CMP73001 Cybersecurity: MyHealth Company Information Assets Report
VerifiedAdded on 2023/01/17
|20
|3704
|91
Report
AI Summary
This report, prepared for a cybersecurity management assignment, analyzes MyHealth Company's information assets, including database servers, web servers, and personal computer systems. It identifies and manages these assets, adhering to Australian cybersecurity standards and utilizing security policies, including acceptable use, access control, and password policies. The report details vulnerability management and risk management, applying the ISO 27001 framework to secure the company's assets from cyber-attacks. It also includes an asset vulnerability threat analysis and discusses incident response and disaster recovery policies to ensure business continuity. The report highlights the importance of information security governance and provides a comprehensive overview of the measures needed to protect MyHealth Company's sensitive data and ensure its operational resilience. The report addresses the contemporary and emerging risks from the cyber threats the company is facing.
Running Head: Information Assets 0
Information Assets
Report
Student name
Information Assets
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Information Assets 1
Table of Contents
Task 1: Identify and Manage Asset.................................................................................................2
Task 2: Vulnerability management and risk management............................................................10
References......................................................................................................................................16
Table of Contents
Task 1: Identify and Manage Asset.................................................................................................2
Task 2: Vulnerability management and risk management............................................................10
References......................................................................................................................................16
Information Assets 2
Task 1: Identify and Manage Asset
Q. 1(a), Q.1 (b), Q.1 (c)
MyHealth Company is a healthcare sector company that provides different services and
products to their patients, such as clinical services, healthcare products, and many others. It has a
cancer-related research department for researching new things in the field of oncology. It have
many information assets to manage different services and operations of the MyHealth Company,
such as computer systems, servers, routers, switches, wireless access points, and many others.
The MyHealth Company requires identification and manages their assets using different security
policies, which are based on the Australian cyber security standards (ACSC, Australian Cyber
Security Centre 2017).
There are many policies and mitigation strategies are used to mitigate the risks from the
organizations. MyHealth Company wants to know about their resources and secure them from
different cyber-attacks. They require security policies to mitigate risk from their organization.
ACSC provides different mitigation rules to mitigate risks (ACSC, Strategies to Mitigate Cyber
Security Incidents 2019).
Information systems are required high security from the cyber-attacks. In addition,
information assets are having a huge value. Therefore, it is highly required strong security
policies to make them secure (Andrijcic and Horowitz 2016).
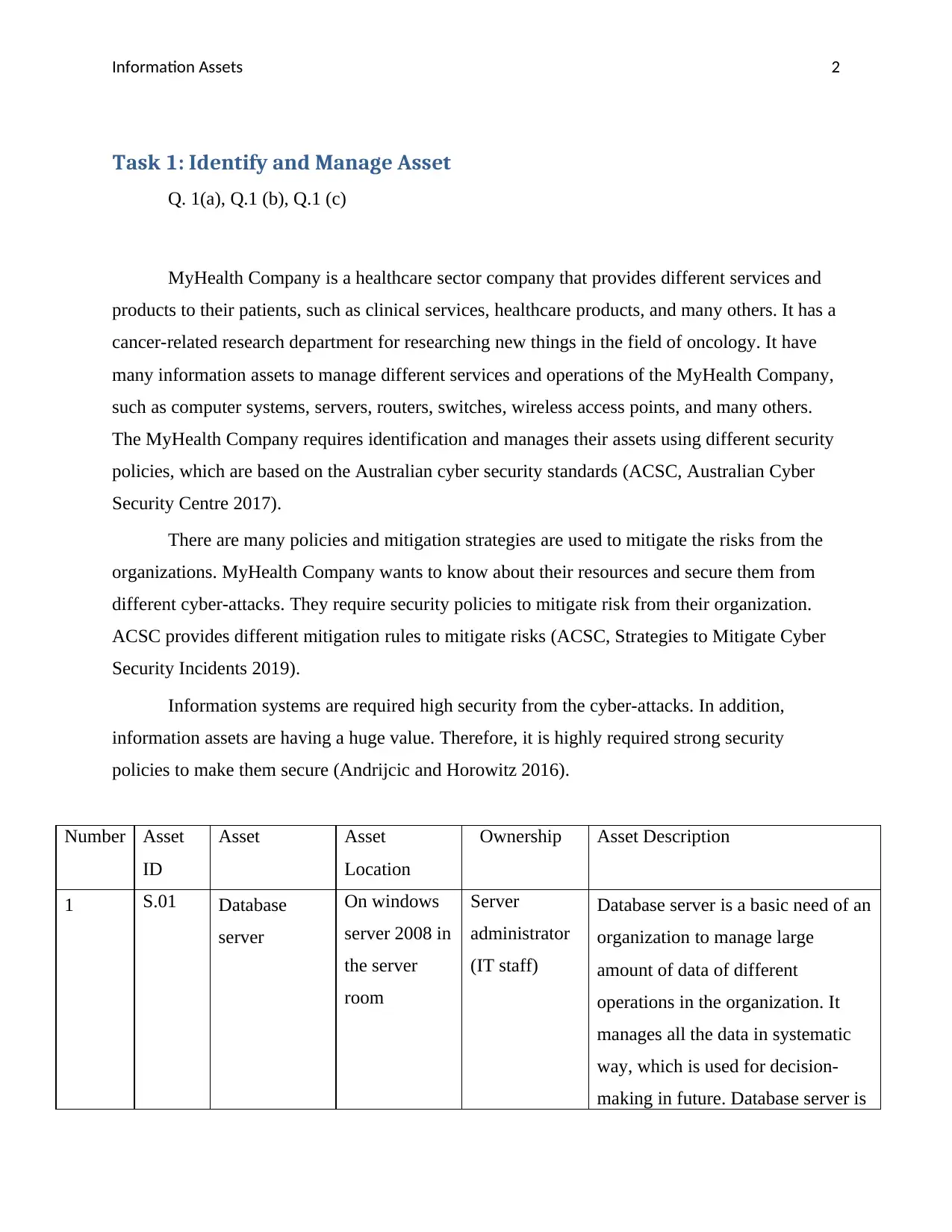
Number Asset
ID
Asset Asset
Location
Ownership Asset Description
1 S.01 Database
server
On windows
server 2008 in
the server
room
Server
administrator
(IT staff)
Database server is a basic need of an
organization to manage large
amount of data of different
operations in the organization. It
manages all the data in systematic
way, which is used for decision-
making in future. Database server is
Task 1: Identify and Manage Asset
Q. 1(a), Q.1 (b), Q.1 (c)
MyHealth Company is a healthcare sector company that provides different services and
products to their patients, such as clinical services, healthcare products, and many others. It has a
cancer-related research department for researching new things in the field of oncology. It have
many information assets to manage different services and operations of the MyHealth Company,
such as computer systems, servers, routers, switches, wireless access points, and many others.
