Risk Assessment on Network Infrastructure of CONVXYZ
VerifiedAdded on 2023/01/19
|27
|3351
|91
AI Summary
This report performs a risk assessment on the network infrastructure of CONVXYZ based on ISO 27005 standards. It includes mapping criteria on assets, identifying vulnerabilities, and determining likelihood and impact levels. The report also discusses risk management and assessment standards such as COBIT, ITIL, and ISO 27001.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

INFORMATION SECURITY MANAGEMENT
Name of the Student
Name of the University
Author Note
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1INFORMATION SECURITY MANAGEMENT
1. INTRODUCTION
In this report, a risk assessment will be performed on the network infrastructure of
CONVXYZ based on ISO 27005 standards. Fists of all the standards will be
reviewed in detail and according to that specific criteria’s will be mapped on the
given network infrastructure of CONVXYZ. First, the design specifies Owner
specification for the network. Now assets of the network classified according to
primary and secondary assets. The explanation for each of the assets provides a
collective explanation for a group of assets instead of explaining for each asset.
Along with that, one vulnerability for each asset defined. The vulnerabilities will
be taken from the
The report provides NVD online vulnerability database along with the official
CVE- number. Once the risks of the network are identified, Likelihood level
computation will be determined, using Boston gird, which will be followed by
Impact table specification.
- Risk management and risk assessment standards
Although there are various risk management and risk assessment standards,
when it is about managing risk in the context of IT infrastructure and network
security, three of the most widely used standards are COBIT, ITIL and ISO
27001.
1. INTRODUCTION
In this report, a risk assessment will be performed on the network infrastructure of
CONVXYZ based on ISO 27005 standards. Fists of all the standards will be
reviewed in detail and according to that specific criteria’s will be mapped on the
given network infrastructure of CONVXYZ. First, the design specifies Owner
specification for the network. Now assets of the network classified according to
primary and secondary assets. The explanation for each of the assets provides a
collective explanation for a group of assets instead of explaining for each asset.
Along with that, one vulnerability for each asset defined. The vulnerabilities will
be taken from the
The report provides NVD online vulnerability database along with the official
CVE- number. Once the risks of the network are identified, Likelihood level
computation will be determined, using Boston gird, which will be followed by
Impact table specification.
- Risk management and risk assessment standards
Although there are various risk management and risk assessment standards,
when it is about managing risk in the context of IT infrastructure and network
security, three of the most widely used standards are COBIT, ITIL and ISO
27001.
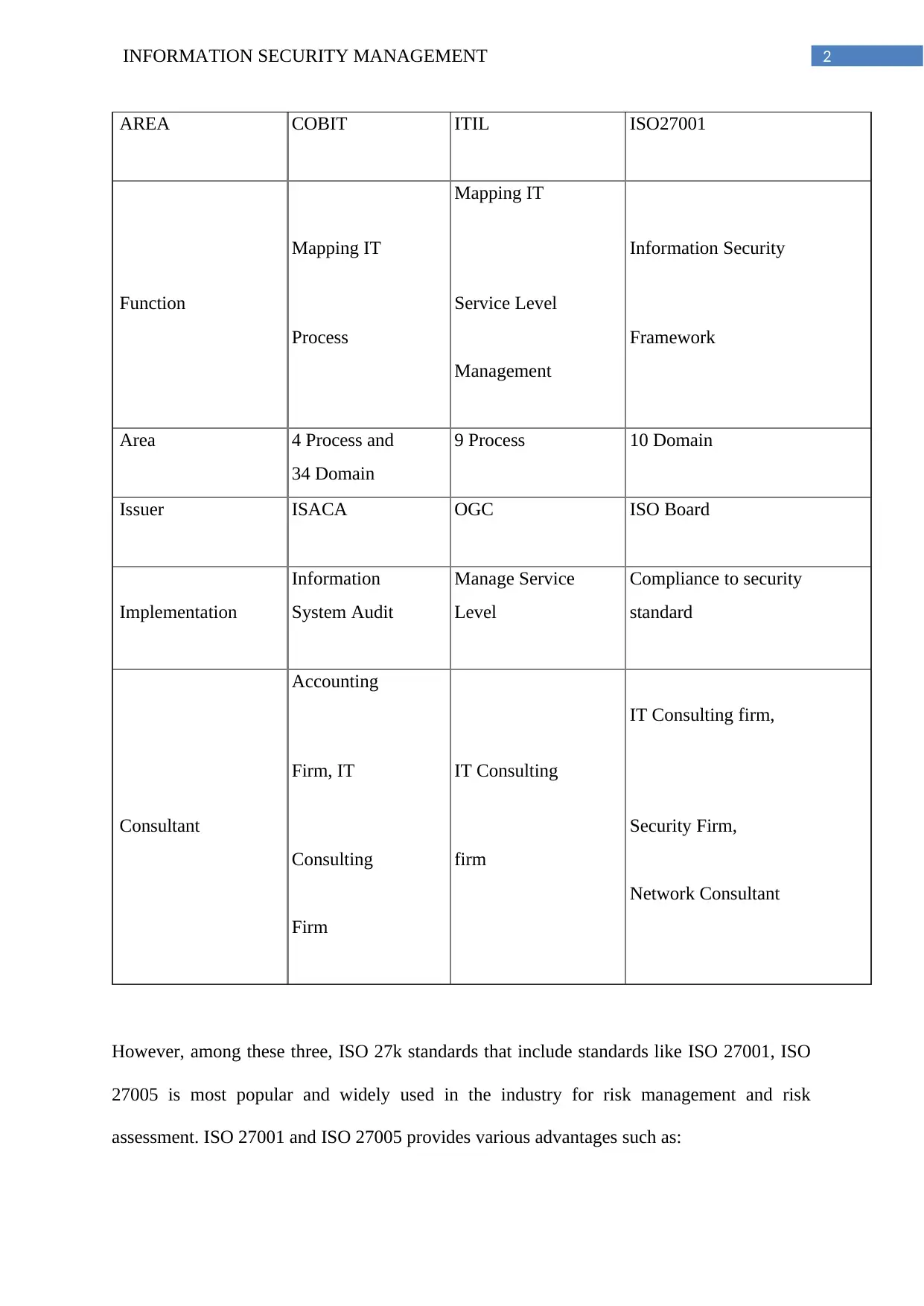
2INFORMATION SECURITY MANAGEMENT
AREA COBIT ITIL ISO27001
Mapping IT
Mapping IT
Information Security
Function Service Level
Process Framework
Management
Area 4 Process and 9 Process 10 Domain
34 Domain
Issuer ISACA OGC ISO Board
Implementation
Information Manage Service Compliance to security
System Audit Level standard
Accounting
IT Consulting firm,
Firm, IT IT Consulting
Consultant Security Firm,
Consulting firm
Network Consultant
Firm
However, among these three, ISO 27k standards that include standards like ISO 27001, ISO
27005 is most popular and widely used in the industry for risk management and risk
assessment. ISO 27001 and ISO 27005 provides various advantages such as:
AREA COBIT ITIL ISO27001
Mapping IT
Mapping IT
Information Security
Function Service Level
Process Framework
Management
Area 4 Process and 9 Process 10 Domain
34 Domain
Issuer ISACA OGC ISO Board
Implementation
Information Manage Service Compliance to security
System Audit Level standard
Accounting
IT Consulting firm,
Firm, IT IT Consulting
Consultant Security Firm,
Consulting firm
Network Consultant
Firm
However, among these three, ISO 27k standards that include standards like ISO 27001, ISO
27005 is most popular and widely used in the industry for risk management and risk
assessment. ISO 27001 and ISO 27005 provides various advantages such as:

3INFORMATION SECURITY MANAGEMENT
It is only international security standards that provide an opportunity for information
auditing
It defines various requirements that are important for an information security
management system (ISMS). An ISMS consists of policies, procedures, processes,
and systems that are essential to managing information risks, such as cyber-crimes,
hacks, data hacks, and theft.
It provides assurance that if an organization has obtained ISO 27001 certifications, it
has integrated best procedures with its information security policy and strategy.
ISO standards provide assistance to organizations in avoiding penalties that are
associated with the data breach
It eliminates the need for frequent auditing
Provide compliance with business, legal, contractual and regulatory requirements
2. System parameters, table.
STAFF PC Windows 8, Intel i3, 8 GB RAM
Customer PC Windows 8, Intel i5, 8 GB RAM
Web servers CentOS 6.8 Enterprise Linux
x86 (Centos.org, 2019)
16 Core - AMD Processor
6376
16 GB RAM
RAID 1
SSD caching
It is only international security standards that provide an opportunity for information
auditing
It defines various requirements that are important for an information security
management system (ISMS). An ISMS consists of policies, procedures, processes,
and systems that are essential to managing information risks, such as cyber-crimes,
hacks, data hacks, and theft.
It provides assurance that if an organization has obtained ISO 27001 certifications, it
has integrated best procedures with its information security policy and strategy.
