CSI2102 - Information Security Report: WAS Swim Association Analysis
VerifiedAdded on 2023/06/04
|16
|3717
|433
Report
AI Summary
This report provides a comprehensive analysis of the information security plan for the WAS Swim Association (WASSA), a fictitious organization representing over 500 members and 5 associated clubs in Western Australia. The report begins with an executive summary and an introduction that defines information security and its importance in protecting data confidentiality, integrity, and availability. It then details the information security plan for WASSA, emphasizing the need to safeguard data from various threats. A risk assessment table is presented, identifying both internal and external risks, their severity, probability, and potential impact. The report also includes a classification table for confidential information, categorizing data into confidential, regulated, internal use, and external use classes, with examples. Finally, the report proposes solutions for the identified risks, such as implementing antivirus software and deploying firewalls, to enhance the overall security posture of WASSA. The report is designed to help the WASSA council to protect their data and systems.

Running head: INFORMATION SECURITY
Information Security
Name of the Student
Name of the University
Author’s Note:
Information Security
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
INFORMATION SECURITY
Table of Contents
Executive Summary...................................................................................................................2
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
1. Information Security Plan of WAS Swim Association......................................................3
2. Risk Assessment for WAS Swim Association...................................................................5
3. Classification Table for Confidential Information in WAS Swim Association.................6
4. Solutions for the Identified Risks in WAS Swim Association..........................................9
Conclusion................................................................................................................................11
References................................................................................................................................12
INFORMATION SECURITY
Table of Contents
Executive Summary...................................................................................................................2
Introduction................................................................................................................................3
Discussion..................................................................................................................................3
1. Information Security Plan of WAS Swim Association......................................................3
2. Risk Assessment for WAS Swim Association...................................................................5
3. Classification Table for Confidential Information in WAS Swim Association.................6
4. Solutions for the Identified Risks in WAS Swim Association..........................................9
Conclusion................................................................................................................................11
References................................................................................................................................12

2
INFORMATION SECURITY
Executive Summary
The major objective of the report is knowing about the case study of WAS Swim Association.
This is one of the fictional swimming associations, which is eventually the main body for
complete administrations of each and every swimmer in Western Australia to represent over
500 members and 5 associated clubs. The information security is the security that is being
applied to the computing devices like smart phones and computers and even the computer
networks for securing the confidential information. This type of information is related to the
mechanisms and processes, by which the organization is executing the various business
operations. The unauthenticated data access is promptly stopped as well as mitigated with
information security. Moreover, the data theft and damage is also stopped and hence the
prevention of the service disruption is also possible. This report has properly explained the
various risks and threats associated with the information system of WAS Swim Association.
Proper solutions are also provided in this report for these identified risks.
INFORMATION SECURITY
Executive Summary
The major objective of the report is knowing about the case study of WAS Swim Association.
This is one of the fictional swimming associations, which is eventually the main body for
complete administrations of each and every swimmer in Western Australia to represent over
500 members and 5 associated clubs. The information security is the security that is being
applied to the computing devices like smart phones and computers and even the computer
networks for securing the confidential information. This type of information is related to the
mechanisms and processes, by which the organization is executing the various business
operations. The unauthenticated data access is promptly stopped as well as mitigated with
information security. Moreover, the data theft and damage is also stopped and hence the
prevention of the service disruption is also possible. This report has properly explained the
various risks and threats associated with the information system of WAS Swim Association.
Proper solutions are also provided in this report for these identified risks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
INFORMATION SECURITY
Introduction
Information security could be designed for the protection of the three factors of
confidentiality, integrity as well as availability of the information or data of computer
systems from all those with all types of malicious intentions (Crossler et al., 2013). These
three factors of CIA are together referred to as the triplet of the information security. This
triad of CIA has evolved for including the possession, authenticity, utility, confidentiality,
availability and integrity. The risk management is properly handled with the help of
information security. Anything that could bring the negative impact within the organizational
information system is termed as a risk. The confidential information should not be changed or
altered under any circumstances. The message could be either modified while transmitting it
someone or could be intercepted even before it is reaching to the intended recipient (Von
Solms & Van Niekerk, 2013). There are various methodologies that are quite helpful in
proper control and mitigation of all types of risks and threats.
This report will be providing a brief description on the WAS Swim Association of
Western Australia. The various details regarding this particular organization and the several
threats of the information system of WAS Swim Association would be given here. Moreover,
a risk matrix showing all the risks and their probable solutions would be provided in the
report.
