Information Security Design Report for ISCSR 2020 Paper Review System
VerifiedAdded on 2023/04/21
|15
|2918
|245
Report
AI Summary
This report presents an analysis of the security requirements and a proposed design for the ISCSR 2020 paper review system, addressing vulnerabilities highlighted by a previous data breach. It identifies primary users and their requirements, critical assets to be protected (paper titles, abstracts, author information), and potential threats like information theft and manipulation. The report outlines a security policy encompassing confidentiality (TLS/SSL, encryption), integrity (WebSafe, WAF, application testing), and availability (DDoS mitigation, WAF, encryption). It details user authentication using API keys and cryptographic technology, proposes an access control scheme defining user permissions, and suggests website protection measures like software updates, firewalls, and SQL injection checks. The proposed security controls aim to safeguard the system and maintain the integrity and confidentiality of submitted research papers. Desklib offers a wide array of study resources, including similar solved assignments and past papers, to aid students in their academic pursuits.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the student:
Name of the university:
Author note:
INFORMATION SECURITY
Name of the student:
Name of the university:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Table of Contents
Analysis of the problem situation:.............................................................................................2
Primary users and their requirements:....................................................................................3
Assets to be protected:...............................................................................................................5
Possible vulnerabilities and threats:...........................................................................................6
Security policy for threats and vulnerabilities:..........................................................................7
Providing Confidentiality:..................................................................................................7
Providing Integrity:............................................................................................................7
Providing Availability:.......................................................................................................7
User authentication:...............................................................................................................8
Access control scheme:..........................................................................................................8
Website protection:................................................................................................................8
Suitability of proposed security controls:..............................................................................9
References:...............................................................................................................................10
Appendix..................................................................................................................................12
Table of Contents
Analysis of the problem situation:.............................................................................................2
Primary users and their requirements:....................................................................................3
Assets to be protected:...............................................................................................................5
Possible vulnerabilities and threats:...........................................................................................6
Security policy for threats and vulnerabilities:..........................................................................7
Providing Confidentiality:..................................................................................................7
Providing Integrity:............................................................................................................7
Providing Availability:.......................................................................................................7
User authentication:...............................................................................................................8
Access control scheme:..........................................................................................................8
Website protection:................................................................................................................8
Suitability of proposed security controls:..............................................................................9
References:...............................................................................................................................10
Appendix..................................................................................................................................12

2INFORMATION SECURITY
Analysis of the problem situation:
Presently there are a number of issues in the system in the ISCSR 2020 paper review
system. Security of the papers and the maintaining the authenticity is one of the primary
concerns. The credibility and respects of the authors depend on the number of citations that
are done for the submitted papers. More number of citations of a given paper give more
prestige to the authors of that paper.
In case a paper is accepted but not published, there is a high chance that the ideas and
contents of the papers are stolen or exploited without the knowledge of the authors
themselves. Since such unpublished papers cannot be cited, other authors can exploit the
information by adding their own information to come up with other better research papers.
Therefore, it is extremely important that such unpublished material should be taken care of by
the committee. Lack of adequate security measures will cause the authors to lose their faith
on the committee’s security policies and they may stop submitting their papers in the future
[1]. Presently there are many ethical issues in the system wherein the board members often
reveal the information from the different papers submitted by the authors. They also often use
the information from valuable papers for their own research until the papers are made
available to the delegates of the conference [13]. The employees are not following the code of
ethics properly.
Presently the required levels of confidentiality, integrity as well as availability of the
papers is not available. The authors of different papers are not given the prestige and
credibility that they deserve for the original papers that they submit. Furthermore, there is no
systematized user authentication system and the access is often available to people who are
not supposed to access the papers and other important information within the system [12].
Due to the lack of a proper access control system, users with less privilege also often gain
Analysis of the problem situation:
Presently there are a number of issues in the system in the ISCSR 2020 paper review
system. Security of the papers and the maintaining the authenticity is one of the primary
concerns. The credibility and respects of the authors depend on the number of citations that
are done for the submitted papers. More number of citations of a given paper give more
prestige to the authors of that paper.
In case a paper is accepted but not published, there is a high chance that the ideas and
contents of the papers are stolen or exploited without the knowledge of the authors
themselves. Since such unpublished papers cannot be cited, other authors can exploit the
information by adding their own information to come up with other better research papers.
