Information Security: CIA Triad and Biometric Authentication
VerifiedAdded on 2023/06/13
|16
|4179
|385
AI Summary
This article discusses the CIA triad and its implementation in Automated Teller Machines (ATMs). It also explores the advantages and disadvantages of biometric authentication in information security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INFORMATION SECURITY
Information Security
Assessment No-
Assessment Title-
Student Name and ID-
Student name and Code-
Student Email Address-
Information Security
Assessment No-
Assessment Title-
Student Name and ID-
Student name and Code-
Student Email Address-
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1INFORMATION SECURITY
Answer to Question 1:
The information security issues are to be mitigated in an Automated Teller Machine and
the software developers of the ATM machine should ensure that there should not exist any kind
of security issues and the customers do not face any transaction problem or they should not have
any authentication problem related to their bank accounts (Beng et al., 2018). So, to ensure
security, the CIA triad is implemented in the security system of the ATM. CIA refers to
confidentiality, Integrity, as well as Availability. The details about the security factors are
explained with examples.
Confidentiality: The main purpose of confidentiality is providing security and privacy to
the data that are involved in the system. Various measures are usually taken so that there is no
issue of confidentiality for the transaction in ATM (Rao & Nayak, 2014). Confidentiality
includes keeping the data secret or private from any other outsider who is not authorized for the
data accessibility. The data needed for ATM transaction should not reach to wrong people who
can misuse the data involved in the system. There should be total restriction about who is access
the ATM data and access should be given only to authenticated user.
Examples of the confidentiality that are related to ATM is that the confidentiality policy
in ATM ensures that account number of the user or the routing number of the user should be kept
private when the user is using Internet banking for all transaction. There are many ways to keep
the data secured, from which one of the process is the data encryption process. By data
encryption, data are made confidentiality (Raspotnig, Karpati & Opdahl, 2017). Another
example of confidentiality related to ATM is that the card should be available with the user while
transaction is going on. Without transaction, there will be no transaction possible. Usually there
Answer to Question 1:
The information security issues are to be mitigated in an Automated Teller Machine and
the software developers of the ATM machine should ensure that there should not exist any kind
of security issues and the customers do not face any transaction problem or they should not have
any authentication problem related to their bank accounts (Beng et al., 2018). So, to ensure
security, the CIA triad is implemented in the security system of the ATM. CIA refers to
confidentiality, Integrity, as well as Availability. The details about the security factors are
explained with examples.
Confidentiality: The main purpose of confidentiality is providing security and privacy to
the data that are involved in the system. Various measures are usually taken so that there is no
issue of confidentiality for the transaction in ATM (Rao & Nayak, 2014). Confidentiality
includes keeping the data secret or private from any other outsider who is not authorized for the
data accessibility. The data needed for ATM transaction should not reach to wrong people who
can misuse the data involved in the system. There should be total restriction about who is access
the ATM data and access should be given only to authenticated user.
Examples of the confidentiality that are related to ATM is that the confidentiality policy
in ATM ensures that account number of the user or the routing number of the user should be kept
private when the user is using Internet banking for all transaction. There are many ways to keep
the data secured, from which one of the process is the data encryption process. By data
encryption, data are made confidentiality (Raspotnig, Karpati & Opdahl, 2017). Another
example of confidentiality related to ATM is that the card should be available with the user while
transaction is going on. Without transaction, there will be no transaction possible. Usually there

2INFORMATION SECURITY
can be two types of data breach that are to be kept in mind. The details of the card should not
been stolen and the employee details of organization should not be accessed by outsiders.
Integrity: The second policy of security is the purpose of integrity. Integrity keep the data
accurate throughout its life, data consistency is followed throughout, and trustworthiness is also
maintained (Salnitri, Dalpiaz & Giorgini, 2017). Integrity assures that the data content remains
same all through the life of the data.
There are some examples of data integrity. The examples are that the information of
ATM card cannot be modified or cannot be changed without the permission of the real user
(Kubbo et al., 2016). The data alteration or modification can be deliberately done or can be
accidental. Accidental as well as deliberate data affects the data integrity of a data. There is
backup storage process to keep the data integrated for the user who wants to keep the data
secured.
Availability: The last policy of the CIA triad is the availability. Availability protects
mainly the hardware of the system and the information that are transmitted while a transaction
process is ongoing (Beng et al., 2018). If the hardware is not maintained, the users will not be
able to proceed with their transaction. There should also be proper upgradation done with the
hardware of the system.
Examples of availability includes that a fully upgraded system is to be used by the
user for transaction of cash (Alsaadi, 2015). Availability also protects any type of denial of
service attack to the system, and data should be available with customer while transaction is
taking place.
can be two types of data breach that are to be kept in mind. The details of the card should not
been stolen and the employee details of organization should not be accessed by outsiders.
Integrity: The second policy of security is the purpose of integrity. Integrity keep the data
accurate throughout its life, data consistency is followed throughout, and trustworthiness is also
maintained (Salnitri, Dalpiaz & Giorgini, 2017). Integrity assures that the data content remains
same all through the life of the data.
There are some examples of data integrity. The examples are that the information of
ATM card cannot be modified or cannot be changed without the permission of the real user
(Kubbo et al., 2016). The data alteration or modification can be deliberately done or can be
accidental. Accidental as well as deliberate data affects the data integrity of a data. There is
backup storage process to keep the data integrated for the user who wants to keep the data
secured.
Availability: The last policy of the CIA triad is the availability. Availability protects
mainly the hardware of the system and the information that are transmitted while a transaction
process is ongoing (Beng et al., 2018). If the hardware is not maintained, the users will not be
able to proceed with their transaction. There should also be proper upgradation done with the
hardware of the system.
Examples of availability includes that a fully upgraded system is to be used by the
user for transaction of cash (Alsaadi, 2015). Availability also protects any type of denial of
service attack to the system, and data should be available with customer while transaction is
taking place.

3INFORMATION SECURITY
Answer to Question 2:
Security is provided by ATM in many ways. There are securities that also includes the
number of transaction that is user can proceed in a day and the number of times the customer can
enter the pin while processing with a single transaction. The security of the ATM allows a
particular customer to input the pin to a maximum of three times for a single transaction (Farooq
et al., 2015). The customer can enter wrong pin accidentally, or can also input the pin wrong
deliberately. But, the maximum number the ATM allows the input of the private pin is three
times. Accidental wrong pins usually happen when the user forgets the pin and goes on trying the
wrong pin several times. But deliberate wrong pins usually occurs when the ATM card is on the
hand of some unauthenticated people and he uses hit and trial method to discover the pin.
The case stated in the question describe a scenario of an ATM where a thief has entered
into an ATM and with a screwdriver he locked the card reader of the machine and broke down
five keypad number keys on the machine. The thief broke five keys of the keypad, and while he
was proceeding with the next one, a customer came to the ATM for transaction.
