SEC 520 - Information Security Management Plan for AD Health Network
VerifiedAdded on 2023/04/21
|18
|2519
|467
Report
AI Summary
This report details an information security management plan developed for AD Health Network, a health services organization. As an IT intern, the author focuses on addressing data loss and security threats to the company's core products: HNetExchange, HNetPay, and HNetConnect. The report includes a threat and vulnerability assessment, a RACI chart defining roles and responsibilities, a Security Education, Training, and Awareness (SETA) program, and an Issue-Specific Security Policy (ISSP) to mitigate insider threats. It also presents a GANTT chart and Work Breakdown Structure (WBS) to outline the project's timeline, milestones, and critical path, concluding with a heat map summarizing the identified risks and their potential impact. This plan aims to enhance the overall security posture of AD Health Network by implementing relevant security controls and mitigation techniques.

Running head: INFORMATION SECURITY MANAGEMENT
Information Security Management
Name of Student-
Name of University-
Author’s Note-
Information Security Management
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY MANAGEMENT
Table of Contents
1. Introduction..................................................................................................................................2
1.1 Introduction of case study and problems identified...............................................................2
1.2 Objectives..............................................................................................................................2
1.3 Role and Tasks assigned in the project..................................................................................3
1.4 Project Timeline.....................................................................................................................3
1.5 Scope and Exclusions............................................................................................................3
2. Threat and Vulnerability Assessment..........................................................................................4
2.1 Introduction of threat and vulnerability.................................................................................4
2.2 Threat and Vulnerability Table..............................................................................................4
2.2.1 Threats, threat agent, assets affected, vulnerabilities, impact of the threat, mitigation
techniques, relevant security controls (ISO 27 K), resources/tools required, and cost of
mitigation.................................................................................................................................4
3. Roles and Responsibilities...........................................................................................................5
3.1 RACI Chart............................................................................................................................5
3.1.1 List the activities.............................................................................................................5
3.1.2 Allocate roles and responsibilities to personnel.............................................................5
4. SETA...........................................................................................................................................6
4.1 Identify a threat that need to be addressed.........................................................................6
4.2 Draft a SETA program.......................................................................................................6
Table of Contents
1. Introduction..................................................................................................................................2
1.1 Introduction of case study and problems identified...............................................................2
1.2 Objectives..............................................................................................................................2
1.3 Role and Tasks assigned in the project..................................................................................3
1.4 Project Timeline.....................................................................................................................3
1.5 Scope and Exclusions............................................................................................................3
2. Threat and Vulnerability Assessment..........................................................................................4
2.1 Introduction of threat and vulnerability.................................................................................4
2.2 Threat and Vulnerability Table..............................................................................................4
2.2.1 Threats, threat agent, assets affected, vulnerabilities, impact of the threat, mitigation
techniques, relevant security controls (ISO 27 K), resources/tools required, and cost of
mitigation.................................................................................................................................4
3. Roles and Responsibilities...........................................................................................................5
3.1 RACI Chart............................................................................................................................5
3.1.1 List the activities.............................................................................................................5
3.1.2 Allocate roles and responsibilities to personnel.............................................................5
4. SETA...........................................................................................................................................6
4.1 Identify a threat that need to be addressed.........................................................................6
4.2 Draft a SETA program.......................................................................................................6

2INFORMATION SECURITY MANAGEMENT
5. Issue Specific Security Policy (ISSP) for a threat.......................................................................7
5.1 Identify a threat that need to be addressed.........................................................................7
5.2 Create an ISSP...................................................................................................................7
6. Plan of Action..............................................................................................................................8
6.1 GANTT Chart........................................................................................................................8
6.1.1 WBS................................................................................................................................8
6.1.2 Milestones.......................................................................................................................8
6.1.3 Schedules........................................................................................................................8
6.1.4 Critical path..................................................................................................................11
6.1.5 Allocate personnel........................................................................................................12
6.1.6 GANTT chart................................................................................................................13
7. Conclusion.................................................................................................................................13
7.1 Summary..........................................................................................................................13
7.2 Heat Map.........................................................................................................................14
Bibliography..................................................................................................................................16
5. Issue Specific Security Policy (ISSP) for a threat.......................................................................7
5.1 Identify a threat that need to be addressed.........................................................................7
5.2 Create an ISSP...................................................................................................................7
6. Plan of Action..............................................................................................................................8
6.1 GANTT Chart........................................................................................................................8
6.1.1 WBS................................................................................................................................8
6.1.2 Milestones.......................................................................................................................8
6.1.3 Schedules........................................................................................................................8
6.1.4 Critical path..................................................................................................................11
6.1.5 Allocate personnel........................................................................................................12
6.1.6 GANTT chart................................................................................................................13
7. Conclusion.................................................................................................................................13
7.1 Summary..........................................................................................................................13
7.2 Heat Map.........................................................................................................................14
Bibliography..................................................................................................................................16
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY MANAGEMENT
1. Introduction
1.1 Introduction of case study and problems identified
The case study that is considered in this research study is the case study of AD Health
Network. The AD Health Network is a health service organization having its headquarters in
Abu Dhabi. The company mainly has three products HNetPay, HNetConnect, and
HNetExchange. HNetExchange is the main source of revenue in the company. This is used for
handling secured electronic messages related to medical. The HNetPay is used for paying of bill
and HNetConnect is online directory of the company that has details of doctors, other medical
facilities and clinics that helps AD Health Network for attracting customers.
