Networking Technologies Report: LAN Design and Implementation
VerifiedAdded on 2020/07/23
|32
|7082
|103
Report
AI Summary
This report provides a comprehensive analysis of networking technologies, focusing on the design and implementation of a Local Area Network (LAN) for Beta Communication Ltd. The report begins with an introduction to various network types and topologies, including LAN, WAN, PAN, MAN, Mesh, Star, Bus, and Ring topologies, along with their benefits and limitations. It delves into the roles of software and hardware components, different server types, and workstation hardware interdependence. The core of the report involves designing a network system diagram using MS Visio, considering current and future user requirements and network infrastructure. This includes the design of the access, aggregation, and core layers, along with the use of Ethernet cabling and establishing storage connectivity. The report further details the implementation of the proposed design using simulation software, testing the network to meet user requirements, and documenting the test results against expected outcomes. Finally, the report recommends potential enhancements for the networked systems, addresses scalability, and designs a maintenance schedule that covers personnel allocation, backup and recovery policies, security, and general administration to support users. References are provided to support the information and findings presented in the report.

Networking Technologies 1
Networking Technologies
Student's Name
Instructor's Name
Date
Networking Technologies
Student's Name
Instructor's Name
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking Technologies 2
Contents
INTRODUCTION........................................................................................................................4
TASK 1...................................................................................................................................... 4
1.1 Types and Topologies of Networking Systems...............................................................4
Networking Topologies.................................................................................................. 10
1.2 Impact of network technology, communication and standards...................................15
1.3 Utilization of networking systems by protocols...........................................................16
TASK 2.................................................................................................................................... 16
2.1 Roles of software and hardware components..............................................................16
2.2 Different Server Types and selection requirements.....................................................17
2.3 Interdependence of workstation hardware.................................................................18
Task 3..................................................................................................................................... 19
3.1. Design a network system diagram using MS Visio or any other tools of your choice for
the given case study. In the design you should consider current and future provisions in
terms of user requirements and the network infrastructure itself....................................19
LAN Design [2][3]................................................................................................................... 21
Using Ethernet Cabling.......................................................................................................21
The Access Layer............................................................................................................ 21
Establishing Storage Connectivity......................................................................................22
The Aggregation Layer....................................................................................................23
The Core Layer............................................................................................................... 23
Benefits in Using the Proposed Solution [1][2][3]..................................................................24
Challenges in the Proposed Beta Communication LAN Design..............................................25
Task 4..................................................................................................................................... 25
4.1 Implement a network systems based on the proposed design. You are required to use
means of simulation software, establish a network according to the design in task 3......26
Implementation of Proposed Design..............................................................................26
4.2. Test network systems to meet user requirements. Your testing includes functionality
of the network to ensure that your developed network will operate seamlessly in a
physical environment so that it can satisfy user requirements..........................................28
Testing the Solution [4]..................................................................................................28
4.3. Document and analyse test result against expected results. While carrying out task
4.2, the testing of the network has produced a number of results. List the results you have
found in task 4.2 by contrasting them with your expected results....................................30
Test Results........................................................................................................................ 30
4.4. Recommend potential enhancement for the networked systems. Your discussions
should include how your developed network will cope with future changing needs and
Contents
INTRODUCTION........................................................................................................................4
TASK 1...................................................................................................................................... 4
1.1 Types and Topologies of Networking Systems...............................................................4
Networking Topologies.................................................................................................. 10
1.2 Impact of network technology, communication and standards...................................15
1.3 Utilization of networking systems by protocols...........................................................16
TASK 2.................................................................................................................................... 16
2.1 Roles of software and hardware components..............................................................16
2.2 Different Server Types and selection requirements.....................................................17
2.3 Interdependence of workstation hardware.................................................................18
Task 3..................................................................................................................................... 19
3.1. Design a network system diagram using MS Visio or any other tools of your choice for
the given case study. In the design you should consider current and future provisions in
terms of user requirements and the network infrastructure itself....................................19
LAN Design [2][3]................................................................................................................... 21
Using Ethernet Cabling.......................................................................................................21
The Access Layer............................................................................................................ 21
Establishing Storage Connectivity......................................................................................22
The Aggregation Layer....................................................................................................23
The Core Layer............................................................................................................... 23
Benefits in Using the Proposed Solution [1][2][3]..................................................................24
Challenges in the Proposed Beta Communication LAN Design..............................................25
Task 4..................................................................................................................................... 25
4.1 Implement a network systems based on the proposed design. You are required to use
means of simulation software, establish a network according to the design in task 3......26
Implementation of Proposed Design..............................................................................26
4.2. Test network systems to meet user requirements. Your testing includes functionality
of the network to ensure that your developed network will operate seamlessly in a
physical environment so that it can satisfy user requirements..........................................28
Testing the Solution [4]..................................................................................................28
4.3. Document and analyse test result against expected results. While carrying out task
4.2, the testing of the network has produced a number of results. List the results you have
found in task 4.2 by contrasting them with your expected results....................................30
Test Results........................................................................................................................ 30
4.4. Recommend potential enhancement for the networked systems. Your discussions
should include how your developed network will cope with future changing needs and

Networking Technologies 3
should address possible enhancements of your network to satisfy needs of changing
future environment............................................................................................................31
Scalability [3][4]..............................................................................................................31
4.5. Design a maintenance schedule to support the network system. Your maintenance
schedule should address various factors like personnel allocation, backup and recovery
policy, maintaining security & integrity; and general administration to support the users.