The customer was able to make his transaction successful. This indicates that the private
pin of the user were from the unbroken keys on the keypad. However, since the card reader was
jammed, the customer could not take out the card. Not able to take out the card, the person went
outside the ATM to get some help. Thinking this as a chance, the thief thought of attempting
some tries to that he can get some cash from the card. With total five keys in working position,
the thief has many possibility to get the private pin of the user. The ATM pin of a card usually
has four digits which were from the five keys that was available. Therefore, total maximum
combinations that are possible to get the pin are:
Answer to Question 2:
Security is provided by ATM in many ways. There are securities that also includes the
number of transaction that is user can proceed in a day and the number of times the customer can
enter the pin while processing with a single transaction. The security of the ATM allows a
particular customer to input the pin to a maximum of three times for a single transaction (Farooq
et al., 2015). The customer can enter wrong pin accidentally, or can also input the pin wrong
deliberately. But, the maximum number the ATM allows the input of the private pin is three
times. Accidental wrong pins usually happen when the user forgets the pin and goes on trying the
wrong pin several times. But deliberate wrong pins usually occurs when the ATM card is on the
hand of some unauthenticated people and he uses hit and trial method to discover the pin.
The case stated in the question describe a scenario of an ATM where a thief has entered
into an ATM and with a screwdriver he locked the card reader of the machine and broke down
five keypad number keys on the machine. The thief broke five keys of the keypad, and while he
was proceeding with the next one, a customer came to the ATM for transaction.
The customer was able to make his transaction successful. This indicates that the private
pin of the user were from the unbroken keys on the keypad. However, since the card reader was
jammed, the customer could not take out the card. Not able to take out the card, the person went
outside the ATM to get some help. Thinking this as a chance, the thief thought of attempting
some tries to that he can get some cash from the card. With total five keys in working position,
the thief has many possibility to get the private pin of the user. The ATM pin of a card usually
has four digits which were from the five keys that was available. Therefore, total maximum
combinations that are possible to get the pin are:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4INFORMATION SECURITY
5P4 = 5! / (5-4)! = 5 * 4 * 3 * 2 = 120 set of ATM pin.
However, the thief will not have the chance to try 120 times the pin of the ATM as per
the security of the ATM. The thief can have only maximum of three tries for the ATM pin. If the
thief can guess the pin within the three allowed tries of ATM private pin, he will be able to take
out some cash from the machine. If he cannot guess the right pin, the card will be immediately
stopped after three tries and the card will not work anymore.
If the card gets blocked, then the user will not be able to any more transaction for that day
(Cooper & Zywicki, 2017). Generally after getting a card blocked, the user of the card has to call
the customer care service of that bank or will have trio wait for some hours for the card to get in
working position again.
Answer to Question 3:
The process of biometric authentication implies to make the security process more strong
and authentication is made strict with the biometric authentication. Biometric authentication
includes specific characteristics or physical unique characteristics connected with biological
parts of a person or an individual (Hajare et al., 2018). The biometric authentication is one of the
most unique and safe authentication techniques for the user. The biometric data or previously
capture data are mainly used for comparing the identifying the biometric authentication in the
system. In biometric systems, a database is included in which previously captured data are
usually stored. As the biometric system deals with the biological parts, when the user inputs the
previously scanned part present in the database, the system shows a match or rejects the user if
there no match found in the database. The process of biometric authentication helps to manage
the system successfully better than any other physical device or any type of digital computing
5P4 = 5! / (5-4)! = 5 * 4 * 3 * 2 = 120 set of ATM pin.
However, the thief will not have the chance to try 120 times the pin of the ATM as per
the security of the ATM. The thief can have only maximum of three tries for the ATM pin. If the
thief can guess the pin within the three allowed tries of ATM private pin, he will be able to take
out some cash from the machine. If he cannot guess the right pin, the card will be immediately
stopped after three tries and the card will not work anymore.
If the card gets blocked, then the user will not be able to any more transaction for that day
(Cooper & Zywicki, 2017). Generally after getting a card blocked, the user of the card has to call
the customer care service of that bank or will have trio wait for some hours for the card to get in
working position again.
Answer to Question 3:
The process of biometric authentication implies to make the security process more strong
and authentication is made strict with the biometric authentication. Biometric authentication
includes specific characteristics or physical unique characteristics connected with biological
parts of a person or an individual (Hajare et al., 2018). The biometric authentication is one of the
most unique and safe authentication techniques for the user. The biometric data or previously
capture data are mainly used for comparing the identifying the biometric authentication in the
system. In biometric systems, a database is included in which previously captured data are
usually stored. As the biometric system deals with the biological parts, when the user inputs the
previously scanned part present in the database, the system shows a match or rejects the user if
there no match found in the database. The process of biometric authentication helps to manage
the system successfully better than any other physical device or any type of digital computing

5INFORMATION SECURITY
devices involved for the purpose of authentication (Risodkar et al., 2017). Nowadays the
biometric system is a very common method and is used in many sectors of life such as schools,
colleges, many offices also uses biometric authentication for logging in time. As the biometric
system is automatic, it does not need manual inspection to get the logging in time or the logging
out time of the employees. There are many ways of biometric authentication. Authentication is
done by scanning the fingerprint, face reorganization technique, voice reorganization, scanning
of retinas and many more.
However, with all the advantages, biometric authentication also provides with many
disadvantages (Haupt & Mozer, 2015). For the disadvantages that the biometric authentication
provides, people find difficulties to use the biometric system. Out of all the disadvantages that
biometric authentication provides, three of them are listed below.
i) Resetting the data is a very difficult task for the users using the biometric system. Resetting is
one of the greatest disadvantages that the system has. The data stored in the database system
cannot be reset very easily. After the biometric scanning is done with the system, to alter or
modify the data stored is very difficult. The resetting problem mainly occurs in electronic
computing gadgets or mobile phones. When the user wants to change the device, deleting the
fingerprint is usually difficult (Rahim, 2016). If those devices do not recognize the fingerprints,
it is very difficult to open the system. To mitigate the problem resetting, there should be some
alternative process for providing the password. Traditional method of using the password or the
ID can be usually used for authentication so that if the system does not detect the scanning data,
the system can be unlocked by providing some password.
devices involved for the purpose of authentication (Risodkar et al., 2017). Nowadays the
biometric system is a very common method and is used in many sectors of life such as schools,
colleges, many offices also uses biometric authentication for logging in time. As the biometric
system is automatic, it does not need manual inspection to get the logging in time or the logging
out time of the employees. There are many ways of biometric authentication. Authentication is
done by scanning the fingerprint, face reorganization technique, voice reorganization, scanning
of retinas and many more.
