Information Security Assignment: Cryptography, Biometrics, and Ciphers
VerifiedAdded on 2023/01/18
|17
|4456
|84
Homework Assignment
AI Summary
This assignment delves into various aspects of information security, beginning with an exploration of the CIA Triad (Confidentiality, Integrity, and Availability) and its application to Automated Teller Machines (ATMs). It examines the security requirements for ATMs, including encryption of communication channels and PINs. The assignment also analyzes a scenario where a thief attempts to compromise an ATM, calculating the potential number of PIN combinations. Furthermore, it discusses the advantages and disadvantages of biometric authentication, highlighting concerns about data privacy, hacking, and surveillance, while also suggesting ways to mitigate these risks. The assignment then defines and differentiates between false positive and false negative errors. Finally, it presents a cipher problem involving Caesar cipher substitution, another substitution with a key, and a one-time pad encryption, requiring the decryption of a message. The student provides detailed explanations and solutions for each question, demonstrating a comprehensive understanding of the concepts.

Running head: INFORMATION SECURITY
Information Security
Name of Student-
Name of University-
Author’s Note-
Information Security
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Table of Contents
Answer to Question 1:.........................................................................................................1
Answer to Question 2:.........................................................................................................3
Answer to Question 3:.........................................................................................................4
Answer to Question 4:.........................................................................................................5
Answer to Question 5..........................................................................................................6
References............................................................................................................................6
Table of Contents
Answer to Question 1:.........................................................................................................1
Answer to Question 2:.........................................................................................................3
Answer to Question 3:.........................................................................................................4
Answer to Question 4:.........................................................................................................5
Answer to Question 5..........................................................................................................6
References............................................................................................................................6

2INFORMATION SECURITY
The answer to Question 1:
Confidentiality, Authenticity, as well as Integrity, is known as the CIA Triadand those
are known as the most basic concept in the sector of security. The three sides of the CIA Triad is
secured and it very much important to secure a particular item with CIA Triad. The system of
Automated Teller Machine (ATM) in this case stores personal identification of all the numbers
that are confidential with the ATM in both host system as well as in the transmission of the
transaction. The system should protect the integrity of the records of the accounts that are stored
in the system,and they should have an individual transaction. Availability of recorded system is
very important to the well-being of the bank,and it is its responsibility to keep the data safe. The
ATM is less concern about the availability. The three CIA Triadis explained in the following
section below.
Confidentiality: When confidentiality is talked about, the information that is relatedto
the system are to be kept a secret so that no unauthorized user can use the data. Confidentiality
states about protecting all information from being disclosed to any unauthorized parties.
All the information that is related to a system has its value in the recent technology
(Ciuffo & Weiss, 2017). The statements that are related to a bank account, all other personal
information, trade secrets, the governmental documents, as well as a number of credit cards are
the important documents related to an account of the bank,and those are to be kept secret. All
individuals want to keep some information secret,and for that reason, confidentiality is required.
Protecting information is one of the main part related to information security.
The most common component that is used to protect the confidentiality of the
information is the process of encryption. The process of encryption mainly states that
authenticated people access the data at the time and can get information about the data. The
process of encryption is commonly used in most of the technologies nowadays as this process
uses secured protocol to keep the data secure. One of the most important examples of SSL/TLS,
which is a security protocol that is used for communication over the internet which is used as a
conjunction including internet protocols for ensuring security. There are many other ways to
ensure the confidentiality of information that includes enforcing all the file permissions as well
as control list that restricts the access of the sensitive information.
The answer to Question 1:
Confidentiality, Authenticity, as well as Integrity, is known as the CIA Triadand those
are known as the most basic concept in the sector of security. The three sides of the CIA Triad is
secured and it very much important to secure a particular item with CIA Triad. The system of
Automated Teller Machine (ATM) in this case stores personal identification of all the numbers
that are confidential with the ATM in both host system as well as in the transmission of the
transaction. The system should protect the integrity of the records of the accounts that are stored
in the system,and they should have an individual transaction. Availability of recorded system is
very important to the well-being of the bank,and it is its responsibility to keep the data safe. The
ATM is less concern about the availability. The three CIA Triadis explained in the following
section below.
Confidentiality: When confidentiality is talked about, the information that is relatedto
the system are to be kept a secret so that no unauthorized user can use the data. Confidentiality
states about protecting all information from being disclosed to any unauthorized parties.
All the information that is related to a system has its value in the recent technology
(Ciuffo & Weiss, 2017). The statements that are related to a bank account, all other personal
information, trade secrets, the governmental documents, as well as a number of credit cards are
the important documents related to an account of the bank,and those are to be kept secret. All
individuals want to keep some information secret,and for that reason, confidentiality is required.
Protecting information is one of the main part related to information security.
