Comprehensive Analysis: CIA Triad, Biometrics & Encryption in InfoSec
VerifiedAdded on 2023/06/13
|14
|3843
|70
Homework Assignment
AI Summary
This assignment provides a detailed exploration of key concepts in information security. It begins with an analysis of the CIA triad (Confidentiality, Integrity, Availability) in the context of ATM security, discussing PIN numbers, data encryption, and the importance of training. It then delves into a scenario involving a compromised ATM, calculating the possible PIN attempts using permutation techniques and highlighting security limitations. The assignment further examines the advantages and disadvantages of biometric authentication systems, addressing concerns like security breaches, false acceptance rates, and mapping challenges, while proposing solutions such as multifactor authentication. It also discusses the implications of false negatives in biometric systems and their impact on institutional security. Finally, the assignment includes practical examples of encryption and decryption using Caesar and substitution ciphers. This document is available on Desklib, which provides a range of study tools and solved assignments for students.

Running head: INFORMATION SECURITY
Information Security
Name of the Student
Name of the University
Author’s Note
Information Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY
Table of Contents
Answer to question 1:......................................................................................................................2
Answer to question 2:......................................................................................................................2
Answer to question 3:......................................................................................................................3
Answer to question 4:......................................................................................................................5
Answer to question 5a:....................................................................................................................6
Answer to question number 5b).......................................................................................................7
References......................................................................................................................................10
INFORMATION SECURITY
Table of Contents
Answer to question 1:......................................................................................................................2
Answer to question 2:......................................................................................................................2
Answer to question 3:......................................................................................................................3
Answer to question 4:......................................................................................................................5
Answer to question 5a:....................................................................................................................6
Answer to question number 5b).......................................................................................................7
References......................................................................................................................................10

2
INFORMATION SECURITY
Answer to question 1:
CIA triad is considered as a guide that mainly includes the concept of confidentiality,
integrity as well as availability that can be used in order to take appropriate measure in context to
information security (Ali & Afzal, 2017). The ATM is currently used as a daily use technology
where security plays an important role. The pin number can be considered as one of the security
aspect, which generally helps in restricting access to unauthorized users (Mosenia, & Jha, 2017).
Integrity mainly focusses on the concept of maintenance, accuracy as well as trustworthiness that
is mainly related to the data over the entire life cycle of the project. Availability concept mainly
deals with concept of data presence that is needed by the user in all kinds of situation.
It is identified that data must be safeguarded taking number of consideration like natural
disaster and fire. The data of the customers must be provided highest priority and therefore
backup system must be present in order to keep the data safe during any critical situation
(Onuchowska & de Vreede, 2018). There can be a situation where the ATM card holder can lost
the card and another unauthorized person can access the account. In this type of scenario,
authentication plays an important role (Jain, Jain & Kapil, 2016).The ATM pin can be
considered as one of the security number through which people can engage in transaction. It is
observed that in order to safeguard data, it is also important to provide proper training to the
people who are generally involved within the technological advancement as well as
implementation of new security tools within the system.
The concept of data encryption is one of the common method, which can be implemented
in order to maintain proper confidentiality. Confidentiality of the customers or users is found as
one of the most critical elements in context to user’s security (Sagar et al., 2015). In addition to
this, it is analyzed that with the help of CIA guide the privacy as well as security of the users as
well as customers in context to data access can be preserved successfully.
Answer to question 2:
In this question, we are provided with the situation where a thief can easily broke into
the ATM machine by utilizing the screwdriver. The thief was able to jam the card reader by
breaking five keys from the machine keypad. The thief generally have to halt with the procedure
of breaking as an customer generally approached for utilizing the ATM. The customer enters the
INFORMATION SECURITY
Answer to question 1:
CIA triad is considered as a guide that mainly includes the concept of confidentiality,
integrity as well as availability that can be used in order to take appropriate measure in context to
information security (Ali & Afzal, 2017). The ATM is currently used as a daily use technology
where security plays an important role. The pin number can be considered as one of the security
aspect, which generally helps in restricting access to unauthorized users (Mosenia, & Jha, 2017).
Integrity mainly focusses on the concept of maintenance, accuracy as well as trustworthiness that
is mainly related to the data over the entire life cycle of the project. Availability concept mainly
deals with concept of data presence that is needed by the user in all kinds of situation.
It is identified that data must be safeguarded taking number of consideration like natural
disaster and fire. The data of the customers must be provided highest priority and therefore
backup system must be present in order to keep the data safe during any critical situation
(Onuchowska & de Vreede, 2018). There can be a situation where the ATM card holder can lost
the card and another unauthorized person can access the account. In this type of scenario,
authentication plays an important role (Jain, Jain & Kapil, 2016).The ATM pin can be
considered as one of the security number through which people can engage in transaction. It is
observed that in order to safeguard data, it is also important to provide proper training to the
people who are generally involved within the technological advancement as well as
implementation of new security tools within the system.
