Information Security Report: Analysis of Te Mata Estate Security
VerifiedAdded on 2019/10/18
|14
|4507
|192
Report
AI Summary
This report provides a comprehensive analysis of information security challenges faced by Te Mata Estate, a New Zealand wine producer. It delves into various aspects of risk management, including risk avoidance, prevention, transfer, and retention, in the context of the company's automated supply chain. The report examines ethical issues related to information security, such as privacy, accuracy, property, and accessibility (PAPA). It also explores risk management controls and standards, particularly ISO 31000, and the importance of software testing standards like ISO/IEC/IEEE 29119. The report highlights instances of unethical hacking and phishing attacks experienced by Te Mata Estate, emphasizing the vulnerabilities of employees and the importance of robust security measures. It further discusses countermeasures against phishing attacks, approaches for securing network components, and recommendations for securing communication, including preventive maintenance and user-friendly e-commerce systems. Finally, the report addresses the components of information security operations, emphasizing the need for comprehensive security measures to protect the company's data and systems.

Information Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Task 1 :
Four components of information security risk management
Te Mata Estate is one of New Zealand’s oldest wine producers in the country. Most of the activities
of this system are automated in order to enhance the effective management of the supply chain. As
at the year 2008 and the year 2011, the company experienced some critical hitches in its information
system. In 2008, a hacking took place which not only denied access to the administrator of the
system but also the functionality of the whole system was highly downgraded. Management of risk
mainly involves risk priorities, assessment of risk, identification of threats and fix them using
various types of resources to minimize the heavy losses. Effective risk management in Te Mata
Estate makes value which plays an important role in their decision-making process against
upcoming threats.
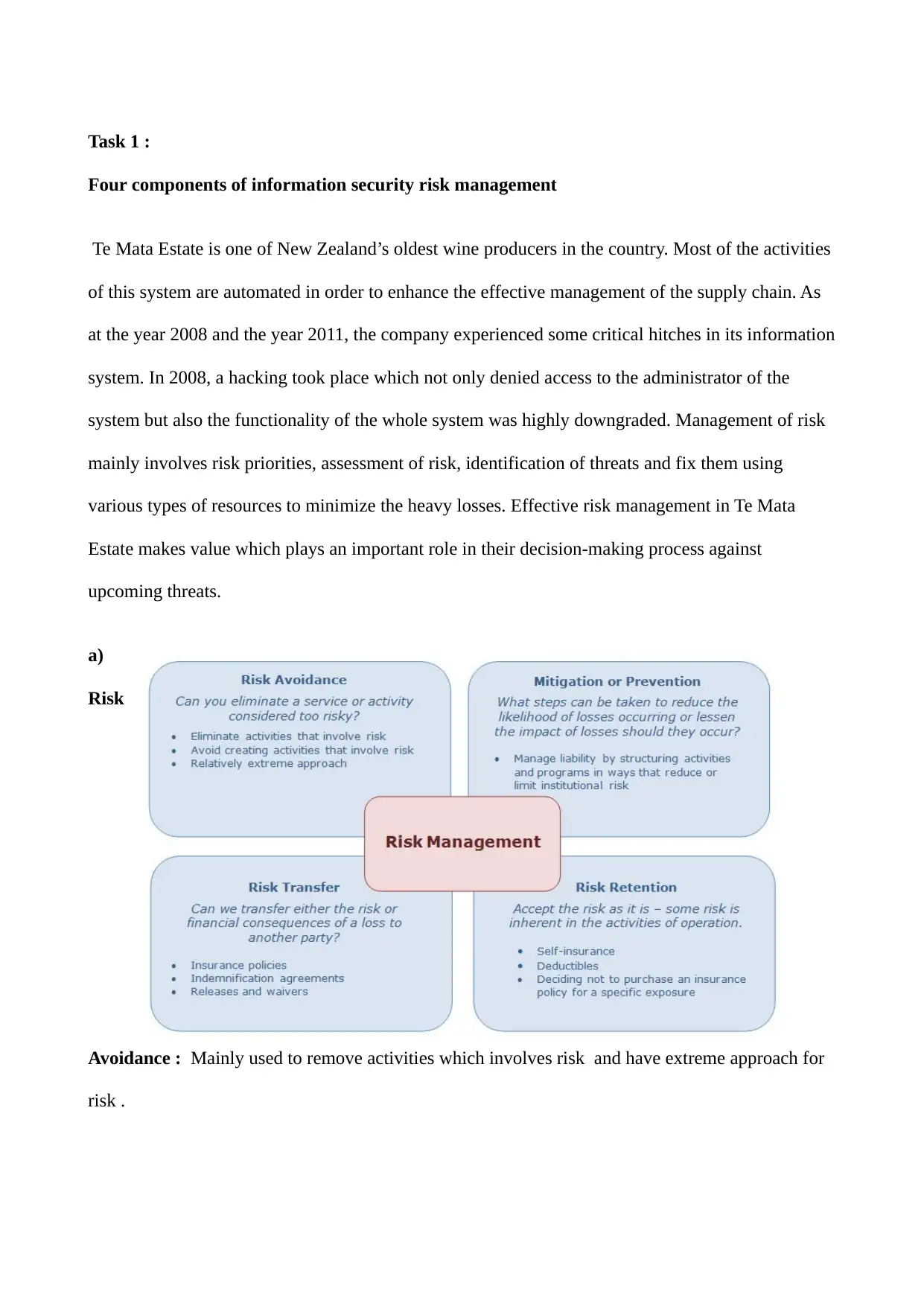
a)
Risk
Avoidance : Mainly used to remove activities which involves risk and have extreme approach for
risk .
Four components of information security risk management
Te Mata Estate is one of New Zealand’s oldest wine producers in the country. Most of the activities
of this system are automated in order to enhance the effective management of the supply chain. As
at the year 2008 and the year 2011, the company experienced some critical hitches in its information
system. In 2008, a hacking took place which not only denied access to the administrator of the
system but also the functionality of the whole system was highly downgraded. Management of risk
