Information Security Management Report for a Mobile App Company
VerifiedAdded on 2023/04/06
|11
|1872
|423
Report
AI Summary
This report provides a detailed analysis of the network security for a mobile application development company. It begins with a network diagram and proceeds to identify and discuss various threats to the network infrastructure, including phishing attacks, social engineering, malware, DNS floods, and Man-in-the-Middle (MITM) attacks. For each threat, the report outlines the potential impact and recommends appropriate security controls, such as administrative, logical, and physical security measures. The report then assesses the risks to network operation, like LAN failures, lack of backups, and outdated security applications, again detailing potential impacts and security controls to mitigate these risks. The conclusion summarizes the key threats and risks, emphasizing the importance of robust security measures to protect the company's data and operations. The report underscores the importance of proactive security management to safeguard against a variety of cyber threats and operational risks, providing a comprehensive overview of the company's security posture.

Running head: INFORMATION SECURITY MANAGEMENT
Information Security Management
Name of the Student
Name of the University
Author Note
Information Security Management
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY MANAGEMENT
Summary
The objective of this report is to analyse the network of the mobile application development
company and based on the network diagram assess the threats and risk of the underlying
infrastructure. Before beginning with the assessment the network diagram is given. Following
the components in the diagram, threats to the components are identified and discussed. Next
appropriate security controls to prevent these threats are listed. Then the risks to operation of
the network are identified and discussed followed by the security controls to avoid these
risks. Then the report ends with conclusions where it is observed that phishing, social
engineering, malware, DNS floods and MITM as the security threats and LAN failure, lack of
backup and outdated security applications as risks likely to affect the company.
Summary
The objective of this report is to analyse the network of the mobile application development
company and based on the network diagram assess the threats and risk of the underlying
infrastructure. Before beginning with the assessment the network diagram is given. Following
the components in the diagram, threats to the components are identified and discussed. Next
appropriate security controls to prevent these threats are listed. Then the risks to operation of
the network are identified and discussed followed by the security controls to avoid these
risks. Then the report ends with conclusions where it is observed that phishing, social
engineering, malware, DNS floods and MITM as the security threats and LAN failure, lack of
backup and outdated security applications as risks likely to affect the company.

2INFORMATION SECURITY MANAGEMENT
Table of Contents
Introduction................................................................................................................................3
Network security assessment.....................................................................................................3
Threats to the network infrastructure.....................................................................................3
Potential impact......................................................................................................................4
Security Controls....................................................................................................................5
Administrative security controls........................................................................................5
Logical security controls....................................................................................................6
Physical security controls...................................................................................................6
Risks to network and applications..........................................................................................7
Potential Impact.....................................................................................................................7
Security controls.....................................................................................................................8