The main issue found in the information system of the company is losing of data due to
various reasons. There are many insider threats, internet threats and losing of data threat that are
faced by the company. The company needs a IS Security risk management plan for mitigating
those threat. Assigned as Information Technology Intern of the company, the risk management
plan is discussed in this report that will help to mitigate the risks associated with the company.
This report has threat and vulnerability matrix, roles and responsibilities chart, SETA and ISSP
threat for the issues identified. There are also some action plan that are to be prepared for
carrying out the activities in the company.
1.2 Objectives
The main objectives of this reports are listed below:
To identify the threat and vulnerability assessment related with the case study
To define the roles and responsibilities through RACI Chart
1. Introduction
1.1 Introduction of case study and problems identified
The case study that is considered in this research study is the case study of AD Health
Network. The AD Health Network is a health service organization having its headquarters in
Abu Dhabi. The company mainly has three products HNetPay, HNetConnect, and
HNetExchange. HNetExchange is the main source of revenue in the company. This is used for
handling secured electronic messages related to medical. The HNetPay is used for paying of bill
and HNetConnect is online directory of the company that has details of doctors, other medical
facilities and clinics that helps AD Health Network for attracting customers.
The main issue found in the information system of the company is losing of data due to
various reasons. There are many insider threats, internet threats and losing of data threat that are
faced by the company. The company needs a IS Security risk management plan for mitigating
those threat. Assigned as Information Technology Intern of the company, the risk management
plan is discussed in this report that will help to mitigate the risks associated with the company.
This report has threat and vulnerability matrix, roles and responsibilities chart, SETA and ISSP
threat for the issues identified. There are also some action plan that are to be prepared for
carrying out the activities in the company.
1.2 Objectives
The main objectives of this reports are listed below:
To identify the threat and vulnerability assessment related with the case study
To define the roles and responsibilities through RACI Chart
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY MANAGEMENT
To study the SETA and ISSP threat associated with the case study
To prepare Gantt Chart and WBS (Work Breakdown Structure) for analysis the risk in the
company
1.3 Role and Tasks assigned in the project
The role allocated for this project is the Information Technology Risk Analyst for the
company of AD Health Network. The task that is assigned is to develop a new risk management
plan for the risks that are identified in the organization. IS security risk is one of the major issue
faced by the organization and as a risk analyst it is important to develop a risk assessment plan
for the organization. The analyst needs to create a threat and vulnerability assessment plan with
roles and responsibilities that are to be involved while handling the activities in the company.
1.4 Project Timeline
The starting date of the project is 28 January 2019 and the end date of the project is 25th
February 2019. The total time for completing the project is 21 days.
1.5 Scope and Exclusions
The scope of the project is to create a risk assessment plan for the AD Health network by
developing threat and vulnerability assessment, RACI Chart, ISSP chart and SETA. The scope of
this project is also to develop the actions that are to be taken and plan them accordingly.
The exclusions that are considered while handling this project is that the natural
calamities are not taken in to account. To train the employees to carry out the activities in the
risk assessment project is also the exclusion of this project.
