Information Security Concepts: CIA, ATM Security & Authentication
VerifiedAdded on 2023/06/14
|12
|2845
|300
Homework Assignment
AI Summary
This assignment delves into the core principles of information security, focusing on the CIA Triad (Confidentiality, Integrity, and Availability) and their practical applications. It examines ATM security measures, highlighting vulnerabilities and potential threats, such as card jamming and PIN theft. The discussion extends to biometric authentication, exploring the reasons for user reluctance, including security concerns, forgery risks, and difficulties in changing biometric data. Furthermore, the assignment addresses false positives and false negatives in biometric systems, providing real-world examples. Finally, it includes a practical exercise in decryption using Caesar cipher and substitution methods, demonstrating the process of converting ciphertext to plaintext, with a detailed breakdown of the decryption process applied to a given text, ultimately revealing a hidden message about processor frequency.

Running head: INFORMATION SECURITY
Information Security
Name of Student-
Name of University-
Author’s Note-
Information Security
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Question 1:
Confidentiality, integrity, and availability are the three basic privacy factors that deals
with the securing the data in the system. According to Triad, there are many reasons to involve
the three factors in data security.
Confidentiality: The confidentiality ensures to keep the data confidential while the data
is transmitting (Kim et al., 2015). One example of confidentiality is that the data is to be kept
confidential while processing transaction in an ATM. The data that is confidential is only
available with the authorized user, and no other unauthorized user gets the access of the data.
The pin number, card number, and the CVV number are extremely confidential and is to be kept
secret by the user (Bhagavatula et al., 2015). The process by which the data can be kept
confidential is by using the data encryption technique. Data encryption process is applied to the
original text and then the cipher text is transmitted from the sender to the receiver. The
passwords of the account and the CVV number are to be kept private by the user.
Integrity: The process of integrity involves to keep the data accurate, the data consistent
and the data should be have trustworthiness throughout its life. Data integrity ensures that the
information should remain same while it is being transmitted from the receiver to the sender or
vice-versa (Ghosh et al., 2017). Any other unauthorized person should not have the accessibility
of change the data. The file permission should not be given to unauthenticated person. There are
many cryptography methods that can be used to keep the data integrity (Ciuffo & Weiss, 2017).
Example of data integrity is the information that is involved in the ATM is kept to be kept same
while user is using the ATM card. There can also be redundancy algorithms that are used for data
integrity.
Question 1:
Confidentiality, integrity, and availability are the three basic privacy factors that deals
with the securing the data in the system. According to Triad, there are many reasons to involve
the three factors in data security.
Confidentiality: The confidentiality ensures to keep the data confidential while the data
is transmitting (Kim et al., 2015). One example of confidentiality is that the data is to be kept
confidential while processing transaction in an ATM. The data that is confidential is only
available with the authorized user, and no other unauthorized user gets the access of the data.
The pin number, card number, and the CVV number are extremely confidential and is to be kept
secret by the user (Bhagavatula et al., 2015). The process by which the data can be kept
confidential is by using the data encryption technique. Data encryption process is applied to the
original text and then the cipher text is transmitted from the sender to the receiver. The
passwords of the account and the CVV number are to be kept private by the user.
Integrity: The process of integrity involves to keep the data accurate, the data consistent
and the data should be have trustworthiness throughout its life. Data integrity ensures that the
information should remain same while it is being transmitted from the receiver to the sender or
vice-versa (Ghosh et al., 2017). Any other unauthorized person should not have the accessibility
of change the data. The file permission should not be given to unauthenticated person. There are
many cryptography methods that can be used to keep the data integrity (Ciuffo & Weiss, 2017).
Example of data integrity is the information that is involved in the ATM is kept to be kept same
while user is using the ATM card. There can also be redundancy algorithms that are used for data
integrity.

