Information Security - ATMs, Biometric Sensors, Key Combinations, Caesar Cypher
VerifiedAdded on 2023/06/14
|9
|1999
|425
AI Summary
This article discusses various information security measures like ATMs, biometric sensors, key combinations, and Caesar Cypher. It explains the importance of confidentiality, integrity, and availability in securing data. The article also highlights the problems associated with biometric authentication and suggests ways to overcome them.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: INFORMATION SECURITY
Information Security
Name of the student
Name of the University
Author Note
Information Security
Name of the student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1INFORMATION SECURITY
Table of Contents
Automated teller machines..................................................................................................2
Bio metric sensors................................................................................................................3
Key combinations................................................................................................................3
Problems..............................................................................................................................4
Caesar Cypher......................................................................................................................5
References............................................................................................................................7
Table of Contents
Automated teller machines..................................................................................................2
Bio metric sensors................................................................................................................3
Key combinations................................................................................................................3
Problems..............................................................................................................................4
Caesar Cypher......................................................................................................................5
References............................................................................................................................7

2INFORMATION SECURITY
Automated teller machines
Automated Teller Machines or the ATMs are planned so that operators will run a
personal identification number or the PIN and a card to access their bank accounts. The pin
number in any ATM card is the most important thing that secures the entire money of the of the
user, and hence the user needs to keep the pin secured form any one. In order to secure the pin,
the user must keep in mind these three important factors:
Confidentiality: Confidentiality is to keep the data secret. That is the user must always
keep the data the data that is the ATM pin secured from any one. The user must never write
down the code anywhere and never share it with any one. One thing to be kept in mind that the
bank staff never asks for such information from the user(Bachu, 2017)..
Integrity: Data integrity can be defined as the technique to keep any data protected so that no one
else than the user is able to change or modify the data. This is one of the major thing to keep in
mind while using an ATM card, if someone changes the information that is the pin of the user
the entire money on the bank can be stolen from the user (Katz, & Lindell, 2014). Hence the user
must always keep the data protected.
Availability: Availability is, right information must be available in the time of need by the
authorised user. That is the user must prove the right pin at time for the right traction.
Automated teller machines
Automated Teller Machines or the ATMs are planned so that operators will run a
personal identification number or the PIN and a card to access their bank accounts. The pin
number in any ATM card is the most important thing that secures the entire money of the of the
user, and hence the user needs to keep the pin secured form any one. In order to secure the pin,
the user must keep in mind these three important factors:
Confidentiality: Confidentiality is to keep the data secret. That is the user must always
keep the data the data that is the ATM pin secured from any one. The user must never write
down the code anywhere and never share it with any one. One thing to be kept in mind that the
bank staff never asks for such information from the user(Bachu, 2017)..
Integrity: Data integrity can be defined as the technique to keep any data protected so that no one
else than the user is able to change or modify the data. This is one of the major thing to keep in
mind while using an ATM card, if someone changes the information that is the pin of the user
the entire money on the bank can be stolen from the user (Katz, & Lindell, 2014). Hence the user
must always keep the data protected.
Availability: Availability is, right information must be available in the time of need by the
authorised user. That is the user must prove the right pin at time for the right traction.

3INFORMATION SECURITY
Bio metric sensors
Biometric sensors are of the key technology which is developed in the modern generation for
providing better security to the people. Bio metric sensors uses the technology of detecting
minute features in the body of the user for authentication. This may be facial recognition or
fingerprint sensors or heart beat detectors (Ketab, Clarke & Dowland, 2016). These are one of
the most secured measures because these things are unique in every person and no one person
can take advantage of the technology. Despite of all the advantages many people fear to use this
technology. One of the main reason many people fear this technology is people think that the
information of the bio metrics is used by the governments for collecting and storing the
information about the person (Konheim, 2016). IN banks the people fear the use of the finger
print sensors as it is seen that the card of the bank account is used by some one closer of the
person and hence if there is bio metric authentication the person may be unable to use the ATM
card and hence people refuse to use the technology. One of the other main reason is the fear of
the false negative, that when the authenticated user’s marks are rejected by the machines. These
people can be eradicated by teaching the people the better use and the importance of the
technology. Also, advancing the technology to an extent that there is no chance of the false
negative can help to earn the trust in the technology.
Key combinations
2. As the thief has already blocked 5keys out of the 10 keys present in the number pad,
the users pin must be from the other 5pins that the thief has not blocked, so for getting the right
pin the number of the permutations and the combinations the user has to try (Martinovic et al.,
2017).