The most common component that is used to protect the confidentiality of the
information is the process of encryption. The process of encryption mainly states that
authenticated people access the data at the time and can get information about the data. The
process of encryption is commonly used in most of the technologies nowadays as this process
uses secured protocol to keep the data secure. One of the most important examples of SSL/TLS,
which is a security protocol that is used for communication over the internet which is used as a
conjunction including internet protocols for ensuring security. There are many other ways to
ensure the confidentiality of information that includes enforcing all the file permissions as well
as control list that restricts the access of the sensitive information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
Integrity: Integrity is the term used for data that states the protection of data to get access
from unauthorized users. Information is only valid if the data has its value and the data that is
being accessed has the original value (Kim et al., 2015). The information that isbeing changedisa
very costly method to get back to get the original data. For example, if a user in an ATM is
sending $10 to some other users, if the information tampers, the amount will change to
$1000,and more money will be deducted from the user.
There is a method of maintaining the data confidentiality that is cryptography. The
cryptography is a process that helps to keep the data integrity of a data. This process ensures that
data integrity is being ensured. Another commonly used method that is used for data integrity is
hashing, that includes comparing the data that is received along with comparing the hash with the
original message that is received. The hash that was in the original message should be
donesecurely.
Availability: The process of availability mainly states that the authorized users of the
data have access to the information when they need the data. Information or data only has value
if the data is accessed by the right people at the right amount of time (Thomas, Vinod &
Robinson, 2017). Denying information access is a common attack that is performed by users in a
highly technological world. There isa DDoS attack that is performed by the users for hampering
the availability of data in the system. The downtime of these particular attack is very costly.
Confidentiality requirements related to ATM are:
The channel of communication that connects the bank and the ATM of the bank should
have encryption process to ensure confidentiality.
The PIN generated in ATM should also be encrypted.
Integrity requirements that are required for an ATM are:
The actions that are performed through ATM are connected to the particular account
connected with the card.
Availability requirements required by ATM:
The ATM system should have the availability to serve at least more than one user at a
time and the ATM should be available 24x7.
Integrity: Integrity is the term used for data that states the protection of data to get access
from unauthorized users. Information is only valid if the data has its value and the data that is
being accessed has the original value (Kim et al., 2015). The information that isbeing changedisa
very costly method to get back to get the original data. For example, if a user in an ATM is
sending $10 to some other users, if the information tampers, the amount will change to
$1000,and more money will be deducted from the user.
There is a method of maintaining the data confidentiality that is cryptography. The
cryptography is a process that helps to keep the data integrity of a data. This process ensures that
data integrity is being ensured. Another commonly used method that is used for data integrity is
hashing, that includes comparing the data that is received along with comparing the hash with the
original message that is received. The hash that was in the original message should be
donesecurely.
Availability: The process of availability mainly states that the authorized users of the
data have access to the information when they need the data. Information or data only has value
if the data is accessed by the right people at the right amount of time (Thomas, Vinod &
Robinson, 2017). Denying information access is a common attack that is performed by users in a
highly technological world. There isa DDoS attack that is performed by the users for hampering
the availability of data in the system. The downtime of these particular attack is very costly.
Confidentiality requirements related to ATM are:
The channel of communication that connects the bank and the ATM of the bank should
have encryption process to ensure confidentiality.
The PIN generated in ATM should also be encrypted.
Integrity requirements that are required for an ATM are:
The actions that are performed through ATM are connected to the particular account
connected with the card.
Availability requirements required by ATM:
The ATM system should have the availability to serve at least more than one user at a
time and the ATM should be available 24x7.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
Answer to Question 2:
In the case explained, a thief has broken in an ATM and has jammed the card reader
using a screwdriver. The thief was able to break five keys in the keypad of the ATM. The thief
was working on when a customer came to the ATM to withdraw money. The customer was able
to withdraw money from the ATM but was not able to take out the ATM card from the ATM as
the thief jammed the card reader. After trying for some time, the customer went out to seek help
from others, meanwhile, the thief got a chance to withdraw some money from the ATM. As the
customer was able to draw money from the ATM, the thief understood that the four-digit pin of
the card was excluding the five keys he broke in the keypad of the ATM.
The thief was left out with five more keys from which four-digit ATM pin was to be
found out. Mathematically, a possible number of times that the thief was able to generate the
ATM pin was:
5!/ (5-4)! = (5 * 4 * 3 * 2 * 1)/ 1 = 120 four-digit pins.
But for the security concerns, the banks have secured the ATM system by limiting the
wrong generation of pin three times. The thief was able to input the pin three times as per the
regulations of banks. If the thief had the opportunity to input the unlimited pin time, the thief
would have 120 chances to find out the pin. The three times that the thief will be able to input the
pin, if the pin coincidently matches the customer pin, the thief will be able to withdraw cash
from the customer’s account number. And if the thief was not able to get the pin, after three trials
the card would get blocked and would be unblocked only after 24 hours.
