Information Security: Analyzing CIA Triad, Biometrics & Encryption
VerifiedAdded on 2023/06/13
|10
|1770
|281
Homework Assignment
AI Summary
This assignment solution covers fundamental concepts in information security, including the CIA triad (Confidentiality, Integrity, Availability) and its application in ATM security. It addresses the challenges and issues associated with biometric authentication systems, such as sensor vulnerabilities, communication security, accuracy, and privacy. Furthermore, the assignment includes a practical problem involving permutation calculations for ATM pin cracking and demonstrates Caesar cipher decryption techniques. The document provides detailed explanations and solutions, referencing relevant sources and adhering to APA referencing style. Desklib offers this and many other solved assignments to help students in their studies.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................2
Answer to Question 3:.........................................................................................................3
Answer to question 4:..........................................................................................................4
Answer to Question 5:.........................................................................................................5
References............................................................................................................................7
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................2
Answer to Question 3:.........................................................................................................3
Answer to question 4:..........................................................................................................4
Answer to Question 5:.........................................................................................................5
References............................................................................................................................7

2INFORMATION SECURITY
Answer to Question 1:
CIA stands for confidentiality, integrity and availability is nothing but a guide which can
be used for measuring the security of information. Information security generally focus on the
idea or logic that how information security can be easily used (Betab & Sandhu, 2014). CIA triad
can be easily used as a tool for or guide for securing information system and various kinds of
networks related to it. CIA is nothing but a model which can be used for achievement of
information security. There are large number of factors behind CIA triad like confidentiality,
integrity and lastly availability. In ATM machine confidentiality can be easily used for protection
of large number of information from any kind of unauthorized access. CIA Triad mainly relates
to information security which is used for having control on access to the protected kinds of
information (Khan, Hasan & Xu, 2015). CIA triad mainly requires proper kinds of information
security measures for monitoring and controlling with authorized use and access of transmission
of information. The availability is CIA Triad can be easily used for situation which can be used
for focusing on information which is needed in right amount. Availability is nothing but a
maintaining of all kinds of components of information system which tend to work properly
(Karovaliya et al., 2015). The goal of integrity is nothing but a condition in which information
can be easily kept accurate and consistent until and unless certain number of authorization are
made. In various kinds of ATM machine confidentiality, integrity and availability is considered
to be basic kinds of goals of information security.
Answer to Question 2:
The entire keypad of a ATM machine generally has ten number of keys (0-9). As directed
in the question the thief has broken five number of keys from the keypad. The pin number of a
ATM machine generally consist of four number so the thief is bound to select the number from
Answer to Question 1:
CIA stands for confidentiality, integrity and availability is nothing but a guide which can
be used for measuring the security of information. Information security generally focus on the
idea or logic that how information security can be easily used (Betab & Sandhu, 2014). CIA triad
can be easily used as a tool for or guide for securing information system and various kinds of
networks related to it. CIA is nothing but a model which can be used for achievement of
information security. There are large number of factors behind CIA triad like confidentiality,
integrity and lastly availability. In ATM machine confidentiality can be easily used for protection
of large number of information from any kind of unauthorized access. CIA Triad mainly relates
to information security which is used for having control on access to the protected kinds of
information (Khan, Hasan & Xu, 2015). CIA triad mainly requires proper kinds of information
security measures for monitoring and controlling with authorized use and access of transmission
of information. The availability is CIA Triad can be easily used for situation which can be used
for focusing on information which is needed in right amount. Availability is nothing but a
maintaining of all kinds of components of information system which tend to work properly
(Karovaliya et al., 2015). The goal of integrity is nothing but a condition in which information
can be easily kept accurate and consistent until and unless certain number of authorization are
made. In various kinds of ATM machine confidentiality, integrity and availability is considered
to be basic kinds of goals of information security.
Answer to Question 2:
The entire keypad of a ATM machine generally has ten number of keys (0-9). As directed
in the question the thief has broken five number of keys from the keypad. The pin number of a
ATM machine generally consist of four number so the thief is bound to select the number from
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
remaining five keys which is available to him. For overcoming the problem and taking right
decision in this situation we are making use of permutation and combination from mathematics.