Therefore, it is extremely important that such unpublished material should be taken care of by
the committee. Lack of adequate security measures will cause the authors to lose their faith
on the committee’s security policies and they may stop submitting their papers in the future
[1]. Presently there are many ethical issues in the system wherein the board members often
reveal the information from the different papers submitted by the authors. They also often use
the information from valuable papers for their own research until the papers are made
available to the delegates of the conference [13]. The employees are not following the code of
ethics properly.
Presently the required levels of confidentiality, integrity as well as availability of the
papers is not available. The authors of different papers are not given the prestige and
credibility that they deserve for the original papers that they submit. Furthermore, there is no
systematized user authentication system and the access is often available to people who are
not supposed to access the papers and other important information within the system [12].
Due to the lack of a proper access control system, users with less privilege also often gain
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3INFORMATION SECURITY
access to the important information of the committee and eventually breaching the privacy of
the research papers [2]. The website lacks adequate security features, leading to the
vulnerability of being hacked by the hackers at any point in time.
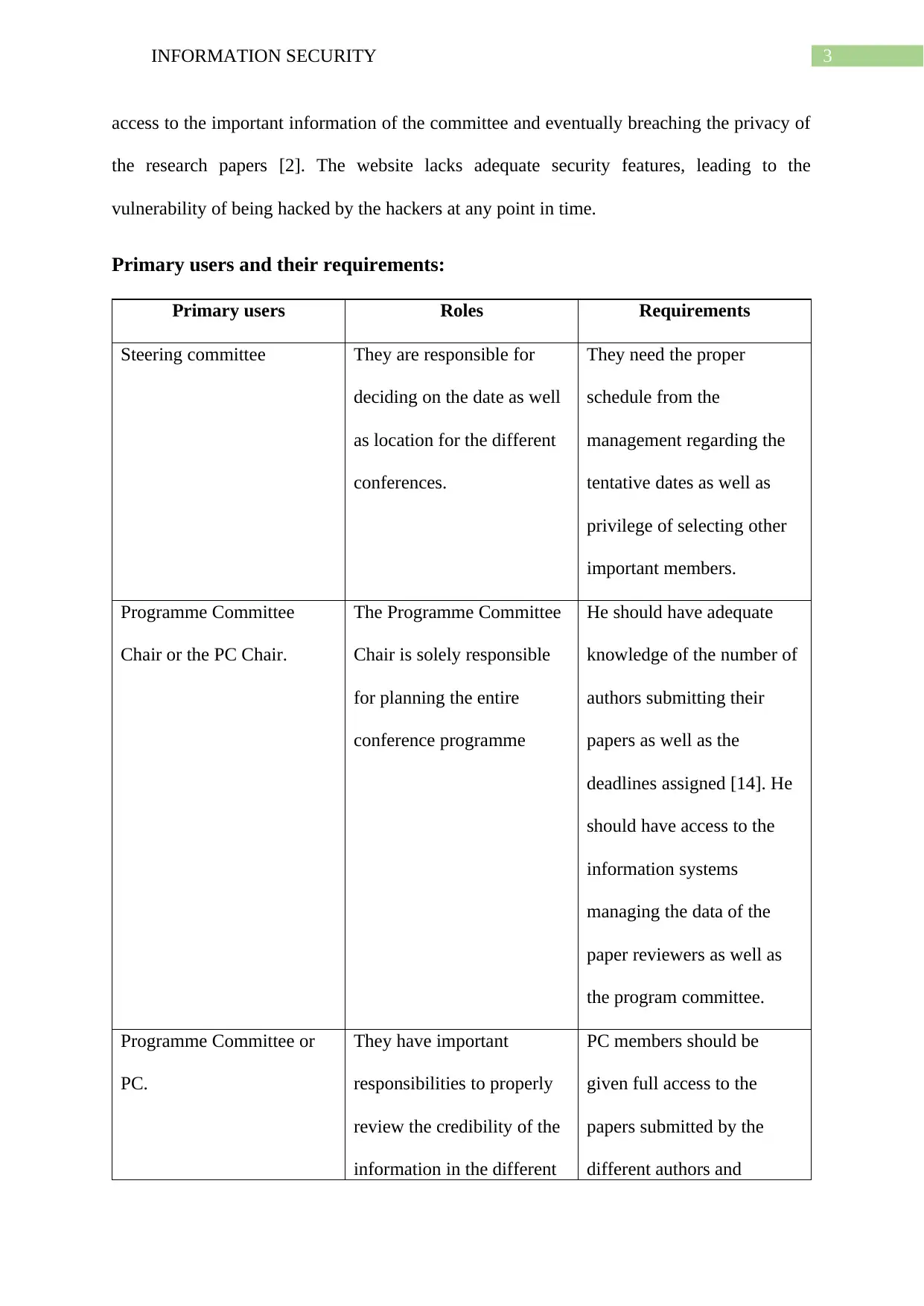
Primary users and their requirements:
Primary users Roles Requirements
Steering committee They are responsible for
deciding on the date as well
as location for the different
conferences.
