Network Security: Assurance, Vulnerabilities, and Packet Analysis
VerifiedAdded on 2023/01/18
|28
|3012
|28
Report
AI Summary
This report identifies and assesses the security requirements of a company's ICT infrastructure, analyzing the network environment to propose adequate security solutions. It covers tracing options, acceptable traces, and Wireshark configuration. The report delves into administrative network management systems, IP network security algorithms, cryptography, encapsulation, encryption, enterprise security solutions, firewalls, network topologies, routing theories, system threats, and transaction protocols. Practical demonstrations include analyzing packets from HTTP, HTTPS, trace route, FTP, and POP3 traces, along with penetration testing. The report concludes with key observations and findings, providing a comprehensive overview of network security assurance.

Running head: INFORMATION SECURITY ASSURANCE
Information Security Assurance
Name of the Student
Name of the University
Author Note
Information Security Assurance
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY ASSURANCE
Summary
The purpose of this report is to identify and assess the security requirements of the
information communication technology (ICT) of a company and analyse the environment to
suggest adequate security solutions as also generate a report based on conducting traces on
the network. First the report identifies the tracing options, mentions the acceptable traces
talks about configuring Wireshark. Then the report discusses the network environment and
security needs of the company by talking about network management systems, network
security algorithms, purpose of cryptography, encapsulation and encryption, enterprise
security solutions, firewalls network topologies, routing theories, possible system threats and
transaction protocols. Then the report proceeds to the practical demonstration comprising
analysis of the packets of the various traces after which the report ends with concluding
notes.
INFORMATION SECURITY ASSURANCE
Summary
The purpose of this report is to identify and assess the security requirements of the
information communication technology (ICT) of a company and analyse the environment to
suggest adequate security solutions as also generate a report based on conducting traces on
the network. First the report identifies the tracing options, mentions the acceptable traces
talks about configuring Wireshark. Then the report discusses the network environment and
security needs of the company by talking about network management systems, network
security algorithms, purpose of cryptography, encapsulation and encryption, enterprise
security solutions, firewalls network topologies, routing theories, possible system threats and
transaction protocols. Then the report proceeds to the practical demonstration comprising
analysis of the packets of the various traces after which the report ends with concluding
notes.

2
INFORMATION SECURITY ASSURANCE
Table of Contents
Introduction................................................................................................................................4
Part A: Consultation...................................................................................................................4
Tracing Option.......................................................................................................................4
Acceptable Traces..................................................................................................................4
Wireshark Configuration........................................................................................................5
Part B: Research, Analysis and Reporting of Technical Information........................................5
Administrative Network Management System......................................................................5
Algorithms in IP network security.........................................................................................6
Purpose of cryptography in security systems.........................................................................6
Encapsulation and Encryption in Data Transmission............................................................7
Example of Enterprise solutions............................................................................................7
Firewall and Security Solutions.............................................................................................7
Common Network Topologies...............................................................................................7
Operations Network Management Systems...........................................................................8
Routing Theory......................................................................................................................8
System Threats.......................................................................................................................9
Transaction Protocols.............................................................................................................9
Part C: Analysing Packets..........................................................................................................9
HTTP Trace............................................................................................................................9
HTTPS Trace.......................................................................................................................12
Trace Route..........................................................................................................................17
INFORMATION SECURITY ASSURANCE
Table of Contents
Introduction................................................................................................................................4
Part A: Consultation...................................................................................................................4
Tracing Option.......................................................................................................................4
Acceptable Traces..................................................................................................................4
Wireshark Configuration........................................................................................................5
Part B: Research, Analysis and Reporting of Technical Information........................................5
Administrative Network Management System......................................................................5
Algorithms in IP network security.........................................................................................6
Purpose of cryptography in security systems.........................................................................6
Encapsulation and Encryption in Data Transmission............................................................7
Example of Enterprise solutions............................................................................................7
Firewall and Security Solutions.............................................................................................7
Common Network Topologies...............................................................................................7