2INFORMATION SECURITY
Availability: The data availability is the most important part in the privacy method of
data security. The data that are available should be present with all the security to the user. The
hardware and the software that are associated with the data should be available to the user, and
there should always a backup storage of data that is available with the user (Alsaadi, 2015). The
firewalls can also be used as an proxy servers to give security to the data available. The user of
the ATM should not lose their data to other some other unauthorized person, which can lead to
data breach (He & Wang, 2015). The systems involved with the system should be upgraded and
the systems should always perform all its functions correctly.
Question 2:
There are many security systems that the ATM that are implemented by the system
developers of ATM. The ATM system provides with many security process. One of those
securities states that the user is not able to enter the ATM pin wrong more than three times. The
customer can enter wrong pin of maximum three times (Rahman & Choo, 2015). The wrong pin
by a customer can be dialed accidentally, or it can be deliberate as well. The security of the ATM
allows three wrong pins and that after that the card usually gets blocked and no more transaction
is possible for that time. In the given scenario, a thief broke into an ATM and jammed the card
reader of the atm. He also broke down keys from the keypad of the ATM machine. After
breaking five keys on the keypad, he was interrupted by a customer who can to withdraw money
from the account. After the successful transaction of the customer, he was not able to take out the
ATM card as the reader was jammed. When he went outside to get some helps, the thief in the
meantime tried with the customer’s card to withdraw some cash. With five keys available, there
Availability: The data availability is the most important part in the privacy method of
data security. The data that are available should be present with all the security to the user. The
hardware and the software that are associated with the data should be available to the user, and
there should always a backup storage of data that is available with the user (Alsaadi, 2015). The
firewalls can also be used as an proxy servers to give security to the data available. The user of
the ATM should not lose their data to other some other unauthorized person, which can lead to
data breach (He & Wang, 2015). The systems involved with the system should be upgraded and
the systems should always perform all its functions correctly.
Question 2:
There are many security systems that the ATM that are implemented by the system
developers of ATM. The ATM system provides with many security process. One of those
securities states that the user is not able to enter the ATM pin wrong more than three times. The
customer can enter wrong pin of maximum three times (Rahman & Choo, 2015). The wrong pin
by a customer can be dialed accidentally, or it can be deliberate as well. The security of the ATM
allows three wrong pins and that after that the card usually gets blocked and no more transaction
is possible for that time. In the given scenario, a thief broke into an ATM and jammed the card
reader of the atm. He also broke down keys from the keypad of the ATM machine. After
breaking five keys on the keypad, he was interrupted by a customer who can to withdraw money
from the account. After the successful transaction of the customer, he was not able to take out the
ATM card as the reader was jammed. When he went outside to get some helps, the thief in the
meantime tried with the customer’s card to withdraw some cash. With five keys available, there
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
are many possibilities to generate a four digit pin. The total outcome of possibilities is 5! / (5-4)!
= 120 times.
Since, there is no possibility in the ATM to input 120 times the trial pin, the thief has
only three hit and trial method to input the pin in the machine. Only three times, the ATM pin
can be tried (Ciuffo & Weiss, 2016). If the thief is lucky enough to get the pin within the three
trial methods, he will be successful in withdrawing the money from the ATM. If all the three trail
pins, tried by the thief gets wrong then the card will be blocked and the there cannot be any
transaction possible for that time. If the card gets blocked there are many security process the
user has to go through. The user will have to call the customer care service of the bank to
unblock the card with certain credentials that will be asked by the customer care agent, and the
second process is that the customer will have to wait for 24 hours before the card starts working.
Question 3:
There are many reasons for which the people finds reluctant to use the biometric
authentication. The following are the reasons for not depending on the biometric authentication.
1) Providing Security: The system of biometric authentication ensures to provide security to all
the organization and the people they work for. The biometric authentication system are to
provide convenience of data, accountability of data, and the system demands that the data
available in the system are very difficult to forge. But, none of the security is totally fulfilled by
the concept of biometric authentication (Layton, 2016). There are many data breach case that are
involved in organizations that uses biometric authentication. The system so biometric has some
other problems as well in the sector of security. There are false acceptance case and false
rejection case in the system for which security cannot be provided properly. The system
are many possibilities to generate a four digit pin. The total outcome of possibilities is 5! / (5-4)!
