cipher.
1. Create a frequency analysis chart for your ciphertext.
Cipher text:
n*f*ep*ennsesfr*il*khedti*cem*haa*hit**iAdaigaiTse***o*ennst*rnfuseh*ytcWnt*ogehud
*ynaeroiistiesheIn
Frequency analysis:
Using shift +15:
and seemed quite disappointed when she answered no was she quite sure no man with a trap
who would g
Plain text:
and seemed quite disappointed when she answered no was she quite sure no man with a trap
who would g
Row/column Transposition Cipher:
Unlike the Caesar cipher (simple substitution cipher) that switches each and every
letters of messages around, the transposition cipher works instead by messing with letter
orders for hiding the messages those have been sent. There are two types of transposition
cipher. One is column transposition cipher and the other one is row transposition cipher.
1. Create a frequency analysis chart for your ciphertext.
Cipher text:
n*f*ep*ennsesfr*il*khedti*cem*haa*hit**iAdaigaiTse***o*ennst*rnfuseh*ytcWnt*ogehud
*ynaeroiistiesheIn
Frequency analysis:
5IFN648 APPLIED CRYPTOGRAPHY
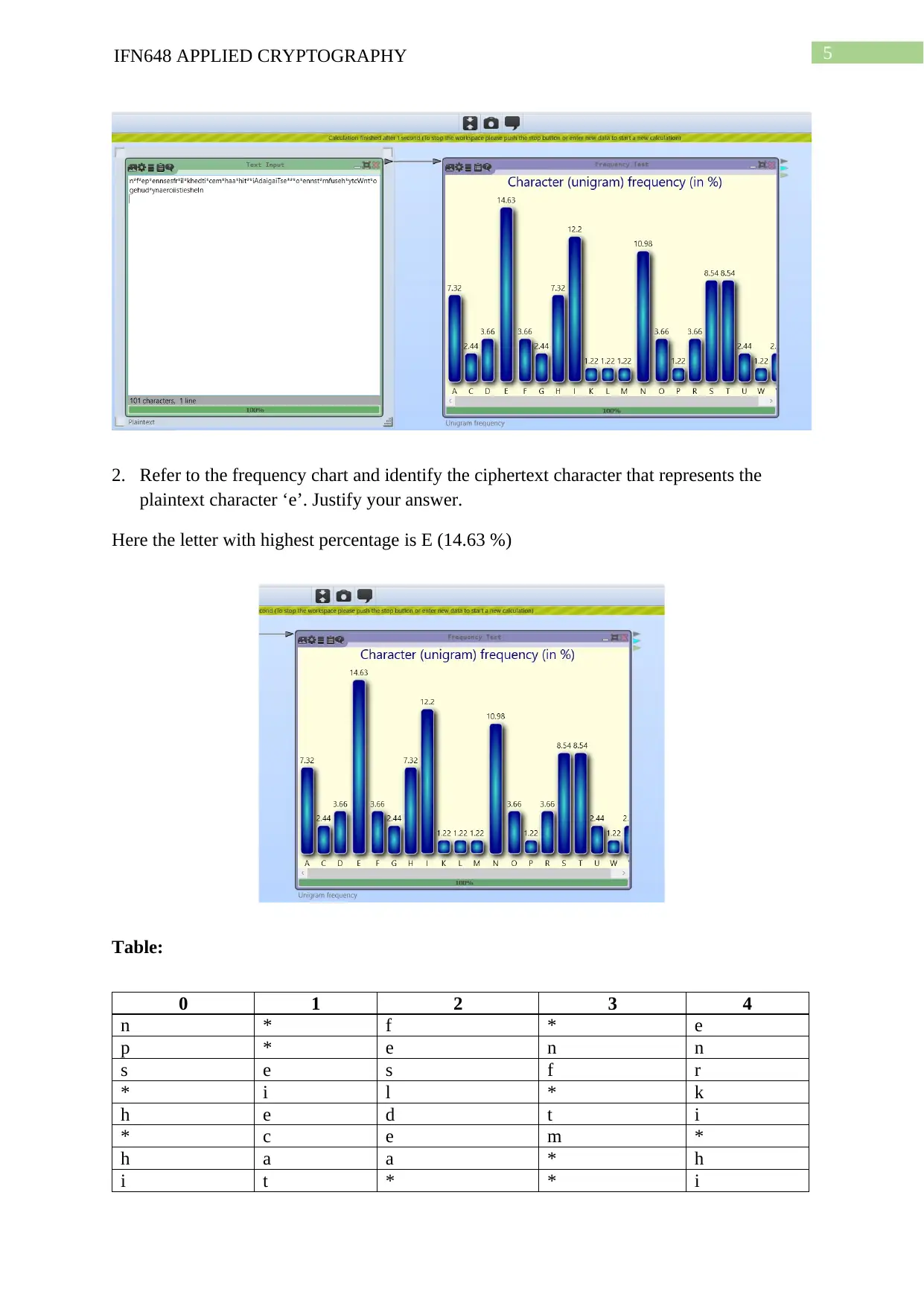
2. Refer to the frequency chart and identify the ciphertext character that represents the
plaintext character ‘e’. Justify your answer.