Administrative controls......................................................................................................8
Logical controls..................................................................................................................8
Physical controls................................................................................................................8
Conclusion..................................................................................................................................8
References..................................................................................................................................9
Table of Contents
Introduction................................................................................................................................3
Network security assessment.....................................................................................................3
Threats to the network infrastructure.....................................................................................3
Potential impact......................................................................................................................4
Security Controls....................................................................................................................5
Administrative security controls........................................................................................5
Logical security controls....................................................................................................6
Physical security controls...................................................................................................6
Risks to network and applications..........................................................................................7
Potential Impact.....................................................................................................................7
Security controls.....................................................................................................................8
Administrative controls......................................................................................................8
Logical controls..................................................................................................................8
Physical controls................................................................................................................8
Conclusion..................................................................................................................................8
References..................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
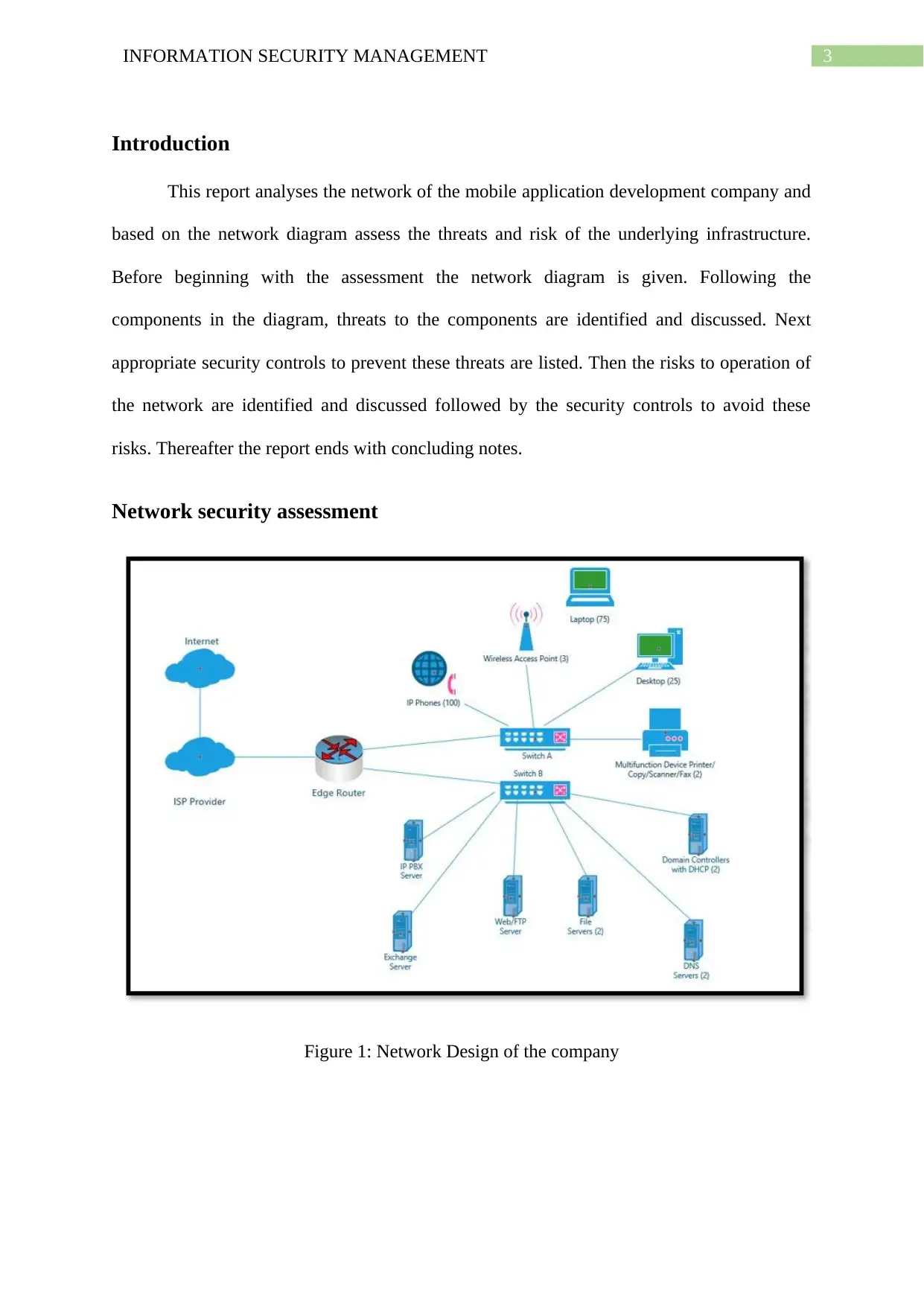
3INFORMATION SECURITY MANAGEMENT
Introduction
This report analyses the network of the mobile application development company and
based on the network diagram assess the threats and risk of the underlying infrastructure.
Before beginning with the assessment the network diagram is given. Following the
components in the diagram, threats to the components are identified and discussed. Next
appropriate security controls to prevent these threats are listed. Then the risks to operation of
the network are identified and discussed followed by the security controls to avoid these
risks. Thereafter the report ends with concluding notes.
Network security assessment
Figure 1: Network Design of the company
Introduction
This report analyses the network of the mobile application development company and
based on the network diagram assess the threats and risk of the underlying infrastructure.
Before beginning with the assessment the network diagram is given. Following the
components in the diagram, threats to the components are identified and discussed. Next
appropriate security controls to prevent these threats are listed. Then the risks to operation of
the network are identified and discussed followed by the security controls to avoid these
risks. Thereafter the report ends with concluding notes.
Network security assessment
Figure 1: Network Design of the company
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY MANAGEMENT
Threats to the network infrastructure
Web server - Phishing attacks help attackers in redirecting victims towards infected sites by
forcing them to click malicious links appearing as legitimate thereby stealing of confidential
data from victims. Several web applications of this kind exists that can lead to attacks to web
servers. These are generally tampering of cookies, tampered Parameter forms, buffer
overflow attacks as also SQL injections (Sarma 2017).