= 120 times.
Since, there is no possibility in the ATM to input 120 times the trial pin, the thief has
only three hit and trial method to input the pin in the machine. Only three times, the ATM pin
can be tried (Ciuffo & Weiss, 2016). If the thief is lucky enough to get the pin within the three
trial methods, he will be successful in withdrawing the money from the ATM. If all the three trail
pins, tried by the thief gets wrong then the card will be blocked and the there cannot be any
transaction possible for that time. If the card gets blocked there are many security process the
user has to go through. The user will have to call the customer care service of the bank to
unblock the card with certain credentials that will be asked by the customer care agent, and the
second process is that the customer will have to wait for 24 hours before the card starts working.
Question 3:
There are many reasons for which the people finds reluctant to use the biometric
authentication. The following are the reasons for not depending on the biometric authentication.
1) Providing Security: The system of biometric authentication ensures to provide security to all
the organization and the people they work for. The biometric authentication system are to
provide convenience of data, accountability of data, and the system demands that the data
available in the system are very difficult to forge. But, none of the security is totally fulfilled by
the concept of biometric authentication (Layton, 2016). There are many data breach case that are
involved in organizations that uses biometric authentication. The system so biometric has some
other problems as well in the sector of security. There are false acceptance case and false
rejection case in the system for which security cannot be provided properly. The system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
sometimes falsely detects the data of an authenticated user as a unauthenticated one, and
sometimes the data of an authenticated user does not match the data in the database and rejects
the authentication of the user (Alaskar, Vodanovich & Shen, 2015). These are very usual
problems that users face while dealing with the biometric system.
2) As the biometric deals with physiological part of the body, there are many chances of making
a fake fingerprint if the attacker wants to breach the data. the attacker can make a high quality
printing of fingerprint and can do the authentication without the acknowledgement of the
authenticated user (Memon, 2017). The iris scanning can also be tricked by the attacker by the
process of taking photo with a cheap camera at night mode, and then print the paper and also use
a lens to detect the roundness of the eye.
3) The biometric system does not allow the user to change the print of the finger, or scanning or
retina or iris. The Biometric scanning is very difficult to change. This is not the case in
authentication that deals with passwords or ID cards. The passwords can be changed easily, and
there is also a recovery mode if the password is forgotten. So, using the biometric authentication,
it is very difficult to recover the password (Chen, Pande & Mohapatra, 2014). Using another
password or new ID card is much easier than changing the biometric scanning for the
authentication process. The data in the biometric system cannot be changed remotely as done in
password authentication. The user have to be present with the system at the time of scanning.
Question 4:
The case of false positive implies when a biometric system falsely accepts the data of an
unauthenticated user as a valid one and allows the authentication for the unauthorized user. This
hampers the login security of the system (Barbosa & Silva, 2015). There are false positive rates
sometimes falsely detects the data of an authenticated user as a unauthenticated one, and
sometimes the data of an authenticated user does not match the data in the database and rejects
the authentication of the user (Alaskar, Vodanovich & Shen, 2015). These are very usual
problems that users face while dealing with the biometric system.
2) As the biometric deals with physiological part of the body, there are many chances of making
a fake fingerprint if the attacker wants to breach the data. the attacker can make a high quality
printing of fingerprint and can do the authentication without the acknowledgement of the
authenticated user (Memon, 2017). The iris scanning can also be tricked by the attacker by the
process of taking photo with a cheap camera at night mode, and then print the paper and also use
a lens to detect the roundness of the eye.