mainly involves risk priorities, assessment of risk, identification of threats and fix them using
various types of resources to minimize the heavy losses. Effective risk management in Te Mata
Estate makes value which plays an important role in their decision-making process against
upcoming threats.
a)
Risk
Avoidance : Mainly used to remove activities which involves risk and have extreme approach for
risk .

b) Prevention : Manage liabilities by making activities and program in a way which reduce the
limitations risk.
c) Risk Transfer : By using insurance policies and identification of agreements we transfer the risk
to another party .
d) Risk Retention : In this we accept the risk as it is for a specific purpose.
The overall transaction process is also known as data processing. The transaction system mainly
includes this type of subsystems like sales, production, purchasing, shipping, inventory, and payroll
of the company. A transaction cycle is a set of interlocking business transactions. Due to the lack of
process visibility,, it is very tough to assess the real progress through documented analysis in e -
commerce. The risk is mainly related to the quality and amount of the available information. Due to
lack of information the risk is higher. The different process model has different levels of risk.
Task 2 :
Assurance and compliance components
There are so many different types of ethical issues are present. They are normally divided into four
categories and generally known as acronym PAPA. Here PAPA stands for Privacy, Accuracy,
Property, and Accessibility.
a) In privacy, we mainly work on what an individual data and information are going to exchange
and share under some specific terms and conditions with other people as well as also help in
deciding what to keep safe and what to share with others.
b) Whereas inaccuracy we look for the data and information validity, as well as find out the
responsible authorities for error in data and information and also the affected party lost.
c)In property, we basically tried to find out the owner of the data and information and also tried to
fix the prices for its exchange.
limitations risk.
c) Risk Transfer : By using insurance policies and identification of agreements we transfer the risk
to another party .
d) Risk Retention : In this we accept the risk as it is for a specific purpose.
The overall transaction process is also known as data processing. The transaction system mainly
includes this type of subsystems like sales, production, purchasing, shipping, inventory, and payroll
of the company. A transaction cycle is a set of interlocking business transactions. Due to the lack of
process visibility,, it is very tough to assess the real progress through documented analysis in e -
commerce. The risk is mainly related to the quality and amount of the available information. Due to
lack of information the risk is higher. The different process model has different levels of risk.