They need the proper
schedule from the
management regarding the
tentative dates as well as
privilege of selecting other
important members.
Programme Committee
Chair or the PC Chair.
The Programme Committee
Chair is solely responsible
for planning the entire
conference programme
He should have adequate
knowledge of the number of
authors submitting their
papers as well as the
deadlines assigned [14]. He
should have access to the
information systems
managing the data of the
paper reviewers as well as
the program committee.
Programme Committee or
PC.
They have important
responsibilities to properly
review the credibility of the
information in the different
PC members should be
given full access to the
papers submitted by the
different authors and
access to the important information of the committee and eventually breaching the privacy of
the research papers [2]. The website lacks adequate security features, leading to the
vulnerability of being hacked by the hackers at any point in time.
Primary users and their requirements:
Primary users Roles Requirements
Steering committee They are responsible for
deciding on the date as well
as location for the different
conferences.
They need the proper
schedule from the
management regarding the
tentative dates as well as
privilege of selecting other
important members.
Programme Committee
Chair or the PC Chair.
The Programme Committee
Chair is solely responsible
for planning the entire
conference programme
He should have adequate
knowledge of the number of
authors submitting their
papers as well as the
deadlines assigned [14]. He
should have access to the
information systems
managing the data of the
paper reviewers as well as
the program committee.
Programme Committee or
PC.
They have important
responsibilities to properly
review the credibility of the
information in the different
PC members should be
given full access to the
papers submitted by the
different authors and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
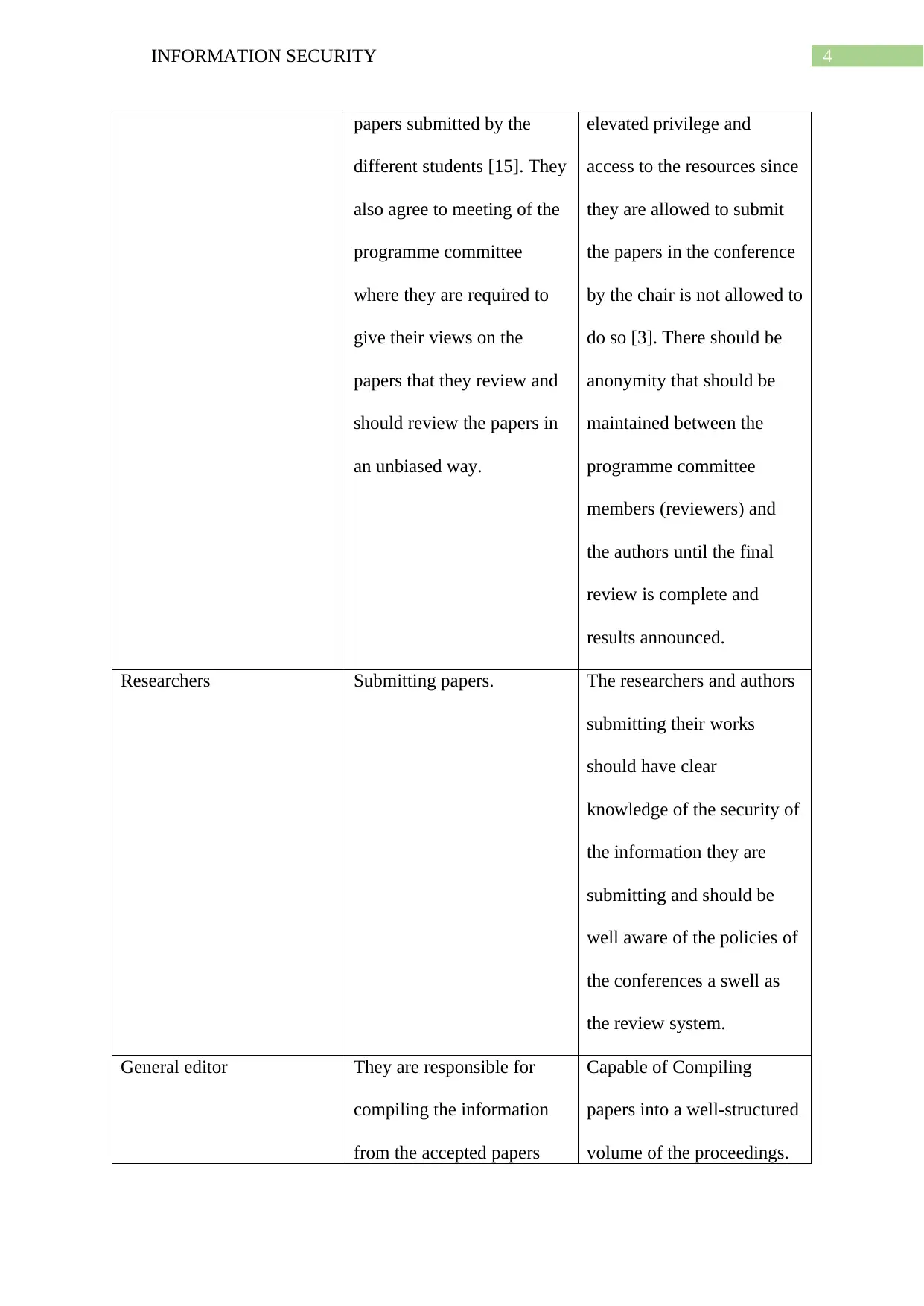
4INFORMATION SECURITY
papers submitted by the
different students [15]. They
also agree to meeting of the
programme committee