Here the letter with highest percentage is E (14.63 %)
Table:
0 1 2 3 4
n * f * e
p * e n n
s e s f r
* i l * k
h e d t i
* c e m *
h a a * h
i t * * i
2. Refer to the frequency chart and identify the ciphertext character that represents the
plaintext character ‘e’. Justify your answer.
Here the letter with highest percentage is E (14.63 %)
Table:
0 1 2 3 4
n * f * e
p * e n n
s e s f r
* i l * k
h e d t i
* c e m *
h a a * h
i t * * i
6IFN648 APPLIED CRYPTOGRAPHY
A d a i g
a i T s e
* * * o *
e n n s t
* r n f u
s e h * y
t c W n t
* o g e h
u d * y n
a e r o i
i s t i e
s h e I n
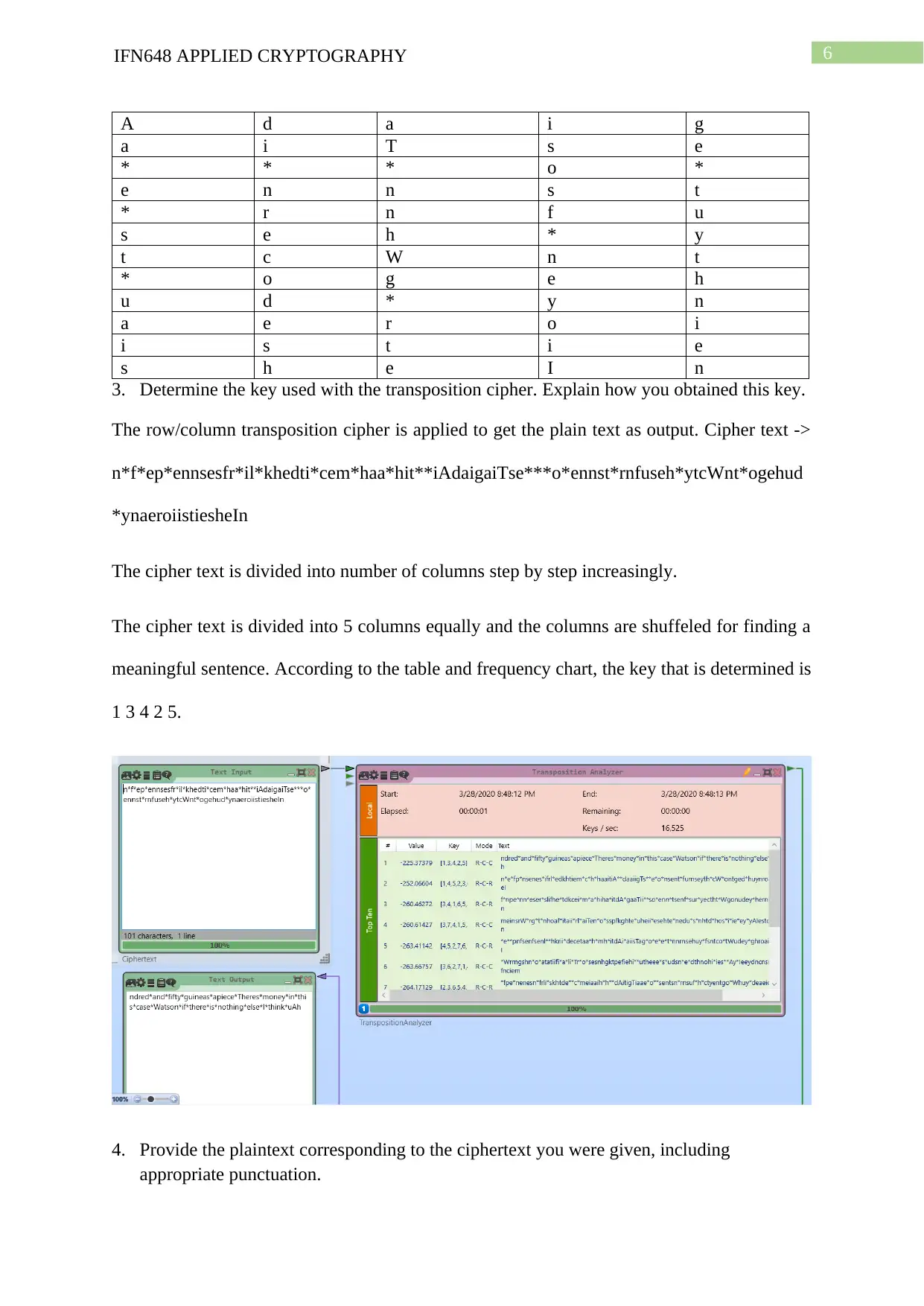
3. Determine the key used with the transposition cipher. Explain how you obtained this key.
The row/column transposition cipher is applied to get the plain text as output. Cipher text ->
n*f*ep*ennsesfr*il*khedti*cem*haa*hit**iAdaigaiTse***o*ennst*rnfuseh*ytcWnt*ogehud
*ynaeroiistiesheIn
The cipher text is divided into number of columns step by step increasingly.
The cipher text is divided into 5 columns equally and the columns are shuffeled for finding a
meaningful sentence. According to the table and frequency chart, the key that is determined is
1 3 4 2 5.
4. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
A d a i g
a i T s e
* * * o *
e n n s t
* r n f u
s e h * y
t c W n t
* o g e h
u d * y n
a e r o i
i s t i e
s h e I n
3. Determine the key used with the transposition cipher. Explain how you obtained this key.
