Information Security Management: Risks, Prevention, and Frameworks
VerifiedAdded on 2023/04/21
|11
|2362
|381
AI Summary
This report discusses the importance of information security management in organizations, focusing on the risks associated with mishandling information resources and the steps that can be taken to prevent breaches. It also explores the identification of information assets and the use of risk management frameworks to ensure the security of sensitive data. The report concludes with a discussion on the role of a comprehensive information security management framework in minimizing risks and maintaining the confidentiality, integrity, and availability of information assets.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
information security management
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1 | P a g e
Table of Contents
Introduction................................................................................................................................1
Ethical issues related to mishandling of various information resources....................................1
Steps taken to prevent braeches.................................................................................................1
Identification of information assets........................................................................................2
The risks associated with information assets..........................................................................2
Risk management framework(s).............................................................................................2
Conclusion..................................................................................................................................3
Table of Contents
Introduction................................................................................................................................1
Ethical issues related to mishandling of various information resources....................................1
Steps taken to prevent braeches.................................................................................................1
Identification of information assets........................................................................................2
The risks associated with information assets..........................................................................2
Risk management framework(s).............................................................................................2
Conclusion..................................................................................................................................3

2 | P a g e
Introduction
Information security management is a pre-defined set of rules and policies that are used to
manage all the sensitive data in an organisation. The goal of this security system is to
minimize the risk and ensure that business continuity goes on without any security breach
(Von Solms and Von Solms, 2014). The organisation that is considered in this report is Smart
Software Pty Ltd which is a leading software company based in Melbourne. Thus the risks
plans are developed in a way that integrity, confidentiality and availability of data packets are
maintained.
Ethical issues related to mishandling of various information resources
In case of Smart Software Pty Ltd if information is mishandled by the staff it can cause
security breaches. If resources are not handled correctly then it can cause leakage of personal
data. The sensitive files can be leaked or data loss can be a failure for the organisation. As
given the case study many employees do work from home that can cause security issue if
access is given to some unauthorised user (Von Solms and Von Solms, 2014). The ethical
issues associated in the company if information resources are not handled carefully are
hacking crimes. It is a way in which unauthorised access or man in middle tries to gain access
to authenticated information (Safa and Von Solms, 2016). Cyber criminals design techniques
to read the data from computers thus these issues can be resolved by developing proper
privacy. The virtual private networks that are used by employees can not cause harm if there
are nor securely certified. As listed in the case study some of the resources are open and
public which can cause data breach (Safa and Von Solms, 2016).
Introduction
Information security management is a pre-defined set of rules and policies that are used to
manage all the sensitive data in an organisation. The goal of this security system is to
minimize the risk and ensure that business continuity goes on without any security breach
(Von Solms and Von Solms, 2014). The organisation that is considered in this report is Smart
Software Pty Ltd which is a leading software company based in Melbourne. Thus the risks
plans are developed in a way that integrity, confidentiality and availability of data packets are
maintained.
Ethical issues related to mishandling of various information resources
In case of Smart Software Pty Ltd if information is mishandled by the staff it can cause
security breaches. If resources are not handled correctly then it can cause leakage of personal
data. The sensitive files can be leaked or data loss can be a failure for the organisation. As
given the case study many employees do work from home that can cause security issue if
access is given to some unauthorised user (Von Solms and Von Solms, 2014). The ethical
issues associated in the company if information resources are not handled carefully are
hacking crimes. It is a way in which unauthorised access or man in middle tries to gain access
to authenticated information (Safa and Von Solms, 2016). Cyber criminals design techniques
to read the data from computers thus these issues can be resolved by developing proper
privacy. The virtual private networks that are used by employees can not cause harm if there
are nor securely certified. As listed in the case study some of the resources are open and
public which can cause data breach (Safa and Von Solms, 2016).

3 | P a g e
Steps taken to prevent breaches
Some of the measures that Smart Software Pty Ltd should take to prevent its staff members
from handling information unethically are listed below.
The information should be protected by storing it over a protected network.
Downloads are restricted from any unauthorised users, as well as computers have
access to only secure sites (Ho, Hsu and Yen, 2015).
