IMAT5262 Research, Ethics & Professionalism in Computing
VerifiedAdded on 2021/05/27
|25
|3691
|112
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

MSc Information Systems Management
IMAT5262 Research, Ethics &
Professionalism in Computing
Assignment - Project Proposal
Ethics of Cyber Security
Pxxxxxxxx
De Montfort University
DO NOT INCLUDE YOUR
NAME AS THE WORK WILL BE
ANONYMOUSLY MARKED
IMAT5262 Research, Ethics &
Professionalism in Computing
Assignment - Project Proposal
Ethics of Cyber Security
Pxxxxxxxx
De Montfort University
DO NOT INCLUDE YOUR
NAME AS THE WORK WILL BE
ANONYMOUSLY MARKED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
Abstract
The modern times are characterized by the presence of computers and other digital devices.
All around us we see the digital devices that have engulfed us. No office, no house or no
vehicle can be spotted that does not make use of the technology. It has made our life very
easy, and something that would take months and weeks are solved in matter of hours with
help of these digital devices. One can hardly imagine an activity that would not involve the
computer and other digital equipment being used in them. Their usage is further more visible
in the organizational structures, both on managerial front, educational and governmental level
Key Words
Ethics, cyber security, computer security, computer networks, privacy.
1
Computing
Abstract
The modern times are characterized by the presence of computers and other digital devices.
All around us we see the digital devices that have engulfed us. No office, no house or no
vehicle can be spotted that does not make use of the technology. It has made our life very
easy, and something that would take months and weeks are solved in matter of hours with
help of these digital devices. One can hardly imagine an activity that would not involve the
computer and other digital equipment being used in them. Their usage is further more visible
in the organizational structures, both on managerial front, educational and governmental level
Key Words
Ethics, cyber security, computer security, computer networks, privacy.
1

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
Table of Contents
1. Background................................................................................................................................3
2. Research questions.................................................................................................................3
3. Literature Review......................................................................................................................3
4. Methodology Review................................................................................................................7
5. Conclusion.................................................................................................................................8
6. References...............................................................................................................................10
7. APPENDICES...........................................................................................................................12
Appendix (i): Project Plan.............................................................................................................12
Appendix (ii): Ethical Review Form..............................................................................................0
Appendix (iii): Consent Form.........................................................................................................5
Appendix (iv): Pilot study...............................................................................................................7
2
Computing
Table of Contents
1. Background................................................................................................................................3
2. Research questions.................................................................................................................3
3. Literature Review......................................................................................................................3
4. Methodology Review................................................................................................................7
5. Conclusion.................................................................................................................................8
6. References...............................................................................................................................10
7. APPENDICES...........................................................................................................................12
Appendix (i): Project Plan.............................................................................................................12
Appendix (ii): Ethical Review Form..............................................................................................0
Appendix (iii): Consent Form.........................................................................................................5
Appendix (iv): Pilot study...............................................................................................................7
2

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
1. Background
Cyber world is just like the society of human being. While over 3 billion people from across
the world are on board on the digital interface, it does require patrolling and controlling of the
entire traffic. Just like the society would need law and order, police control and patrol, in the
same way a medium that has over 3 billion users would require a scheme which would ensure
safe usage of internet and computers (Alves & Morris, 2018). With all kinds of operations
subject to the usage of online resources, it is highly imperative to create a zone that is
shielded with secure browsing of computers and the world of internet.
2. Research questions
Understanding what the cyber security concept means, what challenges are faced by it, what
are the agents and elements that contribute towards it and finally, the remedial actions that
can be suggested towards counteracting and mitigating the impact of overall cyber security
threats. In other words cyber security pertains to all the elements both that work in its favor
and those that work against it. It is the overall study of the scenario with aim to bring about
the most and best out of the situation.
3. Literature Review
McAfee that has been in the business of cyber security and cyber protection for a long while,
took an initiative and conducted a thorough study on a massive scale to understand the
overall scenario of cyber security, the possible threats, the factors that contribute towards the
cyber security, the factors that act against it and those reasons due to which the cyber security
remains a constant loophole and menace on all levels which ranges from individual level to
massive level on organizational front as well as international level (Andress & Winterfeld,
2014).
3
Computing
1. Background
Cyber world is just like the society of human being. While over 3 billion people from across
the world are on board on the digital interface, it does require patrolling and controlling of the
entire traffic. Just like the society would need law and order, police control and patrol, in the
same way a medium that has over 3 billion users would require a scheme which would ensure
safe usage of internet and computers (Alves & Morris, 2018). With all kinds of operations
subject to the usage of online resources, it is highly imperative to create a zone that is
shielded with secure browsing of computers and the world of internet.
2. Research questions
Understanding what the cyber security concept means, what challenges are faced by it, what
are the agents and elements that contribute towards it and finally, the remedial actions that
can be suggested towards counteracting and mitigating the impact of overall cyber security
threats. In other words cyber security pertains to all the elements both that work in its favor
and those that work against it. It is the overall study of the scenario with aim to bring about
the most and best out of the situation.
3. Literature Review
McAfee that has been in the business of cyber security and cyber protection for a long while,
took an initiative and conducted a thorough study on a massive scale to understand the
overall scenario of cyber security, the possible threats, the factors that contribute towards the
cyber security, the factors that act against it and those reasons due to which the cyber security
remains a constant loophole and menace on all levels which ranges from individual level to
massive level on organizational front as well as international level (Andress & Winterfeld,
2014).
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
The study took into account number of factors, and it was an extensive research in this field
which involved questionnaires, surveys and interviews from various stakeholders in the field
of computing. The studies aimed at addressing the core issues and problems that are faced in
the field of cyber security and computing (Lucas, 2017).
The study took into account the opinions and observations of over 200 renown companies
and big wigs from the field of computing and technology and sought their opinion about the
overall standing and position and their understanding of the concept of the cyber
vulnerabilities and threats that are faced in different segments (Blakemore & Awan, 2016).
Lars Nicander an expert in the field of cyber security has opinioned that the threats are
existent just because of lack of protection. Although he explains this in the view point of
governmental and nationwide security that suffers from threats in form of cyber war fare
(Samuels & Rohsenow, 2015).
The speed with which the attacks are being carried out has risen by extremely higher
proportions in recent years compared to the yester years. H.P (Hewlett Packard) a pioneer in
the field of digital devices and computers that has long affiliation with these devices
conducted a survey in 2011 to find out the reasons and the possible impacts of the security
vulnerabilities (Stallings, 2017). According to the report the recent times have seen more
attacks directed towards the organizations and computer enterprises of large scale. These
include the service providers like Google Inc, Microsoft’s Msn, Sony , H.P’s own website
and many other interfaces. The report findings state that new means of attacks have been
launched in recent times which are totally new in their nature and type and have taken the
users of computer both on individual level and on organizational level by total surprise
(Burgess, 2012).
