GDPR Regulation and Data Protection Laws
VerifiedAdded on 2020/04/21
|23
|6058
|30
AI Summary
This assignment delves into the complexities of the General Data Protection Regulation (GDPR), analyzing its formulation process and impact on existing data protection laws. It examines key aspects like data breach notification, privacy rights, and the 'right to be forgotten'. The analysis incorporates legal perspectives, empirical studies, and real-world examples to illustrate the challenges and opportunities presented by GDPR in a rapidly evolving digital landscape.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

1
Information Management for Business Intelligence
Name
Course
Professor
School
City
Date
Information Management for Business Intelligence
Name
Course
Professor
School
City
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2
Abstract
In this report, it examines the ethical issues which surround the use of the personal data with a
focus on the relevant UK laws which relates to the data protection. Additionally, it has sought to
discuss on the issue of privacy and anonymity and how the organization are securing as well as
safeguarding the user’s personal data. The research has also looked at the new GDPR laws which
have been upgraded from the previous legislation DPA. They have added some additional
safeguards to the UK law. It will also examine on the how the companies will change their
structures to accommodate on these new laws and how they will manage the consents of its
users. Lastly, it will look at the implication of the data breach to the companies and individuals.
Prefaces
DPA Data Protection Act
GDPR General Data Protection Regulation
Abstract
In this report, it examines the ethical issues which surround the use of the personal data with a
focus on the relevant UK laws which relates to the data protection. Additionally, it has sought to
discuss on the issue of privacy and anonymity and how the organization are securing as well as
safeguarding the user’s personal data. The research has also looked at the new GDPR laws which
have been upgraded from the previous legislation DPA. They have added some additional
safeguards to the UK law. It will also examine on the how the companies will change their
structures to accommodate on these new laws and how they will manage the consents of its
users. Lastly, it will look at the implication of the data breach to the companies and individuals.
Prefaces
DPA Data Protection Act
GDPR General Data Protection Regulation

3
Table of Contents
Introduction.................................................................................................................................................4
Ethical issues on the use of personal data....................................................................................................4
UK laws that affect the use of personal data................................................................................................6
Discussion of privacy and anonymity..........................................................................................................8
How companies should secure and safeguard users’ personal data.............................................................9
GDPR context and background; discussion of extra safeguards GDPR adds to UK law...........................11
Structures and management systems commercial enterprises need to set up.............................................14
How companies should manage users’ consent.........................................................................................15
Implications of data breach........................................................................................................................17
Conclusion.................................................................................................................................................18
References.................................................................................................................................................19
Appendices................................................................................................................................................22
Appendix 1:.......................................................................................................................................22
Appendix 2:.......................................................................................................................................23
Table of Contents
Introduction.................................................................................................................................................4
Ethical issues on the use of personal data....................................................................................................4
UK laws that affect the use of personal data................................................................................................6
Discussion of privacy and anonymity..........................................................................................................8
How companies should secure and safeguard users’ personal data.............................................................9
GDPR context and background; discussion of extra safeguards GDPR adds to UK law...........................11
Structures and management systems commercial enterprises need to set up.............................................14
How companies should manage users’ consent.........................................................................................15
Implications of data breach........................................................................................................................17
Conclusion.................................................................................................................................................18
References.................................................................................................................................................19
Appendices................................................................................................................................................22
Appendix 1:.......................................................................................................................................22
Appendix 2:.......................................................................................................................................23

4
Introduction
Collecting, using as well as sharing of personal data entails taking into consideration of the legal
landscape as well as the ethical standards by the government (Romanosky, Hoffman and
Acquisti, 2014). Based on the ethical aspect it entails the standards of the right and wrong which
is prescribed what one ought to do, which is guided by the duties, rights, costs as well as the
benefits (Acquisti, Brandimarte and Loewenstein, 2015). In the UK it has been one of the most
active regions for the regulatory enforcement actions in regards to the issues over the data
protection. In handling of personal information in regards to individuals, there are a number of
the legal obligations so as to protect that personal data under the Data protection Act of 1998.
Based on this legislation it protect individuals under certain rights, as well as impose the
obligations on those who record as well as use the personal data to be open about how the data is
used (Acquisti, Brandimarte and Loewenstein, 2015). On the ethical aspect all the research on
data need to be conducted to the highest level of integrity so as to ensure that there it is robust
and defensible. In this research it will investigate into the issues which should be considered by
the organization as well as the government which collect the personal information (Barocas and
Nissenbaum, 2014). Additionally, it will look at the introduced General Data Protection
Regulation. On this regulation it will look at the safeguards that are introduced by GDPR, the
structures which company chosen will use, the roles and responsibilities that will be defined and
how the company need to manage the consent of the users and the implications to the
organization and the individuals in case there is a data breach which may occur.
Ethical issues on the use of personal data
The personal data is the new asset class which touches all the aspects of the society. It is very
valuable resource when it comes to the 21st Century (Caudill and Murphy, 2000). Nonetheless,
Introduction
Collecting, using as well as sharing of personal data entails taking into consideration of the legal
landscape as well as the ethical standards by the government (Romanosky, Hoffman and
Acquisti, 2014). Based on the ethical aspect it entails the standards of the right and wrong which
is prescribed what one ought to do, which is guided by the duties, rights, costs as well as the
benefits (Acquisti, Brandimarte and Loewenstein, 2015). In the UK it has been one of the most
active regions for the regulatory enforcement actions in regards to the issues over the data
protection. In handling of personal information in regards to individuals, there are a number of
the legal obligations so as to protect that personal data under the Data protection Act of 1998.
Based on this legislation it protect individuals under certain rights, as well as impose the
obligations on those who record as well as use the personal data to be open about how the data is
used (Acquisti, Brandimarte and Loewenstein, 2015). On the ethical aspect all the research on
data need to be conducted to the highest level of integrity so as to ensure that there it is robust
and defensible. In this research it will investigate into the issues which should be considered by
the organization as well as the government which collect the personal information (Barocas and
Nissenbaum, 2014). Additionally, it will look at the introduced General Data Protection
Regulation. On this regulation it will look at the safeguards that are introduced by GDPR, the
structures which company chosen will use, the roles and responsibilities that will be defined and
how the company need to manage the consent of the users and the implications to the
organization and the individuals in case there is a data breach which may occur.
Ethical issues on the use of personal data
The personal data is the new asset class which touches all the aspects of the society. It is very
valuable resource when it comes to the 21st Century (Caudill and Murphy, 2000). Nonetheless,
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5
the aspect of the personal data lacks the trading rules as well as policy framework which exist.
Many individuals care about their privacy and they do not often share their personal information
online (Barocas and Nissenbaum, 2014). Many fear that the data will not be protected when they
share or even think it will be shared. Some individuals rarely read the policies of the organization
which offer services. In UK the government is trying to leverage on all the personal data so as to
stimulate the aspect of innovation and drive the growth, while at the same time simultaneously
protecting persons (Pardo and Siemens, 2014). There is need for establishing internal policies so
as to ensure there is proper protection of the individual’s privacy.
There are various ethical issues which rises as a result of the personal data some are highlighted
as follows; one of the issue is in regards to the privacy. This refers to the personal right to be free
from any intrusion or perhaps the interference by others (Caudill and Murphy, 2000). It is a
fundamental rights especially in a free as well as democratic society for the personal information
for the people to be secure. People have the privacy interest in relation to their personal
information and the research could affect various domain in regards to the privacy in numerous
ways depending on the objectives and the methods. A significant aspect in regard to the privacy
is the right to control the information about an individual. The concept of consent is much related
to the right of privacy. It is respected if a person has the opportunity to exercise the control over
one personal information through consent to, or without holding the content for.
Another ethical issue which may arise in regards to personal data is that of confidentiality. The
ethical duty of the confidentiality regards to the obligation of the individuals in safeguarding on
the entrusted information (Martin, 2015). The question which could arise is would the UK
government safeguard on the personal data of their citizens? The ethical duty of confidentiality
entails obligation to protect the information from the unauthorized access, use, modification, loss
the aspect of the personal data lacks the trading rules as well as policy framework which exist.
Many individuals care about their privacy and they do not often share their personal information
online (Barocas and Nissenbaum, 2014). Many fear that the data will not be protected when they
share or even think it will be shared. Some individuals rarely read the policies of the organization
which offer services. In UK the government is trying to leverage on all the personal data so as to
stimulate the aspect of innovation and drive the growth, while at the same time simultaneously
protecting persons (Pardo and Siemens, 2014). There is need for establishing internal policies so
as to ensure there is proper protection of the individual’s privacy.
There are various ethical issues which rises as a result of the personal data some are highlighted
as follows; one of the issue is in regards to the privacy. This refers to the personal right to be free
from any intrusion or perhaps the interference by others (Caudill and Murphy, 2000). It is a
fundamental rights especially in a free as well as democratic society for the personal information
for the people to be secure. People have the privacy interest in relation to their personal
information and the research could affect various domain in regards to the privacy in numerous
ways depending on the objectives and the methods. A significant aspect in regard to the privacy
is the right to control the information about an individual. The concept of consent is much related
to the right of privacy. It is respected if a person has the opportunity to exercise the control over
one personal information through consent to, or without holding the content for.
Another ethical issue which may arise in regards to personal data is that of confidentiality. The
ethical duty of the confidentiality regards to the obligation of the individuals in safeguarding on
the entrusted information (Martin, 2015). The question which could arise is would the UK
government safeguard on the personal data of their citizens? The ethical duty of confidentiality
entails obligation to protect the information from the unauthorized access, use, modification, loss