3) The biometric system does not allow the user to change the print of the finger, or scanning or
retina or iris. The Biometric scanning is very difficult to change. This is not the case in
authentication that deals with passwords or ID cards. The passwords can be changed easily, and
there is also a recovery mode if the password is forgotten. So, using the biometric authentication,
it is very difficult to recover the password (Chen, Pande & Mohapatra, 2014). Using another
password or new ID card is much easier than changing the biometric scanning for the
authentication process. The data in the biometric system cannot be changed remotely as done in
password authentication. The user have to be present with the system at the time of scanning.
Question 4:
The case of false positive implies when a biometric system falsely accepts the data of an
unauthenticated user as a valid one and allows the authentication for the unauthorized user. This
hampers the login security of the system (Barbosa & Silva, 2015). There are false positive rates

5INFORMATION SECURITY
or false acceptance rate that is determined by the ratio of the total number of data that are false
positive to the total number of identification that is done. False negative generally occurs when
the system does not recognize the data of an authenticated user and rejects the authentication
even if the user is an authorized one. There is false negative rate as well. The ratio between the
total number of false negative identification, to that of the total number of identification is the
false negative rate or the false rejection rate (De Luca et al., 2015). There are many examples
that depict the fact that the false negative rate is basically more than the false acceptance rate. In
the month of October 2011, the company named Microsoft Security Essentials faced false
negative rate by thinking Chrome Browser as a malware known as Zbot. Another example of
false negative rate is software developers spens lot of time for tracking the flagged
vulnerabilities.
Question 5:
a) There are many process of converting the text to cipher text. Caesar substitution
method can be used that is similar to transposition method of encrypting as well as decrypting a
text. There are other methods as well. Substitution method can also be used for encryption
process. Other methods that are used for encrypting and decrypting the text are Baconian
method, columnar transposition method, Affine method, Double transportation method.
b) The given text for decryption is:
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
The decryption process is firstly done by applying the given key to the numeric alphabet
values of the text. Then substitution method is applied. After substitution method, a Caesar
or false acceptance rate that is determined by the ratio of the total number of data that are false
positive to the total number of identification that is done. False negative generally occurs when
the system does not recognize the data of an authenticated user and rejects the authentication
even if the user is an authorized one. There is false negative rate as well. The ratio between the
total number of false negative identification, to that of the total number of identification is the
false negative rate or the false rejection rate (De Luca et al., 2015). There are many examples
that depict the fact that the false negative rate is basically more than the false acceptance rate. In
the month of October 2011, the company named Microsoft Security Essentials faced false
negative rate by thinking Chrome Browser as a malware known as Zbot. Another example of
false negative rate is software developers spens lot of time for tracking the flagged
vulnerabilities.
Question 5:
a) There are many process of converting the text to cipher text. Caesar substitution
method can be used that is similar to transposition method of encrypting as well as decrypting a
text. There are other methods as well. Substitution method can also be used for encryption
process. Other methods that are used for encrypting and decrypting the text are Baconian
method, columnar transposition method, Affine method, Double transportation method.