The open sources software’s that are used by the company should be licenced so risk
of transferring data to external sources are minimised. The system should have
automated security to check passwords and firewall configuration regularly.
Apart from that, an IT team of the company is used to identify suspicious network so
that attacks are identified and then steps are taken (Fakhri, Fahimah and Ibrahim,
2015). It is suggested that threats should be identified by keeping track of all the
suspicious activities.
Smart soft Pvt. Lmt. should deploy a strict but realistic security policy by controlling
the access to data. An access list should be created so that only authorised users are
able to access the information (Fakhri, Fahimah and Ibrahim, 2015). The files are
encrypted while transferring them over the channel so that even if the data is leaked it
is not in a readable format.
The other step that should be taken is by separating the personal and professional
work; the strict rule should be defined by the company that no employee is allowed to
access personal information or emails of computer networks (Kong and You,
Samsung Electronics, 2015).
Steps taken to prevent breaches
Some of the measures that Smart Software Pty Ltd should take to prevent its staff members
from handling information unethically are listed below.
The information should be protected by storing it over a protected network.
Downloads are restricted from any unauthorised users, as well as computers have
access to only secure sites (Ho, Hsu and Yen, 2015).
The open sources software’s that are used by the company should be licenced so risk
of transferring data to external sources are minimised. The system should have
automated security to check passwords and firewall configuration regularly.
Apart from that, an IT team of the company is used to identify suspicious network so
that attacks are identified and then steps are taken (Fakhri, Fahimah and Ibrahim,
2015). It is suggested that threats should be identified by keeping track of all the
suspicious activities.
Smart soft Pvt. Lmt. should deploy a strict but realistic security policy by controlling
the access to data. An access list should be created so that only authorised users are
able to access the information (Fakhri, Fahimah and Ibrahim, 2015). The files are
encrypted while transferring them over the channel so that even if the data is leaked it
is not in a readable format.
The other step that should be taken is by separating the personal and professional
work; the strict rule should be defined by the company that no employee is allowed to
access personal information or emails of computer networks (Kong and You,
Samsung Electronics, 2015).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4 | P a g e
The laptops should be updated regularly this improves security. The operating system
and software’s that are used should be updated regularly so that security breaches are
controlled (Laudon and Laudon, 2015).
The data should be backed up at regular interval so that defence is gained against
ransom ware (Haufe, Colomo-Palacios, Dzombeta, Brandis and Stantchev, 2016).
Antiviruses software’s should be installed in every computer so that data files and
information remains protected.
Identification of information assets
Some of the information assets of Smart Software Pty Ltd are the documented data that is
used to empower communication to reach the goals. The information maintained by the
financial manager and the documents prepared are important informational asset. The plans
that will be followed by the company to achieve success are also considered as information
asset (Safa, et. al, 2015). Information asset of the company consists of enterprise application
that is very sensitive data and should not be leaked as it could be used by the competitors.
Information asset is sensitive information that can to be protected to avoid the risk of breach.
In case of Smart software the information asset that needs to be protected is the software
created by the developed team as it could be hacked by the other companies. The other
important information of Smart software is the database that stores the data set of all the
operations performed (Haufe, Colomo-Palacios, Dzombeta, Brandis and Stantchev, 2016).
The files that are used in the projects also play important role and should be stored over
secure networks. The financial data of the organisation can be considered as the most
significant data asset. Information asset can be any document for file that contains business
needs. These assets need to be controlled so that privacy of data is maintained. The security
The laptops should be updated regularly this improves security. The operating system
and software’s that are used should be updated regularly so that security breaches are
controlled (Laudon and Laudon, 2015).
The data should be backed up at regular interval so that defence is gained against
ransom ware (Haufe, Colomo-Palacios, Dzombeta, Brandis and Stantchev, 2016).
Antiviruses software’s should be installed in every computer so that data files and
information remains protected.