2. Threat and Vulnerability Assessment
To study the SETA and ISSP threat associated with the case study
To prepare Gantt Chart and WBS (Work Breakdown Structure) for analysis the risk in the
company
1.3 Role and Tasks assigned in the project
The role allocated for this project is the Information Technology Risk Analyst for the
company of AD Health Network. The task that is assigned is to develop a new risk management
plan for the risks that are identified in the organization. IS security risk is one of the major issue
faced by the organization and as a risk analyst it is important to develop a risk assessment plan
for the organization. The analyst needs to create a threat and vulnerability assessment plan with
roles and responsibilities that are to be involved while handling the activities in the company.
1.4 Project Timeline
The starting date of the project is 28 January 2019 and the end date of the project is 25th
February 2019. The total time for completing the project is 21 days.
1.5 Scope and Exclusions
The scope of the project is to create a risk assessment plan for the AD Health network by
developing threat and vulnerability assessment, RACI Chart, ISSP chart and SETA. The scope of
this project is also to develop the actions that are to be taken and plan them accordingly.
The exclusions that are considered while handling this project is that the natural
calamities are not taken in to account. To train the employees to carry out the activities in the
risk assessment project is also the exclusion of this project.
2. Threat and Vulnerability Assessment
5INFORMATION SECURITY MANAGEMENT
2.1 Introduction of threat and vulnerability
Security is one of the most important feature that the organizations give priority. There
are many ways to secure the information of an organization. Right strategy of risk and right
security are the important factors that are to be followed by all the organizations. Cyber threats
are more sophisticated and is one of the most upcoming industry in the black market.
The organization of AD health Network has many IS security threat that vulnerable for
the organization. Loss of data from the company dues to many reason is one of the biggest
vulnerable threat for the company. The company might also face loss of customer because of the
production outages and might face internet threat because of the products. There are also insider
threat that are vulnerable for the company.
2.2 Threat and Vulnerability Table
2.2.1 Threats, threat agent, assets affected, vulnerabilities, impact of the threat,
mitigation techniques, relevant security controls (ISO 27 K), resources/tools required, and cost
of mitigation
Threa
ts
Threat
Agent
Assets
Affecte
d
Vulnerabili
ties
Impact
of Treat
Mitigatio
n
Techniqu
es
Security
Controls
Resource
s
Required
Mitigati
on Cost
1.
Loss
of
data
Hardware
being
removed
Data
loss of
the
compa
Data loss The
compan
y loses
its
All data
needs to
be kept
as back
Needs
to
implem
ent
One
cloud
storage
device.
$15,00
0 per
month
2.1 Introduction of threat and vulnerability
Security is one of the most important feature that the organizations give priority. There
are many ways to secure the information of an organization. Right strategy of risk and right
security are the important factors that are to be followed by all the organizations. Cyber threats
are more sophisticated and is one of the most upcoming industry in the black market.
The organization of AD health Network has many IS security threat that vulnerable for
the organization. Loss of data from the company dues to many reason is one of the biggest
vulnerable threat for the company. The company might also face loss of customer because of the
production outages and might face internet threat because of the products. There are also insider
threat that are vulnerable for the company.
2.2 Threat and Vulnerability Table
2.2.1 Threats, threat agent, assets affected, vulnerabilities, impact of the threat,
mitigation techniques, relevant security controls (ISO 27 K), resources/tools required, and cost
of mitigation
Threa
ts
Threat
Agent
Assets
Affecte
d
Vulnerabili
ties
Impact
of Treat
Mitigatio
n
Techniqu
es
Security
Controls
Resource
s
Required
Mitigati
on Cost
1.
Loss
of
data
Hardware
being
removed
Data
loss of
the
compa
Data loss The
compan
y loses
its
All data
needs to
be kept
as back
Needs
to
implem
ent
One
cloud
storage
device.
$15,00
0 per
month
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INFORMATION SECURITY MANAGEMENT
ny importa
nt data.
up in the
cloud.
cloud.
2.
Insid
er
Thre
at
Downloadi
ng
Problem
System
s and
data
affecte
d
Cyber
Attack
The
system
can
have
cyber-
attack.
Employe
es
should
be
restricte
d to the
usage of
Internet.
Needs
to
secure
the
traffic
with
firewall.
Firewall
to block
vulnera
ble
sites.