The concept of data encryption is one of the common method, which can be implemented
in order to maintain proper confidentiality. Confidentiality of the customers or users is found as
one of the most critical elements in context to user’s security (Sagar et al., 2015). In addition to
this, it is analyzed that with the help of CIA guide the privacy as well as security of the users as
well as customers in context to data access can be preserved successfully.
Answer to question 2:
In this question, we are provided with the situation where a thief can easily broke into
the ATM machine by utilizing the screwdriver. The thief was able to jam the card reader by
breaking five keys from the machine keypad. The thief generally have to halt with the procedure
of breaking as an customer generally approached for utilizing the ATM. The customer enters the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY
card however was unable to take out the card from the ATM machine and therefore ran for some
kind of help. In the same time, the thief tried number of ways so that the pin of the customer can
be discovered so that the thief can be able to steal large amount of money from the ATM
machine.
The maximum number of pins that can be entered by the thief before discovering the
password of the ATM can be calculated by utilizing the concept of permutation technique. It is
identified that total number of keypad within an ATM machine generally ranges from 0 to 10.
Now in this specific situation, the thief has already broken five keys and therefore only five keys
are available for making input within the ATM machine. The ATM pin is mainly made up of
four digits so after breaking the five keys, the thief will enter the four digit pin within the
remaining five breaks which are generally available. The permutation is calculated below:
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
Therefore, total number of possible outcome for the thief is 120. However, as per the
security of the users is concerned, a user can only enter pin maximum of three times. However,
after three wrong inputs within the ATM as Pin, the card will be blocked. Therefore, it is
analyzed that the thief can enter the pin maximum 3 times and after the third trail, the card will
automatically get blocked.
Answer to question 3:
There are number of advantages of using biometric authentication system however in
spite of the advantages, number of issues as well as problems are also encountered due to the
utilization of the system and due to the challenges as well as issues people may reluctant to use
the system (Pagnin & Mitrokotsa, 2017). There are number of reasons due to which people may
be reluctant to utilize biometrics. The reasons are as follows:
Security: Security is one of the main reason due to which people are reluctant to utilize
biometric systems. Over the years, the attacks that are made on the biometric systems has been
considered successful. In the system of biometrics, various kinds of data as well as information
related with people are stored within the database (Johnston & Weiss, 2015). The information
that are stored in the system generally includes phone number, address as well as other personal
INFORMATION SECURITY
card however was unable to take out the card from the ATM machine and therefore ran for some
kind of help. In the same time, the thief tried number of ways so that the pin of the customer can
be discovered so that the thief can be able to steal large amount of money from the ATM
machine.
The maximum number of pins that can be entered by the thief before discovering the
password of the ATM can be calculated by utilizing the concept of permutation technique. It is
identified that total number of keypad within an ATM machine generally ranges from 0 to 10.
Now in this specific situation, the thief has already broken five keys and therefore only five keys
are available for making input within the ATM machine. The ATM pin is mainly made up of
four digits so after breaking the five keys, the thief will enter the four digit pin within the
remaining five breaks which are generally available. The permutation is calculated below:
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
Therefore, total number of possible outcome for the thief is 120. However, as per the
security of the users is concerned, a user can only enter pin maximum of three times. However,
after three wrong inputs within the ATM as Pin, the card will be blocked. Therefore, it is
analyzed that the thief can enter the pin maximum 3 times and after the third trail, the card will
automatically get blocked.
Answer to question 3:
There are number of advantages of using biometric authentication system however in
spite of the advantages, number of issues as well as problems are also encountered due to the
utilization of the system and due to the challenges as well as issues people may reluctant to use
the system (Pagnin & Mitrokotsa, 2017). There are number of reasons due to which people may
be reluctant to utilize biometrics. The reasons are as follows:
Security: Security is one of the main reason due to which people are reluctant to utilize
biometric systems. Over the years, the attacks that are made on the biometric systems has been
considered successful. In the system of biometrics, various kinds of data as well as information
related with people are stored within the database (Johnston & Weiss, 2015). The information
that are stored in the system generally includes phone number, address as well as other personal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY
details of the users. If the personal details that are stored within the database is hacked by an
outsider then it will generally create privacy as well as security related issues. The identity of a
user can be misused by undertaking some of the illegal activities that further leads to the creation
of an unethical event (Kremic, 2017).
False acceptance or false entry: Various kinds of technology related errors occurs
within the biometric system. One such issue is false entry and false acceptance. The biometric
systems generally does not have proper idea or logic related to user’s identity. Failure rates are
so high that is as one of the critical consideration for the biometric system (Deokar & Wakode,
2017). The biometric system mainly categorizes the failure rates of the system into false
acceptance and false rejection. The failure rates are helpful in analyzing the ways that can be
used for verifying each of the kind of users against various characteristics, which is mainly
register against them.