6
or even theft. Another ethical issue is that of security (Martin, 2015). This relates to the measures
which is used to protect the information. It could include the physical, technical as well as the
administrative (Ogbanufe and Avery, 2016). The UK government should adopt as well as
enforce appropriate security measures as part of their confidentiality duties. Some of the physical
safeguards could entail the use storing of the personal data away from the public areas (Slade and
Prinsloo, 2013). The aspect of the administrative safeguards entails the development as well as
the enforcement of the rules in regards to who to access the personal data of individuals (Slade
and Prinsloo, 2013). The aspect on the technical safeguard entails the use of the passwords,
firewalls as well as encryption to their system and other measures which could protect the data
from the unauthorized access or even the loss and modification.
UK laws that affect the use of personal data
The laws which relate to the data protection of personal data are designed in order to regulate the
organization which are regarded as the data controllers those who collect and process
information relating to identifiable personal with the rights in relation to such data (Caudilland
Murphy, 2000). In the UK the position has been currently governed by the Data Protection Act
1998, which is designed to comply with the European Union Directive on the aspect of the Data
Protection so as to harmonize the various data protection laws that are within the numerous
Member States (Caudill and Murphy, 2000). The personal data are the information in regards to
living individuals who could be identified from the information as well as other which is in or
likely come into the data controller possession and could be minimal.
The Data Protection Act will be replaced by the EU General Data Protection Regulation
framework with much greater scope and tougher punishment for those who fail in complying
or even theft. Another ethical issue is that of security (Martin, 2015). This relates to the measures
which is used to protect the information. It could include the physical, technical as well as the
administrative (Ogbanufe and Avery, 2016). The UK government should adopt as well as
enforce appropriate security measures as part of their confidentiality duties. Some of the physical
safeguards could entail the use storing of the personal data away from the public areas (Slade and
Prinsloo, 2013). The aspect of the administrative safeguards entails the development as well as
the enforcement of the rules in regards to who to access the personal data of individuals (Slade
and Prinsloo, 2013). The aspect on the technical safeguard entails the use of the passwords,
firewalls as well as encryption to their system and other measures which could protect the data
from the unauthorized access or even the loss and modification.
UK laws that affect the use of personal data
The laws which relate to the data protection of personal data are designed in order to regulate the
organization which are regarded as the data controllers those who collect and process
information relating to identifiable personal with the rights in relation to such data (Caudilland
Murphy, 2000). In the UK the position has been currently governed by the Data Protection Act
1998, which is designed to comply with the European Union Directive on the aspect of the Data
Protection so as to harmonize the various data protection laws that are within the numerous
Member States (Caudill and Murphy, 2000). The personal data are the information in regards to
living individuals who could be identified from the information as well as other which is in or
likely come into the data controller possession and could be minimal.
The Data Protection Act will be replaced by the EU General Data Protection Regulation
framework with much greater scope and tougher punishment for those who fail in complying