Operations Network Management Systems...........................................................................8
Routing Theory......................................................................................................................8
System Threats.......................................................................................................................9
Transaction Protocols.............................................................................................................9
Part C: Analysing Packets..........................................................................................................9
HTTP Trace............................................................................................................................9
HTTPS Trace.......................................................................................................................12
Trace Route..........................................................................................................................17
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY ASSURANCE
FTP Trace.............................................................................................................................18
POP3 Trace..........................................................................................................................21
Penetration Testing...............................................................................................................24
Conclusion................................................................................................................................25
Bibliography.............................................................................................................................27
INFORMATION SECURITY ASSURANCE
FTP Trace.............................................................................................................................18
POP3 Trace..........................................................................................................................21
Penetration Testing...............................................................................................................24
Conclusion................................................................................................................................25
Bibliography.............................................................................................................................27
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY ASSURANCE
Introduction
The following report identifies and assesses the network security requirements of the
information communication technology or ICT of a company and analyses the network
environment in order to suggest adequate security solutions as also generate a report based on
conducting traces on the network. The report begins by identifying the tracing options,
mentions the acceptable traces and talks about configuring Wireshark. Then the report
discusses the network environment and security needs of the company by talking about
network management systems, network security algorithms, purpose of cryptography,
encapsulation and encryption, enterprise security solutions, firewalls network topologies,
routing theories, possible system threats and transaction protocols. Then the report moves
into the practical demonstration part comprising analysis of the packets of the various traces
after which the report ends with observations in concluding notes.
Part A: Consultation
Tracing Option
For performing the various types of traces, the free to use open source protocol
analyser software application called Wireshark is being used. This is because Wireshark is a
very powerful protocol analyser tool that can be used to perform and analyse all kinds of
traces be it HTTPS, FTP, trace route, POP3 trace, or trace of attacks on the network. It lists
the communication packets of all kinds of protocols and offers a segmented and organized
view of the respective details in different parts like IP (Internet Protocol), ICMP (Internet
Control Message Protocol), Frame and Ethernet.
Acceptable Traces
The acceptable traces for the project is found to be gameaddicts.net for the HTTP
trace. This is because the chosen site does not have a SSL certificate. The websites regularly
INFORMATION SECURITY ASSURANCE
Introduction
The following report identifies and assesses the network security requirements of the
information communication technology or ICT of a company and analyses the network
environment in order to suggest adequate security solutions as also generate a report based on
conducting traces on the network. The report begins by identifying the tracing options,
mentions the acceptable traces and talks about configuring Wireshark. Then the report
discusses the network environment and security needs of the company by talking about
network management systems, network security algorithms, purpose of cryptography,
encapsulation and encryption, enterprise security solutions, firewalls network topologies,
routing theories, possible system threats and transaction protocols. Then the report moves
into the practical demonstration part comprising analysis of the packets of the various traces
after which the report ends with observations in concluding notes.
Part A: Consultation
Tracing Option
For performing the various types of traces, the free to use open source protocol
analyser software application called Wireshark is being used. This is because Wireshark is a
very powerful protocol analyser tool that can be used to perform and analyse all kinds of
traces be it HTTPS, FTP, trace route, POP3 trace, or trace of attacks on the network. It lists
the communication packets of all kinds of protocols and offers a segmented and organized
view of the respective details in different parts like IP (Internet Protocol), ICMP (Internet
Control Message Protocol), Frame and Ethernet.
Acceptable Traces
The acceptable traces for the project is found to be gameaddicts.net for the HTTP
trace. This is because the chosen site does not have a SSL certificate. The websites regularly

5
INFORMATION SECURITY ASSURANCE
visited by the company are amazon.com.au, inria.fr, gameaddicts.net, gamerval.com to name
a few. The website chosen for HTTPS trace is https://amazon.com.au. This is because the
website uses a SSL certificate. A different website www.inria.fr is chosen for conducting the
trace route process. All these activities are recorded with the help of the protocol analyser
called Wireshark so that the captured packets of the protocols involved as well as the
respective details can be analysed.
Wireshark Configuration
The configuration of the Wireshark tool is fairly simple. When Wireshark is launched,
the application lists down an array of networks present within the system1. Among these
networks present in the system, the most likely network that is actively used for the tracing
activities is the Ethernet as in most cases systems use their Ethernet network to access the
Internet. Therefore the Ethernet network needs to be selected. After that the recording can be
started by either clicking the Wireshark icon or even by clicking start from the options that
are available in the capture menu on the menu bar.