........................................................................................................................................... 32
Network Maintenance................................................................................................... 32
References............................................................................................................................. 34
should address possible enhancements of your network to satisfy needs of changing
future environment............................................................................................................31
Scalability [3][4]..............................................................................................................31
4.5. Design a maintenance schedule to support the network system. Your maintenance
schedule should address various factors like personnel allocation, backup and recovery
policy, maintaining security & integrity; and general administration to support the users.
........................................................................................................................................... 32
Network Maintenance................................................................................................... 32
References............................................................................................................................. 34
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking Technologies 4
INTRODUCTION
A network can be said as a group of computers sharing data and information with
each other using a data link. The computers on which sharing is being done are called nodes.
Networking Technologies are some mediums that helps in connecting with people lacking
geographical restrictions. These systems offer an easy way to share files. Also it proves
beneficial for resource sharing as devices like printers, modems, scanners can be shared over
all the computers in the network. These technologies gives flexible access to people as
accessing files from systems throughout the network is allowed. Some common types of
network consists of LAN ( Local Area Network), WAN ( Wireless LAN), PAN(Personal
Area Network) etc. The Beta Communication Ltd is a telecommunication company that deals
in telecom products. This report is about designing and implementing LAN in the Beta
Communication Ltd.
TASK 1
1.1 Types and Topologies of Networking Systems
As a Network Consultant, it is important to have a deep knowledge of all the types of
network because any customer can request for a different network any time depending on his
work schedules and lifestyle.
Some common types of network are:
1. Local Area Network (LAN) – LAN connects various network computers over short
distances. This connection can establish in buildings, schools, hostels or any place
where devices can connect over short distance (Luehmann and Tinelli, 2008). It can
also be said as a group of computers sharing a same communication line.
Benefits:
We can send e-mails between different nodes.
Centrally management of all the nodes attached is easy.
Communication through a LAN network is cheaper than the other networks.
The data is stored on the server computer which makes it more secure.
The same internet connection is served among all the users connected to the LAN.
INTRODUCTION
A network can be said as a group of computers sharing data and information with
each other using a data link. The computers on which sharing is being done are called nodes.
Networking Technologies are some mediums that helps in connecting with people lacking
geographical restrictions. These systems offer an easy way to share files. Also it proves
beneficial for resource sharing as devices like printers, modems, scanners can be shared over
all the computers in the network. These technologies gives flexible access to people as
accessing files from systems throughout the network is allowed. Some common types of
network consists of LAN ( Local Area Network), WAN ( Wireless LAN), PAN(Personal
Area Network) etc. The Beta Communication Ltd is a telecommunication company that deals
in telecom products. This report is about designing and implementing LAN in the Beta
Communication Ltd.
TASK 1
1.1 Types and Topologies of Networking Systems
As a Network Consultant, it is important to have a deep knowledge of all the types of
network because any customer can request for a different network any time depending on his
work schedules and lifestyle.
Some common types of network are:
1. Local Area Network (LAN) – LAN connects various network computers over short
distances. This connection can establish in buildings, schools, hostels or any place
where devices can connect over short distance (Luehmann and Tinelli, 2008). It can
also be said as a group of computers sharing a same communication line.
Benefits:
We can send e-mails between different nodes.
Centrally management of all the nodes attached is easy.
Communication through a LAN network is cheaper than the other networks.
The data is stored on the server computer which makes it more secure.
The same internet connection is served among all the users connected to the LAN.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking Technologies 5
Limitations:
Less chance to move in a different location.
Server maintenance is expensive. The set up cost used in the implementation and then
maintenance of a LAN is quite expensive (Burgess, 2009).
This connection only covers a limited area as it covers short distances.
The LAN administrator has permissions to check the files on any computer connected
to the server any time and somewhere it violates users privacy (Luehmann and Tinelli,
2008).
A LAN administrator is always required as if sometime errors or any problems attack
the system, the administrator can solve it. His/her absence can lead to a huge loss of
time which can affect the company as well.
Limitations:
Less chance to move in a different location.
Server maintenance is expensive. The set up cost used in the implementation and then
maintenance of a LAN is quite expensive (Burgess, 2009).
This connection only covers a limited area as it covers short distances.
The LAN administrator has permissions to check the files on any computer connected
to the server any time and somewhere it violates users privacy (Luehmann and Tinelli,
2008).
A LAN administrator is always required as if sometime errors or any problems attack
the system, the administrator can solve it. His/her absence can lead to a huge loss of
time which can affect the company as well.
