IT Security Assignment: ATM Security, Biometrics, and Encryption
VerifiedAdded on 2022/10/11
|6
|1257
|31
Homework Assignment
AI Summary
This assignment solution addresses various aspects of IT security, focusing on ATM security, biometric authentication, and encryption methods. It begins by outlining security requirements like confidentiality, integrity, and availability in the context of ATM systems, providing examples of how these principles are applied and the consequences of their compromise. The solution then delves into the security implications of compromised ATM keys, calculating the possible PIN combinations. Further, it explores biometric authentication, discussing its advantages and disadvantages, including cost, points of failure, and accuracy concerns. It also analyzes scenarios where biometric security might fail, such as in emergencies or situations involving physical harm, and the potential for false negatives. Finally, the solution touches upon transposition ciphers as an encryption method.

Running Head: IT 0
Information SECURITY
Information SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT 1
1) Some examples related to requirements of such as system includes –
Confidentiality
The security will be enhanced as only authorised users have the security
password to do any sort of transaction with debit or credit cards.
It is also the accountability of the ultimate user to check whether strong pin is
being set or not.
Whenever the transaction is initiated between the server of bank and ATM, it
is necessary to ensure privacy in relation to concern team of the bank.
In relation with degree of importance, one can state this as compromise to the
privacy of account as to maintain high level of confidentiality, the PIN must
be properly encrypted.
Integrity
To maintain high integrity, it is necessary to implement advanced technology
with timely optimization. This will keep customer information secure.
Degree of importance – Assume that user withdrew $600 from his account and
not only $5400 balance is left in the account. If unintentionally it updates to
$5300 instead of $5400, there will be an unanticipated amount of loss. So,
operation integrity must be secured. For this, a committee can be selected to
whom customer can raise query related to data mismatch in account as of
ATM.
Availability
Customer can require cash at any time. It is necessary to have ATM installed
at various location to offer accessibility benefit to customer. In addition, the
ATM also not should be out of service anytime and maintenance team needs
to ensure frequent check of the system (Mookerjee & Kalipioni, 2010).
Considering degree of availability – The financial growth of bank is also
associated with ATM functionality and availability and therefore, all ATM of
the bank should be functional at least 99.99 %.
1) Some examples related to requirements of such as system includes –
Confidentiality
The security will be enhanced as only authorised users have the security
password to do any sort of transaction with debit or credit cards.
It is also the accountability of the ultimate user to check whether strong pin is
being set or not.
Whenever the transaction is initiated between the server of bank and ATM, it
is necessary to ensure privacy in relation to concern team of the bank.
In relation with degree of importance, one can state this as compromise to the
privacy of account as to maintain high level of confidentiality, the PIN must
be properly encrypted.
Integrity
To maintain high integrity, it is necessary to implement advanced technology
with timely optimization. This will keep customer information secure.
Degree of importance – Assume that user withdrew $600 from his account and
not only $5400 balance is left in the account. If unintentionally it updates to
$5300 instead of $5400, there will be an unanticipated amount of loss. So,
operation integrity must be secured. For this, a committee can be selected to
whom customer can raise query related to data mismatch in account as of
ATM.
Availability
Customer can require cash at any time. It is necessary to have ATM installed
at various location to offer accessibility benefit to customer. In addition, the
ATM also not should be out of service anytime and maintenance team needs
to ensure frequent check of the system (Mookerjee & Kalipioni, 2010).
Considering degree of availability – The financial growth of bank is also
associated with ATM functionality and availability and therefore, all ATM of
the bank should be functional at least 99.99 %.

IT 2
2) In ATM machine, one can observe that there is 0-9 numeric key with support of some
special keys. In relation with given situation in the question, five numeric keys are already
been broken by the thief. Hence, there is a chance of creating ATM combination pin that
should be trailed with the help of available five keys. Bank allows ATM pin to be of only 4
number and this enables thief to enter only those four number between 0000 and 9999 with
repetition be allowed.
nPr = 5P4 = 54 = 625. However, cardholder pin is also considered as 1 likely permutation,
hence 624 will be the maximum integer of pins to be selected.
