IMAT5262 Ethics & Professionalism in Computing Research 2022
VerifiedAdded on 2022/10/19
|25
|5169
|11
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

MSc
Information
Systems
Management
IMAT5262Research, Ethics &
Professionalism in
Computing
Assignment - Project Proposal
Child Protection on Internet
Pxxxxxxxx
De Montfort University
Information
Systems
Management
IMAT5262Research, Ethics &
Professionalism in
Computing
Assignment - Project Proposal
Child Protection on Internet
Pxxxxxxxx
De Montfort University
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
Abstract
In the past decades a matter of the use of internet by the children, has raised and enlarged to
be the famous matter covered by legal researchers, institutions, universities, as well as others.
The internet also happens to be good and most helpful learning tool, academic tool,
communicating tool as well as entertainment tool. In a case when the internet was the real
place there is not the parent in world who will let the children near this. The internet has
some positive effects as well as negative effects on the children. Their parents only have the
solution of this issue. When the previous research carried out on the utilisation of internet by
children, and the consequences of utilisation of internet by children; there is the lack of
research on what steps the parents are required to be taken. For that reason this research
proposal is made to conduct research in this area.
Key words
Children, Internet, Protection, Cyber-bullying, Parents
1
Abstract
In the past decades a matter of the use of internet by the children, has raised and enlarged to
be the famous matter covered by legal researchers, institutions, universities, as well as others.
The internet also happens to be good and most helpful learning tool, academic tool,
communicating tool as well as entertainment tool. In a case when the internet was the real
place there is not the parent in world who will let the children near this. The internet has
some positive effects as well as negative effects on the children. Their parents only have the
solution of this issue. When the previous research carried out on the utilisation of internet by
children, and the consequences of utilisation of internet by children; there is the lack of
research on what steps the parents are required to be taken. For that reason this research
proposal is made to conduct research in this area.
Key words
Children, Internet, Protection, Cyber-bullying, Parents
1

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
Contents
1. Background.......................................................................................................................3
2. Research questions............................................................................................................3
3. Literature Review.............................................................................................................3
4. Methodology Review.........................................................................................................3
5. Conclusion.........................................................................................................................4
6. References..........................................................................................................................4
APPENDICES..........................................................................................................................4
7. Appendices.........................................................................................................................4
8. Project Plan.......................................................................................................................4
9. Ethical Review Form........................................................................................................0
10. Consent Form.....................................................................................................................5
11. Pilot study...........................................................................................................................7
2
Contents
1. Background.......................................................................................................................3
2. Research questions............................................................................................................3
3. Literature Review.............................................................................................................3
4. Methodology Review.........................................................................................................3
5. Conclusion.........................................................................................................................4
6. References..........................................................................................................................4
APPENDICES..........................................................................................................................4
7. Appendices.........................................................................................................................4
8. Project Plan.......................................................................................................................4
9. Ethical Review Form........................................................................................................0
10. Consent Form.....................................................................................................................5
11. Pilot study...........................................................................................................................7
2

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
1. Background
The Internet is amazing for the children. The children may use the internet to conduct
research for the school report and for establishing the communication with teacher and
classmates or other children. The children can also play the interactive game on Internet.
However, the online access can also lead various risks such as the cyber harassment and
inappropriate contents.
By means of websites as well as apps where the children establish networking with others,
the marauders can pose as the children seeing to make the new friends. The marauders may
poke the children to share own data like contact number and residence. They can also
motivate the children to call them, seeing the contact number by caller-id. However, the
parents have concerns towards the use of Internet by their kids. The parents are required to be
careful of what the children observe and hear on Internet, with whom they get together, and
what their kids exchange data about themselves. Talk with your kids, use tools to protect
them, and keep an eye on their activities. This is a proposal to assess the children protection
on Internet.
2. Research question-
The research questions are discussed as below-
What are consequences of use of the Internet by children?
Which Internet safety laws are introduced to protect the children on Internet?
How to keep children safe on the Internet?
3
1. Background
The Internet is amazing for the children. The children may use the internet to conduct
research for the school report and for establishing the communication with teacher and
classmates or other children. The children can also play the interactive game on Internet.
However, the online access can also lead various risks such as the cyber harassment and
inappropriate contents.
By means of websites as well as apps where the children establish networking with others,
the marauders can pose as the children seeing to make the new friends. The marauders may
poke the children to share own data like contact number and residence. They can also
motivate the children to call them, seeing the contact number by caller-id. However, the
parents have concerns towards the use of Internet by their kids. The parents are required to be
careful of what the children observe and hear on Internet, with whom they get together, and
what their kids exchange data about themselves. Talk with your kids, use tools to protect
them, and keep an eye on their activities. This is a proposal to assess the children protection
on Internet.
2. Research question-
The research questions are discussed as below-
What are consequences of use of the Internet by children?
Which Internet safety laws are introduced to protect the children on Internet?
How to keep children safe on the Internet?
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
3. Literature Review
3.1 The issue of Children protection on Internet
In the present time, the children have completely integrated Internet in the interaction with
other children or person. They have followed some particular habits of communication that
have important impact on the role in the societies and the manner in which they may exercise
the rights. The Internet renders the various good chances for the children to spend the free
time, to discover, to get something new, to say about themselves and to affect the decision
making. In the other terms, it can say that the internet provides the better chance to enjoy the
right to get involvement. So far this is also the place where the children are more simply
uncovered to aggression, ill-treatment or mistreatment and so at the risks of having the rights
debased, in particular the rights to be secured and to live in the secure atmosphere, in
reference to the best interest. It is dangerous as well as worrying and filled with pornography
and marauders utilising inconceivable stages of dishonesty to prepare and ensnare young
persons. There is also a problem of cyber bullying on the internet. In this situation, the
parents are required to give extra attention to the children (DeNardis and Hackl, 2015).
3.2 Consequences of use of Internet by the children
More or less all the new media, involving radio, TV, computers as well as Internet, have been
considered the possible good and bad impact on the children. The children have been treated
as susceptible mediators of the media impact. Furthermore, a matter about the effects of
media upon kids has developed as media engage the larger part of the free time of children
and become accessible in all the schools (Shin and Kang, 2016).
In addition, the Internet is the main developmental tool or the academic tool for the parents
and the teacher. The parents are very much worried about the children because their children
spend most of the time on Internet. They are worried for negative effects of utilisation of
Internet on the kids. The problem of inappropriate content on Internet is one of the possible
4
3. Literature Review
3.1 The issue of Children protection on Internet
In the present time, the children have completely integrated Internet in the interaction with
other children or person. They have followed some particular habits of communication that
have important impact on the role in the societies and the manner in which they may exercise
the rights. The Internet renders the various good chances for the children to spend the free
time, to discover, to get something new, to say about themselves and to affect the decision
making. In the other terms, it can say that the internet provides the better chance to enjoy the
right to get involvement. So far this is also the place where the children are more simply
uncovered to aggression, ill-treatment or mistreatment and so at the risks of having the rights
debased, in particular the rights to be secured and to live in the secure atmosphere, in
reference to the best interest. It is dangerous as well as worrying and filled with pornography
and marauders utilising inconceivable stages of dishonesty to prepare and ensnare young
persons. There is also a problem of cyber bullying on the internet. In this situation, the
parents are required to give extra attention to the children (DeNardis and Hackl, 2015).
3.2 Consequences of use of Internet by the children
More or less all the new media, involving radio, TV, computers as well as Internet, have been
considered the possible good and bad impact on the children. The children have been treated
as susceptible mediators of the media impact. Furthermore, a matter about the effects of
media upon kids has developed as media engage the larger part of the free time of children
and become accessible in all the schools (Shin and Kang, 2016).
In addition, the Internet is the main developmental tool or the academic tool for the parents
and the teacher. The parents are very much worried about the children because their children
spend most of the time on Internet. They are worried for negative effects of utilisation of
Internet on the kids. The problem of inappropriate content on Internet is one of the possible
4