However, with all the advantages, biometric authentication also provides with many
disadvantages (Haupt & Mozer, 2015). For the disadvantages that the biometric authentication
provides, people find difficulties to use the biometric system. Out of all the disadvantages that
biometric authentication provides, three of them are listed below.
i) Resetting the data is a very difficult task for the users using the biometric system. Resetting is
one of the greatest disadvantages that the system has. The data stored in the database system
cannot be reset very easily. After the biometric scanning is done with the system, to alter or
modify the data stored is very difficult. The resetting problem mainly occurs in electronic
computing gadgets or mobile phones. When the user wants to change the device, deleting the
fingerprint is usually difficult (Rahim, 2016). If those devices do not recognize the fingerprints,
it is very difficult to open the system. To mitigate the problem resetting, there should be some
alternative process for providing the password. Traditional method of using the password or the
ID can be usually used for authentication so that if the system does not detect the scanning data,
the system can be unlocked by providing some password.

6INFORMATION SECURITY
ii) Second problem that biometric system is that the system needs additional system for storing
the scanned data of the physical body part and needs additional gadgets to scan the body part.
People usually thinks that the biometric system cut less the cost of hardware and system
maintenance (Kim et al., 2015). But, actually the case is not so. Many systems are needed to
maintain the biometric system properly.
iii) It is very usual to think that the biometric system is very accurate and provides its user an
accurate identification. But actually the biometric system used for authentication is very accurate
and the users now do not find it reluctant to use it. To make the system accurate, metrics such as
FRR or FAR are used in the systems (Meng et al., 2015). To calculate the accuracy of the
system, False Rejection Rate and False Acceptance Rate is calculated. False positive and false
negative are the errors that are provided by the system that deals with accuracy.
Answer to Question 4:
It is known that biometric authentication provides an identification that has many
advantages that people finds easy to use (Bhagavatula et al., 2015). But, there are some
disadvantages as well in the biometric system that people cannot depend on for authentication
purpose. The accuracy of the system is not proper. Two accuracy errors that are included with
the system are false negative error and the false positive error. The false negative rate and the
false positive rates are inversely proportional to each other. If one increases, the other
automatically decreases. The accuracy is calculated with the FRR (False Rejection Rate) and
FAR (False Acceptance Rate) that is the ratio between total number of false accepted data or
total number of false rejected data with that of the total number of identification done with that
ii) Second problem that biometric system is that the system needs additional system for storing
the scanned data of the physical body part and needs additional gadgets to scan the body part.
People usually thinks that the biometric system cut less the cost of hardware and system
maintenance (Kim et al., 2015). But, actually the case is not so. Many systems are needed to
maintain the biometric system properly.
iii) It is very usual to think that the biometric system is very accurate and provides its user an
accurate identification. But actually the biometric system used for authentication is very accurate
and the users now do not find it reluctant to use it. To make the system accurate, metrics such as
FRR or FAR are used in the systems (Meng et al., 2015). To calculate the accuracy of the
system, False Rejection Rate and False Acceptance Rate is calculated. False positive and false
negative are the errors that are provided by the system that deals with accuracy.
Answer to Question 4:
It is known that biometric authentication provides an identification that has many
advantages that people finds easy to use (Bhagavatula et al., 2015). But, there are some
disadvantages as well in the biometric system that people cannot depend on for authentication
purpose. The accuracy of the system is not proper. Two accuracy errors that are included with
the system are false negative error and the false positive error. The false negative rate and the
false positive rates are inversely proportional to each other. If one increases, the other
automatically decreases. The accuracy is calculated with the FRR (False Rejection Rate) and
FAR (False Acceptance Rate) that is the ratio between total number of false accepted data or
total number of false rejected data with that of the total number of identification done with that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
system (Yuan, Sun & Lv, 2016). Many instances are there that shows that false negative rate is
usually more serious than the false positive rate.
1) First instance that shows that false negative rate is more serious than the false positive
rate is that when a holder of a very expensive system cannot get access to the object or system
even if the object belongs to that person only (Hadid, 2014). This would lead to a situation where
the system owner will not be able access its own device. This type of error is generally noted as
the false negative error. The false negative error arise when the system of biometric does not
recognize an authenticated user and restricts its access as an unauthorized author (Karabina, K.,
& Robinson, 2016). This is the most common thing that people faces with biometric and finds
reluctant to use.
2) Biometric system sometimes fails to recognize the biometric of patients. This is
another area where false negative rate is more serious than false positive rate (Holz, Buthpitiya &
Knaust, 2015). The tests of a patient does not match with the database of the patient, even though
the patient is the original one. So, the patient cannot take the reports for his health and make the
further treatments. Another problem with biometric occurs if the door of the house is biometric
and a person in the house is having cardiac attack, he will not be able to come out of the house.
Answer to Question 5:
1st section:
Transposition is a method that helps to encrypt a text. There are many other processes
that works similar as transposition method (Hadid et al., 2015). The processes that are involves
encryption as well decryption are Affine method, which is almost similar to Caesar cipher
system (Yuan, Sun & Lv, 2016). Many instances are there that shows that false negative rate is
usually more serious than the false positive rate.
1) First instance that shows that false negative rate is more serious than the false positive
rate is that when a holder of a very expensive system cannot get access to the object or system
even if the object belongs to that person only (Hadid, 2014). This would lead to a situation where
the system owner will not be able access its own device. This type of error is generally noted as
the false negative error. The false negative error arise when the system of biometric does not
recognize an authenticated user and restricts its access as an unauthorized author (Karabina, K.,
& Robinson, 2016). This is the most common thing that people faces with biometric and finds
reluctant to use.
2) Biometric system sometimes fails to recognize the biometric of patients. This is
another area where false negative rate is more serious than false positive rate (Holz, Buthpitiya &
Knaust, 2015). The tests of a patient does not match with the database of the patient, even though
the patient is the original one. So, the patient cannot take the reports for his health and make the
further treatments. Another problem with biometric occurs if the door of the house is biometric
and a person in the house is having cardiac attack, he will not be able to come out of the house.
Answer to Question 5:
1st section:
Transposition is a method that helps to encrypt a text. There are many other processes
that works similar as transposition method (Hadid et al., 2015). The processes that are involves
encryption as well decryption are Affine method, which is almost similar to Caesar cipher
8INFORMATION SECURITY
method, Baconian method, Caesar shifting method, columnar transposition method, railfence
method, substitution method, vigenere method, and Atbash method.