The MyHealth Company requires identification and manages their assets using different security
policies, which are based on the Australian cyber security standards (ACSC, Australian Cyber
Security Centre 2017).
There are many policies and mitigation strategies are used to mitigate the risks from the
organizations. MyHealth Company wants to know about their resources and secure them from
different cyber-attacks. They require security policies to mitigate risk from their organization.
ACSC provides different mitigation rules to mitigate risks (ACSC, Strategies to Mitigate Cyber
Security Incidents 2019).
Information systems are required high security from the cyber-attacks. In addition,
information assets are having a huge value. Therefore, it is highly required strong security
policies to make them secure (Andrijcic and Horowitz 2016).
Number Asset
ID
Asset Asset
Location
Ownership Asset Description
1 S.01 Database
server
On windows
server 2008 in
the server
room
Server
administrator
(IT staff)
Database server is a basic need of an
organization to manage large
amount of data of different
operations in the organization. It
manages all the data in systematic
way, which is used for decision-
making in future. Database server is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Information Assets 3
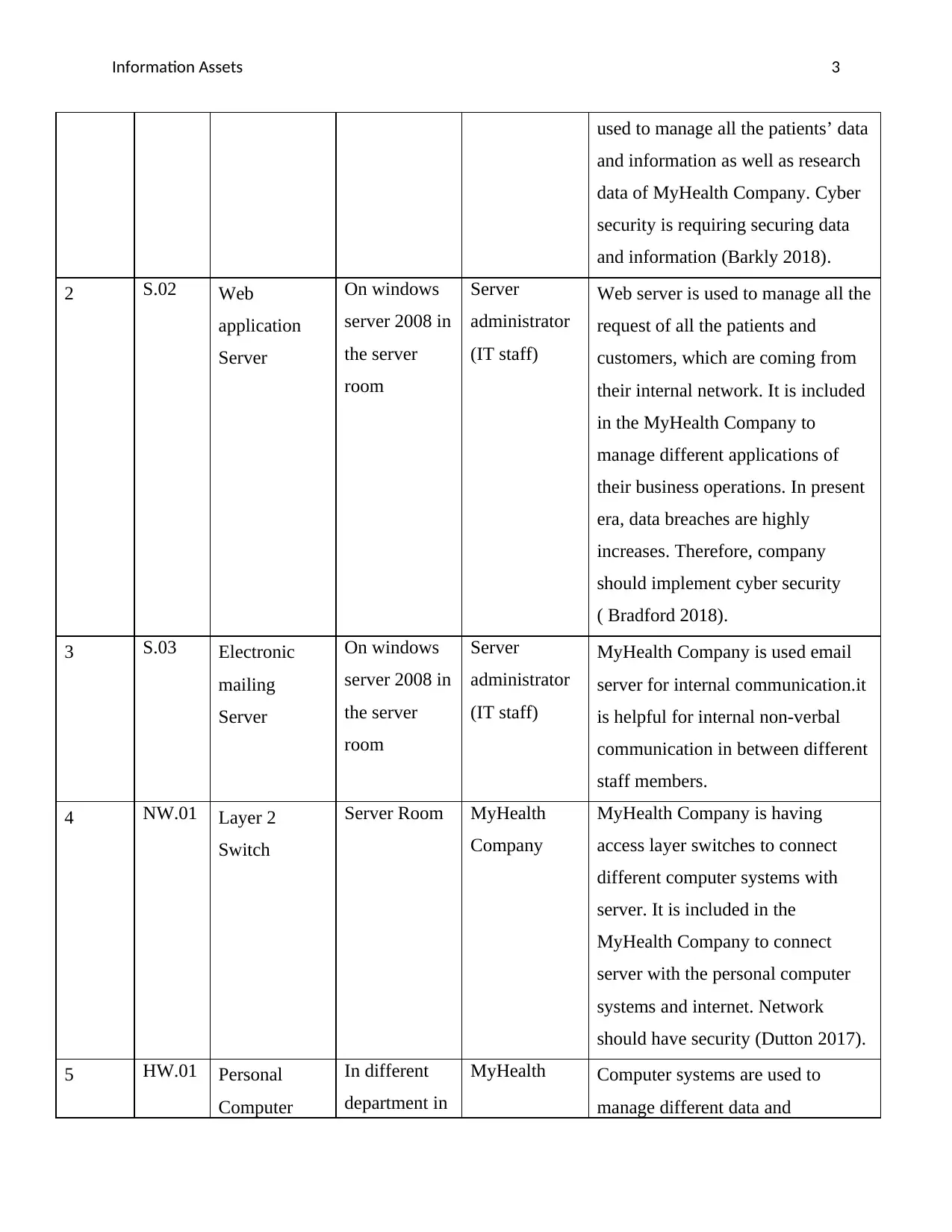
used to manage all the patients’ data
and information as well as research
data of MyHealth Company. Cyber
security is requiring securing data
and information (Barkly 2018).