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
problems for the children. The children are capable to attain personal data via Internet
without mediation of young people in numerous settings involving homes, schools along with
libraries. For instance, the parents whose kids make the bombs by recovering data by the
Internet had to let children use Internet again after certain limitations because they worried
their children maybe computer uninformed. The contents pertaining to aggressive data, like
how to create the bomb, pornographic material, hate data are amongst those that may affect
the children harmfully (Livingstone and Third, 2017).
Further, the chat room can be the other Internet risk. The persons who are below the age of
twenty five were largest group who utilised the chat rooms frequently. Unexpectedly, the big
portion of the chatting interaction was with the persons whose recognition was not
recognized. Additionally, contacting stranger and establishing the friendship with strange
persons make the parents worried about the use of Internet by the children. In addition, since
children can come upon so many various types of pop up window for industrial
advertisement, the impact of these advertisements on the buying as well as consumer
behaviour can be another fear (Thompson, 2015).
3.3 Internet safety laws
The children are specifically at a risk on Internet (MacKinnon, et. al, 2015). The reason is
that it is not so easy to control the children by retrieving and seeing the inappropriate contents
there. Even though there are various children protection rules in USA like The Children’s
Online Privacy Protection Act, but those actually require to secure the children carefully
should act afar the government regulations. The central law, the Children's Online Privacy
Protection Act is very helpful to protect the children younger than thirteen while they are
online. The Children's Online Privacy Protection Act is passed for keeping anyone from
taking the personal data of children without the parents knowing about this and approving it
(Kleinman, 2015).
5
problems for the children. The children are capable to attain personal data via Internet
without mediation of young people in numerous settings involving homes, schools along with
libraries. For instance, the parents whose kids make the bombs by recovering data by the
Internet had to let children use Internet again after certain limitations because they worried
their children maybe computer uninformed. The contents pertaining to aggressive data, like
how to create the bomb, pornographic material, hate data are amongst those that may affect
the children harmfully (Livingstone and Third, 2017).
Further, the chat room can be the other Internet risk. The persons who are below the age of
twenty five were largest group who utilised the chat rooms frequently. Unexpectedly, the big
portion of the chatting interaction was with the persons whose recognition was not
recognized. Additionally, contacting stranger and establishing the friendship with strange
persons make the parents worried about the use of Internet by the children. In addition, since
children can come upon so many various types of pop up window for industrial
advertisement, the impact of these advertisements on the buying as well as consumer
behaviour can be another fear (Thompson, 2015).
3.3 Internet safety laws
The children are specifically at a risk on Internet (MacKinnon, et. al, 2015). The reason is
that it is not so easy to control the children by retrieving and seeing the inappropriate contents
there. Even though there are various children protection rules in USA like The Children’s
Online Privacy Protection Act, but those actually require to secure the children carefully
should act afar the government regulations. The central law, the Children's Online Privacy
Protection Act is very helpful to protect the children younger than thirteen while they are
online. The Children's Online Privacy Protection Act is passed for keeping anyone from
taking the personal data of children without the parents knowing about this and approving it
(Kleinman, 2015).
5