The row/column transposition cipher is applied to get the plain text as output. Cipher text ->
n*f*ep*ennsesfr*il*khedti*cem*haa*hit**iAdaigaiTse***o*ennst*rnfuseh*ytcWnt*ogehud
*ynaeroiistiesheIn
The cipher text is divided into number of columns step by step increasingly.
The cipher text is divided into 5 columns equally and the columns are shuffeled for finding a
meaningful sentence. According to the table and frequency chart, the key that is determined is
1 3 4 2 5.
4. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7IFN648 APPLIED CRYPTOGRAPHY
Plain text:
A*hundred*and*fifty*guineas*apiece*theres*money*in*this*case*watson*if*there*is*nothi
ng*else*i*think
Vigenere cipher:
The vigenere cipher is basically one of the examples of polyalphabetic substitution cipher.
The polyalphabetic substitution cipher is almost similar to the mono alphabetic substitution
cipher. In vigenere cipher, for encryption and decryption, a table is used which is known as
vigenere table. The table is having each of the alphabets, 26 times in various rows.
Cipher text:
NHNFTJBQOKJHJYAWDWNLNBINZJWTBWFRUXGBBCHVXOACFLQQGWZDCAS
NBFYSWWUBSQZQHDDZQICZDCHVXOAQZTOOCLMSPNWQZOYLMOVZAWGV
UFIHJYFNTKFAPSDYASUVBSYDGLKTBKFDHCOYMUWHHGYWNFKY
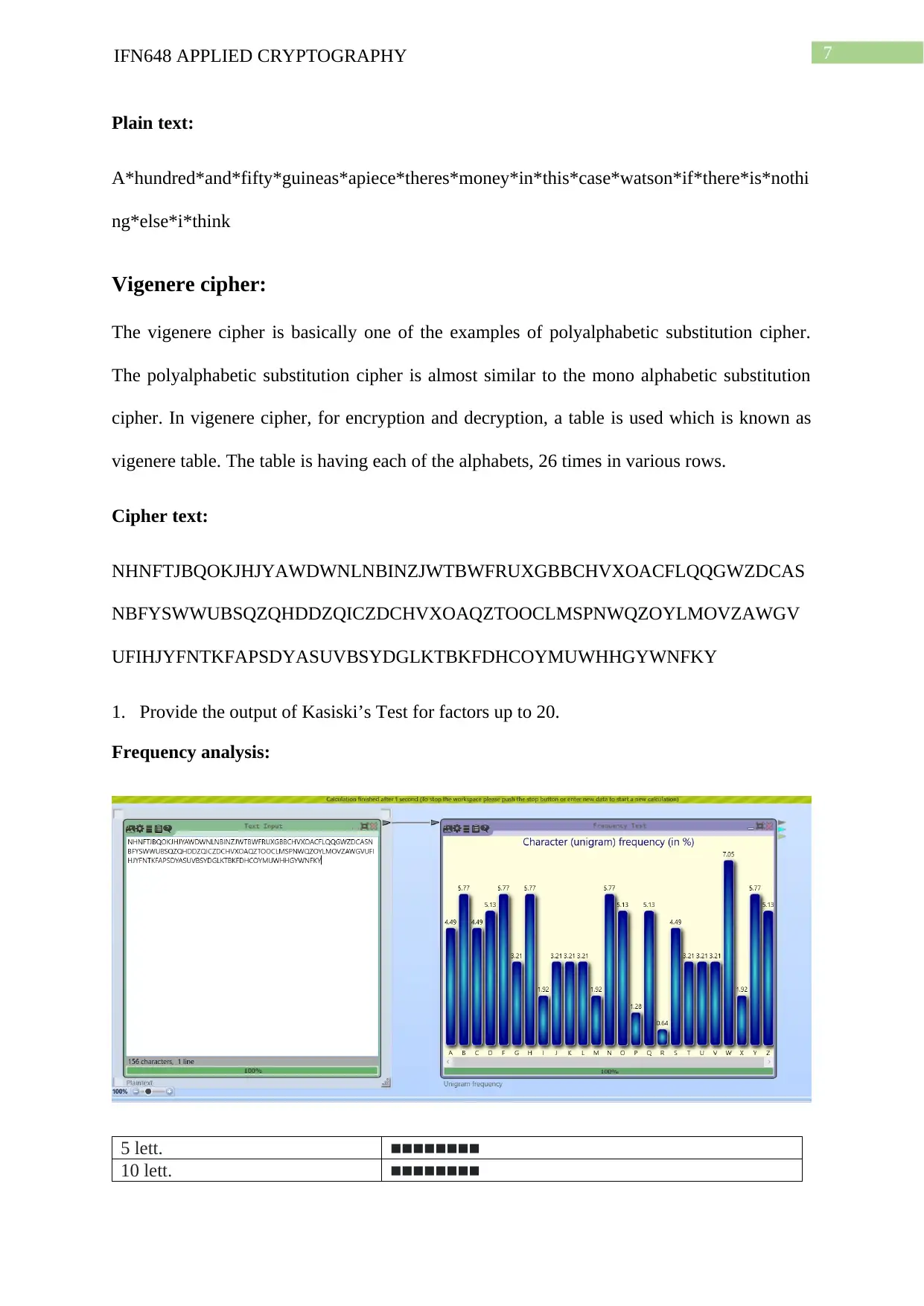
1. Provide the output of Kasiski’s Test for factors up to 20.
Frequency analysis:
5 lett. ■■■■■■■■
10 lett. ■■■■■■■■
Plain text:
A*hundred*and*fifty*guineas*apiece*theres*money*in*this*case*watson*if*there*is*nothi
ng*else*i*think
Vigenere cipher:
