Information Security for ATM, Biometric Sensors and Cipher
VerifiedAdded on 2023/06/14
|10
|2100
|403
AI Summary
This article discusses the security measures for Automated Teller Machines (ATM), Biometric Sensors and Cipher. It covers the importance of confidentiality, data integrity, and the problems of using biometric sensors. The article also explains the Caesar Cipher and its decryption process. The subject is Information Security and the course code is not mentioned. The article is relevant for students studying computer science, cybersecurity, and information technology.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INFORMATION SECURITY
Information Security
Name of the Student
Name of the University
Author Note
Information Security
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1INFORMATION SECURITY
Table of Contents
Automated teller machine:...................................................................................................2
PIN Combinations:..............................................................................................................3
Biometric Sensors:...............................................................................................................3
Problems of using Bio metric:.............................................................................................4
Caeser Cipher:.....................................................................................................................5
References............................................................................................................................8
Table of Contents
Automated teller machine:...................................................................................................2
PIN Combinations:..............................................................................................................3
Biometric Sensors:...............................................................................................................3
Problems of using Bio metric:.............................................................................................4
Caeser Cipher:.....................................................................................................................5
References............................................................................................................................8

2INFORMATION SECURITY
Automated teller machine:
ATM or the automated Teller machines are designed in a way that the customer will need
a personal identification number or PIN and a dedicated card to access their bank account using
the ATM machine. For any ATM card the most important is the PIN number to secure the
account. For every user the PIN number is different and encrypted and to secure the PIN number
the customer needs to take care of some important factors:
To keep the account and the money secure confidentiality is the major factor that the
customer needs to take care of. The user must not leak the ATM PIN to anyone to secure the
money. The user must not write the PIN on the back of the card or anywhere. User must stay
away from the spam calls that asks for the customer’s account number because the bank personal
does not ask the PIN of the customer (Bachu, 2017).
Data integrity is a way of securing the data from the unauthorized people, so the data
cannot be modified or changed in any circumstances. The customer always expects that no
accidental changes reflect on the record of the transaction. The integrity must be secured because
the transaction is performed directly using the customer account. If the integrity is not
maintained, then it can affect the customer account. A proper trusted platform module is used to
maintain the integrity of the ATM machines.
The ATM machines should available all the time for the customers all time. The ATM
must be maintained properly to serve the customer whenever needed. Use of more ATM will
increase the growth of the bank economically. All the ATM’s must be at operational condition
and in serviceable condition most of the times. More the self-banking increase more the
customer base of the bank will be increased.
Automated teller machine:
ATM or the automated Teller machines are designed in a way that the customer will need
a personal identification number or PIN and a dedicated card to access their bank account using
the ATM machine. For any ATM card the most important is the PIN number to secure the
account. For every user the PIN number is different and encrypted and to secure the PIN number
the customer needs to take care of some important factors:
To keep the account and the money secure confidentiality is the major factor that the
customer needs to take care of. The user must not leak the ATM PIN to anyone to secure the
money. The user must not write the PIN on the back of the card or anywhere. User must stay
away from the spam calls that asks for the customer’s account number because the bank personal
does not ask the PIN of the customer (Bachu, 2017).
Data integrity is a way of securing the data from the unauthorized people, so the data
cannot be modified or changed in any circumstances. The customer always expects that no
accidental changes reflect on the record of the transaction. The integrity must be secured because
the transaction is performed directly using the customer account. If the integrity is not
maintained, then it can affect the customer account. A proper trusted platform module is used to
maintain the integrity of the ATM machines.
The ATM machines should available all the time for the customers all time. The ATM
must be maintained properly to serve the customer whenever needed. Use of more ATM will
increase the growth of the bank economically. All the ATM’s must be at operational condition
and in serviceable condition most of the times. More the self-banking increase more the
customer base of the bank will be increased.

3INFORMATION SECURITY
PIN Combinations:
As mentioned in the scenario that the thief already blocked 5 keys out of the 10 keys on
the number pad, if the user PIN is from the rest of the intact 5 keys which are not damaged then
there will be lots of permutations and combinations if the thief wants to debit money from the
account.
the calculation is
(5!)/ (5! -4!) = (5*4*3*2*1)/ 1 = 120
The thief needs to try 120 different combination to get the correct pin to withdraw money
from the ATM.