Task 2 :
Assurance and compliance components
There are so many different types of ethical issues are present. They are normally divided into four
categories and generally known as acronym PAPA. Here PAPA stands for Privacy, Accuracy,
Property, and Accessibility.
a) In privacy, we mainly work on what an individual data and information are going to exchange
and share under some specific terms and conditions with other people as well as also help in
deciding what to keep safe and what to share with others.
b) Whereas inaccuracy we look for the data and information validity, as well as find out the
responsible authorities for error in data and information and also the affected party lost.
c)In property, we basically tried to find out the owner of the data and information and also tried to
fix the prices for its exchange.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

d) And at last inaccessibility, we mainly work on what type of data and information any individual
or organization have the right to obtain under certain terms and conditions.
As we see that there are many problems which occur due to the communication problem between
developers, managers, and customers. Currently, there are two main forces which put major risk on
the privacy of the individual and organization. First one is a sudden rise in the use of information
technology with more new capabilities of communications, surveillance, and storage. Whereas the
second one is a more dangerous threat in which information plays a major role in the decision-
making process. Information leaks lead to invades the privacy of individuals and organization.
Task 3 :
a) Risk management controls and standards
The new risk management standard has many definitions and approaches to managing the risk
factor. All the new method and theory which is developed in AS/NZS ISO 31000:2009 for the
benefits of the organization which help in making confident and balanced decisions about all the
risks which Te Mata Estate are going to face in the future. Data and information which are in the
form of documents, persentations , emails, and databases are the lifeline of the most of the
companies and application which protect and run your organisations requires a lot of space.
Wireless network can be easily compormise by using share key. Due to increasing dependence on
IT also increased the risk impact of IT on overall organization business. Nowadays threats in IT
services is increased because its vulnerabilities is exposed across the world.
b) Identify and analyse
Clause 5 of ISO 31000 defines the risk management process as “the systematic application of
management policies, procedures, and practices to the activities of communicating, consulting,
establishing the context, and identifying, analyzing, evaluating, treating, monitoring and reviewing
risk” (ISO Guide 73:2009, definition 3.1). ISO/IEEE/IEC29119 software testing is a benchmark set
or organization have the right to obtain under certain terms and conditions.
As we see that there are many problems which occur due to the communication problem between
developers, managers, and customers. Currently, there are two main forces which put major risk on
the privacy of the individual and organization. First one is a sudden rise in the use of information
technology with more new capabilities of communications, surveillance, and storage. Whereas the
second one is a more dangerous threat in which information plays a major role in the decision-
making process. Information leaks lead to invades the privacy of individuals and organization.
Task 3 :
a) Risk management controls and standards
The new risk management standard has many definitions and approaches to managing the risk
factor. All the new method and theory which is developed in AS/NZS ISO 31000:2009 for the
benefits of the organization which help in making confident and balanced decisions about all the
risks which Te Mata Estate are going to face in the future. Data and information which are in the
form of documents, persentations , emails, and databases are the lifeline of the most of the
companies and application which protect and run your organisations requires a lot of space.
Wireless network can be easily compormise by using share key. Due to increasing dependence on
IT also increased the risk impact of IT on overall organization business. Nowadays threats in IT
services is increased because its vulnerabilities is exposed across the world.
b) Identify and analyse
Clause 5 of ISO 31000 defines the risk management process as “the systematic application of
management policies, procedures, and practices to the activities of communicating, consulting,
establishing the context, and identifying, analyzing, evaluating, treating, monitoring and reviewing
risk” (ISO Guide 73:2009, definition 3.1). ISO/IEEE/IEC29119 software testing is a benchmark set
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

standard for the world. Standards mean services for everyone. ISO/IEC/IEEE 29119 is a series of
standardization which mainly covers the systems and software testing. The main aim behind these
series is to make a set of standards which is accepted globally. According to IEEE Standard 610.12-
1990, the testing of software is explained as “The methods of analyzing a software product to find
out the differences between old and new situations(which is, bugs) and to measures the new updates
of the software products."