Answer to Question 3:
Answer to Question 2:
In the case explained, a thief has broken in an ATM and has jammed the card reader
using a screwdriver. The thief was able to break five keys in the keypad of the ATM. The thief
was working on when a customer came to the ATM to withdraw money. The customer was able
to withdraw money from the ATM but was not able to take out the ATM card from the ATM as
the thief jammed the card reader. After trying for some time, the customer went out to seek help
from others, meanwhile, the thief got a chance to withdraw some money from the ATM. As the
customer was able to draw money from the ATM, the thief understood that the four-digit pin of
the card was excluding the five keys he broke in the keypad of the ATM.
The thief was left out with five more keys from which four-digit ATM pin was to be
found out. Mathematically, a possible number of times that the thief was able to generate the
ATM pin was:
5!/ (5-4)! = (5 * 4 * 3 * 2 * 1)/ 1 = 120 four-digit pins.
But for the security concerns, the banks have secured the ATM system by limiting the
wrong generation of pin three times. The thief was able to input the pin three times as per the
regulations of banks. If the thief had the opportunity to input the unlimited pin time, the thief
would have 120 chances to find out the pin. The three times that the thief will be able to input the
pin, if the pin coincidently matches the customer pin, the thief will be able to withdraw cash
from the customer’s account number. And if the thief was not able to get the pin, after three trials
the card would get blocked and would be unblocked only after 24 hours.
Answer to Question 3:

5INFORMATION SECURITY
Along with the benefits that are provided by biometric authentication, there are some
disadvantages that the process of biometric addresses. The three major issues that are facedby
using biometric security are stated below:
1. Data in Biometrics are not private: The security of biometrics is just on the surface.
Biometrics stores the data of human fingerprint, ears, as well as data of eyes. But the biometric is
not more secure than of using passwords. Passwords are more secure compared to
biometrics.Passwords are only known by the users,and no other can access the password that a
system has. The passwords can only be acquired by the brute force attacks or by phishing
methods. But hackers usually cannot access the password. The data stored in biometrics are
comparatively public.
In biometrics, the image of users fingerprint, face and eyes are stored in many places that
a user can imagine. For example, Facebook recognizes the face and all the stores and building
that captures video stores the data of the user identification in their database so that the user can
be identified (Memon et al., 2017). There are almost 48 states where the software can be
identified by using the images the users without the consent of the users. The law enforcement
agencies also have the authority to store an image of any user without the consent of the user.
The problem that lies in biometric is to identify the security and the management that is
associated with a user. PII commonly known as Personal Identifiable Information is to have
access control in the places for protecting identity theft. The hackers can breach the database so
that they can leak or steal the biometric identification.
2. Biometrics can be hacked: The ID theft is one of the most stressful as well as
worrying things that can happen with data. The users find many difficulties to prove that their
identity is stolen and the rate of ID theft is increasing day by day (Kimet al., 2015). Hacking is
the biggest obstacle that helps in ID identification. This is because if the credentials are exposed,
any hackers can use the information and pretend to be the user.
The biometric data that are used for identification will have the same data everywhere.
The only way that can be used for preventing the unwanted access of data might be changing the
authentication method in the system. If the biometric data we hacked on a large scale, it would
be difficult for the users to verify their own identity, particularly at the time of data linking.
Along with the benefits that are provided by biometric authentication, there are some
disadvantages that the process of biometric addresses. The three major issues that are facedby
using biometric security are stated below:
1. Data in Biometrics are not private: The security of biometrics is just on the surface.
Biometrics stores the data of human fingerprint, ears, as well as data of eyes. But the biometric is
not more secure than of using passwords. Passwords are more secure compared to
biometrics.Passwords are only known by the users,and no other can access the password that a
system has. The passwords can only be acquired by the brute force attacks or by phishing
methods. But hackers usually cannot access the password. The data stored in biometrics are
comparatively public.
In biometrics, the image of users fingerprint, face and eyes are stored in many places that
a user can imagine. For example, Facebook recognizes the face and all the stores and building
that captures video stores the data of the user identification in their database so that the user can
be identified (Memon et al., 2017). There are almost 48 states where the software can be
identified by using the images the users without the consent of the users. The law enforcement
agencies also have the authority to store an image of any user without the consent of the user.
The problem that lies in biometric is to identify the security and the management that is
associated with a user. PII commonly known as Personal Identifiable Information is to have
access control in the places for protecting identity theft. The hackers can breach the database so
that they can leak or steal the biometric identification.