Biometric Sensors:
Biometric sensors are the modern-day innovation and widely used for providing security
to the people. Bio metric technology use human body detection technology for the
authentication. Several types of bio metric sensors are introduced in the recent years like iris
scanner, fingerprint scanner, voice recognition or heart beat detectors (Eberz et al., 2017). These
mentioned sensors are the most secure as for every human the properties are different and
unique, so the chances of duplicate data are so less even we can say there will be no duplicate
data. As the duplicate data is not there so persons security will be at the optimum level ( Oko &
Oruh, 2012). Though there are lots of advantages of using biometric technology many people
still reluctant to use biometric technology. Many people think that the information is leaked from
the biometric and many people thinks that the government are keeping their personal data. In the
banks customers are not in favour of using the finger print sensors as the ATM card is used by a
people who is closer of the person and if the biometric is there then no one except the customer
PIN Combinations:
As mentioned in the scenario that the thief already blocked 5 keys out of the 10 keys on
the number pad, if the user PIN is from the rest of the intact 5 keys which are not damaged then
there will be lots of permutations and combinations if the thief wants to debit money from the
account.
the calculation is
(5!)/ (5! -4!) = (5*4*3*2*1)/ 1 = 120
The thief needs to try 120 different combination to get the correct pin to withdraw money
from the ATM.
Biometric Sensors:
Biometric sensors are the modern-day innovation and widely used for providing security
to the people. Bio metric technology use human body detection technology for the
authentication. Several types of bio metric sensors are introduced in the recent years like iris
scanner, fingerprint scanner, voice recognition or heart beat detectors (Eberz et al., 2017). These
mentioned sensors are the most secure as for every human the properties are different and
unique, so the chances of duplicate data are so less even we can say there will be no duplicate
data. As the duplicate data is not there so persons security will be at the optimum level ( Oko &
Oruh, 2012). Though there are lots of advantages of using biometric technology many people
still reluctant to use biometric technology. Many people think that the information is leaked from
the biometric and many people thinks that the government are keeping their personal data. In the
banks customers are not in favour of using the finger print sensors as the ATM card is used by a
people who is closer of the person and if the biometric is there then no one except the customer
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4INFORMATION SECURITY
can use the card therefore people are still refusing this technology in many cases. The fear of the
false negative result is another reason why the people are reluctant of using the bio metric
sensors. False negative is when the machine cannot recognise the authenticated user and rejects
them. The false negative works in different way it can se seen as a good thing as the trust in the
technology in increases the trust on the users or the users feels irritated by the system failure.
Problems of using Bio metric:
False negative and false positive are the main major problem regarding the biometric
sensors that the people needs to keep in their mind. When the biometric sensor accepts the wrong
input as right then the condition is called false positive condition. When the biometric sensor
rejects the correct input as false then the condition is called as false negative condition. Many
people’s data got lost due to the false positive condition. In some cases, hackers try to bypass the
fingerprint sensor if then false positive condition happen then the user will be on huge trouble as
all the personal information will be on stake (Ketab, Clarke & Dowland, 2016). The false
positive can happen due to some technical fault or for some other issues. If the sensitivity of the
biometric sensor increased, then these kinds of unwanted condition can be avoided. The people
must register themselves to the biometric after reading all the instructions carefully.
When the biometric scanner throw-outs the right material stating as incorrect called the
false negative circumstance. This is more perilous than the incorrect positive condition. In case
of a emergency if this error happens then the authorised person to whom the bio metric was
assigned fails to detect the user. When this happen in a case of some serious situation then there
is scope for the user to unlock the system. In case of any emergency this can cause major
troubles to the organisation and hence the organisation faces many losses. This problem is a very
common problem in the modern day smart phones which has a inbuit finger print sensor which is
can use the card therefore people are still refusing this technology in many cases. The fear of the
false negative result is another reason why the people are reluctant of using the bio metric
sensors. False negative is when the machine cannot recognise the authenticated user and rejects
them. The false negative works in different way it can se seen as a good thing as the trust in the
technology in increases the trust on the users or the users feels irritated by the system failure.
Problems of using Bio metric:
False negative and false positive are the main major problem regarding the biometric
sensors that the people needs to keep in their mind. When the biometric sensor accepts the wrong
input as right then the condition is called false positive condition. When the biometric sensor
rejects the correct input as false then the condition is called as false negative condition. Many
people’s data got lost due to the false positive condition. In some cases, hackers try to bypass the
fingerprint sensor if then false positive condition happen then the user will be on huge trouble as
all the personal information will be on stake (Ketab, Clarke & Dowland, 2016). The false
positive can happen due to some technical fault or for some other issues. If the sensitivity of the
biometric sensor increased, then these kinds of unwanted condition can be avoided. The people
must register themselves to the biometric after reading all the instructions carefully.
