Information Security Report: ATM Security and Biometric Systems
VerifiedAdded on 2023/06/13
|10
|3304
|496
Report
AI Summary
This report delves into various aspects of information security, focusing on the vulnerabilities and security measures associated with Automated Teller Machines (ATMs) and biometric authentication systems. It begins by outlining the CIA triad (Confidentiality, Integrity, and Availability) requirements for ATM systems, providing examples for each. The report then analyzes a scenario involving a compromised ATM, detailing potential security breaches and methods for PIN recovery. A discussion on biometric authentication systems follows, addressing common user concerns such as password resets, hardware requirements, and accuracy, along with potential solutions. Furthermore, the report compares false negative and false positive rates in biometric systems, highlighting situations where false negatives pose greater risks. Finally, the report explores the use of Caesar cipher encryption in a business context, demonstrating its application in securing sensitive information during transmission.

Running head: INFORMATION SECURITY
Information Security
Name of the Student
Name of the University
Author’s Note:
Information Security
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................3
Question 3..................................................................................................................................4
Question 4..................................................................................................................................5
Question 5..................................................................................................................................6
References..................................................................................................................................8
INFORMATION SECURITY
Table of Contents
Question 1..................................................................................................................................2
Question 2..................................................................................................................................3
Question 3..................................................................................................................................4
Question 4..................................................................................................................................5
Question 5..................................................................................................................................6
References..................................................................................................................................8

2
INFORMATION SECURITY
Question 1
The electronic telecommunication device involved for the purpose of cash
withdrawal or checking balance of the existing bank account of any particular authorized user
is known as an ATM or Automated Teller Machine. All types of financial transactions could
be easily executed with the help of this Automated Teller Machine (De Gramatica et al.,
2015). The financial institutions utilize this typical electronic device for the successful
execution of the financial transactions like cash deposits, getting information regarding bank
accounts, cash withdrawals, transferring funds irrespective of the time or place without
requiring any type of interaction or help from the bank executives. The ATM machines are
utilized and installed in each and every country or city or village in the world.
The users, utilizing the ATM systems are given a card and a PIN number. The card is
referred to as an ATM card and the PIN or the personal identification number is referred to a
four digits code that is absolutely unique for each and every card. With the joint operation of
the ATM card and the four digits PIN number, the user becomes an authorized user and thus
he is able to utilize his card for withdrawing some money from his existing bank account.
Three specific requirements are needed in every specific ATM card (Grama, 2014).
They are termed as the CIA or the confidentiality, integrity and the availability. These three
requirements are being explained in the following paragraphs:
i) Confidentiality: This is the other name of privacy. Confidentiality helps to keep the
privacy and security of the ATM card of any authorized user. This confidentiality is
extremely important for each and every ATM card as it helps in maintaining the details of the
user private as well as secret (Peltier, 2013). The two examples of confidentiality in ATM
card are as follows:
a) The PIN and the card number should be stolen or lost at any cost.
b) The confidentiality of the ATM also deals with the fact the ATM card must be
present with the user while executing a transaction.
ii) Integrity: The next requirement in the CIA is the integrity. This basically refers to
the consistency of the data of the ATM card or the PIN number. Data integrity is the most
important and significant factor in ATM (Siponen, Mahmood & Pahnila, 2014). The
examples of integrity within an ATM card are as follows:
a) No alteration in the data of the ATM card without the consent of the user.
b) Accidental or deliberate data removal solely affects integrity of data.
iii) Availability: The final requirement in the CIA category is the availability. This
refers to the availability of the hardware or the important information that is required for
executing any transaction. The examples of availability within an ATM card are as follows:
a) The information systems used for the ATM machines (Xu, Zhou & Lyu, 2014).
b) The confidential information should be maintained properly.
INFORMATION SECURITY
Question 1
The electronic telecommunication device involved for the purpose of cash
withdrawal or checking balance of the existing bank account of any particular authorized user
is known as an ATM or Automated Teller Machine. All types of financial transactions could
be easily executed with the help of this Automated Teller Machine (De Gramatica et al.,
2015). The financial institutions utilize this typical electronic device for the successful
execution of the financial transactions like cash deposits, getting information regarding bank
accounts, cash withdrawals, transferring funds irrespective of the time or place without
requiring any type of interaction or help from the bank executives. The ATM machines are
utilized and installed in each and every country or city or village in the world.