where they are required to
give their views on the
papers that they review and
should review the papers in
an unbiased way.
elevated privilege and
access to the resources since
they are allowed to submit
the papers in the conference
by the chair is not allowed to
do so [3]. There should be
anonymity that should be
maintained between the
programme committee
members (reviewers) and
the authors until the final
review is complete and
results announced.
Researchers Submitting papers. The researchers and authors
submitting their works
should have clear
knowledge of the security of
the information they are
submitting and should be
well aware of the policies of
the conferences a swell as
the review system.
General editor They are responsible for
compiling the information
from the accepted papers
Capable of Compiling
papers into a well-structured
volume of the proceedings.
papers submitted by the
different students [15]. They
also agree to meeting of the
programme committee
where they are required to
give their views on the
papers that they review and
should review the papers in
an unbiased way.
elevated privilege and
access to the resources since
they are allowed to submit
the papers in the conference
by the chair is not allowed to
do so [3]. There should be
anonymity that should be
maintained between the
programme committee
members (reviewers) and
the authors until the final
review is complete and
results announced.
Researchers Submitting papers. The researchers and authors
submitting their works
should have clear
knowledge of the security of
the information they are
submitting and should be
well aware of the policies of
the conferences a swell as
the review system.
General editor They are responsible for
compiling the information
from the accepted papers
Capable of Compiling
papers into a well-structured
volume of the proceedings.

5INFORMATION SECURITY
into a well-structured
volume of the proceedings.
It is turned into a book that
contain all the accepted
papers.
Managing of unclaimed
paper so that it is not
misused by any other author.
Figure 1: Tabular description the primary users and their responsibilities.