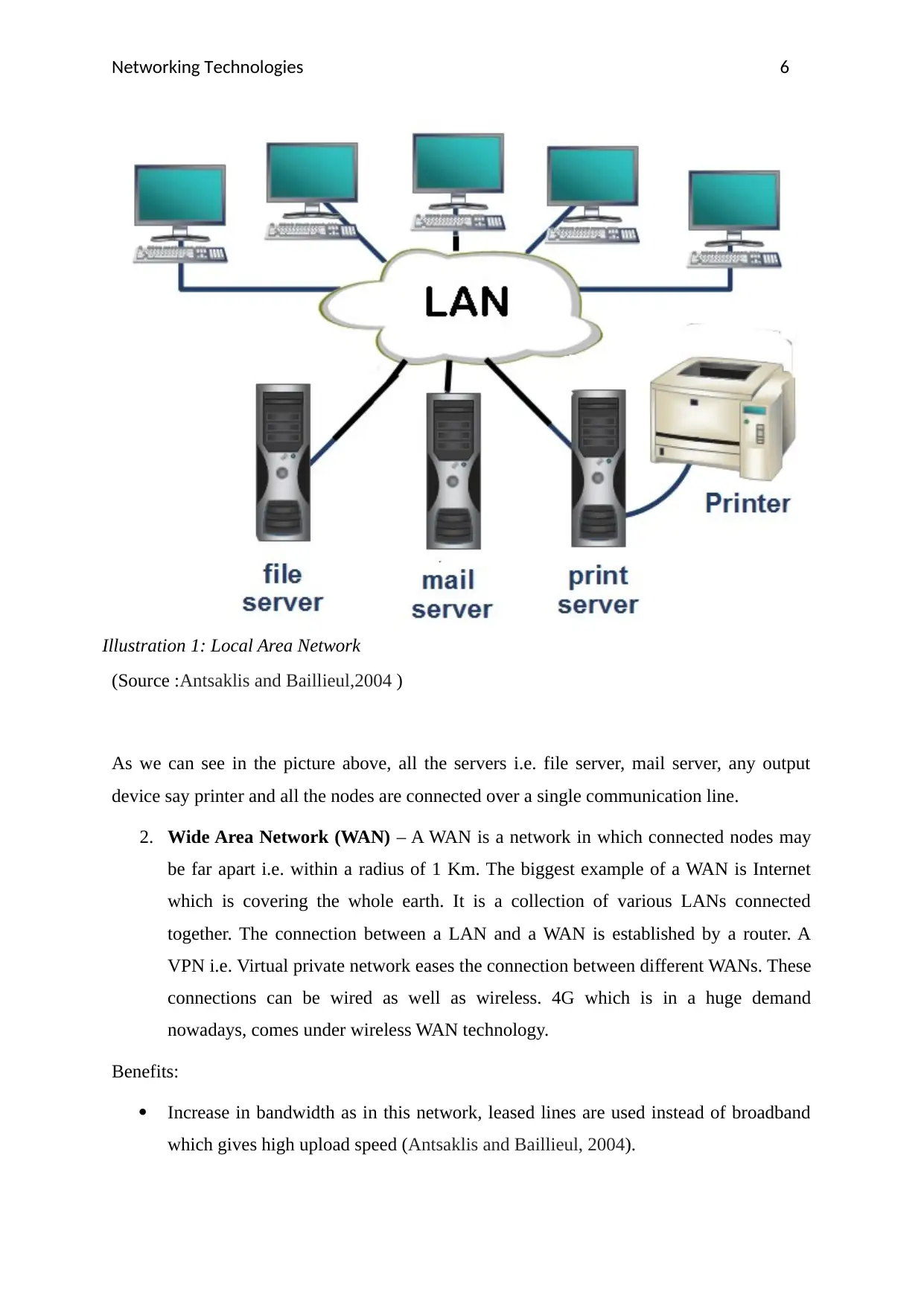
Networking Technologies 6
(Source :Antsaklis and Baillieul,2004 )
As we can see in the picture above, all the servers i.e. file server, mail server, any output
device say printer and all the nodes are connected over a single communication line.