5p4 = 5! / (5-4)! =5! /1! = 5*4*3*2*1/1 =120/1 =120.
So the thief is making 120 number of attempts with respect to situation which is provided
to him. The answer has been found by making use of permutation technique from mathematics.
Answer to Question 3:
Biometric authentication can be easily defined as the identification of individual for
which is totally based on distinguishing of physiological and behaviors relate to characteristics.
Biometric identification is considered to be more reliable and it is more capable of traditional
based token and knowledge depended technologies which is mainly used for differentiation
between authorized and fraudulent kinds of person (Onyesolu & Okpala, 2017). There are large
number of issues which can be easily encountered is biometric systems. Various kinds of attacks
generally exist to have an unauthorized kinds of access to a particular kinds of situation which
can be used for gaining unauthorized kinds of access to a system which is protected by a
biometric authentication. There are large number of issues which can be dealt with biometric
authentication.
Biometrics is generally considered to be associated with security and biometric system is
considered to be reasonably secure and full of trust. There are some kinds of issues in biometric
security. The issues are
Proper kinds of sensors and unauthorized acquisition of samples of biometric.
Proper kinds of communication between various sensors, matchers and database
of biometric.
remaining five keys which is available to him. For overcoming the problem and taking right
decision in this situation we are making use of permutation and combination from mathematics.
5p4 = 5! / (5-4)! =5! /1! = 5*4*3*2*1/1 =120/1 =120.
So the thief is making 120 number of attempts with respect to situation which is provided
to him. The answer has been found by making use of permutation technique from mathematics.
Answer to Question 3:
Biometric authentication can be easily defined as the identification of individual for
which is totally based on distinguishing of physiological and behaviors relate to characteristics.
Biometric identification is considered to be more reliable and it is more capable of traditional
based token and knowledge depended technologies which is mainly used for differentiation
between authorized and fraudulent kinds of person (Onyesolu & Okpala, 2017). There are large
number of issues which can be easily encountered is biometric systems. Various kinds of attacks
generally exist to have an unauthorized kinds of access to a particular kinds of situation which
can be used for gaining unauthorized kinds of access to a system which is protected by a
biometric authentication. There are large number of issues which can be dealt with biometric
authentication.
Biometrics is generally considered to be associated with security and biometric system is
considered to be reasonably secure and full of trust. There are some kinds of issues in biometric
security. The issues are
Proper kinds of sensors and unauthorized acquisition of samples of biometric.
Proper kinds of communication between various sensors, matchers and database
of biometric.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
Issues related to accuracy.
Issues of various kinds of speeds
Issues of cost like biometrics equipment’s are generally considered to be
expensive in nature.
There are certain number of issues like privacy.
Issues in Authentication or Identification
Authentication is nothing but a verification of a user identity who they claim to be. For
this possible case the user generally provides a list or range of users (Koteswari & Paul, 2017).
After that authentication mechanism is mainly used for authentication kinds of mechanism for
analyzing the identity of an individual. In comparison identification is not all compared with any
kinds of identity. Instead of that speed is provided with credentials.
Failure rates
Failure rates are generally considered to be in the configuration and day to day of running
of a biometric system (Pathak et al., 2015). There are mainly two kinds of failure rates like
acceptance rates, false rejection rates.
Answer to question 4:
False negative rates are nothing but a situation in which a particular kind of biometric
fails to recognize the authenticity of a particular person (Mondal, Deb & Adnan, 2017). Based on
a particular kind of situation there can be consequences like personals which makes use of a
particular kind of parameter for accessing or safeguarding of a whole kind of a thing (Singh &
Kaur, 2016). On the level of organization, it can easily shut down the whole kind of
infrastructure for safeguarding the whole thing. On the level of organization, it can easily shut
Issues related to accuracy.
Issues of various kinds of speeds
Issues of cost like biometrics equipment’s are generally considered to be
expensive in nature.
There are certain number of issues like privacy.