2. Biometrics can be hacked: The ID theft is one of the most stressful as well as
worrying things that can happen with data. The users find many difficulties to prove that their
identity is stolen and the rate of ID theft is increasing day by day (Kimet al., 2015). Hacking is
the biggest obstacle that helps in ID identification. This is because if the credentials are exposed,
any hackers can use the information and pretend to be the user.
The biometric data that are used for identification will have the same data everywhere.
The only way that can be used for preventing the unwanted access of data might be changing the
authentication method in the system. If the biometric data we hacked on a large scale, it would
be difficult for the users to verify their own identity, particularly at the time of data linking.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY
3. Surveillance fear: The biggest use of biometric identification with advanced
technology is law enforcement. The facial recognition of biometric has become one of the most
common practices that proactive policing, that is used by police for comparing with the database
of the criminals. Facial recognition is one of the best methods for biometric authentication.
Facial recognition is also used for keeping surveillance for protecting the country against
terrorism.
Overcoming the Biometric Risks: The risks that are relatedto the biometrics are to be
overcome by the user who uses biometric. The ways that can be solved are stated below:
User Experience: The biggest challenge that a company faces is implementing biometric
authentication to the user experience that is easy to understand. The biometric authentication is
easy to implement as easy to use. Biometric authentication requires intuitive interface as well as
a biometric that user finds to use with comfort. The most common biometric that is used in most
of the companies are voice biometric (Ghosh et al., 2017). This is the most common biometric
that gives access to when the user speaks. This the least secured biometric authentication. Retina
scanning is another biometric that are used in many companies and the equipment for retina
scanning is an expensive one but gives most accurate data. The first way to mitigate them is by
selecting the way of biometric that is best for the work.
Spoofing Attacks: The spoofing attacks includes the processes that mimic someone else’s
biometric. This might include copying the fingerprints of the users so that they can fool the
biometric sensor (Luca et al., 2015). Spoofing is one of the most serious problems that the user
faces. This spoofing attackoccurs because of old systems used for authentication. The old
biometrics systems get fooled easily by hackers. According to the study, the fingerprint of the
mobile phone can be spoofed by hackers easily within 15 minutes.
To avoid this, there can be multi-factor authentication in the system. This includes
identifying different identifiers for increasing the security level of the system. This decreases the
risk level within the system. There can be both voice recognition as well as facial recognition
along with biometric verification in the system.
The answer to Question 4:
3. Surveillance fear: The biggest use of biometric identification with advanced
technology is law enforcement. The facial recognition of biometric has become one of the most
common practices that proactive policing, that is used by police for comparing with the database
of the criminals. Facial recognition is one of the best methods for biometric authentication.
Facial recognition is also used for keeping surveillance for protecting the country against
terrorism.
Overcoming the Biometric Risks: The risks that are relatedto the biometrics are to be
overcome by the user who uses biometric. The ways that can be solved are stated below:
User Experience: The biggest challenge that a company faces is implementing biometric
authentication to the user experience that is easy to understand. The biometric authentication is
easy to implement as easy to use. Biometric authentication requires intuitive interface as well as
a biometric that user finds to use with comfort. The most common biometric that is used in most
of the companies are voice biometric (Ghosh et al., 2017). This is the most common biometric
that gives access to when the user speaks. This the least secured biometric authentication. Retina
scanning is another biometric that are used in many companies and the equipment for retina
scanning is an expensive one but gives most accurate data. The first way to mitigate them is by
selecting the way of biometric that is best for the work.
Spoofing Attacks: The spoofing attacks includes the processes that mimic someone else’s
biometric. This might include copying the fingerprints of the users so that they can fool the
biometric sensor (Luca et al., 2015). Spoofing is one of the most serious problems that the user
faces. This spoofing attackoccurs because of old systems used for authentication. The old
biometrics systems get fooled easily by hackers. According to the study, the fingerprint of the
mobile phone can be spoofed by hackers easily within 15 minutes.
To avoid this, there can be multi-factor authentication in the system. This includes
identifying different identifiers for increasing the security level of the system. This decreases the
risk level within the system. There can be both voice recognition as well as facial recognition
along with biometric verification in the system.
The answer to Question 4:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
False positive is commonly known as Type 1 Error and happen when a user rejects a null
hypothesis that is true. False negative is type 2 error where the user accepts a null hypothesis that
is false.
The most appropriate way is forming a null hypothesis in such a way that makes the user
reject it. False positive can be explained by considering an example of medicine (Ciuffo &
Weiss, 2017). The testing that is carried out in the medical sector mainly determines if there is a
disease or any type of illness in the body. If some errors are found, the result of the test would be
positive,and if the test results do not show anything, the test results are negative. This same
conditionis applied for software testing also.
When the test case fails, there is false positive but there is no bug,and the system or
software is working perfectly. False negative occurs when the test results are passed but there are
some bugs in the software,or the system and the software is not functioning properly.