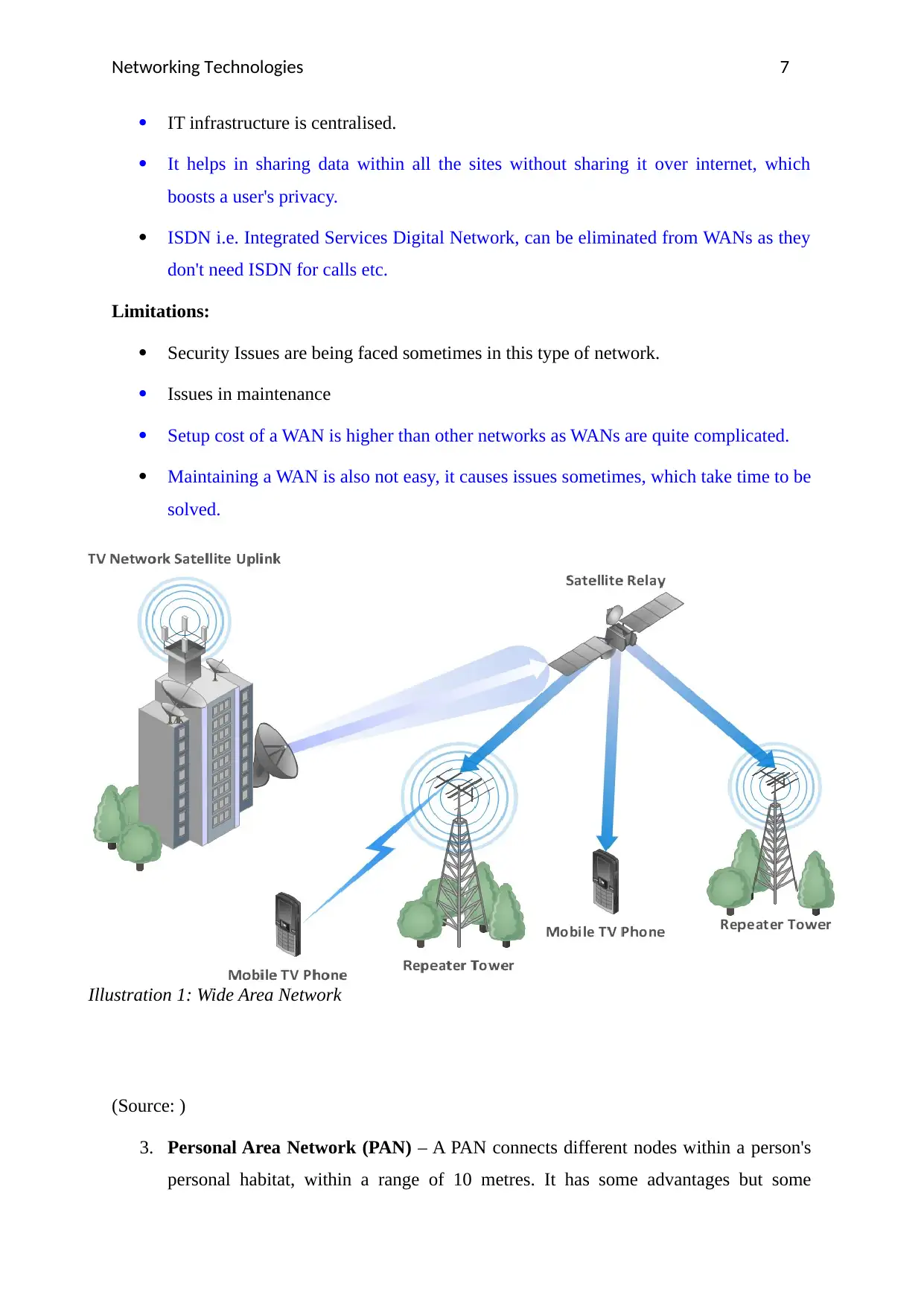
2. Wide Area Network (WAN) – A WAN is a network in which connected nodes may
be far apart i.e. within a radius of 1 Km. The biggest example of a WAN is Internet
which is covering the whole earth. It is a collection of various LANs connected
together. The connection between a LAN and a WAN is established by a router. A
VPN i.e. Virtual private network eases the connection between different WANs. These
connections can be wired as well as wireless. 4G which is in a huge demand
nowadays, comes under wireless WAN technology.
Benefits:
Increase in bandwidth as in this network, leased lines are used instead of broadband
which gives high upload speed (Antsaklis and Baillieul, 2004).
Illustration 1: Local Area Network
(Source :Antsaklis and Baillieul,2004 )
As we can see in the picture above, all the servers i.e. file server, mail server, any output
device say printer and all the nodes are connected over a single communication line.
2. Wide Area Network (WAN) – A WAN is a network in which connected nodes may
be far apart i.e. within a radius of 1 Km. The biggest example of a WAN is Internet
which is covering the whole earth. It is a collection of various LANs connected
together. The connection between a LAN and a WAN is established by a router. A
VPN i.e. Virtual private network eases the connection between different WANs. These
connections can be wired as well as wireless. 4G which is in a huge demand
nowadays, comes under wireless WAN technology.
Benefits:
Increase in bandwidth as in this network, leased lines are used instead of broadband
which gives high upload speed (Antsaklis and Baillieul, 2004).
Illustration 1: Local Area Network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Networking Technologies 7
IT infrastructure is centralised.
It helps in sharing data within all the sites without sharing it over internet, which
boosts a user's privacy.
ISDN i.e. Integrated Services Digital Network, can be eliminated from WANs as they
don't need ISDN for calls etc.
Limitations:
Security Issues are being faced sometimes in this type of network.
Issues in maintenance
Setup cost of a WAN is higher than other networks as WANs are quite complicated.
Maintaining a WAN is also not easy, it causes issues sometimes, which take time to be
solved.
