Information Security: Confidentiality, Integrity, and Availability
VerifiedAdded on 2023/06/14
|6
|2253
|395
AI Summary
This article discusses the concepts of confidentiality, integrity, and availability in information security. It also covers biometric authentication, false negative and false positive biometric authentication, and transportation cipher decryption. The article provides examples and explanations to help readers understand the topics.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INFORMATION SECURITY
Information Security
Name of Student-
Name of University-
Author’s Note-
Information Security
Name of Student-
Name of University-
Author’s Note-
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1INFORMATION SECURITY
Answer for Question 1:
Example of Confidentiality:
Confidentiality is used to give protection to the information from the ATM card by some unauthorized systems or users.
For transaction in ATM, the card has to be physically present and the ATM pin has to be known by the user for successful
transaction (Luca et al., 2015).
The system of ATM card has to inbuilt the confidentiality of the card by encrypting pin and card of the user while transmission
is taking place.
There are mainly two types of breaches in confidentiality. One of the breach in confidentiality may take place when there some
other person looks over the details of the ATM while entering the pin. And the other breach in confidentiality occurs if the
details of the employees in a company may stolen
There is necessity of confidentiality to use ATM for maintaining people’s privacy and the personal information of the user.
Example of Integrity:
Data integrity involves that data cannot be changed or altered without access of the user.
There can be violation of integrity if the user deliberately or accidentally deletes files or changes the content of the details of
atm (Thomas, Vinod & Robinson, 2017).
The professionals who are responsible for information security can find some ways for implementing control over the errors of
integrity.
Example of Availability:
The availability of information states that the information that are needed to complete the transaction should be available with
the user.
The computing systems that are needed to process, store information should be secured, and the data in them must be
protected.
To ensure the data service, the denial-of-service attacks is basically prevented.
Answer for Question 2:
According to the scenario given in the question, a thief broke in an ATM and was successful in jamming the card reader of the
ATM machine. The thief was also successful in breaking five keys from the dial pad. While the thief was on his way to break other
keys as well, he had to stop as a customer approached the ATM for transaction (Ghosh et al., 2017). The customer was successful in
taking out cash from the ATM but the card was jammed because the thief had jammed the card reader. While the customer went out to
fetch help from others, the thief tried to find out the pin of the card. With the four keys that were working, the thief can find out many
possibilities of the entering the keys. The total number of possibilities that the thief can enter is
5P4 = 5!/(5 - 4)! = 5!/4! = 120 ways by which the thief can detect the pin of the card.
However, all the ATMs have many security factors. There are some limitations that thief can enter the pin for the card. An
ATM machine allows the user to enter the pin for maximum 3 times (Memon, 2017). After three wrong attempts, the card will be
blocked.
Answer for Question 1:
Example of Confidentiality:
Confidentiality is used to give protection to the information from the ATM card by some unauthorized systems or users.
For transaction in ATM, the card has to be physically present and the ATM pin has to be known by the user for successful
transaction (Luca et al., 2015).
The system of ATM card has to inbuilt the confidentiality of the card by encrypting pin and card of the user while transmission
is taking place.
There are mainly two types of breaches in confidentiality. One of the breach in confidentiality may take place when there some
other person looks over the details of the ATM while entering the pin. And the other breach in confidentiality occurs if the
details of the employees in a company may stolen
There is necessity of confidentiality to use ATM for maintaining people’s privacy and the personal information of the user.
Example of Integrity:
Data integrity involves that data cannot be changed or altered without access of the user.
There can be violation of integrity if the user deliberately or accidentally deletes files or changes the content of the details of
atm (Thomas, Vinod & Robinson, 2017).
The professionals who are responsible for information security can find some ways for implementing control over the errors of
integrity.
Example of Availability:
The availability of information states that the information that are needed to complete the transaction should be available with
the user.
The computing systems that are needed to process, store information should be secured, and the data in them must be
protected.
To ensure the data service, the denial-of-service attacks is basically prevented.