Both false positive and false negative are an annoyance,and false negative is the most
damaging one compared to false positive. False negative creates a false result of security. False
positive consumes a lot of energy as well as the time of tester (Chen, Pande & Mohapatra, 2014)
whereas false negative ensures to keep the bug in the system and software for some intermediate
time. Both of them increases the cost of the testing wherein false negative result in having more
cost and involves jeopardizingcustomer retention as the software is open to vulnerabilities.
False positive is a testing hypothesis that gives a positive result for a particular test,but
the expected result is to get a negative result. This is sometimes called a false alarm or an error
for false positive. Thisis used in the medical sector and software testing centres. Some of the
examples of false positive cases are:
Sometimes a pregnancy test shows a positive result,but the result is negative.
Test for cancer screening is positive,but the patient does not have the disease.
The anti-virus software in the computer sometimes identifies harmless programs as
harmful software.
Sometimes false positives can become worried mainly in the testing results. The researchers
are under research trying to identify the reasons for the false positive to make the test result
more positive.
False positive is commonly known as Type 1 Error and happen when a user rejects a null
hypothesis that is true. False negative is type 2 error where the user accepts a null hypothesis that
is false.
The most appropriate way is forming a null hypothesis in such a way that makes the user
reject it. False positive can be explained by considering an example of medicine (Ciuffo &
Weiss, 2017). The testing that is carried out in the medical sector mainly determines if there is a
disease or any type of illness in the body. If some errors are found, the result of the test would be
positive,and if the test results do not show anything, the test results are negative. This same
conditionis applied for software testing also.
When the test case fails, there is false positive but there is no bug,and the system or
software is working perfectly. False negative occurs when the test results are passed but there are
some bugs in the software,or the system and the software is not functioning properly.
Both false positive and false negative are an annoyance,and false negative is the most
damaging one compared to false positive. False negative creates a false result of security. False
positive consumes a lot of energy as well as the time of tester (Chen, Pande & Mohapatra, 2014)
whereas false negative ensures to keep the bug in the system and software for some intermediate
time. Both of them increases the cost of the testing wherein false negative result in having more
cost and involves jeopardizingcustomer retention as the software is open to vulnerabilities.
False positive is a testing hypothesis that gives a positive result for a particular test,but
the expected result is to get a negative result. This is sometimes called a false alarm or an error
for false positive. Thisis used in the medical sector and software testing centres. Some of the
examples of false positive cases are:
Sometimes a pregnancy test shows a positive result,but the result is negative.
Test for cancer screening is positive,but the patient does not have the disease.
The anti-virus software in the computer sometimes identifies harmless programs as
harmful software.
Sometimes false positives can become worried mainly in the testing results. The researchers
are under research trying to identify the reasons for the false positive to make the test result
more positive.

8INFORMATION SECURITY
Example one:
The tests done in medicals sectors can be malfunctioned,and that results in a false
positive. A false positive case may show a positive result for a woman to be pregnant when she
is not pregnant. This case occurs frequently. In this sector,a false negative is more to happen
instead of false positive. False positive occurs when the woman is pregnant,and the results show
negative indicating the woman not to be negative.
This can be tremendous to a couple who expects a child for a longer time. Of false
positive occurs, the couple would think that as a miracle and be happy to the most (Bhagavatula
et al., 2015). With false positive results, the people get ready themselves for a baby,and after
some short period, when they get to know about their false positive test, they will be broken in to
parts.
This might acts contradictory for false negative also. A couple who does not expects a
baby get a negative result in the pregnancy test and they are not ready for that. The lady is
pregnant but is not aware of her pregnancy and continues to take drug and drink. This might be
harmful to her family as well as her baby.
But the results of a pregnancy test have been advanced,and that has minimized the
chances of getting a false negative result. There is an improvement in the test results,and the
couple is expected to go for a doctor and confirm their pregnancy.
Example two:
The next example is the test that shows the false positive result for the Aids test. The
result that can come from a false positive of a patient of having AID must be a heartbreaking one
(Barbosa & Silva, 2015). The patient needs to deals with the trauma of having AIDS and that he
has to face his family and friends. When after crossing checking and testing the second time, the
patient might find that he or she does not have the virus.
Contradictory, when there is the false negative result, the tests show that the infected
person has HIV positive,but he is unaware of the fact that he has the virus. This can be more
dangerous. The patients having HIV positive virus might miss out treatments,and that would
Example one:
The tests done in medicals sectors can be malfunctioned,and that results in a false
positive. A false positive case may show a positive result for a woman to be pregnant when she
is not pregnant. This case occurs frequently. In this sector,a false negative is more to happen
instead of false positive. False positive occurs when the woman is pregnant,and the results show
negative indicating the woman not to be negative.