Assets to be protected:
Many important assets have to be protected within the conference. Information
security and its confidentiality has to be ensured by the committee. Some of the important
assets that has to be protected are the paper titles as well as the abstracts [16]. The list of the
authors as well as their affiliation should be protected that can be later used to reveal the
identity of the authors at the time of the final conference. The provision of the author to edit
and modify their texts and their rights have to be protected until the papers are announced in
the final conference and the papers are published [4]. The Programme Committee members
can only view the list of the authors who submit the papers but not their paper titles. They do
not get to know the author of the papers they are reviewing therefore it is of utmost
importance that this information is properly secured by the management and adequate two-
way anonymity between the authors and the reviewers is maintained. Any additional
feedbacks or comments, which are only visible to the chair of the committee or even the
reviewers [5]. However, it should be ensured by the security strategies that this information is
not visible to the authors of the papers that are reviewed. Even though the code of ethics can
be assumed to be followed, there are high chances that the committee members will want to
into a well-structured
volume of the proceedings.
It is turned into a book that
contain all the accepted
papers.
Managing of unclaimed
paper so that it is not
misused by any other author.
Figure 1: Tabular description the primary users and their responsibilities.
Assets to be protected:
Many important assets have to be protected within the conference. Information
security and its confidentiality has to be ensured by the committee. Some of the important
assets that has to be protected are the paper titles as well as the abstracts [16]. The list of the
authors as well as their affiliation should be protected that can be later used to reveal the
identity of the authors at the time of the final conference. The provision of the author to edit
and modify their texts and their rights have to be protected until the papers are announced in
the final conference and the papers are published [4]. The Programme Committee members
can only view the list of the authors who submit the papers but not their paper titles. They do
not get to know the author of the papers they are reviewing therefore it is of utmost
importance that this information is properly secured by the management and adequate two-
way anonymity between the authors and the reviewers is maintained. Any additional
feedbacks or comments, which are only visible to the chair of the committee or even the
reviewers [5]. However, it should be ensured by the security strategies that this information is
not visible to the authors of the papers that are reviewed. Even though the code of ethics can
be assumed to be followed, there are high chances that the committee members will want to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY
know the reviewers of their papers or with whom a CoI is associated. Therefore, this
information also has to be ensured to be protected by the committee.
Possible vulnerabilities and threats:
There are many threats faced by the authors in the process of submission of their
original works. That has to be taken care by the ISCSR 2020 paper review system. According
to the basic copyright law anything created by the authors are owned by them [17]. In spite of
the fact that there are exceptions as well as rules and regulations for the authors while
submitting their papers to the committee, they still have full control over their own materials.
However, as authors they have complete rights over the graphics as well as images in order to
enhance the story of their discussions. It should also be ensured that the authors use the brand
names as well as trademarks for the works that they submit [6]. There should also be
protection against infringement. The most important threat is the implication of the training
procedures of the personnel of the conference in order to promote and inculcate the proper
use as well as non-infringement of others rights. This includes “due diligence” author
inquiries as well as verification of the research background being carried out by the authors.
The papers submitted by the authors are available to the program committee in case
they are accepted but still not published. There are high chanced that their ideas are stolen at
that time [18]. In addition, there are high chances that the authors have internal/external
connection with the COI’s or the reviewers themselves and they can bribe them in order to
get their papers selected etc. [7]. There are also chances that the different personnel in the
conference misuse the resources and they are sold in the external market without the
knowledge of the authors. The authors of the accepted papers have to do the necessary
changes, the amended papers need to have their names as well as affiliations, and it has to be
submitted before a deadline. If the authors fail to do so, the papers will be rejected. There is a
know the reviewers of their papers or with whom a CoI is associated. Therefore, this
information also has to be ensured to be protected by the committee.
Possible vulnerabilities and threats:
There are many threats faced by the authors in the process of submission of their
original works. That has to be taken care by the ISCSR 2020 paper review system. According
to the basic copyright law anything created by the authors are owned by them [17]. In spite of
the fact that there are exceptions as well as rules and regulations for the authors while
submitting their papers to the committee, they still have full control over their own materials.
However, as authors they have complete rights over the graphics as well as images in order to
enhance the story of their discussions. It should also be ensured that the authors use the brand
names as well as trademarks for the works that they submit [6]. There should also be
protection against infringement. The most important threat is the implication of the training
procedures of the personnel of the conference in order to promote and inculcate the proper
use as well as non-infringement of others rights. This includes “due diligence” author
inquiries as well as verification of the research background being carried out by the authors.