2nd Section:
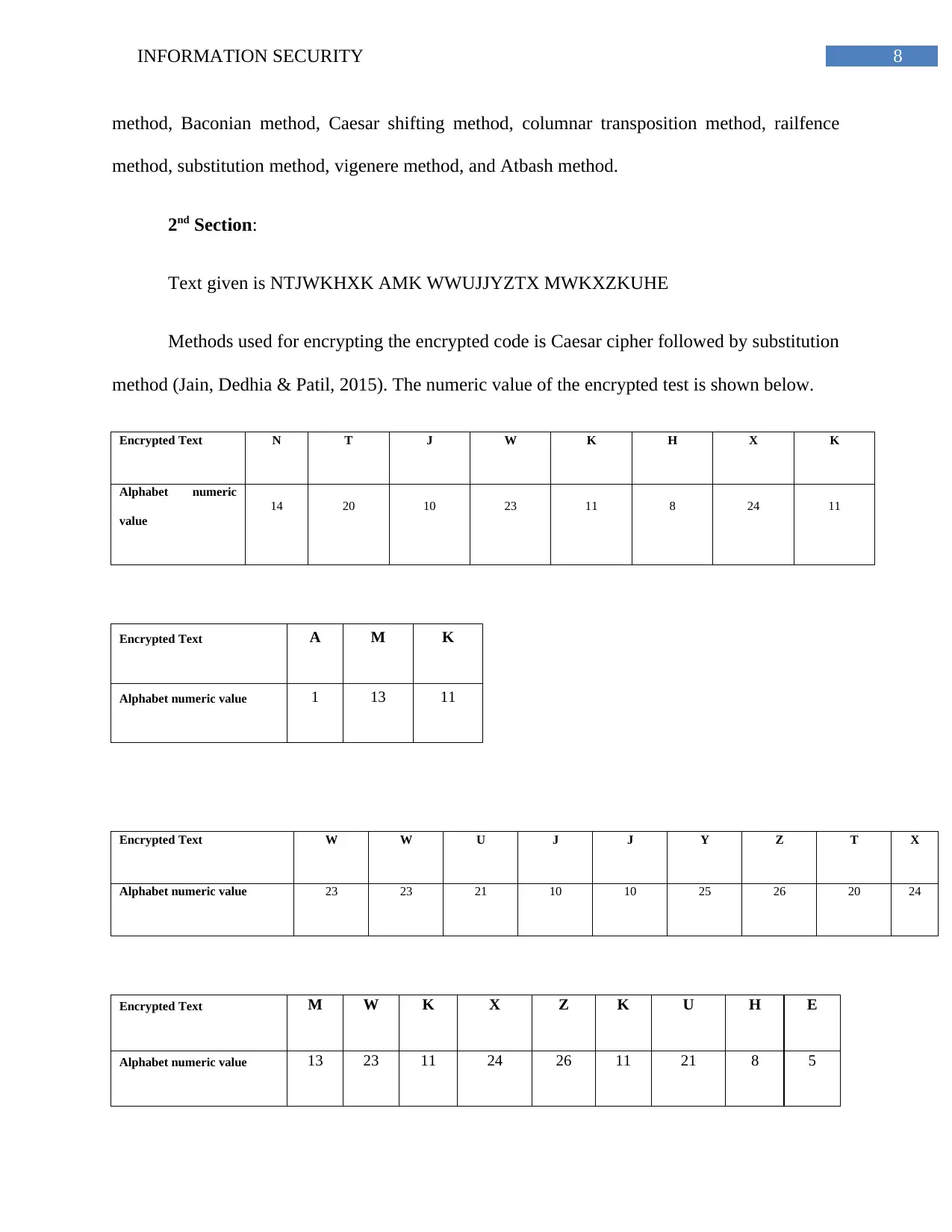
Text given is NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Methods used for encrypting the encrypted code is Caesar cipher followed by substitution
method (Jain, Dedhia & Patil, 2015). The numeric value of the encrypted test is shown below.
Encrypted Text N T J W K H X K
Alphabet numeric
value
14 20 10 23 11 8 24 11
Encrypted Text A M K
Alphabet numeric value 1 13 11
Encrypted Text W W U J J Y Z T X
Alphabet numeric value 23 23 21 10 10 25 26 20 24
Encrypted Text M W K X Z K U H E
Alphabet numeric value 13 23 11 24 26 11 21 8 5
method, Baconian method, Caesar shifting method, columnar transposition method, railfence
method, substitution method, vigenere method, and Atbash method.
2nd Section:
Text given is NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
Methods used for encrypting the encrypted code is Caesar cipher followed by substitution
method (Jain, Dedhia & Patil, 2015). The numeric value of the encrypted test is shown below.
Encrypted Text N T J W K H X K
Alphabet numeric
value
14 20 10 23 11 8 24 11
Encrypted Text A M K
Alphabet numeric value 1 13 11
Encrypted Text W W U J J Y Z T X
Alphabet numeric value 23 23 21 10 10 25 26 20 24
Encrypted Text M W K X Z K U H E
Alphabet numeric value 13 23 11 24 26 11 21 8 5
9INFORMATION SECURITY
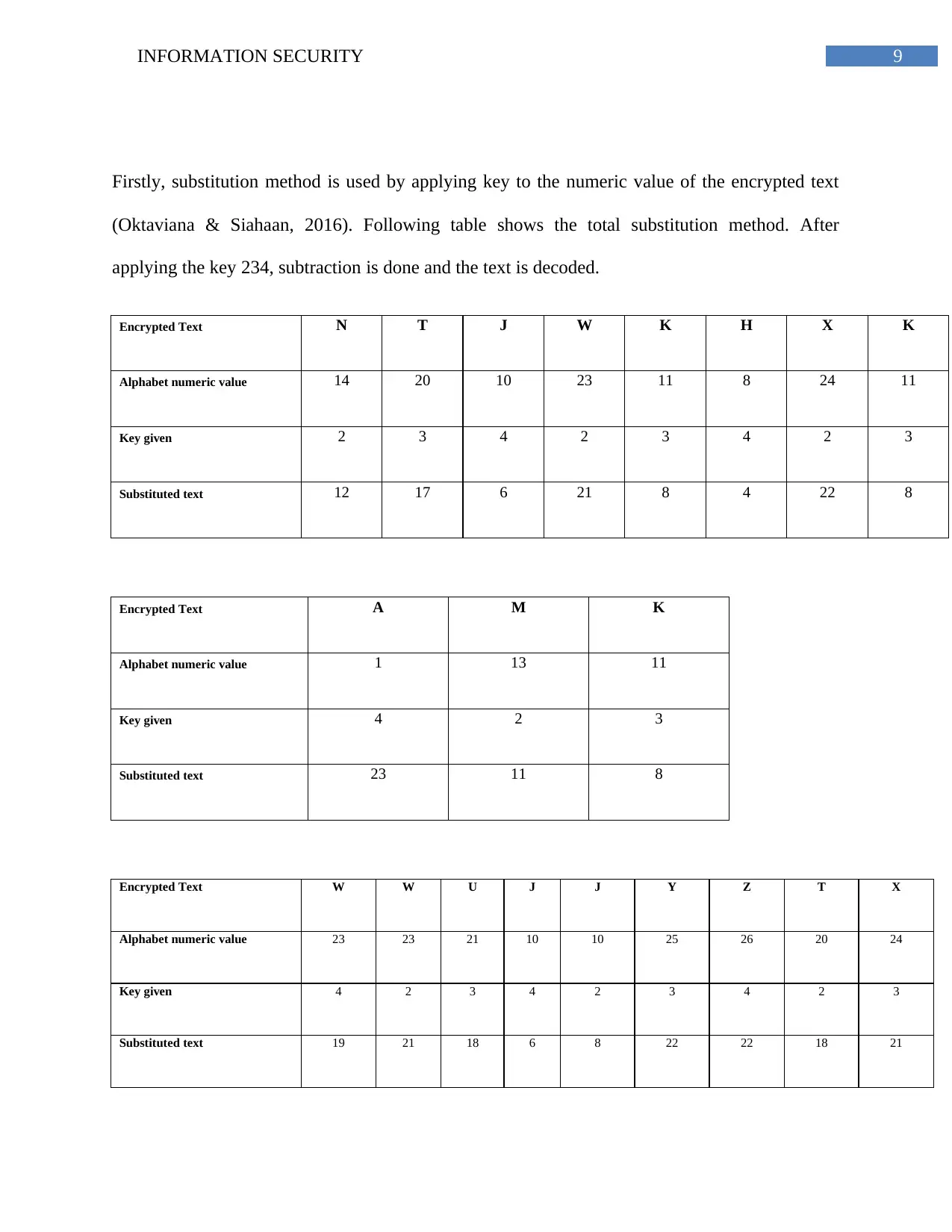
Firstly, substitution method is used by applying key to the numeric value of the encrypted text
(Oktaviana & Siahaan, 2016). Following table shows the total substitution method. After
applying the key 234, subtraction is done and the text is decoded.