The users, utilizing the ATM systems are given a card and a PIN number. The card is
referred to as an ATM card and the PIN or the personal identification number is referred to a
four digits code that is absolutely unique for each and every card. With the joint operation of
the ATM card and the four digits PIN number, the user becomes an authorized user and thus
he is able to utilize his card for withdrawing some money from his existing bank account.
Three specific requirements are needed in every specific ATM card (Grama, 2014).
They are termed as the CIA or the confidentiality, integrity and the availability. These three
requirements are being explained in the following paragraphs:
i) Confidentiality: This is the other name of privacy. Confidentiality helps to keep the
privacy and security of the ATM card of any authorized user. This confidentiality is
extremely important for each and every ATM card as it helps in maintaining the details of the
user private as well as secret (Peltier, 2013). The two examples of confidentiality in ATM
card are as follows:
a) The PIN and the card number should be stolen or lost at any cost.
b) The confidentiality of the ATM also deals with the fact the ATM card must be
present with the user while executing a transaction.
ii) Integrity: The next requirement in the CIA is the integrity. This basically refers to
the consistency of the data of the ATM card or the PIN number. Data integrity is the most
important and significant factor in ATM (Siponen, Mahmood & Pahnila, 2014). The
examples of integrity within an ATM card are as follows:
a) No alteration in the data of the ATM card without the consent of the user.
b) Accidental or deliberate data removal solely affects integrity of data.
iii) Availability: The final requirement in the CIA category is the availability. This
refers to the availability of the hardware or the important information that is required for
executing any transaction. The examples of availability within an ATM card are as follows:
a) The information systems used for the ATM machines (Xu, Zhou & Lyu, 2014).
b) The confidential information should be maintained properly.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY
Question 2
ATM or the Automated Teller Machine is the device used by various individuals for
the purpose of withdrawing cash without any type of help from the bank staffs or bank
executives. It is an extremely safe and secure machine that stores money and money could be
withdrawn with the ATM card (Von Solms & Van Niekerk, 2013). The user has to enter the
ATM card in the card reader or the card slot. Then, he has to punch his unique four digits PIN
number within the keypad of the machine. Next, the customer has to enter the amount he
wants to withdraw and finally after confirmation, he is able to withdraw the cash.
In the given scenario, a thief has broken the Automated Teller Machine or an ATM
after using a screwdriver and finally has jammed the card reader of that particular ATM
machine. Next, this thief has broken the five keys from the keypad of the ATM.
However, this thief has to stop of stealing money from ATM in the middle; a
customer has come to withdraw some cash from his account. Thus, the thief has hidden from
the customer and thus stopped his breaking of machine. The customer did not notice the thief.
He entered his ATM card in the machine, then punched the four digits of is PIN number and
finally entered the amount to be withdrawn. The cash came out and thus he was successful in
making the transaction.
After the cash withdrawal, the customer tried to pull out his card. However, since the
thief has already jammed the card reader, he s unable to do so. He thus, goes out for calling of
help for withdrawing this ATM card from the machine.
Meanwhile, the thief comes out and tried to know about the PIN number of the user.
As the card was already present in the card reader, it would be easier if he could know the
PIN of the card.
There is a procedure to know the PIN of the customer. Four keys are present in a card.
Thus, the total number of possibilities of permutation of those four keys is as follows:
5P4 = 5!/(5 - 4)! = 5!/4! = 120.
The thief can detect the correct PIN in 120 ways of permutation.
Several security factors are there in every Automated Teller Machine. There is a restriction in
entering these keys in an ATM machine. Only 3 times the card can be entered. After the third
wrong detection, automatically the ATM card would be jammed or blocked.
INFORMATION SECURITY
Question 2
ATM or the Automated Teller Machine is the device used by various individuals for
the purpose of withdrawing cash without any type of help from the bank staffs or bank
executives. It is an extremely safe and secure machine that stores money and money could be
withdrawn with the ATM card (Von Solms & Van Niekerk, 2013). The user has to enter the
ATM card in the card reader or the card slot. Then, he has to punch his unique four digits PIN
number within the keypad of the machine. Next, the customer has to enter the amount he
wants to withdraw and finally after confirmation, he is able to withdraw the cash.