Email server – Attacks like Social engineering employ a wide array of malicious techniques
with the help of user interactions. Social engineering attacks can include e-mail spoofing
through which programs or a person can masquerade as legitimate users by carrying fake
sender information in the e-mails for hiding the actual source (Krombholz et al. 2015).
Computers – Malware attacks are very common threats to desktop PCs and laptops. Malware
or malicious software comes in forms of virus, Backdoor Trojans, spyware as well as other
PUPs (Dahl 2013).
DNS – Amplification and reflection attacks to DNS are a common type of distributed denial
of service or DDoS attacks (Ahmed, Kim & Park, 2017). Open DNS servers that are publicly
accessible are used by attackers to serve as accomplice. Here, spoofed requests are sent by
the attackers to the open DNS servers. These requests ask for very large responses like vast
DNS records thereby freezing the network.
VoIP – Man in the Middle Attacks are the most common among threats faced by VoIP
phones on under secured Wireless connection networks (Schürmann et al. 2017).
Cybercriminals attempt to intercept the SIP messages of call signals. When successful, the
attacker can hijack the calls by rerouting it through redirection servers, enabling them to
inject malwares and spywares and compromise the VoIP device used by the caller.
Threats to the network infrastructure
Web server - Phishing attacks help attackers in redirecting victims towards infected sites by
forcing them to click malicious links appearing as legitimate thereby stealing of confidential
data from victims. Several web applications of this kind exists that can lead to attacks to web
servers. These are generally tampering of cookies, tampered Parameter forms, buffer
overflow attacks as also SQL injections (Sarma 2017).
Email server – Attacks like Social engineering employ a wide array of malicious techniques
with the help of user interactions. Social engineering attacks can include e-mail spoofing
through which programs or a person can masquerade as legitimate users by carrying fake
sender information in the e-mails for hiding the actual source (Krombholz et al. 2015).
Computers – Malware attacks are very common threats to desktop PCs and laptops. Malware
or malicious software comes in forms of virus, Backdoor Trojans, spyware as well as other
PUPs (Dahl 2013).
DNS – Amplification and reflection attacks to DNS are a common type of distributed denial
of service or DDoS attacks (Ahmed, Kim & Park, 2017). Open DNS servers that are publicly
accessible are used by attackers to serve as accomplice. Here, spoofed requests are sent by
the attackers to the open DNS servers. These requests ask for very large responses like vast
DNS records thereby freezing the network.
VoIP – Man in the Middle Attacks are the most common among threats faced by VoIP
phones on under secured Wireless connection networks (Schürmann et al. 2017).
Cybercriminals attempt to intercept the SIP messages of call signals. When successful, the
attacker can hijack the calls by rerouting it through redirection servers, enabling them to
inject malwares and spywares and compromise the VoIP device used by the caller.

5INFORMATION SECURITY MANAGEMENT
Potential impact
Phishing attacks – Phishing attacks can lead to theft of data and sensitive information.
Publicly disclosing internal communications which might embarrass the firm can cause
damage to the reputational thereby tarnishing the brand image.
Social Engineering attack – Social engineering attacks gain success in several stages. First
they start obtaining information user information from the victim. Based on the information
obtained, these attacks create plans and programs tailored to user’s interests and then lure the
user to run the programs. When entertained, the attacker gains control over the user’s system
through the malicious program.
Malware attacks – Malware attacks when successful give malicious entities varying levels of
control on workstations, servers and other network components so as to monitor user activity,
accessing confidential data, changing of privileges, charging of ransoms and the like.
DDoS – DNS floods are distributed denial-of-service attacks or DDoS which enable attackers
to flood the DNS servers of any given domain for attempting disruption of DNS resolution of
the particular domain.
MITM – Man in the middle attack in short MITM is primarily used for stealing sensitive
information and confidential data belonging to corporates. These attacks are typically
invisible to the users, which makes detection and stopping very difficult.
Security Controls
Administrative security controls
1) It is important to track changes being made to security application settings by
individual users and blocking them. Only the update service can be allowed use.
Potential impact
Phishing attacks – Phishing attacks can lead to theft of data and sensitive information.