Task 4. Unethical hacking
In Te Mata Estate (2008), a hacking took place which not only denied access to the administrator of
the system but also the functionality of the whole system was highly downgraded. After much
intervention, it was realized that one of the employees had deliberately given out critical
information of the system to some hackers for an exchange with cash. It is proved that data &
information both work as a support system for both consumer and business. The main problem
arises when privacy is invaded, as well as sensitive information and data is lost and stored. Due to
this individual or company security and privacy ethics become very vulnerable. The management of
risk is the basis of an information system to provide the best cybersecurity solution. One of the
major security threats is an employee who works on the system. They can easily harm the system
with intention and for fulfilling some purposes. Hackers are the very common type of attacker on
cyberspace. They find the loophole in security and attack by using the known method at a very high
rate frequently to get the desired results. Mails and servers are their main target. If they are not able
to find the weakness they go for an easy target and plant their attack. Te Mata Estate should also
always check whether the current legal framework fulfills the criteria of available technology or
not. Because without proper security guarantees of security and integrity as well as privacy of the
data and information the digital legal system framework is not going to develop properly.
standardization which mainly covers the systems and software testing. The main aim behind these
series is to make a set of standards which is accepted globally. According to IEEE Standard 610.12-
1990, the testing of software is explained as “The methods of analyzing a software product to find
out the differences between old and new situations(which is, bugs) and to measures the new updates
of the software products."
Task 4. Unethical hacking
In Te Mata Estate (2008), a hacking took place which not only denied access to the administrator of
the system but also the functionality of the whole system was highly downgraded. After much
intervention, it was realized that one of the employees had deliberately given out critical
information of the system to some hackers for an exchange with cash. It is proved that data &
information both work as a support system for both consumer and business. The main problem
arises when privacy is invaded, as well as sensitive information and data is lost and stored. Due to
this individual or company security and privacy ethics become very vulnerable. The management of
risk is the basis of an information system to provide the best cybersecurity solution. One of the
major security threats is an employee who works on the system. They can easily harm the system
with intention and for fulfilling some purposes. Hackers are the very common type of attacker on
cyberspace. They find the loophole in security and attack by using the known method at a very high
rate frequently to get the desired results. Mails and servers are their main target. If they are not able
to find the weakness they go for an easy target and plant their attack. Te Mata Estate should also
always check whether the current legal framework fulfills the criteria of available technology or
not. Because without proper security guarantees of security and integrity as well as privacy of the
data and information the digital legal system framework is not going to develop properly.

Task 5. Counter measures against phishing attack
In Te Mata Estate (2011), An email was sent to the department claiming that the sender was a new
supplier from a subsidiary company and the department was to pay a deposit to the given bank
account number to facilitate the delivery of grapes. Without confirmation from the other
departments, the chief accountant authorized the payment blindly. After a few days, it was realized
that the money was sent to a cybercriminal who had masqueraded to be a supplier. The efforts to
track the money proved futile since the criminal didn’t leave any traces. Information leaks lead to
invades the privacy of individuals and organization. As we see that information technology is the
major sector which rides and lives on cyberspace. In recent time business analytics and intelligence
platform responsible for mainstream data and information flow with a high rate of cloud-based
deployments.offers visual based intuitive interaction experience which permits the user to analyze,
access and finding current errors in their database without having any coding or technical skills. It is
mainly used to provide standard way to visualize the system design process. It enable developer to
construct, visualize, specifies and document the design of the system. Its help in making the
architecture more scalable, robust and secure in execution.
Task 6.
Approaches for Security of network components
Applying these standards of software testing help with global knowledge and mutual standards for
testing software, at the same time it also provides a high-quality method towards the assurance of
quality.
a) The software design must be verified against requirements so that users needs are reflected in the
design.Functional testing mainly carried out to ensure how the product behaves according to
functional requirements in the system. Whereas usability testing mainly focuses on the acceptance
of the customer.
In Te Mata Estate (2011), An email was sent to the department claiming that the sender was a new
supplier from a subsidiary company and the department was to pay a deposit to the given bank
account number to facilitate the delivery of grapes. Without confirmation from the other
departments, the chief accountant authorized the payment blindly. After a few days, it was realized
that the money was sent to a cybercriminal who had masqueraded to be a supplier. The efforts to
track the money proved futile since the criminal didn’t leave any traces. Information leaks lead to
invades the privacy of individuals and organization. As we see that information technology is the
major sector which rides and lives on cyberspace. In recent time business analytics and intelligence
platform responsible for mainstream data and information flow with a high rate of cloud-based
deployments.offers visual based intuitive interaction experience which permits the user to analyze,
access and finding current errors in their database without having any coding or technical skills. It is
mainly used to provide standard way to visualize the system design process. It enable developer to
construct, visualize, specifies and document the design of the system. Its help in making the
architecture more scalable, robust and secure in execution.