Mapping related challenges: Mapping system is as one of the significant aspect of
biometric. It is found that mapping within the biometric system is mainly done with the help of
either information or with the help of fingerprint (Dere, Gurjar, & Sipna, 2016). It is identified
that in some of the cases, information as well as data of the users are successfully stored within
the system however the system is unable to recognize the user, which generally result, is late
entry of data of that particular person.
Objections countered:
The objections can be countered by following methods that are as follows:
Multifactor authentication: Multifactor authentication is considered as a method in
which number of processes are generally implemented in order to encounter large number of
problems as well as challenges. Multifactor authentication is very much helpful in identifying
users by either with their usernames, passwords as well as with their fingerprint (Holz & Knaust,
2015). In this specific method, each of the user generally have a particular name or password,
which is generally activated to certain number of persons. This particular aspect helps in
checking the security successfully.
Gradient biometric team: Gradient biometric is one of the particular domain of
biometric that have achieved success in that specific field. As per the organization, it is very
INFORMATION SECURITY
details of the users. If the personal details that are stored within the database is hacked by an
outsider then it will generally create privacy as well as security related issues. The identity of a
user can be misused by undertaking some of the illegal activities that further leads to the creation
of an unethical event (Kremic, 2017).
False acceptance or false entry: Various kinds of technology related errors occurs
within the biometric system. One such issue is false entry and false acceptance. The biometric
systems generally does not have proper idea or logic related to user’s identity. Failure rates are
so high that is as one of the critical consideration for the biometric system (Deokar & Wakode,
2017). The biometric system mainly categorizes the failure rates of the system into false
acceptance and false rejection. The failure rates are helpful in analyzing the ways that can be
used for verifying each of the kind of users against various characteristics, which is mainly
register against them.
Mapping related challenges: Mapping system is as one of the significant aspect of
biometric. It is found that mapping within the biometric system is mainly done with the help of
either information or with the help of fingerprint (Dere, Gurjar, & Sipna, 2016). It is identified
that in some of the cases, information as well as data of the users are successfully stored within
the system however the system is unable to recognize the user, which generally result, is late
entry of data of that particular person.
Objections countered:
The objections can be countered by following methods that are as follows:
Multifactor authentication: Multifactor authentication is considered as a method in
which number of processes are generally implemented in order to encounter large number of
problems as well as challenges. Multifactor authentication is very much helpful in identifying
users by either with their usernames, passwords as well as with their fingerprint (Holz & Knaust,
2015). In this specific method, each of the user generally have a particular name or password,
which is generally activated to certain number of persons. This particular aspect helps in
checking the security successfully.
Gradient biometric team: Gradient biometric is one of the particular domain of
biometric that have achieved success in that specific field. As per the organization, it is very

5
INFORMATION SECURITY
much important to consider three of the most important aspect including availability, comfort as
well as safety of the users. IT is necessary to include three most significant concepts in context to
biometric in order to achieve desired level of security within the system (Lumini & Nanni,
2017). Access of particular customer’s database is generally done in order to deliver information
as well as data during need however in some of the situations, linkage of the network as well as
information generally leads to failure to access permission and it is ultimate concept that is
related with biometric.
Answer to question 4:
A false negative generally occurs in a situation in which the user of biometric does not
get easy access to biometric location. There can be number of situations due to inappropriate data
storage or due to some technical related challenges (Haque, Nasrollahi & Moeslund, 2015). In
most of the cases it is identified that false identity person generally gets proper identity that
results in idea of miss identity. It is found that in the first situation, person’s identity is not
known but in major of the cases, it can generally create number of challenges as well as issues as
the identity of a person can generally get restricted due to number of activities. In the second
situation, the concept that is considered is the loss of identity (Choi, Lee & Yoon, 2016). It is
found that other person can easily utilize that identity and get involved within some illegal
activities by utilizing identity of some other person. This generally creates number of issues as
well as challenges and thus it is very much necessary to consider it. It is necessary to have more
security-based system with appropriate level of service.