Answer for Question 2:
According to the scenario given in the question, a thief broke in an ATM and was successful in jamming the card reader of the
ATM machine. The thief was also successful in breaking five keys from the dial pad. While the thief was on his way to break other
keys as well, he had to stop as a customer approached the ATM for transaction (Ghosh et al., 2017). The customer was successful in
taking out cash from the ATM but the card was jammed because the thief had jammed the card reader. While the customer went out to
fetch help from others, the thief tried to find out the pin of the card. With the four keys that were working, the thief can find out many
possibilities of the entering the keys. The total number of possibilities that the thief can enter is
5P4 = 5!/(5 - 4)! = 5!/4! = 120 ways by which the thief can detect the pin of the card.
However, all the ATMs have many security factors. There are some limitations that thief can enter the pin for the card. An
ATM machine allows the user to enter the pin for maximum 3 times (Memon, 2017). After three wrong attempts, the card will be
blocked.

2INFORMATION SECURITY
Answer for Question 3:
1. The first advantage is that the users do not have to enter their usernames and their passwords as a login credentials for log in.
The use of bio-metric is a replacement of the password and user-name of the user and is considered as the alternative of entering
password (Barbosa & Silva, 2015). The biometric authentication is also used to enhance the on boarding and methods to know the
customers well. For a brand, the biometric is the most advantageous way to improve the experience of the user.
2. The biometric is a problem solving way for remembering the password for the users. To remember the password is a great
problem for the users and biometric solves that problem for many service providers and different online enterprise (Bhagavatula et al.,
2015). For authentication, the passwords that are used by the users are not always strong and those data has a possibility of facing a
data breach. Biometric helps to solve the problem of password forgetting.
3. The biometric authentication establishes the accountability for the users. After the biometric is implemented, the result of
biometric gives a solid activity of the audit trail so that the accountability can be established (Kim et al., 2015). All the transaction
done by the user is recorded and is documented clearly by the user that are associated with the biometrics. This actually reduces the
misuse of the system and protects the data from being hacked.
Answer for Question 4:
The false negative biometric authentication is a rate in authentication where an authorized user or a person is basically rejected
so that they cannot access the system. This generally happens when the users do not find the biometric data of the user in the database
and rejects their access even if the user is an authenticated one (Chen, Pande & Mohapatra, 2014). All the authentication techniques
should have low false negative data or false rejection rate because if false negative exists in authentication, then the users will become
frustrated. The false positive biometric authentication is basically a process which accepts an unauthorized user as an authorized one.
This mainly occurs when the biometric data of a person matches to some extent of the data of authorized user in the database and the
person is not authorized (Ciuffo & Weiss, 2017). The rate of acceptance is done for a security measure so that the prevention can be
done from falsifying the data. The rate of false negative generally ranges between 0.00066 % up to 1.0 %, which is more than the rate
of false acceptance.
Answer for Question 5:
One way by which the transportation cipher can be decrypted is the columnar transposition of decryption method. The
columnar transposition method generally has a security for the transposition security that has extra benefit to utilize the keyword. The
columnar transposition method is comparatively easier than other methods of decryption and also offers an effect of better mixing
when compared to railfence cipher (Alsaadi, 2015). The main advantage of columnar transposition compared to substitution method of
encrypting is that the algorithms can be used more than one time. For an example, the columnar transposition of decrypting the cipher
can be used twice on plaintext. The keyword that is used first can be used both the times or some different key can be used for
applying the algorithm the second time.
The process to decipher an encrypted text can be done mainly in two steps. The two steps are:
To decipher the text, the user normally has to work on the length of the columns by dividing the length by key length.
After the first step is done, the message is then written in the columns again and then the key retransforms the columns again.
Answer for Question 3:
1. The first advantage is that the users do not have to enter their usernames and their passwords as a login credentials for log in.
The use of bio-metric is a replacement of the password and user-name of the user and is considered as the alternative of entering
password (Barbosa & Silva, 2015). The biometric authentication is also used to enhance the on boarding and methods to know the
customers well. For a brand, the biometric is the most advantageous way to improve the experience of the user.
2. The biometric is a problem solving way for remembering the password for the users. To remember the password is a great
problem for the users and biometric solves that problem for many service providers and different online enterprise (Bhagavatula et al.,
2015). For authentication, the passwords that are used by the users are not always strong and those data has a possibility of facing a
data breach. Biometric helps to solve the problem of password forgetting.