Publicly disclosing internal communications which might embarrass the firm can cause
damage to the reputational thereby tarnishing the brand image.
Social Engineering attack – Social engineering attacks gain success in several stages. First
they start obtaining information user information from the victim. Based on the information
obtained, these attacks create plans and programs tailored to user’s interests and then lure the
user to run the programs. When entertained, the attacker gains control over the user’s system
through the malicious program.
Malware attacks – Malware attacks when successful give malicious entities varying levels of
control on workstations, servers and other network components so as to monitor user activity,
accessing confidential data, changing of privileges, charging of ransoms and the like.
DDoS – DNS floods are distributed denial-of-service attacks or DDoS which enable attackers
to flood the DNS servers of any given domain for attempting disruption of DNS resolution of
the particular domain.
MITM – Man in the middle attack in short MITM is primarily used for stealing sensitive
information and confidential data belonging to corporates. These attacks are typically
invisible to the users, which makes detection and stopping very difficult.
Security Controls
Administrative security controls
1) It is important to track changes being made to security application settings by
individual users and blocking them. Only the update service can be allowed use.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY MANAGEMENT
2) Another control mechanism for securing individual computers and workstations is to
set security policies in place. One such policy can be preventing systems without antimalware
applications or with outdated security software from accessing the company network (Chen et
al., 2016). This can be accomplished using a network access control application.
3) Security control for phishing: This requires administrators to set up different access levels
for users in trying to open emails. These can be:
Preventing users from sending emails contains embedded hyperlinks.
Blocking attempts to download files from emails
Logical security controls
Logical security controls can be used to prevent the network from getting infected by
DDoS attacks. These can be:
1) Setting passwords: Passwords are very effective and simple method to restrict access to
systems and critical data. Passwords play an important role in security of all systems which
cannot be physically kept apart from users. Legitimate users are provided unique codes
(passwords) every time they require accessing the system. This way hackers can be kept
away
2) Permissions: Several types of user profiles can be created for delegating different access
levels to different users. Permission are vital for those systems that provide access to multiple
users. Profiles of the users can be tracked and records on which user accessed what particular
services or programs can be recorded.
3) Segmentation: Oversight of system administration always serves an important purpose.
Any change made to a system or the network needs to be monitored, reviewed and approved
by another person. This prevents users from knowingly or unknowingly placing the network
at risk.
2) Another control mechanism for securing individual computers and workstations is to
set security policies in place. One such policy can be preventing systems without antimalware
applications or with outdated security software from accessing the company network (Chen et
al., 2016). This can be accomplished using a network access control application.
3) Security control for phishing: This requires administrators to set up different access levels
for users in trying to open emails. These can be:
Preventing users from sending emails contains embedded hyperlinks.
Blocking attempts to download files from emails
Logical security controls
Logical security controls can be used to prevent the network from getting infected by
DDoS attacks. These can be:
1) Setting passwords: Passwords are very effective and simple method to restrict access to
systems and critical data. Passwords play an important role in security of all systems which
cannot be physically kept apart from users. Legitimate users are provided unique codes
(passwords) every time they require accessing the system. This way hackers can be kept
away
2) Permissions: Several types of user profiles can be created for delegating different access
levels to different users. Permission are vital for those systems that provide access to multiple
users. Profiles of the users can be tracked and records on which user accessed what particular
services or programs can be recorded.
3) Segmentation: Oversight of system administration always serves an important purpose.
Any change made to a system or the network needs to be monitored, reviewed and approved
by another person. This prevents users from knowingly or unknowingly placing the network
at risk.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY MANAGEMENT
Physical security controls
1) Smart cards: These cards are special kind of devices that contain micro-chips embedded in
them (Farash, 2017). These are the integrated circuit (IC) chips that store user information
and hence can be used as authorization technique for securing network access by users.
2) Biometric access controls: Biometric access controls are a very effective way of ensuring
access is granted to the right person (Karimian et al., 2018). For biometric fingerprints cannot
be stolen and every access with the registered biometric can always be treated as legitimate
access.
3) Sensors and Alarms: Alarms and sensors can be put in place whenever an unauthorized
attempt to access the network infrastructure is made. This alerts the administrators who can
then take action based on severity of the situation.
