Incident Command System: Resources and Homeland Security Report
VerifiedAdded on 2022/09/14
|9
|1419
|20
Report
AI Summary
This report provides an overview of the Incident Command System (ICS), a management system designed for effective domestic incident management. It explores core homeland security aspects, emphasizing the integration of facilities, personnel, procedures, and communications within an organizational structure. The report details the roles within the ICS, including the command staff, public information officer, and safety officer, and their responsibilities. It highlights the contributions of private security professionals to homeland security, focusing on their role in protecting infrastructure and information. The report also defines the role of a security officer in planning and implementing safety measures, coordinating resources, and managing security aspects to ensure the efficient organization of information within various sectors. The report references key literature on the ICS, including studies on its application, adaptation, and the role of security professionals.

Running head: INCIDENT COMMAND SYSTEM
INCIDENT COMMAND SYSTEM RESOURCES
Name of the Student
Name of the University
Author Note
INCIDENT COMMAND SYSTEM RESOURCES
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INCIDENT COMMAND SYSTEM
Table of Contents
Organizational Chart for Incident Command..................................................................................2
Core homeland security aspects.......................................................................................................3
Contribution of private security professionals towards nation’s homeland....................................4
Role of an Security officer...............................................................................................................5
References........................................................................................................................................7
INCIDENT COMMAND SYSTEM
Table of Contents
Organizational Chart for Incident Command..................................................................................2
Core homeland security aspects.......................................................................................................3
Contribution of private security professionals towards nation’s homeland....................................4
Role of an Security officer...............................................................................................................5
References........................................................................................................................................7
2
INCIDENT COMMAND SYSTEM
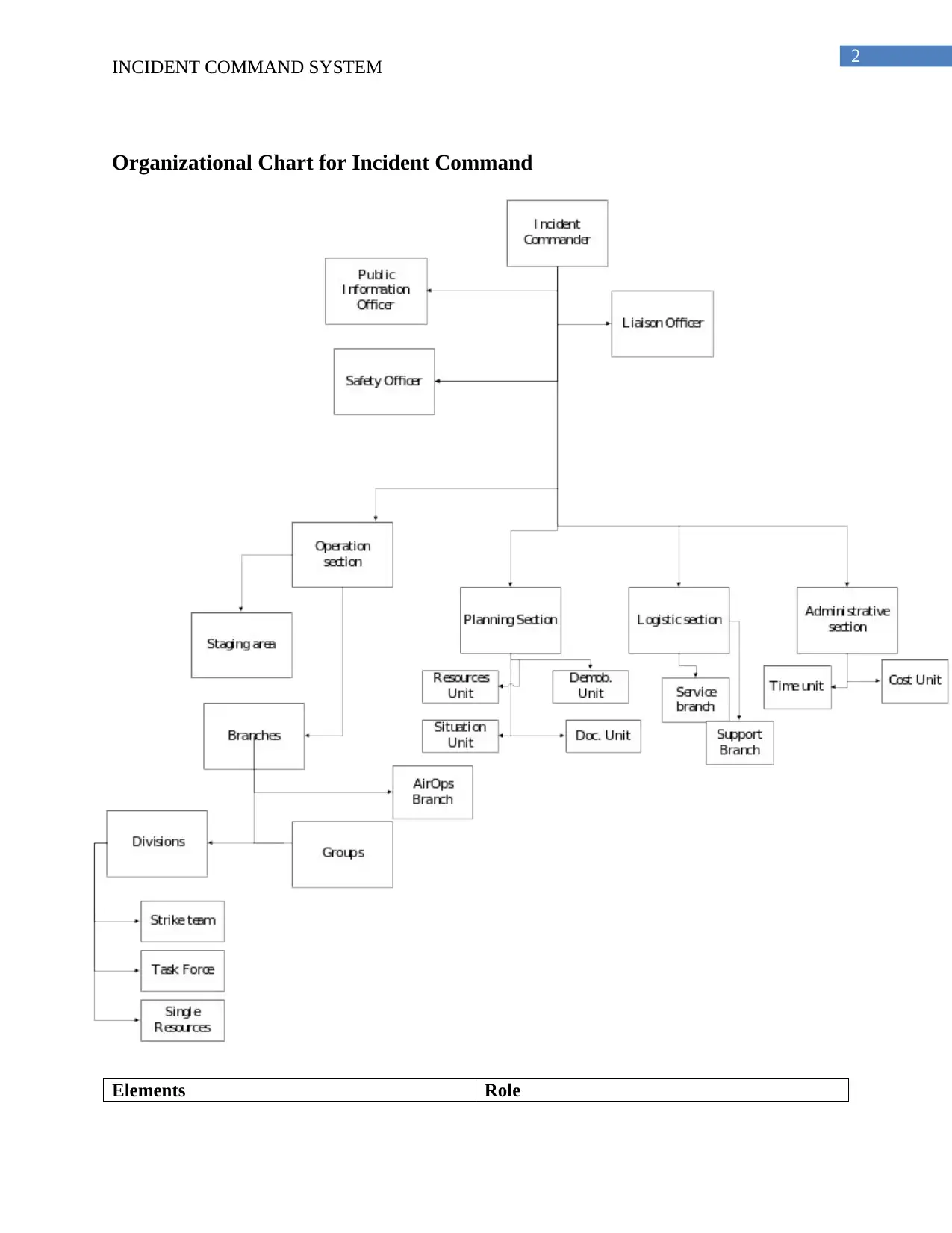
Organizational Chart for Incident Command
Elements Role
INCIDENT COMMAND SYSTEM
Organizational Chart for Incident Command
Elements Role
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
INCIDENT COMMAND SYSTEM
Command staff Responsible for managing the different
activities associated with the incident
Public information officer The public information officer is responsible
for managing the information
Safety officer Responsible for managing the security
Operation section Manages the overall operations associated with
IC
Planning sector For the purpose of managing the incident
within the system it is important to have proper
planning
Logistic section Manages the service and supply associated
with the incident
Finance and administrative section Responsible for organizing the different
components associated with finance
Core homeland security aspects
The incident command system is used for the purpose of enabling efficient and effective
domestic incident management with the use of proper facilities, personal, procedures and
communications operating within organizational structure. There are several concepts that are
implemented for the purpose of providing core Homeland security. The main objective of the
Homeland security is to provide the system from unwanted threats, errors and hazards. The
INCIDENT COMMAND SYSTEM
Command staff Responsible for managing the different
activities associated with the incident
Public information officer The public information officer is responsible
for managing the information
