Analyzing Information Security: ATM, Biometrics, and Ciphers
VerifiedAdded on 2021/04/21
|8
|1622
|352
Homework Assignment
AI Summary
This assignment delves into the realm of information security, exploring key concepts within the context of ATM security, biometrics, and cryptographic methods. The paper begins by explaining the CIA Triad (Confidentiality, Integrity, and Availability) and its application in securing ATM PINs and data. It then analyzes a scenario where a thief has access to a limited number of ATM keys, calculating the maximum possible PIN attempts. The assignment also examines the reluctance to use biometrics, identifying challenges such as accuracy issues and privacy concerns, and proposes solutions like multi-factor authentication. Furthermore, it defines false negatives in biometric systems and their potential consequences. Finally, the assignment explores transposition and substitution ciphers, including Caesar ciphers, providing examples of encryption and decryption processes. The decoded message reveals the importance of processor speed for employees.

Running head: INFORMATION SECURITY
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
INFORMATION SECURITY
Name of the Student
Name of the University
Authors Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................2
Answer to Question 3:.........................................................................................................3
Answer to Question 4:.........................................................................................................3
Answer to Question 5:.........................................................................................................4
References............................................................................................................................5
Table of Contents
Answer to Question 1:.........................................................................................................2
Answer to Question 2:.........................................................................................................2
Answer to Question 3:.........................................................................................................3
Answer to Question 4:.........................................................................................................3
Answer to Question 5:.........................................................................................................4
References............................................................................................................................5

2INFORMATION SECURITY
Answer to Question 1:
Confidentiality, integrity and availability is also known as CIA Triad is nothing but a
model which is designed for guiding policies for information security within an organization. In
the case of ATM machine pin number confidentiality is generally compared to privacy (Hajare et
al., 2018). PIN numbers are designed in such a way that it can prevent from reaching to
unauthorized people. Integrity is much more focused in maintaining, accuracy and
trustworthiness of data over the whole life cycle. Availability is generally ensured by
maintaining of data of all kinds of hardware and repair of data when needed (Onyesolu &
Okpala, 2017). Safeguarding of data or any kinds of interruptions in various kinds of connection
must be included in various kinds of parameters like natural disaster and fire. For prevention of
data a backup must be there so that important data can be easily stored. PIN in ATM mainly
makes use of data so that it cannot be easily accessed or authorized by unauthorized people.
Many times it is seen that safeguarding of data may require special kind of training for looking
into the documents. This kind of training would generally require various kinds of security risk
which is used for threating of information. Data encryption is known to be common kind of
method which is used for ensuring confidentiality. While availability focus on maintaining of
hardware which generally performs maintaining of hardware for functioning of operating system.
Answer to Question 2:
The whole keypad of an ATM machine consists of ten keys that is (0-9). Now in this
situation the thief has broken five keys so more five keys are available to him. The pin number of
an ATM machine generally consist of four numbers. So with the five keys available the
maximum number of possible outcome for a four-digit pin is as follows
Answer to Question 1:
Confidentiality, integrity and availability is also known as CIA Triad is nothing but a
model which is designed for guiding policies for information security within an organization. In
the case of ATM machine pin number confidentiality is generally compared to privacy (Hajare et
al., 2018). PIN numbers are designed in such a way that it can prevent from reaching to
unauthorized people. Integrity is much more focused in maintaining, accuracy and
trustworthiness of data over the whole life cycle. Availability is generally ensured by
maintaining of data of all kinds of hardware and repair of data when needed (Onyesolu &
Okpala, 2017). Safeguarding of data or any kinds of interruptions in various kinds of connection
must be included in various kinds of parameters like natural disaster and fire. For prevention of
data a backup must be there so that important data can be easily stored. PIN in ATM mainly
makes use of data so that it cannot be easily accessed or authorized by unauthorized people.
Many times it is seen that safeguarding of data may require special kind of training for looking
into the documents. This kind of training would generally require various kinds of security risk
which is used for threating of information. Data encryption is known to be common kind of
method which is used for ensuring confidentiality. While availability focus on maintaining of
hardware which generally performs maintaining of hardware for functioning of operating system.
Answer to Question 2:
The whole keypad of an ATM machine consists of ten keys that is (0-9). Now in this
situation the thief has broken five keys so more five keys are available to him. The pin number of
an ATM machine generally consist of four numbers. So with the five keys available the
maximum number of possible outcome for a four-digit pin is as follows
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
So the maximum number of possible outcome in this situation is 120. But according to the ATM
security a user can enter pin for maximum three times. After three wrong inputs the card gets
blocked. So keeping the security of the ATM in mind the maximum time the thief can enter the
pin is three times. After three wrong trials by thief the card will be blocked.