ISO standards provide assistance to organizations in avoiding penalties that are
associated with the data breach
It eliminates the need for frequent auditing
Provide compliance with business, legal, contractual and regulatory requirements
2. System parameters, table.
STAFF PC Windows 8, Intel i3, 8 GB RAM
Customer PC Windows 8, Intel i5, 8 GB RAM
Web servers CentOS 6.8 Enterprise Linux
x86 (Centos.org, 2019)
16 Core - AMD Processor
6376
16 GB RAM
RAID 1
SSD caching
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
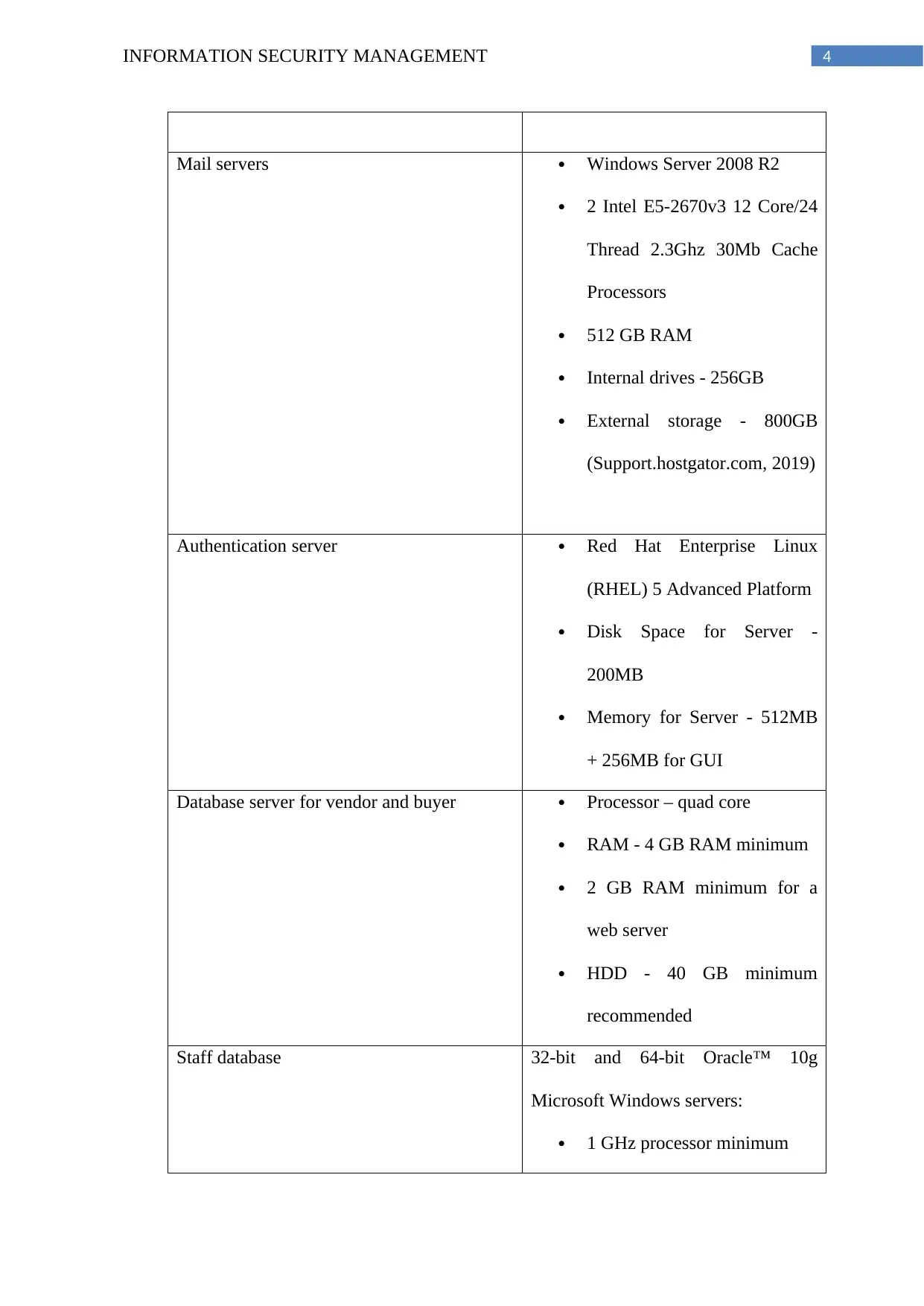
4INFORMATION SECURITY MANAGEMENT
Mail servers Windows Server 2008 R2
2 Intel E5-2670v3 12 Core/24
Thread 2.3Ghz 30Mb Cache
Processors
512 GB RAM
Internal drives - 256GB
External storage - 800GB
(Support.hostgator.com, 2019)
Authentication server Red Hat Enterprise Linux
(RHEL) 5 Advanced Platform
Disk Space for Server -
200MB
Memory for Server - 512MB
+ 256MB for GUI
Database server for vendor and buyer Processor – quad core
RAM - 4 GB RAM minimum
2 GB RAM minimum for a
web server
HDD - 40 GB minimum
recommended
Staff database 32-bit and 64-bit Oracle™ 10g
Microsoft Windows servers:
1 GHz processor minimum
Mail servers Windows Server 2008 R2
2 Intel E5-2670v3 12 Core/24
Thread 2.3Ghz 30Mb Cache
Processors
512 GB RAM
Internal drives - 256GB
External storage - 800GB
(Support.hostgator.com, 2019)
Authentication server Red Hat Enterprise Linux
(RHEL) 5 Advanced Platform
Disk Space for Server -
200MB
Memory for Server - 512MB
+ 256MB for GUI
Database server for vendor and buyer Processor – quad core
RAM - 4 GB RAM minimum
2 GB RAM minimum for a
web server
HDD - 40 GB minimum
recommended
Staff database 32-bit and 64-bit Oracle™ 10g
Microsoft Windows servers:
1 GHz processor minimum

5INFORMATION SECURITY MANAGEMENT
Minimum of 2 GB RAM (8
GB or better is recommended)
free disk space – 100 GB
minimum
Switch The Cisco SGE2000 24-Port Gigabit
Switch (Cisco.com, 2019):
Ports:
● 24 RJ-45 connectors for
10BASE-T/100BASE-TX/100
0BASE-T with 4 shared
Gigabit SFP slots
● Console port
● Auto medium dependent
interface (MDI) and MDI
crossover (MDI-X)
● Auto-negotiate/manual
setting
● RPS port for connecting to
a redundant power supply unit
VLAN:
● Port-based and 802.1Q tag-
based VLANs
● Protocol-based VLAN
● Management VLAN
Minimum of 2 GB RAM (8
GB or better is recommended)
free disk space – 100 GB
minimum
Switch The Cisco SGE2000 24-Port Gigabit
Switch (Cisco.com, 2019):
Ports:
● 24 RJ-45 connectors for
10BASE-T/100BASE-TX/100
0BASE-T with 4 shared
Gigabit SFP slots
● Console port
● Auto medium dependent
interface (MDI) and MDI
crossover (MDI-X)
● Auto-negotiate/manual
setting
● RPS port for connecting to
a redundant power supply unit
VLAN:
● Port-based and 802.1Q tag-
based VLANs
● Protocol-based VLAN
● Management VLAN

6INFORMATION SECURITY MANAGEMENT
● Private VLAN Edge (PVE)
● GVRP
Web user interface:
HTTP/HTTPS
SNMP:
SNMP versions 1, 2c, and
3 with support for traps
RMON:
Embedded RMON
software agent
Firmware upgrade
Web browser upgrade
(HTTP) and Trivial File
Transfer Protocol (TFTP)
Dual images for resilient
firmware upgrades
Firewall Hardware Specifications PA-3260
Interfaces supported
4 (12) 10/100/1000, (8) 1G/10G
● Private VLAN Edge (PVE)
● GVRP
Web user interface:
HTTP/HTTPS
SNMP:
SNMP versions 1, 2c, and
3 with support for traps
RMON:
Embedded RMON
software agent
Firmware upgrade
Web browser upgrade
(HTTP) and Trivial File
Transfer Protocol (TFTP)
Dual images for resilient
firmware upgrades
Firewall Hardware Specifications PA-3260
Interfaces supported
4 (12) 10/100/1000, (8) 1G/10G
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY MANAGEMENT
SFP/SFP+, (4) 40G QSFP+
Management I/O
(1) 10/100/1000 out-of-band
management port, (2)
10/100/1000 high
availability, (1) 10G SFP+
high availability, (1) RJ-45
console port, (1) Micro
USB
Size:
2U, 19” standard rack
(3.5” H x 20.53” D x
17.34” W)
Power supply
650 W AC or DC
(180/240) Redundant
power supply Yes Disk
drives 240 GB SSD
Hot-swappable fans
SFP/SFP+, (4) 40G QSFP+
Management I/O
(1) 10/100/1000 out-of-band
management port, (2)
10/100/1000 high
availability, (1) 10G SFP+
high availability, (1) RJ-45
console port, (1) Micro
USB
Size:
2U, 19” standard rack
(3.5” H x 20.53” D x
17.34” W)
Power supply
650 W AC or DC
(180/240) Redundant
power supply Yes Disk
drives 240 GB SSD
Hot-swappable fans
8INFORMATION SECURITY MANAGEMENT
Yes
3. Risk assessment process
a. Asset classification (primary and supporting) + Asset ID
Primary assets are those that should be incorporate first and once these assets are
incorporated into the system, then only other assets are possible to be
implemented in the system. Such assets are known as secondary assets. Based on
this description, the assets have been classified into primary and secondary assets.
The reason for the same has been defined as well along with the classification.
Assets Assets type Description
STAFF PC Primary It does not require
support for another
resource incorporated
into the system. Rather
Individual
visitors/customers can
browse the website of
CONVXYZ and
register/login with their
PCs via the Internet.