Safety officer Responsible for managing the security
Operation section Manages the overall operations associated with
IC
Planning sector For the purpose of managing the incident
within the system it is important to have proper
planning
Logistic section Manages the service and supply associated
with the incident
Finance and administrative section Responsible for organizing the different
components associated with finance
Core homeland security aspects
The incident command system is used for the purpose of enabling efficient and effective
domestic incident management with the use of proper facilities, personal, procedures and
communications operating within organizational structure. There are several concepts that are
implemented for the purpose of providing core Homeland security. The main objective of the
Homeland security is to provide the system from unwanted threats, errors and hazards. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INCIDENT COMMAND SYSTEM
Department of Homeland security has the ability to enhance the security measures by managing
the borders and securing the cyberspace (Givens, 2015). It can be stated that with the help of
proper enhancement in the administrative law it becomes easy to improve the response to the
incident. The focus is to secure the data that are transmitted through the systems. With the use of
proper security measures it becomes easy to protect the data from threats (Ansell & Keller,
2014). The focus is to prevent the data from security challenges. This offers enhanced privacy
policy for the purpose of protecting the information from unwanted threats. There are several
functional areas associated with the incident command system these include command,
operations, planning, logistic and administration finance. It is important to manage each faces
effectively. Each part please important role for homeland security. It becomes very difficult to
remove any security aspect from the system. Without proper security measures it becomes very
difficult to manage the security aspect. The security features that are associated with the ICS
structure include providing proper access control, managing the traffic and crowd control and
also enforcing proper law interface (Jensen & Thompson, 2016). With the use of proper security
measures it becomes easy to protect the homeland facilities.
Contribution of private security professionals towards nation’s homeland
The main reason behind having an Incident Command System (ICS) is that it provides a
proper management system that has been designed for the purpose of enabling effective and
efficient domestic incident management. This is achieved with the use of integration of proper
facilities, personnel, equipment, and procedures, and within an organizational structure. Privacy
security factors are considered to be one of the most crucial factors while protecting the
homeland infrastructure (Bogucki & Schulz, 2015). The Department of Homeland security has
INCIDENT COMMAND SYSTEM
Department of Homeland security has the ability to enhance the security measures by managing
the borders and securing the cyberspace (Givens, 2015). It can be stated that with the help of
proper enhancement in the administrative law it becomes easy to improve the response to the
incident. The focus is to secure the data that are transmitted through the systems. With the use of
proper security measures it becomes easy to protect the data from threats (Ansell & Keller,
2014). The focus is to prevent the data from security challenges. This offers enhanced privacy
policy for the purpose of protecting the information from unwanted threats. There are several
functional areas associated with the incident command system these include command,
operations, planning, logistic and administration finance. It is important to manage each faces
effectively. Each part please important role for homeland security. It becomes very difficult to
remove any security aspect from the system. Without proper security measures it becomes very
difficult to manage the security aspect. The security features that are associated with the ICS
structure include providing proper access control, managing the traffic and crowd control and
also enforcing proper law interface (Jensen & Thompson, 2016). With the use of proper security
measures it becomes easy to protect the homeland facilities.
