University Information Security Report: ATM and Biometric Analysis
VerifiedAdded on 2022/09/18
|14
|4556
|34
Report
AI Summary
This report delves into the realm of information security, focusing on the Automated Teller Machine (ATM) and biometric authentication systems. It begins by exploring the ATM's role in automating financial transactions, emphasizing the importance of security measures such as the Confidentiality, Integrity, and Availability (CIA) triad. The report examines ATM functionality, including input and output devices, and the potential vulnerabilities associated with PIN security. The second part of the report analyzes the working principle of an ATM, detailing the input and output devices. It provides a practical example involving a compromised ATM and calculates the possible PIN combinations a thief could attempt, highlighting the importance of strong PIN practices. Finally, the report discusses biometric authentication as a security enhancement, outlining different techniques like fingerprint and iris scanning. It addresses the triggers that may make individuals hesitant to adopt biometric authentication, such as cost, and the need for robust security to safeguard against evolving hacking techniques.

Running head: INFORMATION SECURITY
Information Security
Name of the Student:
Name of the University:
Information Security
Name of the Student:
Name of the University:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Answer to Question 1
Automated Teller Machine (ATM) is referred to as a banking machine that helps to
automate money transaction process where no bank representatives are required while
processing. Two different types of ATM are most installed by the banking industry to credit and
debit money regardless of time and location of the users. However, it is duty of the IT security
team working for the bank industry to make sure that all security aspects are properly followed
for the system and information (Yoon & Jain, 2015). The machines are designed so that users
can use their PIN as well as card to access the bank account with high level security.
Confidentiality, integrity and availability (CIA) model is a security triad which is developed and
modeled for designing guidance policies mainly for the information stored in the server.
Sometimes this model is also known as AIC triad. The model also helps to avoid potential
confusion by Central Intelligence Agency. In any system presence of these three factors
demonstrates the degree of significance for each of the requirement. Examples of three of the
factors are elaborate in the below section:
Confidentiality: In order to access credit and debit the users should go into a safety
password that is only available to the authorized users. This factor helps to improve security
level. Card reader is the input device which reads information as soon as the card is swiped. Card
reader is used as a part of identification of an accurate account number (Tome et al., 2015). In
order to make connection between the card and the machine a magnetic band is available in back
of the card. Then the card is passed to the server or the host server. As soon as the ATM
recognizes the card user identification number, withdrawal, mini statement etc options become
available. Then the users need to input the PIN (4 digit). The PIN numbers input in the keypad
are inserted in an encrypted form. However, in order to ensure financial security it is
responsibility of the users to use stronger PIN code (Smith, Wiliem & Lovell, 2015). Whenever
communication between bank server and the ATM card is processed it is responsibility of the
bank authority to ensure enough security to protect user information to get hacked by
unauthorized users. The process of money transaction is needed to be secured to avoid unwanted
harm, data hacking and data misuse by the unauthorized hackers. Encryption is the best suited
approach that helps to keep information protected from outside attackers. In order to keep
Answer to Question 1
Automated Teller Machine (ATM) is referred to as a banking machine that helps to
automate money transaction process where no bank representatives are required while
processing. Two different types of ATM are most installed by the banking industry to credit and
debit money regardless of time and location of the users. However, it is duty of the IT security
team working for the bank industry to make sure that all security aspects are properly followed
for the system and information (Yoon & Jain, 2015). The machines are designed so that users
can use their PIN as well as card to access the bank account with high level security.
Confidentiality, integrity and availability (CIA) model is a security triad which is developed and
modeled for designing guidance policies mainly for the information stored in the server.
Sometimes this model is also known as AIC triad. The model also helps to avoid potential
confusion by Central Intelligence Agency. In any system presence of these three factors
demonstrates the degree of significance for each of the requirement. Examples of three of the
factors are elaborate in the below section:
Confidentiality: In order to access credit and debit the users should go into a safety
password that is only available to the authorized users. This factor helps to improve security
level. Card reader is the input device which reads information as soon as the card is swiped. Card
reader is used as a part of identification of an accurate account number (Tome et al., 2015). In
order to make connection between the card and the machine a magnetic band is available in back
of the card. Then the card is passed to the server or the host server. As soon as the ATM
recognizes the card user identification number, withdrawal, mini statement etc options become
available. Then the users need to input the PIN (4 digit). The PIN numbers input in the keypad
are inserted in an encrypted form. However, in order to ensure financial security it is
responsibility of the users to use stronger PIN code (Smith, Wiliem & Lovell, 2015). Whenever
communication between bank server and the ATM card is processed it is responsibility of the
bank authority to ensure enough security to protect user information to get hacked by
unauthorized users. The process of money transaction is needed to be secured to avoid unwanted
harm, data hacking and data misuse by the unauthorized hackers. Encryption is the best suited
approach that helps to keep information protected from outside attackers. In order to keep

2INFORMATION SECURITY
information tenable from outside attackers it is essential for the users to follow PIN changing
related policy and guidelines after periodic intervals. It also helps to boost up the information
security process.
Integrity: In order to make sure that consumers or user data are integrated, secured and
properly maintained advanced, efficient and effective technology for optimizing and
collaborating ATM are required. The system is needed to be chronologically updated using
authenticated information and PIN numbers both in while money will be debited and credited
(Larbi & Taleb, 2018). The process of money withdrawal is known as credit and fund deposit is
known as debited. However, each bank needs to have an inquiry department to deal with the
query coming from the users frequently. It is their responsibility to resolve those queries and
make sure that the process is completely integrated.