2 S.02 Web
application
Server
On windows
server 2008 in
the server
room
Server
administrator
(IT staff)
Web server is used to manage all the
request of all the patients and
customers, which are coming from
their internal network. It is included
in the MyHealth Company to
manage different applications of
their business operations. In present
era, data breaches are highly
increases. Therefore, company
should implement cyber security
( Bradford 2018).
3 S.03 Electronic
mailing
Server
On windows
server 2008 in
the server
room
Server
administrator
(IT staff)
MyHealth Company is used email
server for internal communication.it
is helpful for internal non-verbal
communication in between different
staff members.
4 NW.01 Layer 2
Switch
Server Room MyHealth
Company
MyHealth Company is having
access layer switches to connect
different computer systems with
server. It is included in the
MyHealth Company to connect
server with the personal computer
systems and internet. Network
should have security (Dutton 2017).
5 HW.01 Personal
Computer
In different
department in
MyHealth Computer systems are used to
manage different data and
used to manage all the patients’ data
and information as well as research
data of MyHealth Company. Cyber
security is requiring securing data
and information (Barkly 2018).
2 S.02 Web
application
Server
On windows
server 2008 in
the server
room
Server
administrator
(IT staff)
Web server is used to manage all the
request of all the patients and
customers, which are coming from
their internal network. It is included
in the MyHealth Company to
manage different applications of
their business operations. In present
era, data breaches are highly
increases. Therefore, company
should implement cyber security
( Bradford 2018).
3 S.03 Electronic
mailing
Server
On windows
server 2008 in
the server
room
Server
administrator
(IT staff)
MyHealth Company is used email
server for internal communication.it
is helpful for internal non-verbal
communication in between different
staff members.
4 NW.01 Layer 2
Switch
Server Room MyHealth
Company
MyHealth Company is having
access layer switches to connect
different computer systems with
server. It is included in the
MyHealth Company to connect
server with the personal computer
systems and internet. Network
should have security (Dutton 2017).
5 HW.01 Personal
Computer
In different
department in
MyHealth Computer systems are used to
manage different data and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
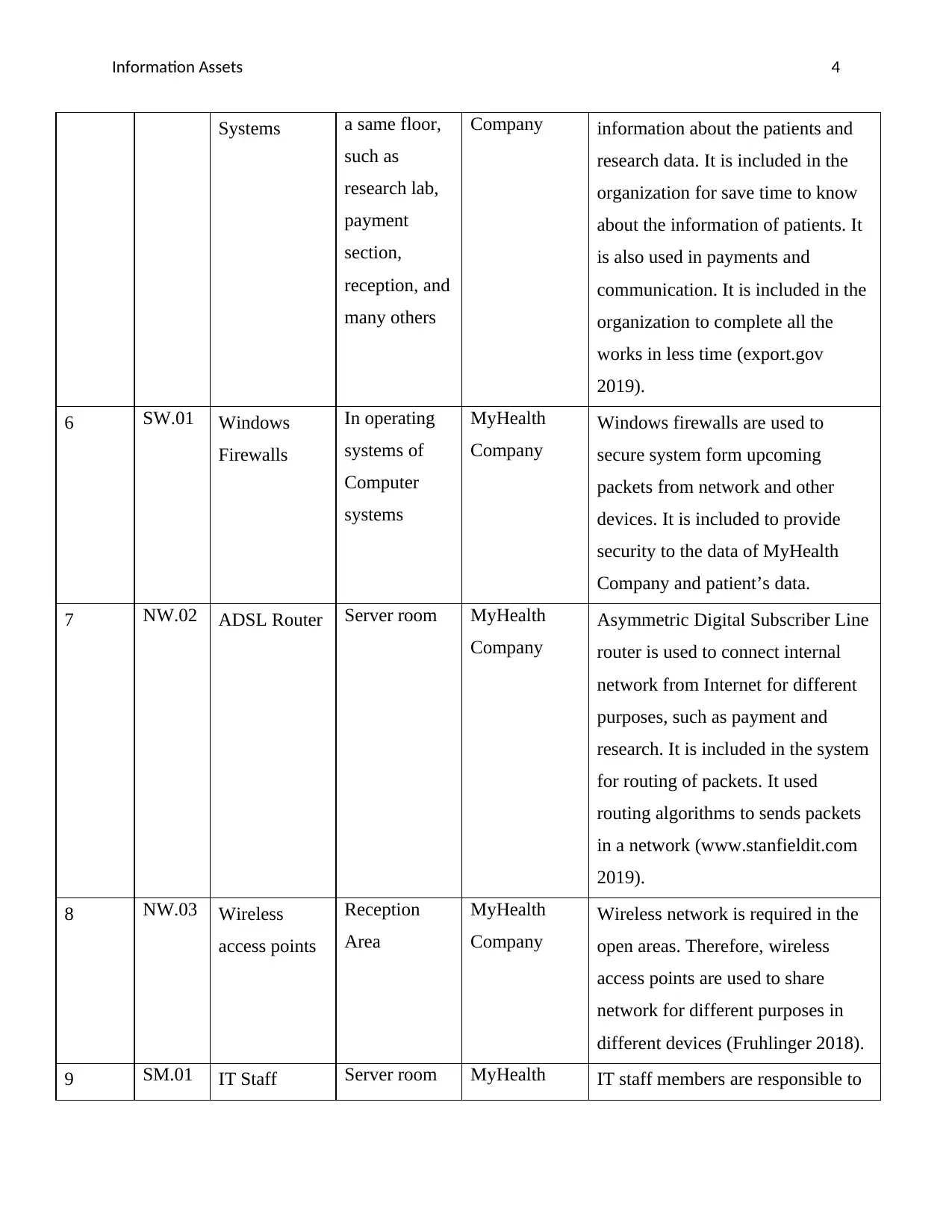
Information Assets 4
Systems a same floor,
such as
research lab,
payment
section,
reception, and
many others
Company information about the patients and
research data. It is included in the
organization for save time to know
about the information of patients. It
is also used in payments and
communication. It is included in the
organization to complete all the
works in less time (export.gov
2019).