$25,00
0 per
month.
3. Roles and Responsibilities
3.1 RACI Chart
3.1.1 List the activities
The list of activities that are included in the project are meeting with the stakeholders,
identifying the risks, risks prioritize, deploying RACI chart, create SETA, and create ISSP.
3.1.2 Allocate roles and responsibilities to personnel
Activities Network
Admin
CFO Programmer
s
Admin
Manager
Networking
team
Meeting with
stakeholders
R C A I
ny importa
nt data.
up in the
cloud.
cloud.
2.
Insid
er
Thre
at
Downloadi
ng
Problem
System
s and
data
affecte
d
Cyber
Attack
The
system
can
have
cyber-
attack.
Employe
es
should
be
restricte
d to the
usage of
Internet.
Needs
to
secure
the
traffic
with
firewall.
Firewall
to block
vulnera
ble
sites.
$25,00
0 per
month.
3. Roles and Responsibilities
3.1 RACI Chart
3.1.1 List the activities
The list of activities that are included in the project are meeting with the stakeholders,
identifying the risks, risks prioritize, deploying RACI chart, create SETA, and create ISSP.
3.1.2 Allocate roles and responsibilities to personnel
Activities Network
Admin
CFO Programmer
s
Admin
Manager
Networking
team
Meeting with
stakeholders
R C A I
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7INFORMATION SECURITY MANAGEMENT
Identifying
the risks
I A R C
Risk
Prioritize
R A C I
Deploying
RACI chart
R C I A
Create SETA I R A C
Create ISSP C R A I
4. SETA
4.1 Identify a threat that need to be addressed
The threat that is to be addressed in this SETA program is Loss of data that is addressed
in this SETA program.
4.2 Draft a SETA program
Security Education: Security Education mainly involves program to educate the members
involved in the organization. The organization needs to prepare the way they are to be addressed.
Training: Training is an important part of Seta program and training is to be given to the
members of the team. When threats are faced by the members of the organizations, they should
know about the primary steps that are to be taken.
Identifying
the risks
I A R C
Risk
Prioritize
R A C I
Deploying
RACI chart
R C I A
Create SETA I R A C
Create ISSP C R A I
4. SETA
4.1 Identify a threat that need to be addressed
The threat that is to be addressed in this SETA program is Loss of data that is addressed
in this SETA program.
4.2 Draft a SETA program
Security Education: Security Education mainly involves program to educate the members
involved in the organization. The organization needs to prepare the way they are to be addressed.
Training: Training is an important part of Seta program and training is to be given to the
members of the team. When threats are faced by the members of the organizations, they should
know about the primary steps that are to be taken.

8INFORMATION SECURITY MANAGEMENT
Awareness: The third program that is addressed in SETA program is awareness. The employees
handling the resources and computer system of the organization should know about the latest
types of cyber-attack that are in the market. The employees should be aware of them from time
to time.
5. Issue Specific Security Policy (ISSP) for a threat
5.1 Identify a threat that need to be addressed
The threat that is to be addressed for the ISSP are Insider threat. Insider threat includes
downloading issues, installation of software, leakage of data, using of other application over the
network, and fraud case.
5.2 Create an ISSP
The ISSP for this threat is shown below:
The employee should use the email of the company instead of using their personal email
ids.
The employees should use only the equipment that are given by the company and cannot
use other equipment for offices work.
The computer system that will be used by the employees will have some common
security measure to prevent the system from small attacks.
The employees should not be allowed to use the office Wi-Fi network on their personal
devices.
6. Plan of Action
6.1 GANTT Chart
Awareness: The third program that is addressed in SETA program is awareness. The employees
handling the resources and computer system of the organization should know about the latest
types of cyber-attack that are in the market. The employees should be aware of them from time
to time.
5. Issue Specific Security Policy (ISSP) for a threat
5.1 Identify a threat that need to be addressed
The threat that is to be addressed for the ISSP are Insider threat. Insider threat includes
downloading issues, installation of software, leakage of data, using of other application over the
network, and fraud case.
5.2 Create an ISSP
The ISSP for this threat is shown below:
The employee should use the email of the company instead of using their personal email
ids.
The employees should use only the equipment that are given by the company and cannot
use other equipment for offices work.