The papers submitted by the authors are available to the program committee in case
they are accepted but still not published. There are high chanced that their ideas are stolen at
that time [18]. In addition, there are high chances that the authors have internal/external
connection with the COI’s or the reviewers themselves and they can bribe them in order to
get their papers selected etc. [7]. There are also chances that the different personnel in the
conference misuse the resources and they are sold in the external market without the
knowledge of the authors. The authors of the accepted papers have to do the necessary
changes, the amended papers need to have their names as well as affiliations, and it has to be
submitted before a deadline. If the authors fail to do so, the papers will be rejected. There is a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
great chance that the amended papers are misused at this transition phase of time [8].
Therefore, it is the responsibility of the committee to ensure that the risks as well as possible
vulnerabilities are taken care once the authors submit their papers. In the process of accepting
as well as rejecting a paper, at least two reviewers should strongly agree or disagree with the
submitted papers respectively. In this process, there are high chances that the results of the
two reviewers are manipulated.
Security policy for threats and vulnerabilities:
Providing Confidentiality:
- Enabling TLS/SSL and HTTPS.
- Critical data should be strongly encrypted, especially personal information of the
authors [9]. Simple passwords should not be used and advanced encryption techniques
such as hash plus salt can be used.
Providing Integrity:
- Implementation of tools such as WebSafe as well as WAF in order to limit the
capability of nefarious users to corrupt important data.
- Automatic application testing can provide quick notification as soon as it detects any
change implemented in the applications.
Providing Availability:
- Mitigation services that use DDoS help in blocking network attacks [19]. It can also
help in cost cutting since it eliminates the additional charges.
- Usage of WAF as well as DDoS protection techniques in order to prevent layer 7 or
application-level attacks.
- Encryption is also one of the primary techniques to prevent the attack of DDoS as it
will assist in send an encrypted message that can only be decrypted using the unique
great chance that the amended papers are misused at this transition phase of time [8].
Therefore, it is the responsibility of the committee to ensure that the risks as well as possible
vulnerabilities are taken care once the authors submit their papers. In the process of accepting
as well as rejecting a paper, at least two reviewers should strongly agree or disagree with the
submitted papers respectively. In this process, there are high chances that the results of the
two reviewers are manipulated.
Security policy for threats and vulnerabilities:
Providing Confidentiality:
- Enabling TLS/SSL and HTTPS.
- Critical data should be strongly encrypted, especially personal information of the
authors [9]. Simple passwords should not be used and advanced encryption techniques
such as hash plus salt can be used.
Providing Integrity:
- Implementation of tools such as WebSafe as well as WAF in order to limit the
capability of nefarious users to corrupt important data.
- Automatic application testing can provide quick notification as soon as it detects any
change implemented in the applications.
Providing Availability:
- Mitigation services that use DDoS help in blocking network attacks [19]. It can also
help in cost cutting since it eliminates the additional charges.
- Usage of WAF as well as DDoS protection techniques in order to prevent layer 7 or
application-level attacks.
- Encryption is also one of the primary techniques to prevent the attack of DDoS as it
will assist in send an encrypted message that can only be decrypted using the unique

8INFORMATION SECURITY
key which can be similar as that of the user in case of symmetric encryption and can
differ if asymmetric encryption is used.
User authentication:
API keys can be used for this in which unique value are assigned to every first time
users, which signifies that the users are known [10]. On trying to re-enter into the systems,
the unique keys are used to prove that they are the same users as earlier. Furthermore,
encryption of the cryptographic technology can also be used for the user identification. In the
discussed scenario, the user will be provided with a unique key that can be used for logging
into the system.
Access control scheme:
The access control scheme that can be used is explained below:
- Ownership of the information can be transferred by the authors to other users
- Authors can determine the kind of access that can be given to the conference officials
(read, write, copy, etc.)
- Repetitive authorization should lead to failure of access for the ICSCR officials.
- Special add-on as well as software plug-in’s should be required to prevent apply to an
HTTP client’s from to copying data such as information "cut and paste".
- Adoption of the firewall to prevent external interference is also one of the prominent
ways to prevent the illegal accessibility.
Website protection:
The steps that can be used to secure the website are:
- Keeping the software’s and security patches up to date.