Risks to network and applications
The three risks existing in the networks and applications can be:
Failures in the local area network (LAN) and other hardware components
Lack of backup facilities
Inadequate or outdated anti malware security applications
Potential Impact
LAN and Hardware failure: The obvious impact of LAN failures lies in costs. These
expenses occur from loss of production due to idling of work from employees. Additional
costs are incurred from loss of orders from potential clients.
Lack of Backup facilities: Absence of proper backup systems and procedure can lead to
permanent loss of critical data (Ismail et al, 2016). This loss of data can include loss of
financial information, information related to HR, leases and contracts.
Physical security controls
1) Smart cards: These cards are special kind of devices that contain micro-chips embedded in
them (Farash, 2017). These are the integrated circuit (IC) chips that store user information
and hence can be used as authorization technique for securing network access by users.
2) Biometric access controls: Biometric access controls are a very effective way of ensuring
access is granted to the right person (Karimian et al., 2018). For biometric fingerprints cannot
be stolen and every access with the registered biometric can always be treated as legitimate
access.
3) Sensors and Alarms: Alarms and sensors can be put in place whenever an unauthorized
attempt to access the network infrastructure is made. This alerts the administrators who can
then take action based on severity of the situation.
Risks to network and applications
The three risks existing in the networks and applications can be:
Failures in the local area network (LAN) and other hardware components
Lack of backup facilities
Inadequate or outdated anti malware security applications
Potential Impact
LAN and Hardware failure: The obvious impact of LAN failures lies in costs. These
expenses occur from loss of production due to idling of work from employees. Additional
costs are incurred from loss of orders from potential clients.
Lack of Backup facilities: Absence of proper backup systems and procedure can lead to
permanent loss of critical data (Ismail et al, 2016). This loss of data can include loss of
financial information, information related to HR, leases and contracts.

8INFORMATION SECURITY MANAGEMENT
Inadequate Security solutions: Security risks pose serious threats to networks of any
organization (Bonaci et al., 2015). Hence absence of comprehensive firewall or anti-virus
applications can lead to data theft and charging of ransoms from ransomware attacks along
with other severe damages.
Security controls
Administrative controls
LAN equipment should be accessible to select group of admins specialized for
managing networks to ensure the components are always properly configured and patched.
Logical controls
Network configuration should be password protected so that users for attackers find it
difficult to change the existing configuration.
Physical controls
One of the existing file servers to should be configured store backup of company
information as well configuration and diagnostic information of the network.
Conclusion
In conclusion, the report successfully analyses the network of the mobile application
development company and based on the network diagram assess the threats and risk of the
underlying infrastructure. Before beginning with the assessment the network diagram is
given. Following the components in the diagram, threats to the components are identified and
discussed. Next appropriate security controls to prevent these threats are listed. Then the risks
to operation of the network are identified and discussed followed by the security controls to
avoid these risks. It is concluded that phishing, social engineering, malware, DNS floods and
MITM as the security threats and LAN failure, lack of backup and outdated security
applications as risks likely to affect the company.
Inadequate Security solutions: Security risks pose serious threats to networks of any
organization (Bonaci et al., 2015). Hence absence of comprehensive firewall or anti-virus
applications can lead to data theft and charging of ransoms from ransomware attacks along
with other severe damages.
Security controls
Administrative controls
LAN equipment should be accessible to select group of admins specialized for
managing networks to ensure the components are always properly configured and patched.
Logical controls
Network configuration should be password protected so that users for attackers find it
difficult to change the existing configuration.
Physical controls
One of the existing file servers to should be configured store backup of company
information as well configuration and diagnostic information of the network.
Conclusion
In conclusion, the report successfully analyses the network of the mobile application
development company and based on the network diagram assess the threats and risk of the
underlying infrastructure. Before beginning with the assessment the network diagram is
given. Following the components in the diagram, threats to the components are identified and
discussed. Next appropriate security controls to prevent these threats are listed. Then the risks
to operation of the network are identified and discussed followed by the security controls to
avoid these risks. It is concluded that phishing, social engineering, malware, DNS floods and
MITM as the security threats and LAN failure, lack of backup and outdated security
applications as risks likely to affect the company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY MANAGEMENT
References
Ahmed, M. E., Kim, H., & Park, M. (2017, October). Mitigating dns query-based ddos
attacks with machine learning on software-defined networking. In MILCOM 2017-
2017 IEEE Military Communications Conference (MILCOM) (pp. 11-16). IEEE.
Bonaci, T., Herron, J., Yusuf, T., Yan, J., Kohno, T., & Chizeck, H. J. (2015). To make a
robot secure: An experimental analysis of cyber security threats against teleoperated
surgical robots. arXiv preprint arXiv:1504.04339.