This can be tremendous to a couple who expects a child for a longer time. Of false
positive occurs, the couple would think that as a miracle and be happy to the most (Bhagavatula
et al., 2015). With false positive results, the people get ready themselves for a baby,and after
some short period, when they get to know about their false positive test, they will be broken in to
parts.
This might acts contradictory for false negative also. A couple who does not expects a
baby get a negative result in the pregnancy test and they are not ready for that. The lady is
pregnant but is not aware of her pregnancy and continues to take drug and drink. This might be
harmful to her family as well as her baby.
But the results of a pregnancy test have been advanced,and that has minimized the
chances of getting a false negative result. There is an improvement in the test results,and the
couple is expected to go for a doctor and confirm their pregnancy.
Example two:
The next example is the test that shows the false positive result for the Aids test. The
result that can come from a false positive of a patient of having AID must be a heartbreaking one
(Barbosa & Silva, 2015). The patient needs to deals with the trauma of having AIDS and that he
has to face his family and friends. When after crossing checking and testing the second time, the
patient might find that he or she does not have the virus.
Contradictory, when there is the false negative result, the tests show that the infected
person has HIV positive,but he is unaware of the fact that he has the virus. This can be more
dangerous. The patients having HIV positive virus might miss out treatments,and that would
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY
result in spreading out the virus to others as well. The false negative, in this case, can also be a
big problem for that particular person as well as society.
Many researchers and doctors specify the AID as reactive instead of specifying them a
positive virus. There are many series of tests that are to be carried out before confirming the
patient having HIV positive as a single test might result in a false negative.
The answer to Question 5
Transportation cypher is a process that rearranges the order of letters that are in cypher
test that is the encoded test (Alsaadi, 2015). Thisis generally done according to some of the
predefined methods or substitution methods used for encrypting the code or decrypting the code.
There are many different classes of algorithms that help an encoder to encode or decode a
text. Each of the methods is used to jumble up the characters of plain text. The algorithms of
transposition ciphertexts are as follows:
The transposition cyphers mainly involve the permuting the position of the characters of
the texts but leaves an identity of the characters that are unchanged. Examples are
columnar transposition or railfence algorithm.
Mono-alphabetic cypher substitution is a method where each of the lettersis replaced by
some other letter. Examples areCaesar cypher, substitution method, Baconian cypher,
Polybius cypher and many more.
Poly-alphabetic cyphersuse the concept of using different alphabets that are generally
used to encipher the characters depending on the position of the letters. Examples are
Autokey, Running cypher key, enigma, porta cypher, and Gronsfeld.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
result in spreading out the virus to others as well. The false negative, in this case, can also be a
big problem for that particular person as well as society.
Many researchers and doctors specify the AID as reactive instead of specifying them a
positive virus. There are many series of tests that are to be carried out before confirming the
patient having HIV positive as a single test might result in a false negative.
The answer to Question 5
Transportation cypher is a process that rearranges the order of letters that are in cypher
test that is the encoded test (Alsaadi, 2015). Thisis generally done according to some of the
predefined methods or substitution methods used for encrypting the code or decrypting the code.
There are many different classes of algorithms that help an encoder to encode or decode a
text. Each of the methods is used to jumble up the characters of plain text. The algorithms of
transposition ciphertexts are as follows:
The transposition cyphers mainly involve the permuting the position of the characters of
the texts but leaves an identity of the characters that are unchanged. Examples are
columnar transposition or railfence algorithm.
Mono-alphabetic cypher substitution is a method where each of the lettersis replaced by
some other letter. Examples areCaesar cypher, substitution method, Baconian cypher,
Polybius cypher and many more.