When the biometric scanner throw-outs the right material stating as incorrect called the
false negative circumstance. This is more perilous than the incorrect positive condition. In case
of a emergency if this error happens then the authorised person to whom the bio metric was
assigned fails to detect the user. When this happen in a case of some serious situation then there
is scope for the user to unlock the system. In case of any emergency this can cause major
troubles to the organisation and hence the organisation faces many losses. This problem is a very
common problem in the modern day smart phones which has a inbuit finger print sensor which is

5INFORMATION SECURITY
a form of the biometric sensor. Many a times it is seen that the biometric sensors rejects the data
of the authenticated user, this can cause serious problems at the times of any emergency.
Supposing in a situation someone needs to call an ambulance then the in a case of the emergency
but the bio metric sensors in the phone are not working and taking false negative input. These
problems are caused due to various problems like the echinococcal issue , sensing power of the
sensors, minor software bugs , sometimes the fault is not only of the technology but the user
does not read the full instructions before registering themselves to the biometric a result the input
was not recorded properly and resulted these cases (Katz & Lindell,2014). These problems can
easily be eradicated by updating the technology of the bio metric scanners, introducing of new
technologies had already removed this problem a lot. Other than this while registering the user
must properly read the instructions and do the same.
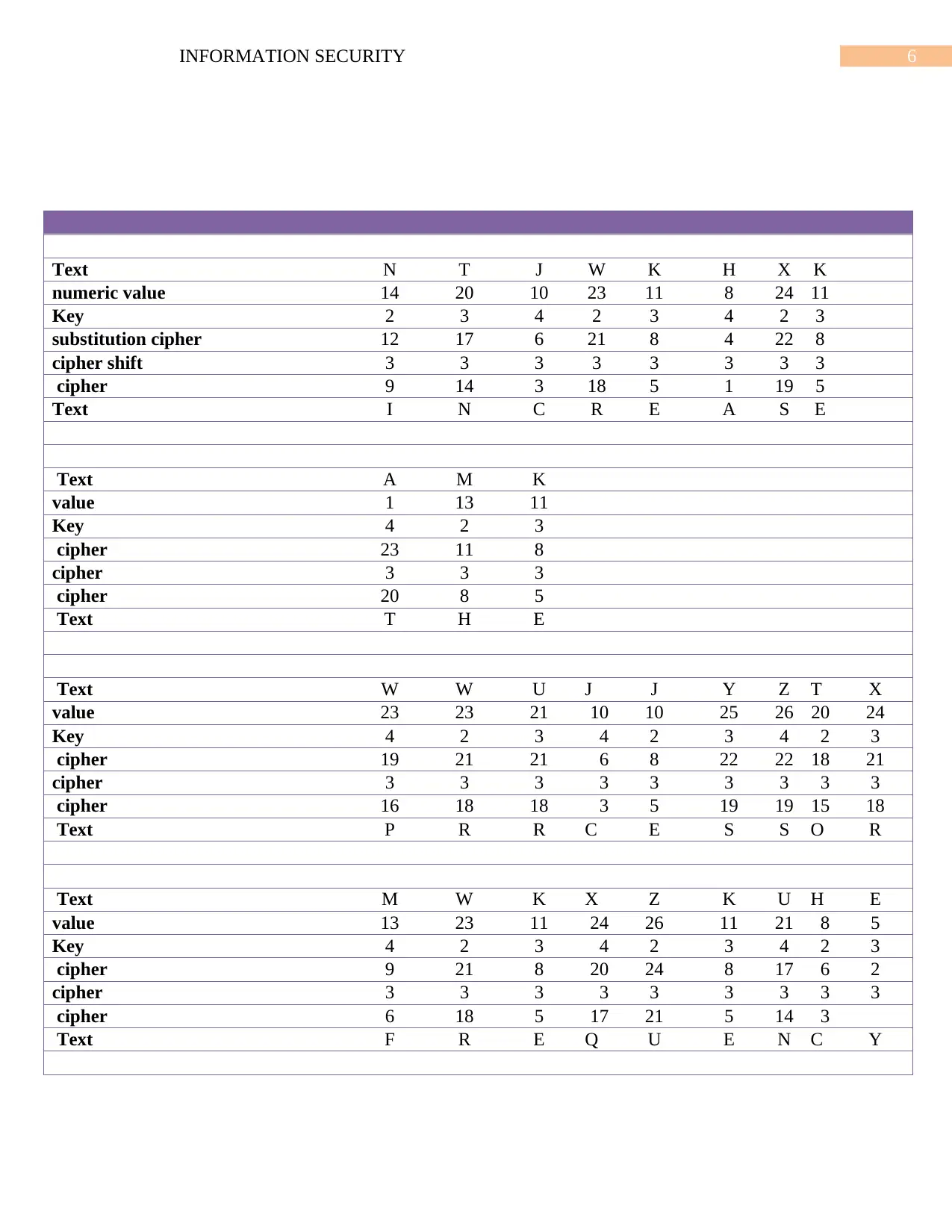
Caeser Cipher:
Inverse order is one of the relaxed and most humble technique for decoding a cipher text.