- Network firewall techniques should be used such as DMX servers as well as network
address translation. This will help in filtering the inbound as well as outbound traffic.
key which can be similar as that of the user in case of symmetric encryption and can
differ if asymmetric encryption is used.
User authentication:
API keys can be used for this in which unique value are assigned to every first time
users, which signifies that the users are known [10]. On trying to re-enter into the systems,
the unique keys are used to prove that they are the same users as earlier. Furthermore,
encryption of the cryptographic technology can also be used for the user identification. In the
discussed scenario, the user will be provided with a unique key that can be used for logging
into the system.
Access control scheme:
The access control scheme that can be used is explained below:
- Ownership of the information can be transferred by the authors to other users
- Authors can determine the kind of access that can be given to the conference officials
(read, write, copy, etc.)
- Repetitive authorization should lead to failure of access for the ICSCR officials.
- Special add-on as well as software plug-in’s should be required to prevent apply to an
HTTP client’s from to copying data such as information "cut and paste".
- Adoption of the firewall to prevent external interference is also one of the prominent
ways to prevent the illegal accessibility.
Website protection:
The steps that can be used to secure the website are:
- Keeping the software’s and security patches up to date.
- Network firewall techniques should be used such as DMX servers as well as network
address translation. This will help in filtering the inbound as well as outbound traffic.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY
Any unnecessary inbound traffic will be blocked or redirected back to the source and
will not be allowed to enter the organizational network.
- SQL query injection must be checked from time to time.
- Passwords and error messages should be kept under a check.
- XSS attacks must be avoided and https should be used.
Suitability of proposed security controls:
The above discussed security controls will be extremely helpful for the organization.
The security patches of antivirus solutions should be ensured at all points in time. QL queries
can often be injected by the hackers in case of excessive file uploads therefore it should be
monitored by the system administrators [20]. Strong passwords will be used which are a
combination of upper case and lower case alphabets along with number and special
characters. Using HTTPS will also ensure that the website are inaccessible by the hackers and
the information available are safe and secure. Therefore, these measures will be extremely
beneficial for the organization.
Any unnecessary inbound traffic will be blocked or redirected back to the source and
will not be allowed to enter the organizational network.
- SQL query injection must be checked from time to time.
- Passwords and error messages should be kept under a check.
- XSS attacks must be avoided and https should be used.
Suitability of proposed security controls:
The above discussed security controls will be extremely helpful for the organization.
The security patches of antivirus solutions should be ensured at all points in time. QL queries
can often be injected by the hackers in case of excessive file uploads therefore it should be
monitored by the system administrators [20]. Strong passwords will be used which are a
combination of upper case and lower case alphabets along with number and special
characters. Using HTTPS will also ensure that the website are inaccessible by the hackers and
the information available are safe and secure. Therefore, these measures will be extremely
beneficial for the organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SECURITY
References:
[1]T. Peltier, Information security fundamentals.
[2]D. Death, Information Security Handbook. Packt Publishing, 2017.
[3]L. Navarro, "Information Security Risks and Managed Security Service", Information
Security Technical Report, vol. 6, no. 3, pp. 28-36, 2014. Available: 10.1016/s1363-
4127(01)00305-3.
[4]T. Sastry, "Right to Infromation as a Human Right: The Role of Supreme Court", Indian
Journal of Public Administration, vol. 55, no. 3, pp. 609-618, 2015. Available:
10.1177/0019556120090319.
[5]R. Schultz, Contemporary Issues in Ethics and Information Technology. London: Idea
Group,U.S., 2006.
Engdahl, Intellectual property rights. Detroit, MI: Greenhaven Press, 2010.
[7]S. McJohn, Intellectual property.
Pollaud-Dulian, The internet and authors' rights, 3rd ed. London: Sweet & Maxwell, 2014.
[9]J. Han, "Intellectual Property Rights and Performance of Start-ups", Intellectual Property
Rights: Open Access, vol. 4, no. 2, 2016. Available: 10.4172/2375-4516.1000156.
[10]J. Broderick, "Information Security Risk Management — When Should It be Managed?",
Information Security Technical Report, vol. 6, no. 3, pp. 12-18, 2014. Available:
10.1016/s1363-4127(01)00303-x.