Task 6.
Approaches for Security of network components
Applying these standards of software testing help with global knowledge and mutual standards for
testing software, at the same time it also provides a high-quality method towards the assurance of
quality.
a) The software design must be verified against requirements so that users needs are reflected in the
design.Functional testing mainly carried out to ensure how the product behaves according to
functional requirements in the system. Whereas usability testing mainly focuses on the acceptance
of the customer.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

b) The software and hardware part which are going to use in the Te Mata Estate is also checked by
the IT professional upcoming risks. Session management, ID management, security events, and
logging are the major risk factor areas of the Te Mata Estate. There are so many salient features of
the password policy like enforced password history, password maximum age, password minimum
age, password minimum length, passwords must meet the complexity requirements and then after
stores the passwords using the reversible encryption. In today time there are so many systems like
Google and other IT giant have built-in password methods to set the policy.
c) As we see that nowadays most of business pc is overtake by mobile devices. Data sent over the
wireless network can be easily accessed by attackers using various data interception techniques.
Identity theft is also very common in wireless network when able to capture the network traffic and
able to identifies the address of the computer using network privileges. wireless computing device
and mobile are the main target to attackers because of unmanaged use of wireless links. As we see
that in a big organisation network infrastructure data mainly originates and travel in so many
different environments like remote locations and main office.
Task 7.
Recommendations/solutions for Security of communication
a) Te Mata Estate IT system provides management features where they can store complete
information of the customer and their details of purchasing in the estate, details of Te Mata Estate
products information. Its mainly helps Te Mata Estate to monitor every information which is used in
their E-Commerce system in the time of online activities like payment cycle and information about
the product. Resource management of Te Mata Estate e-commerce system helps in removing and
adding new data as well as information about the transaction, user and products.
b) Te Mata previous system is not very user-friendly. Now, Estate e-commerce system user
interfaces mainly design by keeping the mind in customer requirements with their new system.
the IT professional upcoming risks. Session management, ID management, security events, and
logging are the major risk factor areas of the Te Mata Estate. There are so many salient features of
the password policy like enforced password history, password maximum age, password minimum
age, password minimum length, passwords must meet the complexity requirements and then after
stores the passwords using the reversible encryption. In today time there are so many systems like
Google and other IT giant have built-in password methods to set the policy.
c) As we see that nowadays most of business pc is overtake by mobile devices. Data sent over the
wireless network can be easily accessed by attackers using various data interception techniques.
Identity theft is also very common in wireless network when able to capture the network traffic and
able to identifies the address of the computer using network privileges. wireless computing device
and mobile are the main target to attackers because of unmanaged use of wireless links. As we see
that in a big organisation network infrastructure data mainly originates and travel in so many
different environments like remote locations and main office.
Task 7.
Recommendations/solutions for Security of communication
a) Te Mata Estate IT system provides management features where they can store complete
information of the customer and their details of purchasing in the estate, details of Te Mata Estate
products information. Its mainly helps Te Mata Estate to monitor every information which is used in
their E-Commerce system in the time of online activities like payment cycle and information about
the product. Resource management of Te Mata Estate e-commerce system helps in removing and
adding new data as well as information about the transaction, user and products.
b) Te Mata previous system is not very user-friendly. Now, Estate e-commerce system user
interfaces mainly design by keeping the mind in customer requirements with their new system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Their e-commerce system fulfills the needs of users and products information in a user-friendly
way so that they can purchase without any problem. When we check in the business model then we
found that only the location of the site is a risky thing otherwise company purpose and plan are
same and good. When human interaction with the system then there is a high level of privacy
concern among the users. Companies which rely more on human interaction with the system often
face these mistakes: Sometimes they use these things to answer meaningless questions.
c) In privacy, we mainly work onwhat an individual data and information is going to exchange and
share under some specific terms and conditions with other people as well as also help in deciding
what to keep safe and what to share with others. Whereas inaccuracy we look for the data and
information validity, as well as find out the responsible authorities for error in data and information
and also the affected party lost. In property, we basically tried to find out the owner of the data and
information and also tried to fix the prices for its exchange. And at last inaccessibility, we mainly
work on what type of data and information any individual or organization have the right to obtain
under certain terms and conditions.