Answer to Question 3:
The reasons behind the reluctant to the use of biometrics are:
One of the biggest challenges is the kind of process which is involved in
capturing or mapping it a particular kind of identity (Karovaliya et al., 2015).
Lack of accuracy in the kind of capturing may easily led to failure of a particular
system.
Privacy is considered to be one of the biggest concern in the kind of biometric
solutions (Pathak et al., 2015). If somehow the server storing the biometric
information is hacked in anyway then it may have led to serious kind of impact
on a particular kind of individual.
Any kind of error in biometric devices may led to false rejection and false kind of
acceptance. This is mainly due to biometric technology which is unable to have
an idea regarding the characteristic of a particular person for various kinds of
reasons.
There are certain number of steps which can be used for overcoming issues in biometric
kind of authentication (Singh & Kaur, 2016). Spoofing attack is considered to be well known
kind of attack in which biometric of other persons are created. Another way for the
5P4 = 5! / (5-4)! = 5! /1! = 5*4*3*2*1/ 1 =120/1 =120.
So the maximum number of possible outcome in this situation is 120. But according to the ATM
security a user can enter pin for maximum three times. After three wrong inputs the card gets
blocked. So keeping the security of the ATM in mind the maximum time the thief can enter the
pin is three times. After three wrong trials by thief the card will be blocked.
Answer to Question 3:
The reasons behind the reluctant to the use of biometrics are:
One of the biggest challenges is the kind of process which is involved in
capturing or mapping it a particular kind of identity (Karovaliya et al., 2015).
Lack of accuracy in the kind of capturing may easily led to failure of a particular
system.
Privacy is considered to be one of the biggest concern in the kind of biometric
solutions (Pathak et al., 2015). If somehow the server storing the biometric
information is hacked in anyway then it may have led to serious kind of impact
on a particular kind of individual.
Any kind of error in biometric devices may led to false rejection and false kind of
acceptance. This is mainly due to biometric technology which is unable to have
an idea regarding the characteristic of a particular person for various kinds of
reasons.
There are certain number of steps which can be used for overcoming issues in biometric
kind of authentication (Singh & Kaur, 2016). Spoofing attack is considered to be well known
kind of attack in which biometric of other persons are created. Another way for the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY
implementation is the multifactor authentication which mainly requires multiple kind of
identifiers on depending on certain number or level of risk.
Answer to Question 4:
A false negative is a thing in biometric system when a particular kind of system fails to
recognize the authenticity of an individual which might lead to something which is not
happening in general (Khan, Hasan & Xu, 2015). Depending on the thing there can be serious
kinds of consequences like personal who is considered to have safety on the parameter of
accessing inspite of guarding the whole kind of thing. On organizational level it can easily shut
down the whole infrastructure and various kinds of things needed will be the data centers needed
for restoring of various kinds of services.
Answer to Question 5:
Transposition cipher is nothing but a simple scheme in which some of the plaintext are
shifted in some kinds of regular pattern for forming cipher text. In some of the manual system
transposition is generally carried out by making use of mnemonic. Simple frequency count can
easily reveal to cryptanalyst. It generally has the same frequency in the cipher like some of the
average in plaintext. And so simple rearrangement of various kinds of letters are possible in this.
Simple distribution cipher is a kind of cypher which is being used for many years. It
basically consists of plaintext character which are considered to be different from cipher text
character. It is considered to be different from Caesar cipher in the context that cipher alphabet is
not alphabet shifted instead of that is jumbled completely.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
implementation is the multifactor authentication which mainly requires multiple kind of
identifiers on depending on certain number or level of risk.
Answer to Question 4:
A false negative is a thing in biometric system when a particular kind of system fails to
recognize the authenticity of an individual which might lead to something which is not
happening in general (Khan, Hasan & Xu, 2015). Depending on the thing there can be serious
kinds of consequences like personal who is considered to have safety on the parameter of
accessing inspite of guarding the whole kind of thing. On organizational level it can easily shut
down the whole infrastructure and various kinds of things needed will be the data centers needed
for restoring of various kinds of services.
Answer to Question 5:
Transposition cipher is nothing but a simple scheme in which some of the plaintext are
shifted in some kinds of regular pattern for forming cipher text. In some of the manual system
transposition is generally carried out by making use of mnemonic. Simple frequency count can
easily reveal to cryptanalyst. It generally has the same frequency in the cipher like some of the
average in plaintext. And so simple rearrangement of various kinds of letters are possible in this.