Web servers Secondary Web servers provide
webs pages through
HTTP to the clients of
Yes
3. Risk assessment process
a. Asset classification (primary and supporting) + Asset ID
Primary assets are those that should be incorporate first and once these assets are
incorporated into the system, then only other assets are possible to be
implemented in the system. Such assets are known as secondary assets. Based on
this description, the assets have been classified into primary and secondary assets.
The reason for the same has been defined as well along with the classification.
Assets Assets type Description
STAFF PC Primary It does not require
support for another
resource incorporated
into the system. Rather
Individual
visitors/customers can
browse the website of
CONVXYZ and
register/login with their
PCs via the Internet.
Web servers Secondary Web servers provide
webs pages through
HTTP to the clients of

9INFORMATION SECURITY MANAGEMENT
CONVXYZ once
request for the same is
made. Now it is not
possible to set up a
webs server if necessary
hardware support as
specified in the system
specifications not
incorporated into the
system. Along with that
necessary network,
support is also
necessary to complete
the setup. Hence, it is
classified as a
secondary asset in this
context.
Mail servers Secondary The mail server enables
staff to send and receive
emails from the
customers and other
members of staff. Still,
it is not possible to
execute this
functionality without
CONVXYZ once
request for the same is
made. Now it is not
possible to set up a
webs server if necessary
hardware support as
specified in the system
specifications not
incorporated into the
system. Along with that
necessary network,
support is also
necessary to complete
the setup. Hence, it is
classified as a
secondary asset in this
context.
Mail servers Secondary The mail server enables
staff to send and receive
emails from the
customers and other
members of staff. Still,
it is not possible to
execute this
functionality without
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
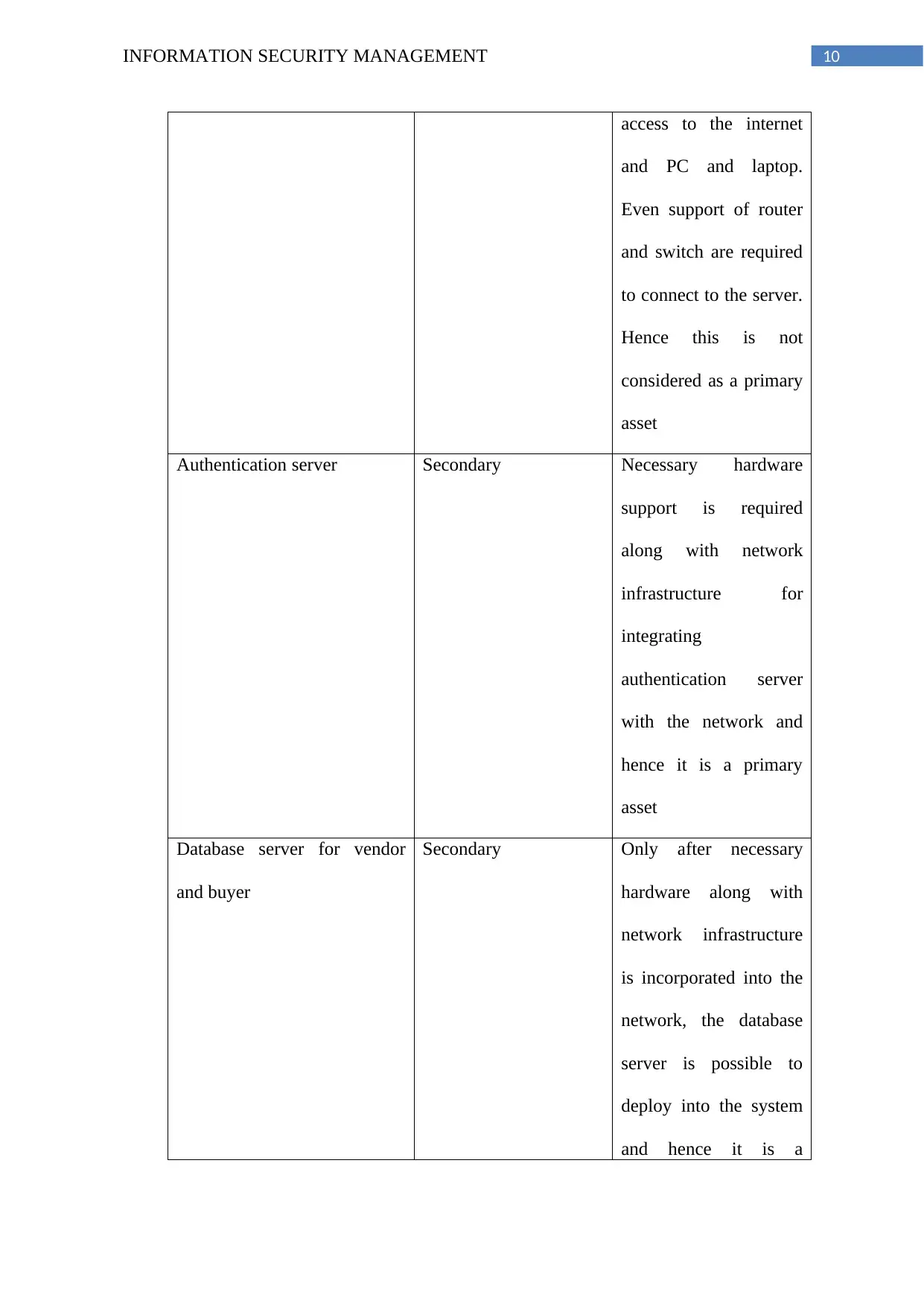
10INFORMATION SECURITY MANAGEMENT
access to the internet
and PC and laptop.
Even support of router
and switch are required
to connect to the server.
Hence this is not
considered as a primary
asset
Authentication server Secondary Necessary hardware
support is required
along with network
infrastructure for
integrating
authentication server
with the network and
hence it is a primary
asset
Database server for vendor
and buyer
Secondary Only after necessary
hardware along with
network infrastructure
is incorporated into the
network, the database
server is possible to
deploy into the system
and hence it is a
access to the internet
and PC and laptop.
Even support of router
and switch are required
to connect to the server.
Hence this is not
considered as a primary
asset
Authentication server Secondary Necessary hardware
support is required
along with network
infrastructure for
integrating
authentication server
with the network and
hence it is a primary
asset
Database server for vendor
and buyer
Secondary Only after necessary
hardware along with
network infrastructure
is incorporated into the
network, the database
server is possible to
deploy into the system
and hence it is a
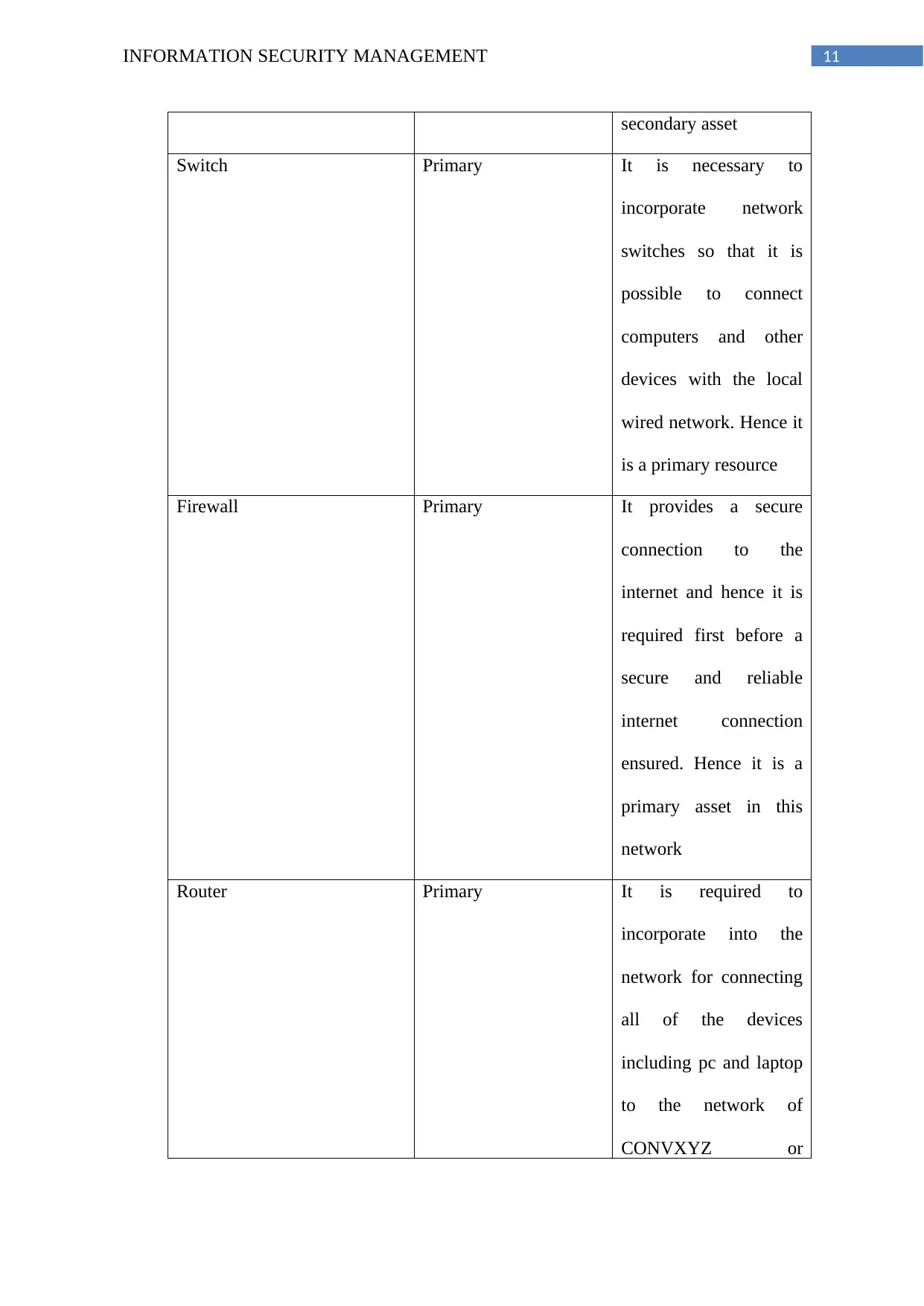
11INFORMATION SECURITY MANAGEMENT
secondary asset
Switch Primary It is necessary to
incorporate network
switches so that it is
possible to connect
computers and other
devices with the local
wired network. Hence it
is a primary resource
Firewall Primary It provides a secure
connection to the
internet and hence it is
required first before a
secure and reliable
internet connection
ensured. Hence it is a
primary asset in this
network
Router Primary It is required to
incorporate into the
network for connecting
all of the devices
including pc and laptop
to the network of
CONVXYZ or
secondary asset
Switch Primary It is necessary to
incorporate network
switches so that it is
possible to connect
computers and other
devices with the local
wired network. Hence it
is a primary resource
Firewall Primary It provides a secure
connection to the
internet and hence it is
required first before a
secure and reliable
internet connection
ensured. Hence it is a
primary asset in this
network
Router Primary It is required to
incorporate into the
network for connecting
all of the devices
including pc and laptop
to the network of
CONVXYZ or
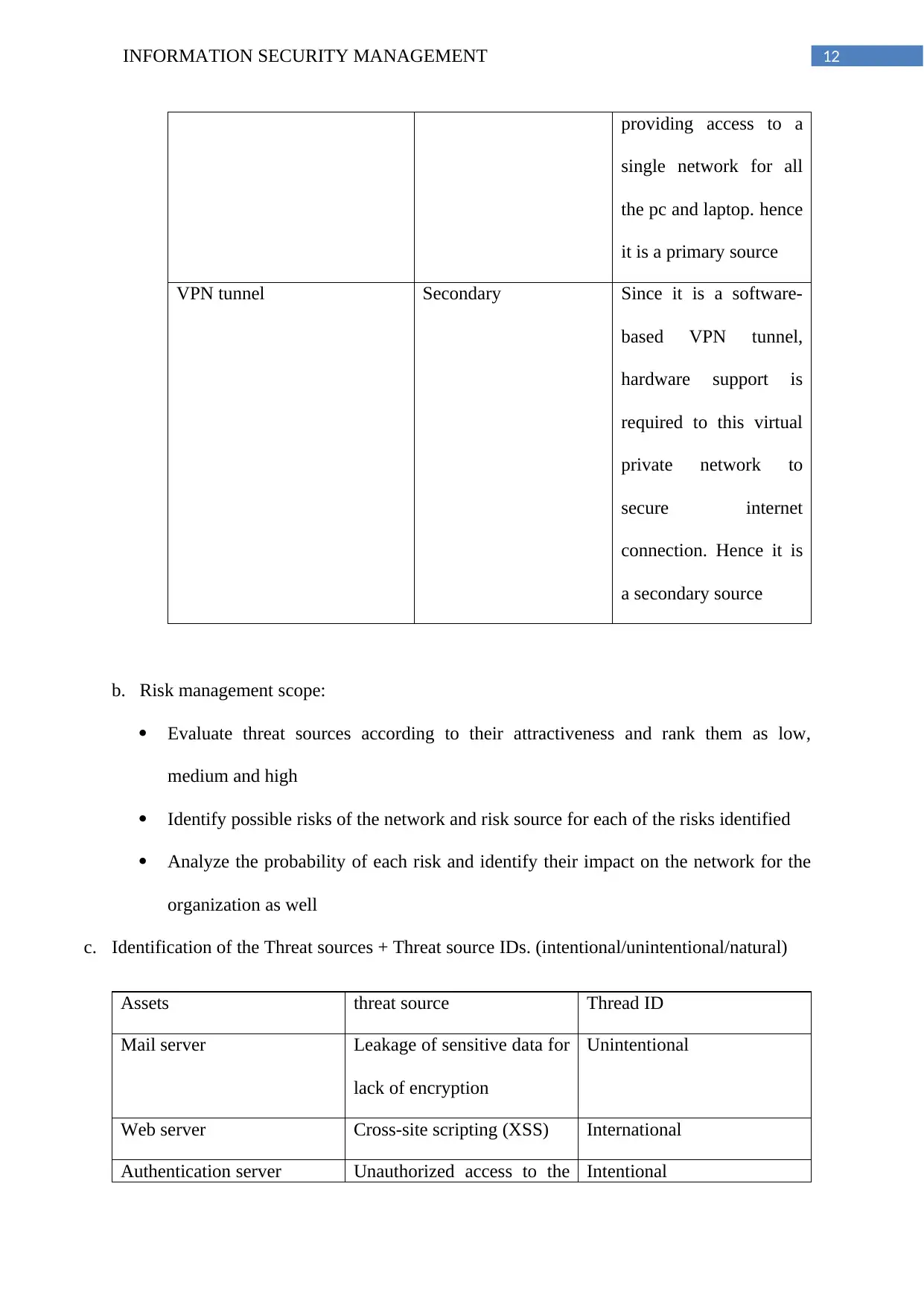
12INFORMATION SECURITY MANAGEMENT
providing access to a
single network for all
the pc and laptop. hence
it is a primary source
VPN tunnel Secondary Since it is a software-