Task 8.
Components of information security operations
a) Preventive maintenance of the Estate IT system maintains, analyze, and control the performance
of Te Mata applications according to the user requirements. It covers from server admin to the end
user and everything which connect all the IT infrastructure for good and bad purpose at the same
time. So regular update on a daily basis of preventive measures makes Te Mata Estate more secure
and user-friendly. According to IEEE Standard 610.12-1990, the testing of software is explained as
“The methods of analyzing a software product to find out the differences between old and new
situations(which is, bugs) and to measures the new updates of the software products."
way so that they can purchase without any problem. When we check in the business model then we
found that only the location of the site is a risky thing otherwise company purpose and plan are
same and good. When human interaction with the system then there is a high level of privacy
concern among the users. Companies which rely more on human interaction with the system often
face these mistakes: Sometimes they use these things to answer meaningless questions.
c) In privacy, we mainly work onwhat an individual data and information is going to exchange and
share under some specific terms and conditions with other people as well as also help in deciding
what to keep safe and what to share with others. Whereas inaccuracy we look for the data and
information validity, as well as find out the responsible authorities for error in data and information
and also the affected party lost. In property, we basically tried to find out the owner of the data and
information and also tried to fix the prices for its exchange. And at last inaccessibility, we mainly
work on what type of data and information any individual or organization have the right to obtain
under certain terms and conditions.
Task 8.
Components of information security operations
a) Preventive maintenance of the Estate IT system maintains, analyze, and control the performance
of Te Mata applications according to the user requirements. It covers from server admin to the end
user and everything which connect all the IT infrastructure for good and bad purpose at the same
time. So regular update on a daily basis of preventive measures makes Te Mata Estate more secure
and user-friendly. According to IEEE Standard 610.12-1990, the testing of software is explained as
“The methods of analyzing a software product to find out the differences between old and new
situations(which is, bugs) and to measures the new updates of the software products."

b) software testing standards have a globally-accepted set of standards which can be used by any
company when they do software testing. Applying these standards of software testing help to ensure
how product behave according to functional requirements in the system. Whereas usability testing
ainly focus on acceptance of the customer. The new global standard nowadays covers the different
level of testing processes. Its mainly cover the documentation process, design test methods, and
concepts. The standard mainly helps in recognizing different types of software and development of
methods of any industry.
c) Testing plays an important role in the foundation of the success of any software products. System
test plan is detailed strategy of test plan. The test document mainly consists of different type of test
plan and test cases. The quality of system and product mainly depends upon the requirements which
explain the problem, design and analysis models of the solution, tests which exercise the software to
find out their error. A good software development process mainly uses measurment to assess the
quality of all four compoenet.
Task 9.
Vulnerabilities assessment and testing
The new global standard nowadays covers the different level of testing processes. Its mainly cover
the documentation process, design test methods, and concepts. The standard mainly helps in
recognizing different types of software and development of methods of any industry. Testing plays
an important role in the foundation of the success of any software products. The test document
mainly consists of different type of test plan and test cases. Standards are published documents
setting out specifications and procedures designed to ensure products, services and systems are safe,
reliable and consistently perform the way they were intended to. They establish a common language
which defines quality and safety criteria. There are several standards, international and national, that
relate specifically to software testing. Standards formalize industry best practice and they are agreed
company when they do software testing. Applying these standards of software testing help to ensure
how product behave according to functional requirements in the system. Whereas usability testing
ainly focus on acceptance of the customer. The new global standard nowadays covers the different
level of testing processes. Its mainly cover the documentation process, design test methods, and
concepts. The standard mainly helps in recognizing different types of software and development of
methods of any industry.
c) Testing plays an important role in the foundation of the success of any software products. System
test plan is detailed strategy of test plan. The test document mainly consists of different type of test
plan and test cases. The quality of system and product mainly depends upon the requirements which
explain the problem, design and analysis models of the solution, tests which exercise the software to
find out their error. A good software development process mainly uses measurment to assess the
quality of all four compoenet.
Task 9.