6 SW.01 Windows
Firewalls
In operating
systems of
Computer
systems
MyHealth
Company
Windows firewalls are used to
secure system form upcoming
packets from network and other
devices. It is included to provide
security to the data of MyHealth
Company and patient’s data.
7 NW.02 ADSL Router Server room MyHealth
Company
Asymmetric Digital Subscriber Line
router is used to connect internal
network from Internet for different
purposes, such as payment and
research. It is included in the system
for routing of packets. It used
routing algorithms to sends packets
in a network (www.stanfieldit.com
2019).
8 NW.03 Wireless
access points
Reception
Area
MyHealth
Company
Wireless network is required in the
open areas. Therefore, wireless
access points are used to share
network for different purposes in
different devices (Fruhlinger 2018).
9 SM.01 IT Staff Server room MyHealth IT staff members are responsible to
Systems a same floor,
such as
research lab,
payment
section,
reception, and
many others
Company information about the patients and
research data. It is included in the
organization for save time to know
about the information of patients. It
is also used in payments and
communication. It is included in the
organization to complete all the
works in less time (export.gov
2019).
6 SW.01 Windows
Firewalls
In operating
systems of
Computer
systems
MyHealth
Company
Windows firewalls are used to
secure system form upcoming
packets from network and other
devices. It is included to provide
security to the data of MyHealth
Company and patient’s data.
7 NW.02 ADSL Router Server room MyHealth
Company
Asymmetric Digital Subscriber Line
router is used to connect internal
network from Internet for different
purposes, such as payment and
research. It is included in the system
for routing of packets. It used
routing algorithms to sends packets
in a network (www.stanfieldit.com
2019).
8 NW.03 Wireless
access points
Reception
Area
MyHealth
Company
Wireless network is required in the
open areas. Therefore, wireless
access points are used to share
network for different purposes in
different devices (Fruhlinger 2018).
9 SM.01 IT Staff Server room MyHealth IT staff members are responsible to
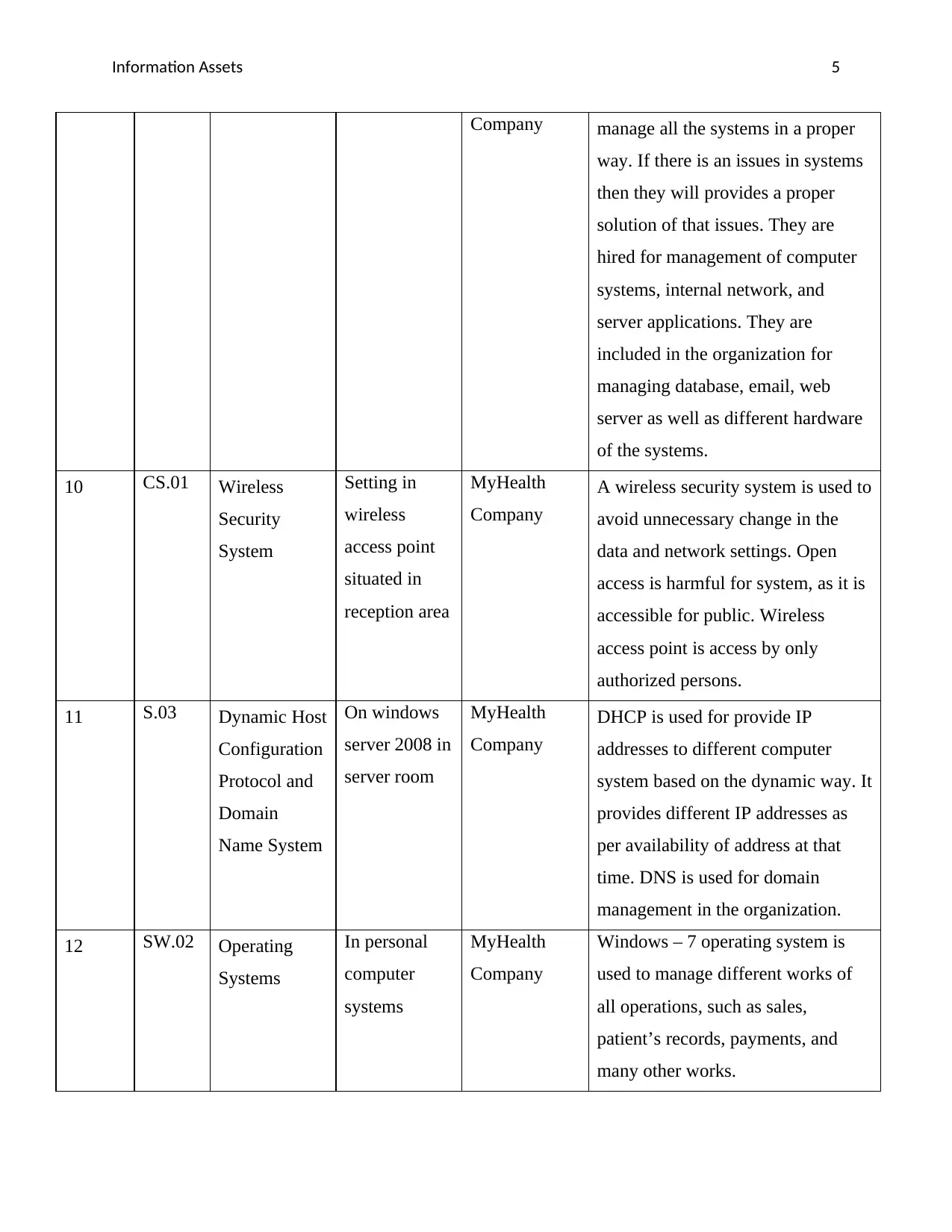
Information Assets 5
Company manage all the systems in a proper
way. If there is an issues in systems
then they will provides a proper
solution of that issues. They are
hired for management of computer
systems, internal network, and
server applications. They are
included in the organization for
managing database, email, web
server as well as different hardware
of the systems.