3) On the base of some similar attributes of human physique, biometrics provides another
level of security to the user. Biometric may be called in future as one of the great authentic
measures to secure the system but it is not fully protected authentication for present time
(Bhattacharyya et al, 2009).
In relation with barriers to biometric authentication, the major three factors include –
Cost Factor – There are known to be as one of the costly authentication formulae to
secure the system as it needs of own servers and hardware for efficient running of the
applications (Li & Hwang, 2010).
Points of Failure – This security system requires lightening and power for its
continuous usage. In addition, some functions in bio-metric needs individual face to
recognise to provide access in the system and any sort of disturbance can result in
entire system failure.
Accuracy – In implementation of biometrics, giving access to correct user is always
be the problem (Venkatraman & Delpachitra, 2008). This results in breakdown of
effective result while accessing the system.
For countering these objections, there is need for some specific measures for each of the
issue. For instance, the cost objection can be controlled by taking assistance from financial
institution so that to implement the system properly. To maintain accuracy, user-friendly
interface needs to be implemented.
4) In case of both the situation -
a) The key functionality uses face recognition in biometric authentication, it would be
treble the safe proprietor in the emergency condition as the proprietor suffers and tend
to develop false negatives when if serious requirement of funds not gets processed
2) In ATM machine, one can observe that there is 0-9 numeric key with support of some
special keys. In relation with given situation in the question, five numeric keys are already
been broken by the thief. Hence, there is a chance of creating ATM combination pin that
should be trailed with the help of available five keys. Bank allows ATM pin to be of only 4
number and this enables thief to enter only those four number between 0000 and 9999 with
repetition be allowed.
nPr = 5P4 = 54 = 625. However, cardholder pin is also considered as 1 likely permutation,
hence 624 will be the maximum integer of pins to be selected.
3) On the base of some similar attributes of human physique, biometrics provides another
level of security to the user. Biometric may be called in future as one of the great authentic
measures to secure the system but it is not fully protected authentication for present time
(Bhattacharyya et al, 2009).
In relation with barriers to biometric authentication, the major three factors include –
Cost Factor – There are known to be as one of the costly authentication formulae to
secure the system as it needs of own servers and hardware for efficient running of the
applications (Li & Hwang, 2010).
Points of Failure – This security system requires lightening and power for its
continuous usage. In addition, some functions in bio-metric needs individual face to
recognise to provide access in the system and any sort of disturbance can result in
entire system failure.
Accuracy – In implementation of biometrics, giving access to correct user is always
be the problem (Venkatraman & Delpachitra, 2008). This results in breakdown of
effective result while accessing the system.
For countering these objections, there is need for some specific measures for each of the
issue. For instance, the cost objection can be controlled by taking assistance from financial
institution so that to implement the system properly. To maintain accuracy, user-friendly
interface needs to be implemented.
4) In case of both the situation -
a) The key functionality uses face recognition in biometric authentication, it would be
treble the safe proprietor in the emergency condition as the proprietor suffers and tend
to develop false negatives when if serious requirement of funds not gets processed
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT 3
appropriately. Sometimes, bio-metric security enables retrieving location information
when in negative kind of situation (Ahmad et al, 2012). With regards to this, person
credentials cannot be retrieved because of technical problem. Therefore, the unknown
identity of person is the first issue that needs to be considered.
b) In scenario associated with giving physical damage to an individual and making
environment near to demise. Workers who are having cardiac arrest not get
considerable support from former co-workers as bio-metric would not identify the
alike. More medical damage to primary employee can be made and this can be called
as playing life of the individual. This situation will be considered as a threat for whole
organisation and thus tends to become false negative. Character loss of a person is the
second issue as there are various numbers of unlawful activities that can be executed
in realization of biometric. Consider about the level of connection, even general
foundation can be closed down and it also take up re-building of wide number of
instructions needed to the particular notion.