Discussion
1. Information Security Plan of WAS Swim Association
Information security planning for WAS Swim Association is extremely vital and
significant for them to safeguard the data, resources and information (Peltier, 2013). This
type of plan is extremely important for the protection of these above mentioned resources.
INFORMATION SECURITY
Introduction
Information security could be designed for the protection of the three factors of
confidentiality, integrity as well as availability of the information or data of computer
systems from all those with all types of malicious intentions (Crossler et al., 2013). These
three factors of CIA are together referred to as the triplet of the information security. This
triad of CIA has evolved for including the possession, authenticity, utility, confidentiality,
availability and integrity. The risk management is properly handled with the help of
information security. Anything that could bring the negative impact within the organizational
information system is termed as a risk. The confidential information should not be changed or
altered under any circumstances. The message could be either modified while transmitting it
someone or could be intercepted even before it is reaching to the intended recipient (Von
Solms & Van Niekerk, 2013). There are various methodologies that are quite helpful in
proper control and mitigation of all types of risks and threats.
This report will be providing a brief description on the WAS Swim Association of
Western Australia. The various details regarding this particular organization and the several
threats of the information system of WAS Swim Association would be given here. Moreover,
a risk matrix showing all the risks and their probable solutions would be provided in the
report.
Discussion
1. Information Security Plan of WAS Swim Association
Information security planning for WAS Swim Association is extremely vital and
significant for them to safeguard the data, resources and information (Peltier, 2013). This
type of plan is extremely important for the protection of these above mentioned resources.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
INFORMATION SECURITY
Some of the major reasons for the safeguards to these resources of WAS Swim Association
are given below:
i) The most important and significant reason to create an information security plan in
WAS Swim Association is to properly protect the information from all types of anticipated
risks or threats for maintaining the security and integrity of data (Siponen, Mahmood, &
Pahnila, 2014).
ii) The confidentiality of the sensitive information or data is also ensured with the
proper implementation of this type of information security plan and also by making the major
changes within it.
iii) The next subsequent reason to create the information security plan for WAS Swim
Association would be that a protection shield would be made by ensuring that all the policies
and procedures are followed here (Yang, Shieh & Tzeng, 2013). Hence, the data, resources
and information are utilized properly.
This information security plan within the WAS Swim Association could eventually
provide the mechanism to gain various advantages that are listed below:
i) The most significant advantages of the information security plan is that there is a
perfect identification of several risks and threats that are threatening for these resources and
data (Peltier, 2016).
ii) Another benefit of this type of planning would be that the various threats
associated with the data can be easily and promptly controlled.
iii) A perfect deployment as well as review of this plan help in understanding these
risks and threats.
INFORMATION SECURITY
Some of the major reasons for the safeguards to these resources of WAS Swim Association
are given below:
i) The most important and significant reason to create an information security plan in
WAS Swim Association is to properly protect the information from all types of anticipated
risks or threats for maintaining the security and integrity of data (Siponen, Mahmood, &
Pahnila, 2014).
ii) The confidentiality of the sensitive information or data is also ensured with the
proper implementation of this type of information security plan and also by making the major
changes within it.
iii) The next subsequent reason to create the information security plan for WAS Swim
Association would be that a protection shield would be made by ensuring that all the policies
and procedures are followed here (Yang, Shieh & Tzeng, 2013). Hence, the data, resources
and information are utilized properly.
This information security plan within the WAS Swim Association could eventually
provide the mechanism to gain various advantages that are listed below:
i) The most significant advantages of the information security plan is that there is a
perfect identification of several risks and threats that are threatening for these resources and
data (Peltier, 2016).
ii) Another benefit of this type of planning would be that the various threats
associated with the data can be easily and promptly controlled.
iii) A perfect deployment as well as review of this plan help in understanding these
risks and threats.
5
INFORMATION SECURITY
iv) WAS Swim Association can adjust the various reflection of changes within the
technology and thus all types of internal and external threats to the data security are properly
identified (Singh, 2013).