7
with the new rules around the storage as well as handling personal data (Schwartz and Solove,
2014).
The data protection law has various implications to the businesses in the UK (Townend, 2017).
In these laws it will ensure data resilience and also provide some challenges for the business in
regards to getting their houses order (Floridi and Taddeo, 2016). Many of the organizations will
need to review their data privacy as well as protection policies in order to be compliant with the
new laws.
Data protection Act 1998: This law controls the collection as well as the storage of individual’s
personal data. The data controller will need to register with the ICO. Organization will only
collect the minimum data which is necessary for the tasks they are performing (Slade and
Prinsloo, 2013). Additionally, they will only need to store personal data for longer than the
necessary for the task they are undertaking.
Privacy and electronic communications regulations 2011: This law controls the ways in which
organizations as well as the public bodies use the electronic communications in order to market
their services to the consumers (Solomon, 2017). In this law an organization cannot send
unsolicited emails, tests or even the voicemail message unless they have the consent of the users
in doing so (Floridi and Taddeo, 2016). Moreover, they are not able to ask the users to send them
marketing message to friends or give them their friend contact details for the purpose of
marketing, unless one is confident they have received the consent from each of their friends.
Among the new conditions one of the biggest change to the SMEs they will face concerns
consent. Under the new regulations, the companies should keep a thorough record in regards to
how and when an individual gives consent to store and use their personal data. The aspect of
with the new rules around the storage as well as handling personal data (Schwartz and Solove,
2014).
The data protection law has various implications to the businesses in the UK (Townend, 2017).
In these laws it will ensure data resilience and also provide some challenges for the business in
regards to getting their houses order (Floridi and Taddeo, 2016). Many of the organizations will
need to review their data privacy as well as protection policies in order to be compliant with the
new laws.
Data protection Act 1998: This law controls the collection as well as the storage of individual’s
personal data. The data controller will need to register with the ICO. Organization will only
collect the minimum data which is necessary for the tasks they are performing (Slade and
Prinsloo, 2013). Additionally, they will only need to store personal data for longer than the
necessary for the task they are undertaking.
Privacy and electronic communications regulations 2011: This law controls the ways in which
organizations as well as the public bodies use the electronic communications in order to market
their services to the consumers (Solomon, 2017). In this law an organization cannot send
unsolicited emails, tests or even the voicemail message unless they have the consent of the users
in doing so (Floridi and Taddeo, 2016). Moreover, they are not able to ask the users to send them
marketing message to friends or give them their friend contact details for the purpose of
marketing, unless one is confident they have received the consent from each of their friends.
Among the new conditions one of the biggest change to the SMEs they will face concerns
consent. Under the new regulations, the companies should keep a thorough record in regards to
how and when an individual gives consent to store and use their personal data. The aspect of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
consent will mean there is an active agreement (Floridi and Taddeo, 2016). It can no longer be
inferred and organization which control how and why the data is processed would have to clearly
audit trail of the consent. Individuals have the rights to withdraw consent at any given time,
easily and swiftly. When they withdraw consent, the organization should permanently erase their
personal data and this new GDPR law gives the individuals the right to be forgotten.
Discussion of privacy and anonymity
Privacy is the ability of individual to seclude information about themselves. The boundaries and
content to which is regarded as private differ among individuals, but share a common themes.
Under the privacy law if a country such as UK is dealing with the personal data, they are outside
the scope of legislation (Caudill and Murphy, 2000). The aspect of privacy and anonymity gets
complicated in the age of the data. According to EU GDPR, the personal data is defined to
whether or not the person could be identified directly or even directly. In UK there is
introduction of the concept of pseudonymisation in order to address the privacy and anonymity
(Floridi and Taddeo, 2016). It talks about the process, which alters on the personal data in
regards to the individual personal data which can longer be attributed to the specific subject data,
without the use of the additional information.
The challenge of the data privacy is to utilize while protecting on the individuals preferences as
well as their personally identifiable information (Narayanan, Huey and Felten, 2016). the laws
and the regulations related to privacy of personal data are changing constantly especially in UK,
therefore, it is important to keep abreast of the various changes in the law and to continually
reassess the compliance with the data privacy as well as the security regulations.
Anonymity:
consent will mean there is an active agreement (Floridi and Taddeo, 2016). It can no longer be
inferred and organization which control how and why the data is processed would have to clearly
audit trail of the consent. Individuals have the rights to withdraw consent at any given time,
easily and swiftly. When they withdraw consent, the organization should permanently erase their
personal data and this new GDPR law gives the individuals the right to be forgotten.
Discussion of privacy and anonymity
Privacy is the ability of individual to seclude information about themselves. The boundaries and
content to which is regarded as private differ among individuals, but share a common themes.
Under the privacy law if a country such as UK is dealing with the personal data, they are outside
the scope of legislation (Caudill and Murphy, 2000). The aspect of privacy and anonymity gets
complicated in the age of the data. According to EU GDPR, the personal data is defined to
whether or not the person could be identified directly or even directly. In UK there is
introduction of the concept of pseudonymisation in order to address the privacy and anonymity
(Floridi and Taddeo, 2016). It talks about the process, which alters on the personal data in
regards to the individual personal data which can longer be attributed to the specific subject data,
without the use of the additional information.
The challenge of the data privacy is to utilize while protecting on the individuals preferences as
well as their personally identifiable information (Narayanan, Huey and Felten, 2016). the laws
and the regulations related to privacy of personal data are changing constantly especially in UK,
therefore, it is important to keep abreast of the various changes in the law and to continually
reassess the compliance with the data privacy as well as the security regulations.
Anonymity:

9
Anonymity regards to sanitization of the information intent in private protection. It can be the
process of encrypting or even removing personally identifiable information from the personal
data set so as individuals whose data describe could remain anonymous (Solove and Schwartz,
2014). According to the GDPR it highlights that the principles of the data protection does not
apply to the anonymous information, especially to the information which does not relate to the
identified or even the identifiable natural person or to personal data which is rendered
anonymous in a manner which the data subject is not or no longer identifiable. Therefore, this
regulation does not concern the process of such anonymous data (Floridi and Taddeo, 2016).
Nonetheless, despite this many have viewed anonymized data as unsafe since the most
sosphicated techniques could be reversed with the right data sets. The purpose of the anonymity
is to protect a person privacy, in order to ensure that the information is treated properly and the
identifiable data is processed by few individuals as possible.
Figure 1: The diagram shows the aspect of anonymity and Privacy.
How companies should secure and safeguard users’ personal data
The information which is trusted to the companies by the customers should be protected not only
for the purpose of the organization brand. When the companies use the personal data or
information which is provided or entrusted to them, this data needs to be used accordingly to the
Anonymity regards to sanitization of the information intent in private protection. It can be the
process of encrypting or even removing personally identifiable information from the personal
data set so as individuals whose data describe could remain anonymous (Solove and Schwartz,
2014). According to the GDPR it highlights that the principles of the data protection does not
apply to the anonymous information, especially to the information which does not relate to the
identified or even the identifiable natural person or to personal data which is rendered
anonymous in a manner which the data subject is not or no longer identifiable. Therefore, this
regulation does not concern the process of such anonymous data (Floridi and Taddeo, 2016).
Nonetheless, despite this many have viewed anonymized data as unsafe since the most
sosphicated techniques could be reversed with the right data sets. The purpose of the anonymity
is to protect a person privacy, in order to ensure that the information is treated properly and the
identifiable data is processed by few individuals as possible.
Figure 1: The diagram shows the aspect of anonymity and Privacy.
How companies should secure and safeguard users’ personal data
The information which is trusted to the companies by the customers should be protected not only
for the purpose of the organization brand. When the companies use the personal data or
information which is provided or entrusted to them, this data needs to be used accordingly to the