Poly-alphabetic cyphersuse the concept of using different alphabets that are generally
used to encipher the characters depending on the position of the letters. Examples are
Autokey, Running cypher key, enigma, porta cypher, and Gronsfeld.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
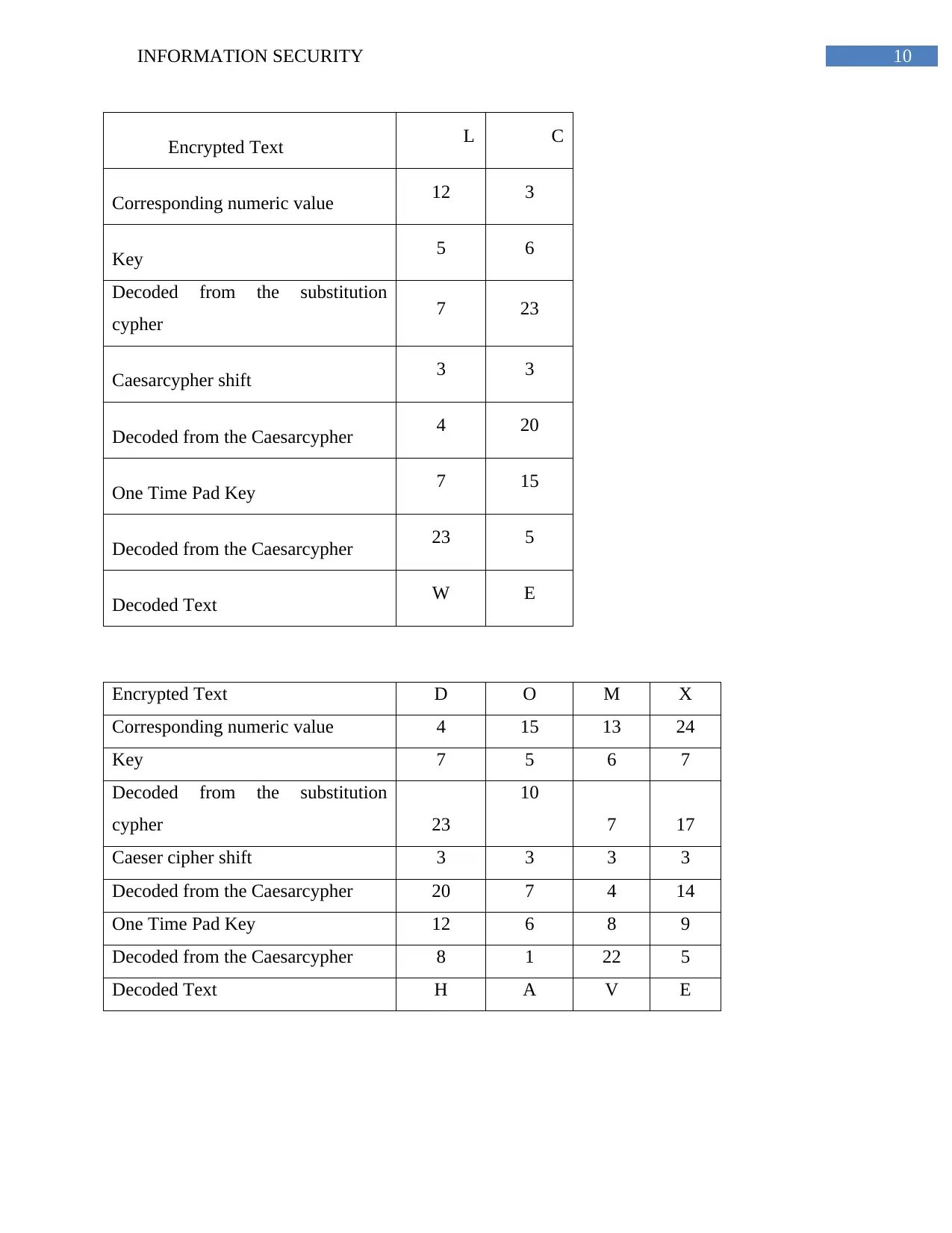
10INFORMATION SECURITY
Encrypted Text L C
Corresponding numeric value 12 3
Key 5 6
Decoded from the substitution
cypher 7 23
Caesarcypher shift 3 3
Decoded from the Caesarcypher 4 20
One Time Pad Key 7 15
Decoded from the Caesarcypher 23 5
Decoded Text W E
Encrypted Text D O M X
Corresponding numeric value 4 15 13 24
Key 7 5 6 7
Decoded from the substitution
cypher 23
10
7 17
Caeser cipher shift 3 3 3 3
Decoded from the Caesarcypher 20 7 4 14
One Time Pad Key 12 6 8 9
Decoded from the Caesarcypher 8 1 22 5
Decoded Text H A V E
Encrypted Text L C
Corresponding numeric value 12 3
Key 5 6
Decoded from the substitution
cypher 7 23
Caesarcypher shift 3 3
Decoded from the Caesarcypher 4 20
One Time Pad Key 7 15
Decoded from the Caesarcypher 23 5
Decoded Text W E
Encrypted Text D O M X
Corresponding numeric value 4 15 13 24
Key 7 5 6 7
Decoded from the substitution
cypher 23
10
7 17