10 CS.01 Wireless
Security
System
Setting in
wireless
access point
situated in
reception area
MyHealth
Company
A wireless security system is used to
avoid unnecessary change in the
data and network settings. Open
access is harmful for system, as it is
accessible for public. Wireless
access point is access by only
authorized persons.
11 S.03 Dynamic Host
Configuration
Protocol and
Domain
Name System
On windows
server 2008 in
server room
MyHealth
Company
DHCP is used for provide IP
addresses to different computer
system based on the dynamic way. It
provides different IP addresses as
per availability of address at that
time. DNS is used for domain
management in the organization.
12 SW.02 Operating
Systems
In personal
computer
systems
MyHealth
Company
Windows – 7 operating system is
used to manage different works of
all operations, such as sales,
patient’s records, payments, and
many other works.
Company manage all the systems in a proper
way. If there is an issues in systems
then they will provides a proper
solution of that issues. They are
hired for management of computer
systems, internal network, and
server applications. They are
included in the organization for
managing database, email, web
server as well as different hardware
of the systems.
10 CS.01 Wireless
Security
System
Setting in
wireless
access point
situated in
reception area
MyHealth
Company
A wireless security system is used to
avoid unnecessary change in the
data and network settings. Open
access is harmful for system, as it is
accessible for public. Wireless
access point is access by only
authorized persons.
11 S.03 Dynamic Host
Configuration
Protocol and
Domain
Name System
On windows
server 2008 in
server room
MyHealth
Company
DHCP is used for provide IP
addresses to different computer
system based on the dynamic way. It
provides different IP addresses as
per availability of address at that
time. DNS is used for domain
management in the organization.
12 SW.02 Operating
Systems
In personal
computer
systems
MyHealth
Company
Windows – 7 operating system is
used to manage different works of
all operations, such as sales,
patient’s records, payments, and
many other works.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Information Assets 6
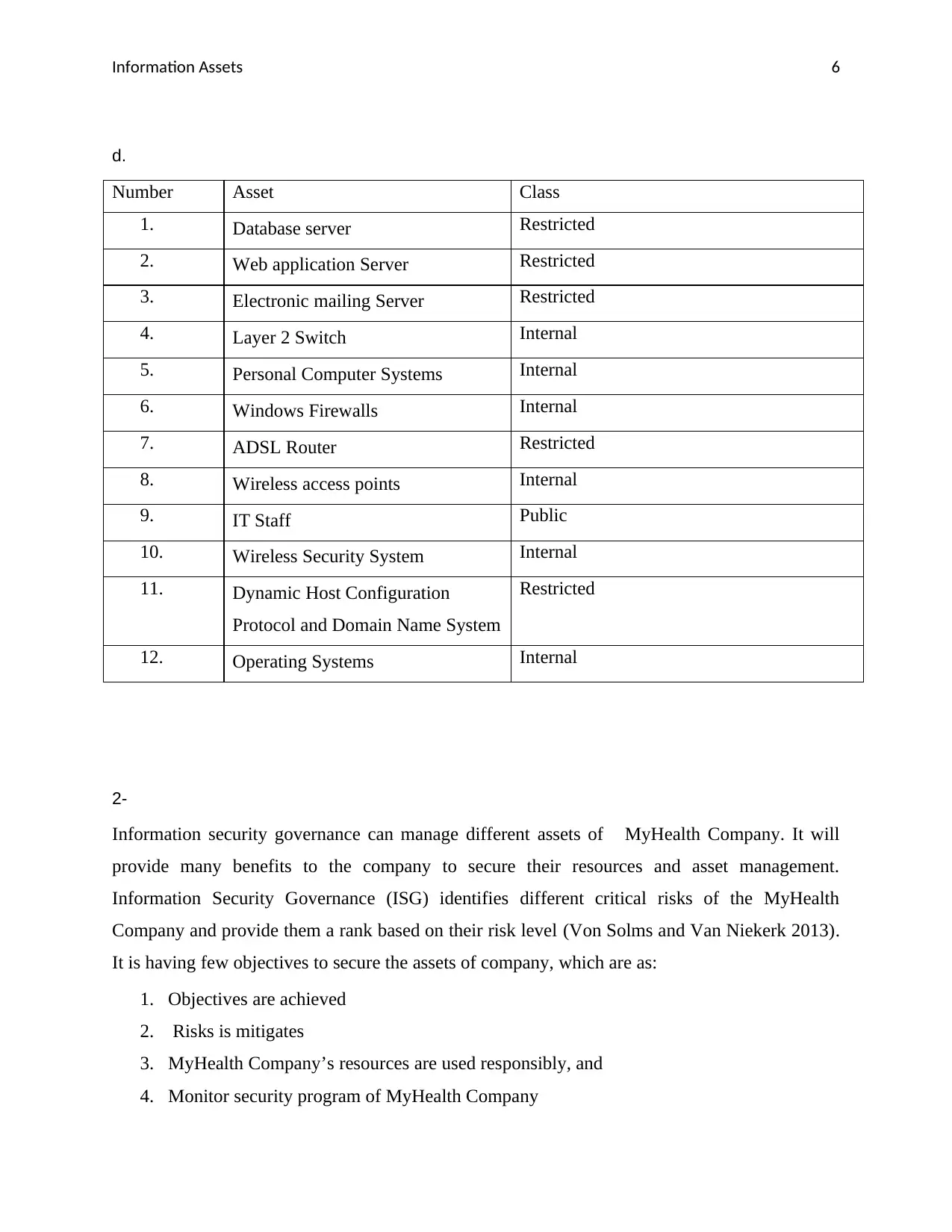
d.