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
Further, it is required by the Children's Online Privacy Protection Act that websites should
explain privacy policy. The websites should get the consents of parents before the collection
as well as utilization of the personal data of children. The personal data can be name, contact
number, social security number and home address. In addition, the law restricts website from
wanting the children to render more personal data than essential to play the games and enter
the competition. With the help of these children protection rules, the parents would be able to
know that what options are available to them to secure the children from a darker side of
Internet and the inappropriate contents (Stuckey, 2018).
3.4 Protection of children against the use Internet
As with a real world, the Internet has its rough side, as well as this is very easy for the
children to get lost in this. The parents can find the solutions of this problem. It is required by
the parents to get involvement in the world of Internet. They are required to know about the
gym, swimming pool, play ground as well as tuition classes of the children. In addition, the
parents should decide how much time they are comfy with the kids being online and which
site they can go to (Montgomery, Chester and Milosevic, 2017). The parents may also post
the short list or the agreement next to a computer. It will be easy to ignore the confusion to
talk about the rules and their violation. The parents should tell them about the negative effects
of the use of internet. They should tell them to not to interact with unknown people and not to
give replies to the disturbing messages on various sites. The parents should also tell their kids
that they should not meet the person who became familiar at social networking sites on
Internet (Akdeniz, 2016).
Moreover, the parents can have regular check-up on all the computers and laptops of house.
They should not immediately rescind the human rights of the girls. They can take help of
internet service provider. If the ISP lacks that ability, then the parents should have certain
6
Further, it is required by the Children's Online Privacy Protection Act that websites should
explain privacy policy. The websites should get the consents of parents before the collection
as well as utilization of the personal data of children. The personal data can be name, contact
number, social security number and home address. In addition, the law restricts website from
wanting the children to render more personal data than essential to play the games and enter
the competition. With the help of these children protection rules, the parents would be able to
know that what options are available to them to secure the children from a darker side of
Internet and the inappropriate contents (Stuckey, 2018).
3.4 Protection of children against the use Internet
As with a real world, the Internet has its rough side, as well as this is very easy for the
children to get lost in this. The parents can find the solutions of this problem. It is required by
the parents to get involvement in the world of Internet. They are required to know about the
gym, swimming pool, play ground as well as tuition classes of the children. In addition, the
parents should decide how much time they are comfy with the kids being online and which
site they can go to (Montgomery, Chester and Milosevic, 2017). The parents may also post
the short list or the agreement next to a computer. It will be easy to ignore the confusion to
talk about the rules and their violation. The parents should tell them about the negative effects
of the use of internet. They should tell them to not to interact with unknown people and not to
give replies to the disturbing messages on various sites. The parents should also tell their kids
that they should not meet the person who became familiar at social networking sites on
Internet (Akdeniz, 2016).
Moreover, the parents can have regular check-up on all the computers and laptops of house.
They should not immediately rescind the human rights of the girls. They can take help of
internet service provider. If the ISP lacks that ability, then the parents should have certain
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
safe surfing option at hand on the browser. In addition of this, the parents should set the
restriction on the inappropriate sites on the Internet.
4. Methodology Review
There are so many approaches for the utilisation in the research study to give the correct
answers of the research questions. These research approaches contain the various kinds of
quantitative methodologies as well as qualitative technologies including interviews, surveys
as well as the questionnaires. These qualitative as well as quantitative methodologies have
certain benefits along with the drawbacks. Therefore, this is very important to ensure that
proper research methods are taken as per types of data that is going to be collected.
4.1. Interviews
The interview is very general qualitative methodology, which is used to gather information. It
may be described as the qualitative research technique, which involves “doing thorough
separate interview with the small number of the participants for discovering the viewpoints
upon the specific concepts, programs and the situations. It permits the investigator to collect
more data. It also makes able the investigator to ask applicants open-ended questionnaires. It
also allows them to go in detail and attains complete answers in comparison to the
quantitative methodologies like the questionnaire, which stop investigator from attaining the
comprehensive replies of the questions. The interviews have different types. Main categories
of the interviews are semi-structured interview, unstructured interviews as well as structured
interviews.
Further, there are some advantages as well as disadvantages of Interview research methods.
The major advantage of interview research method is that it can be useful to collect the
comprehensive as well as thorough information on the research matter to be covered. The
other benefit is that this method is very flexible. Due to the flexibility of this method, the
7
safe surfing option at hand on the browser. In addition of this, the parents should set the
restriction on the inappropriate sites on the Internet.
4. Methodology Review
There are so many approaches for the utilisation in the research study to give the correct
answers of the research questions. These research approaches contain the various kinds of
quantitative methodologies as well as qualitative technologies including interviews, surveys
as well as the questionnaires. These qualitative as well as quantitative methodologies have
certain benefits along with the drawbacks. Therefore, this is very important to ensure that
proper research methods are taken as per types of data that is going to be collected.
4.1. Interviews
The interview is very general qualitative methodology, which is used to gather information. It
may be described as the qualitative research technique, which involves “doing thorough
separate interview with the small number of the participants for discovering the viewpoints
upon the specific concepts, programs and the situations. It permits the investigator to collect
more data. It also makes able the investigator to ask applicants open-ended questionnaires. It
also allows them to go in detail and attains complete answers in comparison to the
quantitative methodologies like the questionnaire, which stop investigator from attaining the
comprehensive replies of the questions. The interviews have different types. Main categories
of the interviews are semi-structured interview, unstructured interviews as well as structured
interviews.
Further, there are some advantages as well as disadvantages of Interview research methods.
The major advantage of interview research method is that it can be useful to collect the
comprehensive as well as thorough information on the research matter to be covered. The
other benefit is that this method is very flexible. Due to the flexibility of this method, the
7

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
interviewer may regulate the questions and ask more information as progress of interviews.
On the other hand, the interviews may be time-taking for an investigator. The reason is that
the investigator has to write down answers as well as assess the result of information that is
not structured (Mneimneh, et. al, 2018).
4.2. Survey
The second method of collecting data is survey. The survey can be utilised in the research
project very effectively. This research method enables the investigator to ask the similar
queries to the larger group of participants so that to analyse any kind of pattern in data. The
survey is extensively admitted as well as utilised for the research purposes as they may be
circulated effortlessly with the help of various methods such as emails along with internet
(Converse, 2017).
Moreover, the key advantage of using survey method is that this can include the larger and
inclusive participants so that results are possible to be spokesperson of the generous people
that would permit to come to the comprehensive result. On the other hand, there are also
some disadvantages of this method. The main disadvantage of this method is that it does not
render thorough details on the investigated subject of research. The survey research method
mainly focuses on getting larger amount of the information in place of the detailed
information.
4.3. Questionnaires
Other quantitative research methodology is questionnaires. The questionnaires are
the research tool that contains the series of questions to collect the data from participants.
The questionnaire is also sharply restricted by the facts that the members should be capable to
read question as well as give the replies to them. This research method is very useful in
gathering information from the larger number of the participants. It is also defined as pre
8
interviewer may regulate the questions and ask more information as progress of interviews.
On the other hand, the interviews may be time-taking for an investigator. The reason is that
the investigator has to write down answers as well as assess the result of information that is
not structured (Mneimneh, et. al, 2018).
4.2. Survey
The second method of collecting data is survey. The survey can be utilised in the research
project very effectively. This research method enables the investigator to ask the similar
queries to the larger group of participants so that to analyse any kind of pattern in data. The
survey is extensively admitted as well as utilised for the research purposes as they may be
circulated effortlessly with the help of various methods such as emails along with internet
(Converse, 2017).
Moreover, the key advantage of using survey method is that this can include the larger and
inclusive participants so that results are possible to be spokesperson of the generous people
that would permit to come to the comprehensive result. On the other hand, there are also
some disadvantages of this method. The main disadvantage of this method is that it does not
render thorough details on the investigated subject of research. The survey research method
mainly focuses on getting larger amount of the information in place of the detailed
information.
4.3. Questionnaires
Other quantitative research methodology is questionnaires. The questionnaires are
the research tool that contains the series of questions to collect the data from participants.
The questionnaire is also sharply restricted by the facts that the members should be capable to
read question as well as give the replies to them. This research method is very useful in
gathering information from the larger number of the participants. It is also defined as pre
8