based VPN tunnel,
hardware support is
required to this virtual
private network to
secure internet
connection. Hence it is
a secondary source
b. Risk management scope:
Evaluate threat sources according to their attractiveness and rank them as low,
medium and high
Identify possible risks of the network and risk source for each of the risks identified
Analyze the probability of each risk and identify their impact on the network for the
organization as well
c. Identification of the Threat sources + Threat source IDs. (intentional/unintentional/natural)
Assets threat source Thread ID
Mail server Leakage of sensitive data for
lack of encryption
Unintentional
Web server Cross-site scripting (XSS) International
Authentication server Unauthorized access to the Intentional
providing access to a
single network for all
the pc and laptop. hence
it is a primary source
VPN tunnel Secondary Since it is a software-
based VPN tunnel,
hardware support is
required to this virtual
private network to
secure internet
connection. Hence it is
a secondary source
b. Risk management scope:
Evaluate threat sources according to their attractiveness and rank them as low,
medium and high
Identify possible risks of the network and risk source for each of the risks identified
Analyze the probability of each risk and identify their impact on the network for the
organization as well
c. Identification of the Threat sources + Threat source IDs. (intentional/unintentional/natural)
Assets threat source Thread ID
Mail server Leakage of sensitive data for
lack of encryption
Unintentional
Web server Cross-site scripting (XSS) International
Authentication server Unauthorized access to the Intentional
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
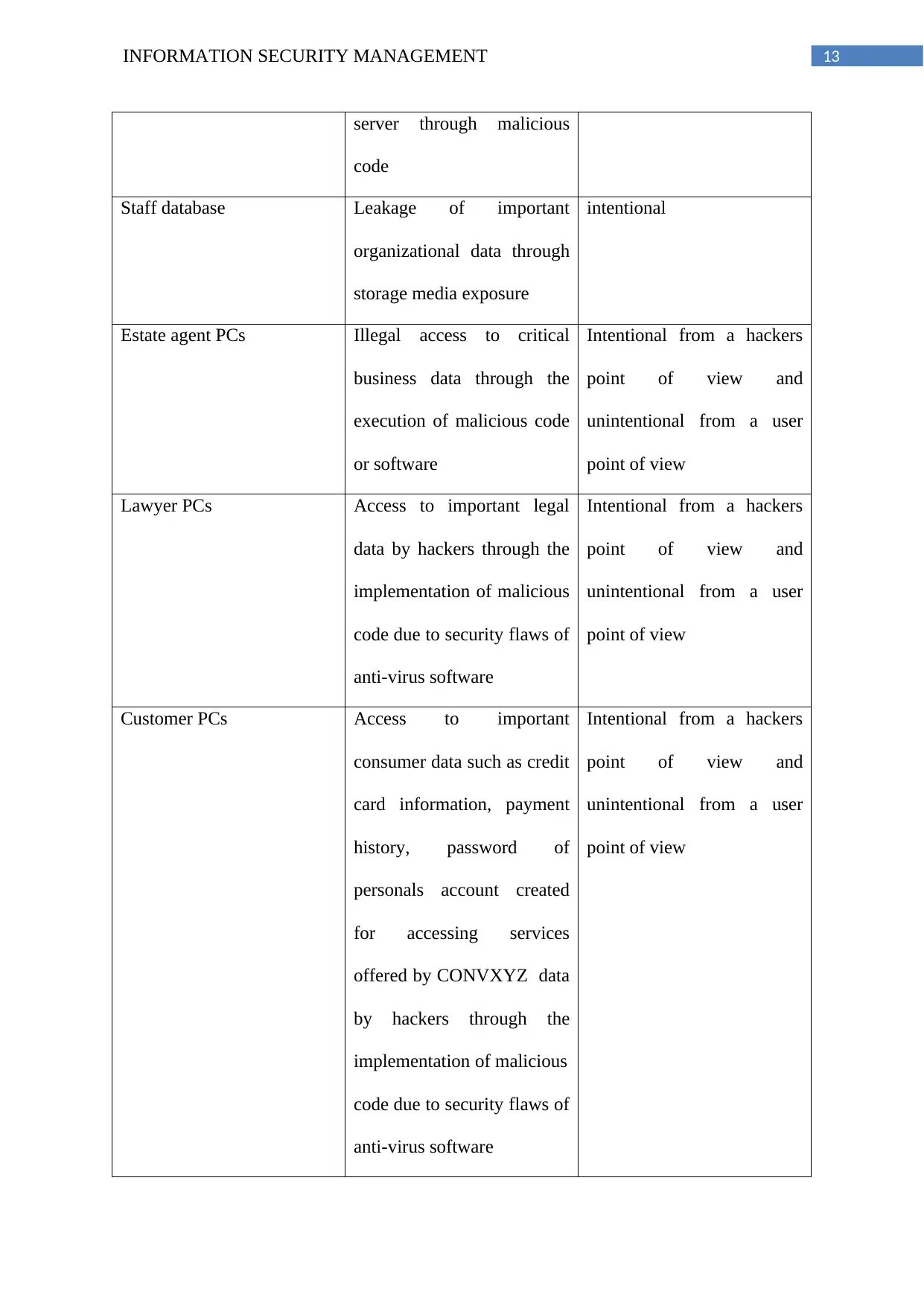
13INFORMATION SECURITY MANAGEMENT
server through malicious
code
Staff database Leakage of important
organizational data through
storage media exposure
intentional
Estate agent PCs Illegal access to critical
business data through the
execution of malicious code
or software
Intentional from a hackers
point of view and
unintentional from a user
point of view
Lawyer PCs Access to important legal
data by hackers through the
implementation of malicious
code due to security flaws of
anti-virus software
Intentional from a hackers
point of view and
unintentional from a user
point of view
Customer PCs Access to important
consumer data such as credit
card information, payment
history, password of
personals account created
for accessing services
offered by CONVXYZ data
by hackers through the
implementation of malicious
code due to security flaws of
anti-virus software
Intentional from a hackers
point of view and
unintentional from a user
point of view
server through malicious
code
Staff database Leakage of important
organizational data through
storage media exposure
intentional
Estate agent PCs Illegal access to critical
business data through the
execution of malicious code
or software
Intentional from a hackers
point of view and
unintentional from a user
point of view
Lawyer PCs Access to important legal
data by hackers through the
implementation of malicious
code due to security flaws of
anti-virus software
Intentional from a hackers
point of view and
unintentional from a user
point of view
Customer PCs Access to important
consumer data such as credit
card information, payment
history, password of
personals account created
for accessing services
offered by CONVXYZ data
by hackers through the
implementation of malicious
code due to security flaws of
anti-virus software
Intentional from a hackers
point of view and
unintentional from a user
point of view
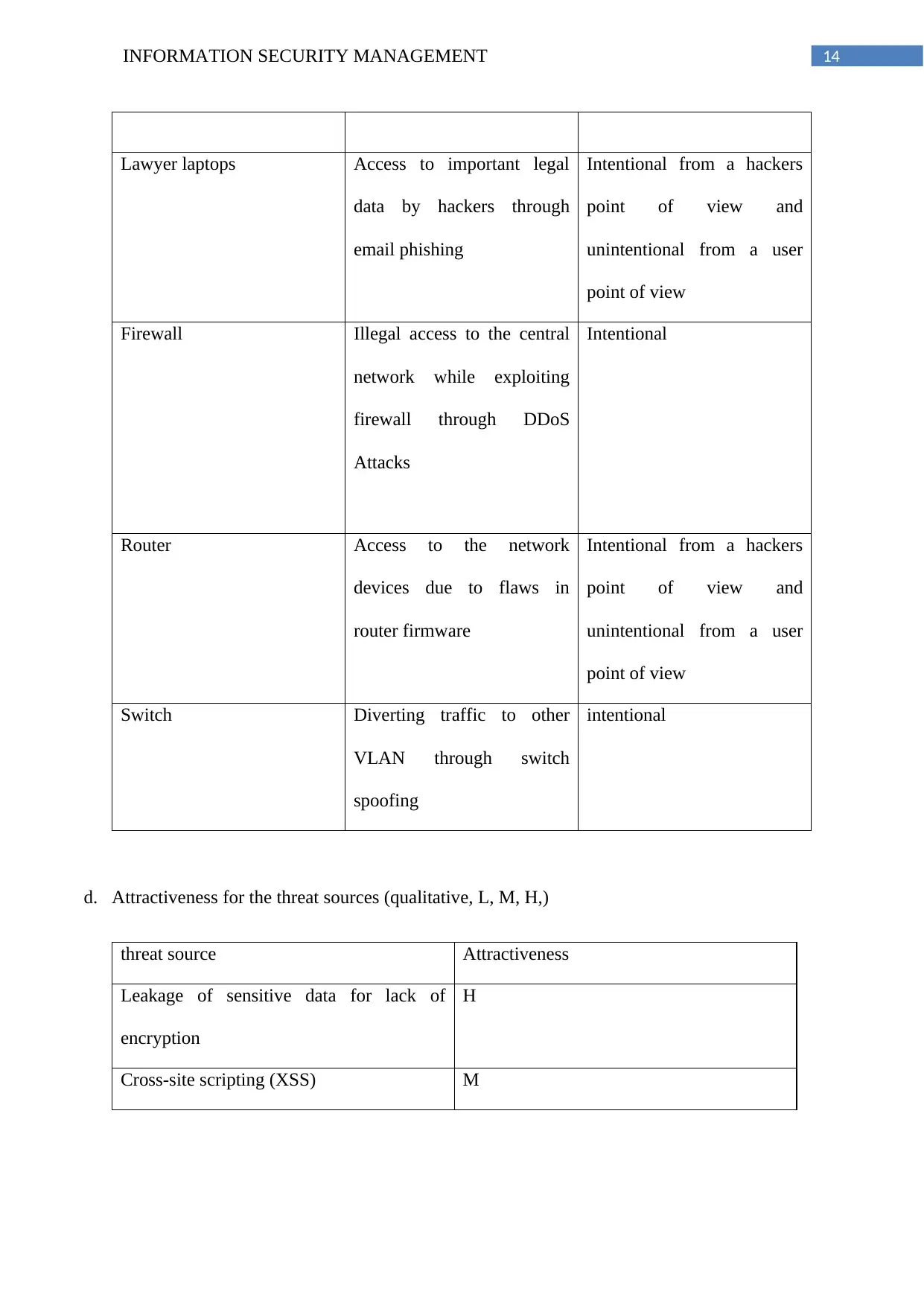
14INFORMATION SECURITY MANAGEMENT
Lawyer laptops Access to important legal
data by hackers through
email phishing
Intentional from a hackers
point of view and
unintentional from a user
point of view
Firewall Illegal access to the central
network while exploiting
firewall through DDoS
Attacks
Intentional
Router Access to the network
devices due to flaws in
router firmware
Intentional from a hackers
point of view and
unintentional from a user
point of view
Switch Diverting traffic to other
VLAN through switch
spoofing
intentional
d. Attractiveness for the threat sources (qualitative, L, M, H,)
threat source Attractiveness
Leakage of sensitive data for lack of
encryption
H
Cross-site scripting (XSS) M
Lawyer laptops Access to important legal
data by hackers through
email phishing
Intentional from a hackers
point of view and
unintentional from a user
point of view
Firewall Illegal access to the central
network while exploiting
firewall through DDoS