4
Computing
The study took into account number of factors, and it was an extensive research in this field
which involved questionnaires, surveys and interviews from various stakeholders in the field
of computing. The studies aimed at addressing the core issues and problems that are faced in
the field of cyber security and computing (Lucas, 2017).
The study took into account the opinions and observations of over 200 renown companies
and big wigs from the field of computing and technology and sought their opinion about the
overall standing and position and their understanding of the concept of the cyber
vulnerabilities and threats that are faced in different segments (Blakemore & Awan, 2016).
Lars Nicander an expert in the field of cyber security has opinioned that the threats are
existent just because of lack of protection. Although he explains this in the view point of
governmental and nationwide security that suffers from threats in form of cyber war fare
(Samuels & Rohsenow, 2015).
The speed with which the attacks are being carried out has risen by extremely higher
proportions in recent years compared to the yester years. H.P (Hewlett Packard) a pioneer in
the field of digital devices and computers that has long affiliation with these devices
conducted a survey in 2011 to find out the reasons and the possible impacts of the security
vulnerabilities (Stallings, 2017). According to the report the recent times have seen more
attacks directed towards the organizations and computer enterprises of large scale. These
include the service providers like Google Inc, Microsoft’s Msn, Sony , H.P’s own website
and many other interfaces. The report findings state that new means of attacks have been
launched in recent times which are totally new in their nature and type and have taken the
users of computer both on individual level and on organizational level by total surprise
(Burgess, 2012).
4

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
H.P report focuses on the basic point and that is of understanding the impact, the possible
repercussions that are attached to the attack and the real motives that may be based on the
attack on a certain area. Knowing the potential target areas, the objectives behind it, knowing
which areas could cost the respective organization more are few of the factors that need to be
taken into account in order to devise a better strategy towards cyber security enhancement
(Glisson & Choo, 2017).
H.P has adopted a special software and data base for this purpose in the name of Open Source
Vulnerability Database (O.S.V.D), which takes into account various factors related to the
cyber security, the trends, the target areas and many other areas and based on it, it helps
creating reports that further enable creating strategies towards reducing any threats that may
exist in the computer world of communications. OSVD generated a ten year report based on
the target zones and the areas that have been brought into attention by the hackers (Guitton,
2017).
The report tries to investigate and unearth the methods that are adopted towards security
infiltration and the report states that new methods have been adopted which are a total
surprise to the members of the field. It’s just like saying that the thieves have adopted new
methods of robbing the property and valuables (Gupta, 2013).
H.P in its report for the year 2011 expresses deep concern over the growing rate of threats in
various forms yet it recommends the remedial actions towards it in form of prioritizing the
level of work along with the functions and content those need more security relative to the
other elements and functions which may require relatively less security (Vacca, 2014).
The overall report aims to find out the inclination of the hackers and other spammers as to in
what way do they target the sites and sources. Based on the findings it is being underscored
5
Computing
H.P report focuses on the basic point and that is of understanding the impact, the possible
repercussions that are attached to the attack and the real motives that may be based on the
attack on a certain area. Knowing the potential target areas, the objectives behind it, knowing
which areas could cost the respective organization more are few of the factors that need to be
taken into account in order to devise a better strategy towards cyber security enhancement
(Glisson & Choo, 2017).
H.P has adopted a special software and data base for this purpose in the name of Open Source
Vulnerability Database (O.S.V.D), which takes into account various factors related to the
cyber security, the trends, the target areas and many other areas and based on it, it helps
creating reports that further enable creating strategies towards reducing any threats that may
exist in the computer world of communications. OSVD generated a ten year report based on
the target zones and the areas that have been brought into attention by the hackers (Guitton,
2017).
The report tries to investigate and unearth the methods that are adopted towards security
infiltration and the report states that new methods have been adopted which are a total
surprise to the members of the field. It’s just like saying that the thieves have adopted new
methods of robbing the property and valuables (Gupta, 2013).
H.P in its report for the year 2011 expresses deep concern over the growing rate of threats in
various forms yet it recommends the remedial actions towards it in form of prioritizing the
level of work along with the functions and content those need more security relative to the
other elements and functions which may require relatively less security (Vacca, 2014).
The overall report aims to find out the inclination of the hackers and other spammers as to in
what way do they target the sites and sources. Based on the findings it is being underscored
5

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
that areas of financial importance are high value targets. These include the banking sectors as
well as the governmental organizations which serve the common citizens (Hudaib, 2015).
The threats may not be only in form of external links and threats, rather they can be from
within and it has been seen many a time that the insiders cause more damage to the
organization than would outsiders. One similar instance was seen in case of soft drinks giants
Coca Cola, where an internal member was convicted and caught in the process of sharing the
company’s secret information to the rivals in the market (In Cleary & In Felici, 2014). This
could have been avoided if safe and protective measures were being adopted in the
organization which would not allow any individual unchecked access to all the documents
and all the segments of organization which can be of any strategic importance or could be
used against the company in any circumstances. This can be ensure in form of multiple
protective layers within the organization (Voeller, 2014).
Verizon has conducted its own research in the field of cyber security and their research is
motivated towards the providing of security to the large scaled governmental organizations.
The survey was undertaken in 2009. The main point of the entire point is concluded against a
single point and that states that over 80 percent of the online mishaps that took place in one
form or another could have been avoided provided there was an infrastructure available, or
people were a little more aware about their roles, responsibilities in case of fulfilling their
duties towards making the network a safe medium to use for all kinds of purposes and usages.
The report further emphasizes that any kind of threat or weakness must not be taken lightly
and it is these threats that lead up to failures in longer run (In Springer, 2017).
Verizon further looks into the possible reasons that contribute to them miss happenings and
why this menace persists to remain in the surrounding despite the realization of how
dangerous it is. Verizon conducted survey across hundred countries and tried to find out how
6
Computing
that areas of financial importance are high value targets. These include the banking sectors as
well as the governmental organizations which serve the common citizens (Hudaib, 2015).
The threats may not be only in form of external links and threats, rather they can be from
within and it has been seen many a time that the insiders cause more damage to the
organization than would outsiders. One similar instance was seen in case of soft drinks giants
Coca Cola, where an internal member was convicted and caught in the process of sharing the
company’s secret information to the rivals in the market (In Cleary & In Felici, 2014). This
could have been avoided if safe and protective measures were being adopted in the
organization which would not allow any individual unchecked access to all the documents
and all the segments of organization which can be of any strategic importance or could be
used against the company in any circumstances. This can be ensure in form of multiple
protective layers within the organization (Voeller, 2014).
Verizon has conducted its own research in the field of cyber security and their research is
motivated towards the providing of security to the large scaled governmental organizations.