False negative also depends on a situation in which the owners are not allowed to access
the information and such situations generally creates issues for individuals while accessing
information as well as data (Wayman, 2015). On institutional level, if the entire server
infrastructure is shut down then the users have to restore the entire services due to which an
organization can losses thousands of dollars of revenue. In addition to this, if a biometric system
does not recognizes an individual then it does not lose large amount of money but also the
organizational reputation. When a biometric system is utilized as one of the main kind of
authentication, it generally helps in providing huge number of assets then it will generally hinder
the assets (Hadid et al, 2015). In many of the cases, fingerprint is used in order to access the
assets. It is generally done as a proof by the lawmakers, which would further helps in punishing
INFORMATION SECURITY
much important to consider three of the most important aspect including availability, comfort as
well as safety of the users. IT is necessary to include three most significant concepts in context to
biometric in order to achieve desired level of security within the system (Lumini & Nanni,
2017). Access of particular customer’s database is generally done in order to deliver information
as well as data during need however in some of the situations, linkage of the network as well as
information generally leads to failure to access permission and it is ultimate concept that is
related with biometric.
Answer to question 4:
A false negative generally occurs in a situation in which the user of biometric does not
get easy access to biometric location. There can be number of situations due to inappropriate data
storage or due to some technical related challenges (Haque, Nasrollahi & Moeslund, 2015). In
most of the cases it is identified that false identity person generally gets proper identity that
results in idea of miss identity. It is found that in the first situation, person’s identity is not
known but in major of the cases, it can generally create number of challenges as well as issues as
the identity of a person can generally get restricted due to number of activities. In the second
situation, the concept that is considered is the loss of identity (Choi, Lee & Yoon, 2016). It is
found that other person can easily utilize that identity and get involved within some illegal
activities by utilizing identity of some other person. This generally creates number of issues as
well as challenges and thus it is very much necessary to consider it. It is necessary to have more
security-based system with appropriate level of service.
False negative also depends on a situation in which the owners are not allowed to access