Vulnerabilities assessment and testing
The new global standard nowadays covers the different level of testing processes. Its mainly cover
the documentation process, design test methods, and concepts. The standard mainly helps in
recognizing different types of software and development of methods of any industry. Testing plays
an important role in the foundation of the success of any software products. The test document
mainly consists of different type of test plan and test cases. Standards are published documents
setting out specifications and procedures designed to ensure products, services and systems are safe,
reliable and consistently perform the way they were intended to. They establish a common language
which defines quality and safety criteria. There are several standards, international and national, that
relate specifically to software testing. Standards formalize industry best practice and they are agreed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

upon by professionals in the industry in which the standards apply. Software testing mainly looks
for a potential threat before going life or moved into the user environment. So many testers still
think that testing field is still not ready for a standard. Independent standards accurately identify
problems in the infrastructure without doing any partiality. It provides solid proofs of product
effectiveness. To make their products more transparent to their vendors and customers it is very
necessary to opt independent standard benchmark for software testing. Due to the lack of process
visibility, it is very tough to assess the real progress through documented standards.
Task 10.
Incident management
a) In a big organization network infrastructure data mainly originates and travel in so many
different environments like remote locations and main office. The main office is where all the
branch offices are reporting and where most important server run whereas branch offices are mainly
located in remote places and connected to the main office through a wide area network. Branch
offices normally host less important servers. To connect many employees at the same time all office
location must access the same network resources.
b) There are so many companies which deploy wide area network(WAN) to connect with the
remote offices. WAN mainly used to connect LAN from different offices together. By using these
services Te Mata Estate can work from separate offices and share or communicate information
easily with effectiveness. The management of risk is the basis of an information system to provide
the best cybersecurity solution. here are so many activities which mainly solved or minimize the
risk associated with specific portion of the software development process like : objective,
constraints, alternatives, risks, risk resolution, results, plan, commitement. As we know that these
activities mainly used for system development task to improve their quality.
for a potential threat before going life or moved into the user environment. So many testers still
think that testing field is still not ready for a standard. Independent standards accurately identify
problems in the infrastructure without doing any partiality. It provides solid proofs of product
effectiveness. To make their products more transparent to their vendors and customers it is very
necessary to opt independent standard benchmark for software testing. Due to the lack of process
visibility, it is very tough to assess the real progress through documented standards.
Task 10.
Incident management
a) In a big organization network infrastructure data mainly originates and travel in so many
different environments like remote locations and main office. The main office is where all the
branch offices are reporting and where most important server run whereas branch offices are mainly
located in remote places and connected to the main office through a wide area network. Branch
offices normally host less important servers. To connect many employees at the same time all office
location must access the same network resources.
b) There are so many companies which deploy wide area network(WAN) to connect with the
remote offices. WAN mainly used to connect LAN from different offices together. By using these
services Te Mata Estate can work from separate offices and share or communicate information
easily with effectiveness. The management of risk is the basis of an information system to provide
the best cybersecurity solution. here are so many activities which mainly solved or minimize the
risk associated with specific portion of the software development process like : objective,
constraints, alternatives, risks, risk resolution, results, plan, commitement. As we know that these
activities mainly used for system development task to improve their quality.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

c) Most of the tests design are according to the initial explanation of the requirements and are not
able to change according to the requirements. If the testing process is not automated then it will be
boring and monotonus and have maximum chance to give the fail results. There is a very huge
chance of fault rate in newly design components. The system design must be verified against
requirements so that users needs are reflected in the design .
d) Due to standards, businesses and users can feel confident that their software products and
services they develop and/or use are safe, reliable and user-friendly. It works as a launch pad for
new innovations. They can be created and destroy according to the requirement of our changing
world. New standards mainly developed to show new technologies and innovations.
Task 11.