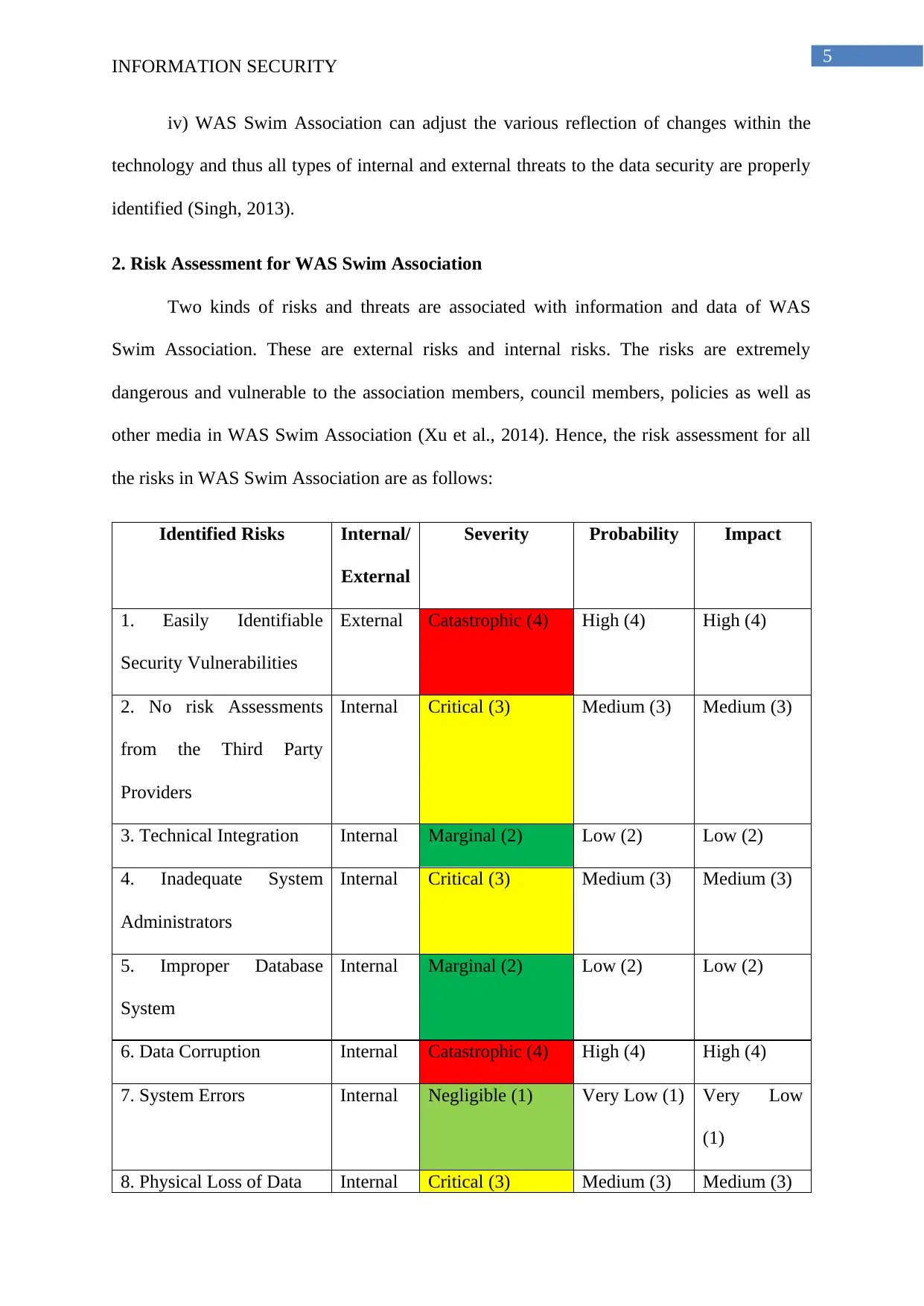
2. Risk Assessment for WAS Swim Association
Two kinds of risks and threats are associated with information and data of WAS
Swim Association. These are external risks and internal risks. The risks are extremely
dangerous and vulnerable to the association members, council members, policies as well as
other media in WAS Swim Association (Xu et al., 2014). Hence, the risk assessment for all
the risks in WAS Swim Association are as follows:
Identified Risks Internal/
External
Severity Probability Impact
1. Easily Identifiable
Security Vulnerabilities
External Catastrophic (4) High (4) High (4)
2. No risk Assessments
from the Third Party
Providers
Internal Critical (3) Medium (3) Medium (3)
3. Technical Integration Internal Marginal (2) Low (2) Low (2)
4. Inadequate System
Administrators
Internal Critical (3) Medium (3) Medium (3)
5. Improper Database
System
Internal Marginal (2) Low (2) Low (2)
6. Data Corruption Internal Catastrophic (4) High (4) High (4)
7. System Errors Internal Negligible (1) Very Low (1) Very Low
(1)
8. Physical Loss of Data Internal Critical (3) Medium (3) Medium (3)
INFORMATION SECURITY
iv) WAS Swim Association can adjust the various reflection of changes within the
technology and thus all types of internal and external threats to the data security are properly
identified (Singh, 2013).