In the given scenario, a thief has broken the Automated Teller Machine or an ATM
after using a screwdriver and finally has jammed the card reader of that particular ATM
machine. Next, this thief has broken the five keys from the keypad of the ATM.
However, this thief has to stop of stealing money from ATM in the middle; a
customer has come to withdraw some cash from his account. Thus, the thief has hidden from
the customer and thus stopped his breaking of machine. The customer did not notice the thief.
He entered his ATM card in the machine, then punched the four digits of is PIN number and
finally entered the amount to be withdrawn. The cash came out and thus he was successful in
making the transaction.
After the cash withdrawal, the customer tried to pull out his card. However, since the
thief has already jammed the card reader, he s unable to do so. He thus, goes out for calling of
help for withdrawing this ATM card from the machine.
Meanwhile, the thief comes out and tried to know about the PIN number of the user.
As the card was already present in the card reader, it would be easier if he could know the
PIN of the card.
There is a procedure to know the PIN of the customer. Four keys are present in a card.
Thus, the total number of possibilities of permutation of those four keys is as follows:
5P4 = 5!/(5 - 4)! = 5!/4! = 120.
The thief can detect the correct PIN in 120 ways of permutation.
Several security factors are there in every Automated Teller Machine. There is a restriction in
entering these keys in an ATM machine. Only 3 times the card can be entered. After the third
wrong detection, automatically the ATM card would be jammed or blocked.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY
Question 3
Biometric authentication system is a privacy and security procedure that does its work
by identifying the biological traits of any particular individual. This type of authentication
system is the safest methodology and is used in several schools, colleges, universities and
offices for attendance (Andress., 2014). The entire procedure of verification by this method
of biometric authentication is extremely easy and simple. The biometric data is compared
with the new data that is to be entered into the system. This particular comparison is done
within few seconds and thus does not incur much time.
The system of biometric authentication comprises of a database. This database is
responsible for storing as well as capturing all the data of an individual. The moment the user
tries to enter into the building, office, school, college or university, the biometric system
checks as well as compares the data with the existing data (Chaudhry et al., 2015). When the
new data matches with the previously existing data, that specific person has the permission to
get in to get the access of the confidential things or information.
There are several types of biometric authentication system. Out of them the most
popular names majorly include retina scans, voice recognition, fingerprint recognition, iris
scan, palm geometry scan, face recognition and many others.
Although, in spite of comprising of these extra ordinary benefits, few people are still
extremely reluctant to utilize this particular system (Lu et al., 2015). Three such situations or
circumstances are provided in the assignment, with their necessary and effective removal.
i) Problem to Reset Password: This is the most significant problem according to
many users. The resetting of passwords often becomes a major problem if the passwords are
of biometric (Singh, 2013). Most of the biometric authentication systems are non resistant to
water and thus if there is any presence of water or sweat, the biometric system does not
allows the access to the system or thing.
This particular problem could be solved by resetting the biometric passwords with
various regulations or rules like Sarbanes-Oxley, PCI-DDS and HIPAA.
ii) Additional Hardware is Required: The second important problem for various users
is the need for extra hardware (Peltier, 2016). When the biometric system is being installed,
an extra hardware is also to be installed with it and thus without this particular hardware, it is
not possible to implement biometric systems.
This particular problem could be solved by implementing lower costs hardware so
that the cost does not cross the budget of the user. Cost effective biometric authentication
machines are available in market for the successful utilization of users.
iii) Lack of Accuracy: The biometric authentication machines are often incapable of
providing 100% accurate data for its users (Xu, Zhou & Lyu, 2014). This is another reason
for people being reluctant to use this system.
This particular problem could be solved by various metrics like FRR and FAR. FRR
is the False Rejection Rate and FAR is the False Acceptance Rate.
INFORMATION SECURITY
Question 3
Biometric authentication system is a privacy and security procedure that does its work
by identifying the biological traits of any particular individual. This type of authentication
system is the safest methodology and is used in several schools, colleges, universities and
offices for attendance (Andress., 2014). The entire procedure of verification by this method
of biometric authentication is extremely easy and simple. The biometric data is compared
with the new data that is to be entered into the system. This particular comparison is done
within few seconds and thus does not incur much time.