Encrypted Text N T J W K H X K
Alphabet numeric value 14 20 10 23 11 8 24 11
Key given 2 3 4 2 3 4 2 3
Substituted text 12 17 6 21 8 4 22 8
Encrypted Text A M K
Alphabet numeric value 1 13 11
Key given 4 2 3
Substituted text 23 11 8
Encrypted Text W W U J J Y Z T X
Alphabet numeric value 23 23 21 10 10 25 26 20 24
Key given 4 2 3 4 2 3 4 2 3
Substituted text 19 21 18 6 8 22 22 18 21
Firstly, substitution method is used by applying key to the numeric value of the encrypted text
(Oktaviana & Siahaan, 2016). Following table shows the total substitution method. After
applying the key 234, subtraction is done and the text is decoded.
Encrypted Text N T J W K H X K
Alphabet numeric value 14 20 10 23 11 8 24 11
Key given 2 3 4 2 3 4 2 3
Substituted text 12 17 6 21 8 4 22 8
Encrypted Text A M K
Alphabet numeric value 1 13 11
Key given 4 2 3
Substituted text 23 11 8
Encrypted Text W W U J J Y Z T X
Alphabet numeric value 23 23 21 10 10 25 26 20 24
Key given 4 2 3 4 2 3 4 2 3
Substituted text 19 21 18 6 8 22 22 18 21
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10INFORMATION SECURITY
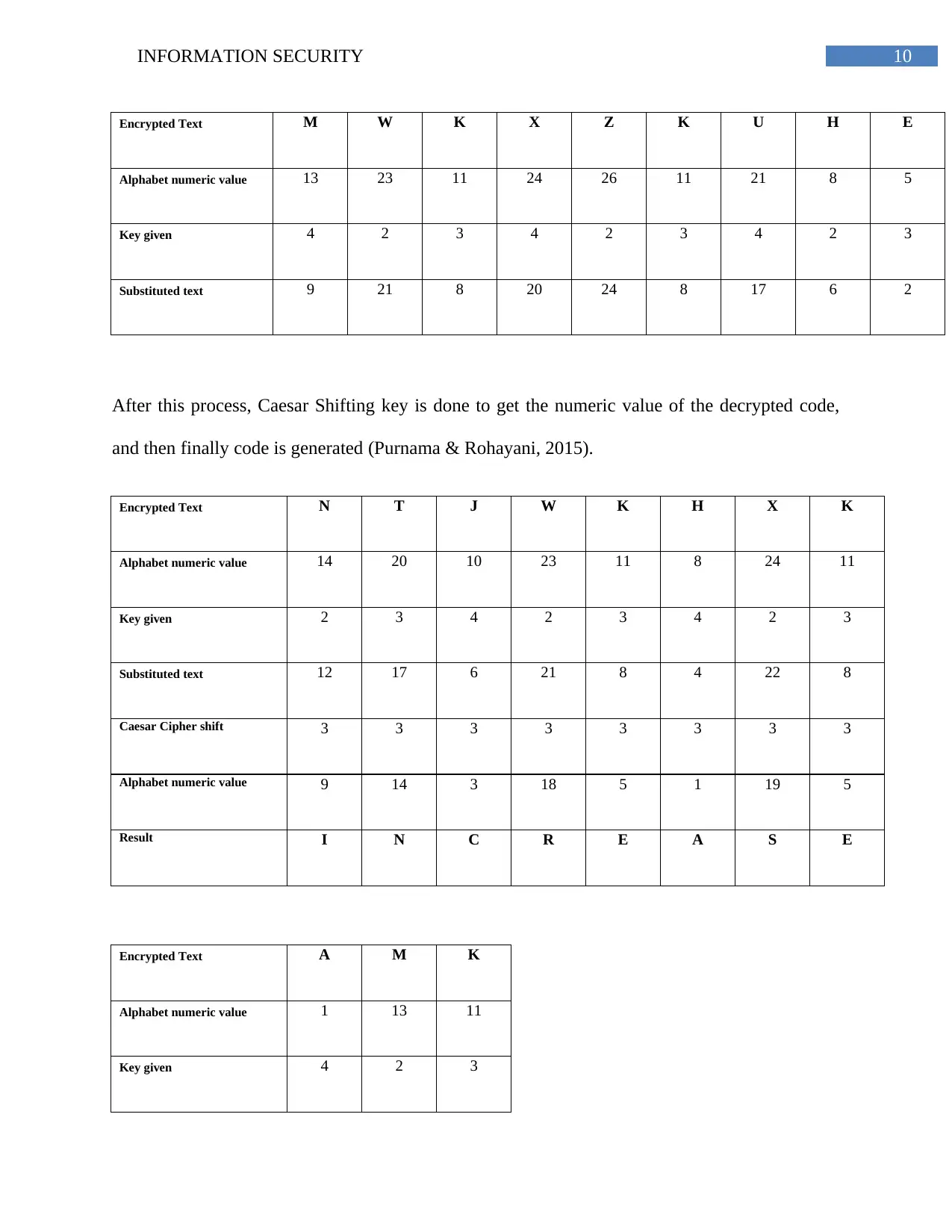
Encrypted Text M W K X Z K U H E
Alphabet numeric value 13 23 11 24 26 11 21 8 5
Key given 4 2 3 4 2 3 4 2 3
Substituted text 9 21 8 20 24 8 17 6 2
After this process, Caesar Shifting key is done to get the numeric value of the decrypted code,
and then finally code is generated (Purnama & Rohayani, 2015).