Availability: Based on demand and expectation of both customers others the frequency
of the ATM needs to be enhanced for accurate service delivery. The availability of any system is
ensured by appropriate maintenance of all available hardware. All crucial systems are needed to
keep well maintained and updated (Vazquez-Fernandez & Gonzalez-Jimenez, 2016). Issues of
failover, data redundancy, data hijack will be completely avoided if theses aspects are throughout
followed. The process must hold capabilities of disaster recovery, back and application
resilience. If any time an ATM is found to be not working accurately it will be a major issue for
the customers. Accuracy in ATM will help to grab more numbers of customers and provide
emergency services to the customers. The process of ATM improves the
Answer to Question 2
The working principle of an ATM is processed by two input devices and four numbers of
output devices. The input devices used in the ATM machines are card reader and a keypad and
the output activities are speaker, display screen, receipt printer and cash depositor. The control
unit of the machine operated the entire process to fulfill the customer requirements. One of the
major input devices that are available in the ATM is card reader. As soon as an ATM card is
inserted to the machine the machine starts reading the information the card. It mainly identifies
the information of the use who wants to either debit or credit money from the machine (Barbello,
2016). As the card reader reads needful information from the user’s card it requests for further
information tenable from outside attackers it is essential for the users to follow PIN changing
related policy and guidelines after periodic intervals. It also helps to boost up the information
security process.
Integrity: In order to make sure that consumers or user data are integrated, secured and
properly maintained advanced, efficient and effective technology for optimizing and
collaborating ATM are required. The system is needed to be chronologically updated using
authenticated information and PIN numbers both in while money will be debited and credited
(Larbi & Taleb, 2018). The process of money withdrawal is known as credit and fund deposit is
known as debited. However, each bank needs to have an inquiry department to deal with the
query coming from the users frequently. It is their responsibility to resolve those queries and
make sure that the process is completely integrated.
Availability: Based on demand and expectation of both customers others the frequency
of the ATM needs to be enhanced for accurate service delivery. The availability of any system is
ensured by appropriate maintenance of all available hardware. All crucial systems are needed to
keep well maintained and updated (Vazquez-Fernandez & Gonzalez-Jimenez, 2016). Issues of
failover, data redundancy, data hijack will be completely avoided if theses aspects are throughout
followed. The process must hold capabilities of disaster recovery, back and application
resilience. If any time an ATM is found to be not working accurately it will be a major issue for
the customers. Accuracy in ATM will help to grab more numbers of customers and provide
emergency services to the customers. The process of ATM improves the
Answer to Question 2
The working principle of an ATM is processed by two input devices and four numbers of
output devices. The input devices used in the ATM machines are card reader and a keypad and
the output activities are speaker, display screen, receipt printer and cash depositor. The control
unit of the machine operated the entire process to fulfill the customer requirements. One of the
major input devices that are available in the ATM is card reader. As soon as an ATM card is
inserted to the machine the machine starts reading the information the card. It mainly identifies
the information of the use who wants to either debit or credit money from the machine (Barbello,
2016). As the card reader reads needful information from the user’s card it requests for further
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
process like: cash withdrawal, mini statement, balance enquiry etc. Each card has different and
unique PIN numbers that is mainly sent in encrypted form. The key board is comprises of 16
keys and these are interfaced to the processor of Automated Teller Machine. Among the 16 keys,
from 0 to 9 total 10 numeric keys are available and some other keys are present in the keypad in
the form of ENTER, CLEAR, CANCEL etc. Then the speaker gives an audio feedback while
any specific key is pressed by the users who wants to either debit or credit money from the ATM
(Kursun et al., 2018). The display screen of ATM shows the transaction details that are the
money to be withdrawal, current value available in the account and some other details as well.
Details are shown in the display.
It has been identified that, an ATM machine is comprises of 0 to 9 numeric numbers and
certain other keys. If the user wants to cancel the transaction then a CANCEL numbers is
available similarly for further progress ENTER button is available (Novack et al., 2015). A thief
insolvent a machine in ATM using a device and successfully blocked the working principle of
the card reader so that it can stop read the information stored in a card. Not only this but also the
thief has also broke 5 keys of the keypad. Thief was aimed to stop running procedure of the
Automated Teller Machine (ATM), as a customer will approach for any amount credit or debit.
Immediately after that another customer came to debit money from his or her bank account. The
customer also successfully withdrawals some money from the financial account but unable to
withdraw the ATM card from the machine. Immediate after that the thief came back and tried to
discover the ATM PIN of the customer so that can steal some money from customer account. In
order to identify the exact PIN of the customer the thief needs to calculate some permutation
combination. As 5 of the keys were already broken therefore, the possible PIN combination
needs to be prepared by the thief are of rest of the 5 keys. ATM PINS are made up of 4 digits.
The possible PIN numbers will be in between 0000 and 9999, where the lower level digit is 0000
and the upper or maximum higher level possible number is 9999 (Smith, Wiliem & Lovell,
(2015). The formula used to identify the possible numbers of PIN that the thief can enter to
withdraw money from the ATM is = nP(n-1).