10
purpose it was agreed (Pardo and Siemens, 2014). The federal Trade Commission’s enforces
various penalties against the organization which have negated so as to ensure the privacy of the
customer data. As a result of the escalation as well as the increase in threat in the public as well
as public sector, it is important for the companies to safeguard the personal data of the customer.
This could take place through having a data security policy in place (Murray, 2013). Making sure
that the company data is private and used properly could be near to impossible task which
involves various layer of security which could include technology that is able to scans for
vulnerabilities. Some of the secure and safeguard measures to ensure security of personal data
are as follows;
Ensuring data security accountability: The companies needs to ensure that their information
technology workers as well as the management are aware that their responsibilities and what is
expected them. The various type of data need to be classified so that the workers and the
management do understand the differences. Through the categorization of the data, the workers
are much aware of how to handle each kind of the data which is allowed to distribute. Important
classes include the policy entails confidential data, data which is meant to be sent internally
within the organization.
System data security policies: The security configuration to all the essential servers as well as
the operating system is important to the data security policy. There should be clear networks and
management of the accounts along with the passwords.
Account monitoring and the control: It is important for the organization to keep track of who
is accessing what is significant component of the data security policy. Some of common sources
of the digital compromises are much legitimate but they are inactive user accounts. There are
various categories which a security policy such as the data and network segmentation, identity
purpose it was agreed (Pardo and Siemens, 2014). The federal Trade Commission’s enforces
various penalties against the organization which have negated so as to ensure the privacy of the
customer data. As a result of the escalation as well as the increase in threat in the public as well
as public sector, it is important for the companies to safeguard the personal data of the customer.
This could take place through having a data security policy in place (Murray, 2013). Making sure
that the company data is private and used properly could be near to impossible task which
involves various layer of security which could include technology that is able to scans for
vulnerabilities. Some of the secure and safeguard measures to ensure security of personal data
are as follows;
Ensuring data security accountability: The companies needs to ensure that their information
technology workers as well as the management are aware that their responsibilities and what is
expected them. The various type of data need to be classified so that the workers and the
management do understand the differences. Through the categorization of the data, the workers
are much aware of how to handle each kind of the data which is allowed to distribute. Important
classes include the policy entails confidential data, data which is meant to be sent internally
within the organization.
System data security policies: The security configuration to all the essential servers as well as
the operating system is important to the data security policy. There should be clear networks and
management of the accounts along with the passwords.
Account monitoring and the control: It is important for the organization to keep track of who
is accessing what is significant component of the data security policy. Some of common sources
of the digital compromises are much legitimate but they are inactive user accounts. There are
various categories which a security policy such as the data and network segmentation, identity
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

11
and access management. There is need to address the organization entire security posture,
monitoring on the activity across each asset within an organization.
Encrypt the data: It is important to keep the organization system secure especially on their
browser. To guard on the customer data such as the online transaction, it is important to encrypt
information which scrambles the information which send one over the internet. The information
need to be secure the clients data always when it is transmitted. Additionally, the organization
should keep the password private. The use of passwords strong password would enable an
organization to safeguard on the customer personal data more secure and ensure that the
attackers do not have an access to this kind of data.
Figure 2: The diagram shows how organization secure personal data
GDPR context and background; discussion of extra safeguards GDPR adds to UK law
The GDPR is the new EU privacy law, which has been aimed in bringing order to the patchwork
of the privacy rules across the European Union (Walker-Osborn and Barry, 2016). This law is a
regulation rather than a directive, and it has been binding the legal force and would be
immediately enforceable as the law in the EU member states. This new law will grant individual
and access management. There is need to address the organization entire security posture,
monitoring on the activity across each asset within an organization.
Encrypt the data: It is important to keep the organization system secure especially on their
browser. To guard on the customer data such as the online transaction, it is important to encrypt
information which scrambles the information which send one over the internet. The information
need to be secure the clients data always when it is transmitted. Additionally, the organization
should keep the password private. The use of passwords strong password would enable an
organization to safeguard on the customer personal data more secure and ensure that the
attackers do not have an access to this kind of data.
Figure 2: The diagram shows how organization secure personal data
GDPR context and background; discussion of extra safeguards GDPR adds to UK law
The GDPR is the new EU privacy law, which has been aimed in bringing order to the patchwork
of the privacy rules across the European Union (Walker-Osborn and Barry, 2016). This law is a
regulation rather than a directive, and it has been binding the legal force and would be
immediately enforceable as the law in the EU member states. This new law will grant individual

12
more control over how others utilize their personal data (Libert, 2015). The law has been
designed to sign the European privacy rules into the British law along with update of the existing
Data Protection Act that had not changed since 1998. This law also include reform of the right to
be forgotten which allow people to ask organization including the social media for their data
from being erased.
Figure 3: The diagram shows a graph to highlight if organization in UK are ready for GDPR
The key changes to the existing to the UK law are;
Much tougher reporting as well as notification obligations. Under the existing legislation in the
UK, there has been no legal obligation in reporting data breaches to the information
Commissioners (Murray, 2013). This bill entailed a mandatory reporting requirement (Fuster,
2014). The data controllers would have to notify the information Commissioner, which would
not be later than seventy two hours after becoming aware of breach, unless they are able to
highlights that the breach is not possible to result to any risk for right as well as the freedom of
data (Weingärtner and Westphall, 2014).
more control over how others utilize their personal data (Libert, 2015). The law has been
designed to sign the European privacy rules into the British law along with update of the existing
Data Protection Act that had not changed since 1998. This law also include reform of the right to
be forgotten which allow people to ask organization including the social media for their data
from being erased.
Figure 3: The diagram shows a graph to highlight if organization in UK are ready for GDPR
The key changes to the existing to the UK law are;
Much tougher reporting as well as notification obligations. Under the existing legislation in the
UK, there has been no legal obligation in reporting data breaches to the information
Commissioners (Murray, 2013). This bill entailed a mandatory reporting requirement (Fuster,
2014). The data controllers would have to notify the information Commissioner, which would
not be later than seventy two hours after becoming aware of breach, unless they are able to
highlights that the breach is not possible to result to any risk for right as well as the freedom of
data (Weingärtner and Westphall, 2014).