The vigenere cipher is basically one of the examples of polyalphabetic substitution cipher.
The polyalphabetic substitution cipher is almost similar to the mono alphabetic substitution
cipher. In vigenere cipher, for encryption and decryption, a table is used which is known as
vigenere table. The table is having each of the alphabets, 26 times in various rows.
Cipher text:
NHNFTJBQOKJHJYAWDWNLNBINZJWTBWFRUXGBBCHVXOACFLQQGWZDCAS
NBFYSWWUBSQZQHDDZQICZDCHVXOAQZTOOCLMSPNWQZOYLMOVZAWGV
UFIHJYFNTKFAPSDYASUVBSYDGLKTBKFDHCOYMUWHHGYWNFKY
1. Provide the output of Kasiski’s Test for factors up to 20.
Frequency analysis:
5 lett. ■■■■■■■■
10 lett. ■■■■■■■■

8IFN648 APPLIED CRYPTOGRAPHY
4 lett. ■■■■■■
8 lett. ■■■■■
2 lett. ■■■■■
20 lett. ■■■■
25 lett. ■■
13 lett. ■
17 lett. ■
16 lett. ■
14 lett. ■
15 lett. ■
11 lett. ■
9 lett. ■
7 lett. ■
6 lett. ■
3 lett. ■
12 lett. ■
24 lett.
28 lett.
27 lett.
26 lett.
1 lett.
23 lett.
22 lett.
21 lett.
19 lett.
18 lett.
29 lett.
Kasiski’s test:
2. Refer to the output of Kasiski’s Test and identify a probable key length.
4 lett. ■■■■■■
8 lett. ■■■■■
2 lett. ■■■■■
20 lett. ■■■■
25 lett. ■■
13 lett. ■
17 lett. ■
16 lett. ■
14 lett. ■
15 lett. ■
11 lett. ■
9 lett. ■
7 lett. ■
6 lett. ■
3 lett. ■
12 lett. ■
24 lett.
28 lett.
27 lett.
26 lett.
1 lett.
23 lett.
22 lett.
21 lett.
19 lett.
18 lett.
29 lett.
Kasiski’s test:
2. Refer to the output of Kasiski’s Test and identify a probable key length.

9IFN648 APPLIED CRYPTOGRAPHY
The possible key length is 5 as 5:6.