Issues in Authentication or Identification
Authentication is nothing but a verification of a user identity who they claim to be. For
this possible case the user generally provides a list or range of users (Koteswari & Paul, 2017).
After that authentication mechanism is mainly used for authentication kinds of mechanism for
analyzing the identity of an individual. In comparison identification is not all compared with any
kinds of identity. Instead of that speed is provided with credentials.
Failure rates
Failure rates are generally considered to be in the configuration and day to day of running
of a biometric system (Pathak et al., 2015). There are mainly two kinds of failure rates like
acceptance rates, false rejection rates.
Answer to question 4:
False negative rates are nothing but a situation in which a particular kind of biometric
fails to recognize the authenticity of a particular person (Mondal, Deb & Adnan, 2017). Based on
a particular kind of situation there can be consequences like personals which makes use of a
particular kind of parameter for accessing or safeguarding of a whole kind of a thing (Singh &
Kaur, 2016). On the level of organization, it can easily shut down the whole kind of
infrastructure for safeguarding the whole thing. On the level of organization, it can easily shut
5INFORMATION SECURITY
down the whole kind of kinds of infrastructure. It can easily shut down the various kinds of
things which is needed by data centers which can be used for restoring various kinds of services.
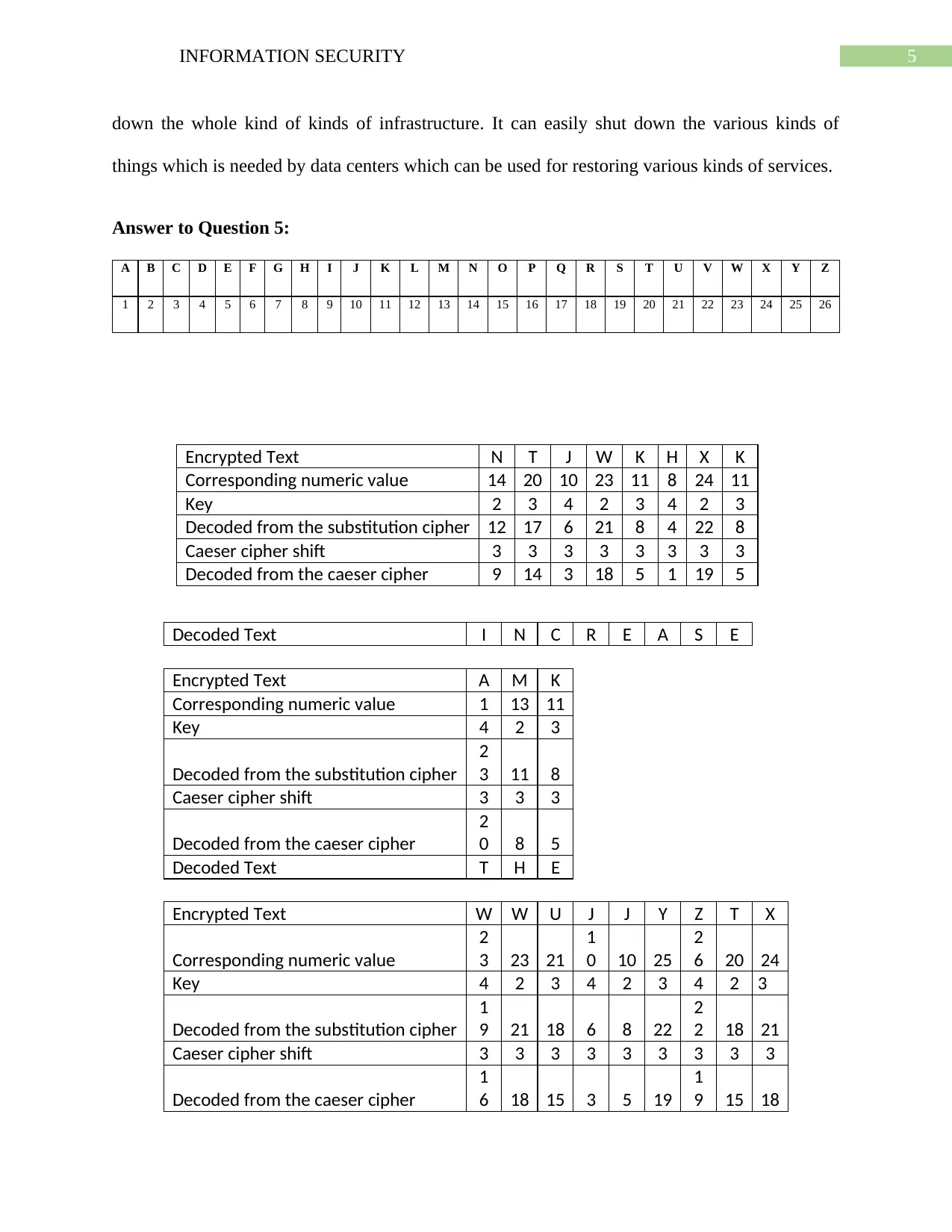
Answer to Question 5:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
down the whole kind of kinds of infrastructure. It can easily shut down the various kinds of
things which is needed by data centers which can be used for restoring various kinds of services.