the information and such situations generally creates issues for individuals while accessing
information as well as data (Wayman, 2015). On institutional level, if the entire server
infrastructure is shut down then the users have to restore the entire services due to which an
organization can losses thousands of dollars of revenue. In addition to this, if a biometric system
does not recognizes an individual then it does not lose large amount of money but also the
organizational reputation. When a biometric system is utilized as one of the main kind of
authentication, it generally helps in providing huge number of assets then it will generally hinder
the assets (Hadid et al, 2015). In many of the cases, fingerprint is used in order to access the
assets. It is generally done as a proof by the lawmakers, which would further helps in punishing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
INFORMATION SECURITY
the person who is found guilty. In addition to validation as well as authentication, biometric
system is used in order to determine the login as well as log out time.
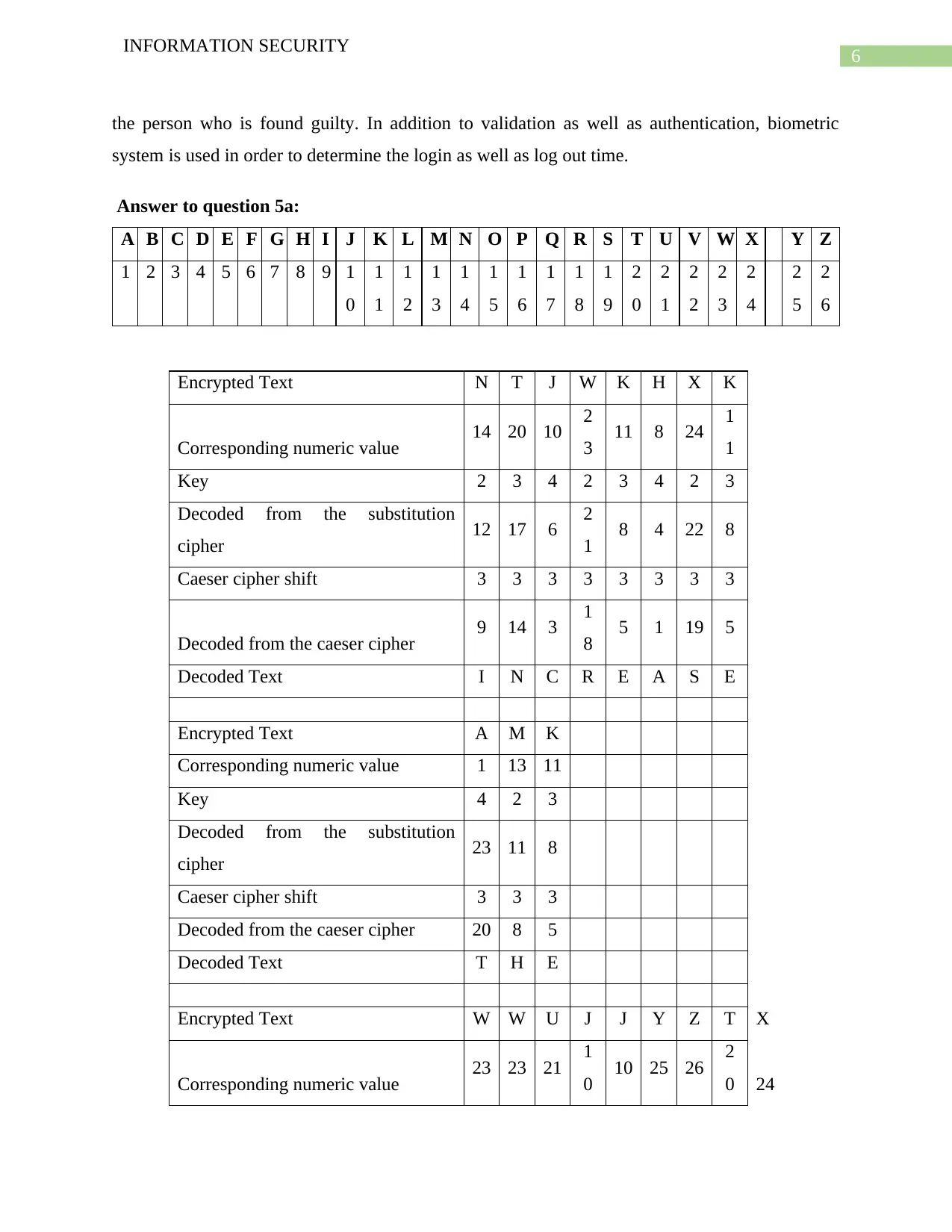
Answer to question 5a:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 2
3 11 8 24 1
1
Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 2
1 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 1
8 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution
cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 1
0 10 25 26 2
0 24
INFORMATION SECURITY
the person who is found guilty. In addition to validation as well as authentication, biometric
system is used in order to determine the login as well as log out time.
Answer to question 5a:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 1
0
1
1
1
2
1
3
1
4
1
5
1
6
1
7
1
8
1
9
2
0
2
1
2
2
2
3
2
4
2
5
2
6
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 2
3 11 8 24 1
1
Key 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 12 17 6 2
1 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 1
8 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution
cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 1
0 10 25 26 2
0 24
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INFORMATION SECURITY
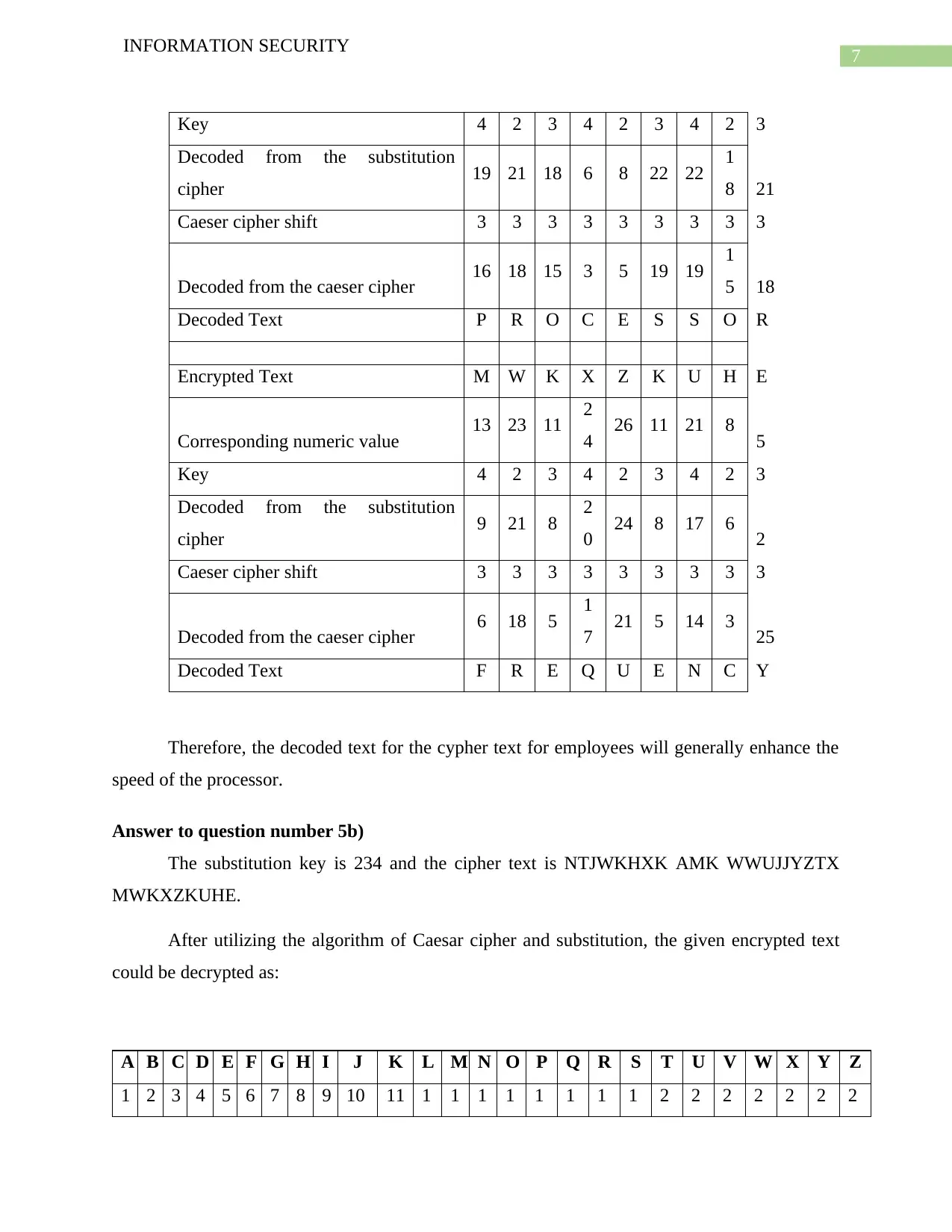
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 19 21 18 6 8 22 22 1
8 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 16 18 15 3 5 19 19 1
5 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 2
4 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 9 21 8 2
0 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5 1
7 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decoded text for the cypher text for employees will generally enhance the
speed of the processor.