Attacks
Intentional
Router Access to the network
devices due to flaws in
router firmware
Intentional from a hackers
point of view and
unintentional from a user
point of view
Switch Diverting traffic to other
VLAN through switch
spoofing
intentional
d. Attractiveness for the threat sources (qualitative, L, M, H,)
threat source Attractiveness
Leakage of sensitive data for lack of
encryption
H
Cross-site scripting (XSS) M
15INFORMATION SECURITY MANAGEMENT
Unauthorized access to the server through
malicious code
M
Leakage of important organizational data
through storage media exposure
H
Illegal access to critical business data
through the execution of malicious code or
software
H
Access to important legal data by hackers
through the implementation of malicious
code due to security flaws of anti-virus
software
M
Access to important consumer data such as
credit card information, payment history,
password of personals account created for
accessing services offered by CONVXYZ
data by hackers through the
implementation of malicious
code due to security flaws of anti-virus
software
H
Access to important legal data by hackers
through email phishing
H
Illegal access to the central network while
exploiting firewall through DDoS Attacks
M
Access to the network devices due to flaws M
Unauthorized access to the server through
malicious code
M
Leakage of important organizational data
through storage media exposure
H
Illegal access to critical business data
through the execution of malicious code or
software
H
Access to important legal data by hackers
through the implementation of malicious
code due to security flaws of anti-virus
software
M
Access to important consumer data such as
credit card information, payment history,
password of personals account created for
accessing services offered by CONVXYZ
data by hackers through the
implementation of malicious
code due to security flaws of anti-virus
software
H
Access to important legal data by hackers
through email phishing
H
Illegal access to the central network while
exploiting firewall through DDoS Attacks
M
Access to the network devices due to flaws M
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
16INFORMATION SECURITY MANAGEMENT
in router firmware
Diverting traffic to other VLAN through
switch spoofing
M
e. Vulnerability identification from the NVD database
Assets f. Vulnerability
identification
g. CVE- number
(Nvd.nist.gov,
2019)
CVSS Severity
Mail server Uncontrolled resource
consumption
CVE-2018-13296 High
Web server Server spoofing CVE-2019-0869 medium
Authentication server An unauthenticated file
upload vulnerability
CVE-2019-3489 high
Staff database Remote code execution CVE-2019-0877 high
Estate agent PCs Remote file
modifications
CVE-2019-3941
Lawyer PCs Endpoint emulation of
the Windows registry
service API
CVE-2019-3880 Medium
Customer PCs Memory leak and
denial of service
CVE-2019-11010 Medium
Lawyer laptops Injection and execution
of OS command as
root
CVE-2019-11001 High
Firewall Access to internal CVE-2019-1841 High
in router firmware
Diverting traffic to other VLAN through
switch spoofing
M
e. Vulnerability identification from the NVD database
Assets f. Vulnerability
identification
g. CVE- number
(Nvd.nist.gov,
2019)
CVSS Severity
Mail server Uncontrolled resource
consumption
CVE-2018-13296 High
Web server Server spoofing CVE-2019-0869 medium
Authentication server An unauthenticated file
upload vulnerability
CVE-2019-3489 high
Staff database Remote code execution CVE-2019-0877 high
Estate agent PCs Remote file
modifications
CVE-2019-3941
Lawyer PCs Endpoint emulation of
the Windows registry
service API
CVE-2019-3880 Medium
Customer PCs Memory leak and
denial of service
CVE-2019-11010 Medium
Lawyer laptops Injection and execution
of OS command as
root
CVE-2019-11001 High
Firewall Access to internal CVE-2019-1841 High
17INFORMATION SECURITY MANAGEMENT
services without
additional
authentication
Router Remote directory
traversal
CVE-2019-3943 High
Switch "local port forwarding"
and "dynamic port
forwarding"
CVE-2019-5426 Medium
h. Calculation of risk (based on the formula, Likelihood x Impact = Risk)
i. Calculation of Likelihood = Threat attractiveness x Vulnerability
services without
additional
authentication
Router Remote directory
traversal
CVE-2019-3943 High
Switch "local port forwarding"
and "dynamic port
forwarding"
CVE-2019-5426 Medium
h. Calculation of risk (based on the formula, Likelihood x Impact = Risk)
i. Calculation of Likelihood = Threat attractiveness x Vulnerability
18INFORMATION SECURITY MANAGEMENT
threat source Likelihood level
Leakage of sensitive data for lack of
encryption
Most likely