Answer to Question 5:
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INFORMATION SECURITY
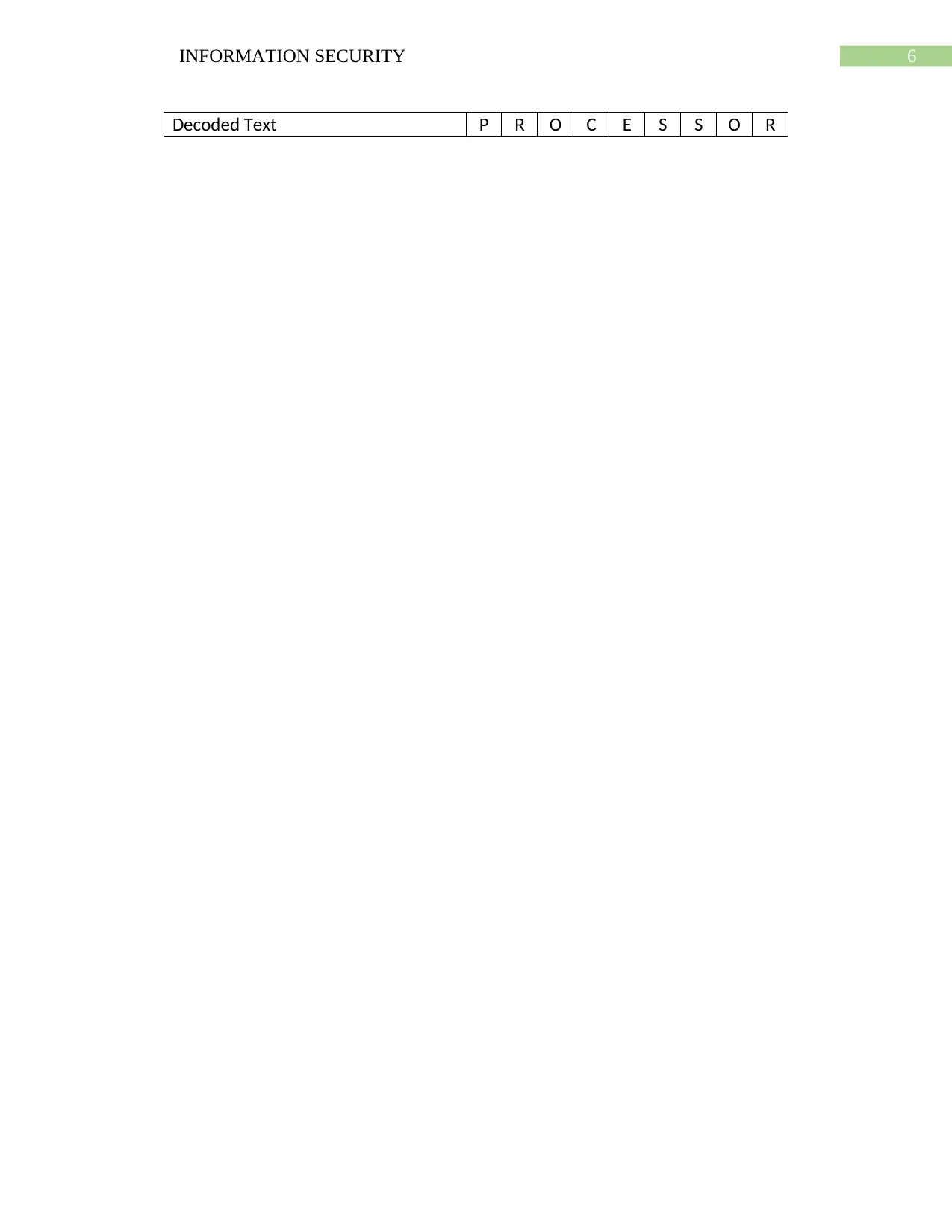
Decoded Text P R O C E S S O R
Decoded Text P R O C E S S O R
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7INFORMATION SECURITY
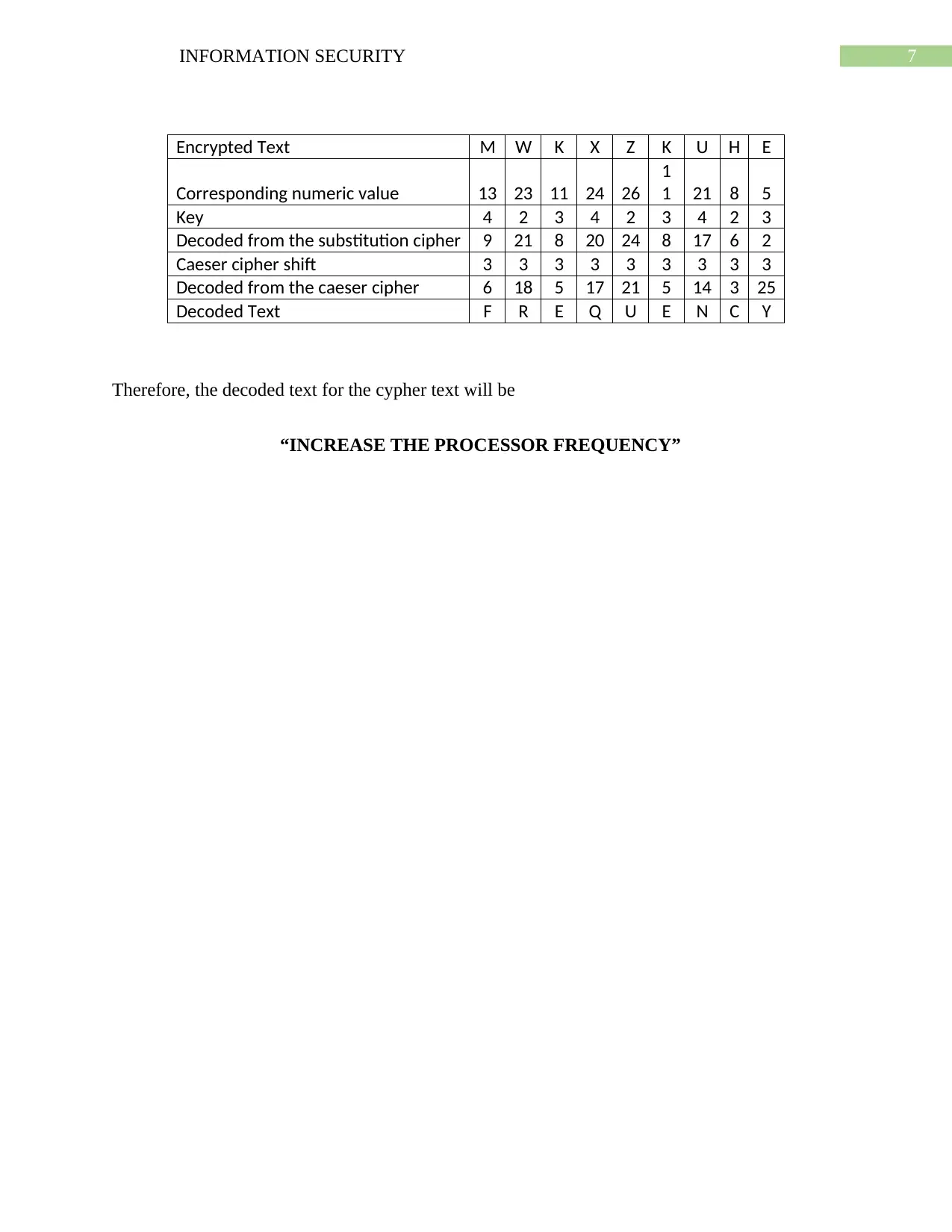
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26
1
1 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decoded text for the cypher text will be
“INCREASE THE PROCESSOR FREQUENCY”
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26
1
1 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5 17 21 5 14 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decoded text for the cypher text will be
“INCREASE THE PROCESSOR FREQUENCY”

8INFORMATION SECURITY
References
Betab, G., & Sandhu, R. K. (2014). Fingerprints in Automated Teller Machine-A
Survey. International Journal of Engineering and Advanced Technology (IJEAT) ISSN:
2249, 8958.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45, 390-
396.