Codes of Professional Practice
a) Many of the recent research shows that the end user has a big impact on the success and failure
of Standards and software testing. As we see that normally people reject the change when they get
instantly in the system. Due to their rejection, it poses a bad effect on the acceptance of the new
system negatively.
b) It is very common for the end users to find it problematic to use any new deploy system. But if
this thing lasts a long then threat to the acceptability of the system increases. The end user always
wants the new requirements during the operation of the system which is implemented mainly to
fulfill the user needs, organizational and environmental changes, and needs of the business.
c) This new risk management standard has many definitions and approaches to managing the risk
factor. All the new method and theory which is developed in AS/NZS ISO 31000:2009 for the
benefits of the organization which helps in making confident and balanced decisions about all the
risks which they are going to face in the future.
able to change according to the requirements. If the testing process is not automated then it will be
boring and monotonus and have maximum chance to give the fail results. There is a very huge
chance of fault rate in newly design components. The system design must be verified against
requirements so that users needs are reflected in the design .
d) Due to standards, businesses and users can feel confident that their software products and
services they develop and/or use are safe, reliable and user-friendly. It works as a launch pad for
new innovations. They can be created and destroy according to the requirement of our changing
world. New standards mainly developed to show new technologies and innovations.
Task 11.
Codes of Professional Practice
a) Many of the recent research shows that the end user has a big impact on the success and failure
of Standards and software testing. As we see that normally people reject the change when they get
instantly in the system. Due to their rejection, it poses a bad effect on the acceptance of the new
system negatively.
b) It is very common for the end users to find it problematic to use any new deploy system. But if
this thing lasts a long then threat to the acceptability of the system increases. The end user always
wants the new requirements during the operation of the system which is implemented mainly to
fulfill the user needs, organizational and environmental changes, and needs of the business.
c) This new risk management standard has many definitions and approaches to managing the risk
factor. All the new method and theory which is developed in AS/NZS ISO 31000:2009 for the
benefits of the organization which helps in making confident and balanced decisions about all the
risks which they are going to face in the future.

d) To solve this they are setting the standard which is capable to solve all forms of risk and provide
reliability and consistency. Independent security checks accurately identify problems in the
infrastructure without doing any partiality. It provides solid proofs of product effectiveness.
Experties in the both the process play a main role in project success. Main issues which affect the
uncertainity in project planning mainly consists of project size, project complexity, and structural
uncertainity .
Task 12.
IT Professionals New Zealand’s Code of Ethics
Examine
According to NewZeland code of IT, Independent security audit to keep all the program in track as
well as decrease the tension of formal audits of the system. It helps in fulfilling an important role to
make sure that all the procedures and policies are followed according to the business standards and
legislation or not. To make audit impartial it is necessary to involve people who are independent of
the specific business enterprise. The way nowadays people use the internet, it is a very high
probability that someone out there knows more about the people than people know about himself.
Discussion
The expertise and experience of the stakeholders in many cases always improves the understanding
of the risk. To make their products more transparent to their vendors and customers it is very
necessary to opt independent security benchmark.They provide surety about the quality and
consistency of software products and their services. They also enhance the company economy,
provide best health services and safety, It also protects the natural resources, and provide a better
quality of life. The new global standard of software testing was created by International
standardization organization (ISO) and International Electrotechnical Commission (IEC) in the year
2013. This method offers the best results. Before the design process of system developers must
have to go for two activities like knowing the problems in brief which they are going to solve and
reliability and consistency. Independent security checks accurately identify problems in the
infrastructure without doing any partiality. It provides solid proofs of product effectiveness.
Experties in the both the process play a main role in project success. Main issues which affect the
uncertainity in project planning mainly consists of project size, project complexity, and structural
uncertainity .
Task 12.
IT Professionals New Zealand’s Code of Ethics
Examine
According to NewZeland code of IT, Independent security audit to keep all the program in track as
well as decrease the tension of formal audits of the system. It helps in fulfilling an important role to
make sure that all the procedures and policies are followed according to the business standards and
legislation or not. To make audit impartial it is necessary to involve people who are independent of
the specific business enterprise. The way nowadays people use the internet, it is a very high
probability that someone out there knows more about the people than people know about himself.
Discussion
The expertise and experience of the stakeholders in many cases always improves the understanding
of the risk. To make their products more transparent to their vendors and customers it is very
necessary to opt independent security benchmark.They provide surety about the quality and
consistency of software products and their services. They also enhance the company economy,
provide best health services and safety, It also protects the natural resources, and provide a better
quality of life. The new global standard of software testing was created by International
standardization organization (ISO) and International Electrotechnical Commission (IEC) in the year
2013. This method offers the best results. Before the design process of system developers must
have to go for two activities like knowing the problems in brief which they are going to solve and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