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
arranged questionnaires collected in pre defined orders. The questionnaires make able the
investigator to ask the members various questions. In this way, it allows the investigator to
assess and interpret the data easily.
Furthermore, a questionnaire may be ended without the researcher being present on time. The
questionnaire can be regulated by an investigator where the questions can be asked by the
audience to complete the questionnaires. There are various benefits as well as drawbacks of
this research method. The main benefit of this method of research is that this is very simpler
for the participants to complete the questionnaires. In addition of this, it also makes able the
investigator to gather the information from the larger number of participants that also creates
it simpler to assess the information. On the other hand, the shortcoming of this method is that
it cannot provide the replies with honesty. In this way, there can be possibility that the
collected data are not reliable (Panneerselvam, 2014).
4.4. Case Study
The case study is also useful technique to conduct research study. A case study is considered
as the experiential inquiry as well as research strategy to make the investigation of fact within
a framework of real life. The investigator may make concentration on some particular things
or the specific situations with the help of case study. These particular things and situations
cover the company, a division, the information system or the development task, and others.
Further, the cast study is applied by utilising the various approaches such as questionnaire,
observation, as well as interview. This research method is capable to conduct huge quantity
of information that is then required to be assessed as well as recognize it so that the
investigator may draw the significant result on the basis what the it is targeting the research.
This research methodology is set of various types involving setting case studies in usual
surroundings, as well as utilisation of different means or approaches for collecting more data.
9
arranged questionnaires collected in pre defined orders. The questionnaires make able the
investigator to ask the members various questions. In this way, it allows the investigator to
assess and interpret the data easily.
Furthermore, a questionnaire may be ended without the researcher being present on time. The
questionnaire can be regulated by an investigator where the questions can be asked by the
audience to complete the questionnaires. There are various benefits as well as drawbacks of
this research method. The main benefit of this method of research is that this is very simpler
for the participants to complete the questionnaires. In addition of this, it also makes able the
investigator to gather the information from the larger number of participants that also creates
it simpler to assess the information. On the other hand, the shortcoming of this method is that
it cannot provide the replies with honesty. In this way, there can be possibility that the
collected data are not reliable (Panneerselvam, 2014).
4.4. Case Study
The case study is also useful technique to conduct research study. A case study is considered
as the experiential inquiry as well as research strategy to make the investigation of fact within
a framework of real life. The investigator may make concentration on some particular things
or the specific situations with the help of case study. These particular things and situations
cover the company, a division, the information system or the development task, and others.
Further, the cast study is applied by utilising the various approaches such as questionnaire,
observation, as well as interview. This research method is capable to conduct huge quantity
of information that is then required to be assessed as well as recognize it so that the
investigator may draw the significant result on the basis what the it is targeting the research.
This research methodology is set of various types involving setting case studies in usual
surroundings, as well as utilisation of different means or approaches for collecting more data.
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
In addition of this, the case studies may be of 3 kinds such as explanatory study, exploratory
study as well as descriptive study. There are various advantages as well as disadvantages of
using the case studies on particular things or particular situations. The main advantage is that
this method makes able the investigator to handle the situation, which is very complex. This
method may be rigid particularly while the specific feature is being considered in the more
details. On the other hand, the disadvantage of utilising the case study for gathering
information is that this may take the longer time. The other shortcoming is that this research
method can be tough to agree the admittance to individuals, settings as well as the documents
that are necessarily required for gathering data (Nobel and Smith, 2014).
4.5. Focus Group
The focus group is research methodology cover under the category of qualitative research
methodologies. The focus group is also considered as the group interview. The focus groups
are very helpful in assessing the matters from the inside out. It considers various approaches
to interview methodologies explained above where all the people are interviewed
independently. In addition, the focus groups make able the investigator to make gathering of
members of the group together. It permits the members of the group to have interaction with
each other and conduct the group discussion on a provided subject. It is also helpful for the
investigator to gather more insight that can take place on a subject that is being explored that
cannot have been recognised before (Day, 2018).
Also, there are various benefits of this research methodology. The main benefit is that this
method helps the investigator to gather general views of a subject. It permits them to come
with theme that they can desire to cover in a discussion of focus group. There are also some
drawbacks of this method. The main drawback is that there are certain members who do not
want to put across the personal opinions in front of the people in a group (Ranganathan,
2017).
10
In addition of this, the case studies may be of 3 kinds such as explanatory study, exploratory
study as well as descriptive study. There are various advantages as well as disadvantages of
using the case studies on particular things or particular situations. The main advantage is that
this method makes able the investigator to handle the situation, which is very complex. This
method may be rigid particularly while the specific feature is being considered in the more
details. On the other hand, the disadvantage of utilising the case study for gathering
information is that this may take the longer time. The other shortcoming is that this research
method can be tough to agree the admittance to individuals, settings as well as the documents
that are necessarily required for gathering data (Nobel and Smith, 2014).
4.5. Focus Group
The focus group is research methodology cover under the category of qualitative research
methodologies. The focus group is also considered as the group interview. The focus groups
are very helpful in assessing the matters from the inside out. It considers various approaches
to interview methodologies explained above where all the people are interviewed
independently. In addition, the focus groups make able the investigator to make gathering of
members of the group together. It permits the members of the group to have interaction with
each other and conduct the group discussion on a provided subject. It is also helpful for the
investigator to gather more insight that can take place on a subject that is being explored that
cannot have been recognised before (Day, 2018).
Also, there are various benefits of this research methodology. The main benefit is that this
method helps the investigator to gather general views of a subject. It permits them to come
with theme that they can desire to cover in a discussion of focus group. There are also some
drawbacks of this method. The main drawback is that there are certain members who do not
want to put across the personal opinions in front of the people in a group (Ranganathan,
2017).
10