2. Risk Assessment for WAS Swim Association
Two kinds of risks and threats are associated with information and data of WAS
Swim Association. These are external risks and internal risks. The risks are extremely
dangerous and vulnerable to the association members, council members, policies as well as
other media in WAS Swim Association (Xu et al., 2014). Hence, the risk assessment for all
the risks in WAS Swim Association are as follows:
Identified Risks Internal/
External
Severity Probability Impact
1. Easily Identifiable
Security Vulnerabilities
External Catastrophic (4) High (4) High (4)
2. No risk Assessments
from the Third Party
Providers
Internal Critical (3) Medium (3) Medium (3)
3. Technical Integration Internal Marginal (2) Low (2) Low (2)
4. Inadequate System
Administrators
Internal Critical (3) Medium (3) Medium (3)
5. Improper Database
System
Internal Marginal (2) Low (2) Low (2)
6. Data Corruption Internal Catastrophic (4) High (4) High (4)
7. System Errors Internal Negligible (1) Very Low (1) Very Low
(1)
8. Physical Loss of Data Internal Critical (3) Medium (3) Medium (3)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
INFORMATION SECURITY
9. Network Security Issues External Catastrophic (4) High (4) High (4)
10. Malware Attacks External Marginal (2) Low (2) Low (2)
Table 1: Risk Assessment Table of WAS Swim Association
The above risk assessment table has clearly depicted all the risks of this organization
with the levels of severity. Here, 4 is depicted as the highest severity and is termed as
catastrophic and 1 is depicted as the lowest severity and is termed as negligible (Safa, Von
Solms & Furnell, 2016). The probabilities as well as the respective impacts of these identified
risks are also provided here. All of these risks should be removed and eradicated on an
immediate purpose for maintaining the balance between the organization as well as the
confidential and sensitive data or information.
3. Classification Table for Confidential Information in WAS Swim Association
A classification table for the confidential information is responsible for dividing the
various information or data to four specified classes, namely confidential, regulated, internal
uses as well as external uses (Andress, 2014). The classification table of information is
helpful for the organization in dealing with the several kinds of information. Hence, the
utmost protection of all types of information is possible with it. Examples are also provided
within this table.
The respective classification table for the information of the WASSA is given below:
Class of
Information in
WASSA
Explanation of the Class Example of these
Information
1. Confidential The confidential class of sensitive
information is related to WASSA and
The various illustrations of
these information mainly
INFORMATION SECURITY
9. Network Security Issues External Catastrophic (4) High (4) High (4)
10. Malware Attacks External Marginal (2) Low (2) Low (2)
Table 1: Risk Assessment Table of WAS Swim Association
The above risk assessment table has clearly depicted all the risks of this organization
with the levels of severity. Here, 4 is depicted as the highest severity and is termed as
catastrophic and 1 is depicted as the lowest severity and is termed as negligible (Safa, Von
Solms & Furnell, 2016). The probabilities as well as the respective impacts of these identified
risks are also provided here. All of these risks should be removed and eradicated on an
immediate purpose for maintaining the balance between the organization as well as the
confidential and sensitive data or information.
3. Classification Table for Confidential Information in WAS Swim Association
A classification table for the confidential information is responsible for dividing the
various information or data to four specified classes, namely confidential, regulated, internal
uses as well as external uses (Andress, 2014). The classification table of information is
helpful for the organization in dealing with the several kinds of information. Hence, the
utmost protection of all types of information is possible with it. Examples are also provided
within this table.
The respective classification table for the information of the WASSA is given below:
Class of
Information in
WASSA
Explanation of the Class Example of these
Information
1. Confidential The confidential class of sensitive
information is related to WASSA and
The various illustrations of
these information mainly
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
INFORMATION SECURITY
thus it is termed as confidential. This
specific access to all types of
unauthenticated or unauthorized parties
can subsequently cause the entity to
incur all types of company losses
(Parsons et al., 2014). This particular
classification of confidential is
responsible for involving all the details
of information that can solely affect the
respective brand names of the WAS
Swim Association. This information is
not shared with the external users.