b) The given text for decryption is:
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE
The decryption process is firstly done by applying the given key to the numeric alphabet
values of the text. Then substitution method is applied. After substitution method, a Caesar
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
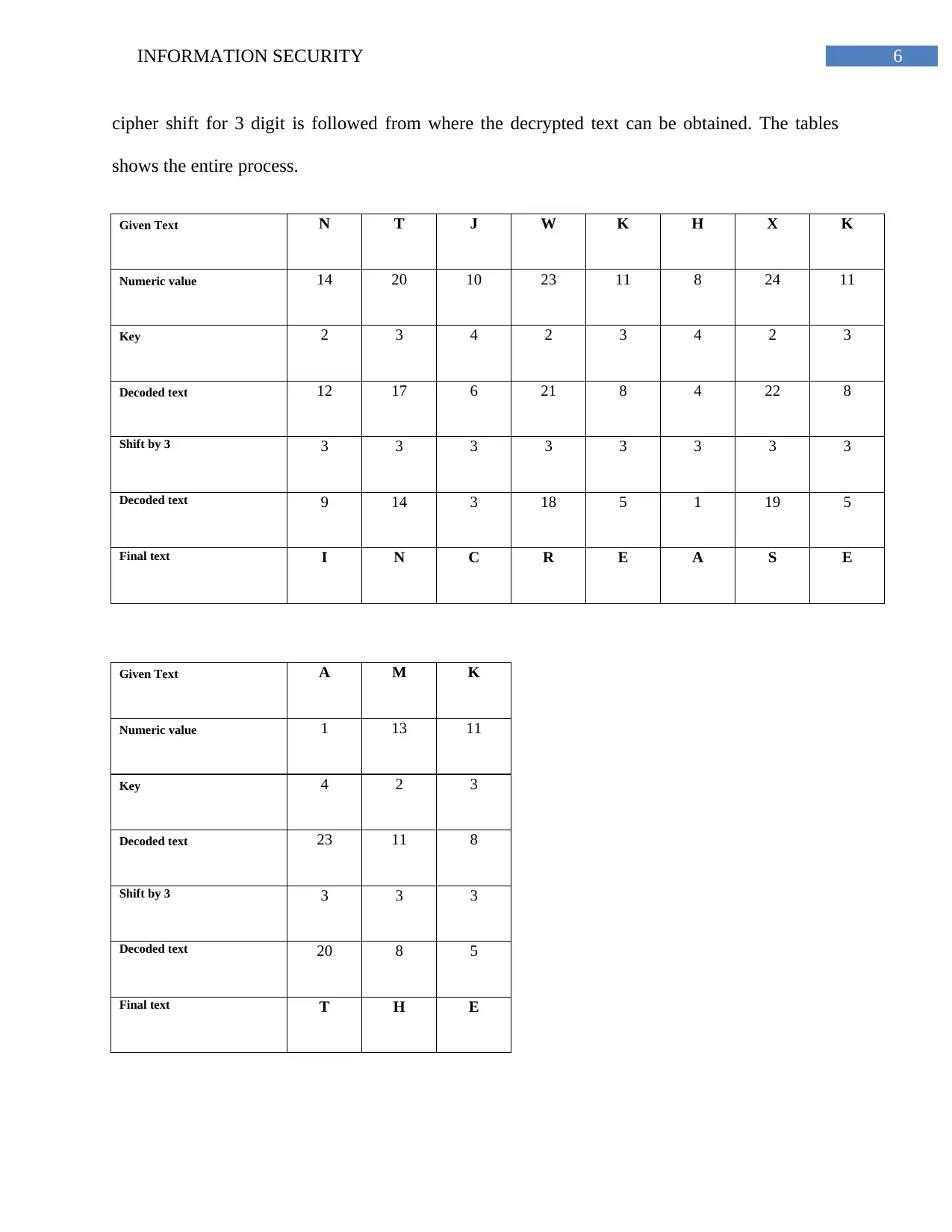
6INFORMATION SECURITY
cipher shift for 3 digit is followed from where the decrypted text can be obtained. The tables
shows the entire process.
Given Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded text 12 17 6 21 8 4 22 8
Shift by 3 3 3 3 3 3 3 3 3
Decoded text 9 14 3 18 5 1 19 5
Final text I N C R E A S E
Given Text A M K
Numeric value 1 13 11
Key 4 2 3
Decoded text 23 11 8
Shift by 3 3 3 3
Decoded text 20 8 5
Final text T H E
cipher shift for 3 digit is followed from where the decrypted text can be obtained. The tables
shows the entire process.