Identification of information assets
Some of the information assets of Smart Software Pty Ltd are the documented data that is
used to empower communication to reach the goals. The information maintained by the
financial manager and the documents prepared are important informational asset. The plans
that will be followed by the company to achieve success are also considered as information
asset (Safa, et. al, 2015). Information asset of the company consists of enterprise application
that is very sensitive data and should not be leaked as it could be used by the competitors.
Information asset is sensitive information that can to be protected to avoid the risk of breach.
In case of Smart software the information asset that needs to be protected is the software
created by the developed team as it could be hacked by the other companies. The other
important information of Smart software is the database that stores the data set of all the
operations performed (Haufe, Colomo-Palacios, Dzombeta, Brandis and Stantchev, 2016).
The files that are used in the projects also play important role and should be stored over
secure networks. The financial data of the organisation can be considered as the most
significant data asset. Information asset can be any document for file that contains business
needs. These assets need to be controlled so that privacy of data is maintained. The security

5 | P a g e
of an organisation is an important aspect and that can be achieved by maintaining integrity,
confidentiality and availability. The data centre system can also be considered as an
important information asset (Saint-Germain, 2005). It can also cause financial loss if the
information is leaked and misused by some unauthorised users. It can also create false brand
image and break the trust of employees.
The risks associated with information assets
Some of the risks that are linked with this information system are issue of privacy. If this
information is accessed by unauthorised users it can cause loss of sensitive data. The risk
should be identified by the leader and top management so that it could be monitored (Peltier,
2016). Apart from that all effectiveness of the process need to be monitored so that risk
associated with it can be tracked. Some of the risk associated with these is financial loss and
reputational risk. It creates instability and attractiveness at the work place (De Lange, Von
Solms and Gerber, 2016). The trust of employees needs to be gained by securing the
information asset. The information asset has risk associated with it as criminals try to access
the data and then they can modify it and might use it in wrong manner. It can cause incorrect
data processing and careless data disposal of data (Chen, Ramamurthy and Wen, 2015).
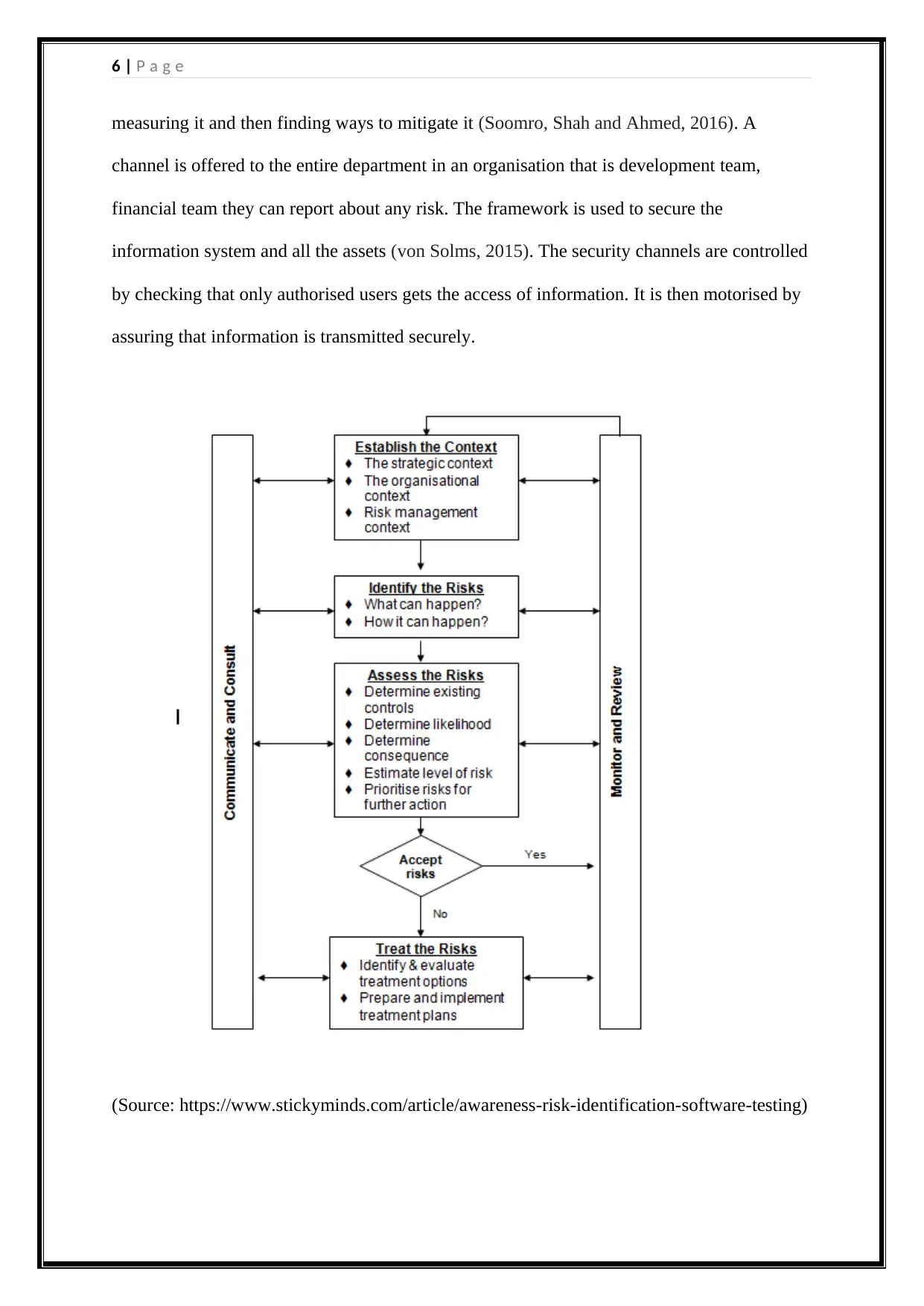
Risk management framework(s)
It is important to adopt a framework through which risk associated in Smart Software Pty
Ltd. is minimized. ORM Framework can be used in this risks are managed by designing some
processes (Ab Rahman and Choo, 2015). They first identify the risk and make sure it does not