(5!)/ (5! -4!) = (5*4*3*2*1)/ 1 = 120 tries
Bio metric sensors
Biometric sensors are of the key technology which is developed in the modern generation for
providing better security to the people. Bio metric sensors uses the technology of detecting
minute features in the body of the user for authentication. This may be facial recognition or
fingerprint sensors or heart beat detectors (Ketab, Clarke & Dowland, 2016). These are one of
the most secured measures because these things are unique in every person and no one person
can take advantage of the technology. Despite of all the advantages many people fear to use this
technology. One of the main reason many people fear this technology is people think that the
information of the bio metrics is used by the governments for collecting and storing the
information about the person (Konheim, 2016). IN banks the people fear the use of the finger
print sensors as it is seen that the card of the bank account is used by some one closer of the
person and hence if there is bio metric authentication the person may be unable to use the ATM
card and hence people refuse to use the technology. One of the other main reason is the fear of
the false negative, that when the authenticated user’s marks are rejected by the machines. These
people can be eradicated by teaching the people the better use and the importance of the
technology. Also, advancing the technology to an extent that there is no chance of the false
negative can help to earn the trust in the technology.
Key combinations
2. As the thief has already blocked 5keys out of the 10 keys present in the number pad,
the users pin must be from the other 5pins that the thief has not blocked, so for getting the right
pin the number of the permutations and the combinations the user has to try (Martinovic et al.,
2017).
(5!)/ (5! -4!) = (5*4*3*2*1)/ 1 = 120 tries
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4INFORMATION SECURITY
That is the thief has to try 120 different combinations of the pins in order to access the
right pin.
Problems
4. In the bio metric authentication, false positive and false negative are some of the major
issues that one of the major things to be kept in mind. False positive is the condition when any
biometric sensor detects the wrong input given as right, this condition is one of the major issue
which can cause serious issues (Pandey & Verma, 2015). Suppose in case of a fingerprint
sensor, some hacker tries to access a device which is locked by the finger print sensor of the user,
but due to the false positive condition the hacker gets the access to the information of the user.
Hence the user gets jeopardised and all the data are lost (Martinovic et al., 2017). This can
happen due to many technical glitches and other issues. This type of problem can be solved by
increasing the sensitivity of the bio meteoric sensors and while the biometric is getting registered
properly following the given instructions.
False negative is the case when the right bio authentication is detected as negative. This
case is even more dangerous than the false positive because in this case the user who is the
authenticated one is unable to use the information in case of emergency. Suppose in case of
emergency in any organisation, the key of any safe is available only to a single selected
employee, but when the employee tries to open the safe the bio metric fails and hence the
situation becomes more serious. One of the other major example are the smartphone finger print
sensors, it is often seen that the finger print sensors fails to detect the correct authenticated finger
mark and rejects it (Sharma et al.,2017). It can be said that the false negative is more harmful
than the false positive as if the user is not able to open the lock chances are less that someone
else can do in an authenticated manner. This may happen due to many technical faults and some
That is the thief has to try 120 different combinations of the pins in order to access the
right pin.
Problems
4. In the bio metric authentication, false positive and false negative are some of the major
issues that one of the major things to be kept in mind. False positive is the condition when any
biometric sensor detects the wrong input given as right, this condition is one of the major issue
which can cause serious issues (Pandey & Verma, 2015). Suppose in case of a fingerprint
sensor, some hacker tries to access a device which is locked by the finger print sensor of the user,
but due to the false positive condition the hacker gets the access to the information of the user.
Hence the user gets jeopardised and all the data are lost (Martinovic et al., 2017). This can
happen due to many technical glitches and other issues. This type of problem can be solved by
increasing the sensitivity of the bio meteoric sensors and while the biometric is getting registered
properly following the given instructions.
False negative is the case when the right bio authentication is detected as negative. This
case is even more dangerous than the false positive because in this case the user who is the
authenticated one is unable to use the information in case of emergency. Suppose in case of
emergency in any organisation, the key of any safe is available only to a single selected
employee, but when the employee tries to open the safe the bio metric fails and hence the
situation becomes more serious. One of the other major example are the smartphone finger print
sensors, it is often seen that the finger print sensors fails to detect the correct authenticated finger
mark and rejects it (Sharma et al.,2017). It can be said that the false negative is more harmful
than the false positive as if the user is not able to open the lock chances are less that someone
else can do in an authenticated manner. This may happen due to many technical faults and some

5INFORMATION SECURITY
time the user’s faults like not registering the biometric properly. Recherche’s are going on and
many researchers try to of advancing the technology for making it better and more secured.
Caesar Cypher
One of the most simple and easiest way for the deciphering a cypher is the reverse order.
Under this technique one needs to reverse the order of the given encrypted message. SO, the
encrypted message “ELPMAXE ELPMIS A” becomes “a simple example”. This is one of the
simplest and most used technique. Although this is not one of the most secured thing that can be
done (Eberz et al., 2017).
For the given cypher text decryption, the technique that is been is used are given in the
steps followed.
Initially the number of the alphabet is noted down.