[11]D. Death, Information Security Handbook. Packt Publishing, 2017.
References:
[1]T. Peltier, Information security fundamentals.
[2]D. Death, Information Security Handbook. Packt Publishing, 2017.
[3]L. Navarro, "Information Security Risks and Managed Security Service", Information
Security Technical Report, vol. 6, no. 3, pp. 28-36, 2014. Available: 10.1016/s1363-
4127(01)00305-3.
[4]T. Sastry, "Right to Infromation as a Human Right: The Role of Supreme Court", Indian
Journal of Public Administration, vol. 55, no. 3, pp. 609-618, 2015. Available:
10.1177/0019556120090319.
[5]R. Schultz, Contemporary Issues in Ethics and Information Technology. London: Idea
Group,U.S., 2006.
Engdahl, Intellectual property rights. Detroit, MI: Greenhaven Press, 2010.
[7]S. McJohn, Intellectual property.
Pollaud-Dulian, The internet and authors' rights, 3rd ed. London: Sweet & Maxwell, 2014.
[9]J. Han, "Intellectual Property Rights and Performance of Start-ups", Intellectual Property
Rights: Open Access, vol. 4, no. 2, 2016. Available: 10.4172/2375-4516.1000156.
[10]J. Broderick, "Information Security Risk Management — When Should It be Managed?",
Information Security Technical Report, vol. 6, no. 3, pp. 12-18, 2014. Available:
10.1016/s1363-4127(01)00303-x.
[11]D. Death, Information Security Handbook. Packt Publishing, 2017.

11INFORMATION SECURITY
[12]J. Bayuk, J. Healey, P. Rohmeyer, M. Sachs, J. Schmidt and J. Weiss, Cyber Security
Policy Guidebook. Somerset: Wiley, 2012.
[13]N. Brügger, "The Archived Website and Website Philology", Nordicom Review, vol. 29,
no. 2, pp. 155-175, 2015. Available: 10.1515/nor-2017-0183.
[14]D. Sherry, Legal issues of data security. Boston, MA (Ten Winter Pl., Boston 02108-
4751): Massachusetts Continuing Legal Education, 2015.
[15]G. Wilshusen, Information security. [Washington, D.C.]: U.S. Govt. Accountability
Office, 2015.
Your Bibliography: [16]K. Grant, R. Hackney and D. Edgar, Strategic information systems
management. Andover: Cengage Learning, 2017.
[17]P. Pawlak, Countering hybrid threats. European Union, 2017.
[18]J. Kizza and F. Kizza, Securing the information infrastructure. Hershey, PA: Cybertech
Pub., 2016.
[19]G. Suarez de Tangil and E. Palomar, Advances in security information management.
Hauppauge, New York: Nova Science Publishers, Inc., 2018.
[20]H. Bleuel, L. Schultz-Wild, T. Andreassen and J. Fearns, Authors' rights. Munich: EWC,
2014.
[12]J. Bayuk, J. Healey, P. Rohmeyer, M. Sachs, J. Schmidt and J. Weiss, Cyber Security
Policy Guidebook. Somerset: Wiley, 2012.
[13]N. Brügger, "The Archived Website and Website Philology", Nordicom Review, vol. 29,
no. 2, pp. 155-175, 2015. Available: 10.1515/nor-2017-0183.
[14]D. Sherry, Legal issues of data security. Boston, MA (Ten Winter Pl., Boston 02108-
4751): Massachusetts Continuing Legal Education, 2015.
[15]G. Wilshusen, Information security. [Washington, D.C.]: U.S. Govt. Accountability
Office, 2015.
Your Bibliography: [16]K. Grant, R. Hackney and D. Edgar, Strategic information systems
management. Andover: Cengage Learning, 2017.
[17]P. Pawlak, Countering hybrid threats. European Union, 2017.
[18]J. Kizza and F. Kizza, Securing the information infrastructure. Hershey, PA: Cybertech
Pub., 2016.
[19]G. Suarez de Tangil and E. Palomar, Advances in security information management.
Hauppauge, New York: Nova Science Publishers, Inc., 2018.
[20]H. Bleuel, L. Schultz-Wild, T. Andreassen and J. Fearns, Authors' rights. Munich: EWC,
2014.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