The system of biometric authentication comprises of a database. This database is
responsible for storing as well as capturing all the data of an individual. The moment the user
tries to enter into the building, office, school, college or university, the biometric system
checks as well as compares the data with the existing data (Chaudhry et al., 2015). When the
new data matches with the previously existing data, that specific person has the permission to
get in to get the access of the confidential things or information.
There are several types of biometric authentication system. Out of them the most
popular names majorly include retina scans, voice recognition, fingerprint recognition, iris
scan, palm geometry scan, face recognition and many others.
Although, in spite of comprising of these extra ordinary benefits, few people are still
extremely reluctant to utilize this particular system (Lu et al., 2015). Three such situations or
circumstances are provided in the assignment, with their necessary and effective removal.
i) Problem to Reset Password: This is the most significant problem according to
many users. The resetting of passwords often becomes a major problem if the passwords are
of biometric (Singh, 2013). Most of the biometric authentication systems are non resistant to
water and thus if there is any presence of water or sweat, the biometric system does not
allows the access to the system or thing.
This particular problem could be solved by resetting the biometric passwords with
various regulations or rules like Sarbanes-Oxley, PCI-DDS and HIPAA.
ii) Additional Hardware is Required: The second important problem for various users
is the need for extra hardware (Peltier, 2016). When the biometric system is being installed,
an extra hardware is also to be installed with it and thus without this particular hardware, it is
not possible to implement biometric systems.
This particular problem could be solved by implementing lower costs hardware so
that the cost does not cross the budget of the user. Cost effective biometric authentication
machines are available in market for the successful utilization of users.
iii) Lack of Accuracy: The biometric authentication machines are often incapable of
providing 100% accurate data for its users (Xu, Zhou & Lyu, 2014). This is another reason
for people being reluctant to use this system.
This particular problem could be solved by various metrics like FRR and FAR. FRR
is the False Rejection Rate and FAR is the False Acceptance Rate.

5
INFORMATION SECURITY
Question 4
Biometric authentication system helps any individual to recognize or identify himself
or any other person by means biometric traits or attributes. Biological traits are those traits or
attributes that could not be transferred to anyone and thus traits could be utilized as
passwords or attendance system (Bhagavatula et al., 2015). Various schools, colleges or
universities or even offices have implemented the system of biometric authentication in their
systems. Even individual use this system for locking and unlocking of any computer systems
or phones.
The biometric identifiers are always sub categorized by several physiological and
behavioural characteristics. The physiological characteristics of any individual are the
features or attributes of the body parts of that person. The most popular names of
physiological attributes majorly include retina scans, voice recognition, fingerprint
recognition, iris scan, palm geometry scan, identification of DNA, face recognition and many
others (He & Wang, 2015). The behavioural attributes on the other hand, are quite different
from the physiological characteristics. They are the gait, voice, behaviour of an individual.
The rhythm of typing is also considered as behavioural feature.
In spite of having these great and important advantages, biometric authentication
system do comprises of few disadvantages. One of these most significant disadvantages is the
false negative rate. In this type of problem, the authorized user does not get the access of
getting his or her thing by utilizing the biometric system (Rewagad & Pawar, 2013). These
are more dangerous than the false positive rates. These false negative and the false positive
rates are complementary to one another.
Two such situations are depicted below, when the false negative rates are more
serious and dangerous than the false positive rates.
i) Accessing Own Things: The first and the foremost circumstance is when the
authorized user of any object or thing is unable to crack his own password or the biometric
system is not taking up his biological trait (Sayed et al., 2013). This could be a major problem
as he might need that particular ting on an urgent basis. However, due to the problem is
unable to do so.
ii) Failure to Identify Patients: The second significant circumstance is when the aged
persons are not being able to give his biometric authentication. The hands of the user could
be burned or the voice could be jammed or he might have a cardiac arrest and eye operation
(Frank et al., 2013). In all of the above mentioned situations, the biometric authentication
system will not work and thus, the patient will be facing major problems for his health.
