Information Security Awareness Training Report for ATI
VerifiedAdded on 2022/08/28
|20
|1073
|57
Report
AI Summary
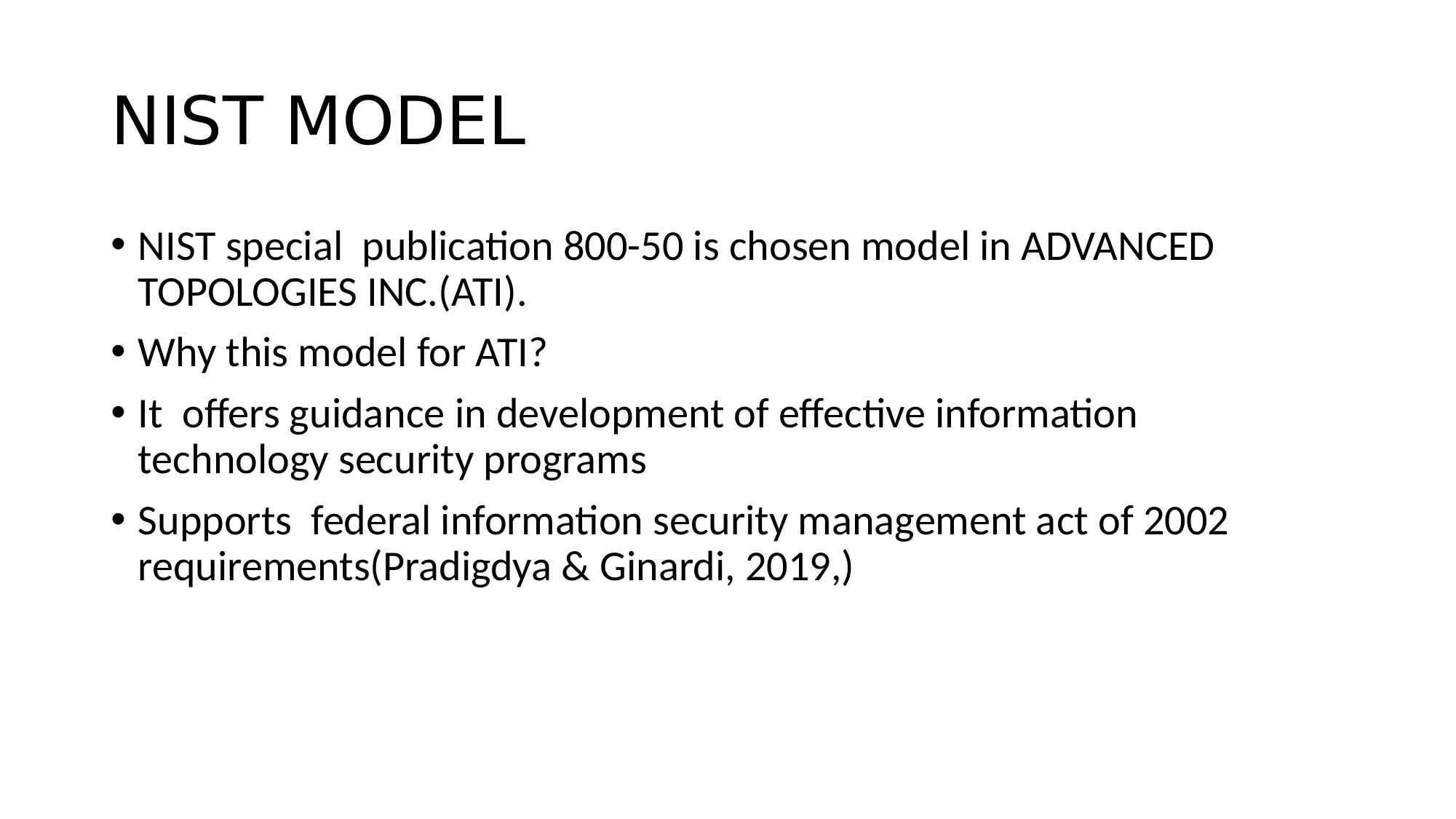
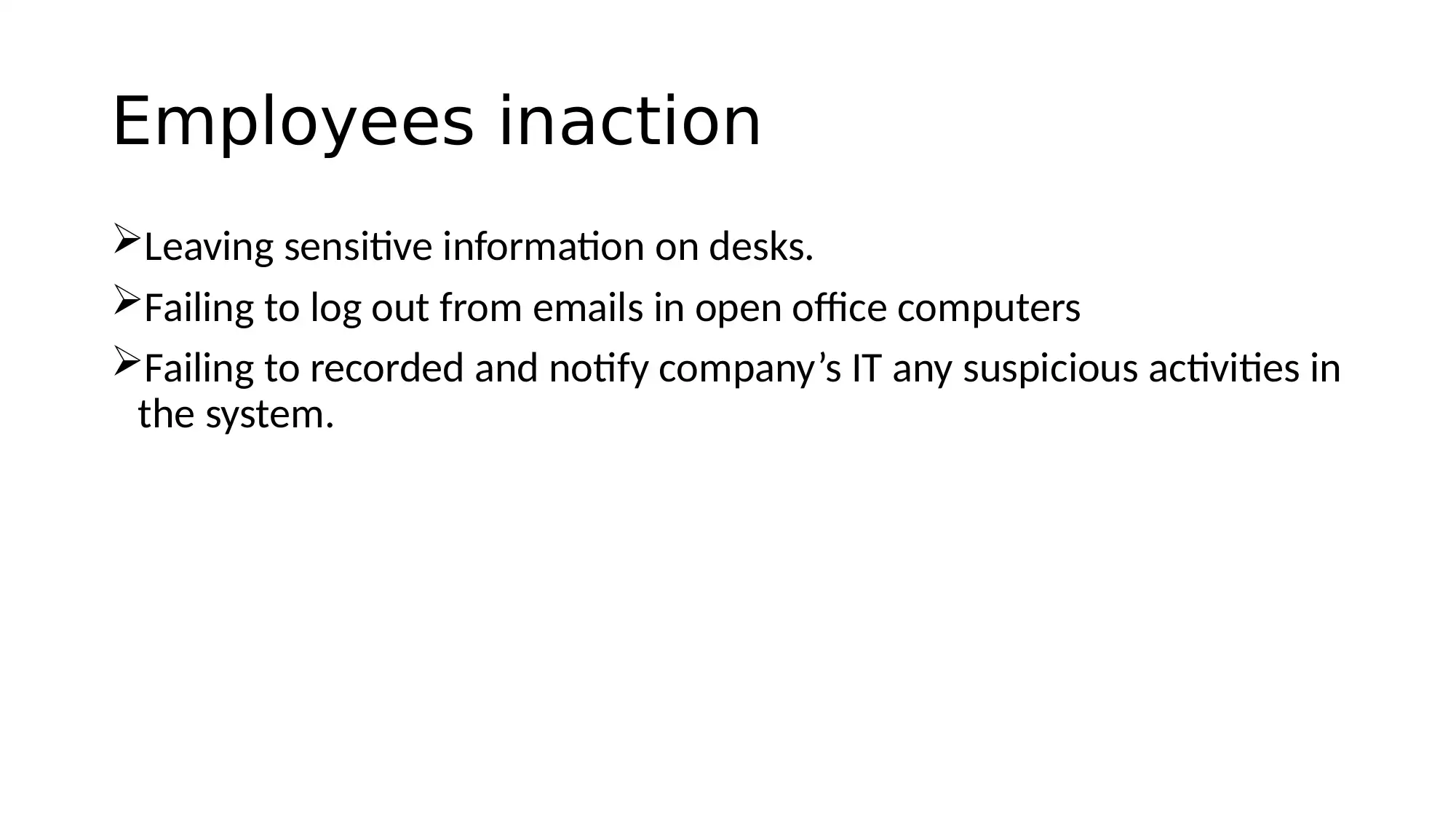
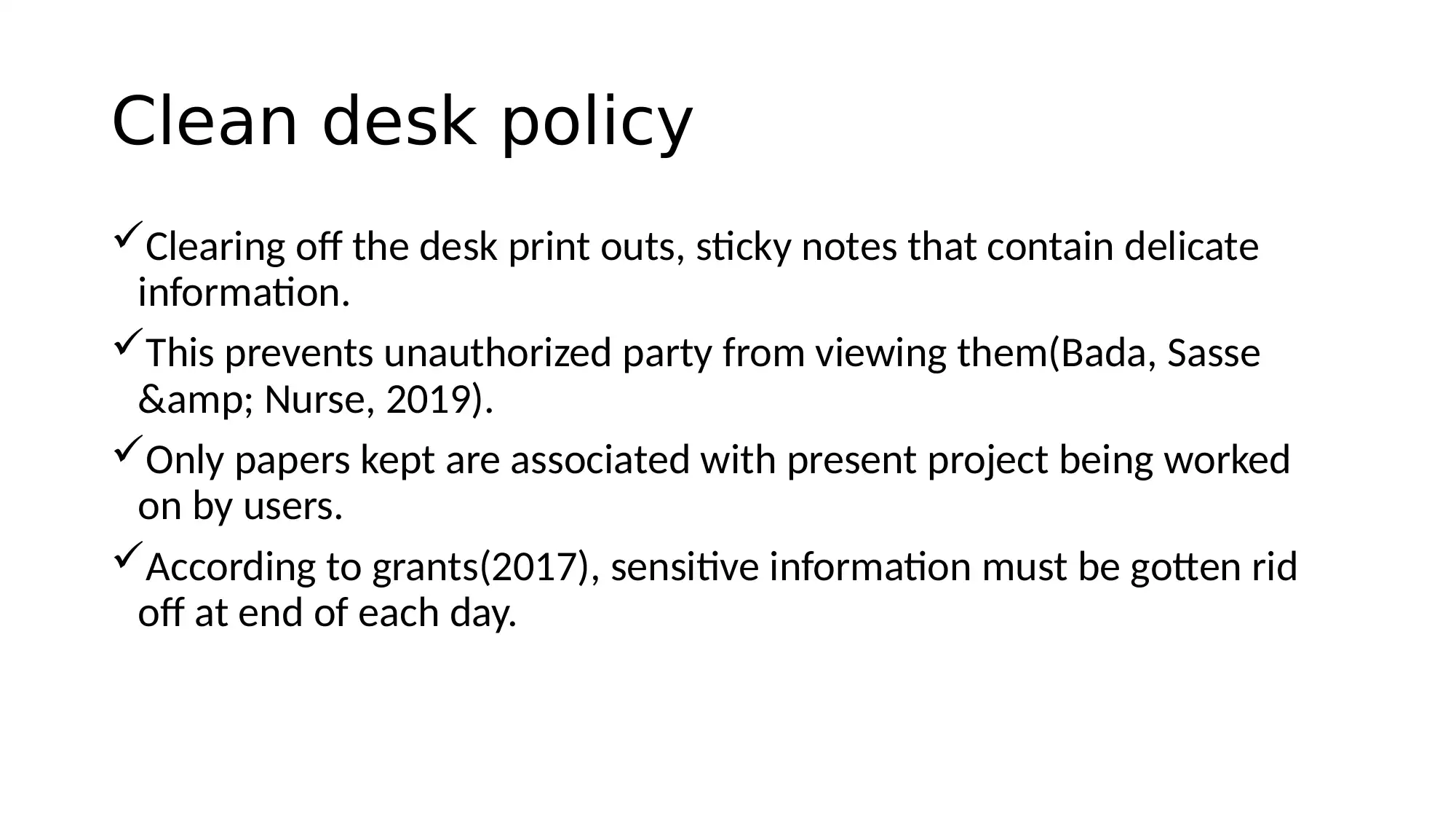
This report details an information security awareness training program designed for Advanced Topologies Inc. (ATI). It begins with an introduction to information security, defining its objectives of integrity, confidentiality, and availability. The report adopts the NIST Special Publication 800-50 model, providing guidance for effective IT security programs. It identifies potential causes of information insecurity, stemming from both employee actions and inactions, and addresses associated risks like leaving sensitive data unattended, clicking on suspicious emails, and using weak passwords. The core of the report covers key policies, including clean desk, bring your own device (BYOD), data management, removable media, and social networking policies. Roles and responsibilities are outlined for agency heads, chief information officers (CIOs), and managers. The report concludes with recommendations such as continuous monitoring of employee activities, discouraging BYOD on company networks, and minimizing the use of sticky notes and printouts, emphasizing that security is the responsibility of every employee. References to key literature are also included.
1 out of 20
















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)