Subtract the number of alphabet from the shift key in sequence, that is for 1st letter
2, for the 2nd letter 3 and the third 3rd letter 4 and continuing (Okokpujie et al.,
2016).
3rd is to subtract the general digit which is used for any cypher key that is 3 from
the previous solution.
The final step is locating the alphabet from the solution number.
Encrypted Text N T J W K H X K
time the user’s faults like not registering the biometric properly. Recherche’s are going on and
many researchers try to of advancing the technology for making it better and more secured.
Caesar Cypher
One of the most simple and easiest way for the deciphering a cypher is the reverse order.
Under this technique one needs to reverse the order of the given encrypted message. SO, the
encrypted message “ELPMAXE ELPMIS A” becomes “a simple example”. This is one of the
simplest and most used technique. Although this is not one of the most secured thing that can be
done (Eberz et al., 2017).
For the given cypher text decryption, the technique that is been is used are given in the
steps followed.
Initially the number of the alphabet is noted down.
Subtract the number of alphabet from the shift key in sequence, that is for 1st letter
2, for the 2nd letter 3 and the third 3rd letter 4 and continuing (Okokpujie et al.,
2016).
3rd is to subtract the general digit which is used for any cypher key that is 3 from
the previous solution.
The final step is locating the alphabet from the solution number.
Encrypted Text N T J W K H X K
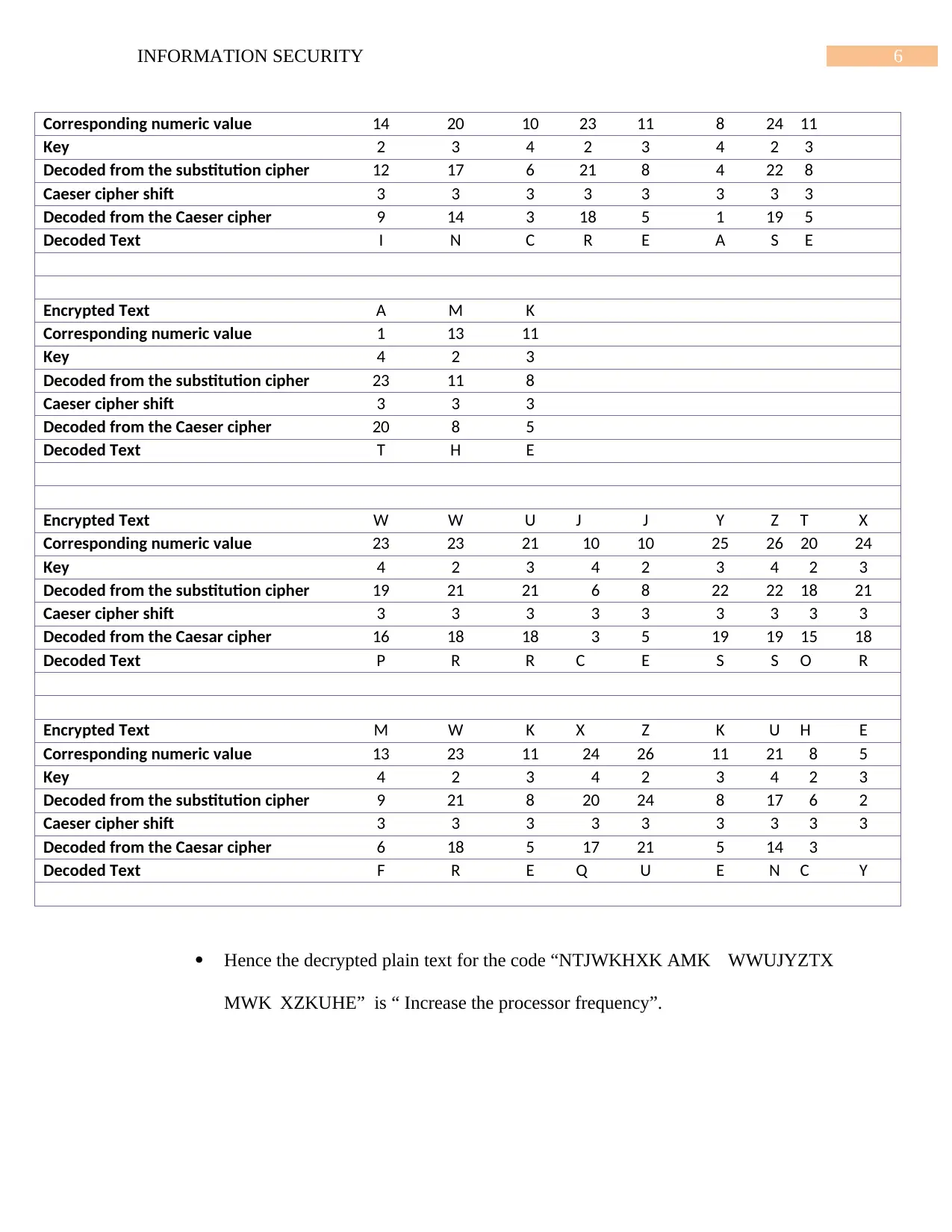
6INFORMATION SECURITY
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the Caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 19 21 21 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 16 18 18 3 5 19 19 15 18
Decoded Text P R R C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 6 18 5 17 21 5 14 3
Decoded Text F R E Q U E N C Y
Hence the decrypted plain text for the code “NTJWKHXK AMK WWUJYZTX
MWK XZKUHE” is “ Increase the processor frequency”.