Furthermore, the sensitive and
important information can also develop
all types of insider threats within the
organization (Soomro, Shah & Ahmed,
2016). Moreover, these information
that can be kept secret from the various
unauthenticated parties is even called
the confidential.
involve the documentations
of administrators and even
all other board members,
budgets and strategy
memoranda, non-published
accounting material, the
transactional information
and the various strategies
regarding the long term
development and many
others.
2. Regulated The second kind of information that is
eventually governed by each and every
regulatory restriction is regulated type.
This regulated data can only be
accessed by the authorized or
The most significant
examples of these regulated
information major involve
the procedures and policies
that are associated with
INFORMATION SECURITY
thus it is termed as confidential. This
specific access to all types of
unauthenticated or unauthorized parties
can subsequently cause the entity to
incur all types of company losses
(Parsons et al., 2014). This particular
classification of confidential is
responsible for involving all the details
of information that can solely affect the
respective brand names of the WAS
Swim Association. This information is
not shared with the external users.
Furthermore, the sensitive and
important information can also develop
all types of insider threats within the
organization (Soomro, Shah & Ahmed,
2016). Moreover, these information
that can be kept secret from the various
unauthenticated parties is even called
the confidential.
involve the documentations
of administrators and even
all other board members,
budgets and strategy
memoranda, non-published
accounting material, the
transactional information
and the various strategies
regarding the long term
development and many
others.
2. Regulated The second kind of information that is
eventually governed by each and every
regulatory restriction is regulated type.
This regulated data can only be
accessed by the authorized or
The most significant
examples of these regulated
information major involve
the procedures and policies
that are associated with
8
INFORMATION SECURITY
authenticated members of WAS Swim
Association. The utmost care is taken
for the case even before this
information could be utilized, stored
and also transmitted. There is an
authenticated disclosure of the
regulated information that can affect
the clients and employees of WAS
Swim Association. This can also
violate guidelines for regulatory
compliance (Baskerville, Spagnoletti &
Kim, 2014).
information, which is
helpful in keeping the
sensitive data for protecting
with federal laws and
regulations (Shropshire,
Warkentin & Sharma,
2015). PII data of WAS
Swim Association are also
examples of such
information. Regulated
information is quite
important.
3. Internal Uses Internal use category deals with those
data that are used by only the internal
members of WAS Swim Association.
This type of information is not being
accessed by any of the external sources
and hence is accessed by only the
internal users of the organization that
too with proper permission.
The examples of this
information are electronic
mail, reports, internal letters
and memos for WAS Swim
Association (Ab Rahman &
Choo, 2015). Moreover, the
instructions and processes of
these information are also
accessed by the internal
users.
4. External Uses The external use category deals with
those data that are used by the external
users. There is no restriction for data
The best examples of the
external use information are
media posted data or
INFORMATION SECURITY
authenticated members of WAS Swim
Association. The utmost care is taken
for the case even before this
information could be utilized, stored
and also transmitted. There is an
authenticated disclosure of the
regulated information that can affect
the clients and employees of WAS
Swim Association. This can also
violate guidelines for regulatory
compliance (Baskerville, Spagnoletti &
Kim, 2014).
information, which is
helpful in keeping the
sensitive data for protecting
with federal laws and
regulations (Shropshire,
Warkentin & Sharma,
2015). PII data of WAS
Swim Association are also
examples of such
information. Regulated
information is quite
important.
3. Internal Uses Internal use category deals with those
data that are used by only the internal
members of WAS Swim Association.
This type of information is not being
accessed by any of the external sources
and hence is accessed by only the
internal users of the organization that
too with proper permission.
The examples of this
information are electronic
mail, reports, internal letters
and memos for WAS Swim
Association (Ab Rahman &
Choo, 2015). Moreover, the
instructions and processes of
these information are also
accessed by the internal
users.
4. External Uses The external use category deals with
those data that are used by the external
users. There is no restriction for data
The best examples of the
external use information are
media posted data or
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
INFORMATION SECURITY
access at any cost and the data loss is
no possible (Dotcenko, Vladyko &
Letenko, 2014). The external users
could only use those data that are
already available in public.
marketing details of WAS
Swim Association.