13
Another change is on the right to be forgotten (Lynskey, 2017). When individuals do not want
their data to be processed and there are no legitimate grounds for retaining it, the data needs to be
deleted. The consumers would be able to ask the businesses such as the retail bank to access their
personal data and it should be deleted (Fuster, 2014). This give they more control over how their
data is removed.
There is easier access to one data with the changes to the new legislation law (Strandburg, 2014).
The individual will have more information on how their data is processed and how the
information should be available in a manner that is clear and understandable.
Other extra safeguard which will be introduced in this law is that there will be mandatory
appointment of the data protection officer. There is a requirement for the mandatory appointment
of the Data Protection officer for the public authorities (Martin, 2015). The organization which
process the large scale data such as the retail bank will need to appoint the data protection
officer. Additionally, there will also be a wider definition of the personal data. There will be
more expansion of the personal data aspect so as to reflect the new types of the data which were
not covered in the regulations in 1998 (Martin, 2015). These included the IP addresses, the
internet cookies as well as the DNA. This follows the concerns which the internet browsing
records which has increasingly been utilized for the purpose of the marketing.
Another change is on the right to be forgotten (Lynskey, 2017). When individuals do not want
their data to be processed and there are no legitimate grounds for retaining it, the data needs to be
deleted. The consumers would be able to ask the businesses such as the retail bank to access their
personal data and it should be deleted (Fuster, 2014). This give they more control over how their
data is removed.
There is easier access to one data with the changes to the new legislation law (Strandburg, 2014).
The individual will have more information on how their data is processed and how the
information should be available in a manner that is clear and understandable.
Other extra safeguard which will be introduced in this law is that there will be mandatory
appointment of the data protection officer. There is a requirement for the mandatory appointment
of the Data Protection officer for the public authorities (Martin, 2015). The organization which
process the large scale data such as the retail bank will need to appoint the data protection
officer. Additionally, there will also be a wider definition of the personal data. There will be
more expansion of the personal data aspect so as to reflect the new types of the data which were
not covered in the regulations in 1998 (Martin, 2015). These included the IP addresses, the
internet cookies as well as the DNA. This follows the concerns which the internet browsing
records which has increasingly been utilized for the purpose of the marketing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
14
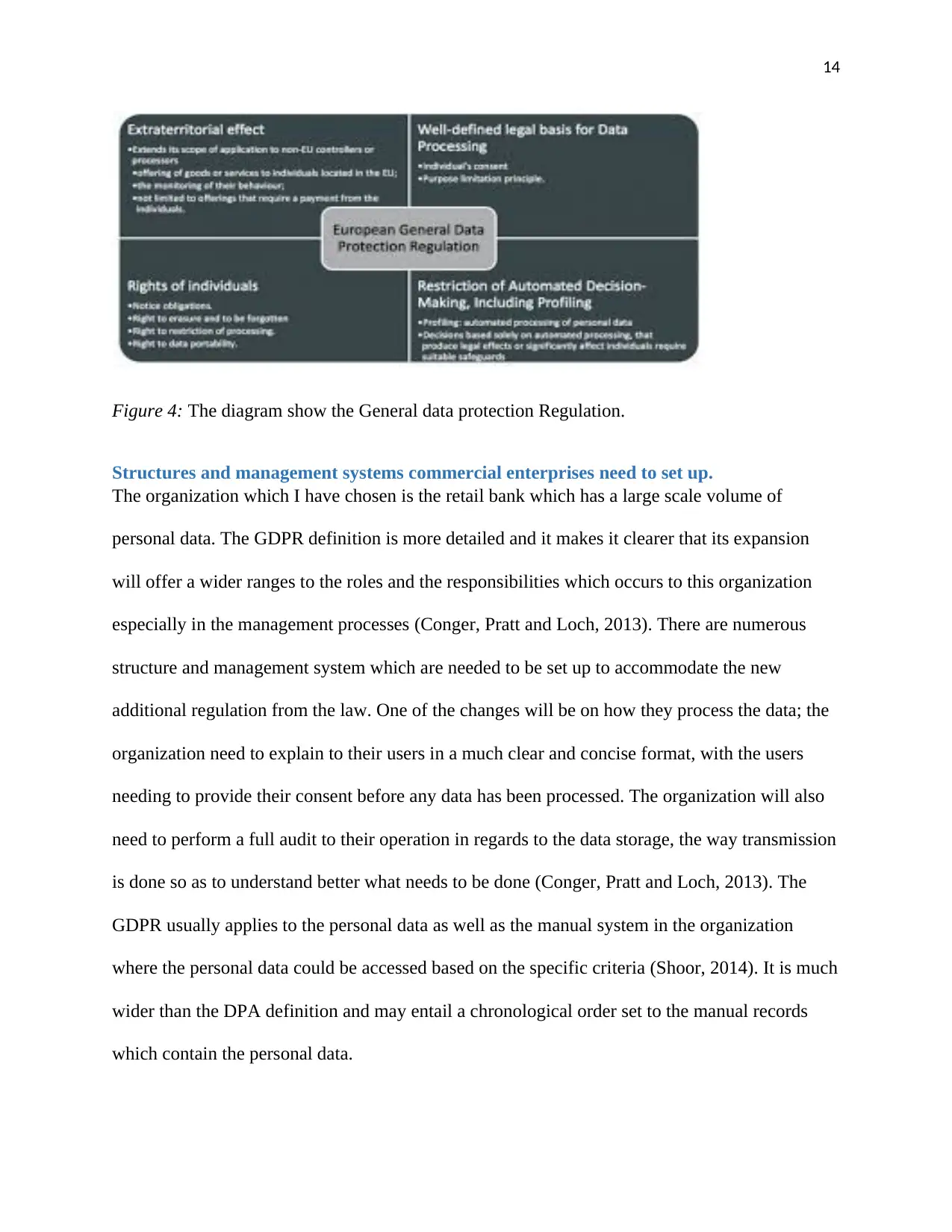
Figure 4: The diagram show the General data protection Regulation.
Structures and management systems commercial enterprises need to set up.
The organization which I have chosen is the retail bank which has a large scale volume of
personal data. The GDPR definition is more detailed and it makes it clearer that its expansion
will offer a wider ranges to the roles and the responsibilities which occurs to this organization
especially in the management processes (Conger, Pratt and Loch, 2013). There are numerous
structure and management system which are needed to be set up to accommodate the new
additional regulation from the law. One of the changes will be on how they process the data; the
organization need to explain to their users in a much clear and concise format, with the users
needing to provide their consent before any data has been processed. The organization will also
need to perform a full audit to their operation in regards to the data storage, the way transmission
is done so as to understand better what needs to be done (Conger, Pratt and Loch, 2013). The
GDPR usually applies to the personal data as well as the manual system in the organization
where the personal data could be accessed based on the specific criteria (Shoor, 2014). It is much
wider than the DPA definition and may entail a chronological order set to the manual records
which contain the personal data.
Figure 4: The diagram show the General data protection Regulation.
Structures and management systems commercial enterprises need to set up.
The organization which I have chosen is the retail bank which has a large scale volume of
personal data. The GDPR definition is more detailed and it makes it clearer that its expansion
will offer a wider ranges to the roles and the responsibilities which occurs to this organization
especially in the management processes (Conger, Pratt and Loch, 2013). There are numerous
structure and management system which are needed to be set up to accommodate the new
additional regulation from the law. One of the changes will be on how they process the data; the
organization need to explain to their users in a much clear and concise format, with the users
needing to provide their consent before any data has been processed. The organization will also
need to perform a full audit to their operation in regards to the data storage, the way transmission
is done so as to understand better what needs to be done (Conger, Pratt and Loch, 2013). The
GDPR usually applies to the personal data as well as the manual system in the organization
where the personal data could be accessed based on the specific criteria (Shoor, 2014). It is much
wider than the DPA definition and may entail a chronological order set to the manual records
which contain the personal data.