The survey was undertaken in 2009. The main point of the entire point is concluded against a
single point and that states that over 80 percent of the online mishaps that took place in one
form or another could have been avoided provided there was an infrastructure available, or
people were a little more aware about their roles, responsibilities in case of fulfilling their
duties towards making the network a safe medium to use for all kinds of purposes and usages.
The report further emphasizes that any kind of threat or weakness must not be taken lightly
and it is these threats that lead up to failures in longer run (In Springer, 2017).
Verizon further looks into the possible reasons that contribute to them miss happenings and
why this menace persists to remain in the surrounding despite the realization of how
dangerous it is. Verizon conducted survey across hundred countries and tried to find out how
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
they go about their online operations, how much consideration do they give to the challenges
and threats that are present in the networks and many other factors which would enable
creating a system that is better suited to the needs of governments and military organizations.
The report states that the kind of network that is in place also defines the kind of vulnerability
it may be faced with. For example a commercial network may not be in direct jurisdiction of
the government agencies, rather the private service providers or international organizations
that bring about investment in the respective countries, only they can handle this in time and
enable saving much more loss that may be incurred afterwards once the attacks have taken
place (International Conference on Cryptology and Network Security, Lin, Tsudik, & Wang,
2011). The possible solutions presented by this extensive report also include the
consideration of the guidance and training that may be provided to the users of internet in
these organizations which would enable them performing in a better way towards improved
existence of the cyber world functions. Providing the users with sufficient technical
knowledge, adapting them to the everyday changes in form of the hardware and software can
make things relatively easier with regard to the cyber security.
4. Methodology Review
SECTION 1 – REVIEW
Questionnaire is a method of data collection that is both qualitative and quantitative;
depending on the type of questions used. It is qualitative once open-ended questions are used
while it is quantitative once close-ended questions. The data from respondents is often
analyzed using software such as SPSS (Statistical Package for the Social Sciences) that is
custom built to analyze such data. Questionnaires, once completed, are submitted for analysis
through several techniques. The most popular is the use of a scale or index, due to its
simplicity (Kannan, 2017).
7
Computing
they go about their online operations, how much consideration do they give to the challenges
and threats that are present in the networks and many other factors which would enable
creating a system that is better suited to the needs of governments and military organizations.
The report states that the kind of network that is in place also defines the kind of vulnerability
it may be faced with. For example a commercial network may not be in direct jurisdiction of
the government agencies, rather the private service providers or international organizations
that bring about investment in the respective countries, only they can handle this in time and
enable saving much more loss that may be incurred afterwards once the attacks have taken
place (International Conference on Cryptology and Network Security, Lin, Tsudik, & Wang,
2011). The possible solutions presented by this extensive report also include the
consideration of the guidance and training that may be provided to the users of internet in
these organizations which would enable them performing in a better way towards improved
existence of the cyber world functions. Providing the users with sufficient technical
knowledge, adapting them to the everyday changes in form of the hardware and software can
make things relatively easier with regard to the cyber security.
4. Methodology Review
SECTION 1 – REVIEW
Questionnaire is a method of data collection that is both qualitative and quantitative;
depending on the type of questions used. It is qualitative once open-ended questions are used
while it is quantitative once close-ended questions. The data from respondents is often
analyzed using software such as SPSS (Statistical Package for the Social Sciences) that is
custom built to analyze such data. Questionnaires, once completed, are submitted for analysis
through several techniques. The most popular is the use of a scale or index, due to its
simplicity (Kannan, 2017).
7

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
According to (Kannan, 2017), the first step in analyzing questionnaire data is to
create a simple grid that collates all the data in the questionnaire. The grid is useful because it
makes it easier to store, and at the same time interpret, the data from the questionnaire. The
grid is usually questions against the responses from the respondents. Designing a simple
coding system follows next. The system is dependent on the type of questions used in the
study. In the case of closed questions, a simple numerical scale is used. The scale used in the
questionnaire will also be used in the grid. During the coding procedure, there should be
allowance for missing data or respondents selecting multiple categories (Willson, 2016).
SECTION 2 - SELECTION
In this research, Online Survey will be the methodology that will be utilized. This will be
done by creating an account with SurveyMonkey and then designing a survey. After
designing a complete survey then a web link is generated. This web link is sent via SMS,
email or any chat services that my target population can use. They will be required to click on
the link and in less than five minutes fill in the questions (Winterfeld & Andress, 2012).
Advantages of Online Surveys
a) Quick results – Results are transmitted in real-time. As soon as your respondents are
done, you can view and analyse their responses
b) More Accurate – data entered by respondent go directly to the online database and the
person doing the survey will not have a chance to alter it (Kizza, 2014).
c) Objectivity – The respondent does answer the questions without being interfered with
by the person administering the survey.
d) Anonymity – “Once confidentiality is assured, participants feel more comfortable
providing open and honest feedback”
8
Computing
According to (Kannan, 2017), the first step in analyzing questionnaire data is to
create a simple grid that collates all the data in the questionnaire. The grid is useful because it
makes it easier to store, and at the same time interpret, the data from the questionnaire. The
grid is usually questions against the responses from the respondents. Designing a simple
coding system follows next. The system is dependent on the type of questions used in the
study. In the case of closed questions, a simple numerical scale is used. The scale used in the
questionnaire will also be used in the grid. During the coding procedure, there should be
allowance for missing data or respondents selecting multiple categories (Willson, 2016).
SECTION 2 - SELECTION
In this research, Online Survey will be the methodology that will be utilized. This will be
done by creating an account with SurveyMonkey and then designing a survey. After
designing a complete survey then a web link is generated. This web link is sent via SMS,
email or any chat services that my target population can use. They will be required to click on
the link and in less than five minutes fill in the questions (Winterfeld & Andress, 2012).
Advantages of Online Surveys
a) Quick results – Results are transmitted in real-time. As soon as your respondents are
done, you can view and analyse their responses
b) More Accurate – data entered by respondent go directly to the online database and the
person doing the survey will not have a chance to alter it (Kizza, 2014).
c) Objectivity – The respondent does answer the questions without being interfered with
by the person administering the survey.
d) Anonymity – “Once confidentiality is assured, participants feel more comfortable
providing open and honest feedback”
8

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
e) Flexibility – one can develop questions to administer in an online survey very easily.
On the part of respondents, they can be able to skip questions that they don’t feel
comfortable answering or questions they do not have an opinion on (Kizza, 2015).
5. Conclusion
The common saying of “a stitch in time saves nice” aptly applies to the field of cyber
security. This can be done so in multiple ways, the first being creating sense of awareness,
second about safe practices, third technical knowledge and increasing research in this field
for further advancements and finally making long term policies that are designed towards
safer operations of computers. Billions of dollars are being lost, and not just the monitory
factor, rather other valuable information is being breached through weak mechanism of cyber
security, this all can be overcome through vigorously keen interest based policies crafting by
the stakeholders on international level as well as local level in different parts of the world to
make the world of world wide web a better and more reliable one.