Contribution of private security professionals towards nation’s homeland
The main reason behind having an Incident Command System (ICS) is that it provides a
proper management system that has been designed for the purpose of enabling effective and
efficient domestic incident management. This is achieved with the use of integration of proper
facilities, personnel, equipment, and procedures, and within an organizational structure. Privacy
security factors are considered to be one of the most crucial factors while protecting the
homeland infrastructure (Bogucki & Schulz, 2015). The Department of Homeland security has

5
INCIDENT COMMAND SYSTEM
established the different laws for the purpose of protecting the pretty girl factors associated with
the system. The main role of the private sector and law in force meant official was to provide
proper security so that they can combat with the traits that have the potential to impact the
infrastructure. The key role of private sector is to protect the information associated with the
infrastructure and also insures that only proper authorized persons are given in the access over
information. The corporate security is mainly known as the internal security that is provided for
the purpose of providing better security towards an organization. On the other hand contact
security is referred to the security personnel that offer services towards the homeowners, Banks
and business without any fees. It can be stated that with the help of proper law enforcement and
privacy measures it becomes easy to manage the gap between the country’s infrastructures. With
the use of proper privacy measure it becomes easy to protect the data sets and also ensures that
unwanted challenges are managed successfully (Chang, 2017). The benefits that are offered with
the use of incident command system is that it helps in defining the chain of the command with
the help of a modular format and also ensure that proper safety of respondents, students, faculty
and workers are provided. Apart from these proper responses is also achieved with the use of
incident command system. The privacy needs to be managed efficiently so that it can enhance
the overall performance in the homeland infrastructure.
Role of an Security officer
The main role is to provide proper facilities towards the different section of the
homeland. With the help of proper facilities and maintenance it becomes easy to manage the
information flow. The role of a security officer is to plan and implement proper safety towards
the members associated with the homeland. With the help of incident command system it can be
INCIDENT COMMAND SYSTEM
established the different laws for the purpose of protecting the pretty girl factors associated with
the system. The main role of the private sector and law in force meant official was to provide
proper security so that they can combat with the traits that have the potential to impact the
infrastructure. The key role of private sector is to protect the information associated with the
infrastructure and also insures that only proper authorized persons are given in the access over
information. The corporate security is mainly known as the internal security that is provided for
the purpose of providing better security towards an organization. On the other hand contact
security is referred to the security personnel that offer services towards the homeowners, Banks
and business without any fees. It can be stated that with the help of proper law enforcement and
privacy measures it becomes easy to manage the gap between the country’s infrastructures. With
the use of proper privacy measure it becomes easy to protect the data sets and also ensures that
unwanted challenges are managed successfully (Chang, 2017). The benefits that are offered with
the use of incident command system is that it helps in defining the chain of the command with
the help of a modular format and also ensure that proper safety of respondents, students, faculty
and workers are provided. Apart from these proper responses is also achieved with the use of
incident command system. The privacy needs to be managed efficiently so that it can enhance
the overall performance in the homeland infrastructure.
Role of an Security officer
The main role is to provide proper facilities towards the different section of the
homeland. With the help of proper facilities and maintenance it becomes easy to manage the
information flow. The role of a security officer is to plan and implement proper safety towards
the members associated with the homeland. With the help of incident command system it can be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INCIDENT COMMAND SYSTEM
stated that there is a need to have proper planning and management functions that will be capable
of providing better facilities towards the systematic approach. These functions include
integrating proper communication media, coordinating with the resource management and the
location and successfully planning the resources. As a security officer it is important to ensure
that every data set are protected and prevented from unwanted attackers. Apart from this it
becomes essential to manage the security aspects (Rimstad et al., 2014). The focus is to enhance
the overall security aspects so that it becomes easy to align the overall activities within the
workplace and other places. Security officer must manage all the aspects of efficiently so that the
chances of errors can be reduced. It is important to organize the information within the different
sectors so that it can meet the overall expected. As a security officer it is the essential to manage
the security related to every aspect of the homeland. With the use of proper technologies and
planning it becomes easy to manage the overall performance and security associated with the
information. Security is one of the most efficient technologies as this helps in organizing the
different components related to the management system. For organizing activities related to
every system it becomes essential to implement security measures. Security officer is responsible
for managing proper efficiency and thus it is important to manage the data sets.