The computer system that will be used by the employees will have some common
security measure to prevent the system from small attacks.
The employees should not be allowed to use the office Wi-Fi network on their personal
devices.
6. Plan of Action
6.1 GANTT Chart
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9INFORMATION SECURITY MANAGEMENT
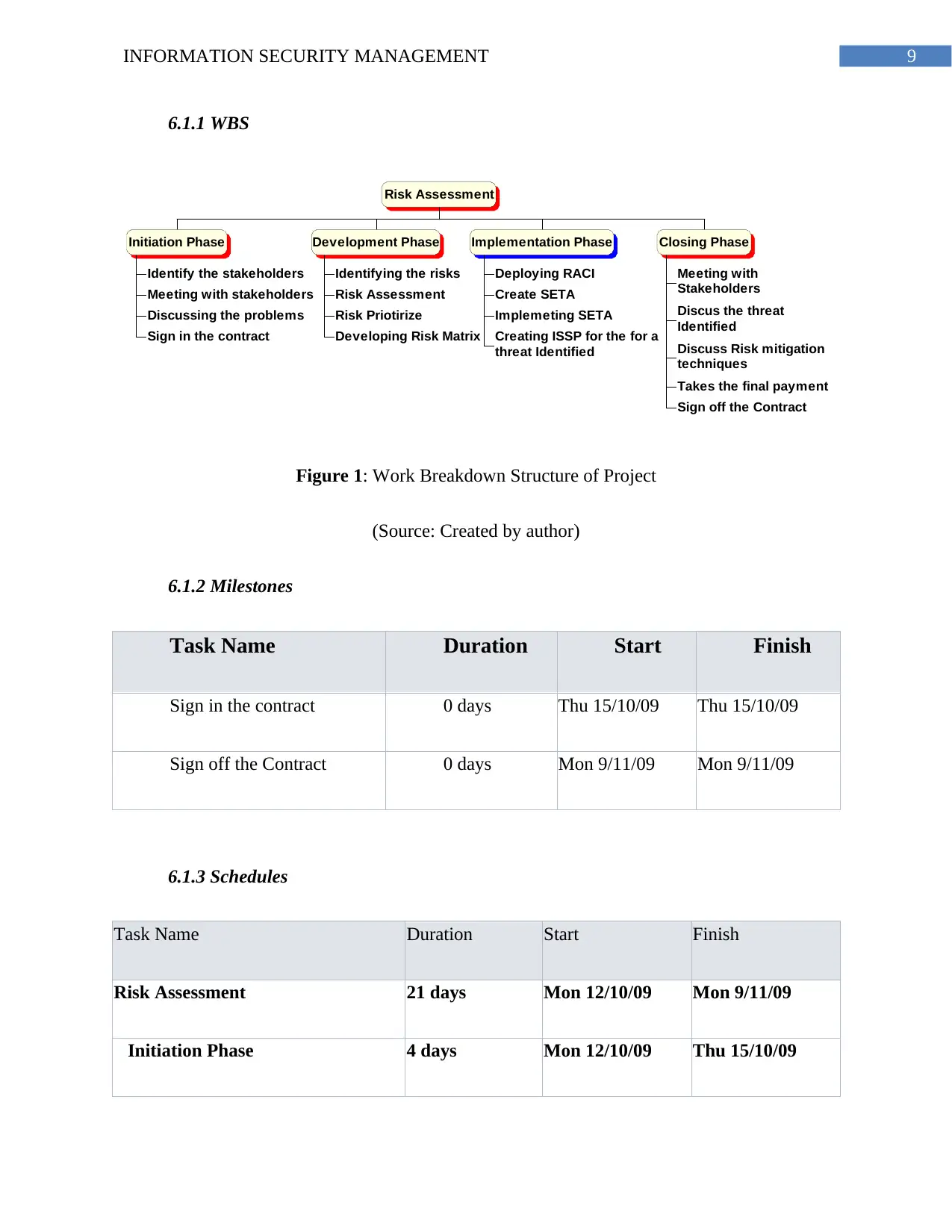
6.1.1 WBS
Risk Assessment
Initiation Phase
Identify the stakeholders
Meeting with stakeholders
Discussing the problems
Sign in the contract
Development Phase
Identifying the risks
Risk Assessment
Risk Priotirize
Developing Risk Matrix
Implementation Phase
Deploying RACI
chartCreate SETA
Implemeting SETA
Creating ISSP for the for a
threat Identified
Closing Phase
Meeting with
Stakeholders
Discus the threat
Identified
Discuss Risk mitigation
techniques
Takes the final payment
Sign off the Contract
Figure 1: Work Breakdown Structure of Project
(Source: Created by author)
6.1.2 Milestones
Task Name Duration Start Finish
Sign in the contract 0 days Thu 15/10/09 Thu 15/10/09
Sign off the Contract 0 days Mon 9/11/09 Mon 9/11/09
6.1.3 Schedules