Number Asset Class
1. Database server Restricted
2. Web application Server Restricted
3. Electronic mailing Server Restricted
4. Layer 2 Switch Internal
5. Personal Computer Systems Internal
6. Windows Firewalls Internal
7. ADSL Router Restricted
8. Wireless access points Internal
9. IT Staff Public
10. Wireless Security System Internal
11. Dynamic Host Configuration
Protocol and Domain Name System
Restricted
12. Operating Systems Internal
2-
Information security governance can manage different assets of MyHealth Company. It will
provide many benefits to the company to secure their resources and asset management.
Information Security Governance (ISG) identifies different critical risks of the MyHealth
Company and provide them a rank based on their risk level (Von Solms and Van Niekerk 2013).
It is having few objectives to secure the assets of company, which are as:
1. Objectives are achieved
2. Risks is mitigates
3. MyHealth Company’s resources are used responsibly, and
4. Monitor security program of MyHealth Company
d.
Number Asset Class
1. Database server Restricted
2. Web application Server Restricted
3. Electronic mailing Server Restricted
4. Layer 2 Switch Internal
5. Personal Computer Systems Internal
6. Windows Firewalls Internal
7. ADSL Router Restricted
8. Wireless access points Internal
9. IT Staff Public
10. Wireless Security System Internal
11. Dynamic Host Configuration
Protocol and Domain Name System
Restricted
12. Operating Systems Internal
2-
Information security governance can manage different assets of MyHealth Company. It will
provide many benefits to the company to secure their resources and asset management.
Information Security Governance (ISG) identifies different critical risks of the MyHealth
Company and provide them a rank based on their risk level (Von Solms and Van Niekerk 2013).
It is having few objectives to secure the assets of company, which are as:
1. Objectives are achieved
2. Risks is mitigates
3. MyHealth Company’s resources are used responsibly, and
4. Monitor security program of MyHealth Company
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Assets 7
It will provide many benefits, such as strategic alignment, risk management, resource
management, performance management, and value delivery.
Information Security Governance (ISG) is a best way to manage all the resource and information
assets of MyHealth Company. It will provide a high security to all the assets of company. It is a
way to manage all the assets of company, such as personal computer systems, server, routers,
switches, wireless access points, and many others (Gordon and Loeb 2006). ISG is having some
objectives, which is as:
1. Goals are achieved
2. All the risks mitigates through controls
3. Tangible resources are used in responsive way
4. Monitor all the activities of MyHealth company network
It will provide many benefits, such as, value delivery, risk management, performance
management, resource management, and strategic alignment.
3-
Acceptable Use Policy (AUP):
Handling of Username and password are responsibility of responsive person, such as
network admin, IT staff and other staff for their credentials
All staff members are responsible for their assets, which are allocated by the company.
Access Control Policy (ACP):
Only authorized persons have entry in restricted areas, such as sever room
Physical security is applied to all information assets
Wireless devices should be in surveillance
Database security:
Database server should have proper cyber security through firewalls
Database server access only by username and passwords
Proper authentication is used for accessing database server
Firewall configuration policy:
Firewall configuration should be proper to prevent system from cyber-attacks
All the risk controls are managed by the network administrator
Firewall should have IDS and IPS systems for security
It will provide many benefits, such as strategic alignment, risk management, resource
management, performance management, and value delivery.
Information Security Governance (ISG) is a best way to manage all the resource and information
assets of MyHealth Company. It will provide a high security to all the assets of company. It is a
way to manage all the assets of company, such as personal computer systems, server, routers,
switches, wireless access points, and many others (Gordon and Loeb 2006). ISG is having some
objectives, which is as:
1. Goals are achieved
2. All the risks mitigates through controls
3. Tangible resources are used in responsive way
4. Monitor all the activities of MyHealth company network
It will provide many benefits, such as, value delivery, risk management, performance
management, resource management, and strategic alignment.
3-
Acceptable Use Policy (AUP):
Handling of Username and password are responsibility of responsive person, such as
network admin, IT staff and other staff for their credentials
All staff members are responsible for their assets, which are allocated by the company.
Access Control Policy (ACP):
Only authorized persons have entry in restricted areas, such as sever room
Physical security is applied to all information assets
Wireless devices should be in surveillance
Database security:
Database server should have proper cyber security through firewalls
Database server access only by username and passwords
Proper authentication is used for accessing database server
Firewall configuration policy:
Firewall configuration should be proper to prevent system from cyber-attacks
All the risk controls are managed by the network administrator
Firewall should have IDS and IPS systems for security

Information Assets 8
Antivirus update policy:
Antivirus are always updated in all the working systems of the company
Respective person is responsible for update process
Respective person should have record for different changes in system based on the
hardware and software
Antivirus should have proper license
Information Security Policy (ISP):
Credential are responsibility of respective person
Roles and responsibilities are distributed in terms of documents of email into all the staff
members by the IT staff members at training time of staff.