Internet operations are termed as once those are without borders, without walls and without
fences, everyone can barge into the network and can cause any damage what so ever.
However this damage can be controlled and checked if proper measures are adopted and
implemented in form of network security. Network security comes in various forms, such as
hardware implementation, software installation and many other factors relevant.
9
Computing
e) Flexibility – one can develop questions to administer in an online survey very easily.
On the part of respondents, they can be able to skip questions that they don’t feel
comfortable answering or questions they do not have an opinion on (Kizza, 2015).
5. Conclusion
The common saying of “a stitch in time saves nice” aptly applies to the field of cyber
security. This can be done so in multiple ways, the first being creating sense of awareness,
second about safe practices, third technical knowledge and increasing research in this field
for further advancements and finally making long term policies that are designed towards
safer operations of computers. Billions of dollars are being lost, and not just the monitory
factor, rather other valuable information is being breached through weak mechanism of cyber
security, this all can be overcome through vigorously keen interest based policies crafting by
the stakeholders on international level as well as local level in different parts of the world to
make the world of world wide web a better and more reliable one.
Internet operations are termed as once those are without borders, without walls and without
fences, everyone can barge into the network and can cause any damage what so ever.
However this damage can be controlled and checked if proper measures are adopted and
implemented in form of network security. Network security comes in various forms, such as
hardware implementation, software installation and many other factors relevant.
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
10
Computing
10

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
6. References
Alves, T., & Morris, T. (2018). Hardware-based Cyber Threats. Proceedings of the 4th
International Conference on Information Systems Security and Privacy.
doi:10.5220/0006577202590266
Andress, J., & Winterfeld, S. (2014). Cyber Warfare: Techniques, Tactics and Tools for
Security Practitioners.
Blakemore, B., & Awan, I. (2016). Policing Cyber Hate, Cyber Threats and Cyber
Terrorism. London: Taylor and Francis.
Burgess, J. P. (2012). The Routledge handbook of new security studies. London [England:
Routledge.
Glisson, W., & Choo, R. (2017). Introduction to Cyber-of-Things: Cyber-crimes and Cyber-
Security Minitrack. Proceedings of the 50th Hawaii International Conference on System
Sciences (2017). doi:10.24251/hicss.2017.718
Guitton, C. (2017). Foiling cyber attacks. 2017 International Conference on Cyber Security
And Protection Of Digital Services (Cyber Security).
doi:10.1109/cybersecpods.2017.8074853
Gupta, M. S. (2013). Cyber crimes. New Delhi: Anmol.
Hudaib, A. (2015). Social Media Cyber Crimes And XKeyscore Espionage Technologies:
XKeyscore Espionage Technologies & Social Media Cyber crimes in Practice. Saarbrücken:
LAP LAMBERT Academic Publishing.
11
Computing
6. References
Alves, T., & Morris, T. (2018). Hardware-based Cyber Threats. Proceedings of the 4th
International Conference on Information Systems Security and Privacy.
doi:10.5220/0006577202590266
Andress, J., & Winterfeld, S. (2014). Cyber Warfare: Techniques, Tactics and Tools for
Security Practitioners.
Blakemore, B., & Awan, I. (2016). Policing Cyber Hate, Cyber Threats and Cyber
Terrorism. London: Taylor and Francis.
Burgess, J. P. (2012). The Routledge handbook of new security studies. London [England:
Routledge.
Glisson, W., & Choo, R. (2017). Introduction to Cyber-of-Things: Cyber-crimes and Cyber-
Security Minitrack. Proceedings of the 50th Hawaii International Conference on System
Sciences (2017). doi:10.24251/hicss.2017.718
Guitton, C. (2017). Foiling cyber attacks. 2017 International Conference on Cyber Security
And Protection Of Digital Services (Cyber Security).
doi:10.1109/cybersecpods.2017.8074853
Gupta, M. S. (2013). Cyber crimes. New Delhi: Anmol.
Hudaib, A. (2015). Social Media Cyber Crimes And XKeyscore Espionage Technologies:
XKeyscore Espionage Technologies & Social Media Cyber crimes in Practice. Saarbrücken:
LAP LAMBERT Academic Publishing.
11

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
In Cleary, F., & In Felici, M. (2014). Cyber Security and Privacy: Third Cyber Security and
Privacy EU Forum, CSP Forum 2014, Athens, Greece, May 21-22, 2014, Revised Selected
Papers. Cham: Springer International Publishing.
In Springer, P. J. (2017). Encyclopedia of cyber warfare.
International Conference on Cryptology and Network Security, Lin, D., Tsudik, G., &
Wang, X. (2011). Cryptology and network security. Berlin: Springer.
Kannan, M. K. (2017). A bird's eye view of Cyber Crimes and Free and Open Source
Software's to Detoxify Cyber Crime Attacks - an End User Perspective. 2017 2nd
International Conference on Anti-Cyber Crimes (ICACC). doi:10.1109/anti-
cybercrime.2017.7905297
Kizza, J. M. (2014). Computer network security and cyber ethics.
Kizza, J. M. (2015). Guide to computer network security.
Lucas, G. (2017). Cyber (In)security. Ethics and Cyber Warfare, 16-32.
doi:10.1093/acprof:oso/9780190276522.003.0002
Samuels, D., & Rohsenow, T. (2015). Cyber security. New York: Arcler Press.
Stallings, W. (2017). Cryptography and network security: Principles and practice.
Vacca, J. R. (2014). Network and system security. Amsterdam: Syngress.
Voeller, J. G. (2014). Cyber Security. Wiley.
Willson, D. (2016). Ethics. Cyber Security Awareness for CEOs and Management, 37-40.
doi:10.1016/b978-0-12-804754-5.00005-2
12
Computing
In Cleary, F., & In Felici, M. (2014). Cyber Security and Privacy: Third Cyber Security and
Privacy EU Forum, CSP Forum 2014, Athens, Greece, May 21-22, 2014, Revised Selected
Papers. Cham: Springer International Publishing.
In Springer, P. J. (2017). Encyclopedia of cyber warfare.
International Conference on Cryptology and Network Security, Lin, D., Tsudik, G., &
Wang, X. (2011). Cryptology and network security. Berlin: Springer.
Kannan, M. K. (2017). A bird's eye view of Cyber Crimes and Free and Open Source
Software's to Detoxify Cyber Crime Attacks - an End User Perspective. 2017 2nd
International Conference on Anti-Cyber Crimes (ICACC). doi:10.1109/anti-
cybercrime.2017.7905297
Kizza, J. M. (2014). Computer network security and cyber ethics.
Kizza, J. M. (2015). Guide to computer network security.
Lucas, G. (2017). Cyber (In)security. Ethics and Cyber Warfare, 16-32.
doi:10.1093/acprof:oso/9780190276522.003.0002
Samuels, D., & Rohsenow, T. (2015). Cyber security. New York: Arcler Press.