Task Name Duration Start Finish
Risk Assessment 21 days Mon 12/10/09 Mon 9/11/09
Initiation Phase 4 days Mon 12/10/09 Thu 15/10/09
6.1.1 WBS
Risk Assessment
Initiation Phase
Identify the stakeholders
Meeting with stakeholders
Discussing the problems
Sign in the contract
Development Phase
Identifying the risks
Risk Assessment
Risk Priotirize
Developing Risk Matrix
Implementation Phase
Deploying RACI
chartCreate SETA
Implemeting SETA
Creating ISSP for the for a
threat Identified
Closing Phase
Meeting with
Stakeholders
Discus the threat
Identified
Discuss Risk mitigation
techniques
Takes the final payment
Sign off the Contract
Figure 1: Work Breakdown Structure of Project
(Source: Created by author)
6.1.2 Milestones
Task Name Duration Start Finish
Sign in the contract 0 days Thu 15/10/09 Thu 15/10/09
Sign off the Contract 0 days Mon 9/11/09 Mon 9/11/09
6.1.3 Schedules
Task Name Duration Start Finish
Risk Assessment 21 days Mon 12/10/09 Mon 9/11/09
Initiation Phase 4 days Mon 12/10/09 Thu 15/10/09
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
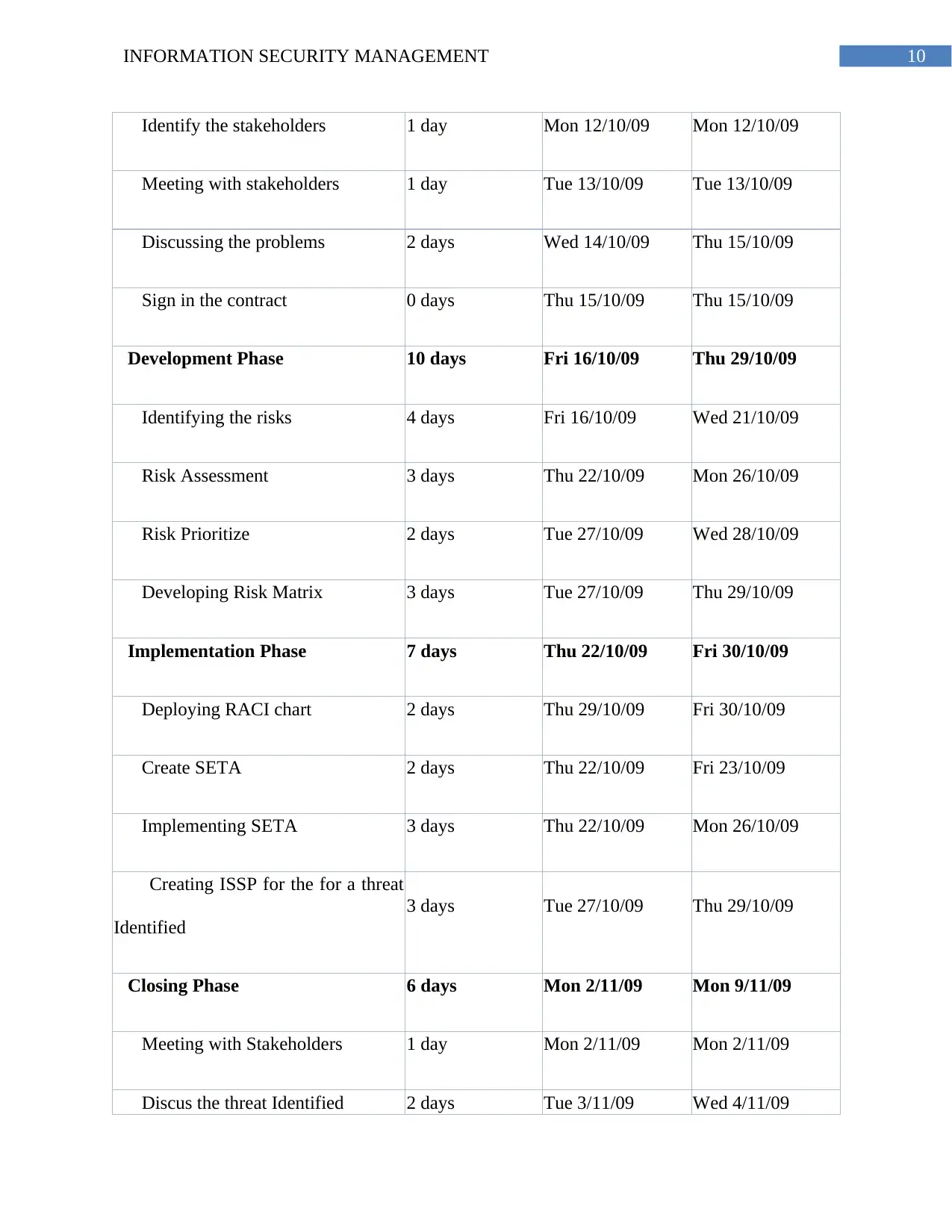
10INFORMATION SECURITY MANAGEMENT
Identify the stakeholders 1 day Mon 12/10/09 Mon 12/10/09