In the formula n is the numbers of possible digits available. 5 keys are already broken
thus only 5 keys are left. Thus, the combination will be formed considering the left 5 numbers
only.
process like: cash withdrawal, mini statement, balance enquiry etc. Each card has different and
unique PIN numbers that is mainly sent in encrypted form. The key board is comprises of 16
keys and these are interfaced to the processor of Automated Teller Machine. Among the 16 keys,
from 0 to 9 total 10 numeric keys are available and some other keys are present in the keypad in
the form of ENTER, CLEAR, CANCEL etc. Then the speaker gives an audio feedback while
any specific key is pressed by the users who wants to either debit or credit money from the ATM
(Kursun et al., 2018). The display screen of ATM shows the transaction details that are the
money to be withdrawal, current value available in the account and some other details as well.
Details are shown in the display.
It has been identified that, an ATM machine is comprises of 0 to 9 numeric numbers and
certain other keys. If the user wants to cancel the transaction then a CANCEL numbers is
available similarly for further progress ENTER button is available (Novack et al., 2015). A thief
insolvent a machine in ATM using a device and successfully blocked the working principle of
the card reader so that it can stop read the information stored in a card. Not only this but also the
thief has also broke 5 keys of the keypad. Thief was aimed to stop running procedure of the
Automated Teller Machine (ATM), as a customer will approach for any amount credit or debit.
Immediately after that another customer came to debit money from his or her bank account. The
customer also successfully withdrawals some money from the financial account but unable to
withdraw the ATM card from the machine. Immediate after that the thief came back and tried to
discover the ATM PIN of the customer so that can steal some money from customer account. In
order to identify the exact PIN of the customer the thief needs to calculate some permutation
combination. As 5 of the keys were already broken therefore, the possible PIN combination
needs to be prepared by the thief are of rest of the 5 keys. ATM PINS are made up of 4 digits.
The possible PIN numbers will be in between 0000 and 9999, where the lower level digit is 0000
and the upper or maximum higher level possible number is 9999 (Smith, Wiliem & Lovell,
(2015). The formula used to identify the possible numbers of PIN that the thief can enter to
withdraw money from the ATM is = nP(n-1).
In the formula n is the numbers of possible digits available. 5 keys are already broken
thus only 5 keys are left. Thus, the combination will be formed considering the left 5 numbers
only.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
The maximum combination= nP(n-1)
=5P4
=5! / (5-4)!
= 5! /1!
=(5*4*3*2*1)/1
=120
Therefore, in order to thief money from target customer’s account, 120 possible
combinations can be applied for the PIN identification. Personal Security Number (PIN) is
referred to as a security code used to verify identities. The PIN must be kept secured from the
external attackers like passwords as PIN code allows the Accessor to access important
confidential data from the server (Smith, Wiliem & Lovell, 2015). For financial transaction PIN
codes are used in the ATMs. For maintaining the bank account secured from outsider attackers
some factors that must be considered include:
Avoiding straightforward or sequence numeric sequences like 2345, 1234, and
also number repetition like 3344, 4455 etc.
Specific dates (like DOB) should be completely avoided
The users should not use any part from the postal code, address, security codes
and security numbers as well
The users are needs to avoid using parts from phone numbers
There are certain methods can be used by the users to while creating a secured PIN for
the Automated Teller Machine (ATM) and these tactics include the word method, random data
method, Cellphone Friend Method etc.
Answer to Question 3
Biometric authentication is referred to as a security development approach that is
dependent on biological and unique features of individuals. This approach is used to verify
specific person. These days in order to tighten security of organizations and banking industries
The maximum combination= nP(n-1)
=5P4
=5! / (5-4)!
= 5! /1!
=(5*4*3*2*1)/1
=120
Therefore, in order to thief money from target customer’s account, 120 possible
combinations can be applied for the PIN identification. Personal Security Number (PIN) is
referred to as a security code used to verify identities. The PIN must be kept secured from the
external attackers like passwords as PIN code allows the Accessor to access important
confidential data from the server (Smith, Wiliem & Lovell, 2015). For financial transaction PIN
codes are used in the ATMs. For maintaining the bank account secured from outsider attackers
some factors that must be considered include:
Avoiding straightforward or sequence numeric sequences like 2345, 1234, and
also number repetition like 3344, 4455 etc.
Specific dates (like DOB) should be completely avoided
The users should not use any part from the postal code, address, security codes
and security numbers as well
The users are needs to avoid using parts from phone numbers
There are certain methods can be used by the users to while creating a secured PIN for
the Automated Teller Machine (ATM) and these tactics include the word method, random data
method, Cellphone Friend Method etc.
Answer to Question 3
Biometric authentication is referred to as a security development approach that is
dependent on biological and unique features of individuals. This approach is used to verify
specific person. These days in order to tighten security of organizations and banking industries

5INFORMATION SECURITY
biometric authentication system are widely using by the management heads and CIO. However,
there are some triggers for that people may feel unwilling while using process of biometric
authentication. The biometric systems are used to make comparison between the biometric data
those have been stored in the server and the data that are already confirmed as authentic one in
the database (Vazquez-Fernandez & Gonzalez-Jimenez, 2016). Data authentication will be
confirmed if collected sample and biometric data are matched. Biometric authentication
approach is used for managing digital resource and physical data as well from external unwanted
access. There are different biometric authentications techniques are available such as:
Finger vain ID: The vascular pattern of different person varies from other. Therefore,
individual’s finger vain ids are also different based on the vascular patterns
Fingerprint scanning: The fingerprint of different persona re also different from other.