Encrypted Text N T J W K H X K
Alphabet numeric value 14 20 10 23 11 8 24 11
Key given 2 3 4 2 3 4 2 3
Substituted text 12 17 6 21 8 4 22 8
Caesar Cipher shift 3 3 3 3 3 3 3 3
Alphabet numeric value 9 14 3 18 5 1 19 5
Result I N C R E A S E
Encrypted Text A M K
Alphabet numeric value 1 13 11
Key given 4 2 3
Encrypted Text M W K X Z K U H E
Alphabet numeric value 13 23 11 24 26 11 21 8 5
Key given 4 2 3 4 2 3 4 2 3
Substituted text 9 21 8 20 24 8 17 6 2
After this process, Caesar Shifting key is done to get the numeric value of the decrypted code,
and then finally code is generated (Purnama & Rohayani, 2015).
Encrypted Text N T J W K H X K
Alphabet numeric value 14 20 10 23 11 8 24 11
Key given 2 3 4 2 3 4 2 3
Substituted text 12 17 6 21 8 4 22 8
Caesar Cipher shift 3 3 3 3 3 3 3 3
Alphabet numeric value 9 14 3 18 5 1 19 5
Result I N C R E A S E
Encrypted Text A M K
Alphabet numeric value 1 13 11
Key given 4 2 3
11INFORMATION SECURITY
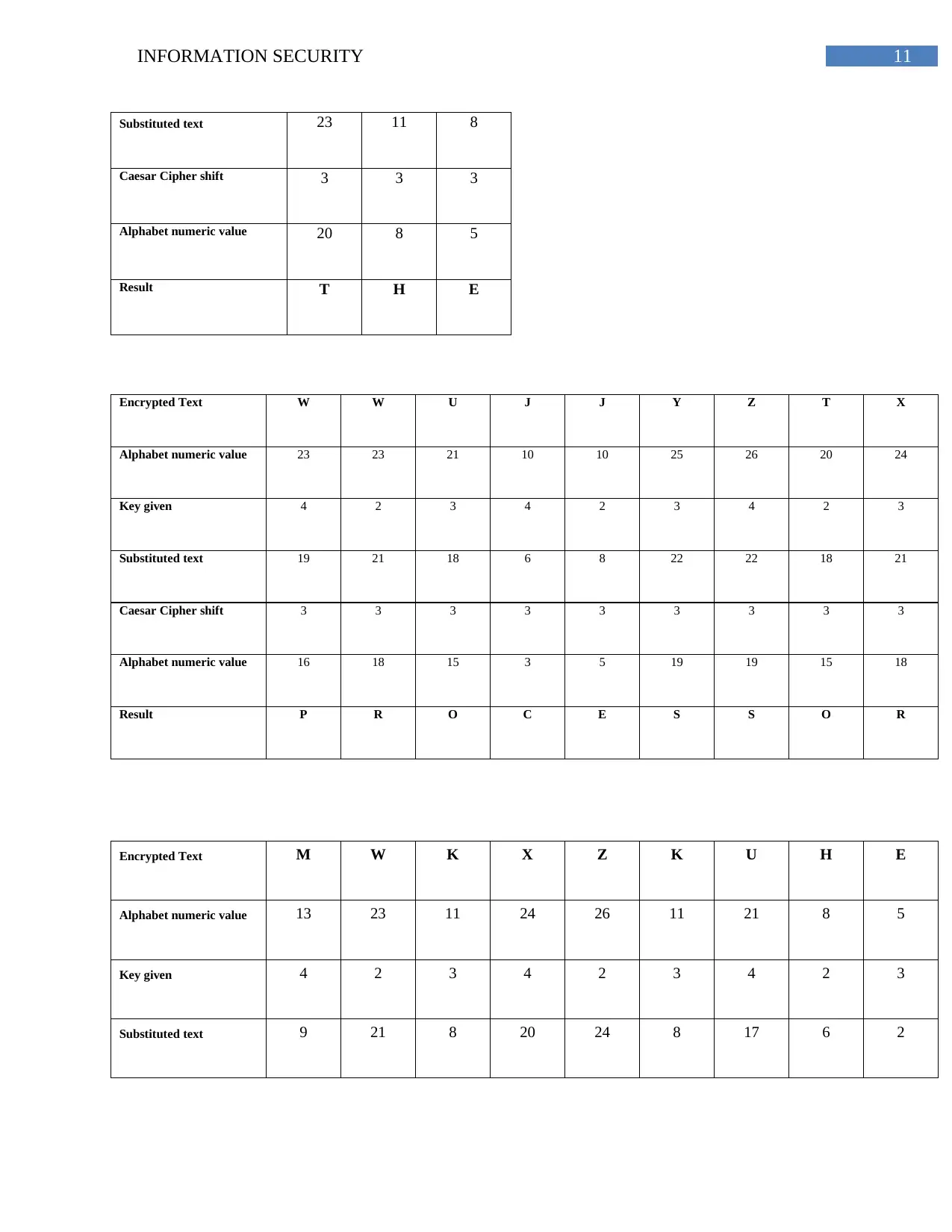
Substituted text 23 11 8
Caesar Cipher shift 3 3 3
Alphabet numeric value 20 8 5
Result T H E
Encrypted Text W W U J J Y Z T X
Alphabet numeric value 23 23 21 10 10 25 26 20 24
Key given 4 2 3 4 2 3 4 2 3
Substituted text 19 21 18 6 8 22 22 18 21
Caesar Cipher shift 3 3 3 3 3 3 3 3 3
Alphabet numeric value 16 18 15 3 5 19 19 15 18
Result P R O C E S S O R
Encrypted Text M W K X Z K U H E
Alphabet numeric value 13 23 11 24 26 11 21 8 5
Key given 4 2 3 4 2 3 4 2 3
Substituted text 9 21 8 20 24 8 17 6 2
Substituted text 23 11 8
Caesar Cipher shift 3 3 3
Alphabet numeric value 20 8 5
Result T H E
Encrypted Text W W U J J Y Z T X
Alphabet numeric value 23 23 21 10 10 25 26 20 24
Key given 4 2 3 4 2 3 4 2 3
Substituted text 19 21 18 6 8 22 22 18 21
Caesar Cipher shift 3 3 3 3 3 3 3 3 3
Alphabet numeric value 16 18 15 3 5 19 19 15 18
Result P R O C E S S O R
Encrypted Text M W K X Z K U H E
Alphabet numeric value 13 23 11 24 26 11 21 8 5
Key given 4 2 3 4 2 3 4 2 3
Substituted text 9 21 8 20 24 8 17 6 2
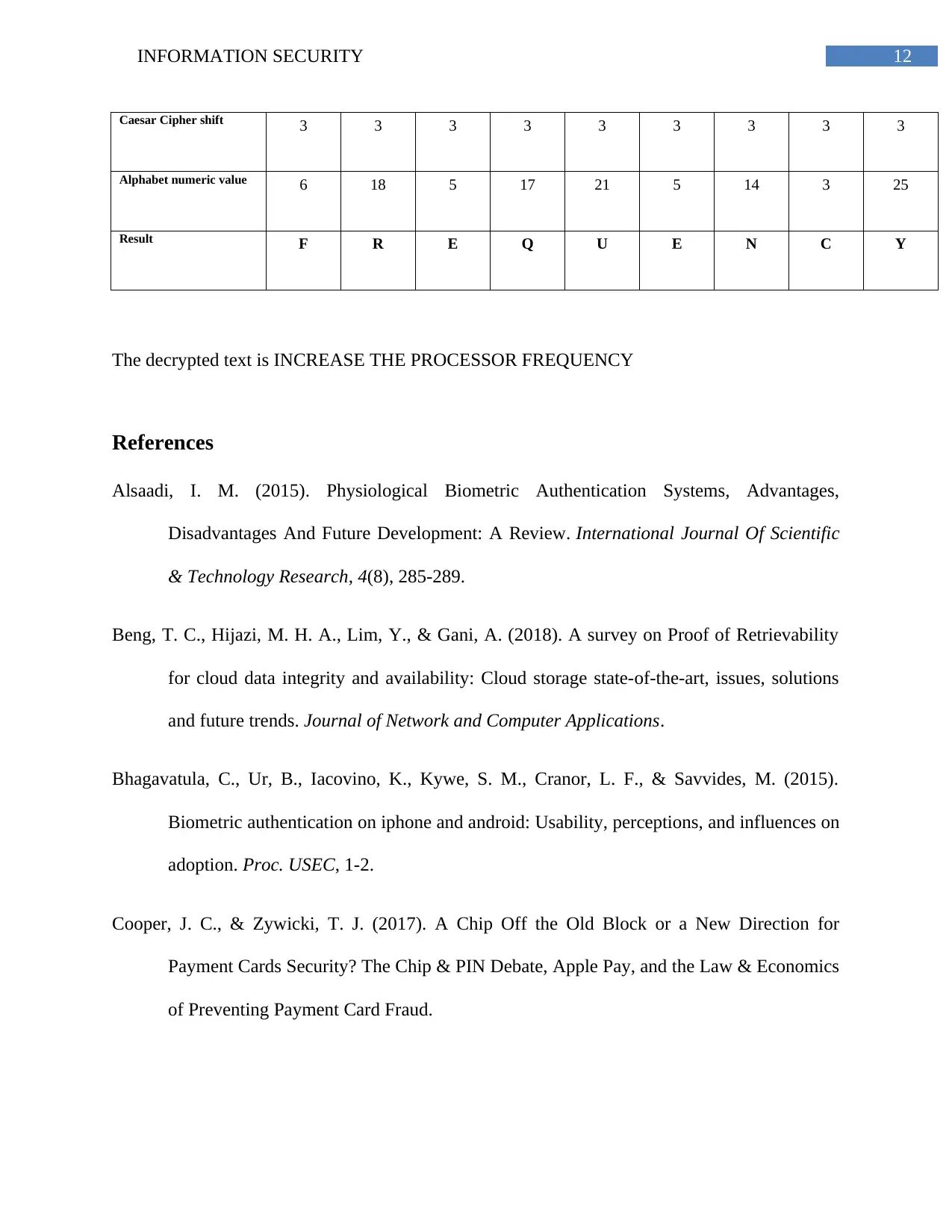
12INFORMATION SECURITY
Caesar Cipher shift 3 3 3 3 3 3 3 3 3
Alphabet numeric value 6 18 5 17 21 5 14 3 25
Result F R E Q U E N C Y
The decrypted text is INCREASE THE PROCESSOR FREQUENCY
References
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Beng, T. C., Hijazi, M. H. A., Lim, Y., & Gani, A. (2018). A survey on Proof of Retrievability
for cloud data integrity and availability: Cloud storage state-of-the-art, issues, solutions