15
The organization will also need to accommodate the data protection officer who is mandatory
who will monitor on the way the personal data is being handled (Liu, 2014). Additionally, this
individual will ensure that the organization does comply with the regulation.
This will entail establishment of a department in the organization which will be concerned with
the personal data monitoring so that the officer will be able to monitor on the uses of the data.
The retail bank will also need to automate on all their processing (Edwards, Hofmeyr and
Forrest, 2016). when persons are profiled through the algorithm based on their personal data,
such kind of the evaluation of their health, individuals could demand on this action to be
undertaken, rather than a machine; therefore, they need to be prepared on such shortcomings.
How companies should manage users’ consent
The core requirement to coming up with this new UK law GDPR is that processing on the
personal data the organization need to seek consent from the users to do so and let them revoke
that consent any time in an easy manner like they were given (Porter and Heppelmann, 2014).
Keeping of an audit able trail of the consent, scope of the user as well as the revocation during
the client’s identity life cycle.
The organization especially in the retail bank usually utilize SAS approach so as to link the
consent information with the data usage policies as well as the personal data in order to offer a
complete picture to the personal data and its usage in the organization (Chander and Lê, 2014).
Bringing these 3 aspects together makes it easy for the reporting compliance, and allow at the
same time the organization to base their marketing campaign along with the other channels
activities on a given consent which is given by every person (Jay, Pearson and Farmer, 2016).
With the use of the SAS for the personal Data protection, the organization can immediately begin
to manage and store their usage of the data policies more transparently and at the same time
The organization will also need to accommodate the data protection officer who is mandatory
who will monitor on the way the personal data is being handled (Liu, 2014). Additionally, this
individual will ensure that the organization does comply with the regulation.
This will entail establishment of a department in the organization which will be concerned with
the personal data monitoring so that the officer will be able to monitor on the uses of the data.
The retail bank will also need to automate on all their processing (Edwards, Hofmeyr and
Forrest, 2016). when persons are profiled through the algorithm based on their personal data,
such kind of the evaluation of their health, individuals could demand on this action to be
undertaken, rather than a machine; therefore, they need to be prepared on such shortcomings.
How companies should manage users’ consent
The core requirement to coming up with this new UK law GDPR is that processing on the
personal data the organization need to seek consent from the users to do so and let them revoke
that consent any time in an easy manner like they were given (Porter and Heppelmann, 2014).
Keeping of an audit able trail of the consent, scope of the user as well as the revocation during
the client’s identity life cycle.
The organization especially in the retail bank usually utilize SAS approach so as to link the
consent information with the data usage policies as well as the personal data in order to offer a
complete picture to the personal data and its usage in the organization (Chander and Lê, 2014).
Bringing these 3 aspects together makes it easy for the reporting compliance, and allow at the
same time the organization to base their marketing campaign along with the other channels
activities on a given consent which is given by every person (Jay, Pearson and Farmer, 2016).
With the use of the SAS for the personal Data protection, the organization can immediately begin
to manage and store their usage of the data policies more transparently and at the same time

16
collaborate in the web based programs (Liu, 2014). This is one of the step towards the GDPR
compliance which is the starting point for the governance of the personal data. Moreover, rather
than serving as the library towards the personal data usage policies, the solution thus support
continuous maintenance of the policies which could incorporate the general policies of the data
as the central instance for the workflow incident management for the personal information.
To manage the personal data, the usage of the data policies could be linked to the information in
regards to the data sources (Conger, Pratt and Loch, 2013). The organizing using SAS for the
personal data protection might find the personal data in many data sources. The solution utilizes
what is regarded as parsing, matching as well as identification capabilities that is able to identify
the sources which contain the sensitive personal data.
The companies are adapting their infrastructure so as to comply with the legislation and the
demands of the customers. Even though the personal data has been collected through various
ways (Chander and Lê, 2014). The cookie banners and the pop-ups on the website are one way
which the customers are able to control what it collected by the organization (Ford, 2016). Other
ways has been through customization; the company needs to customize the solution for the given
client. The consent API provides the opportunity so as to store the JavaScript for the tags so as to
load the platform rather than the website (Edwards, Hofmeyr and Forrest, 2016). When an
individual visit the web page for a company they consent-API is loaded initially in case
permission is provided, the tag is able to load.
The aspect of consent information should be brought into the picture. The SAS personal Data
Protection is able to combine the consent information as well as the personal data to a single data
model, and offer a data model template in order to store personal data records along with the
collaborate in the web based programs (Liu, 2014). This is one of the step towards the GDPR
compliance which is the starting point for the governance of the personal data. Moreover, rather
than serving as the library towards the personal data usage policies, the solution thus support
continuous maintenance of the policies which could incorporate the general policies of the data
as the central instance for the workflow incident management for the personal information.
To manage the personal data, the usage of the data policies could be linked to the information in
regards to the data sources (Conger, Pratt and Loch, 2013). The organizing using SAS for the
personal data protection might find the personal data in many data sources. The solution utilizes
what is regarded as parsing, matching as well as identification capabilities that is able to identify
the sources which contain the sensitive personal data.
The companies are adapting their infrastructure so as to comply with the legislation and the
demands of the customers. Even though the personal data has been collected through various
ways (Chander and Lê, 2014). The cookie banners and the pop-ups on the website are one way
which the customers are able to control what it collected by the organization (Ford, 2016). Other
ways has been through customization; the company needs to customize the solution for the given
client. The consent API provides the opportunity so as to store the JavaScript for the tags so as to
load the platform rather than the website (Edwards, Hofmeyr and Forrest, 2016). When an
individual visit the web page for a company they consent-API is loaded initially in case
permission is provided, the tag is able to load.
The aspect of consent information should be brought into the picture. The SAS personal Data
Protection is able to combine the consent information as well as the personal data to a single data
model, and offer a data model template in order to store personal data records along with the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