Part B: Research, Analysis and Reporting of Technical Information
Administrative Network Management System
Administrative Network Management Systems are those applications or application
sets which help network administrators in managing the framework of the network. These
applications can be used in monitoring software as well as hardware components. In general
data gets recorded from the remote points of the network to help conduct centralised
reporting to system administrators.
1 Alshammari, Fayzah. "Towards an Evaluation of a Recommended Tor Browser Configuration in Light of
Website Fingerprinting Attacks." PhD diss., Université d'Ottawa/University of Ottawa, 2017.
INFORMATION SECURITY ASSURANCE
visited by the company are amazon.com.au, inria.fr, gameaddicts.net, gamerval.com to name
a few. The website chosen for HTTPS trace is https://amazon.com.au. This is because the
website uses a SSL certificate. A different website www.inria.fr is chosen for conducting the
trace route process. All these activities are recorded with the help of the protocol analyser
called Wireshark so that the captured packets of the protocols involved as well as the
respective details can be analysed.
Wireshark Configuration
The configuration of the Wireshark tool is fairly simple. When Wireshark is launched,
the application lists down an array of networks present within the system1. Among these
networks present in the system, the most likely network that is actively used for the tracing
activities is the Ethernet as in most cases systems use their Ethernet network to access the
Internet. Therefore the Ethernet network needs to be selected. After that the recording can be
started by either clicking the Wireshark icon or even by clicking start from the options that
are available in the capture menu on the menu bar.
Part B: Research, Analysis and Reporting of Technical Information
Administrative Network Management System
Administrative Network Management Systems are those applications or application
sets which help network administrators in managing the framework of the network. These
applications can be used in monitoring software as well as hardware components. In general
data gets recorded from the remote points of the network to help conduct centralised
reporting to system administrators.
1 Alshammari, Fayzah. "Towards an Evaluation of a Recommended Tor Browser Configuration in Light of
Website Fingerprinting Attacks." PhD diss., Université d'Ottawa/University of Ottawa, 2017.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INFORMATION SECURITY ASSURANCE
Algorithms in IP network security
IPsec or Internet Protocol Security refers to the secure suite of networking protocols.
Here a security association is used the parties where communicating parties set up shared
attributes for security which are generally keys an algorithms. The algorithms are mainly
cryptographic algorithms and are listed below:
HMAC-SHA1/SHA2: This algorithm is used to ensure integrity, protection and
authentication purposes.
TripleDES-CBC: This algorithm is used for ensuring confidentiality purposes
AES-CBC: This algorithm is also used for the purpose of ensuring confidentiality
AES-GCM: This algorithm is used for setting up security to efficiently provide both
authentication and confidentiality.
ChaCha + Poly1305: This algorithm is also used for establishing security to ensure both
authentication and confidentiality in an efficient manner.
Purpose of cryptography in security systems
Cryptography is used for the purpose of protecting data when they are transmitted in
through unsecured networks2. Cryptographic data encryption refers to the process of hiding
plaintext data or encrypting it which results to creation of an altered text called the cipher text
which do not reveal any original inputs. This is commonly used in almost all business
organizations.
2 Kumar, Shyam Nandan. "Review on network security and cryptography." International Transaction of
Electrical and Computer Engineers System 3, no. 1 (2015): 1-11.
INFORMATION SECURITY ASSURANCE
Algorithms in IP network security
IPsec or Internet Protocol Security refers to the secure suite of networking protocols.
Here a security association is used the parties where communicating parties set up shared
attributes for security which are generally keys an algorithms. The algorithms are mainly
cryptographic algorithms and are listed below:
HMAC-SHA1/SHA2: This algorithm is used to ensure integrity, protection and
authentication purposes.
TripleDES-CBC: This algorithm is used for ensuring confidentiality purposes
AES-CBC: This algorithm is also used for the purpose of ensuring confidentiality
AES-GCM: This algorithm is used for setting up security to efficiently provide both
authentication and confidentiality.
ChaCha + Poly1305: This algorithm is also used for establishing security to ensure both
authentication and confidentiality in an efficient manner.