(Source: )
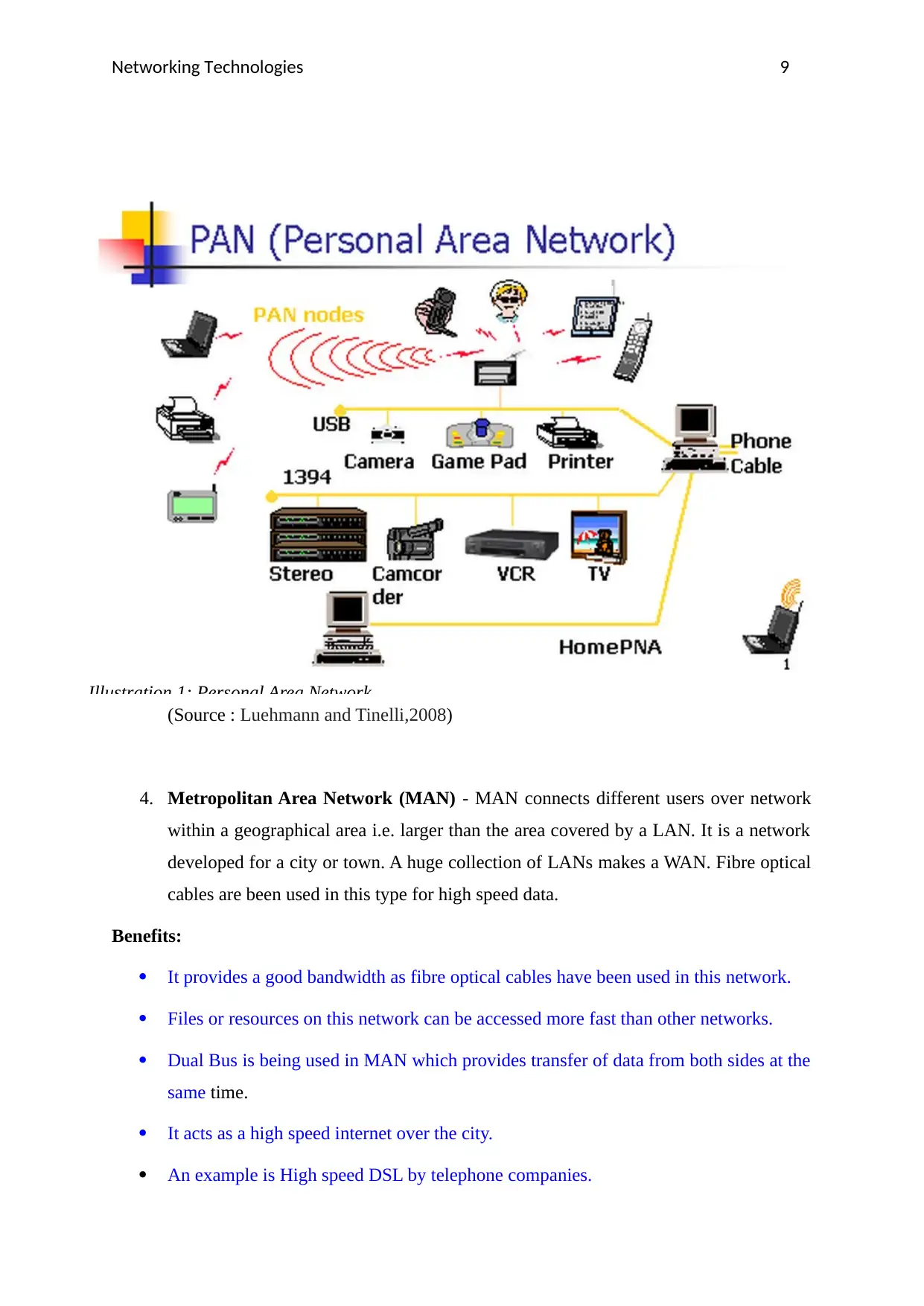
3. Personal Area Network (PAN) – A PAN connects different nodes within a person's
personal habitat, within a range of 10 metres. It has some advantages but some
Illustration 1: Wide Area Network
IT infrastructure is centralised.
It helps in sharing data within all the sites without sharing it over internet, which
boosts a user's privacy.
ISDN i.e. Integrated Services Digital Network, can be eliminated from WANs as they
don't need ISDN for calls etc.
Limitations:
Security Issues are being faced sometimes in this type of network.
Issues in maintenance
Setup cost of a WAN is higher than other networks as WANs are quite complicated.
Maintaining a WAN is also not easy, it causes issues sometimes, which take time to be
solved.
(Source: )
3. Personal Area Network (PAN) – A PAN connects different nodes within a person's
personal habitat, within a range of 10 metres. It has some advantages but some
Illustration 1: Wide Area Network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking Technologies 8
disadvantages too. It is handy and safe but sometimes have a slow speed for data
transfer. Explaining with an example, If a person is travelling along with his tablet, a
PDA( personal digital assistant) and a printer that is portable, he can interconnect
them without any plug-in and take the output as well (Burgess, 2009). This makes
PAN different from other networks.
Benefits:
There are no security issues in this network because it is limited to a very small area.
A PAN network is movable. It is easy to move this network from one place to another.