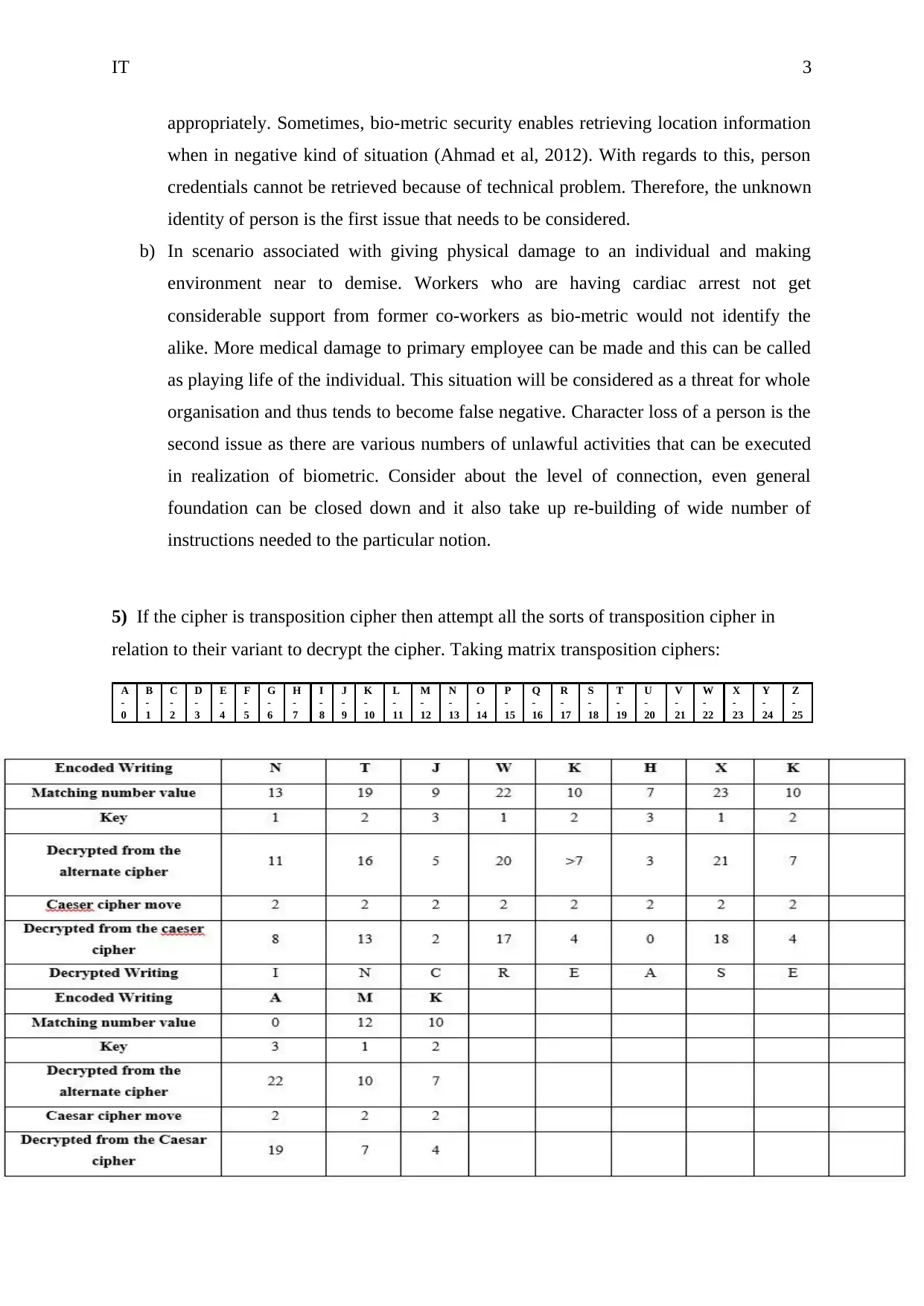
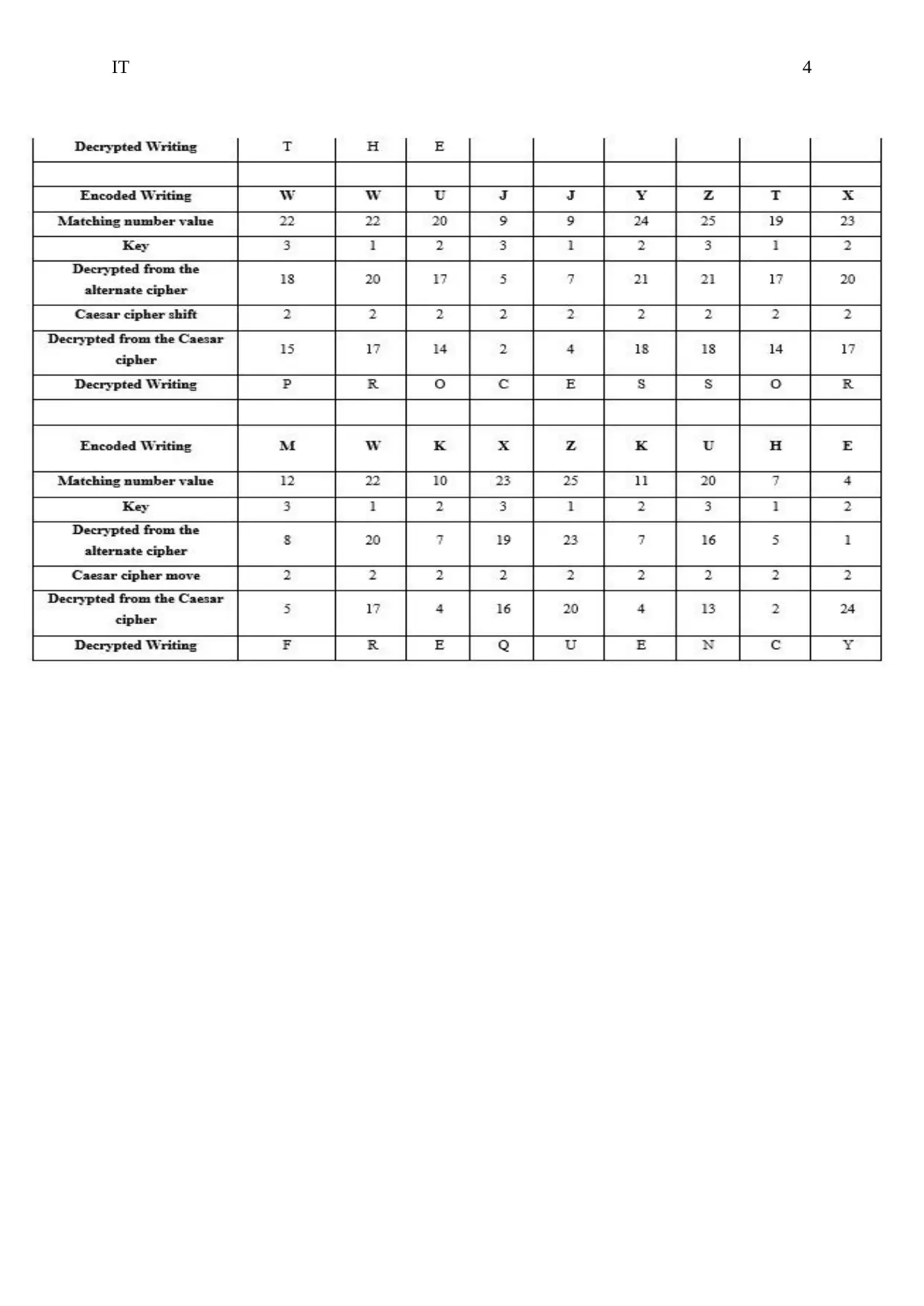
5) If the cipher is transposition cipher then attempt all the sorts of transposition cipher in
relation to their variant to decrypt the cipher. Taking matrix transposition ciphers:
A
-
0
B
-
1
C
-
2
D
-
3
E
-
4
F
-
5
G
-
6
H
-
7
I
-
8
J
-
9
K
-
10
L
-
11
M
-
12
N
-
13
O
-
14
P
-
15
Q
-
16
R
-
17
S
-
18
T
-
19
U
-
20
V
-
21
W
-
22
X
-
23
Y
-
24
Z
-
25
appropriately. Sometimes, bio-metric security enables retrieving location information
when in negative kind of situation (Ahmad et al, 2012). With regards to this, person
credentials cannot be retrieved because of technical problem. Therefore, the unknown
identity of person is the first issue that needs to be considered.