Purpose of cryptography in security systems
Cryptography is used for the purpose of protecting data when they are transmitted in
through unsecured networks2. Cryptographic data encryption refers to the process of hiding
plaintext data or encrypting it which results to creation of an altered text called the cipher text
which do not reveal any original inputs. This is commonly used in almost all business
organizations.
2 Kumar, Shyam Nandan. "Review on network security and cryptography." International Transaction of
Electrical and Computer Engineers System 3, no. 1 (2015): 1-11.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
INFORMATION SECURITY ASSURANCE
Encapsulation and Encryption in Data Transmission
Encapsulation concerns wrapping data into some sort of packets – usually a header
and a trailer. Encryption simply involves changing the data while having the ability to retain
the original data.
Encrypting passwords prevents the exact system password from being visible to all
actors over the network.
Example of Enterprise solutions
Cisco DNA or Digital Network Architecture is the enterprise network security
solution to be installed in the company network. This is the only network security solution in
the industry to have the ability of finding threats existing in traffic which is already
encrypted.
Firewall and Security Solutions
Firewalls can be hardware devices or even programs which filter all the information
arriving via the Internet and onto the private network of users3. If such filters end up flagging
some incoming packets of data, they are not allowed. Other than that real time protection
from antivirus and antimalware solutions can also help the company securing their network.
Common Network Topologies
The networking topologies commonly used in businesses and enterprises are Local
Area Networks (LAN), Wide Area Networks (WAN) and Wireless Local Area Networks
(WLAN)4. Both the other two types of network topologies are extended implementations of
LAN. WAN is used as a LAN network of other LAN networks spread across multiple regions
3 Malmgren, Andreas, and Simon Persson. "A comparative study of Palo Alto Networks and Juniper Networks
next-generation firewalls for a small enterprise network." (2016).
4 Sunny, Albert, Sumankumar Panchal, Nikhil Vidhani, Subhashini Krishnasamy, S. V. R. Anand, Malati
Hegde, Joy Kuri, and Anurag Kumar. "ADWISERv2: A Plug-and-play Controller for Managing TCP Transfers
in IEEE~ 802.11 Infrastructure WLANs with Multiple Access Points." arXiv preprint arXiv:1609.04197 (2016).
INFORMATION SECURITY ASSURANCE
Encapsulation and Encryption in Data Transmission
Encapsulation concerns wrapping data into some sort of packets – usually a header
and a trailer. Encryption simply involves changing the data while having the ability to retain
the original data.
Encrypting passwords prevents the exact system password from being visible to all
actors over the network.
Example of Enterprise solutions
Cisco DNA or Digital Network Architecture is the enterprise network security
solution to be installed in the company network. This is the only network security solution in
the industry to have the ability of finding threats existing in traffic which is already
encrypted.
Firewall and Security Solutions
Firewalls can be hardware devices or even programs which filter all the information
arriving via the Internet and onto the private network of users3. If such filters end up flagging
some incoming packets of data, they are not allowed. Other than that real time protection
from antivirus and antimalware solutions can also help the company securing their network.
Common Network Topologies
The networking topologies commonly used in businesses and enterprises are Local
Area Networks (LAN), Wide Area Networks (WAN) and Wireless Local Area Networks
(WLAN)4. Both the other two types of network topologies are extended implementations of
LAN. WAN is used as a LAN network of other LAN networks spread across multiple regions
3 Malmgren, Andreas, and Simon Persson. "A comparative study of Palo Alto Networks and Juniper Networks
next-generation firewalls for a small enterprise network." (2016).
4 Sunny, Albert, Sumankumar Panchal, Nikhil Vidhani, Subhashini Krishnasamy, S. V. R. Anand, Malati
Hegde, Joy Kuri, and Anurag Kumar. "ADWISERv2: A Plug-and-play Controller for Managing TCP Transfers
in IEEE~ 802.11 Infrastructure WLANs with Multiple Access Points." arXiv preprint arXiv:1609.04197 (2016).

8
INFORMATION SECURITY ASSURANCE
and WLANs involve use of wireless routers and access points for providing network access
to laptops and smartphones.