It can be established either wirelessly or by cables (Luehmann and Tinelli, 2008).
Less technical skills required than the other networks because it is less complicated.
Easy and simple to set up a PAN network.
Limitations:
Instead it's simple to implement a PAN network but it is costly to use.
It has a small Range of 10 metres only.
Transmission speed is not so high in PAN. It is moderate.
In this network, sometimes there are compatibility issues because WPAN techniques
are usually not compatible with each other.
disadvantages too. It is handy and safe but sometimes have a slow speed for data
transfer. Explaining with an example, If a person is travelling along with his tablet, a
PDA( personal digital assistant) and a printer that is portable, he can interconnect
them without any plug-in and take the output as well (Burgess, 2009). This makes
PAN different from other networks.
Benefits:
There are no security issues in this network because it is limited to a very small area.
A PAN network is movable. It is easy to move this network from one place to another.
It can be established either wirelessly or by cables (Luehmann and Tinelli, 2008).
Less technical skills required than the other networks because it is less complicated.
Easy and simple to set up a PAN network.
Limitations:
Instead it's simple to implement a PAN network but it is costly to use.
It has a small Range of 10 metres only.
Transmission speed is not so high in PAN. It is moderate.
In this network, sometimes there are compatibility issues because WPAN techniques
are usually not compatible with each other.
Networking Technologies 9
(Source : Luehmann and Tinelli,2008)
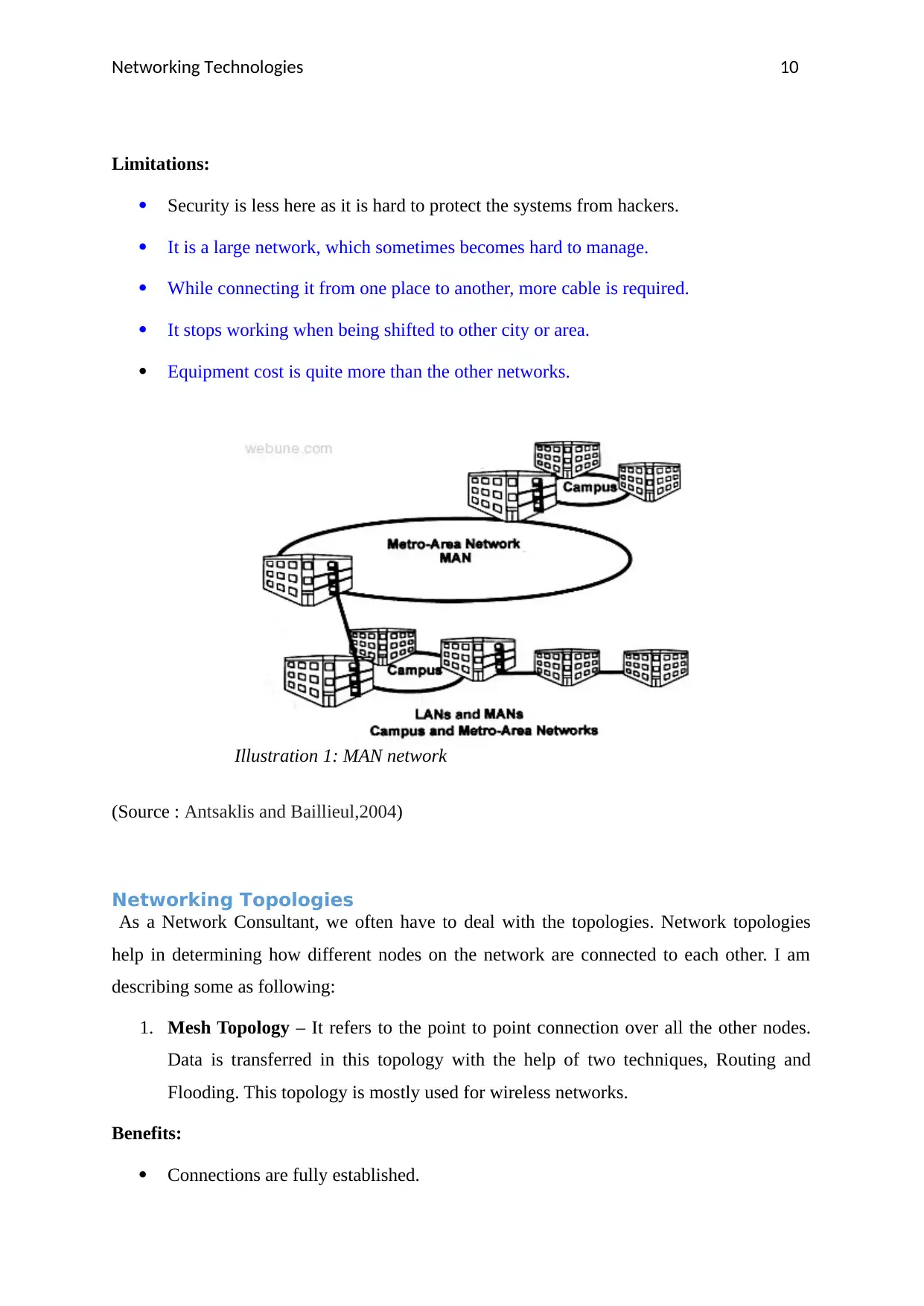
4. Metropolitan Area Network (MAN) - MAN connects different users over network
within a geographical area i.e. larger than the area covered by a LAN. It is a network
developed for a city or town. A huge collection of LANs makes a WAN. Fibre optical
cables are been used in this type for high speed data.