Answer to question number 5b)
The substitution key is 234 and the cipher text is NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE.
After utilizing the algorithm of Caesar cipher and substitution, the given encrypted text
could be decrypted as:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2
INFORMATION SECURITY
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 19 21 18 6 8 22 22 1
8 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 16 18 15 3 5 19 19 1
5 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 2
4 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution
cipher 9 21 8 2
0 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5 1
7 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decoded text for the cypher text for employees will generally enhance the
speed of the processor.
Answer to question number 5b)
The substitution key is 234 and the cipher text is NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE.
After utilizing the algorithm of Caesar cipher and substitution, the given encrypted text
could be decrypted as:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 1 1 1 1 1 1 1 1 2 2 2 2 2 2 2
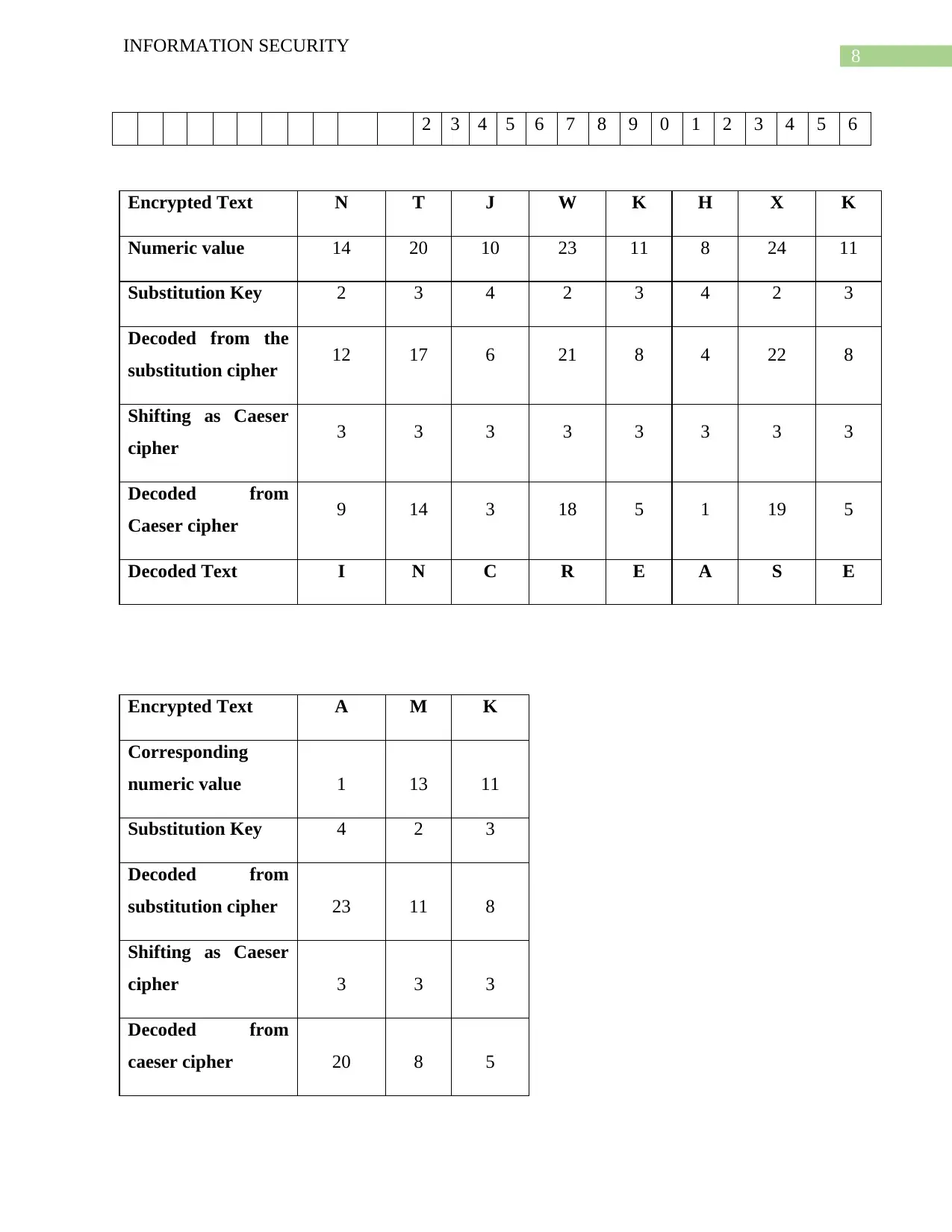
8
INFORMATION SECURITY
2 3 4 5 6 7 8 9 0 1 2 3 4 5 6
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the
substitution cipher 12 17 6 21 8 4 22 8
Shifting as Caeser
cipher 3 3 3 3 3 3 3 3
Decoded from
Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding
numeric value 1 13 11
Substitution Key 4 2 3
Decoded from
substitution cipher 23 11 8
Shifting as Caeser
cipher 3 3 3
Decoded from
caeser cipher 20 8 5
INFORMATION SECURITY
2 3 4 5 6 7 8 9 0 1 2 3 4 5 6
Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Substitution Key 2 3 4 2 3 4 2 3
Decoded from the
substitution cipher 12 17 6 21 8 4 22 8
Shifting as Caeser
cipher 3 3 3 3 3 3 3 3
Decoded from
Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding
numeric value 1 13 11
Substitution Key 4 2 3
Decoded from
substitution cipher 23 11 8
Shifting as Caeser
cipher 3 3 3
Decoded from
caeser cipher 20 8 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
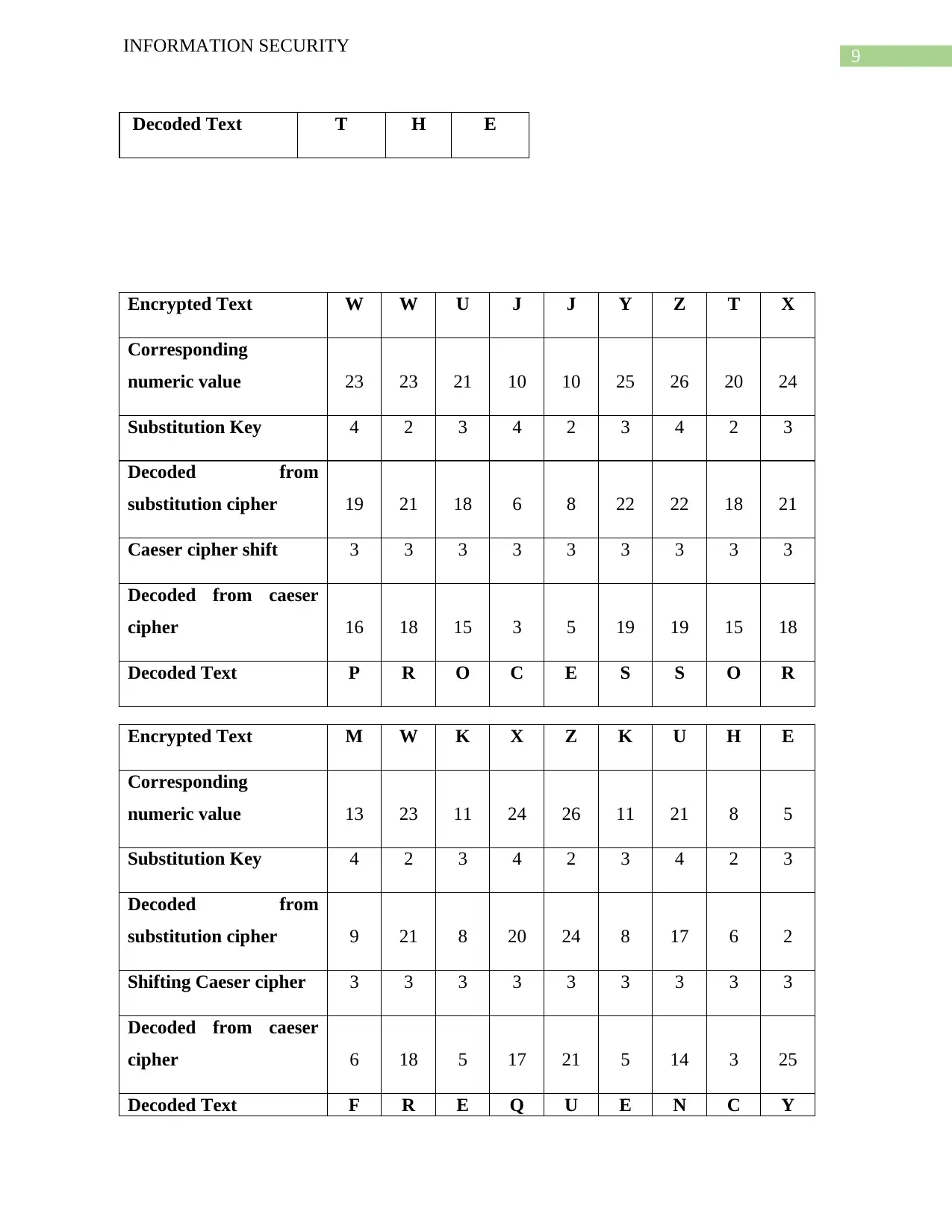