Finger scanning is referred to as a digital description of early days ink paper format (Mahfouz,
Mahmoud & Eldin, 2017). If fingerprint scanning process is used by organizations and banking
industry to keep data secured from external attackers then it will be identified as an effective one.
This type of authentication technique can never be a failure.
Iris scanning: In order to identify individuals depending on the different ring shapes iris
scanning can be done.
Retina scanning: The retina identification process identifies images of blood vessel
patterns in different sensitive platforms for lining the individual’s inner eye.
Voice recognition: Voice recognition is referred to as a process that is used to identify
individual’s voice feature ad quality. A voice identification system is relies on the characteristics
those have been created by throat and mouth shapes of speakers.
There are some triggers for that people may feel unwilling to employ approaching
biometric authentication. The details of these triggers are elaborated in the paper:
Budget: It has been analyzed that bio metric detection system is costlier than any other
option. The biometric process and the biometric devices are much costly than any other security
measurement and management technique. With advancement of technology these days’ hackers
have become stringer and easily retrieving data from seven strongly secured servers as well. It
biometric authentication system are widely using by the management heads and CIO. However,
there are some triggers for that people may feel unwilling while using process of biometric
authentication. The biometric systems are used to make comparison between the biometric data
those have been stored in the server and the data that are already confirmed as authentic one in
the database (Vazquez-Fernandez & Gonzalez-Jimenez, 2016). Data authentication will be
confirmed if collected sample and biometric data are matched. Biometric authentication
approach is used for managing digital resource and physical data as well from external unwanted
access. There are different biometric authentications techniques are available such as:
Finger vain ID: The vascular pattern of different person varies from other. Therefore,
individual’s finger vain ids are also different based on the vascular patterns
Fingerprint scanning: The fingerprint of different persona re also different from other.
Finger scanning is referred to as a digital description of early days ink paper format (Mahfouz,
Mahmoud & Eldin, 2017). If fingerprint scanning process is used by organizations and banking
industry to keep data secured from external attackers then it will be identified as an effective one.
This type of authentication technique can never be a failure.
Iris scanning: In order to identify individuals depending on the different ring shapes iris
scanning can be done.
Retina scanning: The retina identification process identifies images of blood vessel
patterns in different sensitive platforms for lining the individual’s inner eye.
Voice recognition: Voice recognition is referred to as a process that is used to identify
individual’s voice feature ad quality. A voice identification system is relies on the characteristics
those have been created by throat and mouth shapes of speakers.
There are some triggers for that people may feel unwilling to employ approaching
biometric authentication. The details of these triggers are elaborated in the paper:
Budget: It has been analyzed that bio metric detection system is costlier than any other
option. The biometric process and the biometric devices are much costly than any other security
measurement and management technique. With advancement of technology these days’ hackers
have become stringer and easily retrieving data from seven strongly secured servers as well. It
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY
has become responsibility of the company and large organization’s associates to implement the
best suited security approach. It requires many internal applications; software to run thus the
overall cost is higher than any other. Breaking security that are secured through biometric
authentication are still little difficult than PIN code or password breaking. In order to reduce the
security level complexities all companies are required to use biometric authentication in terms of
retina scanning, voice recognition, finger print scanning, iris scanning etc (El Khiyari &
Wechsler, 2016). Thus, before the ultimate implementation of bio metric mechanism location is
needed to be analyzed accurately. However, before implementing such biometric authentication
system the financial and banking institutions needs to understand the purpose.
Accuracy issues: One of the major challenges that obstruct the process of biometric
authentication is accuracy issues. Authorization of exact user is a significant issue with
implementation of bio metric implementation. Due to technical failures sometimes it happens
that the biometric machine fails to identify and scan an appropriate body part. If a specific body
part is not scanned appropriately then accuracy issues may occur. In order to draw accurate
outcomes from the bio metric authentication system accurate scanning is also required. If again
proper security measures are not followed then these data can even be misused by unauthorized
users that will result into bio metric failures.
Failure points: It is acknowledged that, a biometric authentication system generally used
in business organizations are connected with each other. In other word, all the points are
interconnected to each other or input to one segment is dependent on the output generated from
the immediate previous one. Thus, if any one of the process fails to give expected outcome then
the entire process will fail to meet the expected biometric outcome (Berini et al., 2016). If these
challenges occur then the entire presentation of a biometric authentication system would fail to
meet the expected outcomes and it will also interrupt the customer’s id and account details. The
purpose of biometric is reliant on result generated from finger print scanning, iris scanning,
retina scanning of individual person and interruption in the identification can lead the entire
process towards failure.
has become responsibility of the company and large organization’s associates to implement the
best suited security approach. It requires many internal applications; software to run thus the
overall cost is higher than any other. Breaking security that are secured through biometric
authentication are still little difficult than PIN code or password breaking. In order to reduce the
security level complexities all companies are required to use biometric authentication in terms of
retina scanning, voice recognition, finger print scanning, iris scanning etc (El Khiyari &
Wechsler, 2016). Thus, before the ultimate implementation of bio metric mechanism location is
needed to be analyzed accurately. However, before implementing such biometric authentication
system the financial and banking institutions needs to understand the purpose.