Cross-site scripting (XSS) Likely
Unauthorized access to the server through
malicious code
Most likely
Leakage of important organizational data
through storage media exposure
Most likely
Illegal access to critical business data
through the execution of malicious code or
software
Most likely
Access to important legal data by hackers
through the implementation of malicious
code due to security flaws of anti-virus
software
Likely
Access to important consumer data such as
credit card information, payment history,
password of personals account created for
accessing services offered by CONVXYZ
data by hackers through the
implementation of malicious
code due to security flaws of anti-virus
Most likely
threat source Likelihood level
Leakage of sensitive data for lack of
encryption
Most likely
Cross-site scripting (XSS) Likely
Unauthorized access to the server through
malicious code
Most likely
Leakage of important organizational data
through storage media exposure
Most likely
Illegal access to critical business data
through the execution of malicious code or
software
Most likely
Access to important legal data by hackers
through the implementation of malicious
code due to security flaws of anti-virus
software
Likely
Access to important consumer data such as
credit card information, payment history,
password of personals account created for
accessing services offered by CONVXYZ
data by hackers through the
implementation of malicious
code due to security flaws of anti-virus
Most likely
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
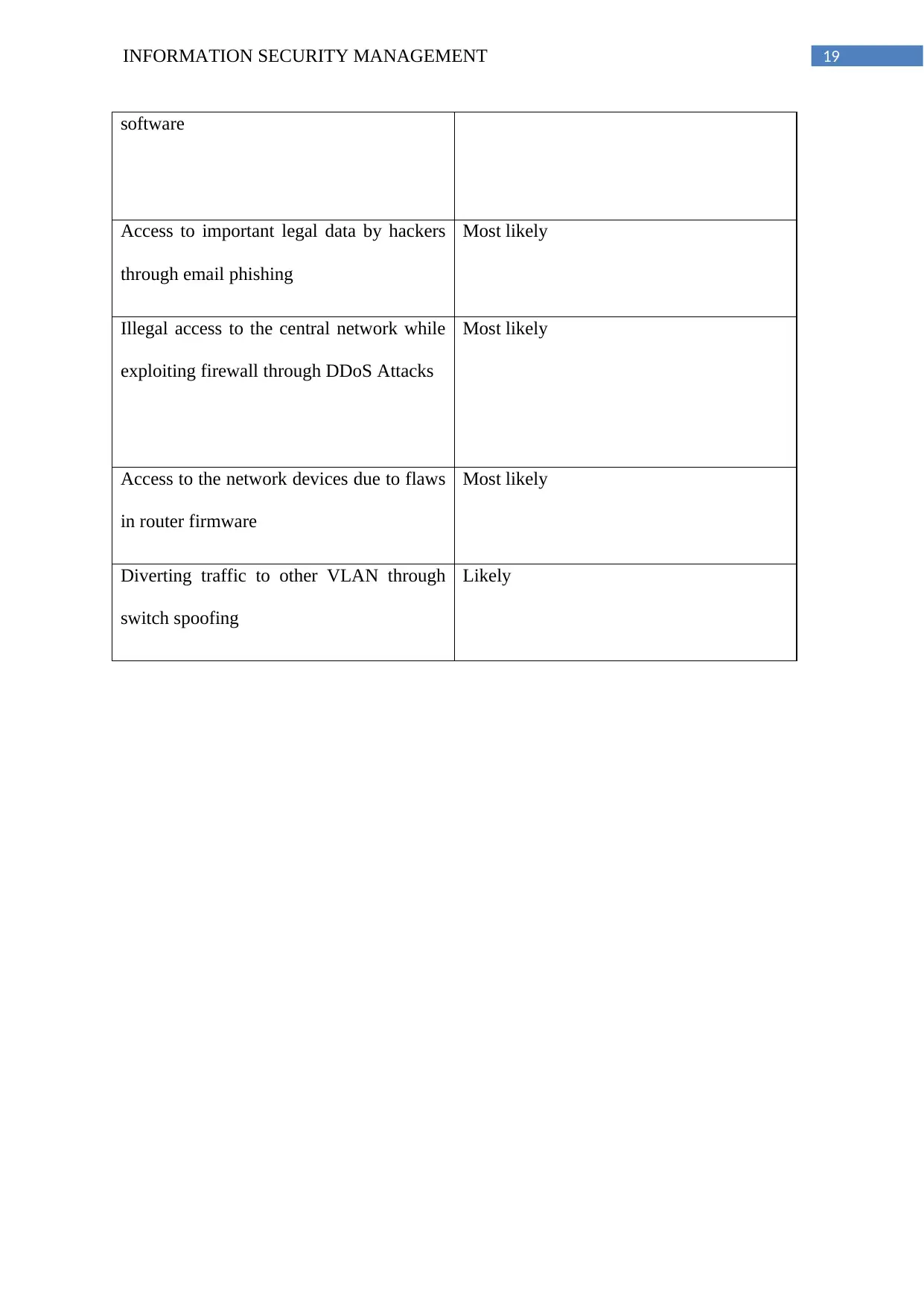
19INFORMATION SECURITY MANAGEMENT
software
Access to important legal data by hackers
through email phishing
Most likely
Illegal access to the central network while
exploiting firewall through DDoS Attacks
Most likely
Access to the network devices due to flaws
in router firmware
Most likely
Diverting traffic to other VLAN through
switch spoofing
Likely
software
Access to important legal data by hackers
through email phishing
Most likely
Illegal access to the central network while
exploiting firewall through DDoS Attacks
Most likely
Access to the network devices due to flaws
in router firmware
Most likely
Diverting traffic to other VLAN through
switch spoofing
Likely
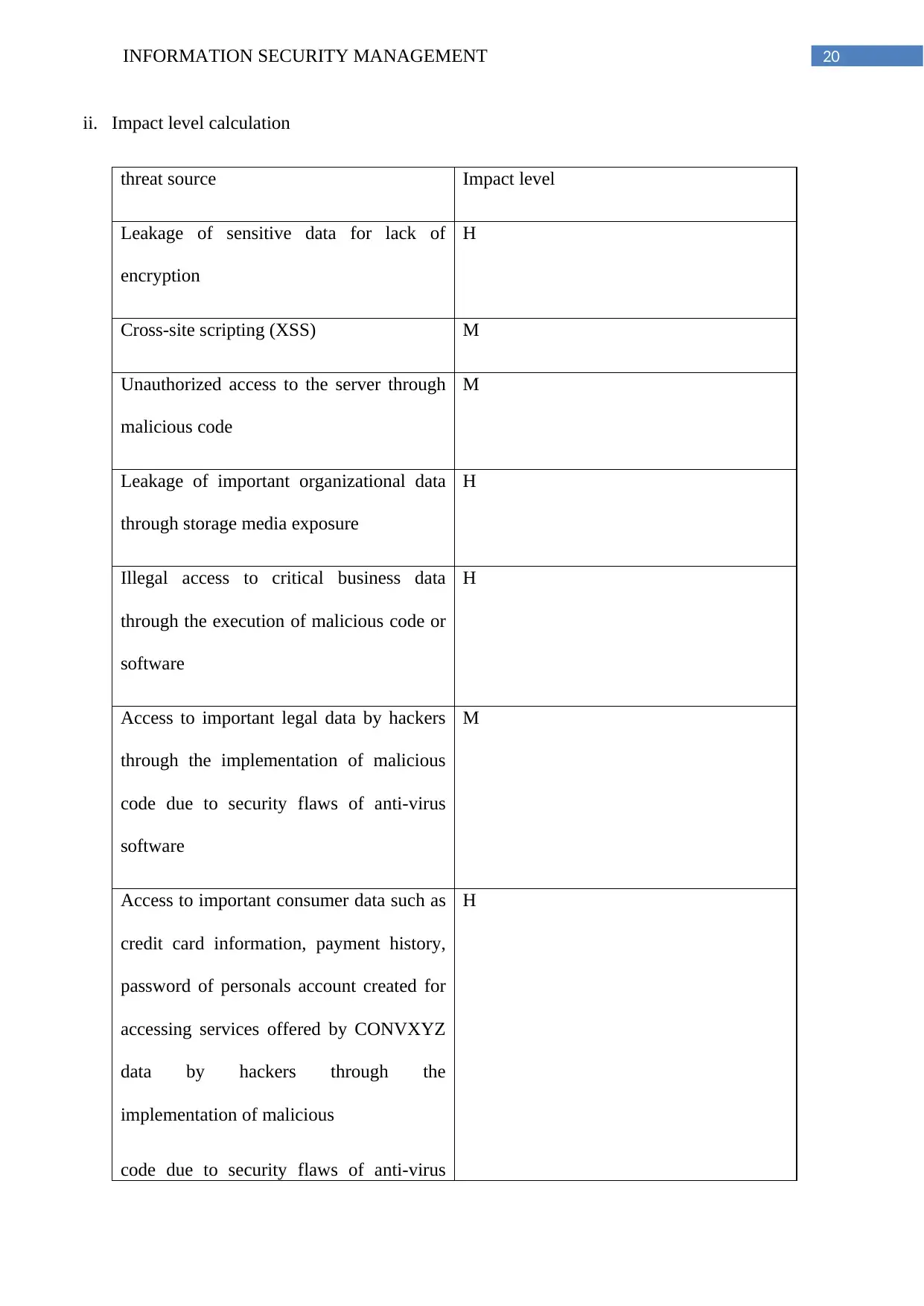
20INFORMATION SECURITY MANAGEMENT
ii. Impact level calculation
threat source Impact level
Leakage of sensitive data for lack of
encryption
H
Cross-site scripting (XSS) M
Unauthorized access to the server through
malicious code
M
Leakage of important organizational data
through storage media exposure
H
Illegal access to critical business data
through the execution of malicious code or
software
H
Access to important legal data by hackers
through the implementation of malicious
code due to security flaws of anti-virus
software
M
Access to important consumer data such as
credit card information, payment history,
password of personals account created for
accessing services offered by CONVXYZ
data by hackers through the
implementation of malicious
code due to security flaws of anti-virus
H
ii. Impact level calculation
threat source Impact level
Leakage of sensitive data for lack of
encryption
H
Cross-site scripting (XSS) M
Unauthorized access to the server through
malicious code
M
Leakage of important organizational data
through storage media exposure
H
Illegal access to critical business data
through the execution of malicious code or
software
H
Access to important legal data by hackers
through the implementation of malicious
code due to security flaws of anti-virus
software
M
Access to important consumer data such as
credit card information, payment history,
password of personals account created for
accessing services offered by CONVXYZ
data by hackers through the
implementation of malicious
code due to security flaws of anti-virus
H
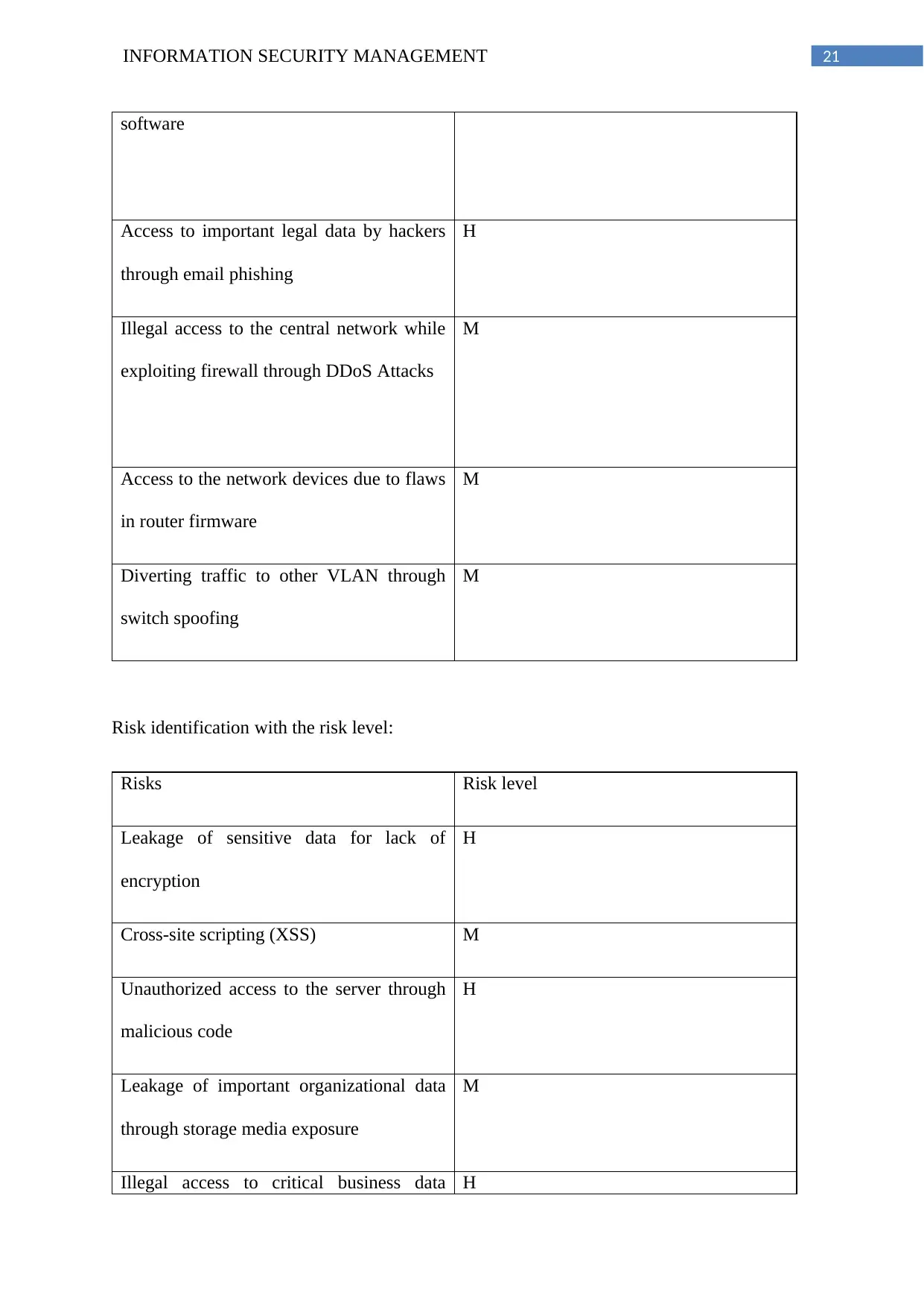
21INFORMATION SECURITY MANAGEMENT
software
Access to important legal data by hackers
through email phishing
H
Illegal access to the central network while
exploiting firewall through DDoS Attacks
M
Access to the network devices due to flaws
in router firmware
M
Diverting traffic to other VLAN through
switch spoofing
M
Risk identification with the risk level:
Risks Risk level
Leakage of sensitive data for lack of
encryption
H
Cross-site scripting (XSS) M
Unauthorized access to the server through
malicious code
H
Leakage of important organizational data
through storage media exposure
M
Illegal access to critical business data H
software
Access to important legal data by hackers
through email phishing
H
Illegal access to the central network while