Benefits:
It provides a good bandwidth as fibre optical cables have been used in this network.
Files or resources on this network can be accessed more fast than other networks.
Dual Bus is being used in MAN which provides transfer of data from both sides at the
same time.
It acts as a high speed internet over the city.
An example is High speed DSL by telephone companies.
Illustration 1: Personal Area Network
(Source : Luehmann and Tinelli,2008)
4. Metropolitan Area Network (MAN) - MAN connects different users over network
within a geographical area i.e. larger than the area covered by a LAN. It is a network
developed for a city or town. A huge collection of LANs makes a WAN. Fibre optical
cables are been used in this type for high speed data.
Benefits:
It provides a good bandwidth as fibre optical cables have been used in this network.
Files or resources on this network can be accessed more fast than other networks.
Dual Bus is being used in MAN which provides transfer of data from both sides at the
same time.
It acts as a high speed internet over the city.
An example is High speed DSL by telephone companies.
Illustration 1: Personal Area Network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Networking Technologies 10
Limitations:
Security is less here as it is hard to protect the systems from hackers.
It is a large network, which sometimes becomes hard to manage.
While connecting it from one place to another, more cable is required.
It stops working when being shifted to other city or area.
Equipment cost is quite more than the other networks.
(Source : Antsaklis and Baillieul,2004)
Networking Topologies
As a Network Consultant, we often have to deal with the topologies. Network topologies
help in determining how different nodes on the network are connected to each other. I am
describing some as following:
1. Mesh Topology – It refers to the point to point connection over all the other nodes.
Data is transferred in this topology with the help of two techniques, Routing and
Flooding. This topology is mostly used for wireless networks.
Benefits:
Connections are fully established.
Illustration 1: MAN network
Limitations:
Security is less here as it is hard to protect the systems from hackers.
It is a large network, which sometimes becomes hard to manage.
While connecting it from one place to another, more cable is required.
It stops working when being shifted to other city or area.
Equipment cost is quite more than the other networks.
(Source : Antsaklis and Baillieul,2004)
Networking Topologies
As a Network Consultant, we often have to deal with the topologies. Network topologies
help in determining how different nodes on the network are connected to each other. I am
describing some as following:
1. Mesh Topology – It refers to the point to point connection over all the other nodes.
Data is transferred in this topology with the help of two techniques, Routing and
Flooding. This topology is mostly used for wireless networks.
Benefits:
Connections are fully established.
Illustration 1: MAN network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking Technologies 11
Strong
High security
Many devices transmit data at the same time, so it handles huge amount of data.
Any error or problem in one device does not affect the other devices in the network.
The other systems work keep going on without any issue.
Addition of new devices does not interrupt the transmission in previous ones.
Limitations:
In starting, configuring is quite tough.
Cable used is costly.
Implementing and then maintenance of this topology is hard.