Data and information of patients and company is an important asset. Therefore, everyone
should responsible for that data and could not share with anyone (Arlitsch and Edelman
2014).
Incident Response Policy (IRP):
All the staff members should inform about any incident related to the computer system,
data, and information of company.
CISOs are responsible to take proper response based on mitigation controls
Disaster Recovery Policy (DSP):
Disaster recovery plan should be implement to business continuity
Activate business continuity program after any disaster
Business Continuity Policy:
Business continuity process start after disaster and disaster recovery plan is activated
CISOs start security checks after disaster
All the connectivity of network should check by respective person
Password Policy:
Do not use personal information in password, such as date of birth, name, address, and
anything else.
Password should have at least eight characters
Password should have combination of different character, such as uppercase, number,
lowercase, and special characters (NCSC 2019).
Antivirus update policy:
Antivirus are always updated in all the working systems of the company
Respective person is responsible for update process
Respective person should have record for different changes in system based on the
hardware and software
Antivirus should have proper license
Information Security Policy (ISP):
Credential are responsibility of respective person
Roles and responsibilities are distributed in terms of documents of email into all the staff
members by the IT staff members at training time of staff.
Data and information of patients and company is an important asset. Therefore, everyone
should responsible for that data and could not share with anyone (Arlitsch and Edelman
2014).
Incident Response Policy (IRP):
All the staff members should inform about any incident related to the computer system,
data, and information of company.
CISOs are responsible to take proper response based on mitigation controls
Disaster Recovery Policy (DSP):
Disaster recovery plan should be implement to business continuity
Activate business continuity program after any disaster
Business Continuity Policy:
Business continuity process start after disaster and disaster recovery plan is activated
CISOs start security checks after disaster
All the connectivity of network should check by respective person
Password Policy:
Do not use personal information in password, such as date of birth, name, address, and
anything else.
Password should have at least eight characters
Password should have combination of different character, such as uppercase, number,
lowercase, and special characters (NCSC 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Information Assets 9
In every month password should change by the respective person with the help of
password tool or software
Password should have a meaning to remember.
In every month password should change by the respective person with the help of
password tool or software
Password should have a meaning to remember.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Information Assets 10
Task 2: Vulnerability management and risk management
1-
ISO framework is used to secure different assets of an organization. In case of MyHealth
Company, they have many information assets (iso27001security.com 2019). Therefore, they
should use a proper framework to secure them. Information assets require security from different
cyber-attacks (Hayslip 2018). ISO 27001 is perfect for the MyHealth Company and it is suitable
to secure information assets from cyber-attacks (Kosutic 2016). These are the steps to secure
enterprise:
1. Identify the goals of your Business
2. Obtain Management Support to secure assets
3. Define the Scope of risk
4. Write a brief ISMS Policy as a document
5. Define Risk Assessment Methodology and Strategy
6. Create an Inventory of Information Assets to Protect them
7. Rank all the Assets based on Risk Assessment
8. Create a Risk Treatment Plan and Manage those Risks
9. Set Up Policies and Procedures to Control Risks
10. Allocate Required Resources to all staff and provide training to secure resources
11. Prepare for an Internal Audit of the company’s tangible and non-tangible resources
12. Periodic Management Review ( Cobb 2010).
These steps are strictly followed by the company to secure assets of the company. ISO 27001 is a
framework, which provides full protection to the information assets (Verma 2019). MyHealth
Company requires a framework to manage their assets from cyber-attacks. Therefore, they
should choose ISO/IEC 27001 framework for enterprise risk management ( Licato 2014).
2-
Asset Vulnerability Threat Analysis
Database server Lack of access control Unauthorized Patients and company information
Task 2: Vulnerability management and risk management
1-
ISO framework is used to secure different assets of an organization. In case of MyHealth
Company, they have many information assets (iso27001security.com 2019). Therefore, they
should use a proper framework to secure them. Information assets require security from different
cyber-attacks (Hayslip 2018). ISO 27001 is perfect for the MyHealth Company and it is suitable
to secure information assets from cyber-attacks (Kosutic 2016). These are the steps to secure
enterprise:
1. Identify the goals of your Business
2. Obtain Management Support to secure assets
3. Define the Scope of risk
4. Write a brief ISMS Policy as a document
5. Define Risk Assessment Methodology and Strategy
6. Create an Inventory of Information Assets to Protect them
7. Rank all the Assets based on Risk Assessment
8. Create a Risk Treatment Plan and Manage those Risks
9. Set Up Policies and Procedures to Control Risks
10. Allocate Required Resources to all staff and provide training to secure resources
11. Prepare for an Internal Audit of the company’s tangible and non-tangible resources
12. Periodic Management Review ( Cobb 2010).
These steps are strictly followed by the company to secure assets of the company. ISO 27001 is a
framework, which provides full protection to the information assets (Verma 2019). MyHealth
Company requires a framework to manage their assets from cyber-attacks. Therefore, they
should choose ISO/IEC 27001 framework for enterprise risk management ( Licato 2014).