Khan, R., Hasan, R., & Xu, J. (2015, March). SEPIA: Secure-PIN-authentication-as-a-service for
ATM using mobile and wearable devices. In Mobile Cloud Computing, Services, and
Engineering (MobileCloud), 2015 3rd IEEE International Conference on (pp. 41-50).
IEEE.
Koteswari, S., & Paul, P. J. (2017). A Survey: Fusion of Fingerprint and Iris for ATM services.
Mondal, P. C., Deb, R., & Adnan, M. N. (2017, September). On reinforcing automatic teller
machine (ATM) transaction authentication security process by imposing behavioral
biometrics. In Advances in Electrical Engineering (ICAEE), 2017 4th International
Conference on (pp. 369-372). IEEE.
Onyesolu, M. O., & Okpala, A. C. (2017). Improving Security Using a Three-Tier
Authentication for Automated Teller Machine (ATM). International Journal of
Computer Network and Information Security, 9(10), 50.
Pathak, S. K., Pathak, S. K., Mishra, M. K., Kesharwani, L., & Gupta, A. K. (2015). Automated
Teller Machine (ATM) Frauds and Security. EDITORIAL BOARD, 192.
References
Betab, G., & Sandhu, R. K. (2014). Fingerprints in Automated Teller Machine-A
Survey. International Journal of Engineering and Advanced Technology (IJEAT) ISSN:
2249, 8958.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45, 390-
396.
Khan, R., Hasan, R., & Xu, J. (2015, March). SEPIA: Secure-PIN-authentication-as-a-service for
ATM using mobile and wearable devices. In Mobile Cloud Computing, Services, and
Engineering (MobileCloud), 2015 3rd IEEE International Conference on (pp. 41-50).
IEEE.
Koteswari, S., & Paul, P. J. (2017). A Survey: Fusion of Fingerprint and Iris for ATM services.
Mondal, P. C., Deb, R., & Adnan, M. N. (2017, September). On reinforcing automatic teller
machine (ATM) transaction authentication security process by imposing behavioral
biometrics. In Advances in Electrical Engineering (ICAEE), 2017 4th International
Conference on (pp. 369-372). IEEE.
Onyesolu, M. O., & Okpala, A. C. (2017). Improving Security Using a Three-Tier
Authentication for Automated Teller Machine (ATM). International Journal of
Computer Network and Information Security, 9(10), 50.
Pathak, S. K., Pathak, S. K., Mishra, M. K., Kesharwani, L., & Gupta, A. K. (2015). Automated
Teller Machine (ATM) Frauds and Security. EDITORIAL BOARD, 192.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY
Singh, S., & Kaur, S. (2016). Enhancing ATM Security Using Fusion of Biometric
Techniques. IITM Journal of Management and IT, 7(1), 79-82.
Singh, S., & Kaur, S. (2016). Enhancing ATM Security Using Fusion of Biometric
Techniques. IITM Journal of Management and IT, 7(1), 79-82.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