Caeser cipher shift 3 3 3 3
Decoded from the Caesarcypher 20 7 4 14
One Time Pad Key 12 6 8 9
Decoded from the Caesarcypher 8 1 22 5
Decoded Text H A V E
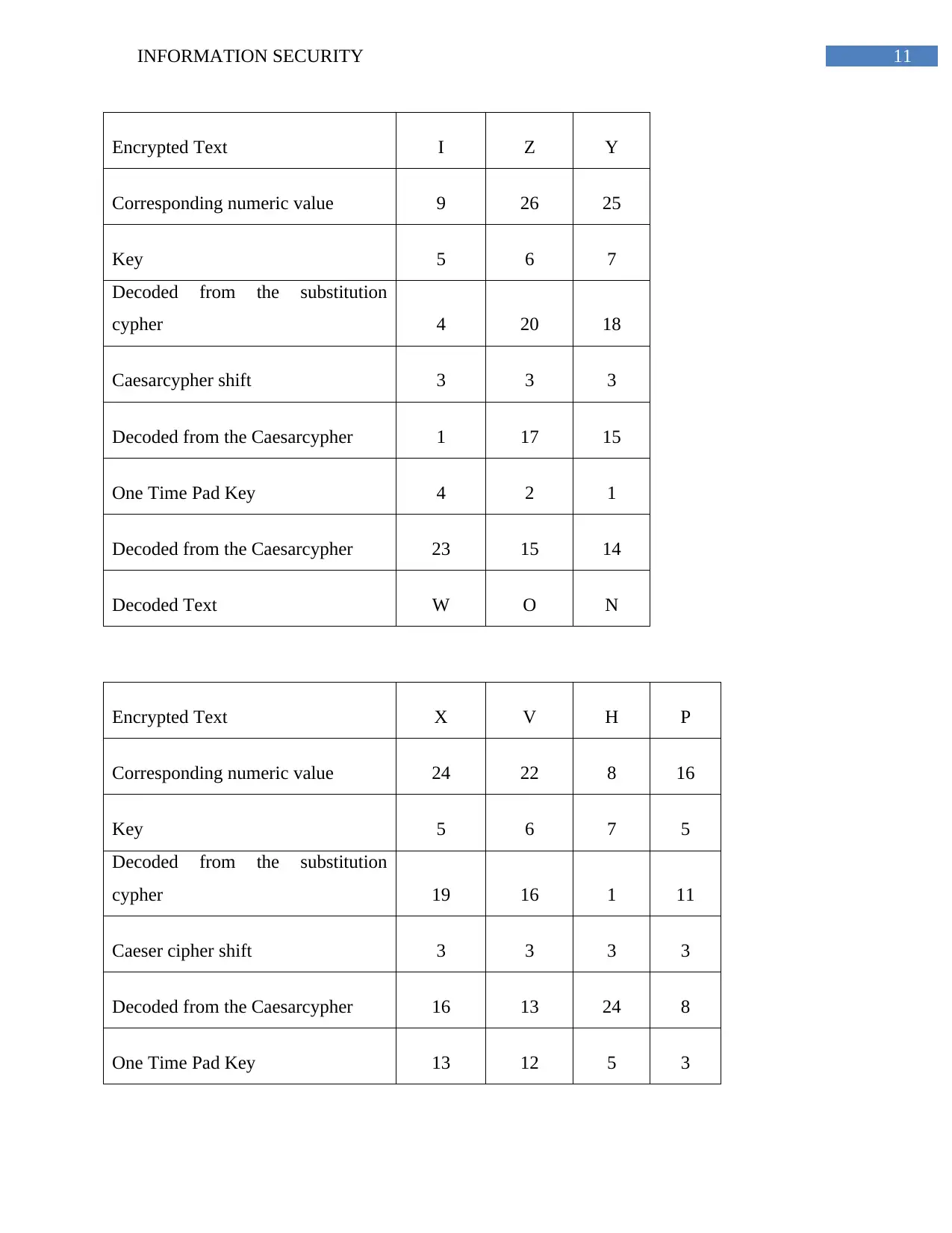
11INFORMATION SECURITY
Encrypted Text I Z Y
Corresponding numeric value 9 26 25
Key 5 6 7
Decoded from the substitution
cypher 4 20 18
Caesarcypher shift 3 3 3
Decoded from the Caesarcypher 1 17 15
One Time Pad Key 4 2 1
Decoded from the Caesarcypher 23 15 14
Decoded Text W O N
Encrypted Text X V H P
Corresponding numeric value 24 22 8 16
Key 5 6 7 5
Decoded from the substitution
cypher 19 16 1 11
Caeser cipher shift 3 3 3 3
Decoded from the Caesarcypher 16 13 24 8
One Time Pad Key 13 12 5 3
Encrypted Text I Z Y
Corresponding numeric value 9 26 25
Key 5 6 7
Decoded from the substitution
cypher 4 20 18
Caesarcypher shift 3 3 3
Decoded from the Caesarcypher 1 17 15
One Time Pad Key 4 2 1
Decoded from the Caesarcypher 23 15 14
Decoded Text W O N
Encrypted Text X V H P
Corresponding numeric value 24 22 8 16
Key 5 6 7 5
Decoded from the substitution
cypher 19 16 1 11
Caeser cipher shift 3 3 3 3
Decoded from the Caesarcypher 16 13 24 8
One Time Pad Key 13 12 5 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