exploiting firewall through DDoS Attacks
M
Access to the network devices due to flaws
in router firmware
M
Diverting traffic to other VLAN through
switch spoofing
M
Risk identification with the risk level:
Risks Risk level
Leakage of sensitive data for lack of
encryption
H
Cross-site scripting (XSS) M
Unauthorized access to the server through
malicious code
H
Leakage of important organizational data
through storage media exposure
M
Illegal access to critical business data H
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
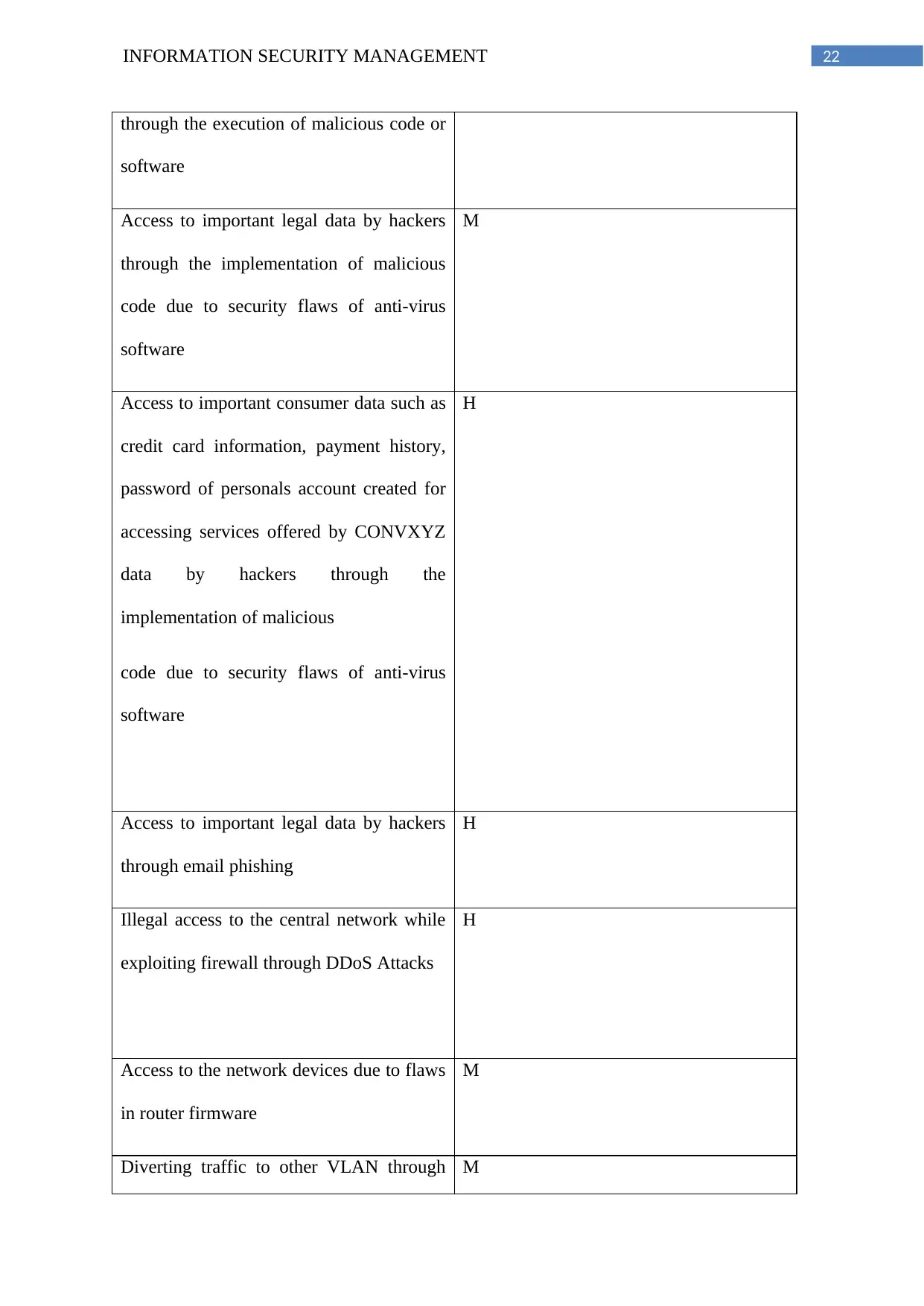
22INFORMATION SECURITY MANAGEMENT
through the execution of malicious code or
software
Access to important legal data by hackers
through the implementation of malicious
code due to security flaws of anti-virus
software
M
Access to important consumer data such as
credit card information, payment history,
password of personals account created for
accessing services offered by CONVXYZ
data by hackers through the
implementation of malicious
code due to security flaws of anti-virus
software
H
Access to important legal data by hackers
through email phishing
H
Illegal access to the central network while
exploiting firewall through DDoS Attacks
H
Access to the network devices due to flaws
in router firmware
M
Diverting traffic to other VLAN through M
through the execution of malicious code or
software
Access to important legal data by hackers
through the implementation of malicious
code due to security flaws of anti-virus
software
M
Access to important consumer data such as
credit card information, payment history,
password of personals account created for
accessing services offered by CONVXYZ
data by hackers through the
implementation of malicious
code due to security flaws of anti-virus
software
H
Access to important legal data by hackers
through email phishing
H
Illegal access to the central network while
exploiting firewall through DDoS Attacks
H
Access to the network devices due to flaws
in router firmware
M
Diverting traffic to other VLAN through M

23INFORMATION SECURITY MANAGEMENT
switch spoofing
4. Non-technical/Executive summary
- Main findings
A detailed assessment done on the network infrastructure of CONVXYZ.
According to the assessment, there are certain security issues, which needs proper
assessment. One of the basic things that is important is to enhance the security of
the firewall as this is one of the most critical assets of the network and it is
responsible for filtering traffic from customer and lawyer laptops that are outside
of the network infrastructure of CONVXYZ. Hence, this needs to be improved.
There are also chances of security threats from assets like a Mail server, Web
server, Authentication server, Staff database, Estate agent PCs, Lawyer PCs, and
Customer PCs. Some of these threats include database hack, exploitation of mail
and authentication server and access important organizational data and hence
these threats are important to recognize. The security of primary assets needs
assurance first as a lack of security for primary assets might compromise security
for secondary assets as well. Primary assets that need security before secondary
assets are the switch, firewall, and router. Although securing other assets are
equally important, but security for secondary assets are not possible to ensure
without securing these primary assets. Hence, security for both of these assets
needs effective security strategy.
- Risk treatment recommendation
switch spoofing
4. Non-technical/Executive summary
- Main findings
A detailed assessment done on the network infrastructure of CONVXYZ.
According to the assessment, there are certain security issues, which needs proper
assessment. One of the basic things that is important is to enhance the security of
the firewall as this is one of the most critical assets of the network and it is
responsible for filtering traffic from customer and lawyer laptops that are outside
of the network infrastructure of CONVXYZ. Hence, this needs to be improved.
There are also chances of security threats from assets like a Mail server, Web
server, Authentication server, Staff database, Estate agent PCs, Lawyer PCs, and
Customer PCs. Some of these threats include database hack, exploitation of mail
and authentication server and access important organizational data and hence
these threats are important to recognize. The security of primary assets needs
assurance first as a lack of security for primary assets might compromise security
for secondary assets as well. Primary assets that need security before secondary
assets are the switch, firewall, and router. Although securing other assets are