Encoded message is inverted in this method to get the actual text. So if the encoded message is
“elpmaxe na si siht” becomes” this is an example”. this system uses the most to decipher a cipher
text. Though there are more safe techniques are there than this (Martinovic et al ., 2016).
For the given cipher text to decipher, the steps are given below:
First note down the alphabet number.
Subtract the number of alphabet from the shift key in sequence, that is for number
1 letter 2, for the number 2 letter 3 and the number 3 letter 4 and continuing
(Okokpujie et al., 2016).
3rd is to subtract the general digit which is used for any cypher key that is 3 from
the previous solution.
The final step is locating the alphabet from the solution number.
a form of the biometric sensor. Many a times it is seen that the biometric sensors rejects the data
of the authenticated user, this can cause serious problems at the times of any emergency.
Supposing in a situation someone needs to call an ambulance then the in a case of the emergency
but the bio metric sensors in the phone are not working and taking false negative input. These
problems are caused due to various problems like the echinococcal issue , sensing power of the
sensors, minor software bugs , sometimes the fault is not only of the technology but the user
does not read the full instructions before registering themselves to the biometric a result the input
was not recorded properly and resulted these cases (Katz & Lindell,2014). These problems can
easily be eradicated by updating the technology of the bio metric scanners, introducing of new
technologies had already removed this problem a lot. Other than this while registering the user
must properly read the instructions and do the same.
Caeser Cipher:
Inverse order is one of the relaxed and most humble technique for decoding a cipher text.
Encoded message is inverted in this method to get the actual text. So if the encoded message is
“elpmaxe na si siht” becomes” this is an example”. this system uses the most to decipher a cipher
text. Though there are more safe techniques are there than this (Martinovic et al ., 2016).
For the given cipher text to decipher, the steps are given below:
First note down the alphabet number.
Subtract the number of alphabet from the shift key in sequence, that is for number
1 letter 2, for the number 2 letter 3 and the number 3 letter 4 and continuing
(Okokpujie et al., 2016).
3rd is to subtract the general digit which is used for any cypher key that is 3 from
the previous solution.
The final step is locating the alphabet from the solution number.
6INFORMATION SECURITY
Text N T J W K H X K
numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
substitution cipher 12 17 6 21 8 4 22 8
cipher shift 3 3 3 3 3 3 3 3
cipher 9 14 3 18 5 1 19 5
Text I N C R E A S E
Text A M K
value 1 13 11
Key 4 2 3
cipher 23 11 8
cipher 3 3 3
cipher 20 8 5
Text T H E
Text W W U J J Y Z T X
value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
cipher 19 21 21 6 8 22 22 18 21
cipher 3 3 3 3 3 3 3 3 3
cipher 16 18 18 3 5 19 19 15 18
Text P R R C E S S O R
Text M W K X Z K U H E
value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
cipher 9 21 8 20 24 8 17 6 2
cipher 3 3 3 3 3 3 3 3 3
cipher 6 18 5 17 21 5 14 3
Text F R E Q U E N C Y
Text N T J W K H X K
numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
substitution cipher 12 17 6 21 8 4 22 8
cipher shift 3 3 3 3 3 3 3 3
cipher 9 14 3 18 5 1 19 5
Text I N C R E A S E
Text A M K
value 1 13 11
Key 4 2 3
cipher 23 11 8
cipher 3 3 3
cipher 20 8 5
Text T H E
Text W W U J J Y Z T X
value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
cipher 19 21 21 6 8 22 22 18 21
cipher 3 3 3 3 3 3 3 3 3
cipher 16 18 18 3 5 19 19 15 18
Text P R R C E S S O R
Text M W K X Z K U H E
value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
cipher 9 21 8 20 24 8 17 6 2
cipher 3 3 3 3 3 3 3 3 3
cipher 6 18 5 17 21 5 14 3
Text F R E Q U E N C Y
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
Therefore, the decrypted basic text for the cypher “NTJWKHXK AMK WWUJYZTX MWK
XZKUHE” is “Increase the processor frequency”.