Meeting with stakeholders 1 day Tue 13/10/09 Tue 13/10/09
Discussing the problems 2 days Wed 14/10/09 Thu 15/10/09
Sign in the contract 0 days Thu 15/10/09 Thu 15/10/09
Development Phase 10 days Fri 16/10/09 Thu 29/10/09
Identifying the risks 4 days Fri 16/10/09 Wed 21/10/09
Risk Assessment 3 days Thu 22/10/09 Mon 26/10/09
Risk Prioritize 2 days Tue 27/10/09 Wed 28/10/09
Developing Risk Matrix 3 days Tue 27/10/09 Thu 29/10/09
Implementation Phase 7 days Thu 22/10/09 Fri 30/10/09
Deploying RACI chart 2 days Thu 29/10/09 Fri 30/10/09
Create SETA 2 days Thu 22/10/09 Fri 23/10/09
Implementing SETA 3 days Thu 22/10/09 Mon 26/10/09
Creating ISSP for the for a threat
Identified
3 days Tue 27/10/09 Thu 29/10/09
Closing Phase 6 days Mon 2/11/09 Mon 9/11/09
Meeting with Stakeholders 1 day Mon 2/11/09 Mon 2/11/09
Discus the threat Identified 2 days Tue 3/11/09 Wed 4/11/09
Identify the stakeholders 1 day Mon 12/10/09 Mon 12/10/09
Meeting with stakeholders 1 day Tue 13/10/09 Tue 13/10/09
Discussing the problems 2 days Wed 14/10/09 Thu 15/10/09
Sign in the contract 0 days Thu 15/10/09 Thu 15/10/09
Development Phase 10 days Fri 16/10/09 Thu 29/10/09