3. The biometric authentication establishes the accountability for the users. After the biometric is implemented, the result of
biometric gives a solid activity of the audit trail so that the accountability can be established (Kim et al., 2015). All the transaction
done by the user is recorded and is documented clearly by the user that are associated with the biometrics. This actually reduces the
misuse of the system and protects the data from being hacked.
Answer for Question 4:
The false negative biometric authentication is a rate in authentication where an authorized user or a person is basically rejected
so that they cannot access the system. This generally happens when the users do not find the biometric data of the user in the database
and rejects their access even if the user is an authenticated one (Chen, Pande & Mohapatra, 2014). All the authentication techniques
should have low false negative data or false rejection rate because if false negative exists in authentication, then the users will become
frustrated. The false positive biometric authentication is basically a process which accepts an unauthorized user as an authorized one.
This mainly occurs when the biometric data of a person matches to some extent of the data of authorized user in the database and the
person is not authorized (Ciuffo & Weiss, 2017). The rate of acceptance is done for a security measure so that the prevention can be
done from falsifying the data. The rate of false negative generally ranges between 0.00066 % up to 1.0 %, which is more than the rate
of false acceptance.
Answer for Question 5:
One way by which the transportation cipher can be decrypted is the columnar transposition of decryption method. The
columnar transposition method generally has a security for the transposition security that has extra benefit to utilize the keyword. The
columnar transposition method is comparatively easier than other methods of decryption and also offers an effect of better mixing
when compared to railfence cipher (Alsaadi, 2015). The main advantage of columnar transposition compared to substitution method of
encrypting is that the algorithms can be used more than one time. For an example, the columnar transposition of decrypting the cipher
can be used twice on plaintext. The keyword that is used first can be used both the times or some different key can be used for
applying the algorithm the second time.
The process to decipher an encrypted text can be done mainly in two steps. The two steps are:
To decipher the text, the user normally has to work on the length of the columns by dividing the length by key length.
After the first step is done, the message is then written in the columns again and then the key retransforms the columns again.

3INFORMATION SECURITY
The transposition that is done by the columnar method is very easy to implement and follows a very simple technique. The
columnar transposition follows simple rules of mixing the characters of the plaintext multiple times to convert into cipher text and vice
versa in to plain text by using the key. This transposition algorithm can be combined with other ciphers and the combination follows a
strong algorithm.
The given encrypted text is-
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
The key give is 234
Using the Caesar cipher algorithm and substitution method, the encrypted text can be decrypted as
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
The Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from substitution cipher 12 17 6 21 8 4 22 8
Shifting as Caeser cipher 3 3 3 3 3 3 3 3
Decoded from caeser cipher 9 14 3 18 5 1 19 5
The Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher 20 8 5
The Decoded Text T H E
The transposition that is done by the columnar method is very easy to implement and follows a very simple technique. The
columnar transposition follows simple rules of mixing the characters of the plaintext multiple times to convert into cipher text and vice
versa in to plain text by using the key. This transposition algorithm can be combined with other ciphers and the combination follows a
strong algorithm.