Operations Network Management Systems
Network management systems are those that can viewed as primary consoles used by
network operators for detecting faults in the network infrastructure. These systems allow
operators in quickly detecting issues on the network so as to proactively work on resolving
the problem. They also offer graphical network maps for network operators to rely on to
know about the operating status of critical elements in the network which can include routers,
switches and even circuits.
Routing Theory
IP Routing concerns the use of a set of protocols for determining the path for data
packets to follow so as to travel through multiple networks from the source to the
destination5. Several routers are used for routing the Data from their source to the destination
and the routing protocols help the routers in building forwarding tables which correlate the
next hop addresses with the destinations.
The various types of routing protocols are:
o RIP (Routing Information Protocol)
o OSPF (Open Shortest Path First)
o BGP (Border Gateway Protocol)
o IS-IS (Intermediate System - Intermediate System)
5 Kawano, Ryuta, Ryota Yasudo, Hiroki Matsutani, Michihiro Koibuchi, and Hideharu Amano. "HiRy: An
advanced theory on design of deadlock-free adaptive routing for arbitrary topologies." In 2017 IEEE 23rd
International Conference on Parallel and Distributed Systems (ICPADS), pp. 664-673. IEEE, 2017.
INFORMATION SECURITY ASSURANCE
and WLANs involve use of wireless routers and access points for providing network access
to laptops and smartphones.
Operations Network Management Systems
Network management systems are those that can viewed as primary consoles used by
network operators for detecting faults in the network infrastructure. These systems allow
operators in quickly detecting issues on the network so as to proactively work on resolving
the problem. They also offer graphical network maps for network operators to rely on to
know about the operating status of critical elements in the network which can include routers,
switches and even circuits.
Routing Theory
IP Routing concerns the use of a set of protocols for determining the path for data
packets to follow so as to travel through multiple networks from the source to the
destination5. Several routers are used for routing the Data from their source to the destination
and the routing protocols help the routers in building forwarding tables which correlate the
next hop addresses with the destinations.
The various types of routing protocols are:
o RIP (Routing Information Protocol)
o OSPF (Open Shortest Path First)
o BGP (Border Gateway Protocol)
o IS-IS (Intermediate System - Intermediate System)
5 Kawano, Ryuta, Ryota Yasudo, Hiroki Matsutani, Michihiro Koibuchi, and Hideharu Amano. "HiRy: An
advanced theory on design of deadlock-free adaptive routing for arbitrary topologies." In 2017 IEEE 23rd
International Conference on Parallel and Distributed Systems (ICPADS), pp. 664-673. IEEE, 2017.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
INFORMATION SECURITY ASSURANCE
System Threats
The threats to the systems of the company are likely to occur from exploits used by
cyber criminals to sabotage the network or steal sensitive information. These threats can
mainly be remote attacks, client side attacks, blind side attacks, social engineering attacks,
denial of service (DoS) and man in the middle (MITM) attacks.
Transaction Protocols
The transaction protocol WS-Atomic Transaction and the coordination protocol WS-
Coordination is implemented by the WCF or Windows Communication Foundation.
Applications and transaction managers are the two levels at which interoperability is required
on the protocol specifications.
Part C: Analysing Packets
HTTP Trace
Website for HTTP Trace
INFORMATION SECURITY ASSURANCE
System Threats
The threats to the systems of the company are likely to occur from exploits used by
cyber criminals to sabotage the network or steal sensitive information. These threats can
mainly be remote attacks, client side attacks, blind side attacks, social engineering attacks,
denial of service (DoS) and man in the middle (MITM) attacks.
Transaction Protocols
The transaction protocol WS-Atomic Transaction and the coordination protocol WS-
Coordination is implemented by the WCF or Windows Communication Foundation.
Applications and transaction managers are the two levels at which interoperability is required
on the protocol specifications.