Vigenere table:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
A A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
B B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
C C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
D D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
E E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
F F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
G G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
H H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
I I J K L M N O P Q R S T U V W X Y Z A B C D E F G H
J J K L M N O P Q R S T U V W X Y Z A B C D E F G H I
K K L M N O P Q R S T U V W X Y Z A B C D E F G H I J
L L M N O P Q R S T U V W X Y Z A B C D E F G H I J K
M M N O P Q R S T U V W X Y Z A B C D E F G H I J K L
N N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
O O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
P P Q R S T U V W X Y Z A B C D E F G H I J K L M N O
Q Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
R R S T U V W X Y Z A B C D E F G H I J K L M N O P Q
S S T U V W X Y Z A B C D E F G H I J K L M N O P Q R
T T U V W X Y Z A B C D E F G H I J K L M N O P Q R S
U U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
V V W X Y Z A B C D E F G H I J K L M N O P Q R S T U
W W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
X X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
Y Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
Z Z A B C D E F G H I J K L M N O P Q R S T U V W X Y
3. Describe the process involved in breaking the Vigenere cipher once the key length is
determined.
The procedure is involving to break the vigenere cipher text. The cipher text is is vigenere
analysis used in CrpTool 2. The process is:
CrypTool -> Templates -> Vigenere Analysis
4. Apply this process to determine the key used with the Vigenere cipher. Clearly explain
how you obtained the key
The procedure is utilized for determining the key by the help is, Vigener Analysis .
The possible key length is 5 as 5:6.
Vigenere table:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
A A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
B B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
C C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
D D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
E E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
F F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
G G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
H H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
I I J K L M N O P Q R S T U V W X Y Z A B C D E F G H
J J K L M N O P Q R S T U V W X Y Z A B C D E F G H I
K K L M N O P Q R S T U V W X Y Z A B C D E F G H I J
L L M N O P Q R S T U V W X Y Z A B C D E F G H I J K
M M N O P Q R S T U V W X Y Z A B C D E F G H I J K L
N N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
O O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
P P Q R S T U V W X Y Z A B C D E F G H I J K L M N O
Q Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