Given Text N T J W K H X K
Numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded text 12 17 6 21 8 4 22 8
Shift by 3 3 3 3 3 3 3 3 3
Decoded text 9 14 3 18 5 1 19 5
Final text I N C R E A S E
Given Text A M K
Numeric value 1 13 11
Key 4 2 3
Decoded text 23 11 8
Shift by 3 3 3 3
Decoded text 20 8 5
Final text T H E
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
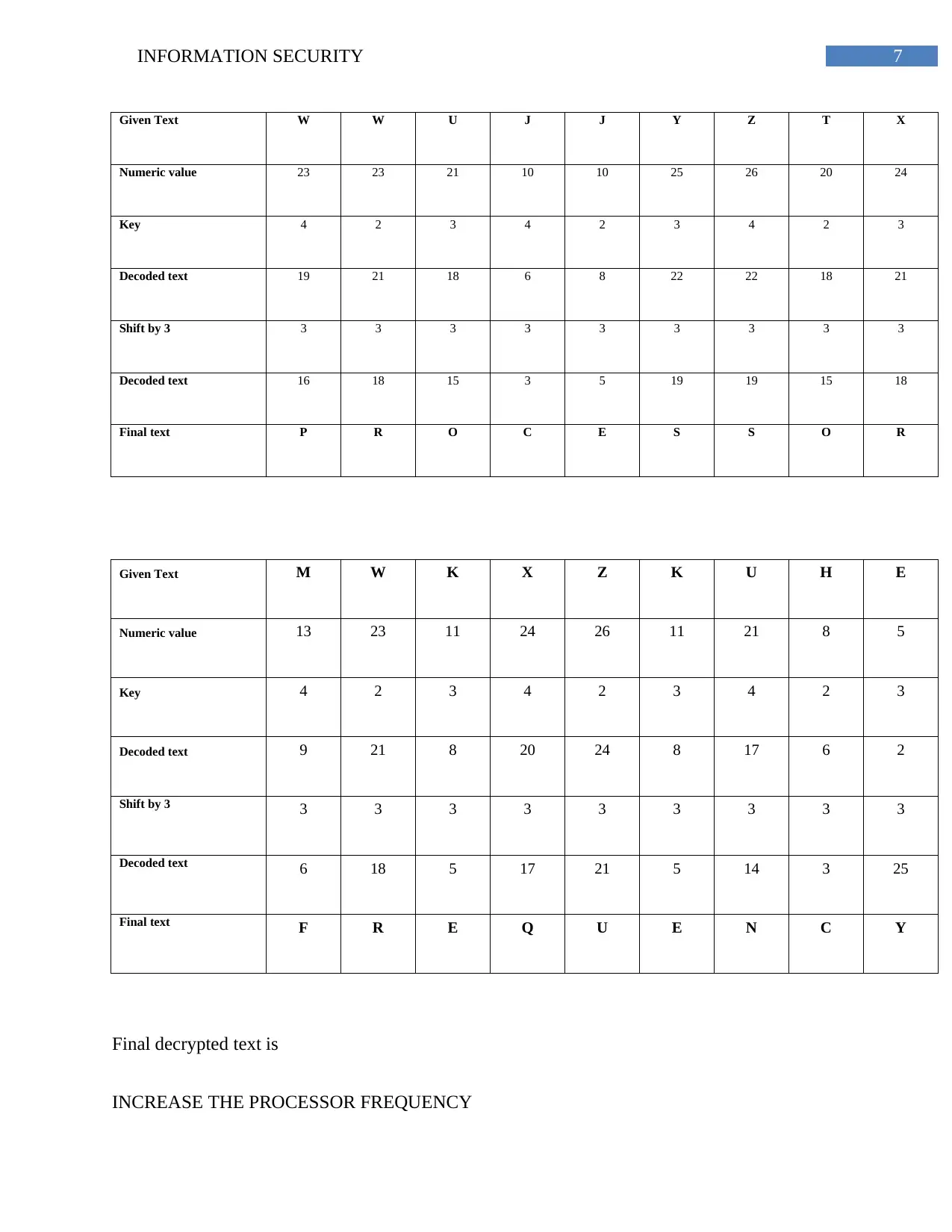
7INFORMATION SECURITY
Given Text W W U J J Y Z T X
Numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded text 19 21 18 6 8 22 22 18 21
Shift by 3 3 3 3 3 3 3 3 3 3
Decoded text 16 18 15 3 5 19 19 15 18
Final text P R O C E S S O R
Given Text M W K X Z K U H E
Numeric value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded text 9 21 8 20 24 8 17 6 2
Shift by 3 3 3 3 3 3 3 3 3 3
Decoded text 6 18 5 17 21 5 14 3 25
Final text F R E Q U E N C Y
Final decrypted text is
INCREASE THE PROCESSOR FREQUENCY
Given Text W W U J J Y Z T X
Numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded text 19 21 18 6 8 22 22 18 21
Shift by 3 3 3 3 3 3 3 3 3 3
Decoded text 16 18 15 3 5 19 19 15 18
Final text P R O C E S S O R
Given Text M W K X Z K U H E
Numeric value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded text 9 21 8 20 24 8 17 6 2
Shift by 3 3 3 3 3 3 3 3 3 3
Decoded text 6 18 5 17 21 5 14 3 25
Final text F R E Q U E N C Y
Final decrypted text is
INCREASE THE PROCESSOR FREQUENCY

8INFORMATION SECURITY
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY
REFERENCES
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption. Proc. USEC, 1-2.
De Luca, A., Hang, A., Von Zezschwitz, E., & Hussmann, H. (2015, April). I feel like I'm taking
selfies all day!: towards understanding biometric authentication on smartphones.
In Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing
Systems (pp. 1411-1414). ACM.
Ghosh, S., Majumder, A., Goswami, J., Kumar, A., Mohanty, S. P., & Bhattacharyya, B. K.
(2017). Swing-Pay: One Card Meets All User Payment and Identity Needs: A Digital
Card Module using NFC and Biometric Authentication for Peer-to-Peer Payment. IEEE
Consumer Electronics Magazine, 6(1), 82-93.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart
device environment. In Mobile and Wireless Technology 2015 (pp. 199-206). Springer,
Berlin, Heidelberg.
Memon, N. (2017). How Biometric Authentication Poses New Challenges to Our Security and
Privacy [In the Spotlight]. IEEE Signal Processing Magazine, 34(4), 196-194.
REFERENCES
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages,
Disadvantages And Future Development: A Review. International Journal Of Scientific
& Technology Research, 4(8), 285-289.
Bhagavatula, C., Ur, B., Iacovino, K., Kywe, S. M., Cranor, L. F., & Savvides, M. (2015).
Biometric authentication on iphone and android: Usability, perceptions, and influences on
adoption. Proc. USEC, 1-2.
De Luca, A., Hang, A., Von Zezschwitz, E., & Hussmann, H. (2015, April). I feel like I'm taking
selfies all day!: towards understanding biometric authentication on smartphones.
In Proceedings of the 33rd Annual ACM Conference on Human Factors in Computing
Systems (pp. 1411-1414). ACM.
Ghosh, S., Majumder, A., Goswami, J., Kumar, A., Mohanty, S. P., & Bhattacharyya, B. K.
(2017). Swing-Pay: One Card Meets All User Payment and Identity Needs: A Digital
Card Module using NFC and Biometric Authentication for Peer-to-Peer Payment. IEEE
Consumer Electronics Magazine, 6(1), 82-93.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart
device environment. In Mobile and Wireless Technology 2015 (pp. 199-206). Springer,
Berlin, Heidelberg.