The given encrypted text is-
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
The key give is 234
Using the Caesar cipher algorithm and substitution method, the encrypted text can be decrypted as
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
The Encrypted Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from substitution cipher 12 17 6 21 8 4 22 8
Shifting as Caeser cipher 3 3 3 3 3 3 3 3
Decoded from caeser cipher 9 14 3 18 5 1 19 5
The Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher 20 8 5
The Decoded Text T H E
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4INFORMATION SECURITY
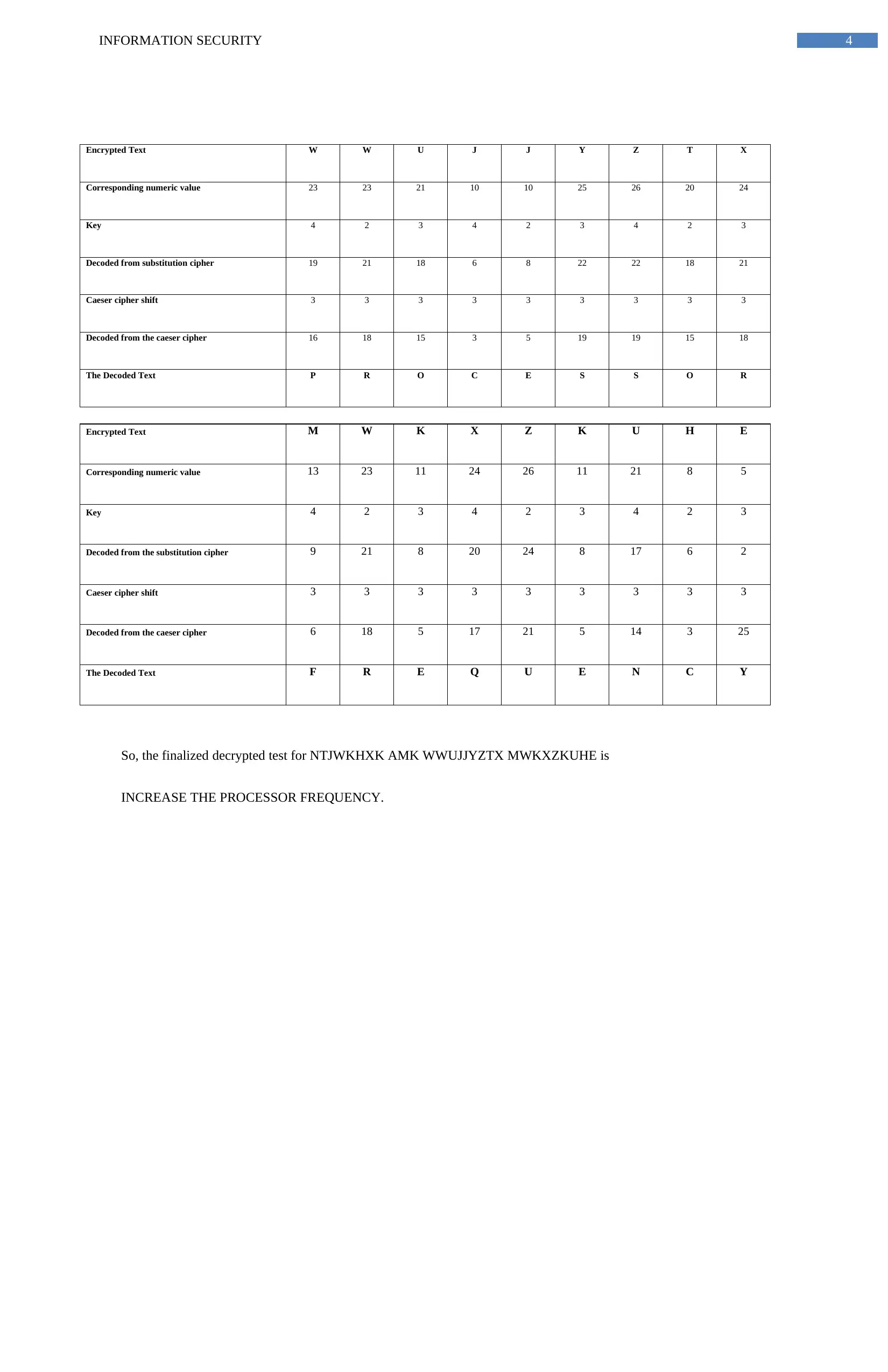
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 16 18 15 3 5 19 19 15 18
The Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5 17 21 5 14 3 25
The Decoded Text F R E Q U E N C Y
So, the finalized decrypted test for NTJWKHXK AMK WWUJJYZTX MWKXZKUHE is
INCREASE THE PROCESSOR FREQUENCY.
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from substitution cipher 19 21 18 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 16 18 15 3 5 19 19 15 18
The Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5 17 21 5 14 3 25
The Decoded Text F R E Q U E N C Y
So, the finalized decrypted test for NTJWKHXK AMK WWUJJYZTX MWKXZKUHE is
INCREASE THE PROCESSOR FREQUENCY.

5INFORMATION SECURITY
REFERENCES
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages, Disadvantages And Future Development: A
Review. International Journal Of Scientific & Technology Research, 4(8), 285-289.