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the Caeser cipher 9 14 3 18 5 1 19 5
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher 23 11 8
Caeser cipher shift 3 3 3
Decoded from the Caeser cipher 20 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value 23 23 21 10 10 25 26 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 19 21 21 6 8 22 22 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 16 18 18 3 5 19 19 15 18
Decoded Text P R R C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value 13 23 11 24 26 11 21 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8 20 24 8 17 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the Caesar cipher 6 18 5 17 21 5 14 3
Decoded Text F R E Q U E N C Y
Hence the decrypted plain text for the code “NTJWKHXK AMK WWUJYZTX
MWK XZKUHE” is “ Increase the processor frequency”.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
References
Bachu, S. (2017). Three-step authentication for ATMs.
Eberz, S., Rasmussen, K. B., Lenders, V., & Martinovic, I. (2017, April). Evaluating
behavioral biometrics for continuous authentication: Challenges and metrics. In Proceedings of
the 2017 ACM on Asia Conference on Computer and Communications Security (pp. 386-399).
ACM.
Katz, J., & Lindell, Y. (2014). Introduction to modern cryptography. CRC press.
Ketab, S. S., Clarke, N. L., & Dowland, P. S. (2016). The Value of the Biometrics in
Invigilated E-Assessments.
Konheim, A. G. (2016). Automated teller machines: their history and authentication
protocols. Journal of Cryptographic Engineering, 6(1), 1-29.
Martinovic, I., Rasmussen, K., Roeschlin, M., & Tsudik, G. (2017). Authentication using
pulse-response biometrics. Communications of the ACM, 60(2), 108-115.
Oko, S., & Oruh, J. (2012). Enhanced ATM security system using
biometrics. International Journal of Computer Science Issues, 9(5), 355-363.
Okokpujie, K., Olajide, F., John, S., & Kennedy, C. G. (2016, January). Implementation
of the enhanced fingerprint authentication in the ATM system using ATmega128.
In Proceedings of the International Conference on Security and Management
(SAM) (p. 258). The Steering Committee of The World Congress in Computer
Science, Computer Engineering and Applied Computing (WorldComp).
References
Bachu, S. (2017). Three-step authentication for ATMs.
Eberz, S., Rasmussen, K. B., Lenders, V., & Martinovic, I. (2017, April). Evaluating
behavioral biometrics for continuous authentication: Challenges and metrics. In Proceedings of
the 2017 ACM on Asia Conference on Computer and Communications Security (pp. 386-399).
ACM.
Katz, J., & Lindell, Y. (2014). Introduction to modern cryptography. CRC press.
Ketab, S. S., Clarke, N. L., & Dowland, P. S. (2016). The Value of the Biometrics in
Invigilated E-Assessments.
Konheim, A. G. (2016). Automated teller machines: their history and authentication
protocols. Journal of Cryptographic Engineering, 6(1), 1-29.
Martinovic, I., Rasmussen, K., Roeschlin, M., & Tsudik, G. (2017). Authentication using
pulse-response biometrics. Communications of the ACM, 60(2), 108-115.
Oko, S., & Oruh, J. (2012). Enhanced ATM security system using
biometrics. International Journal of Computer Science Issues, 9(5), 355-363.
Okokpujie, K., Olajide, F., John, S., & Kennedy, C. G. (2016, January). Implementation
of the enhanced fingerprint authentication in the ATM system using ATmega128.
In Proceedings of the International Conference on Security and Management
(SAM) (p. 258). The Steering Committee of The World Congress in Computer
Science, Computer Engineering and Applied Computing (WorldComp).

8INFORMATION SECURITY
Pandey, R. M., & Verma, V. K. (2015). Data Security using Various Cryptography
Techniques: A recent Survey.
Sharma, A., Misra, P. K., & Misra, P. (2014). A Security Measure for Electronic
Business Applications. International Journal of Computer Applications, 102(7).
Pandey, R. M., & Verma, V. K. (2015). Data Security using Various Cryptography
Techniques: A recent Survey.
Sharma, A., Misra, P. K., & Misra, P. (2014). A Security Measure for Electronic
Business Applications. International Journal of Computer Applications, 102(7).
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