and future trends. Journal of Network and Computer Applications.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption. Proc. USEC, 1-2.
Cooper, J. C., & Zywicki, T. J. (2017). A Chip Off the Old Block or a New Direction for
Payment Cards Security? The Chip & PIN Debate, Apple Pay, and the Law & Economics
of Preventing Payment Card Fraud.
Caesar Cipher shift 3 3 3 3 3 3 3 3 3
Alphabet numeric value 6 18 5 17 21 5 14 3 25
Result F R E Q U E N C Y
The decrypted text is INCREASE THE PROCESSOR FREQUENCY
References
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Beng, T. C., Hijazi, M. H. A., Lim, Y., & Gani, A. (2018). A survey on Proof of Retrievability
for cloud data integrity and availability: Cloud storage state-of-the-art, issues, solutions
and future trends. Journal of Network and Computer Applications.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption. Proc. USEC, 1-2.
Cooper, J. C., & Zywicki, T. J. (2017). A Chip Off the Old Block or a New Direction for
Payment Cards Security? The Chip & PIN Debate, Apple Pay, and the Law & Economics
of Preventing Payment Card Fraud.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13INFORMATION SECURITY
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the security
concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
French, P., Foulkes, P., Harrison, P., Hughes, V., San Segundo, E., & Stevens, L. (2015). The
vocal tract as a biometric: output measures, interrelationships, and efficacy.
In Proceedings of the 18th International Congress of Phonetic Sciences (ICPhS).
Hadid, A. (2014). Face biometrics under spoofing attacks: Vulnerabilities, countermeasures,
open issues, and research directions. In Proceedings of the IEEE Conference on
Computer Vision and Pattern Recognition Workshops (pp. 113-118).
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack:
an evaluation methodology and lessons learned. IEEE Signal Processing
Magazine, 32(5), 20-30.
Hajare, U., Mahajan, R., Jadhav, S., Pingale, N., & Salunke, S. (2018). Efficient Cash
Withdrawal from ATM machine using Mobile Banking.
Haupt, G., & Mozer, T. (2015). Assessing biometric authentication: a holistic approach to
accuracy. Biometric Technology Today, 2015(3), 5-8.
Holz, C., Buthpitiya, S., & Knaust, M. (2015, April). Bodyprint: Biometric user identification on
mobile devices using the capacitive touchscreen to scan body parts. In Proceedings of the
33rd annual ACM conference on human factors in computing systems (pp. 3011-3014).