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
4.6. Chosen research Methodologies
4.6.1 Surveys
A survey is a methodology selected for answering the research questions. The major aim of
selecting survey method is that this is rapid as well as easy mean of collecting data from the
larger population. The interview is conducted to obtain comprehensive data; the survey
would permit to get proper data that may simply be interpreted in the numerical form.
Further, one can generalise the conclusion by using this research method. In addition of this,
the survey does not take more time. The survey can be accessible for the audience (parents)
to complete it on the web portal in where they will be able to get easy access. In this way,
they can also submit the survey in a very easy way after finishing this. Three hundred
members from 3 various geographical locations would be ask to get participation in finishing
the survey (Eriksson and Kovalainen, 2015).
4.6.2 Interviews
This research method is qualitative research methodology. This research method is selected
on the priority to give the relevant answers to conduct the research. the major reason of the
selection of this research is that this will be helpful in collecting the open ended replies that
cannot be states by the parents in the survey. The interview creates the opportunity for the
parents to enlarge replies to interview question to be asked permitting them to give answers
within the detail. On the other hand, it permits them to ask various questions related to the
research subject. As parents, for that reason using this methodology would be useful in
attaining these replies. For the example of question in interviews would enquire “What are
you concerned about the most in relation to information gathered about the use of internet by
children, as well as what is the reason?”. It can permit the researcher to obtain more data so
as to reply research question. It makes able parents to address the concern in depth (Eriksson
and Kovalainen, 2015).
11
4.6. Chosen research Methodologies
4.6.1 Surveys
A survey is a methodology selected for answering the research questions. The major aim of
selecting survey method is that this is rapid as well as easy mean of collecting data from the
larger population. The interview is conducted to obtain comprehensive data; the survey
would permit to get proper data that may simply be interpreted in the numerical form.
Further, one can generalise the conclusion by using this research method. In addition of this,
the survey does not take more time. The survey can be accessible for the audience (parents)
to complete it on the web portal in where they will be able to get easy access. In this way,
they can also submit the survey in a very easy way after finishing this. Three hundred
members from 3 various geographical locations would be ask to get participation in finishing
the survey (Eriksson and Kovalainen, 2015).
4.6.2 Interviews
This research method is qualitative research methodology. This research method is selected
on the priority to give the relevant answers to conduct the research. the major reason of the
selection of this research is that this will be helpful in collecting the open ended replies that
cannot be states by the parents in the survey. The interview creates the opportunity for the
parents to enlarge replies to interview question to be asked permitting them to give answers
within the detail. On the other hand, it permits them to ask various questions related to the
research subject. As parents, for that reason using this methodology would be useful in
attaining these replies. For the example of question in interviews would enquire “What are
you concerned about the most in relation to information gathered about the use of internet by
children, as well as what is the reason?”. It can permit the researcher to obtain more data so
as to reply research question. It makes able parents to address the concern in depth (Eriksson
and Kovalainen, 2015).
11

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
Additionally, the face-to-face interviews would be helpful for the investigator to see the
answers of the audience while they are replying the question. In addition, if the members do
not understand the questions asked by investigator, then they have also an option to make
request to the researcher to make clear the questions for developing understanding on the
questions. In this way, the reliability of answers can be ensured. Thirty participants from
three various locations will be enquired to get participation in interview. This interview
would take be 40 minutes for the completion (Mackey and Gass, 2015).
5. Conclusion
As per the above analysis, it can be concluded that as children are depended on Internet more
than before, they put the trust on all the data from Internet. The credibility of the Internet is
not assured for the use of Internet. There is no check on the data of internet. Anyone can be
the author on Internet. There are great chances that the Internet may render the imprecise,
partial, and confusing information.
12
Additionally, the face-to-face interviews would be helpful for the investigator to see the
answers of the audience while they are replying the question. In addition, if the members do
not understand the questions asked by investigator, then they have also an option to make
request to the researcher to make clear the questions for developing understanding on the
questions. In this way, the reliability of answers can be ensured. Thirty participants from
three various locations will be enquired to get participation in interview. This interview
would take be 40 minutes for the completion (Mackey and Gass, 2015).
5. Conclusion
As per the above analysis, it can be concluded that as children are depended on Internet more
than before, they put the trust on all the data from Internet. The credibility of the Internet is
not assured for the use of Internet. There is no check on the data of internet. Anyone can be
the author on Internet. There are great chances that the Internet may render the imprecise,
partial, and confusing information.
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
6. References
Akdeniz, Y. (2016) Internet child pornography and the law: national and international
responses. New York: Routledge
Converse, J.M. (2017) Survey research in the United States: Roots and emergence 1890-
1960. New York: Routledge.
Day, J.K. (2018) Survey and Interview Approaches to Studying Occupants. In Exploring
Occupant Behavior in Buildings, 23(9), pp. 213-238.
DeNardis, L. and Hackl, A.M. (2015) Internet governance by social media
platforms. Telecommunications Policy, 39(9), pp.761-770
Eriksson, P., and Kovalainen, A. (2015) Qualitative methods in business research: A
practical guide to social research, USA: Sage.
Kleinman, P.K. ed. (2015) Diagnostic imaging of child abuse. Cambridge: Cambridge
University Press.
Livingstone, S. and Third, A. (2017) Children and young people’s rights in the digital age:
An emerging agenda. New York: Routledge
Livingstone, S., Carr, J. and Byrne, J. (2015) One in three: Internet governance and
children's rights. New York: Routledge
Mackey, A., and Gass, S. M. (2015) Second language research: Methodology and design,
UK: New York: Routledge.
MacKinnon, R., Hickok, E., Bar, A. and Lim, H.I. (2015) Fostering freedom online: The role
of internet intermediaries. France: UNESCO Publishing.
13
6. References
Akdeniz, Y. (2016) Internet child pornography and the law: national and international
responses. New York: Routledge
Converse, J.M. (2017) Survey research in the United States: Roots and emergence 1890-
1960. New York: Routledge.
Day, J.K. (2018) Survey and Interview Approaches to Studying Occupants. In Exploring
Occupant Behavior in Buildings, 23(9), pp. 213-238.
DeNardis, L. and Hackl, A.M. (2015) Internet governance by social media
platforms. Telecommunications Policy, 39(9), pp.761-770
Eriksson, P., and Kovalainen, A. (2015) Qualitative methods in business research: A
practical guide to social research, USA: Sage.
Kleinman, P.K. ed. (2015) Diagnostic imaging of child abuse. Cambridge: Cambridge
University Press.
Livingstone, S. and Third, A. (2017) Children and young people’s rights in the digital age:
An emerging agenda. New York: Routledge
Livingstone, S., Carr, J. and Byrne, J. (2015) One in three: Internet governance and
children's rights. New York: Routledge
Mackey, A., and Gass, S. M. (2015) Second language research: Methodology and design,
UK: New York: Routledge.
MacKinnon, R., Hickok, E., Bar, A. and Lim, H.I. (2015) Fostering freedom online: The role
of internet intermediaries. France: UNESCO Publishing.
13