penetrate into the system. The objective of using this framework is managing all the risk at
systematic and consistent level (Tsohou, Karyda and Kokolakis, 2015). It balances the risk
taking and risk serving. The decisions are taken in such a way that the information assets are
secure. It makes sure that privacy of data is maintained. This framework also promotes
awareness among people to take actions and enhance confidence. They identify the risk by
of an organisation is an important aspect and that can be achieved by maintaining integrity,
confidentiality and availability. The data centre system can also be considered as an
important information asset (Saint-Germain, 2005). It can also cause financial loss if the
information is leaked and misused by some unauthorised users. It can also create false brand
image and break the trust of employees.
The risks associated with information assets
Some of the risks that are linked with this information system are issue of privacy. If this
information is accessed by unauthorised users it can cause loss of sensitive data. The risk
should be identified by the leader and top management so that it could be monitored (Peltier,
2016). Apart from that all effectiveness of the process need to be monitored so that risk
associated with it can be tracked. Some of the risk associated with these is financial loss and
reputational risk. It creates instability and attractiveness at the work place (De Lange, Von
Solms and Gerber, 2016). The trust of employees needs to be gained by securing the
information asset. The information asset has risk associated with it as criminals try to access
the data and then they can modify it and might use it in wrong manner. It can cause incorrect
data processing and careless data disposal of data (Chen, Ramamurthy and Wen, 2015).
Risk management framework(s)
It is important to adopt a framework through which risk associated in Smart Software Pty
Ltd. is minimized. ORM Framework can be used in this risks are managed by designing some
processes (Ab Rahman and Choo, 2015). They first identify the risk and make sure it does not
penetrate into the system. The objective of using this framework is managing all the risk at
systematic and consistent level (Tsohou, Karyda and Kokolakis, 2015). It balances the risk
taking and risk serving. The decisions are taken in such a way that the information assets are
secure. It makes sure that privacy of data is maintained. This framework also promotes
awareness among people to take actions and enhance confidence. They identify the risk by
6 | P a g e
measuring it and then finding ways to mitigate it (Soomro, Shah and Ahmed, 2016). A
channel is offered to the entire department in an organisation that is development team,
financial team they can report about any risk. The framework is used to secure the
information system and all the assets (von Solms, 2015). The security channels are controlled
by checking that only authorised users gets the access of information. It is then motorised by
assuring that information is transmitted securely.