9
INFORMATION SECURITY
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding
numeric value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from
substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser
cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding
numeric value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from
substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser
cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
INFORMATION SECURITY
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding
numeric value 23 23 21 10 10 25 26 20 24
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from
substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from caeser
cipher 16 18 15 3 5 19 19 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding
numeric value 13 23 11 24 26 11 21 8 5
Substitution Key 4 2 3 4 2 3 4 2 3
Decoded from
substitution cipher 9 21 8 20 24 8 17 6 2
Shifting Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded from caeser
cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INFORMATION SECURITY
Therefore, the decrypted text for the given text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is INCREASE THE PROCESSOR FREQUENCY
INFORMATION SECURITY
Therefore, the decrypted text for the given text of NTJWKHXK AMK WWUJJYZTX
MWKXZKUHE is INCREASE THE PROCESSOR FREQUENCY

11
INFORMATION SECURITY
References
Ali, A., & Afzal, M. M. (2017). Database Security: Threats and Solutions. International Journal
of Engineering Inventions, 6(2), 25-27.
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption. Proc. USEC, 1-2.
Choi, H. S., Lee, B., & Yoon, S. (2016). Biometric authentication using noisy
electrocardiograms acquired by mobile sensors. IEEE Access, 4, 1266-1273.
Deokar, S. R., & Wakode, J. S. (2017). Coal Mine Safety Monitoring and Alerting System.
Dere, S. N., Gurjar, A. A., & Sipna, C. O. E. T. (2016). Human Identification Using Palm-Vein
Images: A New Trend in Biometrics. International Journal of Engineering Science, 2298.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the security
concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