Chen, M., Qian, Y., Mao, S., Tang, W., & Yang, X. (2016). Software-defined mobile
networks security. Mobile Networks and Applications, 21(5), 729-743.
Dahl, G.E., Stokes, J.W., Deng, L. and Yu, D., 2013, May. Large-scale malware
classification using random projections and neural networks. In 2013 IEEE
International Conference on Acoustics, Speech and Signal Processing (pp. 3422-
3426). IEEE.
Farash, M. S. (2017). An improved password‐based authentication scheme for session
initiation protocol using smart cards without verification table. International Journal
of Communication Systems, 30(1), e2879.
Ismail, Z., Kiennert, C., Leneutre, J., & Chen, L. (2016). Auditing a cloud provider’s
compliance with data backup requirements: A game theoretical analysis. IEEE
Transactions on Information Forensics and Security, 11(8), 1685-1699.
Karimian, N., Guo, Z., Tehranipoor, F., Woodard, D., Tehranipoor, M., & Forte, D. (2018).
Secure and Reliable Biometric Access Control for Resource-Constrained Systems and
IoT. arXiv preprint arXiv:1803.09710.
References
Ahmed, M. E., Kim, H., & Park, M. (2017, October). Mitigating dns query-based ddos
attacks with machine learning on software-defined networking. In MILCOM 2017-
2017 IEEE Military Communications Conference (MILCOM) (pp. 11-16). IEEE.
Bonaci, T., Herron, J., Yusuf, T., Yan, J., Kohno, T., & Chizeck, H. J. (2015). To make a
robot secure: An experimental analysis of cyber security threats against teleoperated
surgical robots. arXiv preprint arXiv:1504.04339.
Chen, M., Qian, Y., Mao, S., Tang, W., & Yang, X. (2016). Software-defined mobile
networks security. Mobile Networks and Applications, 21(5), 729-743.
Dahl, G.E., Stokes, J.W., Deng, L. and Yu, D., 2013, May. Large-scale malware
classification using random projections and neural networks. In 2013 IEEE
International Conference on Acoustics, Speech and Signal Processing (pp. 3422-
3426). IEEE.
Farash, M. S. (2017). An improved password‐based authentication scheme for session
initiation protocol using smart cards without verification table. International Journal
of Communication Systems, 30(1), e2879.
Ismail, Z., Kiennert, C., Leneutre, J., & Chen, L. (2016). Auditing a cloud provider’s
compliance with data backup requirements: A game theoretical analysis. IEEE
Transactions on Information Forensics and Security, 11(8), 1685-1699.
Karimian, N., Guo, Z., Tehranipoor, F., Woodard, D., Tehranipoor, M., & Forte, D. (2018).
Secure and Reliable Biometric Access Control for Resource-Constrained Systems and
IoT. arXiv preprint arXiv:1803.09710.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SECURITY MANAGEMENT
Krombholz, K., Hobel, H., Huber, M. and Weippl, E., 2015. Advanced social engineering
attacks. Journal of Information Security and applications, 22, pp.113-122.
Sarma, S., 2017. A Study on Common Web Based Hacking and Preventive Measure.
Schürmann, D., Kabus, F., Hildermeier, G., & Wolf, L. (2017). Wiretapping end-to-end
encrypted VoIP calls: real-world attacks on ZRTP. Proceedings on Privacy
Enhancing Technologies, 2017(3), 4-20.
Krombholz, K., Hobel, H., Huber, M. and Weippl, E., 2015. Advanced social engineering
attacks. Journal of Information Security and applications, 22, pp.113-122.
Sarma, S., 2017. A Study on Common Web Based Hacking and Preventive Measure.
Schürmann, D., Kabus, F., Hildermeier, G., & Wolf, L. (2017). Wiretapping end-to-end
encrypted VoIP calls: real-world attacks on ZRTP. Proceedings on Privacy
Enhancing Technologies, 2017(3), 4-20.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