INFORMATION SECURITY
Question 4
Biometric authentication system helps any individual to recognize or identify himself
or any other person by means biometric traits or attributes. Biological traits are those traits or
attributes that could not be transferred to anyone and thus traits could be utilized as
passwords or attendance system (Bhagavatula et al., 2015). Various schools, colleges or
universities or even offices have implemented the system of biometric authentication in their
systems. Even individual use this system for locking and unlocking of any computer systems
or phones.
The biometric identifiers are always sub categorized by several physiological and
behavioural characteristics. The physiological characteristics of any individual are the
features or attributes of the body parts of that person. The most popular names of
physiological attributes majorly include retina scans, voice recognition, fingerprint
recognition, iris scan, palm geometry scan, identification of DNA, face recognition and many
others (He & Wang, 2015). The behavioural attributes on the other hand, are quite different
from the physiological characteristics. They are the gait, voice, behaviour of an individual.
The rhythm of typing is also considered as behavioural feature.
In spite of having these great and important advantages, biometric authentication
system do comprises of few disadvantages. One of these most significant disadvantages is the
false negative rate. In this type of problem, the authorized user does not get the access of
getting his or her thing by utilizing the biometric system (Rewagad & Pawar, 2013). These
are more dangerous than the false positive rates. These false negative and the false positive
rates are complementary to one another.
Two such situations are depicted below, when the false negative rates are more
serious and dangerous than the false positive rates.
i) Accessing Own Things: The first and the foremost circumstance is when the
authorized user of any object or thing is unable to crack his own password or the biometric
system is not taking up his biological trait (Sayed et al., 2013). This could be a major problem
as he might need that particular ting on an urgent basis. However, due to the problem is