4. Solutions for the Identified Risks in WAS Swim Association
There are several important and significant risks that are being identified within the
respective risk matrix of WAS Swim Association. This risk matrix is required to understand
the severity of all risks. A proper removal of these risks are required for WAS Swim
Association so that their confidential information is safe and secured (Flores, Antonsen &
Ekstedt, 2014). There are four type of risks identified in the risk matrix, which are
catastrophic, critical, marginal and negligible and the impacts of these risks are high,
medium, low and very low. However, these risks could be removed by undertaking some of
the most significant and important solutions, which are given below:
i) Implementation of Antivirus Software: The first and the most significant and
important solution for the proper removal of all types of identified risks and threats that are
associated with the information system of WAS Swim Association is to implement the
software of antivirus (Layton, 2016). The antivirus software is one of the most basic and
primitive kind of computer program, which could be easily used to properly and perfectly
prevent, detect and finally eradicate the malicious software and malware. All types of
malware attacks and virus attacks could be perfectly and easily eradicated with the help of
this particular software. Moreover, the other computer threats and risks are also removed with
the help of this particular software (Kolkowska & Dhillon, 2013). Phishing, online identity
threats and risks are easily stopped or removed with the antivirus software.
INFORMATION SECURITY
access at any cost and the data loss is
no possible (Dotcenko, Vladyko &
Letenko, 2014). The external users
could only use those data that are
already available in public.
marketing details of WAS
Swim Association.
4. Solutions for the Identified Risks in WAS Swim Association
There are several important and significant risks that are being identified within the
respective risk matrix of WAS Swim Association. This risk matrix is required to understand
the severity of all risks. A proper removal of these risks are required for WAS Swim
Association so that their confidential information is safe and secured (Flores, Antonsen &
Ekstedt, 2014). There are four type of risks identified in the risk matrix, which are
catastrophic, critical, marginal and negligible and the impacts of these risks are high,
medium, low and very low. However, these risks could be removed by undertaking some of
the most significant and important solutions, which are given below:
i) Implementation of Antivirus Software: The first and the most significant and
important solution for the proper removal of all types of identified risks and threats that are
associated with the information system of WAS Swim Association is to implement the
software of antivirus (Layton, 2016). The antivirus software is one of the most basic and
primitive kind of computer program, which could be easily used to properly and perfectly
prevent, detect and finally eradicate the malicious software and malware. All types of
malware attacks and virus attacks could be perfectly and easily eradicated with the help of
this particular software. Moreover, the other computer threats and risks are also removed with
the help of this particular software (Kolkowska & Dhillon, 2013). Phishing, online identity
threats and risks are easily stopped or removed with the antivirus software.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
INFORMATION SECURITY
ii) Deployment of Firewalls: Another important and significant solution that would be
extremely efficient as well as effective for the appropriate removal of all types of identified
risks and threats associated with the specific information system of the WASSA is to deploy
the software of firewalls (AlHogail, 2015). This firewall, as the name suggests, acts like a
specific wall for any type of threat and risk. This is the significant system of network security
that helps in the proper monitoring as well as controlling the incoming and outgoing network
traffics over the subsequent basis of all pre determined security regulations, policies and
rules. The firewall eventually establishes the barrier within the trusted internal networks and
the untrusted external networks like the Internet connection. There could be two types of
these firewalls, which are either host based firewall and the network firewall. This network
firewall could sieve the traffic within networks (Peltier, 2013). On the other hand, the host-
based firewall runs on the specific host computers and then controls the traffic of the
machines.
iii) Network Controls as well as Network Access: Another important and significant
solution for any type of issues or problems that are associated with the network of the
organization of WAS Swim Association is the significant network control and the network
access. This is a major step for reducing any type of information related threat or risk (Von
Solms & Van Niekerk, 2013). The information or the confidential and sensitive data often
gets hacked and damaged by the hackers or attackers. Several activities are present that can
negatively affect or impact the complete and important operations of peripherals, computers
as well as networks to impede the capability of this network access.
iv) Deployment of DHCP and DNS Servers: The servers of the dynamic host
configuration protocol or the DHCP as well as the domain name system or the DNS should
be eventually deployed in the respective network of WAS Swim Association for perfectly
mitigating all the risks and threats effectively and efficiently (Siponen, Mahmood & Pahnila,
INFORMATION SECURITY
ii) Deployment of Firewalls: Another important and significant solution that would be
extremely efficient as well as effective for the appropriate removal of all types of identified
risks and threats associated with the specific information system of the WASSA is to deploy
the software of firewalls (AlHogail, 2015). This firewall, as the name suggests, acts like a
specific wall for any type of threat and risk. This is the significant system of network security
that helps in the proper monitoring as well as controlling the incoming and outgoing network
traffics over the subsequent basis of all pre determined security regulations, policies and
rules. The firewall eventually establishes the barrier within the trusted internal networks and
the untrusted external networks like the Internet connection. There could be two types of
these firewalls, which are either host based firewall and the network firewall. This network
firewall could sieve the traffic within networks (Peltier, 2013). On the other hand, the host-
based firewall runs on the specific host computers and then controls the traffic of the
machines.