Stallings, W. (2017). Cryptography and network security: Principles and practice.
Vacca, J. R. (2014). Network and system security. Amsterdam: Syngress.
Voeller, J. G. (2014). Cyber Security. Wiley.
Willson, D. (2016). Ethics. Cyber Security Awareness for CEOs and Management, 37-40.
doi:10.1016/b978-0-12-804754-5.00005-2
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
Winterfeld, S., & Andress, J. (2012). The basics of cyber warfare: Understanding the
fundamentals of cyber warfare in theory and practice. Place of publication not identified:
Syngress.
7. APPENDICES
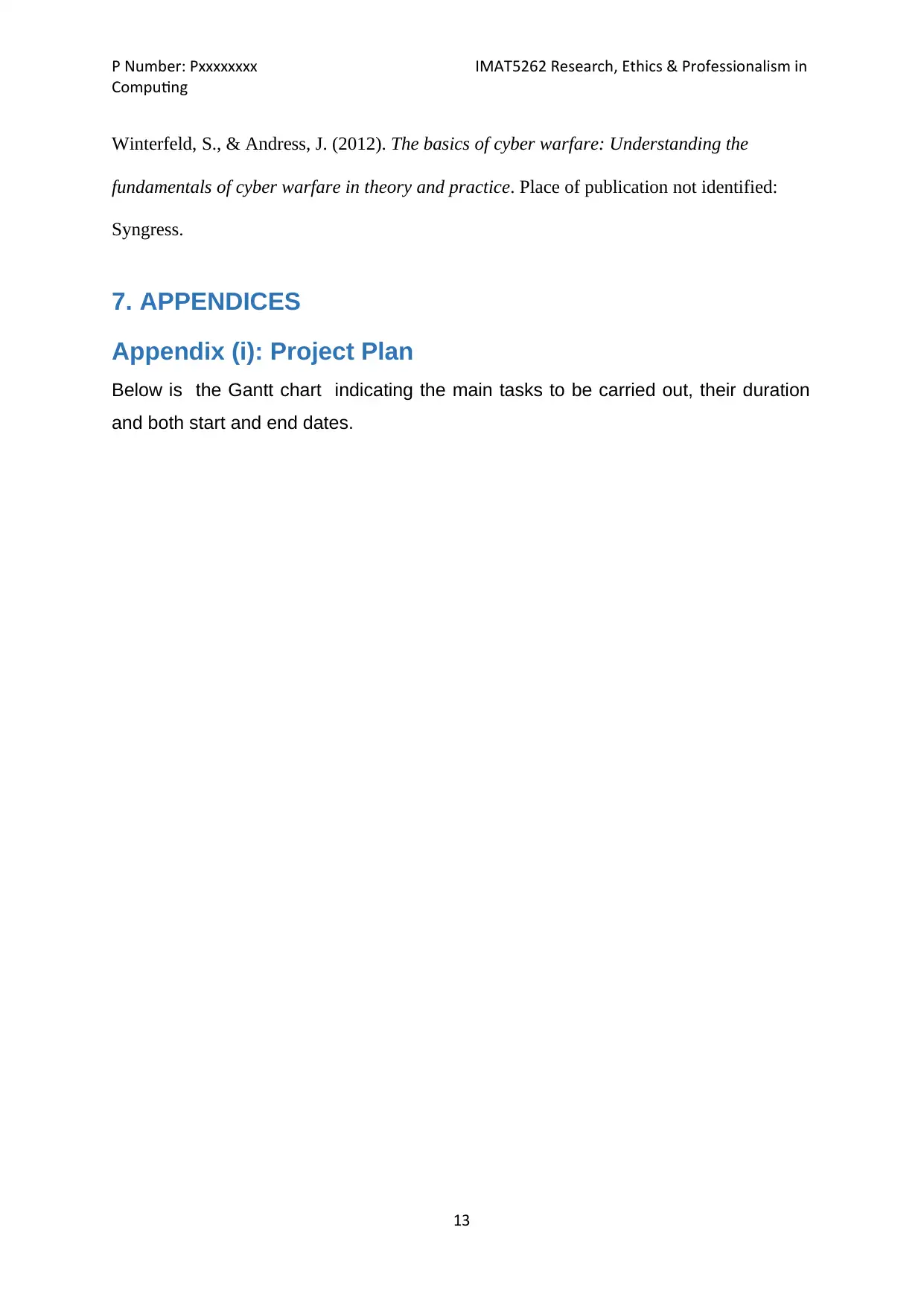