Therefore, the decrypted basic text for the cypher “NTJWKHXK AMK WWUJYZTX MWK
XZKUHE” is “Increase the processor frequency”.

8INFORMATION SECURITY
References
Bachu, S. (2017). Three-step authentication for ATMs.
Eberz, S., Rasmussen, K. B., Lenders, V., & Martinovic, I. (2017, April). Evaluating
behavioral biometrics for continuous authentication: Challenges and metrics. In Proceedings of
the 2017 ACM on Asia Conference on Computer and Communications Security (pp. 386-399).
ACM.
Katz, J., & Lindell, Y. (2014). Introduction to modern cryptography. CRC press.
Ketab, S. S., Clarke, N. L., & Dowland, P. S. (2016). The Value of the Biometrics in
Invigilated E-Assessments.
Konheim, A. G. (2016). Automated teller machines: their history and authentication
protocols. Journal of Cryptographic Engineering, 6(1), 1-29.
Martinovic, I., Rasmussen, K., Roeschlin, M., & Tsudik, G. (2017). Authentication using
pulse-response biometrics. Communications of the ACM, 60(2), 108-115.
Oko, S., & Oruh, J. (2012). Enhanced ATM security system using
biometrics. International Journal of Computer Science Issues, 9(5), 355-363.
Okokpujie, K., Olajide, F., John, S., & Kennedy, C. G. (2016, January). Implementation
of the enhanced fingerprint authentication in the ATM system using ATmega128.
In Proceedings of the International Conference on Security and Management
(SAM) (p. 258). The Steering Committee of The World Congress in Computer
Science, Computer Engineering and Applied Computing (WorldComp).
References
Bachu, S. (2017). Three-step authentication for ATMs.
Eberz, S., Rasmussen, K. B., Lenders, V., & Martinovic, I. (2017, April). Evaluating
behavioral biometrics for continuous authentication: Challenges and metrics. In Proceedings of
the 2017 ACM on Asia Conference on Computer and Communications Security (pp. 386-399).
ACM.
Katz, J., & Lindell, Y. (2014). Introduction to modern cryptography. CRC press.
Ketab, S. S., Clarke, N. L., & Dowland, P. S. (2016). The Value of the Biometrics in
Invigilated E-Assessments.
Konheim, A. G. (2016). Automated teller machines: their history and authentication
protocols. Journal of Cryptographic Engineering, 6(1), 1-29.
Martinovic, I., Rasmussen, K., Roeschlin, M., & Tsudik, G. (2017). Authentication using
pulse-response biometrics. Communications of the ACM, 60(2), 108-115.
Oko, S., & Oruh, J. (2012). Enhanced ATM security system using
biometrics. International Journal of Computer Science Issues, 9(5), 355-363.
Okokpujie, K., Olajide, F., John, S., & Kennedy, C. G. (2016, January). Implementation
of the enhanced fingerprint authentication in the ATM system using ATmega128.
In Proceedings of the International Conference on Security and Management
(SAM) (p. 258). The Steering Committee of The World Congress in Computer
Science, Computer Engineering and Applied Computing (WorldComp).

9INFORMATION SECURITY
Pandey, R. M., & Verma, V. K. (2015). Data Security using Various Cryptography
Techniques: A recent Survey.
Sharma, A., Misra, P. K., & Misra, P. (2014). A Security Measure for Electronic
Business Applications. International Journal of Computer Applications, 102(7).
Pandey, R. M., & Verma, V. K. (2015). Data Security using Various Cryptography
Techniques: A recent Survey.
Sharma, A., Misra, P. K., & Misra, P. (2014). A Security Measure for Electronic
Business Applications. International Journal of Computer Applications, 102(7).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