ACM.
Farooq, M. U., Waseem, M., Khairi, A., & Mazhar, S. (2015). A critical analysis on the security
concerns of internet of things (IoT). International Journal of Computer
Applications, 111(7).
French, P., Foulkes, P., Harrison, P., Hughes, V., San Segundo, E., & Stevens, L. (2015). The
vocal tract as a biometric: output measures, interrelationships, and efficacy.
In Proceedings of the 18th International Congress of Phonetic Sciences (ICPhS).
Hadid, A. (2014). Face biometrics under spoofing attacks: Vulnerabilities, countermeasures,
open issues, and research directions. In Proceedings of the IEEE Conference on
Computer Vision and Pattern Recognition Workshops (pp. 113-118).
Hadid, A., Evans, N., Marcel, S., & Fierrez, J. (2015). Biometrics systems under spoofing attack:
an evaluation methodology and lessons learned. IEEE Signal Processing
Magazine, 32(5), 20-30.
Hajare, U., Mahajan, R., Jadhav, S., Pingale, N., & Salunke, S. (2018). Efficient Cash
Withdrawal from ATM machine using Mobile Banking.
Haupt, G., & Mozer, T. (2015). Assessing biometric authentication: a holistic approach to
accuracy. Biometric Technology Today, 2015(3), 5-8.
Holz, C., Buthpitiya, S., & Knaust, M. (2015, April). Bodyprint: Biometric user identification on
mobile devices using the capacitive touchscreen to scan body parts. In Proceedings of the
33rd annual ACM conference on human factors in computing systems (pp. 3011-3014).
ACM.

14INFORMATION SECURITY
Jain, A., Dedhia, R., & Patil, A. (2015). Enhancing the security of caesar cipher substitution
method using a randomized approach for more secure communication. arXiv preprint
arXiv:1512.05483.
Karabina, K., & Robinson, A. (2016, August). Revisiting the False Acceptance Rate Attack on
Biometric Visual Cryptographic Schemes. In International Conference on Information
Theoretic Security (pp. 114-125). Springer, Cham.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart
device environment. In Mobile and Wireless Technology 2015 (pp. 199-206). Springer,
Berlin, Heidelberg.
Kubbo, M., Jayabalan, M., & Rana, M. E. (2016, September). Privacy and Security Challenges
in Cloud Based Electronic Health Record: Towards Access Control Model. In The Third
International Conference on Digital Security and Forensics (DigitalSec2016) (p. 113).
Meng, W., Wong, D. S., Furnell, S., & Zhou, J. (2015). Surveying the development of biometric
user authentication on mobile phones. IEEE Communications Surveys & Tutorials, 17(3),
1268-1293.
Oktaviana, B., & Siahaan, A. P. U. (2016). Three-Pass Protocol Implementation in Caesar
Cipher Classic Cryptography. IOSR Journal of Computer Engineering (IOSR-
JCE), 18(4), 26-29.
Purnama, B., & Rohayani, A. H. (2015). A New Modified Caesar Cipher Cryptography Method
with LegibleCiphertext From a Message to Be Encrypted. Procedia Computer
Science, 59, 195-204.
Jain, A., Dedhia, R., & Patil, A. (2015). Enhancing the security of caesar cipher substitution
method using a randomized approach for more secure communication. arXiv preprint
arXiv:1512.05483.
Karabina, K., & Robinson, A. (2016, August). Revisiting the False Acceptance Rate Attack on
Biometric Visual Cryptographic Schemes. In International Conference on Information
Theoretic Security (pp. 114-125). Springer, Cham.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart
device environment. In Mobile and Wireless Technology 2015 (pp. 199-206). Springer,
Berlin, Heidelberg.
Kubbo, M., Jayabalan, M., & Rana, M. E. (2016, September). Privacy and Security Challenges
in Cloud Based Electronic Health Record: Towards Access Control Model. In The Third
International Conference on Digital Security and Forensics (DigitalSec2016) (p. 113).
Meng, W., Wong, D. S., Furnell, S., & Zhou, J. (2015). Surveying the development of biometric
user authentication on mobile phones. IEEE Communications Surveys & Tutorials, 17(3),
1268-1293.
Oktaviana, B., & Siahaan, A. P. U. (2016). Three-Pass Protocol Implementation in Caesar
Cipher Classic Cryptography. IOSR Journal of Computer Engineering (IOSR-
JCE), 18(4), 26-29.
Purnama, B., & Rohayani, A. H. (2015). A New Modified Caesar Cipher Cryptography Method
with LegibleCiphertext From a Message to Be Encrypted. Procedia Computer
Science, 59, 195-204.

15INFORMATION SECURITY
Rahim, M. R. (2016). Implementation of biometric authentication methods for home based
systems (Doctoral dissertation, Cardiff Metropolitan University).
Rao, U. H., & Nayak, U. (2014). Physical Security and Biometrics. In The InfoSec
Handbook (pp. 293-306). Apress, Berkeley, CA.
Raspotnig, C., Karpati, P., & Opdahl, A. L. (2017). Addendum to:" Combined Assessment of
Software Safety and Security Requirements-An Industrial Evaluation of the CHASSIS
Method''.
Risodkar, Y. R., Pawar, A. B., Chavanke, S. N., & Pawar, A. S. (2017). ATM Authentication
with Enhance Security Using GSM. Journal of Science and Technology (JST), 2(5), 01-
05.
Salnitri, M., Dalpiaz, F., & Giorgini, P. (2017). Designing secure business processes with
SecBPMN. Software & Systems Modeling, 16(3), 737-757.
Yuan, C., Sun, X., & Lv, R. (2016). Fingerprint liveness detection based on multi-scale LPQ and
PCA. China Communications, 13(7), 60-65.
Rahim, M. R. (2016). Implementation of biometric authentication methods for home based
systems (Doctoral dissertation, Cardiff Metropolitan University).
Rao, U. H., & Nayak, U. (2014). Physical Security and Biometrics. In The InfoSec
Handbook (pp. 293-306). Apress, Berkeley, CA.
Raspotnig, C., Karpati, P., & Opdahl, A. L. (2017). Addendum to:" Combined Assessment of
Software Safety and Security Requirements-An Industrial Evaluation of the CHASSIS
Method''.
Risodkar, Y. R., Pawar, A. B., Chavanke, S. N., & Pawar, A. S. (2017). ATM Authentication
with Enhance Security Using GSM. Journal of Science and Technology (JST), 2(5), 01-
05.
Salnitri, M., Dalpiaz, F., & Giorgini, P. (2017). Designing secure business processes with
SecBPMN. Software & Systems Modeling, 16(3), 737-757.
Yuan, C., Sun, X., & Lv, R. (2016). Fingerprint liveness detection based on multi-scale LPQ and
PCA. China Communications, 13(7), 60-65.
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