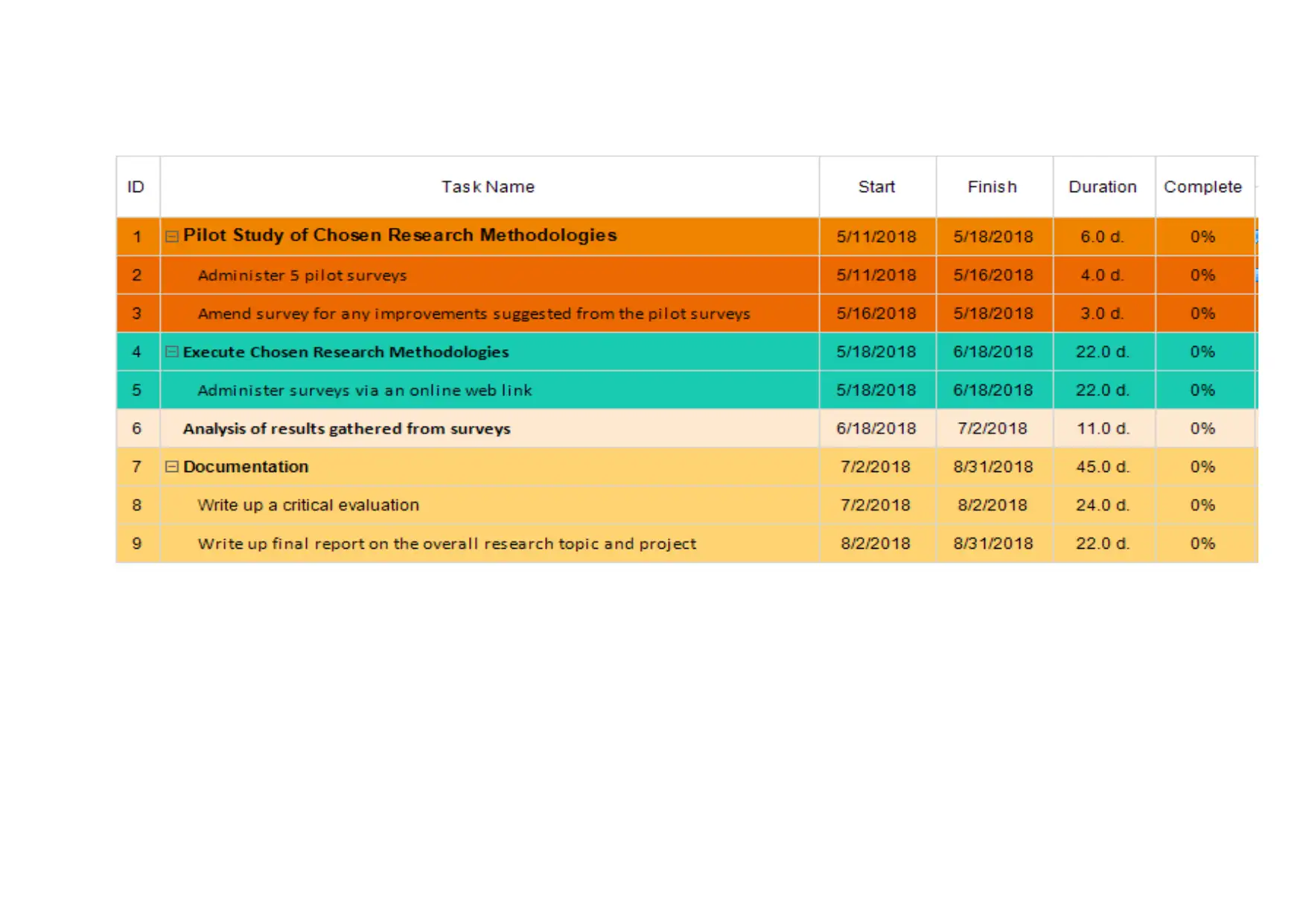
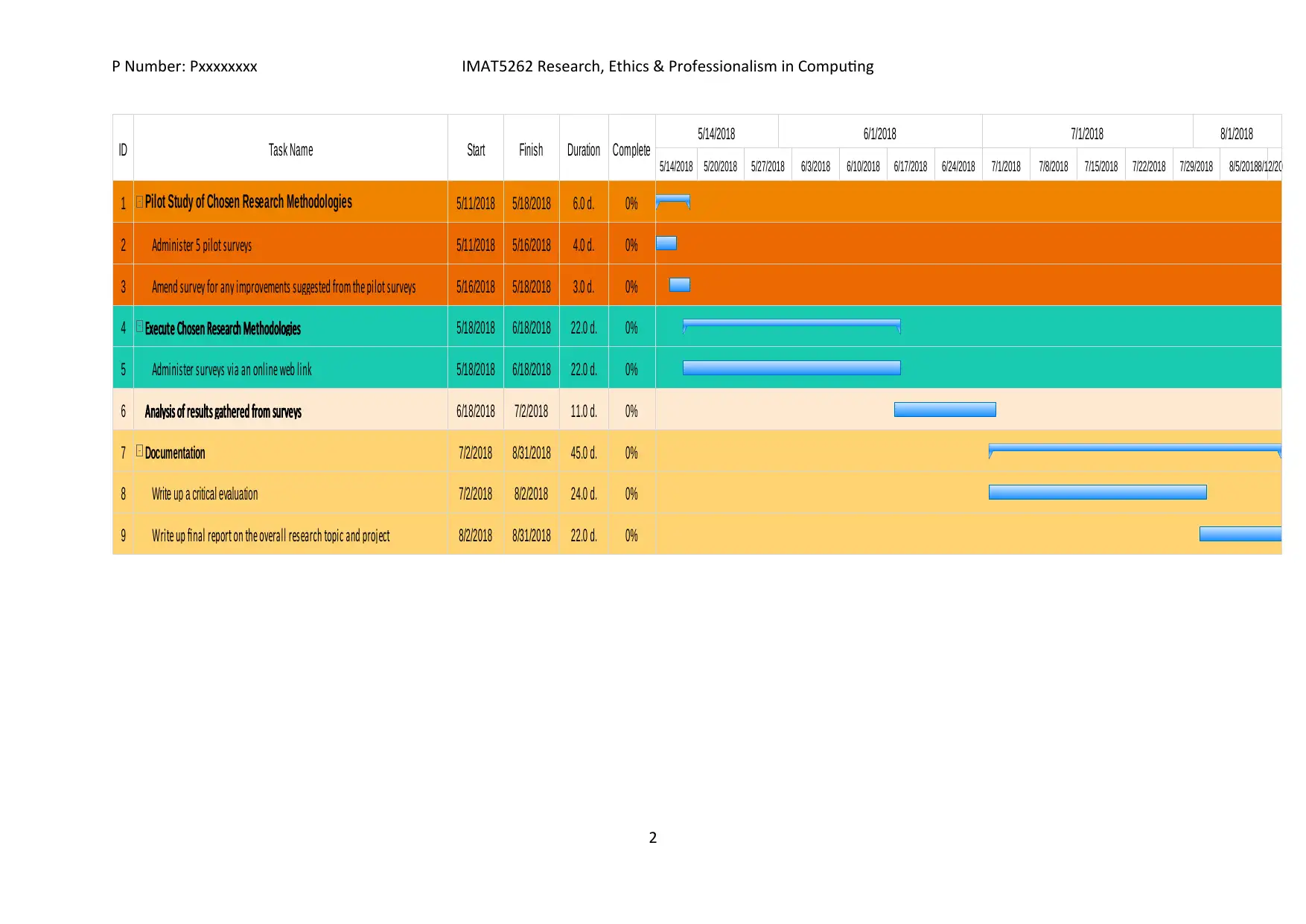
Appendix (i): Project Plan
Below is the Gantt chart indicating the main tasks to be carried out, their duration
and both start and end dates.
13
Computing
Winterfeld, S., & Andress, J. (2012). The basics of cyber warfare: Understanding the
fundamentals of cyber warfare in theory and practice. Place of publication not identified:
Syngress.
7. APPENDICES
Appendix (i): Project Plan
Below is the Gantt chart indicating the main tasks to be carried out, their duration
and both start and end dates.