R R S T U V W X Y Z A B C D E F G H I J K L M N O P Q
S S T U V W X Y Z A B C D E F G H I J K L M N O P Q R
T T U V W X Y Z A B C D E F G H I J K L M N O P Q R S
U U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
V V W X Y Z A B C D E F G H I J K L M N O P Q R S T U
W W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
X X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
Y Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
Z Z A B C D E F G H I J K L M N O P Q R S T U V W X Y
3. Describe the process involved in breaking the Vigenere cipher once the key length is
determined.
The procedure is involving to break the vigenere cipher text. The cipher text is is vigenere
analysis used in CrpTool 2. The process is:
CrypTool -> Templates -> Vigenere Analysis
4. Apply this process to determine the key used with the Vigenere cipher. Clearly explain
how you obtained the key
The procedure is utilized for determining the key by the help is, Vigener Analysis .
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10IFN648 APPLIED CRYPTOGRAPHY
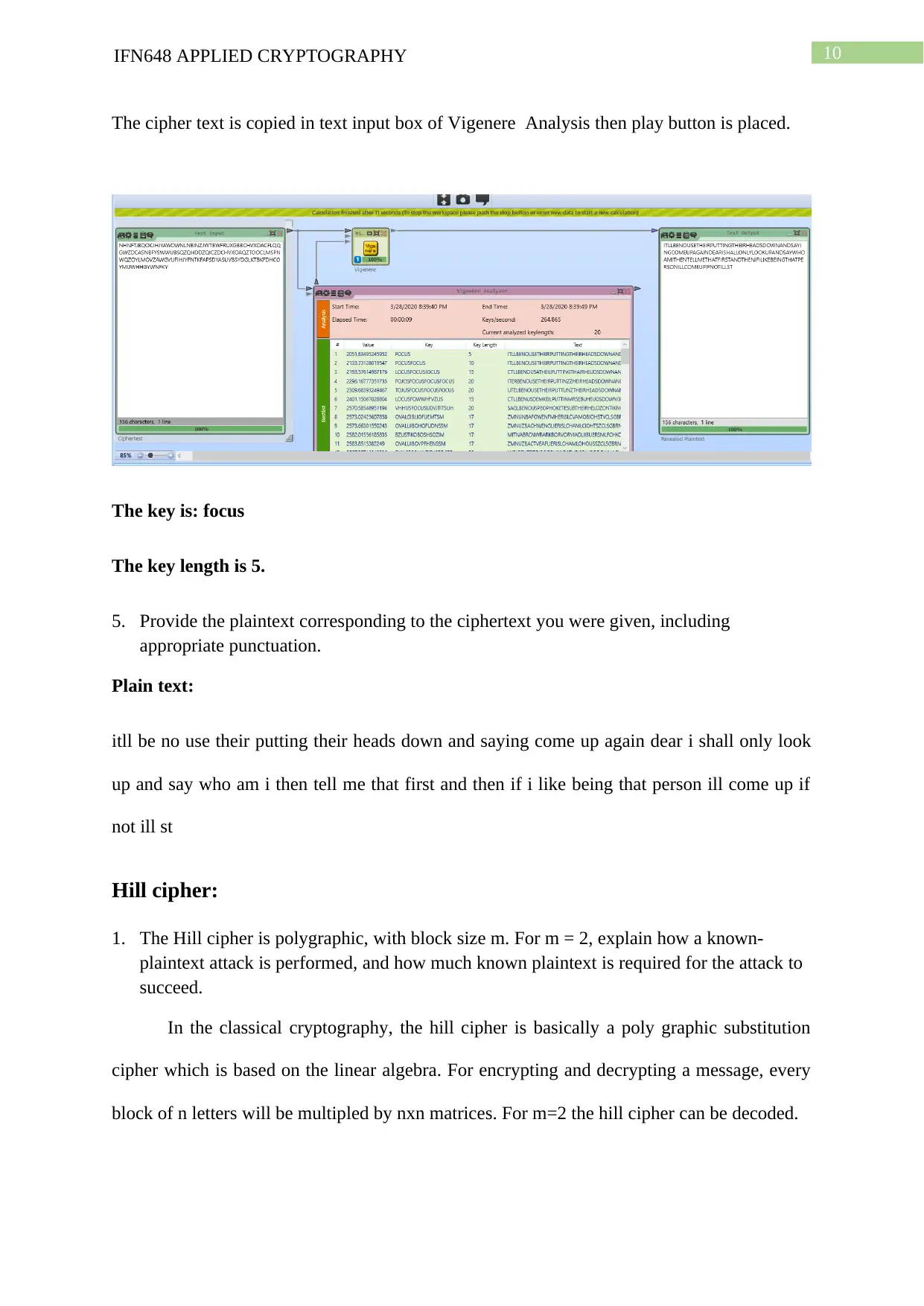
The cipher text is copied in text input box of Vigenere Analysis then play button is placed.
The key is: focus
The key length is 5.
5. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Plain text:
itll be no use their putting their heads down and saying come up again dear i shall only look
up and say who am i then tell me that first and then if i like being that person ill come up if
not ill st
Hill cipher:
1. The Hill cipher is polygraphic, with block size m. For m = 2, explain how a known-
plaintext attack is performed, and how much known plaintext is required for the attack to
succeed.
In the classical cryptography, the hill cipher is basically a poly graphic substitution
cipher which is based on the linear algebra. For encrypting and decrypting a message, every
block of n letters will be multipled by nxn matrices. For m=2 the hill cipher can be decoded.
The cipher text is copied in text input box of Vigenere Analysis then play button is placed.
The key is: focus
The key length is 5.
5. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Plain text:
itll be no use their putting their heads down and saying come up again dear i shall only look
up and say who am i then tell me that first and then if i like being that person ill come up if
not ill st
Hill cipher:
1. The Hill cipher is polygraphic, with block size m. For m = 2, explain how a known-
plaintext attack is performed, and how much known plaintext is required for the attack to
succeed.
In the classical cryptography, the hill cipher is basically a poly graphic substitution
cipher which is based on the linear algebra. For encrypting and decrypting a message, every
block of n letters will be multipled by nxn matrices. For m=2 the hill cipher can be decoded.
11IFN648 APPLIED CRYPTOGRAPHY
2. For a ciphertext-alone attack on a Hill cipher,some plaintext must be guessed.Assuming
the plaintext is in English,list some common digrams. Justify your choice of items.