Accuracy issues: One of the major challenges that obstruct the process of biometric
authentication is accuracy issues. Authorization of exact user is a significant issue with
implementation of bio metric implementation. Due to technical failures sometimes it happens
that the biometric machine fails to identify and scan an appropriate body part. If a specific body
part is not scanned appropriately then accuracy issues may occur. In order to draw accurate
outcomes from the bio metric authentication system accurate scanning is also required. If again
proper security measures are not followed then these data can even be misused by unauthorized
users that will result into bio metric failures.
Failure points: It is acknowledged that, a biometric authentication system generally used
in business organizations are connected with each other. In other word, all the points are
interconnected to each other or input to one segment is dependent on the output generated from
the immediate previous one. Thus, if any one of the process fails to give expected outcome then
the entire process will fail to meet the expected biometric outcome (Berini et al., 2016). If these
challenges occur then the entire presentation of a biometric authentication system would fail to
meet the expected outcomes and it will also interrupt the customer’s id and account details. The
purpose of biometric is reliant on result generated from finger print scanning, iris scanning,
retina scanning of individual person and interruption in the identification can lead the entire
process towards failure.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
Answer to Question 4
In case of biometric authentication approach it is recognized that, the rate of false
negative and false positive can be successfully tuned based on requirements and in most cases
theses are sometimes much complimentary. Two different types of circumstances are considered
here and elaborated properly.
Case 1:
It has been identified that, in different bio metric authentication mechanisms face
recognition is one of the serious issues that may interrupt the overall biometric authentication
process. In any sort of emergency situation face recognition technique can be used by the
organizations to identify any specific person. After analyzing various emergency situations it has
been determined that if fund is needed in emergency then a person would not be avail that
because this is mainly used for security purposes not for money lending. In other words, it can be
said that if urgent fund is required then that would not be processed through the face recognition
biometric validation process. This is a situation that can be identified as a false positive situation.
If proper approach is not done in the biometric verification process then, different confidential
data such as location, financial data, bank records and even address details can become easily
accessible from the server were data are not stored. Another example that can be used to
demonstrate such situation is also elaborated in the paper. It may possible that personnel and
financial data are stored in more than one database. It will result issues in data redundancy or
data repetition. If same data are stored reputedly in more than one database then in order to
retrieve any single data from the server while query will run die to technical issues wrong data
can be generated and this cannot be recovered by biometric authentication technique. If such
technical issues occur then authority would not be capable to spot the exact person who is needed
to be identified. It can also be said that if identify of any specific person is not known then major
biometric issues will occur.
Case 2:
Answer to Question 4
In case of biometric authentication approach it is recognized that, the rate of false
negative and false positive can be successfully tuned based on requirements and in most cases
theses are sometimes much complimentary. Two different types of circumstances are considered
here and elaborated properly.
Case 1:
It has been identified that, in different bio metric authentication mechanisms face
recognition is one of the serious issues that may interrupt the overall biometric authentication
process. In any sort of emergency situation face recognition technique can be used by the
organizations to identify any specific person. After analyzing various emergency situations it has
been determined that if fund is needed in emergency then a person would not be avail that
because this is mainly used for security purposes not for money lending. In other words, it can be
said that if urgent fund is required then that would not be processed through the face recognition
biometric validation process. This is a situation that can be identified as a false positive situation.
If proper approach is not done in the biometric verification process then, different confidential
data such as location, financial data, bank records and even address details can become easily
accessible from the server were data are not stored. Another example that can be used to
demonstrate such situation is also elaborated in the paper. It may possible that personnel and
financial data are stored in more than one database. It will result issues in data redundancy or
data repetition. If same data are stored reputedly in more than one database then in order to
retrieve any single data from the server while query will run die to technical issues wrong data
can be generated and this cannot be recovered by biometric authentication technique. If such
technical issues occur then authority would not be capable to spot the exact person who is needed
to be identified. It can also be said that if identify of any specific person is not known then major
biometric issues will occur.
Case 2:
8INFORMATION SECURITY
In order to identify false positive situation, this section identifies another case scenario.
This situation demonstrates creation of personnel effecting situation or physically hurting
situation. It is not mandatory that each time all working people in an organization will posses
similar qualities, skills and knowledge. It may possible that some employees are lagging quality
skill and knowledge or even some physical disability. It is identified that there are certain cases
where, physically disable people fails to get support and coordination from the other working
employees of the similar organization. These issues can be categorized as human resource level
issues and cannot be identified with any kind of biometric authentication process such as
fingerprint scanning, iris scanning, and retina scanning etc. In order to manage these difficulties
the Human resource manager needs to take effective action instead of using any bio metric
authentication techniques. Not only this but also, it can interrupt the medical status of working
employees as well. This type of situation can be identified as a false negative situation. This type
of situation is not only harmful for the personnel but also cause harms for complete workplace
activities. It may also happen that, the fingerprint of an employee is used by another employer to
hijack either personnel or financial data from the server without taking permission. If such
technical issues occur then that cannot be identified with biometric authentication mechanism.
Again many mimic artists are also there who can mimic others voice exactly same to same. This
issue cannot be identified with biometric authentication and can be defined as false negative
situation.