equally important, but security for secondary assets are not possible to ensure
without securing these primary assets. Hence, security for both of these assets
needs effective security strategy.
- Risk treatment recommendation

24INFORMATION SECURITY MANAGEMENT
In order to develop a risk treatment plan, it is important to identify potential
risk and once risk is identified, it is important to develop comprehensive strategies
that minimize chances of risk implementation.
Conducting audit for network security. Network security audit helps in
identifying issues and vulnerabilities in the network assets. Identification of
issues and vulnerabilities is extremely important for effective risk treatment of
the identified risks in the network.
Awareness regarding cybersecurity is important. No matter how effective
security measures are if employees are not properly aware of possible security
threats and possible security solutions, there is always the chance of risk due
to lack of awareness which might affect the effectiveness of security
In order to develop a risk treatment plan, it is important to identify potential
risk and once risk is identified, it is important to develop comprehensive strategies
that minimize chances of risk implementation.
Conducting audit for network security. Network security audit helps in
identifying issues and vulnerabilities in the network assets. Identification of
issues and vulnerabilities is extremely important for effective risk treatment of
the identified risks in the network.
Awareness regarding cybersecurity is important. No matter how effective
security measures are if employees are not properly aware of possible security
threats and possible security solutions, there is always the chance of risk due
to lack of awareness which might affect the effectiveness of security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25INFORMATION SECURITY MANAGEMENT
References:
Centos.org. (2019). Kernel Panic on " AMD EPYC 7351 16-Core Processor" server -
CentOS. [online] Available at: https://www.centos.org/forums/viewtopic.php?t=66507
[Accessed 18 Apr. 2019].
Cisco.com. (2019). [online] Available at:
https://www.cisco.com/c/en/us/products/collateral/wireless/catalyst-9800-series-wireless-
controllers/nb-06-cat9800-wirel-cont-data-sheet-ctp-en.pdf [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2018-13296. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-0869. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-0877. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-11001. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-11010. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-1841. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-3489. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
References:
Centos.org. (2019). Kernel Panic on " AMD EPYC 7351 16-Core Processor" server -
CentOS. [online] Available at: https://www.centos.org/forums/viewtopic.php?t=66507
[Accessed 18 Apr. 2019].
Cisco.com. (2019). [online] Available at:
https://www.cisco.com/c/en/us/products/collateral/wireless/catalyst-9800-series-wireless-
controllers/nb-06-cat9800-wirel-cont-data-sheet-ctp-en.pdf [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2018-13296. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-0869. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-0877. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-11001. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-11010. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-1841. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-3489. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].

26INFORMATION SECURITY MANAGEMENT
Nvd.nist.gov. (2019). NVD - CVE-2019-3880. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-3941. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-3943. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Support.hostgator.com. (2019). Server Specifications, Specs « HostGator.com Support
Portal. [online] Available at: https://support.hostgator.com/articles/server-specifications-
specs [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-3880. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-3941. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Nvd.nist.gov. (2019). NVD - CVE-2019-3943. [online] Available at:
https://nvd.nist.gov/vuln/detail/CVE-2018-13296 [Accessed 18 Apr. 2019].
Support.hostgator.com. (2019). Server Specifications, Specs « HostGator.com Support
Portal. [online] Available at: https://support.hostgator.com/articles/server-specifications-
specs [Accessed 18 Apr. 2019].
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