iii) Network Controls as well as Network Access: Another important and significant
solution for any type of issues or problems that are associated with the network of the
organization of WAS Swim Association is the significant network control and the network
access. This is a major step for reducing any type of information related threat or risk (Von
Solms & Van Niekerk, 2013). The information or the confidential and sensitive data often
gets hacked and damaged by the hackers or attackers. Several activities are present that can
negatively affect or impact the complete and important operations of peripherals, computers
as well as networks to impede the capability of this network access.
iv) Deployment of DHCP and DNS Servers: The servers of the dynamic host
configuration protocol or the DHCP as well as the domain name system or the DNS should
be eventually deployed in the respective network of WAS Swim Association for perfectly
mitigating all the risks and threats effectively and efficiently (Siponen, Mahmood & Pahnila,

11
INFORMATION SECURITY
2014). The main benefit of this deployment of DHCP and DNS server is that the access of
data and the loss or damage of data is strictly prohibited by all types of unauthorized access
or hackers. Hence, the confidentiality and integrity of the data is secured.
v) Restriction of the Physical Accessing of Data: Another important and noteworthy
solution for the information security of the organization of WAS Swim Association is
keeping a restriction on the physical accessing of any type of confidential data or information
(Peltier, 2016). WAS Swim Association should ensure the fact only the authorized users are
accessing the data and hence there is absolutely no chance for the data manipulation and data
loss.
Conclusion
Therefore, from this discussion, a proper conclusion could be drawn that the
information security or simply infosec can be stated as the significant set of various
strategies, which would be helpful for the management of various tools, technologies,
procedures and policies that are needed to prevent, detect, document and counter the risks for
both non digital and digital information. The most important responsibilities of this
information security would be an establishment of a collection of several business procedures
that would be substantially required for the protection of information assets and not on the
processing procedure and the process of keeping the information within storage. The major
goals of these programs of IS are CIA for the respective systems of information technology.
These goals eventually ensure the fact that sensitive information or data are getting disclosed
in front of only authenticated parties and thus there is a prevention of unauthorized
modifications of those data. Furthermore, these data can also be accessed and retrieved by all
authorized parties anytime. The process of the risk management is required for this purpose
to assess these vulnerabilities and threats continuously. The above provided report has clearly
demonstrated the various details regarding WAS Swim Association to subsequently
INFORMATION SECURITY
2014). The main benefit of this deployment of DHCP and DNS server is that the access of
data and the loss or damage of data is strictly prohibited by all types of unauthorized access
or hackers. Hence, the confidentiality and integrity of the data is secured.
v) Restriction of the Physical Accessing of Data: Another important and noteworthy
solution for the information security of the organization of WAS Swim Association is
keeping a restriction on the physical accessing of any type of confidential data or information
(Peltier, 2016). WAS Swim Association should ensure the fact only the authorized users are
accessing the data and hence there is absolutely no chance for the data manipulation and data
loss.
Conclusion
Therefore, from this discussion, a proper conclusion could be drawn that the
information security or simply infosec can be stated as the significant set of various
strategies, which would be helpful for the management of various tools, technologies,
procedures and policies that are needed to prevent, detect, document and counter the risks for
both non digital and digital information. The most important responsibilities of this
information security would be an establishment of a collection of several business procedures
that would be substantially required for the protection of information assets and not on the
processing procedure and the process of keeping the information within storage. The major
goals of these programs of IS are CIA for the respective systems of information technology.
These goals eventually ensure the fact that sensitive information or data are getting disclosed
in front of only authenticated parties and thus there is a prevention of unauthorized
modifications of those data. Furthermore, these data can also be accessed and retrieved by all
authorized parties anytime. The process of the risk management is required for this purpose
to assess these vulnerabilities and threats continuously. The above provided report has clearly
demonstrated the various details regarding WAS Swim Association to subsequently
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