unable to do so.
ii) Failure to Identify Patients: The second significant circumstance is when the aged
persons are not being able to give his biometric authentication. The hands of the user could
be burned or the voice could be jammed or he might have a cardiac arrest and eye operation
(Frank et al., 2013). In all of the above mentioned situations, the biometric authentication
system will not work and thus, the patient will be facing major problems for his health.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INFORMATION SECURITY
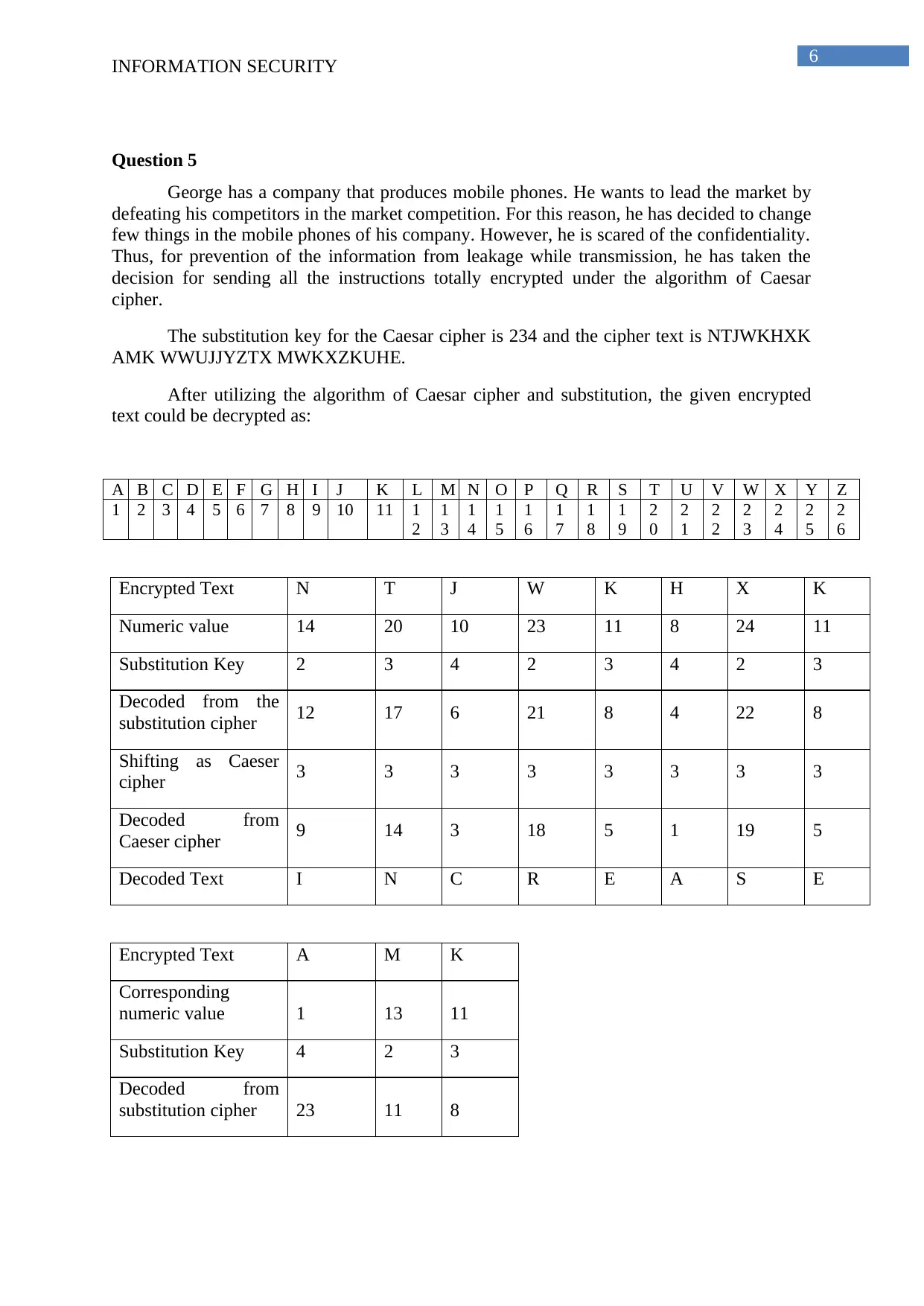
Question 5
George has a company that produces mobile phones. He wants to lead the market by
defeating his competitors in the market competition. For this reason, he has decided to change
few things in the mobile phones of his company. However, he is scared of the confidentiality.
Thus, for prevention of the information from leakage while transmission, he has taken the
decision for sending all the instructions totally encrypted under the algorithm of Caesar
cipher.
The substitution key for the Caesar cipher is 234 and the cipher text is NTJWKHXK
AMK WWUJJYZTX MWKXZKUHE.
After utilizing the algorithm of Caesar cipher and substitution, the given encrypted
text could be decrypted as:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the
substitution cipher 12 17 6 21 8 4 22 8
Shifting as Caeser
cipher 3 3 3 3 3 3 3 3
Decoded from
Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding
numeric value 1 13 11
Substitution Key 4 2 3
Decoded from
substitution cipher 23 11 8
INFORMATION SECURITY
Question 5
George has a company that produces mobile phones. He wants to lead the market by
defeating his competitors in the market competition. For this reason, he has decided to change
few things in the mobile phones of his company. However, he is scared of the confidentiality.
Thus, for prevention of the information from leakage while transmission, he has taken the
decision for sending all the instructions totally encrypted under the algorithm of Caesar
cipher.
The substitution key for the Caesar cipher is 234 and the cipher text is NTJWKHXK
AMK WWUJJYZTX MWKXZKUHE.