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
McReynolds, E., Hubbard, S., Lau, T., Saraf, A., Cakmak, M. and Roesner, F. (2017) May.
Toys that listen: A study of parents, children, and internet-connected toys. In Proceedings of
the 2017 CHI Conference on Human Factors in Computing Systems, pp. 5197-5207
Mneimneh, Z.N., Elliott, M.R., Tourangeau, R. and Heeringa, S.G. (2018) Cultural and
Interviewer Effects on Interview Privacy: Individualism and National Wealth. Cross-Cultural
Research, 52(5), pp.496-523
Montgomery, K.C., Chester, J. and Milosevic, T. (2017) Children’s privacy in the big data
era: Research opportunities. Pediatrics, 140(Supplement 2), pp.S117-S121
Myers, M. D. (2013) Qualitative research in business and management, USA: Sage.
Noble, H., and Smith, J. (2014) Qualitative data analysis: a practical example, Evidence-
based nursing, 17(1), pp. 2-3.
Panneerselvam, R. (2014) Research methodology, USA: PHI Learning Pvt.Ltd
Ranganathan, C. (2017) Research Methdology: Process of Research. Oxford: Oxford
University press
Shin, W. and Kang, H. (2016) Adolescents' privacy concerns and information disclosure
online: The role of parents and the Internet. Computers in Human Behavior, 54, pp.114-123
Stuckey, K.D. (2018) Internet and online law. New York: Law Journal Press.
Thompson, R.A. (2015) Social support and child protection: Lessons learned and
learning. Child Abuse & Neglect, 41, pp.19-29
14
McReynolds, E., Hubbard, S., Lau, T., Saraf, A., Cakmak, M. and Roesner, F. (2017) May.
Toys that listen: A study of parents, children, and internet-connected toys. In Proceedings of
the 2017 CHI Conference on Human Factors in Computing Systems, pp. 5197-5207
Mneimneh, Z.N., Elliott, M.R., Tourangeau, R. and Heeringa, S.G. (2018) Cultural and
Interviewer Effects on Interview Privacy: Individualism and National Wealth. Cross-Cultural
Research, 52(5), pp.496-523
Montgomery, K.C., Chester, J. and Milosevic, T. (2017) Children’s privacy in the big data
era: Research opportunities. Pediatrics, 140(Supplement 2), pp.S117-S121
Myers, M. D. (2013) Qualitative research in business and management, USA: Sage.
Noble, H., and Smith, J. (2014) Qualitative data analysis: a practical example, Evidence-
based nursing, 17(1), pp. 2-3.
Panneerselvam, R. (2014) Research methodology, USA: PHI Learning Pvt.Ltd
Ranganathan, C. (2017) Research Methdology: Process of Research. Oxford: Oxford
University press
Shin, W. and Kang, H. (2016) Adolescents' privacy concerns and information disclosure
online: The role of parents and the Internet. Computers in Human Behavior, 54, pp.114-123
Stuckey, K.D. (2018) Internet and online law. New York: Law Journal Press.
Thompson, R.A. (2015) Social support and child protection: Lessons learned and
learning. Child Abuse & Neglect, 41, pp.19-29
14

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
APPENDICES
7. Appendices
Various appendices are attached below. The appendices include the project plan, ethical
consent form and pilot study.
8. Project Plan
Activities which will be executed A total number of weeks to perform
these activities.
1 2 3 4 5 6 7 8 9 10
Research issues selection
Developing appropriate aim and objectives
Pilot study of research methodology
Execute chosen research methodology
Analyse the results of survey and interview
Evaluation of findings
Write up critical evaluation
Final submission of report
15
APPENDICES
7. Appendices
Various appendices are attached below. The appendices include the project plan, ethical
consent form and pilot study.
8. Project Plan
Activities which will be executed A total number of weeks to perform
these activities.
1 2 3 4 5 6 7 8 9 10
Research issues selection
Developing appropriate aim and objectives
Pilot study of research methodology
Execute chosen research methodology
Analyse the results of survey and interview
Evaluation of findings
Write up critical evaluation
Final submission of report
15
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