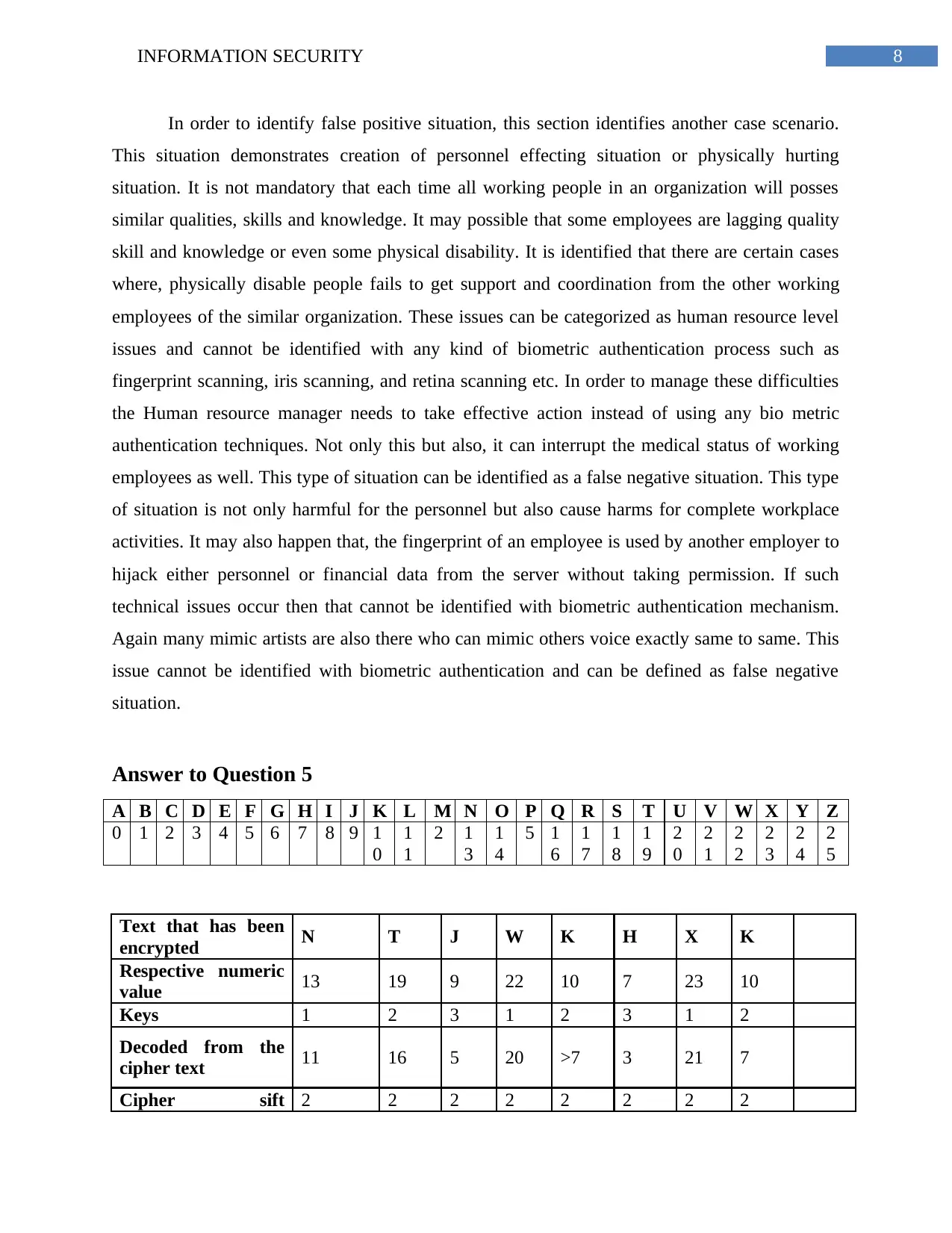
Answer to Question 5
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
0 1 2 3 4 5 6 7 8 9 1
0
1
1
2 1
3
1
4
5 1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
Text that has been
encrypted N T J W K H X K
Respective numeric
value 13 19 9 22 10 7 23 10
Keys 1 2 3 1 2 3 1 2
Decoded from the
cipher text 11 16 5 20 >7 3 21 7
Cipher sift 2 2 2 2 2 2 2 2
In order to identify false positive situation, this section identifies another case scenario.
This situation demonstrates creation of personnel effecting situation or physically hurting
situation. It is not mandatory that each time all working people in an organization will posses
similar qualities, skills and knowledge. It may possible that some employees are lagging quality
skill and knowledge or even some physical disability. It is identified that there are certain cases
where, physically disable people fails to get support and coordination from the other working
employees of the similar organization. These issues can be categorized as human resource level
issues and cannot be identified with any kind of biometric authentication process such as
fingerprint scanning, iris scanning, and retina scanning etc. In order to manage these difficulties
the Human resource manager needs to take effective action instead of using any bio metric
authentication techniques. Not only this but also, it can interrupt the medical status of working
employees as well. This type of situation can be identified as a false negative situation. This type
of situation is not only harmful for the personnel but also cause harms for complete workplace
activities. It may also happen that, the fingerprint of an employee is used by another employer to
hijack either personnel or financial data from the server without taking permission. If such
technical issues occur then that cannot be identified with biometric authentication mechanism.
Again many mimic artists are also there who can mimic others voice exactly same to same. This
issue cannot be identified with biometric authentication and can be defined as false negative
situation.