After utilizing the algorithm of Caesar cipher and substitution, the given encrypted
text could be decrypted as:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the
substitution cipher 12 17 6 21 8 4 22 8
Shifting as Caeser
cipher 3 3 3 3 3 3 3 3
Decoded from
Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding
numeric value 1 13 11
Substitution Key 4 2 3
Decoded from
substitution cipher 23 11 8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INFORMATION SECURITY
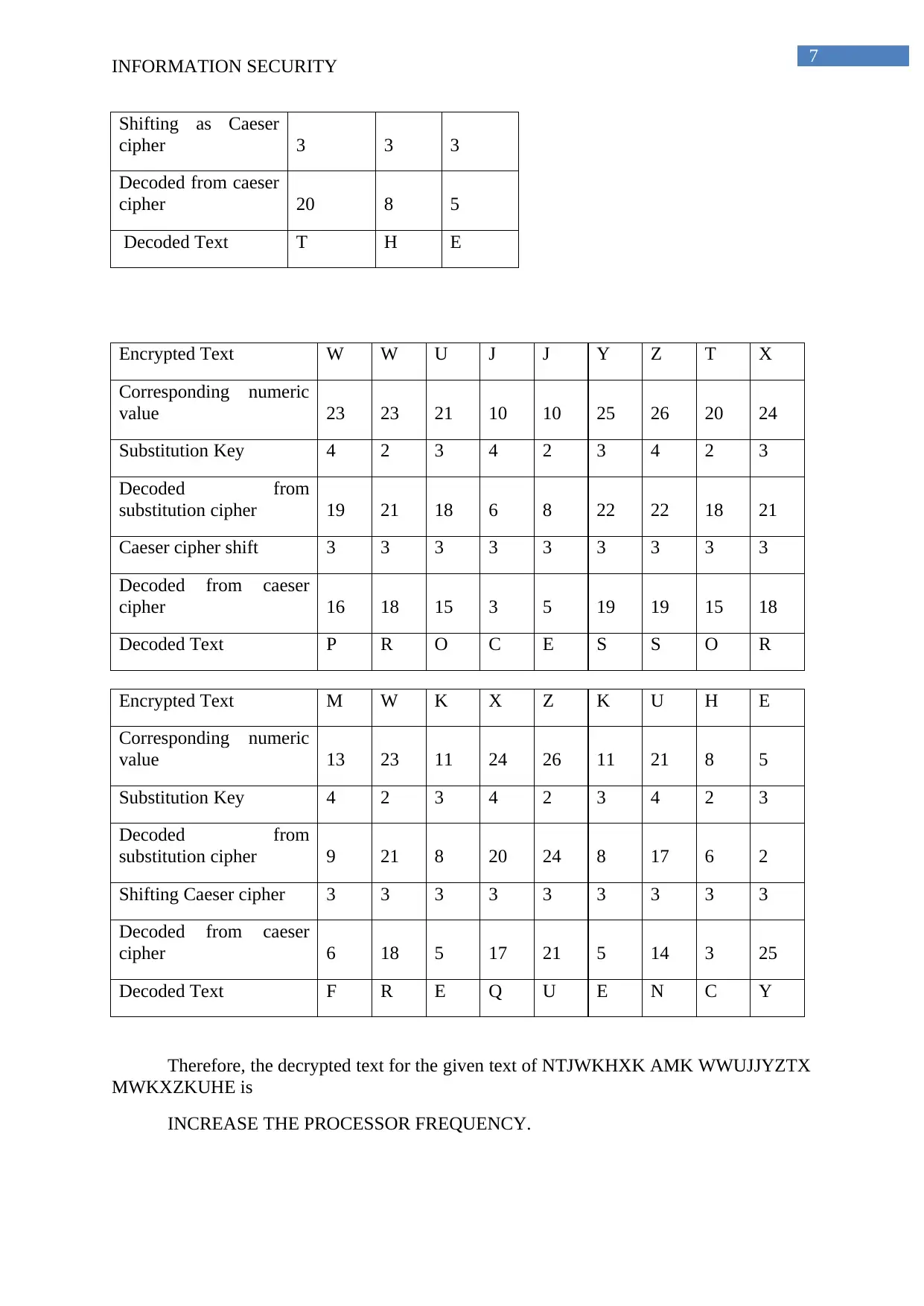
Shifting as Caeser
cipher 3 3 3
Decoded from caeser
cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric
value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from
substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser
cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric
value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from
substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser
cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decrypted text for the given text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is
INCREASE THE PROCESSOR FREQUENCY.
INFORMATION SECURITY
Shifting as Caeser
cipher 3 3 3
Decoded from caeser
cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric
value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from
substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser
cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric
value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from
substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser
cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decrypted text for the given text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is
INCREASE THE PROCESSOR FREQUENCY.

8
INFORMATION SECURITY
References
Andress, J. (2014). The basics of information security: understanding the fundamentals of
InfoSec in theory and practice. Syngress.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and
influences on adoption. Proc. USEC, 1-2.
Chaudhry, S. A., Mahmood, K., Naqvi, H., & Khan, M. K. (2015). An improved and secure
biometric authentication scheme for telecare medicine information systems based on
elliptic curve cryptography. Journal of Medical Systems, 39(11), 175.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The
role of catalogues of threats and security controls in security risk assessment: an
empirical study with ATM professionals. In International Working Conference on
Requirements Engineering: Foundation for Software Quality (pp. 98-114). Springer,
Cham.