Memon, N. (2017). How Biometric Authentication Poses New Challenges to Our Security and
Privacy [In the Spotlight]. IEEE Signal Processing Magazine, 34(4), 196-194.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SECURITY
Ab Rahman, N. H., & Choo, K. K. R. (2015). A survey of information security incident handling
in the cloud. Computers & Security, 49, 45-69.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
Layton, T. P. (2016). Information Security: Design, implementation, measurement, and
compliance. CRC Press.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an
enhanced biometric authentication system for smartphones. In Proceedings of the 12th
annual international conference on Mobile systems, applications, and services (pp. 109-
122). ACM.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an
enhanced biometric authentication system for smartphones. In Proceedings of the 12th
annual international conference on Mobile systems, applications, and services (pp. 109-
122). ACM.
Alaskar, M., Vodanovich, S., & Shen, K. N. (2015, January). Evolvement of Information
Security Research on Employees' Behavior: A Systematic Review and Future Direction.
In System Sciences (HICSS), 2015 48th Hawaii International Conference on (pp. 4241-
4250). IEEE.
Barbosa, F. G., & Silva, W. L. S. (2015, November). Support vector machines, Mel-Frequency
Cepstral Coefficients and the Discrete Cosine Transform applied on voice based
Ab Rahman, N. H., & Choo, K. K. R. (2015). A survey of information security incident handling
in the cloud. Computers & Security, 49, 45-69.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver
environment. IEEE Systems Journal, 9(3), 816-823.
Layton, T. P. (2016). Information Security: Design, implementation, measurement, and
compliance. CRC Press.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an
enhanced biometric authentication system for smartphones. In Proceedings of the 12th
annual international conference on Mobile systems, applications, and services (pp. 109-
122). ACM.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an
enhanced biometric authentication system for smartphones. In Proceedings of the 12th
annual international conference on Mobile systems, applications, and services (pp. 109-
122). ACM.
Alaskar, M., Vodanovich, S., & Shen, K. N. (2015, January). Evolvement of Information
Security Research on Employees' Behavior: A Systematic Review and Future Direction.
In System Sciences (HICSS), 2015 48th Hawaii International Conference on (pp. 4241-
4250). IEEE.
Barbosa, F. G., & Silva, W. L. S. (2015, November). Support vector machines, Mel-Frequency
Cepstral Coefficients and the Discrete Cosine Transform applied on voice based

11INFORMATION SECURITY
biometric authentication. In SAI Intelligent Systems Conference (IntelliSys), 2015 (pp.
1032-1039). IEEE.
Thomas, K. P., Vinod, A. P., & Robinson, N. (2017, March). Online Biometric Authentication
Using Subject-Specific Band Power features of EEG. In Proceedings of the 2017
International Conference on Cryptography, Security and Privacy (pp. 136-141). ACM.
Ciuffo, F., & Weiss, G. M. (2017, October). Smartwatch-based transcription biometrics.
In Ubiquitous Computing, Electronics and Mobile Communication Conference
(UEMCON), 2017 IEEE 8th Annual (pp. 145-149). IEEE.
Ciuffo, F., & Weiss, G. M. (2017, October). Smartwatch-based transcription biometrics.
In Ubiquitous Computing, Electronics and Mobile Communication Conference
(UEMCON), 2017 IEEE 8th Annual (pp. 145-149). IEEE.
biometric authentication. In SAI Intelligent Systems Conference (IntelliSys), 2015 (pp.
1032-1039). IEEE.
Thomas, K. P., Vinod, A. P., & Robinson, N. (2017, March). Online Biometric Authentication
Using Subject-Specific Band Power features of EEG. In Proceedings of the 2017
International Conference on Cryptography, Security and Privacy (pp. 136-141). ACM.
Ciuffo, F., & Weiss, G. M. (2017, October). Smartwatch-based transcription biometrics.
In Ubiquitous Computing, Electronics and Mobile Communication Conference
(UEMCON), 2017 IEEE 8th Annual (pp. 145-149). IEEE.
Ciuffo, F., & Weiss, G. M. (2017, October). Smartwatch-based transcription biometrics.
In Ubiquitous Computing, Electronics and Mobile Communication Conference
(UEMCON), 2017 IEEE 8th Annual (pp. 145-149). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