Fernandez, A., & Alexander, K. M. (2016). Data Privacy and Confidentiality. iURBAN:
Intelligent Urban Energy Tool, 35.
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack:
an evaluation methodology and lessons learned. IEEE Signal Processing
Magazine, 32(5), 20-30.
Haque, M. A., Nasrollahi, K., & Moeslund, T. B. (2015, June). Heartbeat signal from facial
video for biometric recognition. In Scandinavian Conference on Image Analysis (pp. 165-
174). Springer, Cham.
Havenetidis, K., Paradisis, G. P., Karanasiou, I. S., & Tsekouras, G. J. (2015). An investigation
of an Artificial Neural Network method for personal identification using kinematic
INFORMATION SECURITY
References
Ali, A., & Afzal, M. M. (2017). Database Security: Threats and Solutions. International Journal
of Engineering Inventions, 6(2), 25-27.
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption. Proc. USEC, 1-2.
Choi, H. S., Lee, B., & Yoon, S. (2016). Biometric authentication using noisy
electrocardiograms acquired by mobile sensors. IEEE Access, 4, 1266-1273.
Deokar, S. R., & Wakode, J. S. (2017). Coal Mine Safety Monitoring and Alerting System.
Dere, S. N., Gurjar, A. A., & Sipna, C. O. E. T. (2016). Human Identification Using Palm-Vein
Images: A New Trend in Biometrics. International Journal of Engineering Science, 2298.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the security
concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
Fernandez, A., & Alexander, K. M. (2016). Data Privacy and Confidentiality. iURBAN:
Intelligent Urban Energy Tool, 35.
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack:
an evaluation methodology and lessons learned. IEEE Signal Processing
Magazine, 32(5), 20-30.
Haque, M. A., Nasrollahi, K., & Moeslund, T. B. (2015, June). Heartbeat signal from facial
video for biometric recognition. In Scandinavian Conference on Image Analysis (pp. 165-
174). Springer, Cham.
Havenetidis, K., Paradisis, G. P., Karanasiou, I. S., & Tsekouras, G. J. (2015). An investigation
of an Artificial Neural Network method for personal identification using kinematic
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