Answer to Question 5
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
0 1 2 3 4 5 6 7 8 9 1
0
1
1
2 1
3
1
4
5 1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
Text that has been
encrypted N T J W K H X K
Respective numeric
value 13 19 9 22 10 7 23 10
Keys 1 2 3 1 2 3 1 2
Decoded from the
cipher text 11 16 5 20 >7 3 21 7
Cipher sift 2 2 2 2 2 2 2 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9INFORMATION SECURITY
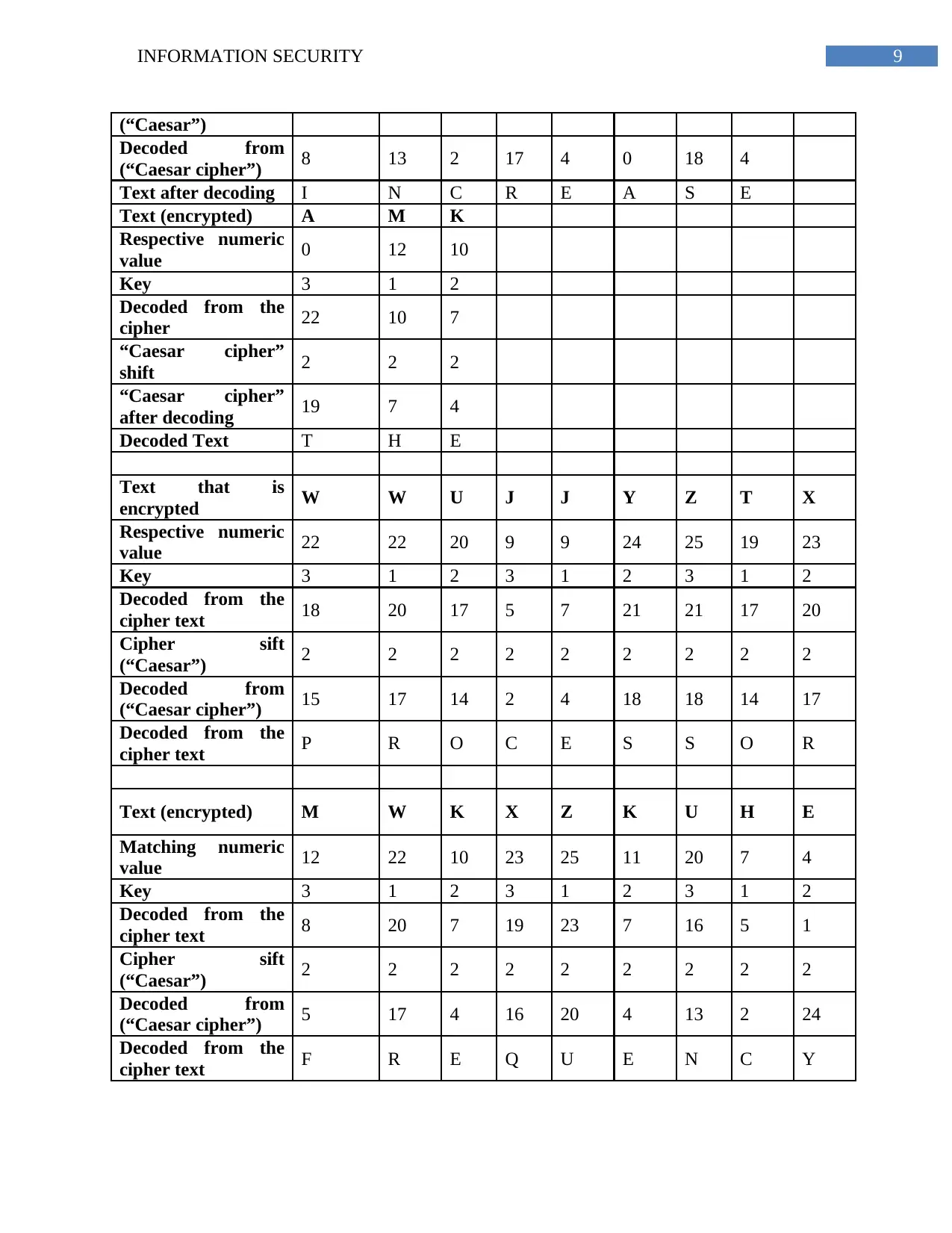
(“Caesar”)
Decoded from
(“Caesar cipher”) 8 13 2 17 4 0 18 4
Text after decoding I N C R E A S E
Text (encrypted) A M K
Respective numeric
value 0 12 10
Key 3 1 2
Decoded from the
cipher 22 10 7
“Caesar cipher”
shift 2 2 2
“Caesar cipher”
after decoding 19 7 4
Decoded Text T H E
Text that is
encrypted W W U J J Y Z T X
Respective numeric
value 22 22 20 9 9 24 25 19 23
Key 3 1 2 3 1 2 3 1 2
Decoded from the
cipher text 18 20 17 5 7 21 21 17 20
Cipher sift
(“Caesar”) 2 2 2 2 2 2 2 2 2
Decoded from
(“Caesar cipher”) 15 17 14 2 4 18 18 14 17
Decoded from the
cipher text P R O C E S S O R
Text (encrypted) M W K X Z K U H E
Matching numeric
value 12 22 10 23 25 11 20 7 4
Key 3 1 2 3 1 2 3 1 2
Decoded from the
cipher text 8 20 7 19 23 7 16 5 1
Cipher sift
(“Caesar”) 2 2 2 2 2 2 2 2 2
Decoded from
(“Caesar cipher”) 5 17 4 16 20 4 13 2 24
Decoded from the
cipher text F R E Q U E N C Y
(“Caesar”)
Decoded from
(“Caesar cipher”) 8 13 2 17 4 0 18 4
Text after decoding I N C R E A S E
Text (encrypted) A M K
Respective numeric
value 0 12 10
Key 3 1 2
Decoded from the
cipher 22 10 7
“Caesar cipher”
shift 2 2 2
“Caesar cipher”
after decoding 19 7 4
Decoded Text T H E
Text that is
encrypted W W U J J Y Z T X
Respective numeric
value 22 22 20 9 9 24 25 19 23
Key 3 1 2 3 1 2 3 1 2
Decoded from the
cipher text 18 20 17 5 7 21 21 17 20
Cipher sift
(“Caesar”) 2 2 2 2 2 2 2 2 2
Decoded from
(“Caesar cipher”) 15 17 14 2 4 18 18 14 17
Decoded from the
cipher text P R O C E S S O R
Text (encrypted) M W K X Z K U H E
Matching numeric
value 12 22 10 23 25 11 20 7 4
Key 3 1 2 3 1 2 3 1 2
Decoded from the
cipher text 8 20 7 19 23 7 16 5 1
Cipher sift
(“Caesar”) 2 2 2 2 2 2 2 2 2
Decoded from
(“Caesar cipher”) 5 17 4 16 20 4 13 2 24
Decoded from the
cipher text F R E Q U E N C Y
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SECURITY

11INFORMATION SECURITY
References
Ajala, O., Aljamea, M., Alzamel, M., Iliopoulos, C., & Strigini, Y. (2016). Fast fingerprint
recognition using circular string pattern matching techniques.
Ali, M. M., Mahale, V. H., Yannawar, P., & Gaikwad, A. T. (2016, March). Overview of
fingerprint recognition system. In 2016 International Conference on Electrical,
Electronics, and Optimization Techniques (ICEEOT) (pp. 1334-1338). IEEE.
Barbello, B. (2016). Continuous user authentication on mobile devices: Recent progress and
