Risk Assessment on Network Infrastructure of CONVXYZ
This assignment requires conducting and documenting a risk assessment based on a given scenario in the field of Information Security Management.
27 Pages3351 Words91 Views
Added on 2023-01-19
About This Document
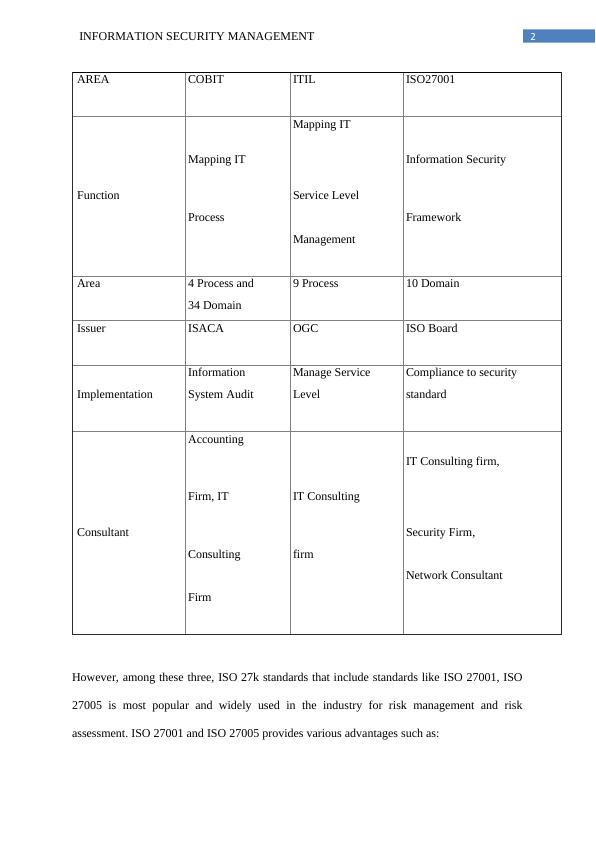
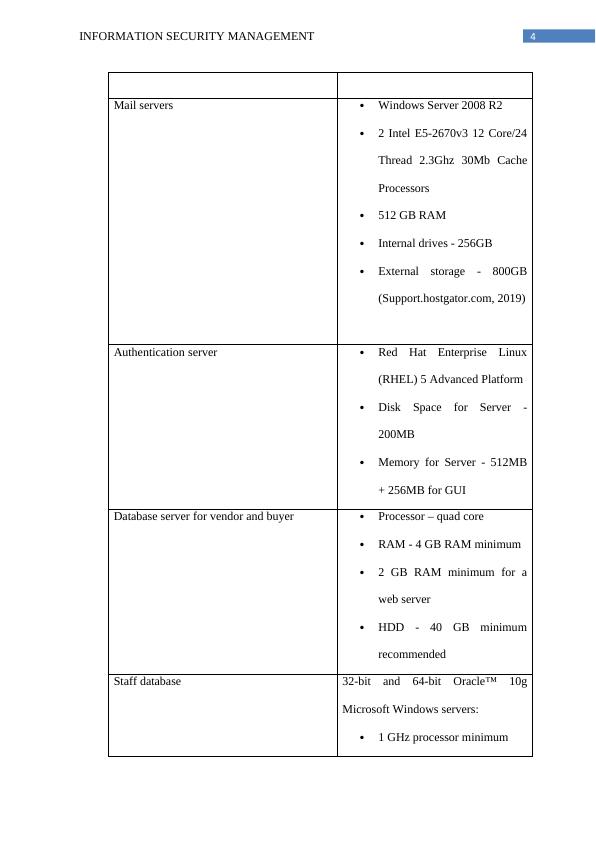
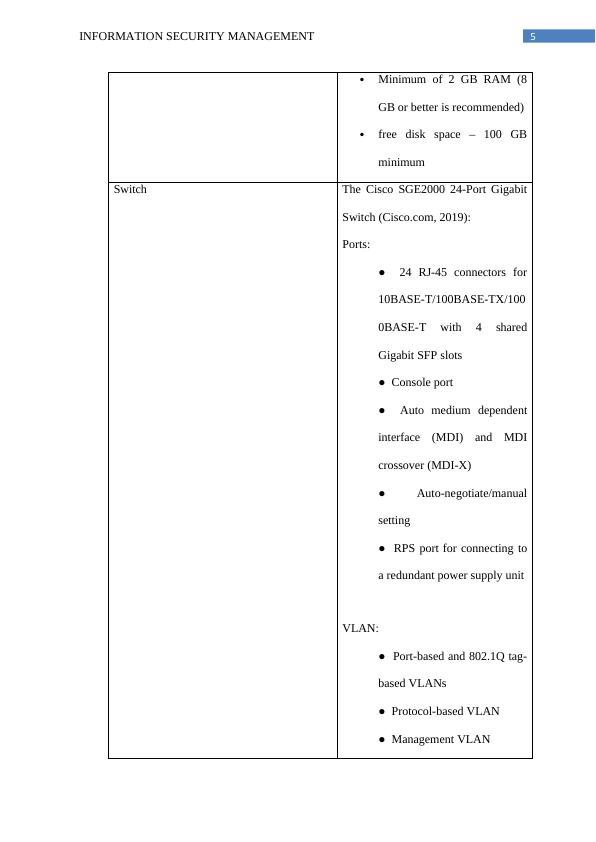
This report performs a risk assessment on the network infrastructure of CONVXYZ based on ISO 27005 standards. It includes mapping criteria on assets, identifying vulnerabilities, and determining likelihood and impact levels. The report also discusses risk management and assessment standards such as COBIT, ITIL, and ISO 27001.
Risk Assessment on Network Infrastructure of CONVXYZ
This assignment requires conducting and documenting a risk assessment based on a given scenario in the field of Information Security Management.
Added on 2023-01-19
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Risk Assessment on Network of CONVXYZ
|16
|3227
|104
Policy Management | Overview of Models
|6
|1182
|24
Cybersecurity. task. Student name. Solution: one. Cyber
|3
|326
|72
Cyber security Planning and Compliance (pdf)
|11
|3109
|30
System Security Management
|6
|1504
|37
Security policy development and risk management Report 2022
|13
|2914
|21