Part C: Analysing Packets
HTTP Trace
Website for HTTP Trace
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
INFORMATION SECURITY ASSURANCE
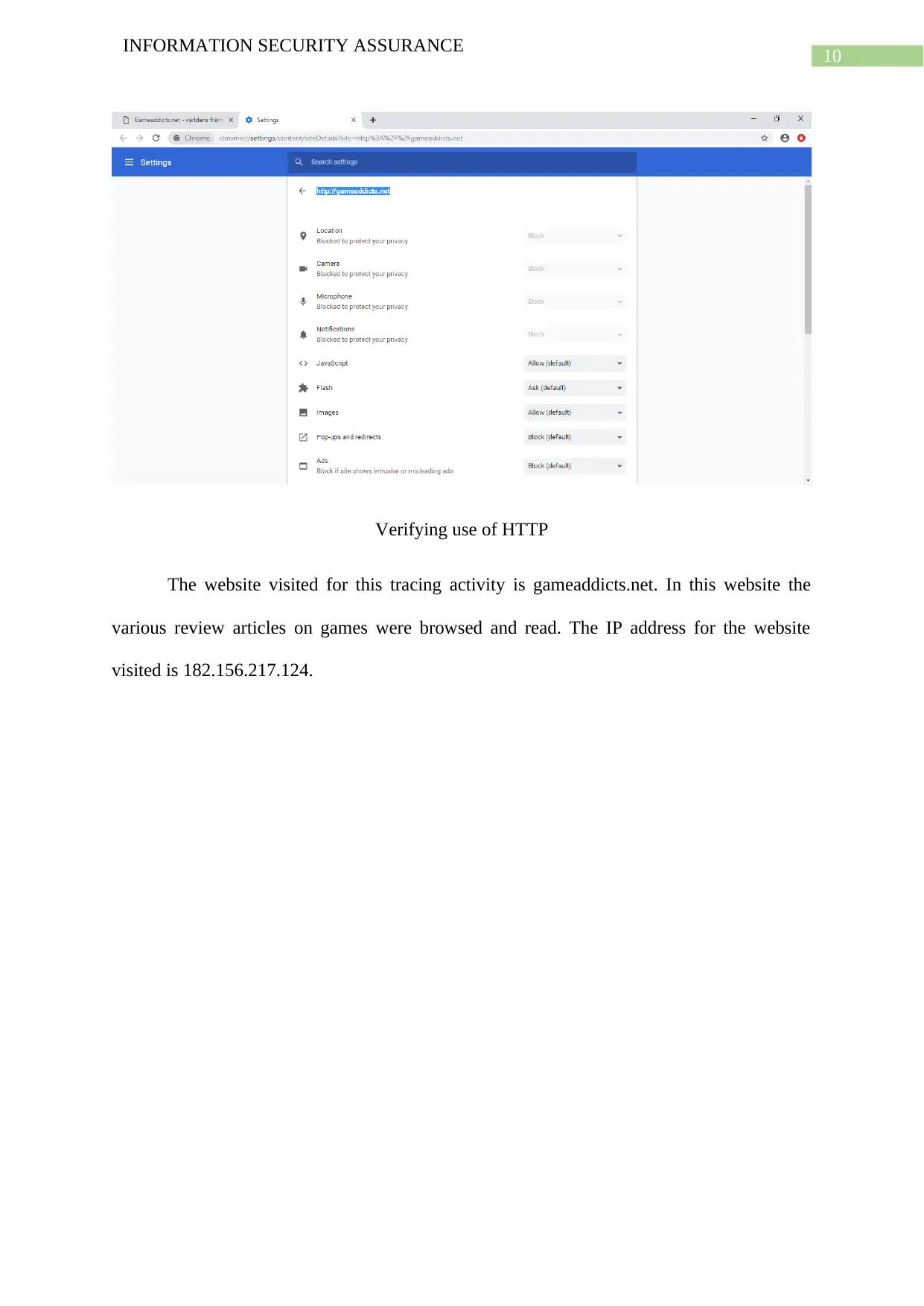
Verifying use of HTTP
The website visited for this tracing activity is gameaddicts.net. In this website the
various review articles on games were browsed and read. The IP address for the website
visited is 182.156.217.124.
INFORMATION SECURITY ASSURANCE
Verifying use of HTTP
The website visited for this tracing activity is gameaddicts.net. In this website the
various review articles on games were browsed and read. The IP address for the website
visited is 182.156.217.124.