Barbosa, F. G., & Silva, W. L. S. (2015, November). Support vector machines, Mel-Frequency Cepstral Coefficients and the Discrete
Cosine Transform applied on voice based biometric authentication. In SAI Intelligent Systems Conference (IntelliSys),
2015 (pp. 1032-1039). IEEE.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015). Biometric authentication on iphone and
android: Usability, perceptions, and influences on adoption. Proc. USEC, 1-2.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an enhanced biometric authentication system
for smartphones. In Proceedings of the 12th annual international conference on Mobile systems, applications, and
services (pp. 109-122). ACM.
Ciuffo, F., & Weiss, G. M. (2017, October). Smartwatch-based transcription biometrics. In Ubiquitous Computing, Electronics and
Mobile Communication Conference (UEMCON), 2017 IEEE 8th Annual (pp. 145-149). IEEE.
De Luca, A., Hang, A., Von Zezschwitz, E., & Hussmann, H. (2015, April). I feel like I'm taking selfies all day!: towards
understanding biometric authentication on smartphones. In Proceedings of the 33rd Annual ACM Conference on Human
Factors in Computing Systems (pp. 1411-1414). ACM.
Ghosh, S., Majumder, A., Goswami, J., Kumar, A., Mohanty, S. P., & Bhattacharyya, B. K. (2017). Swing-Pay: One Card Meets All
User Payment and Identity Needs: A Digital Card Module using NFC and Biometric Authentication for Peer-to-Peer
Payment. IEEE Consumer Electronics Magazine, 6(1), 82-93.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart device environment. In Mobile and
Wireless Technology 2015 (pp. 199-206). Springer, Berlin, Heidelberg.
Memon, N. (2017). How Biometric Authentication Poses New Challenges to Our Security and Privacy [In the Spotlight]. IEEE Signal
Processing Magazine, 34(4), 196-194.
Thomas, K. P., Vinod, A. P., & Robinson, N. (2017, March). Online Biometric Authentication Using Subject-Specific Band Power
features of EEG. In Proceedings of the 2017 International Conference on Cryptography, Security and Privacy (pp. 136-141).
ACM.
REFERENCES
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages, Disadvantages And Future Development: A
Review. International Journal Of Scientific & Technology Research, 4(8), 285-289.
Barbosa, F. G., & Silva, W. L. S. (2015, November). Support vector machines, Mel-Frequency Cepstral Coefficients and the Discrete
Cosine Transform applied on voice based biometric authentication. In SAI Intelligent Systems Conference (IntelliSys),
2015 (pp. 1032-1039). IEEE.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015). Biometric authentication on iphone and
android: Usability, perceptions, and influences on adoption. Proc. USEC, 1-2.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an enhanced biometric authentication system
for smartphones. In Proceedings of the 12th annual international conference on Mobile systems, applications, and
services (pp. 109-122). ACM.
Ciuffo, F., & Weiss, G. M. (2017, October). Smartwatch-based transcription biometrics. In Ubiquitous Computing, Electronics and
Mobile Communication Conference (UEMCON), 2017 IEEE 8th Annual (pp. 145-149). IEEE.
De Luca, A., Hang, A., Von Zezschwitz, E., & Hussmann, H. (2015, April). I feel like I'm taking selfies all day!: towards
understanding biometric authentication on smartphones. In Proceedings of the 33rd Annual ACM Conference on Human
Factors in Computing Systems (pp. 1411-1414). ACM.
Ghosh, S., Majumder, A., Goswami, J., Kumar, A., Mohanty, S. P., & Bhattacharyya, B. K. (2017). Swing-Pay: One Card Meets All
User Payment and Identity Needs: A Digital Card Module using NFC and Biometric Authentication for Peer-to-Peer
Payment. IEEE Consumer Electronics Magazine, 6(1), 82-93.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart device environment. In Mobile and
Wireless Technology 2015 (pp. 199-206). Springer, Berlin, Heidelberg.
Memon, N. (2017). How Biometric Authentication Poses New Challenges to Our Security and Privacy [In the Spotlight]. IEEE Signal
Processing Magazine, 34(4), 196-194.
Thomas, K. P., Vinod, A. P., & Robinson, N. (2017, March). Online Biometric Authentication Using Subject-Specific Band Power
features of EEG. In Proceedings of the 2017 International Conference on Cryptography, Security and Privacy (pp. 136-141).
ACM.
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