b) In scenario associated with giving physical damage to an individual and making
environment near to demise. Workers who are having cardiac arrest not get
considerable support from former co-workers as bio-metric would not identify the
alike. More medical damage to primary employee can be made and this can be called
as playing life of the individual. This situation will be considered as a threat for whole
organisation and thus tends to become false negative. Character loss of a person is the
second issue as there are various numbers of unlawful activities that can be executed
in realization of biometric. Consider about the level of connection, even general
foundation can be closed down and it also take up re-building of wide number of
instructions needed to the particular notion.
5) If the cipher is transposition cipher then attempt all the sorts of transposition cipher in
relation to their variant to decrypt the cipher. Taking matrix transposition ciphers:
A
-
0
B
-
1
C
-
2
D
-
3
E
-
4
F
-
5
G
-
6
H
-
7
I
-
8
J
-
9
K
-
10
L
-
11
M
-
12
N
-
13
O
-
14
P
-
15
Q
-
16
R
-
17
S
-
18
T
-
19
U
-
20
V
-
21
W
-
22
X
-
23
Y
-
24
Z
-
25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT 4

IT 5
References
Ahmad, S. M. S., Ali, B. M., & Adnan, W. A. W. (2012). Technical issues and challenges of
biometric applications as access control tools of information security. international
journal of innovative computing, information and control, 8(11), 7983-7999.
Bhattacharyya, D., Ranjan, R., Alisherov, F., & Choi, M. (2009). Biometric authentication: A
review. International Journal of u-and e-Service, Science and Technology, 2(3), 13-
28.
Li, C. T., & Hwang, M. S. (2010). An efficient biometrics-based remote user authentication
scheme using smart cards. Journal of Network and computer applications, 33(1), 1-5.
Mookerjee, R., & Kalipioni, P. (2010). Availability of financial services and income
inequality: The evidence from many countries. Emerging Markets Review, 11(4), 404-
408.
Venkatraman, S., & Delpachitra, I. (2008). Biometrics in banking security: a case
study. Information Management & Computer Security, 16(4), 415-430.
References
Ahmad, S. M. S., Ali, B. M., & Adnan, W. A. W. (2012). Technical issues and challenges of
biometric applications as access control tools of information security. international
journal of innovative computing, information and control, 8(11), 7983-7999.
Bhattacharyya, D., Ranjan, R., Alisherov, F., & Choi, M. (2009). Biometric authentication: A
review. International Journal of u-and e-Service, Science and Technology, 2(3), 13-
28.
Li, C. T., & Hwang, M. S. (2010). An efficient biometrics-based remote user authentication
scheme using smart cards. Journal of Network and computer applications, 33(1), 1-5.
Mookerjee, R., & Kalipioni, P. (2010). Availability of financial services and income
inequality: The evidence from many countries. Emerging Markets Review, 11(4), 404-
408.
Venkatraman, S., & Delpachitra, I. (2008). Biometrics in banking security: a case
study. Information Management & Computer Security, 16(4), 415-430.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