(Source: https://www.stickyminds.com/article/awareness-risk-identification-software-testing)
measuring it and then finding ways to mitigate it (Soomro, Shah and Ahmed, 2016). A
channel is offered to the entire department in an organisation that is development team,
financial team they can report about any risk. The framework is used to secure the
information system and all the assets (von Solms, 2015). The security channels are controlled
by checking that only authorised users gets the access of information. It is then motorised by
assuring that information is transmitted securely.
(Source: https://www.stickyminds.com/article/awareness-risk-identification-software-testing)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7 | P a g e
The risk management framework follows a stepwise approach it makes sure that
confidentiality, integrity and authentication is met. Once the risks are identified it is accessed
by determining the control measures (Parsons, Young, Butavicius, McCormac, Pattinson
and Jerram, 2015). The level of risk is estimated and it is prioritised so that loss is minimised.
Risk management framework assures that all the software’s and laptops used by the
employees are certified. It can be concluded that this framework is used to identify and fill
the gap between objectives. It ensures that proper communication link is established that
helps in identifying the potential risks. It also improves the monitoring standards. This
framework oversees risk management activities and then defines strategies so that successful
execution takes place.
Conclusion
From this report, it can be concluded that Smart software have various issues associated with
it if the information are not handled carefully. The ethical issues can be resolved by taking
steps through which security breaches can be avoided. It is suggested that all the software’s
should be licenced and the computers should make use of secure virtual private networks so
that chances of data breaches reduces. The information asset of the company are also listed in
ways are found through which risk can be mitigated. One of the risk management
frameworks is also discussed that describes the how it secures the network.
The risk management framework follows a stepwise approach it makes sure that
confidentiality, integrity and authentication is met. Once the risks are identified it is accessed
by determining the control measures (Parsons, Young, Butavicius, McCormac, Pattinson
and Jerram, 2015). The level of risk is estimated and it is prioritised so that loss is minimised.
Risk management framework assures that all the software’s and laptops used by the
employees are certified. It can be concluded that this framework is used to identify and fill
the gap between objectives. It ensures that proper communication link is established that
helps in identifying the potential risks. It also improves the monitoring standards. This
framework oversees risk management activities and then defines strategies so that successful
execution takes place.
Conclusion
From this report, it can be concluded that Smart software have various issues associated with
it if the information are not handled carefully. The ethical issues can be resolved by taking
steps through which security breaches can be avoided. It is suggested that all the software’s
should be licenced and the computers should make use of secure virtual private networks so
that chances of data breaches reduces. The information asset of the company are also listed in
ways are found through which risk can be mitigated. One of the risk management
frameworks is also discussed that describes the how it secures the network.

8 | P a g e
References
Ab Rahman, N.H. and Choo, K.K.R., 2015. A survey of information security incident
handling in the cloud. computers & security, 49, pp.45-69.
Chen, Y.A.N., Ramamurthy, K.R.A.M. and Wen, K.W., 2015. Impacts of comprehensive
information security programs on information security culture. Journal of Computer
Information Systems, 55(3), pp.11-19.
De Lange, J., Von Solms, R. and Gerber, M., 2016, May. Information security management
in local government. In IST-Africa Week Conference, 2016 (pp. 1-11). IEEE.
Fakhri, B., Fahimah, N. and Ibrahim, J., 2015. Information security aligned to enterprise
management. Middle East Journal of Business, 10(1), pp.62-66.
Haufe, K., Colomo-Palacios, R., Dzombeta, S., Brandis, K. and Stantchev, V., 2016. Security
management standards: a mapping. Procedia Computer Science, 100, pp.755-761.
Ho, L.H., Hsu, M.T. and Yen, T.M., 2015. Identifying core control items of information
security management and improvement strategies by applying fuzzy DEMATEL. Information
& Computer Security, 23(2), pp.161-177.