INCIDENT COMMAND SYSTEM
stated that there is a need to have proper planning and management functions that will be capable
of providing better facilities towards the systematic approach. These functions include
integrating proper communication media, coordinating with the resource management and the
location and successfully planning the resources. As a security officer it is important to ensure
that every data set are protected and prevented from unwanted attackers. Apart from this it
becomes essential to manage the security aspects (Rimstad et al., 2014). The focus is to enhance
the overall security aspects so that it becomes easy to align the overall activities within the
workplace and other places. Security officer must manage all the aspects of efficiently so that the
chances of errors can be reduced. It is important to organize the information within the different
sectors so that it can meet the overall expected. As a security officer it is the essential to manage
the security related to every aspect of the homeland. With the use of proper technologies and
planning it becomes easy to manage the overall performance and security associated with the
information. Security is one of the most efficient technologies as this helps in organizing the
different components related to the management system. For organizing activities related to
every system it becomes essential to implement security measures. Security officer is responsible
for managing proper efficiency and thus it is important to manage the data sets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INCIDENT COMMAND SYSTEM
References
Ansell, C., & Keller, A. (2014). Adapting the Incident Command Model for Knowledge-Based
Crises. IBM Center for the Business of Government, Collaboration Series.
Bogucki, S., & Schulz, K. J. (2015). Incident command system and national incident
management system. Emergency Medical Services: Clinical Practice and Systems
Oversight,, 255-263.
Chang, H. H. (2017). A literature review and analysis of the incident command
system. International journal of emergency management, 13(1), 50-67.
Givens, A. D. (2015). Strengthening Cyber Incident Response Capabilities Through Education
and Training in the Incident Command System. Journal of the National Cybersecurity
Institute, 2(3), 65-75.
Incident Command System Resources | FEMA.gov. (2020). Retrieved 5 April 2020, from
https://www.fema.gov/incident-command-system-resources
Jensen, J., & Thompson, S. (2016). The incident command system: a literature
review. Disasters, 40(1), 158-182.
Rimstad, R., Njå, O., Rake, E. L., & Braut, G. S. (2014). Incident command and information
flows in a large‐scale emergency operation. Journal of Contingencies and Crisis
management, 22(1), 29-38.
INCIDENT COMMAND SYSTEM
References
Ansell, C., & Keller, A. (2014). Adapting the Incident Command Model for Knowledge-Based
Crises. IBM Center for the Business of Government, Collaboration Series.
Bogucki, S., & Schulz, K. J. (2015). Incident command system and national incident
management system. Emergency Medical Services: Clinical Practice and Systems
Oversight,, 255-263.
Chang, H. H. (2017). A literature review and analysis of the incident command
system. International journal of emergency management, 13(1), 50-67.
Givens, A. D. (2015). Strengthening Cyber Incident Response Capabilities Through Education
and Training in the Incident Command System. Journal of the National Cybersecurity
Institute, 2(3), 65-75.
Incident Command System Resources | FEMA.gov. (2020). Retrieved 5 April 2020, from
https://www.fema.gov/incident-command-system-resources
Jensen, J., & Thompson, S. (2016). The incident command system: a literature
review. Disasters, 40(1), 158-182.
Rimstad, R., Njå, O., Rake, E. L., & Braut, G. S. (2014). Incident command and information
flows in a large‐scale emergency operation. Journal of Contingencies and Crisis
management, 22(1), 29-38.
8
INCIDENT COMMAND SYSTEM
Overview (Tutorial): The Incident Command System. (2020).
https://www.nationalservice.gov/sites/default/files/olc/moodle/ds_online_orientation/
viewf265.html?id=3139&chapterid=908
INCIDENT COMMAND SYSTEM
Overview (Tutorial): The Incident Command System. (2020).
https://www.nationalservice.gov/sites/default/files/olc/moodle/ds_online_orientation/
viewf265.html?id=3139&chapterid=908
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