17
consent data which could comprise of the historic changes (Edwards, Hofmeyr and Forrest,
2016).
Implications of data breach.
When it comes to the organization which experience data breach it can have a bad reputation on
their brand. Some of the breaches are more devastating than other to an organization reputation
and it brand image (Morey, Forbath and Schoop, 2015). The data protection and the critical
aspects in protecting the reputation of the brand as well as maintaining on the loyalty of the
customers. An example of such organization which suffered from this the Sony Pictures. The
company suffered to more than one million dollars in the direct costs and damages. What
included in such category was the legal expenses. When such issue occurs there is also sinking
customer trust and goodwill, damage caused to the 3rd parties, as well as the rise in the insurance
premiums. The Sony data breach was particular was a result of stolen details of the customers.
This resulted to the violation of the customer trust, and the company lost trust from many of their
current customer, which resulted to the ripple effects in regards to the negative word of mouth
particularly in this age of the social media.
The retail service organization such as the retail bank may suffer a more harsh negative effect
than other industries. They can lose, at least 9% of their market value within a span of thirty days
of the announcement of the breach. The market usually react so severely when it comes to the
issues of breaches for the retail industry since the retail clients might be fickle and not loyal to
the brands. Any kind of the publicized negative event could lead to the switching of their
business to the organization that they compete with them.
On the part of the individuals when the data has breached many feel devastated and they do not
trust the organization again that let their information to be stolen (Posner, 2014). Many
consent data which could comprise of the historic changes (Edwards, Hofmeyr and Forrest,
2016).
Implications of data breach.
When it comes to the organization which experience data breach it can have a bad reputation on
their brand. Some of the breaches are more devastating than other to an organization reputation
and it brand image (Morey, Forbath and Schoop, 2015). The data protection and the critical
aspects in protecting the reputation of the brand as well as maintaining on the loyalty of the
customers. An example of such organization which suffered from this the Sony Pictures. The
company suffered to more than one million dollars in the direct costs and damages. What
included in such category was the legal expenses. When such issue occurs there is also sinking
customer trust and goodwill, damage caused to the 3rd parties, as well as the rise in the insurance
premiums. The Sony data breach was particular was a result of stolen details of the customers.
This resulted to the violation of the customer trust, and the company lost trust from many of their
current customer, which resulted to the ripple effects in regards to the negative word of mouth
particularly in this age of the social media.
The retail service organization such as the retail bank may suffer a more harsh negative effect
than other industries. They can lose, at least 9% of their market value within a span of thirty days
of the announcement of the breach. The market usually react so severely when it comes to the
issues of breaches for the retail industry since the retail clients might be fickle and not loyal to
the brands. Any kind of the publicized negative event could lead to the switching of their
business to the organization that they compete with them.
On the part of the individuals when the data has breached many feel devastated and they do not
trust the organization again that let their information to be stolen (Posner, 2014). Many

18
individual tends to lose interest in a given brand in case such situation was to rise (Lloyd, 2017).
Additionally, when one personal data is stolen especially in a retail bank that offers one services
you can opt to sue them. There is loss in the revenue to that particular organization (Weber,
2015). There is a lot of damages which the clients is entitled to in the even that there data is
breached.
Conclusion
In this report, it has sought to examine on the significance of the security and the privacy of the
data which has been the core activity to many businesses today. It has looked at the current
issues especially on the ethical part when it comes to the data and the analytics. In this case the
focus has been on the current UK law in regards to the personal data protection. There has been
changes to the Data security protection which has incorporated more issues so as to provider the
consumers more scope in regards to their protection. Additionally, it has examined extensively
on the GDPR law and how the companies especially in the retail bank could change on their
structures and the management system to enable them to implement the new Laws which will
soon be in place by May 2018.
individual tends to lose interest in a given brand in case such situation was to rise (Lloyd, 2017).
Additionally, when one personal data is stolen especially in a retail bank that offers one services
you can opt to sue them. There is loss in the revenue to that particular organization (Weber,
2015). There is a lot of damages which the clients is entitled to in the even that there data is
breached.
Conclusion
In this report, it has sought to examine on the significance of the security and the privacy of the
data which has been the core activity to many businesses today. It has looked at the current
issues especially on the ethical part when it comes to the data and the analytics. In this case the
focus has been on the current UK law in regards to the personal data protection. There has been
changes to the Data security protection which has incorporated more issues so as to provider the
consumers more scope in regards to their protection. Additionally, it has examined extensively
on the GDPR law and how the companies especially in the retail bank could change on their
structures and the management system to enable them to implement the new Laws which will
soon be in place by May 2018.

19
References
Acquisti, A., Brandimarte, L. and Loewenstein, G., 2015. Privacy and human behavior in the age
of information. Science, 347(6221), pp.509-514.
Barocas, S. and Nissenbaum, H., 2014. Big data's end run around procedural privacy protections.
Communications of the ACM, 57(11), pp.31-33.
Caudill, E.M. and Murphy, P.E., 2000. Consumer online privacy: Legal and ethical issues.
Journal of Public Policy & Marketing, 19(1), pp.7-19.
Chander, A. and Lê, U.P., 2014. Data nationalism. Emory LJ, 64, p.677.
Conger, S., Pratt, J.H. and Loch, K.D., 2013. Personal information privacy and emerging
technologies. Information Systems Journal, 23(5), pp.401-417.
Edwards, B., Hofmeyr, S. and Forrest, S., 2016. Hype and heavy tails: A closer look at data
breaches. Journal of Cybersecurity, 2(1), pp.3-14.
Floridi, L. and Taddeo, M., 2016. What is data ethics?.
Ford, M., 2016. The Impact of Brexit on UK Labour Law. International Journal of Comparative
Labour Law and Industrial Relations, 32(4), pp.473-495.
Fuster, G.G., 2014. The emergence of personal data protection as a fundamental right of the EU
(Vol. 16). Springer Science & Business.
Jay, S., Pearson, C. and Farmer, N., 2016. Some Reflections on Brexit and the UK Data
Protection Regime. Intellectual Property & Technology Law Journal, 28(12), p.18.
Lloyd, I., 2017. Information technology law. Oxford University Press.
Libert, T., 2015. Privacy implications of health information seeking on the web.
Communications of the ACM, 58(3), pp.68-77.
Liu, Y., 2014. User control of personal information concerning mobile-app: Notice and consent?.
Computer Law & Security Review, 30(5), pp.521-529.
Lynskey, O., 2017. Aligning data protection rights with competition law remedies? The GDPR
right to data portability. European Law Journal.
Martin, K.E., 2015. Ethical issues in the big data industry. Browser Download This Paper.
Morey, T., Forbath, T. and Schoop, A., 2015. Customer data: Designing for transparency and
trust. Harvard Business Review, 93(5), pp.96-105.
References
Acquisti, A., Brandimarte, L. and Loewenstein, G., 2015. Privacy and human behavior in the age
of information. Science, 347(6221), pp.509-514.
Barocas, S. and Nissenbaum, H., 2014. Big data's end run around procedural privacy protections.
Communications of the ACM, 57(11), pp.31-33.
Caudill, E.M. and Murphy, P.E., 2000. Consumer online privacy: Legal and ethical issues.
Journal of Public Policy & Marketing, 19(1), pp.7-19.
Chander, A. and Lê, U.P., 2014. Data nationalism. Emory LJ, 64, p.677.
Conger, S., Pratt, J.H. and Loch, K.D., 2013. Personal information privacy and emerging
technologies. Information Systems Journal, 23(5), pp.401-417.
Edwards, B., Hofmeyr, S. and Forrest, S., 2016. Hype and heavy tails: A closer look at data
breaches. Journal of Cybersecurity, 2(1), pp.3-14.
Floridi, L. and Taddeo, M., 2016. What is data ethics?.
Ford, M., 2016. The Impact of Brexit on UK Labour Law. International Journal of Comparative
Labour Law and Industrial Relations, 32(4), pp.473-495.
Fuster, G.G., 2014. The emergence of personal data protection as a fundamental right of the EU
(Vol. 16). Springer Science & Business.
Jay, S., Pearson, C. and Farmer, N., 2016. Some Reflections on Brexit and the UK Data
Protection Regime. Intellectual Property & Technology Law Journal, 28(12), p.18.
Lloyd, I., 2017. Information technology law. Oxford University Press.
Libert, T., 2015. Privacy implications of health information seeking on the web.
Communications of the ACM, 58(3), pp.68-77.
Liu, Y., 2014. User control of personal information concerning mobile-app: Notice and consent?.
Computer Law & Security Review, 30(5), pp.521-529.
Lynskey, O., 2017. Aligning data protection rights with competition law remedies? The GDPR
right to data portability. European Law Journal.
Martin, K.E., 2015. Ethical issues in the big data industry. Browser Download This Paper.
Morey, T., Forbath, T. and Schoop, A., 2015. Customer data: Designing for transparency and
trust. Harvard Business Review, 93(5), pp.96-105.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