Identifying the risks 4 days Fri 16/10/09 Wed 21/10/09
Risk Assessment 3 days Thu 22/10/09 Mon 26/10/09
Risk Prioritize 2 days Tue 27/10/09 Wed 28/10/09
Developing Risk Matrix 3 days Tue 27/10/09 Thu 29/10/09
Implementation Phase 7 days Thu 22/10/09 Fri 30/10/09
Deploying RACI chart 2 days Thu 29/10/09 Fri 30/10/09
Create SETA 2 days Thu 22/10/09 Fri 23/10/09
Implementing SETA 3 days Thu 22/10/09 Mon 26/10/09
Creating ISSP for the for a threat
Identified
3 days Tue 27/10/09 Thu 29/10/09
Closing Phase 6 days Mon 2/11/09 Mon 9/11/09
Meeting with Stakeholders 1 day Mon 2/11/09 Mon 2/11/09
Discus the threat Identified 2 days Tue 3/11/09 Wed 4/11/09
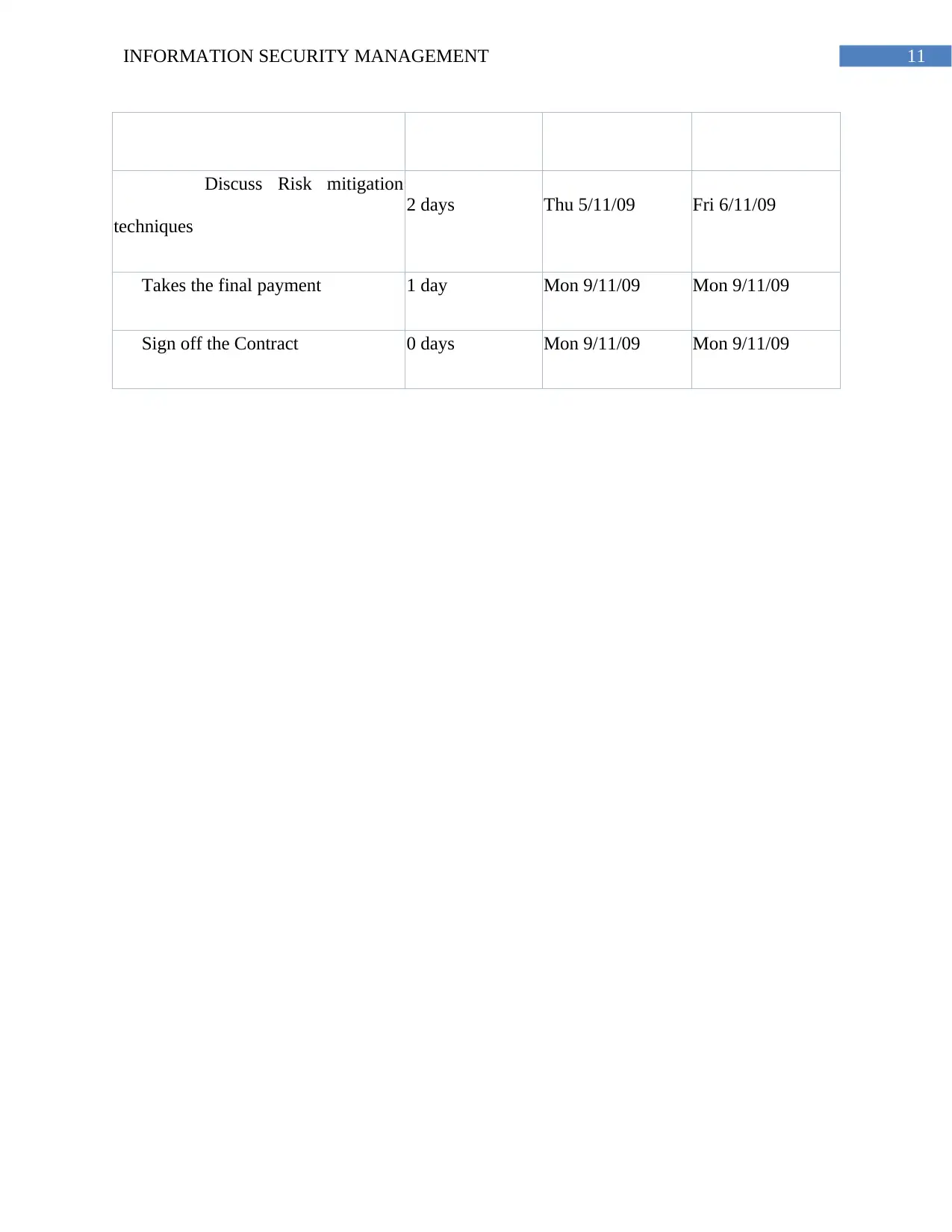
11INFORMATION SECURITY MANAGEMENT
Discuss Risk mitigation
techniques
2 days Thu 5/11/09 Fri 6/11/09
Takes the final payment 1 day Mon 9/11/09 Mon 9/11/09
Sign off the Contract 0 days Mon 9/11/09 Mon 9/11/09
Discuss Risk mitigation
techniques
2 days Thu 5/11/09 Fri 6/11/09
Takes the final payment 1 day Mon 9/11/09 Mon 9/11/09
Sign off the Contract 0 days Mon 9/11/09 Mon 9/11/09
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