13
P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
1
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in Computing
ID Task Name Start Finish Duration Complete 5/14/2018 6/1/2018 7/1/2018 8/1/2018
5/14/2018 5/20/2018 5/27/2018 6/3/2018 6/10/2018 6/17/2018 6/24/2018 7/1/2018 7/8/2018 7/15/2018 7/22/2018 7/29/2018 8/5/20188/12/2018
1 Pilot Study of Chosen Research Methodologies 5/11/2018 5/18/2018 6.0 d. 0%
2 Administer 5 pilot surveys 5/11/2018 5/16/2018 4.0 d. 0%
3 Amend survey for any improvements suggested from the pilot surveys 5/16/2018 5/18/2018 3.0 d. 0%
4 Execute Chosen Research Methodologies 5/18/2018 6/18/2018 22.0 d. 0%
5 Administer surveys via an online web link 5/18/2018 6/18/2018 22.0 d. 0%
6 Analysis of results gathered from surveys 6/18/2018 7/2/2018 11.0 d. 0%
7 Documentation 7/2/2018 8/31/2018 45.0 d. 0%
8 Write up a critical evaluation 7/2/2018 8/2/2018 24.0 d. 0%
9 Write up final report on the overall research topic and project 8/2/2018 8/31/2018 22.0 d. 0%
2
ID Task Name Start Finish Duration Complete 5/14/2018 6/1/2018 7/1/2018 8/1/2018
5/14/2018 5/20/2018 5/27/2018 6/3/2018 6/10/2018 6/17/2018 6/24/2018 7/1/2018 7/8/2018 7/15/2018 7/22/2018 7/29/2018 8/5/20188/12/2018
1 Pilot Study of Chosen Research Methodologies 5/11/2018 5/18/2018 6.0 d. 0%
2 Administer 5 pilot surveys 5/11/2018 5/16/2018 4.0 d. 0%
3 Amend survey for any improvements suggested from the pilot surveys 5/16/2018 5/18/2018 3.0 d. 0%
4 Execute Chosen Research Methodologies 5/18/2018 6/18/2018 22.0 d. 0%
5 Administer surveys via an online web link 5/18/2018 6/18/2018 22.0 d. 0%
6 Analysis of results gathered from surveys 6/18/2018 7/2/2018 11.0 d. 0%
7 Documentation 7/2/2018 8/31/2018 45.0 d. 0%
8 Write up a critical evaluation 7/2/2018 8/2/2018 24.0 d. 0%
9 Write up final report on the overall research topic and project 8/2/2018 8/31/2018 22.0 d. 0%
2

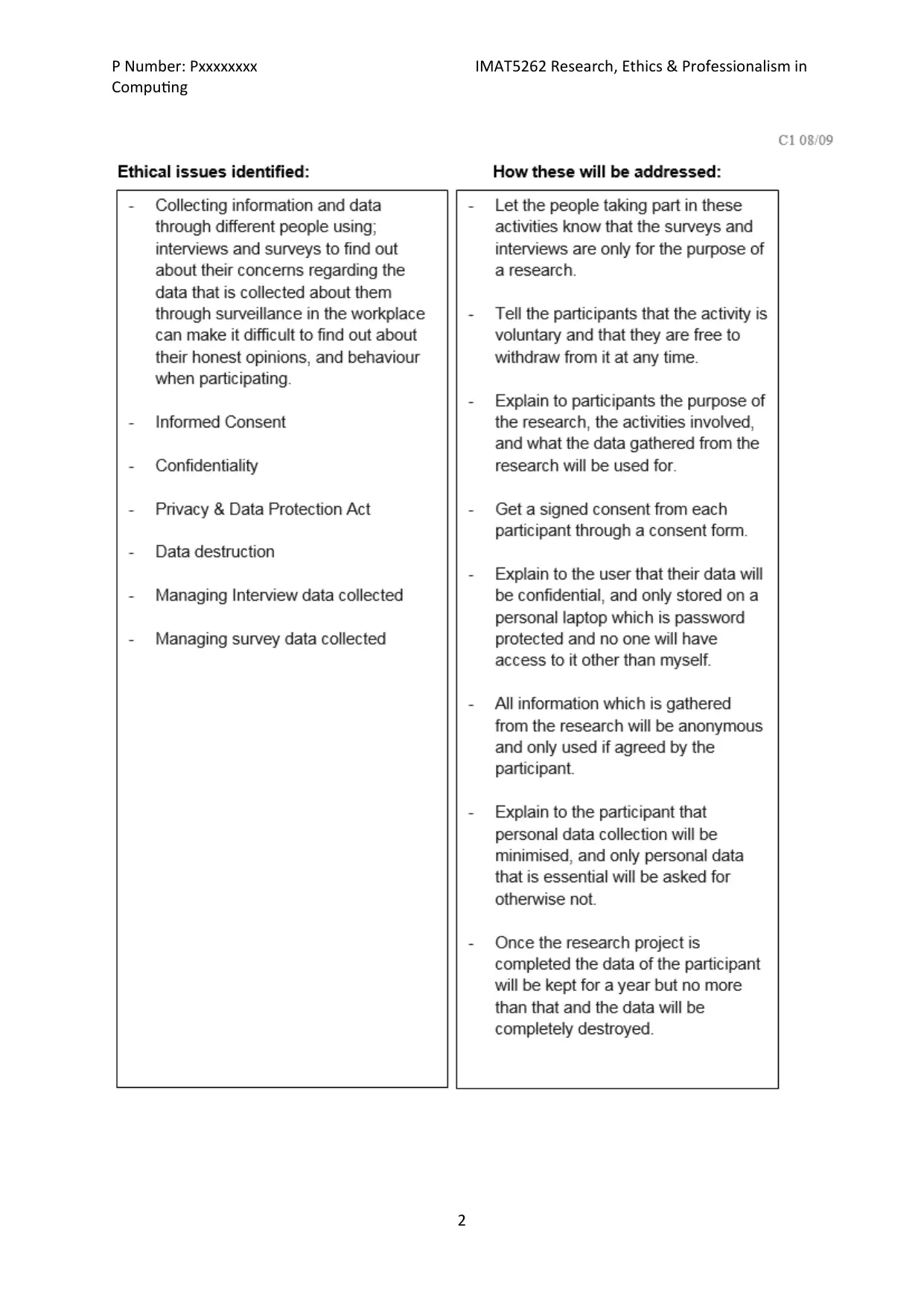
Appendix (ii): Ethical Review Form

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
1
Computing
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
2
Computing
2

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
3
Computing
3

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
4
Computing
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
Appendix (iii): Consent Form
The Ethics of Cyber Security Research Consent Form
Dear Participant,
The purpose of this interview and survey is for a research purpose only as it is part
of my research project “Ethics of Cyber Security.” The aim of this research project is
to investigate the ethics revolving around the use of data, data privacy and cyber
security in the workplace.
I am inviting you to take part in an interview and a survey in which you will be asked
to answer a series of questions; you may wish to complete them both on the same
day or you may to complete the survey in your own time and send it back to me.
The survey will be administered online and will only consume under 10 minutes of
your time.
Your participation in this research is voluntary and you have the right to withdraw any
time. You will get to keep a signed copy of the informed consent form if you wish to
take part in this research, and any information recorded from this research will not be
passed on to any third party. All the data and information collected from this research
is fully confidential and will only be stored on my personal laptop, and the university
account which is password protect and prevents anyone from accessing my account
other than myself.
The personal data collection from this research will be minimised and the personal
data which is necessarily needed will be asked for otherwise not. Your data will only
be used with this project but will not have any of your personal details included.
Once the research project is complete, the data and information gathered about the
participant will be kept for a maximum time of 1 year but, no more than that, and the
entire data and information collected will be fully destroyed.