11
INFORMATION SECURITY ASSURANCE
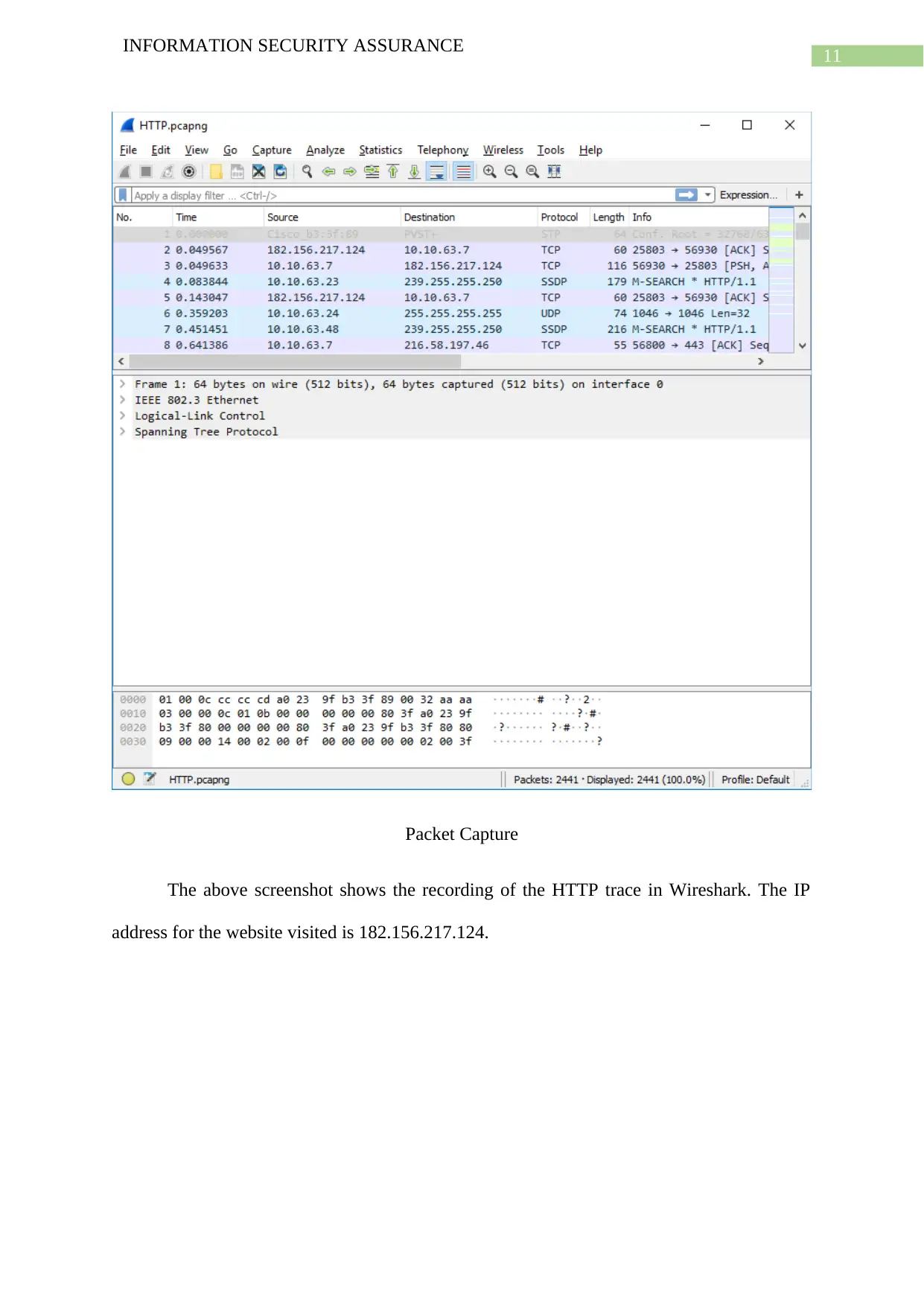
Packet Capture
The above screenshot shows the recording of the HTTP trace in Wireshark. The IP
address for the website visited is 182.156.217.124.
INFORMATION SECURITY ASSURANCE
Packet Capture
The above screenshot shows the recording of the HTTP trace in Wireshark. The IP
address for the website visited is 182.156.217.124.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