remaining challenges.
Berini, D. J., Van Beek, G. A., Arnon, I., Shimek, B. J., Fevens, R. B., & Bell, R. L. (2016). U.S.
Patent No. 9,256,720. Washington, DC: U.S. Patent and Trademark Office.
Best-Rowden, L., & Jain, A. K. (2017). Longitudinal study of automatic face recognition. IEEE
transactions on pattern analysis and machine intelligence, 40(1), 148-162.
Bhagavatula, R., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption.
Biggio, B., Russu, P., Didaci, L., & Roli, F. (2015). Adversarial biometric recognition: A review
on biometric system security from the adversarial machine-learning perspective. IEEE
Signal Processing Magazine, 32(5), 31-41.
Blasco, J., Chen, T. M., Tapiador, J., & Peris-Lopez, P. (2016). A survey of wearable biometric
recognition systems. ACM Computing Surveys (CSUR), 49(3), 43.
El Khiyari, H., & Wechsler, H. (2016). Face recognition across time lapse using convolutional
neural networks. Journal of Information Security, 7(03), 141.
Kasar, M. M., Bhattacharyya, D., & Kim, T. H. (2016). Face recognition using neural network: a
review. International Journal of Security and Its Applications, 10(3), 81-100.
References
Ajala, O., Aljamea, M., Alzamel, M., Iliopoulos, C., & Strigini, Y. (2016). Fast fingerprint
recognition using circular string pattern matching techniques.
Ali, M. M., Mahale, V. H., Yannawar, P., & Gaikwad, A. T. (2016, March). Overview of
fingerprint recognition system. In 2016 International Conference on Electrical,
Electronics, and Optimization Techniques (ICEEOT) (pp. 1334-1338). IEEE.
Barbello, B. (2016). Continuous user authentication on mobile devices: Recent progress and
remaining challenges.
Berini, D. J., Van Beek, G. A., Arnon, I., Shimek, B. J., Fevens, R. B., & Bell, R. L. (2016). U.S.
Patent No. 9,256,720. Washington, DC: U.S. Patent and Trademark Office.
Best-Rowden, L., & Jain, A. K. (2017). Longitudinal study of automatic face recognition. IEEE
transactions on pattern analysis and machine intelligence, 40(1), 148-162.
Bhagavatula, R., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption.
Biggio, B., Russu, P., Didaci, L., & Roli, F. (2015). Adversarial biometric recognition: A review
on biometric system security from the adversarial machine-learning perspective. IEEE
Signal Processing Magazine, 32(5), 31-41.
Blasco, J., Chen, T. M., Tapiador, J., & Peris-Lopez, P. (2016). A survey of wearable biometric
recognition systems. ACM Computing Surveys (CSUR), 49(3), 43.
El Khiyari, H., & Wechsler, H. (2016). Face recognition across time lapse using convolutional
neural networks. Journal of Information Security, 7(03), 141.
Kasar, M. M., Bhattacharyya, D., & Kim, T. H. (2016). Face recognition using neural network: a
review. International Journal of Security and Its Applications, 10(3), 81-100.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