20
Murray, A., 2013. Information technology law: the law and society. Oxford University Press.
Narayanan, A., Huey, J. and Felten, E.W., 2016. A precautionary approach to big data privacy.
In Data protection on the move (pp. 357-385). Springer Netherlands.
Ogbanufe, O. and Avery, A., 2016. Breaching News: Does Media Coverage Increase the Effects
of Data Breach Event Disclosures on Firm Market Value?.
Pardo, A. and Siemens, G., 2014. Ethical and privacy principles for learning analytics. British
Journal of Educational Technology, 45(3), pp.438-450.
Posner, R.A., 2014. Economic analysis of law. Wolters Kluwer Law & Business.
Porter, M.E. and Heppelmann, J.E., 2014. How smart, connected products are transforming
competition. Harvard Business Review, 92(11), pp.64-88.
Romanosky, S., Hoffman, D. and Acquisti, A., 2014. Empirical analysis of data breach litigation.
Journal of Empirical Legal Studies, 11(1), pp.74-104.
Schwartz, P.M. and Solove, D.J., 2014. Reconciling personal information in the United States
and European Union. Cal. L. Rev., 102, p.877.
Sen, R. and Borle, S., 2015. Estimating the contextual risk of data breach: An empirical
approach. Journal of Management Information Systems, 32(2), pp.314-341.
Shoor, E.A., 2014. Narrowing the right to be forgotten: why the European Union needs to amend
the proposed data protection regulation. Brook. J. Int'l L., 39, p.487.
Slade, S. and Prinsloo, P., 2013. Learning analytics: Ethical issues and dilemmas. American
Behavioral Scientist, 57(10), pp.1510-1529.
Solomon, A., 2017. New mandatory data breach notification laws. Superfunds Magazine, (428),
p.16.
Solove, D.J. and Schwartz, P., 2014. Information privacy law. Wolters Kluwer Law & Business.
Strandburg, K.J., 2014. Monitoring, datafication and consent: legal approaches to privacy in the
big data context. Privacy, big data and the public good (eds Lane J, Stodden V, Bender S,
Nissenbaum H), pp.5-43.
Townend, J., 2017. Data protection and the ‘right to be forgotten’in practice: a UK perspective.
International Journal of Legal Information, 45(1), pp.28-33.
Walker-Osborn, C. and Barry, J., 2016. Brexit: Implications for the IT Industry. ITNOW, 58(4),
pp.36-37.
Murray, A., 2013. Information technology law: the law and society. Oxford University Press.
Narayanan, A., Huey, J. and Felten, E.W., 2016. A precautionary approach to big data privacy.
In Data protection on the move (pp. 357-385). Springer Netherlands.
Ogbanufe, O. and Avery, A., 2016. Breaching News: Does Media Coverage Increase the Effects
of Data Breach Event Disclosures on Firm Market Value?.
Pardo, A. and Siemens, G., 2014. Ethical and privacy principles for learning analytics. British
Journal of Educational Technology, 45(3), pp.438-450.
Posner, R.A., 2014. Economic analysis of law. Wolters Kluwer Law & Business.
Porter, M.E. and Heppelmann, J.E., 2014. How smart, connected products are transforming
competition. Harvard Business Review, 92(11), pp.64-88.
Romanosky, S., Hoffman, D. and Acquisti, A., 2014. Empirical analysis of data breach litigation.
Journal of Empirical Legal Studies, 11(1), pp.74-104.
Schwartz, P.M. and Solove, D.J., 2014. Reconciling personal information in the United States
and European Union. Cal. L. Rev., 102, p.877.
Sen, R. and Borle, S., 2015. Estimating the contextual risk of data breach: An empirical
approach. Journal of Management Information Systems, 32(2), pp.314-341.
Shoor, E.A., 2014. Narrowing the right to be forgotten: why the European Union needs to amend
the proposed data protection regulation. Brook. J. Int'l L., 39, p.487.
Slade, S. and Prinsloo, P., 2013. Learning analytics: Ethical issues and dilemmas. American
Behavioral Scientist, 57(10), pp.1510-1529.
Solomon, A., 2017. New mandatory data breach notification laws. Superfunds Magazine, (428),
p.16.
Solove, D.J. and Schwartz, P., 2014. Information privacy law. Wolters Kluwer Law & Business.
Strandburg, K.J., 2014. Monitoring, datafication and consent: legal approaches to privacy in the
big data context. Privacy, big data and the public good (eds Lane J, Stodden V, Bender S,
Nissenbaum H), pp.5-43.
Townend, J., 2017. Data protection and the ‘right to be forgotten’in practice: a UK perspective.
International Journal of Legal Information, 45(1), pp.28-33.
Walker-Osborn, C. and Barry, J., 2016. Brexit: Implications for the IT Industry. ITNOW, 58(4),
pp.36-37.

21
Weber, R.H., 2015. The digital future–A challenge for privacy?. Computer Law & Security
Review, 31(2), pp.234-242.
Weingärtner, R. and Westphall, C.M., 2014. Enhancing privacy on identity providers.
SECURWARE 2014, p.93.
Weber, R.H., 2015. The digital future–A challenge for privacy?. Computer Law & Security
Review, 31(2), pp.234-242.
Weingärtner, R. and Westphall, C.M., 2014. Enhancing privacy on identity providers.
SECURWARE 2014, p.93.

22
Appendices
Appendix 1:
Diagram1: Diagram show the steps need to formulate GDPR regulation.
Appendices
Appendix 1:
Diagram1: Diagram show the steps need to formulate GDPR regulation.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

23
Appendix 2:
Diagram 1: The diagram highlights the Data protection Act of 1998 on personal data.
Appendix 2:
Diagram 1: The diagram highlights the Data protection Act of 1998 on personal data.
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