2-
Asset Vulnerability Threat Analysis
Database server Lack of access control Unauthorized Patients and company information
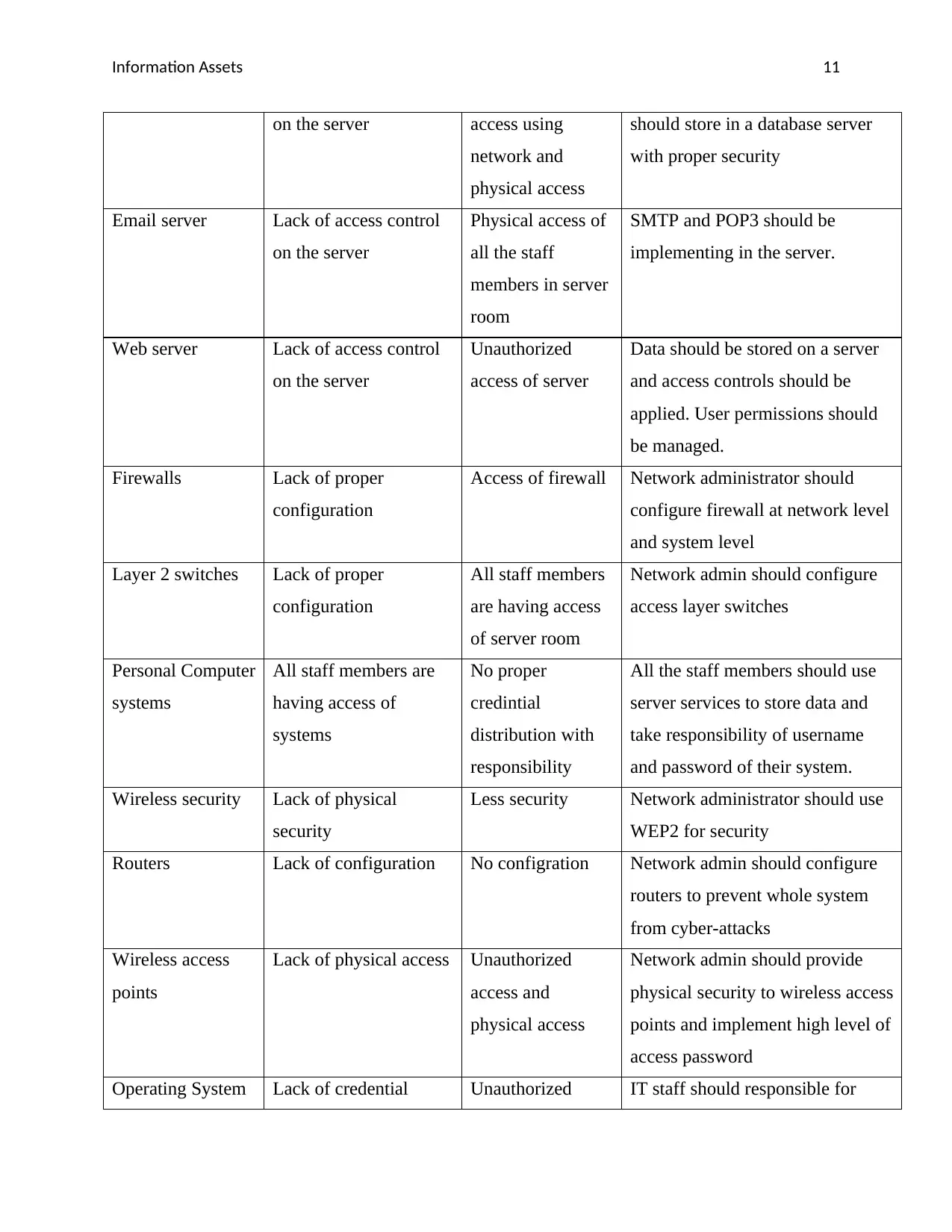
Information Assets 11
on the server access using
network and
physical access
should store in a database server
with proper security
Email server Lack of access control
on the server
Physical access of
all the staff
members in server
room
SMTP and POP3 should be
implementing in the server.
Web server Lack of access control
on the server
Unauthorized
access of server
Data should be stored on a server
and access controls should be
applied. User permissions should
be managed.
Firewalls Lack of proper
configuration
Access of firewall Network administrator should
configure firewall at network level
and system level
Layer 2 switches Lack of proper
configuration
All staff members
are having access
of server room
Network admin should configure
access layer switches
Personal Computer
systems
All staff members are
having access of
systems
No proper
credintial
distribution with
responsibility
All the staff members should use
server services to store data and
take responsibility of username
and password of their system.
Wireless security Lack of physical
security
Less security Network administrator should use
WEP2 for security
Routers Lack of configuration No configration Network admin should configure
routers to prevent whole system
from cyber-attacks
Wireless access
points
Lack of physical access Unauthorized
access and
physical access
Network admin should provide
physical security to wireless access
points and implement high level of
access password
Operating System Lack of credential Unauthorized IT staff should responsible for
on the server access using
network and
physical access
should store in a database server
with proper security
Email server Lack of access control
on the server
Physical access of
all the staff
members in server
room
SMTP and POP3 should be
implementing in the server.
Web server Lack of access control
on the server
Unauthorized
access of server
Data should be stored on a server
and access controls should be
applied. User permissions should
be managed.
Firewalls Lack of proper
configuration
Access of firewall Network administrator should
configure firewall at network level
and system level
Layer 2 switches Lack of proper
configuration
All staff members
are having access
of server room
Network admin should configure
access layer switches
Personal Computer
systems
All staff members are
having access of
systems
No proper
credintial
distribution with
responsibility
All the staff members should use
server services to store data and
take responsibility of username
and password of their system.
Wireless security Lack of physical
security
Less security Network administrator should use
WEP2 for security
Routers Lack of configuration No configration Network admin should configure
routers to prevent whole system
from cyber-attacks
Wireless access
points
Lack of physical access Unauthorized
access and
physical access
Network admin should provide
physical security to wireless access
points and implement high level of
access password
Operating System Lack of credential Unauthorized IT staff should responsible for
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





