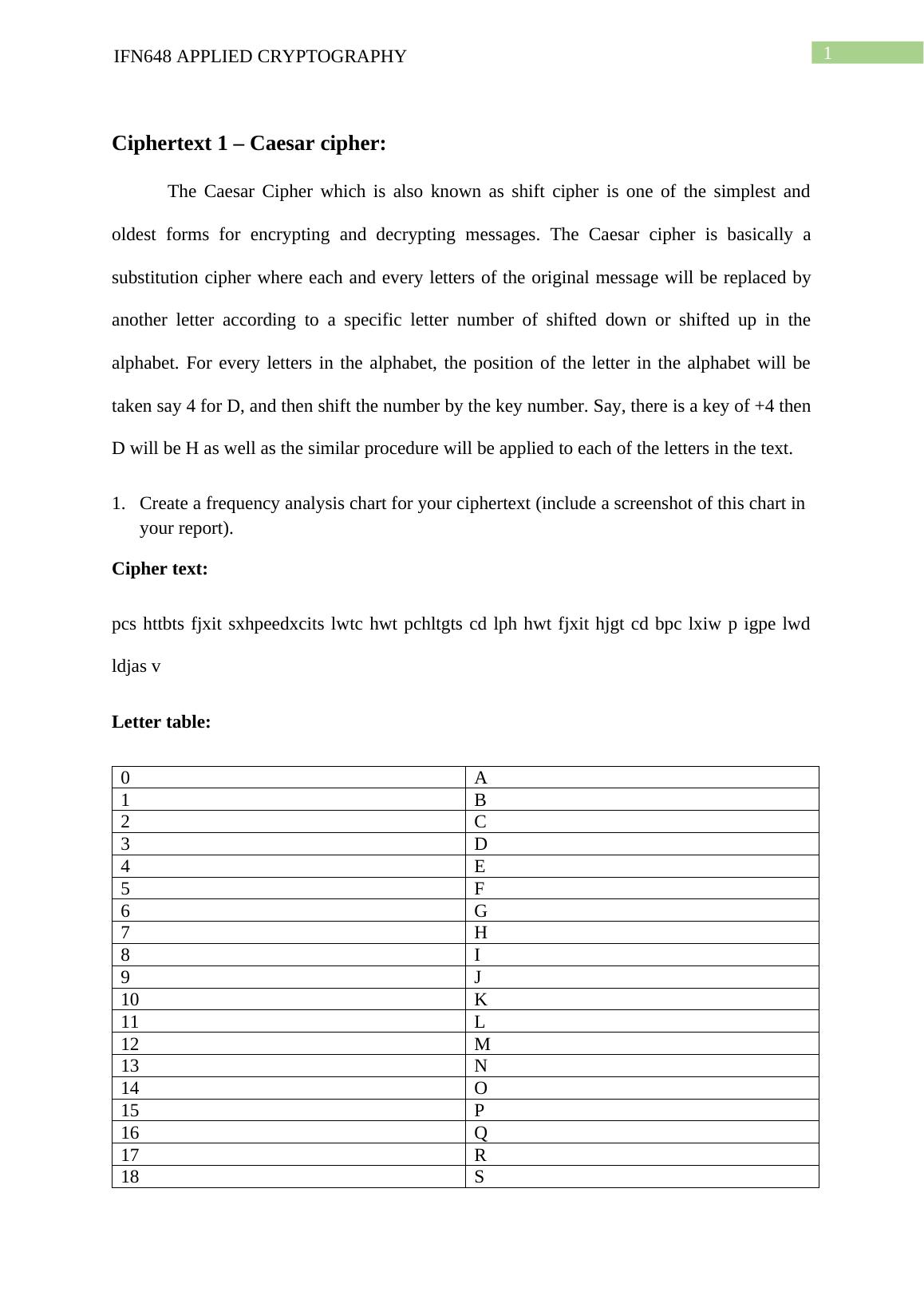
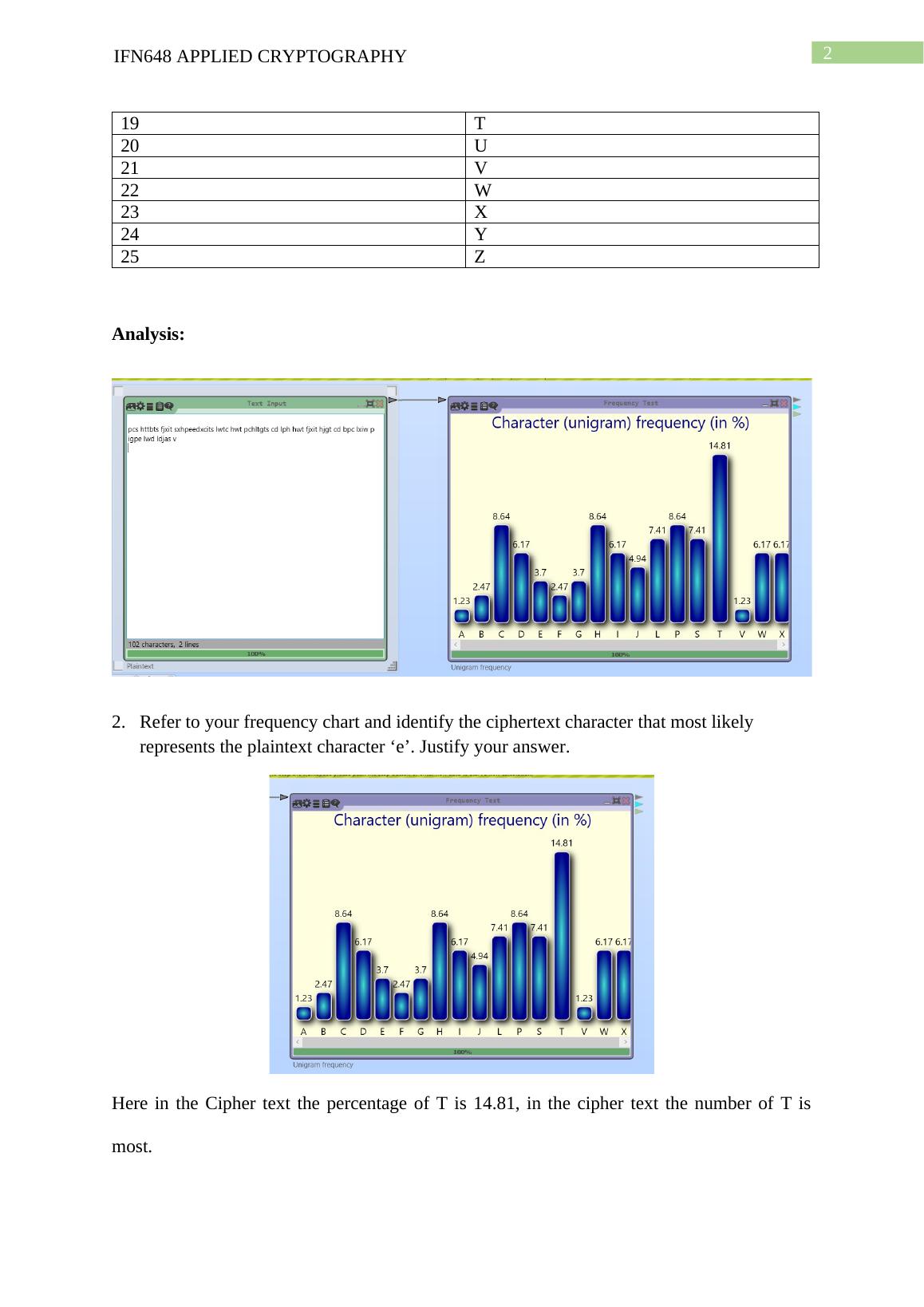
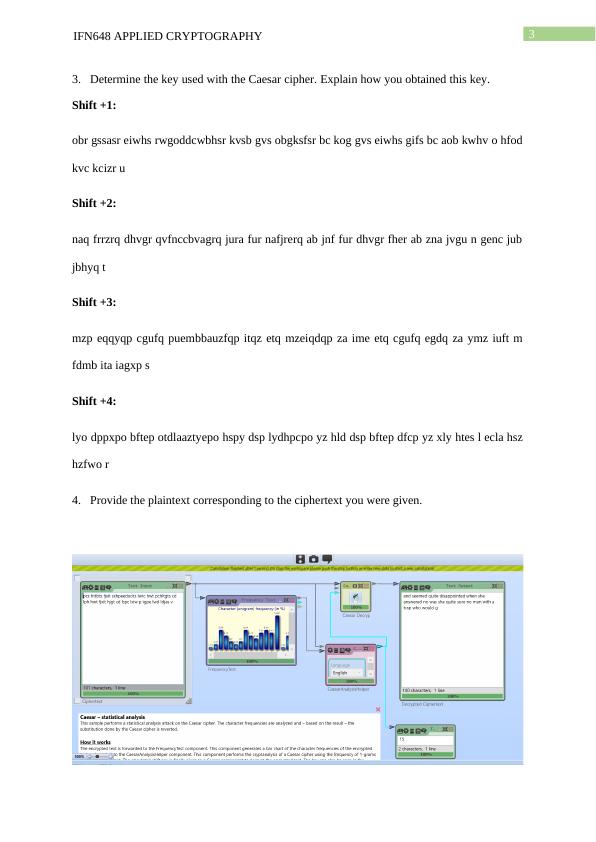
IFN648 | Applied Cryptography
Cryptanalysis of classic ciphers and recovering plaintexts. Submission of a report documenting the cryptanalytic process.
16 Pages2694 Words27 Views
Added on 2022-08-26
IFN648 | Applied Cryptography
Cryptanalysis of classic ciphers and recovering plaintexts. Submission of a report documenting the cryptanalytic process.
Added on 2022-08-26
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Applied Cryptography Assignment 2022
|17
|2555
|21
Cryptography and its Types
|32
|4897
|30
Security in computing and information technology
|9
|1672
|462