Kong, H.S. and You, Y.H., Samsung Electronics Co Ltd, 2015. Security management system
and method for location-based mobile device. U.S. Patent 9,071,621.
Laudon, K.C. and Laudon, J.P., 2015. Management information systems (Vol. 8). Prentice
Hall.
References
Ab Rahman, N.H. and Choo, K.K.R., 2015. A survey of information security incident
handling in the cloud. computers & security, 49, pp.45-69.
Chen, Y.A.N., Ramamurthy, K.R.A.M. and Wen, K.W., 2015. Impacts of comprehensive
information security programs on information security culture. Journal of Computer
Information Systems, 55(3), pp.11-19.
De Lange, J., Von Solms, R. and Gerber, M., 2016, May. Information security management
in local government. In IST-Africa Week Conference, 2016 (pp. 1-11). IEEE.
Fakhri, B., Fahimah, N. and Ibrahim, J., 2015. Information security aligned to enterprise
management. Middle East Journal of Business, 10(1), pp.62-66.
Haufe, K., Colomo-Palacios, R., Dzombeta, S., Brandis, K. and Stantchev, V., 2016. Security
management standards: a mapping. Procedia Computer Science, 100, pp.755-761.
Ho, L.H., Hsu, M.T. and Yen, T.M., 2015. Identifying core control items of information
security management and improvement strategies by applying fuzzy DEMATEL. Information
& Computer Security, 23(2), pp.161-177.
Kong, H.S. and You, Y.H., Samsung Electronics Co Ltd, 2015. Security management system
and method for location-based mobile device. U.S. Patent 9,071,621.
Laudon, K.C. and Laudon, J.P., 2015. Management information systems (Vol. 8). Prentice
Hall.

9 | P a g e
Parsons, K.M., Young, E., Butavicius, M.A., McCormac, A., Pattinson, M.R. and Jerram, C.,
2015. The influence of organizational information security culture on information security
decision making. Journal of Cognitive Engineering and Decision Making, 9(2), pp.117-129.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T., 2015.
Information security conscious care behaviour formation in organizations. Computers &
Security, 53, pp.65-78.
Saint-Germain, R., 2005. Information security management best practice based on ISO/IEC
17799. Information Management Journal-Prairie Village-, 39(4), p.60.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.
Tsohou, A., Karyda, M. and Kokolakis, S., 2015. Analyzing the role of cognitive and cultural
biases in the internalization of information security policies: recommendations for
information security awareness programs. Computers & security, 52, pp.128-141.
Von Solms, B. and Von Solms, R., 2014. The 10 deadly sins of information security
management. Computers & Security, 23(5), pp.371-376.
von Solms, S.B., 2015. Information Security Governance–compliance management vs
operational management. Computers & Security, 24(6), pp.443-447.
Parsons, K.M., Young, E., Butavicius, M.A., McCormac, A., Pattinson, M.R. and Jerram, C.,
2015. The influence of organizational information security culture on information security
decision making. Journal of Cognitive Engineering and Decision Making, 9(2), pp.117-129.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. Auerbach Publications.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
Safa, N.S., Sookhak, M., Von Solms, R., Furnell, S., Ghani, N.A. and Herawan, T., 2015.
Information security conscious care behaviour formation in organizations. Computers &
Security, 53, pp.65-78.
Saint-Germain, R., 2005. Information security management best practice based on ISO/IEC
17799. Information Management Journal-Prairie Village-, 39(4), p.60.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016. Information security management needs
more holistic approach: A literature review. International Journal of Information
Management, 36(2), pp.215-225.
Tsohou, A., Karyda, M. and Kokolakis, S., 2015. Analyzing the role of cognitive and cultural
biases in the internalization of information security policies: recommendations for
information security awareness programs. Computers & security, 52, pp.128-141.
Von Solms, B. and Von Solms, R., 2014. The 10 deadly sins of information security
management. Computers & Security, 23(5), pp.371-376.
von Solms, S.B., 2015. Information Security Governance–compliance management vs
operational management. Computers & Security, 24(6), pp.443-447.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10 | P a g e
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