High implementation cost makes it a less wise option.
Wiring in bulk is requires which adds more cost to it.
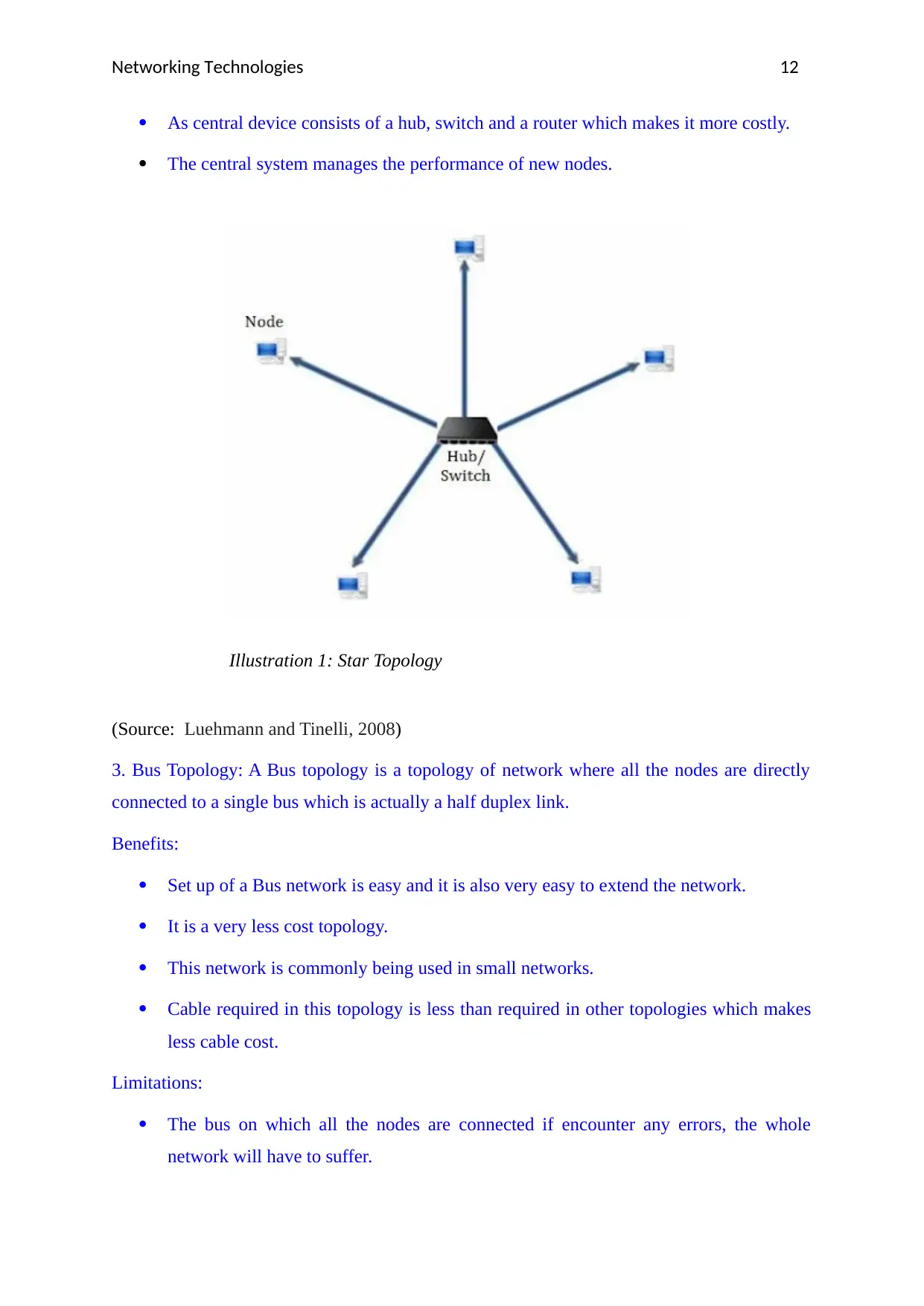
2. Star Topology – This topology says that all the nodes are connected through a single hub
which acts as a central node of the system.
Benefits:
Troubleshooting is easy.
Setup is easy and it is very simple to connect new nodes as it does not affect the rest
of the systems.
This topology is Fast (Burgess, 2009).
Far much better than Bus topology because of its performance.
Monitoring the network is easy because of its centralised management.
Limitations:
Installation cost high.
Quite expensive (Luehmann and Tinelli, 2008).
There is a centralised system. If it fails, the whole network and the devices have to
suffer.
Strong
High security
Many devices transmit data at the same time, so it handles huge amount of data.
Any error or problem in one device does not affect the other devices in the network.
The other systems work keep going on without any issue.
Addition of new devices does not interrupt the transmission in previous ones.
Limitations:
In starting, configuring is quite tough.
Cable used is costly.
Implementing and then maintenance of this topology is hard.
High implementation cost makes it a less wise option.
Wiring in bulk is requires which adds more cost to it.
2. Star Topology – This topology says that all the nodes are connected through a single hub
which acts as a central node of the system.
Benefits:
Troubleshooting is easy.
Setup is easy and it is very simple to connect new nodes as it does not affect the rest
of the systems.
This topology is Fast (Burgess, 2009).
Far much better than Bus topology because of its performance.
Monitoring the network is easy because of its centralised management.
Limitations:
Installation cost high.
Quite expensive (Luehmann and Tinelli, 2008).
There is a centralised system. If it fails, the whole network and the devices have to
suffer.
Networking Technologies 12
As central device consists of a hub, switch and a router which makes it more costly.
The central system manages the performance of new nodes.
(Source: Luehmann and Tinelli, 2008)
3. Bus Topology: A Bus topology is a topology of network where all the nodes are directly
connected to a single bus which is actually a half duplex link.
Benefits:
Set up of a Bus network is easy and it is also very easy to extend the network.
It is a very less cost topology.
This network is commonly being used in small networks.
Cable required in this topology is less than required in other topologies which makes
less cable cost.
Limitations:
The bus on which all the nodes are connected if encounter any errors, the whole
network will have to suffer.
Illustration 1: Star Topology
As central device consists of a hub, switch and a router which makes it more costly.
The central system manages the performance of new nodes.
(Source: Luehmann and Tinelli, 2008)
3. Bus Topology: A Bus topology is a topology of network where all the nodes are directly
connected to a single bus which is actually a half duplex link.
Benefits:
Set up of a Bus network is easy and it is also very easy to extend the network.
It is a very less cost topology.
This network is commonly being used in small networks.
Cable required in this topology is less than required in other topologies which makes
less cable cost.
Limitations:
The bus on which all the nodes are connected if encounter any errors, the whole
network will have to suffer.
Illustration 1: Star Topology
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 32
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