9. Ethical Review Form
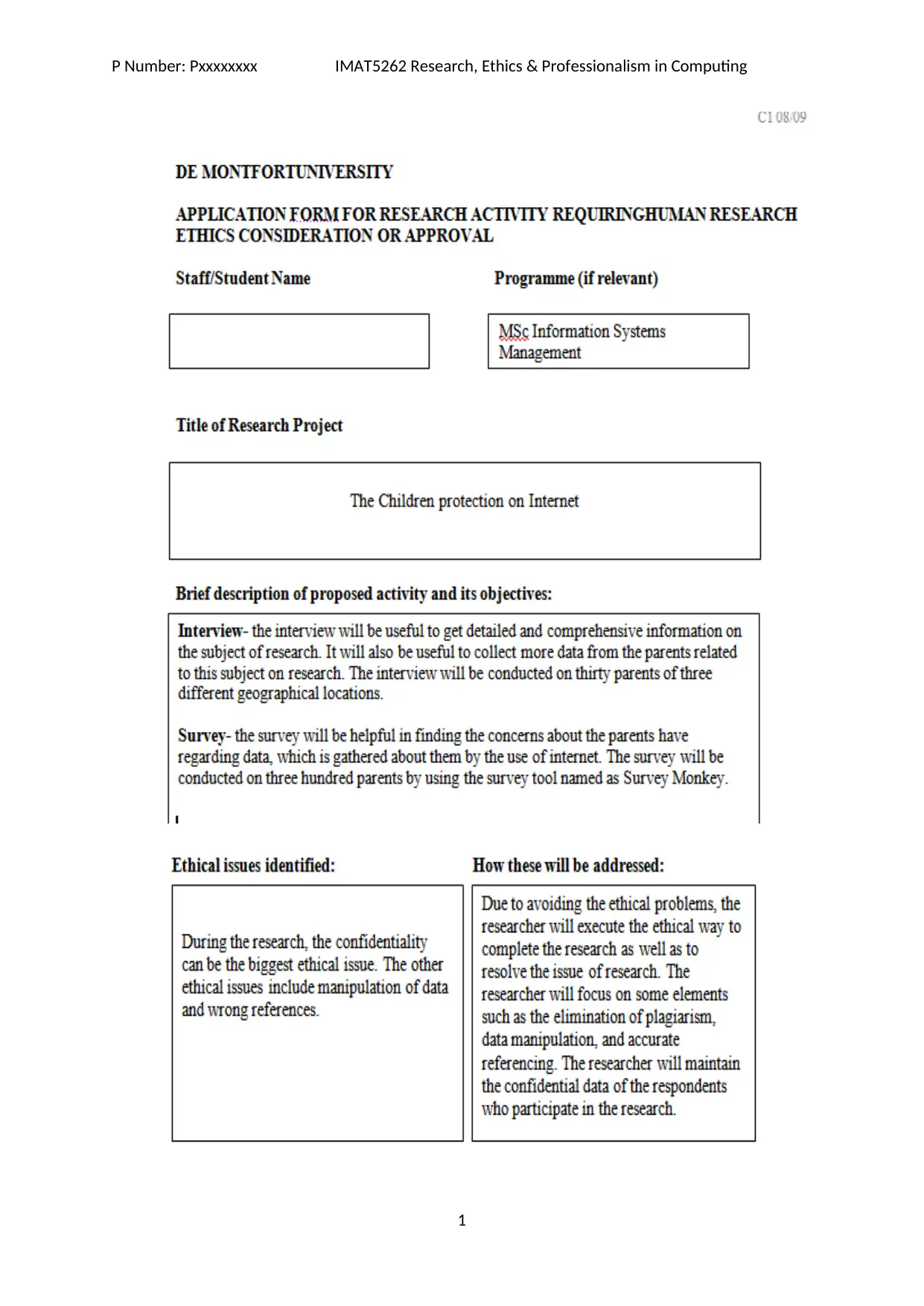
P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
1
1

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
2
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
3
3