If you have any questions regarding this project or research please do not hesitate to
contact myself XXXXXXX, student at De Montfort University via the following email
address; pxxxxxxxx@myemail.dmu.ac.uk
By signing this consent form you specify that you understand the following:
8. I understand the purpose of this project and agree to take part in this research
9. I understand that the data collected will only be used in this project
10. I understand that I can withdraw from this research at any time
11. I understand that the data will be fully destroyed as stated above
5
Computing
Appendix (iii): Consent Form
The Ethics of Cyber Security Research Consent Form
Dear Participant,
The purpose of this interview and survey is for a research purpose only as it is part
of my research project “Ethics of Cyber Security.” The aim of this research project is
to investigate the ethics revolving around the use of data, data privacy and cyber
security in the workplace.
I am inviting you to take part in an interview and a survey in which you will be asked
to answer a series of questions; you may wish to complete them both on the same
day or you may to complete the survey in your own time and send it back to me.
The survey will be administered online and will only consume under 10 minutes of
your time.
Your participation in this research is voluntary and you have the right to withdraw any
time. You will get to keep a signed copy of the informed consent form if you wish to
take part in this research, and any information recorded from this research will not be
passed on to any third party. All the data and information collected from this research
is fully confidential and will only be stored on my personal laptop, and the university
account which is password protect and prevents anyone from accessing my account
other than myself.
The personal data collection from this research will be minimised and the personal
data which is necessarily needed will be asked for otherwise not. Your data will only
be used with this project but will not have any of your personal details included.
Once the research project is complete, the data and information gathered about the
participant will be kept for a maximum time of 1 year but, no more than that, and the
entire data and information collected will be fully destroyed.
If you have any questions regarding this project or research please do not hesitate to
contact myself XXXXXXX, student at De Montfort University via the following email
address; pxxxxxxxx@myemail.dmu.ac.uk
By signing this consent form you specify that you understand the following:
8. I understand the purpose of this project and agree to take part in this research
9. I understand that the data collected will only be used in this project
10. I understand that I can withdraw from this research at any time
11. I understand that the data will be fully destroyed as stated above
5
P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
Participants Signature: _________________________________
Date of Participants Signature: ___________________________
Researcher’s Signature: __________________________________
Date of Researcher’s Signature: ____________________________
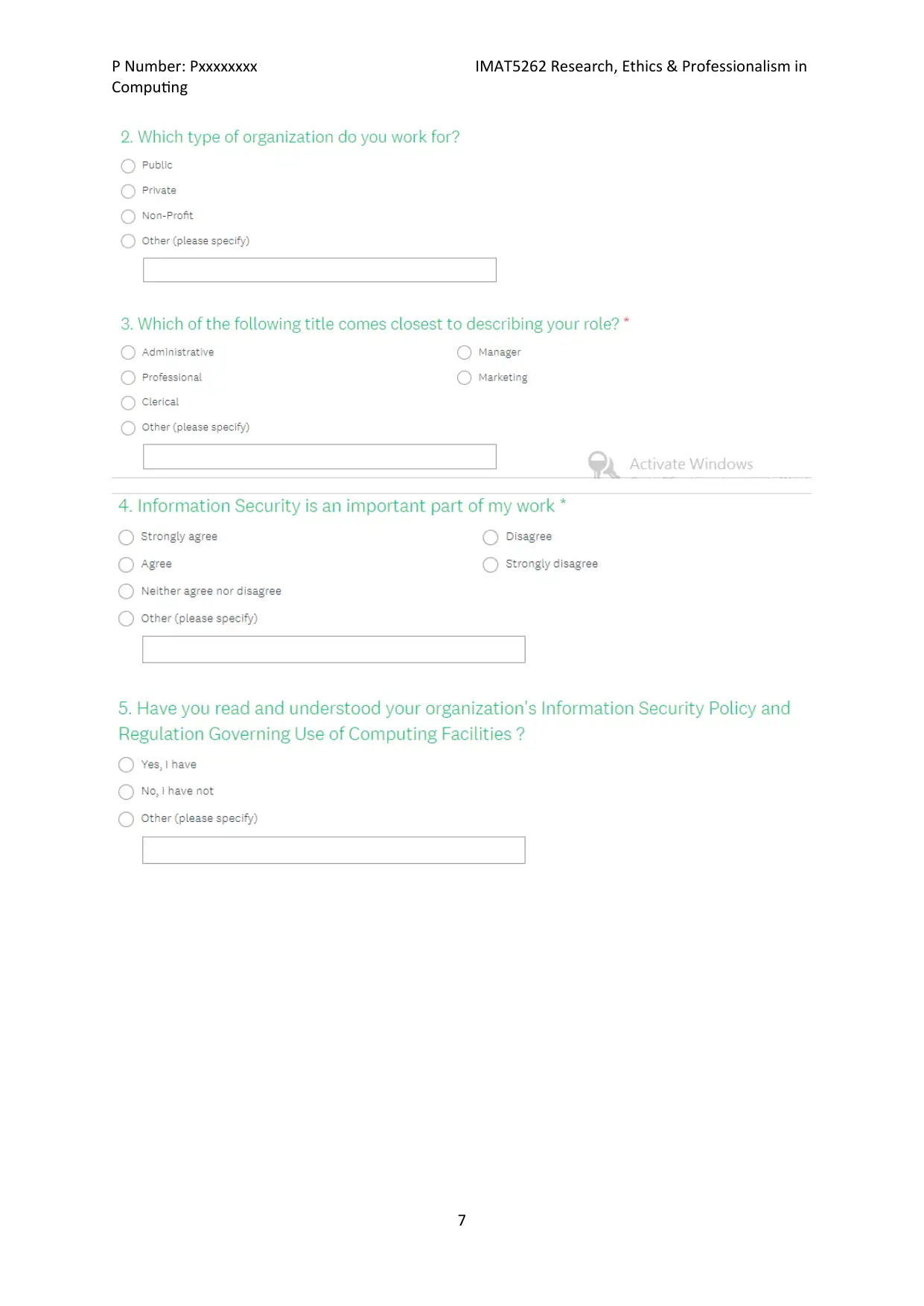
Appendix (iv): Pilot study
The online survey is accessible via the following web link
https://www.surveymonkey.com/r/JDHDCF3
The sample questions and survey are presented below in a screenshot.
6
Computing
Participants Signature: _________________________________
Date of Participants Signature: ___________________________
Researcher’s Signature: __________________________________
Date of Researcher’s Signature: ____________________________
Appendix (iv): Pilot study
The online survey is accessible via the following web link
https://www.surveymonkey.com/r/JDHDCF3
The sample questions and survey are presented below in a screenshot.
6
P Number: Pxxxxxxxx IMAT5262 Research, Ethics & Professionalism in
Computing
7
Computing
7
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