Cipher text:
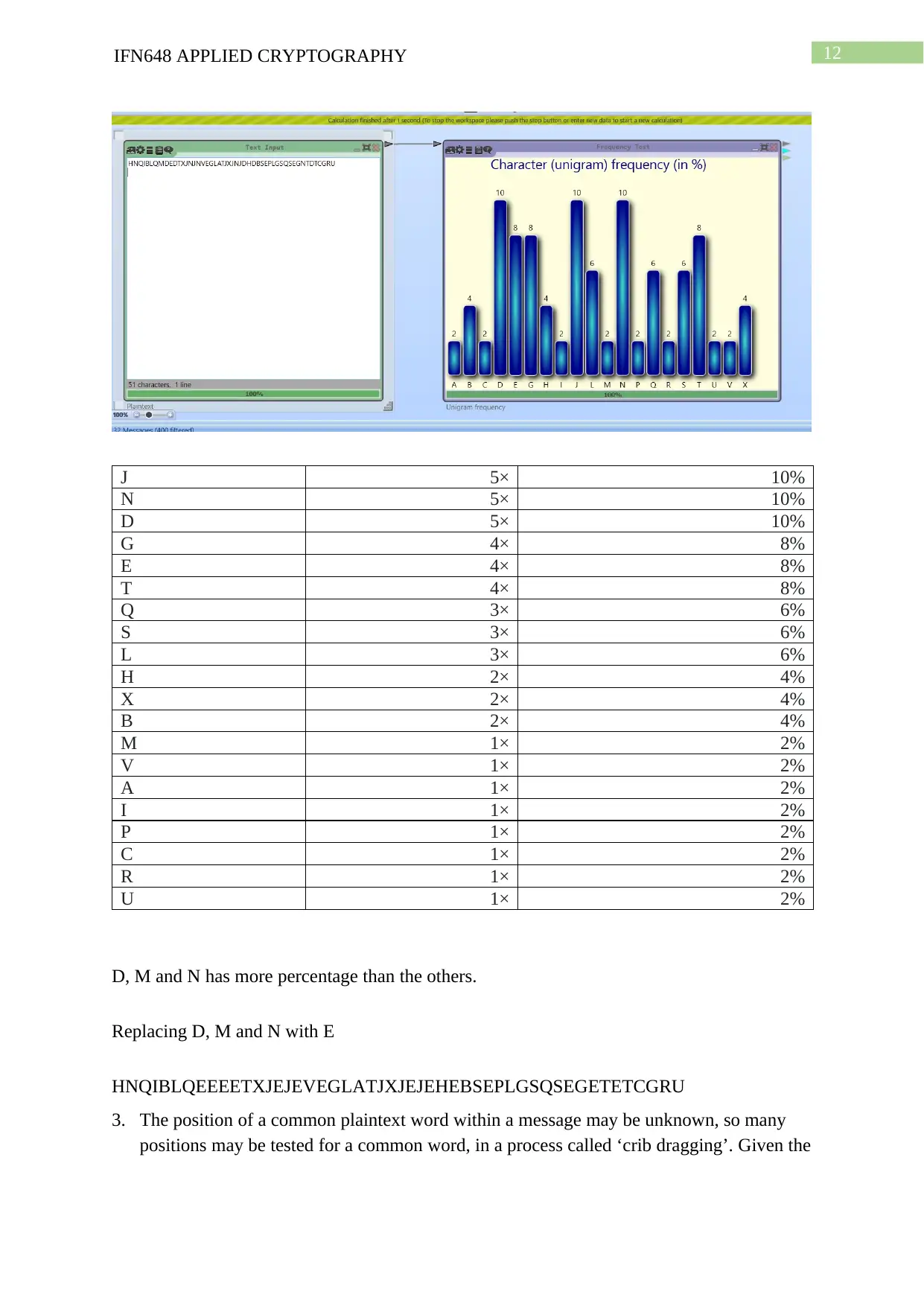
HNQIBLQMDEDTXJNJNVEGLATJXJNJDHDBSEPLGSQSEGNTDTCGRU
Frequency analysis of English letter:
Frequency analysis of cipher text:
2. For a ciphertext-alone attack on a Hill cipher,some plaintext must be guessed.Assuming
the plaintext is in English,list some common digrams. Justify your choice of items.
Cipher text:
HNQIBLQMDEDTXJNJNVEGLATJXJNJDHDBSEPLGSQSEGNTDTCGRU
Frequency analysis of English letter:
Frequency analysis of cipher text:
12IFN648 APPLIED CRYPTOGRAPHY
J 5× 10%
N 5× 10%
D 5× 10%
G 4× 8%
E 4× 8%
T 4× 8%
Q 3× 6%
S 3× 6%
L 3× 6%
H 2× 4%
X 2× 4%
B 2× 4%
M 1× 2%
V 1× 2%
A 1× 2%
I 1× 2%
P 1× 2%
C 1× 2%
R 1× 2%
U 1× 2%
D, M and N has more percentage than the others.
Replacing D, M and N with E
HNQIBLQEEEETXJEJEVEGLATJXJEJEHEBSEPLGSQSEGETETCGRU
3. The position of a common plaintext word within a message may be unknown, so many
positions may be tested for a common word, in a process called ‘crib dragging’. Given the
J 5× 10%
N 5× 10%
D 5× 10%
G 4× 8%
E 4× 8%
T 4× 8%
Q 3× 6%
S 3× 6%
L 3× 6%
H 2× 4%
X 2× 4%
B 2× 4%
M 1× 2%
V 1× 2%
A 1× 2%
I 1× 2%
P 1× 2%
C 1× 2%
R 1× 2%
U 1× 2%
D, M and N has more percentage than the others.
Replacing D, M and N with E
HNQIBLQEEEETXJEJEVEGLATJXJEJEHEBSEPLGSQSEGETETCGRU
3. The position of a common plaintext word within a message may be unknown, so many
positions may be tested for a common word, in a process called ‘crib dragging’. Given the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13IFN648 APPLIED CRYPTOGRAPHY
knowledge that your plaintext contains the word about, apply crib dragging to obtain
the encryption key matrix 1.