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
4
4

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
10. Consent Form
The Ethics of children protection on internet Research Consent Form
Dear Participant,
The purpose of this interview and survey is for a research purpose only as it is part of my
research project “The children protection on internet”. The aim of this research project is to
investigate the concerns parents have regarding the data that is collected about them and
whether they are aware of the use of internet by their children at home or at other places.
I am inviting you to take part in an interview and a survey in which you will be asked to
answer a series of questions; you may wish to complete them both on the same day or you
may to complete the survey in your own time and send it back to me. The interview research
session will involve only two people, me and the participant (yourself) and it will not be
recorded in any kind of way, only your answers will be taken down on paper by me, and the
interview session will last about 40 minutes.
Your participation in this research is voluntary and you have the right to withdraw any time.
You will get to keep a signed copy of the informed consent form if you wish to take part in
this research, and any information recorded from this research will not be passed on to any
third party. All the data and information collected from this research is fully confidential and
will only be stored on my personal laptop, and the university account which is password
protect and prevents anyone from accessing my account other than myself.
The personal data collection from this research will be minimised and the personal data
which is necessarily needed will be asked for otherwise not. Your data will only be used with
this project but will not have any of your personal details included.
Once the research project is complete, the data and information gathered about the participant
will be kept for a maximum time of 1 year but, no more than that, and the entire data and
information collected will be fully destroyed.
If you have any questions regarding this project or research please do not hesitate to contact
myself XXXXXXX, student at De Montfort University via the following email address;
pxxxxxxxx@myemail.dmu.ac.uk
By signing this consent form you specify that you understand the following:
10. I understand the purpose of this project and agree to take part in this research
11. I understand that the data collected will only be used in this project
12. I understand that I can withdraw from this research at any time
5
10. Consent Form
The Ethics of children protection on internet Research Consent Form
Dear Participant,
The purpose of this interview and survey is for a research purpose only as it is part of my
research project “The children protection on internet”. The aim of this research project is to
investigate the concerns parents have regarding the data that is collected about them and
whether they are aware of the use of internet by their children at home or at other places.
I am inviting you to take part in an interview and a survey in which you will be asked to
answer a series of questions; you may wish to complete them both on the same day or you
may to complete the survey in your own time and send it back to me. The interview research
session will involve only two people, me and the participant (yourself) and it will not be
recorded in any kind of way, only your answers will be taken down on paper by me, and the
interview session will last about 40 minutes.
Your participation in this research is voluntary and you have the right to withdraw any time.
You will get to keep a signed copy of the informed consent form if you wish to take part in
this research, and any information recorded from this research will not be passed on to any
third party. All the data and information collected from this research is fully confidential and
will only be stored on my personal laptop, and the university account which is password
protect and prevents anyone from accessing my account other than myself.
The personal data collection from this research will be minimised and the personal data
which is necessarily needed will be asked for otherwise not. Your data will only be used with
this project but will not have any of your personal details included.
Once the research project is complete, the data and information gathered about the participant
will be kept for a maximum time of 1 year but, no more than that, and the entire data and
information collected will be fully destroyed.
If you have any questions regarding this project or research please do not hesitate to contact
myself XXXXXXX, student at De Montfort University via the following email address;
pxxxxxxxx@myemail.dmu.ac.uk
By signing this consent form you specify that you understand the following:
10. I understand the purpose of this project and agree to take part in this research
11. I understand that the data collected will only be used in this project
12. I understand that I can withdraw from this research at any time
5
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
13. I understand that the data will be fully destroyed as stated above
Participants Signature: _________________________________
Date of Participants Signature: ___________________________
Researcher’s Signature: __________________________________
Date of Researcher’s Signature: ____________________________
11. Pilot study
Children protection on internet Interview
1. Gender- male or female?
2. How many children do you have?
3. Are you aware about the use of internet by your children?
4. Do you know the consequences of use of internet by your children?
5. Do you know all the things about your children such their classes, gym and
playground?
6. What protections do you use to secure your children about the use of internet?
7. Do you think there is no problem if children use internet?
8. Do you have healthy conversation with your children?
9. Do you know that how the children feel about being motivated?
10. What can be the alternative of the internet?
Children protection on internet survey
Please make a tick in circle to select the correct answer-
1. What gender are you?
Male
Female
6
13. I understand that the data will be fully destroyed as stated above
Participants Signature: _________________________________
Date of Participants Signature: ___________________________
Researcher’s Signature: __________________________________
Date of Researcher’s Signature: ____________________________
11. Pilot study
Children protection on internet Interview
1. Gender- male or female?
2. How many children do you have?
3. Are you aware about the use of internet by your children?
4. Do you know the consequences of use of internet by your children?
5. Do you know all the things about your children such their classes, gym and
playground?
6. What protections do you use to secure your children about the use of internet?
7. Do you think there is no problem if children use internet?
8. Do you have healthy conversation with your children?
9. Do you know that how the children feel about being motivated?
10. What can be the alternative of the internet?
Children protection on internet survey
Please make a tick in circle to select the correct answer-
1. What gender are you?
Male
Female
6
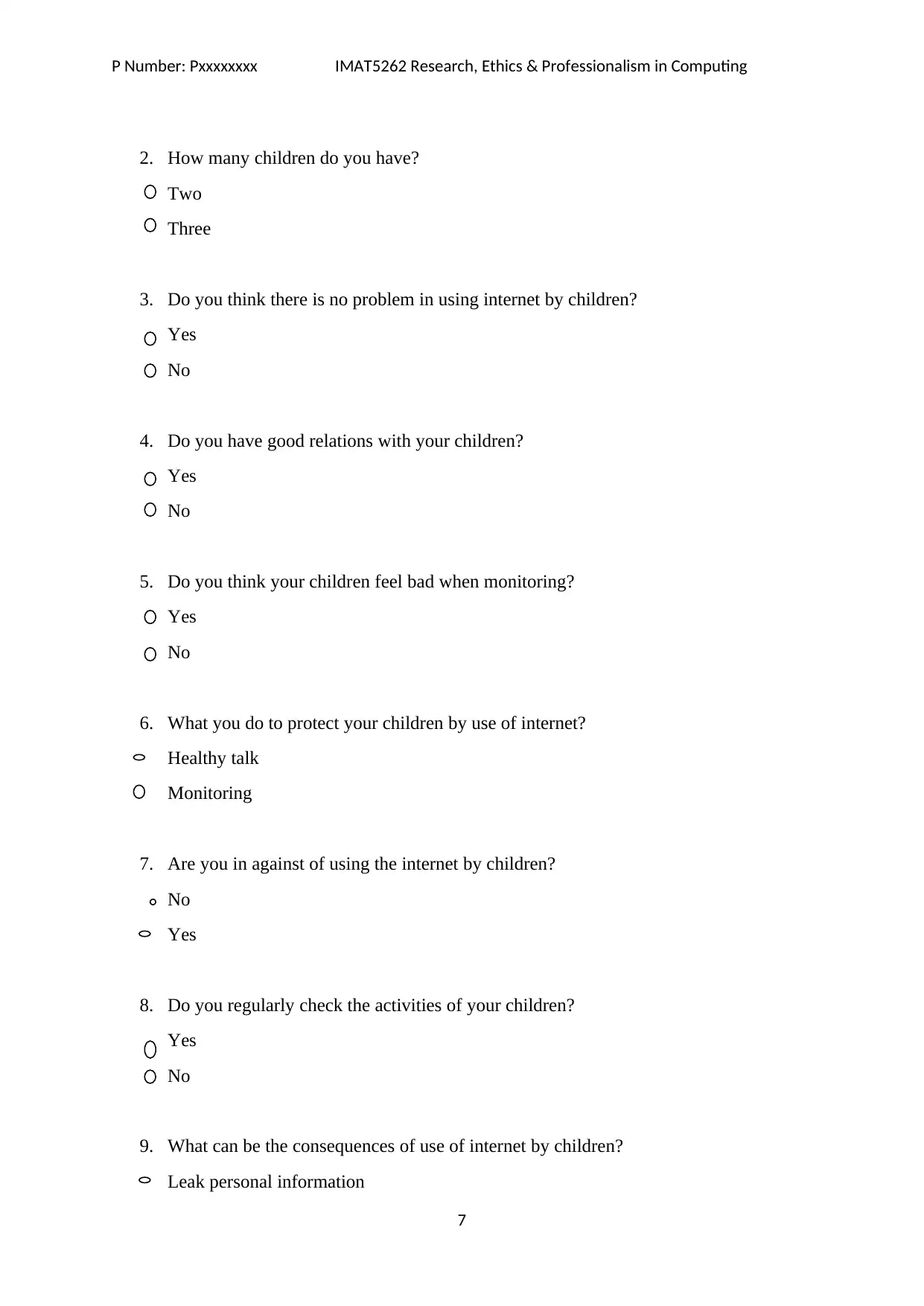
P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
2. How many children do you have?
Two
Three
3. Do you think there is no problem in using internet by children?
Yes
No
4. Do you have good relations with your children?
Yes
No
5. Do you think your children feel bad when monitoring?
Yes
No
6. What you do to protect your children by use of internet?
Healthy talk
Monitoring
7. Are you in against of using the internet by children?
No
Yes
8. Do you regularly check the activities of your children?
Yes
No
9. What can be the consequences of use of internet by children?
Leak personal information
7
2. How many children do you have?
Two
Three
3. Do you think there is no problem in using internet by children?
Yes
No
4. Do you have good relations with your children?
Yes
No
5. Do you think your children feel bad when monitoring?
Yes
No
6. What you do to protect your children by use of internet?
Healthy talk
Monitoring
7. Are you in against of using the internet by children?
No
Yes
8. Do you regularly check the activities of your children?
Yes
No
9. What can be the consequences of use of internet by children?
Leak personal information
7

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
Bad impact of inappropriate content on internet
Both
8
Bad impact of inappropriate content on internet
Both
8
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