Frank, M., Biedert, R., Ma, E., Martinovic, I., & Song, D. (2013). Touchalytics: On the
applicability of touchscreen input as a behavioral biometric for continuous
authentication. IEEE transactions on information forensics and security, 8(1), 136-
148.
Grama, J. L. (2014). Legal issues in information security. Jones & Bartlett Publishers.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
Lu, Y., Li, L., Peng, H., & Yang, Y. (2015). An enhanced biometric-based authentication
scheme for telecare medicine information systems using elliptic curve
cryptosystem. Journal of medical systems, 39(3), 32.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. CRC Press.
Rewagad, P., & Pawar, Y. (2013, April). Use of digital signature with diffie hellman key
exchange and AES encryption algorithm to enhance data security in cloud computing.
In Communication Systems and Network Technologies (CSNT), 2013 International
Conference on (pp. 437-439). IEEE.
Sayed, B., Traoré, I., Woungang, I., & Obaidat, M. S. (2013). Biometric authentication using
mouse gesture dynamics. IEEE Systems Journal, 7(2), 262-274.
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for
information security. International Journal of Computer Applications, 67(19).
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
INFORMATION SECURITY
References
Andress, J. (2014). The basics of information security: understanding the fundamentals of
InfoSec in theory and practice. Syngress.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and
influences on adoption. Proc. USEC, 1-2.
Chaudhry, S. A., Mahmood, K., Naqvi, H., & Khan, M. K. (2015). An improved and secure
biometric authentication scheme for telecare medicine information systems based on
elliptic curve cryptography. Journal of Medical Systems, 39(11), 175.
De Gramatica, M., Labunets, K., Massacci, F., Paci, F., & Tedeschi, A. (2015, March). The
role of catalogues of threats and security controls in security risk assessment: an
empirical study with ATM professionals. In International Working Conference on
Requirements Engineering: Foundation for Software Quality (pp. 98-114). Springer,
Cham.
Frank, M., Biedert, R., Ma, E., Martinovic, I., & Song, D. (2013). Touchalytics: On the
applicability of touchscreen input as a behavioral biometric for continuous
authentication. IEEE transactions on information forensics and security, 8(1), 136-
148.
Grama, J. L. (2014). Legal issues in information security. Jones & Bartlett Publishers.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
Lu, Y., Li, L., Peng, H., & Yang, Y. (2015). An enhanced biometric-based authentication
scheme for telecare medicine information systems using elliptic curve
cryptosystem. Journal of medical systems, 39(3), 32.
Peltier, T. R. (2013). Information security fundamentals. CRC Press.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. CRC Press.
Rewagad, P., & Pawar, Y. (2013, April). Use of digital signature with diffie hellman key
exchange and AES encryption algorithm to enhance data security in cloud computing.
In Communication Systems and Network Technologies (CSNT), 2013 International
Conference on (pp. 437-439). IEEE.
Sayed, B., Traoré, I., Woungang, I., & Obaidat, M. S. (2013). Biometric authentication using
mouse gesture dynamics. IEEE Systems Journal, 7(2), 262-274.
Singh, G. (2013). A study of encryption algorithms (RSA, DES, 3DES and AES) for
information security. International Journal of Computer Applications, 67(19).
Siponen, M., Mahmood, M. A., & Pahnila, S. (2014). Employees’ adherence to information
security policies: An exploratory field study. Information & management, 51(2), 217-
224.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INFORMATION SECURITY
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Xu, H., Zhou, Y., & Lyu, M. R. (2014, July). Towards continuous and passive authentication
via touch biometrics: An experimental study on smartphones. In Symposium On
Usable Privacy and Security, SOUPS (Vol. 14, pp. 187-198).
INFORMATION SECURITY
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Xu, H., Zhou, Y., & Lyu, M. R. (2014, July). Towards continuous and passive authentication
via touch biometrics: An experimental study on smartphones. In Symposium On
Usable Privacy and Security, SOUPS (Vol. 14, pp. 187-198).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