Crab dragging:
Replacing D, M and N with E
HNQIBLQEEEETXJEJEVEGLATJXJEJEHEBSEPLGSQSEGETETCGRU
The plain text given is ABOUT
Plaintext * Key = Ciphertext
Thus to find Key:
Key = ciphertext X plaintext ^ (-1) mod n
Considering:
HNQIB
ABOUT
It is known that A-Z = 0-25
Cipher text:
7 13 = H N
16 8 W N
Plain text:
0 1 = A B
14 20 O U
key = ((ciphertext) * (plaintext)^(-1)) mod n
Inverse of plaintext is
1 0
1 1
KEY=
7 13 1 0
Mod 26
1
knowledge that your plaintext contains the word about, apply crib dragging to obtain
the encryption key matrix 1.
Crab dragging:
Replacing D, M and N with E
HNQIBLQEEEETXJEJEVEGLATJXJEJEHEBSEPLGSQSEGETETCGRU
The plain text given is ABOUT
Plaintext * Key = Ciphertext
Thus to find Key:
Key = ciphertext X plaintext ^ (-1) mod n
Considering:
HNQIB
ABOUT
It is known that A-Z = 0-25
Cipher text:
7 13 = H N
16 8 W N
Plain text:
0 1 = A B
14 20 O U
key = ((ciphertext) * (plaintext)^(-1)) mod n
Inverse of plaintext is
1 0
1 1
KEY=
7 13 1 0
Mod 26
1

14IFN648 APPLIED CRYPTOGRAPHY
16 8 1 1
KEY =
6 7
13 16
4. Compute the corresponding decryption matrix.
7 13 = H N
16 8 Q I
KEY=
7 13 1 0
Mod 26
16 8 1 1
KEY =
6 7
13 16
5. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Cipher text:
HNQIBLQMDEDTXJNJNVEGLATJXJNJDHDBSEPLGSQSEGNTDTCGR
Key:
6 7
13 16
This is about secret message.
16 8 1 1
KEY =
6 7
13 16
4. Compute the corresponding decryption matrix.
7 13 = H N
16 8 Q I
KEY=
7 13 1 0
Mod 26
16 8 1 1
KEY =
6 7
13 16
5. Provide the plaintext corresponding to the ciphertext you were given, including
appropriate punctuation.
Cipher text:
HNQIBLQMDEDTXJNJNVEGLATJXJNJDHDBSEPLGSQSEGNTDTCGR
Key:
6 7
13 16
This is about secret message.

15IFN648 APPLIED CRYPTOGRAPHY
Bibliography:
Dawahdeh, Z. E., Yaakob, S. N., & bin Othman, R. R. (2018). A new image encryption
technique combining Elliptic Curve Cryptosystem with Hill Cipher. Journal of King
Saud University-Computer and Information Sciences, 30(3), 349-355.
Lubis, F. I., Simbolon, H. F. S., Batubara, T. P., & Sembiring, R. W. (2017). Combination of
Caesar Cipher Modification with Transposition Cipher. Advances in Science,
Technology and Engineering Systems Journal, 2(5), 22-25.
Oktaviana, B., & Siahaan, A. P. U. (2016). Three-Pass Protocol Implementation in Caesar
Cipher Classic Cryptography. IOSR J. Comput. Eng, 18(4), 26-29.
Saputra, I., Hasibuan, N. A., & Rahim, R. (2017). Vigenere cipher algorithm with grayscale
image key generator for secure text file. International Journal of Engineering
Research & Technology (IJERT), 6(1), 266-269.
Bibliography:
Dawahdeh, Z. E., Yaakob, S. N., & bin Othman, R. R. (2018). A new image encryption
technique combining Elliptic Curve Cryptosystem with Hill Cipher. Journal of King
Saud University-Computer and Information Sciences, 30(3), 349-355.
Lubis, F. I., Simbolon, H. F. S., Batubara, T. P., & Sembiring, R. W. (2017). Combination of
Caesar Cipher Modification with Transposition Cipher. Advances in Science,
Technology and Engineering Systems Journal, 2(5), 22-25.
Oktaviana, B., & Siahaan, A. P. U. (2016). Three-Pass Protocol Implementation in Caesar
Cipher Classic Cryptography. IOSR J. Comput. Eng, 18(4), 26-29.
Saputra, I., Hasibuan, N. A., & Rahim, R. (2017). Vigenere cipher algorithm with grayscale
image key generator for secure text file. International Journal of Engineering
Research & Technology (IJERT), 6(1), 266-269.
1 out of 16
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