Simple distribution cipher is a kind of cypher which is being used for many years. It
basically consists of plaintext character which are considered to be different from cipher text
character. It is considered to be different from Caesar cipher in the context that cipher alphabet is
not alphabet shifted instead of that is jumbled completely.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
5INFORMATION SECURITY
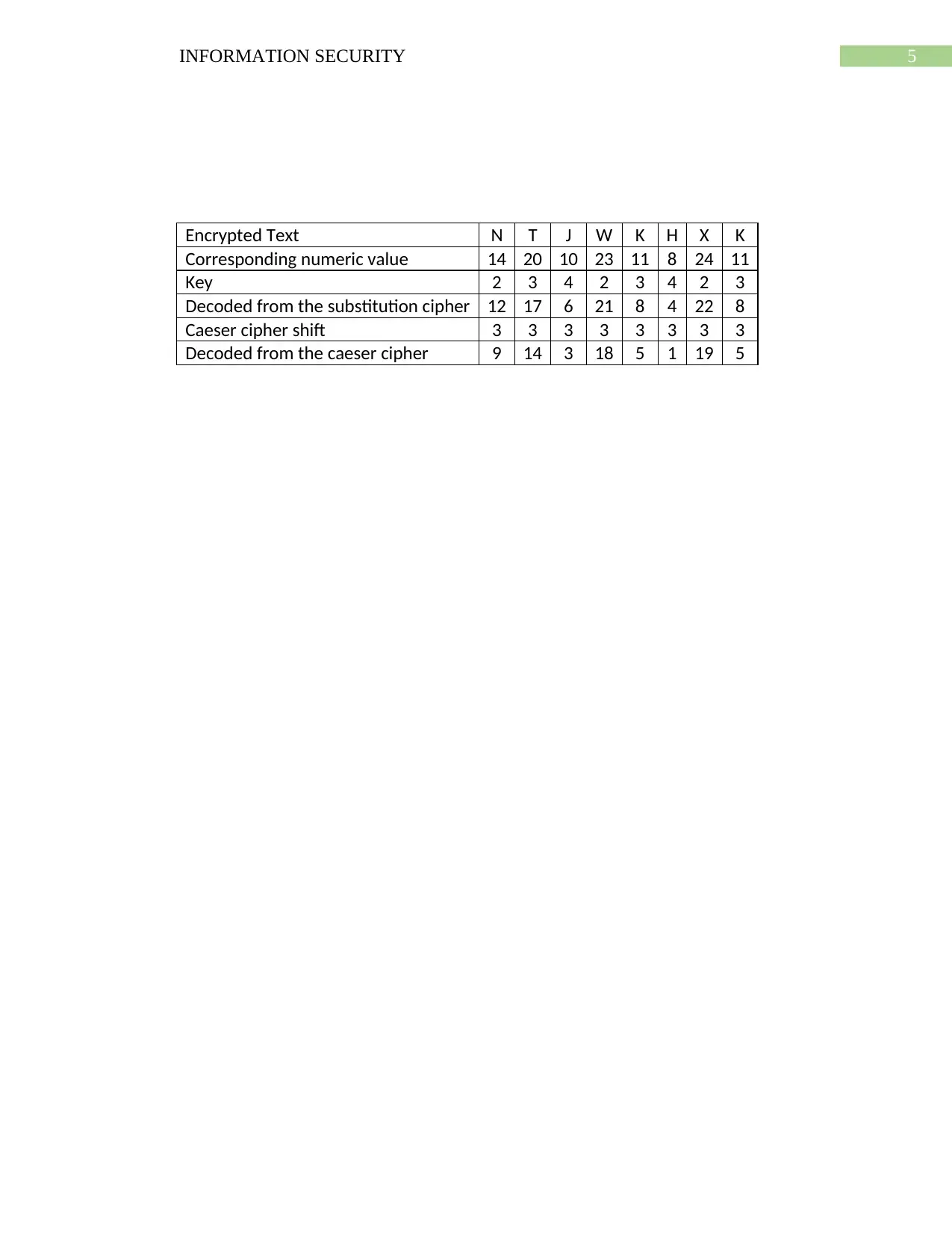
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
Encrypted Text N T J W K H X K
Corresponding numeric value 14 20 10 23 11 8 24 11
Key 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 12 17 6 21 8 4 22 8
Caeser cipher shift 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 9 14 3 18 5 1 19 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6INFORMATION SECURITY
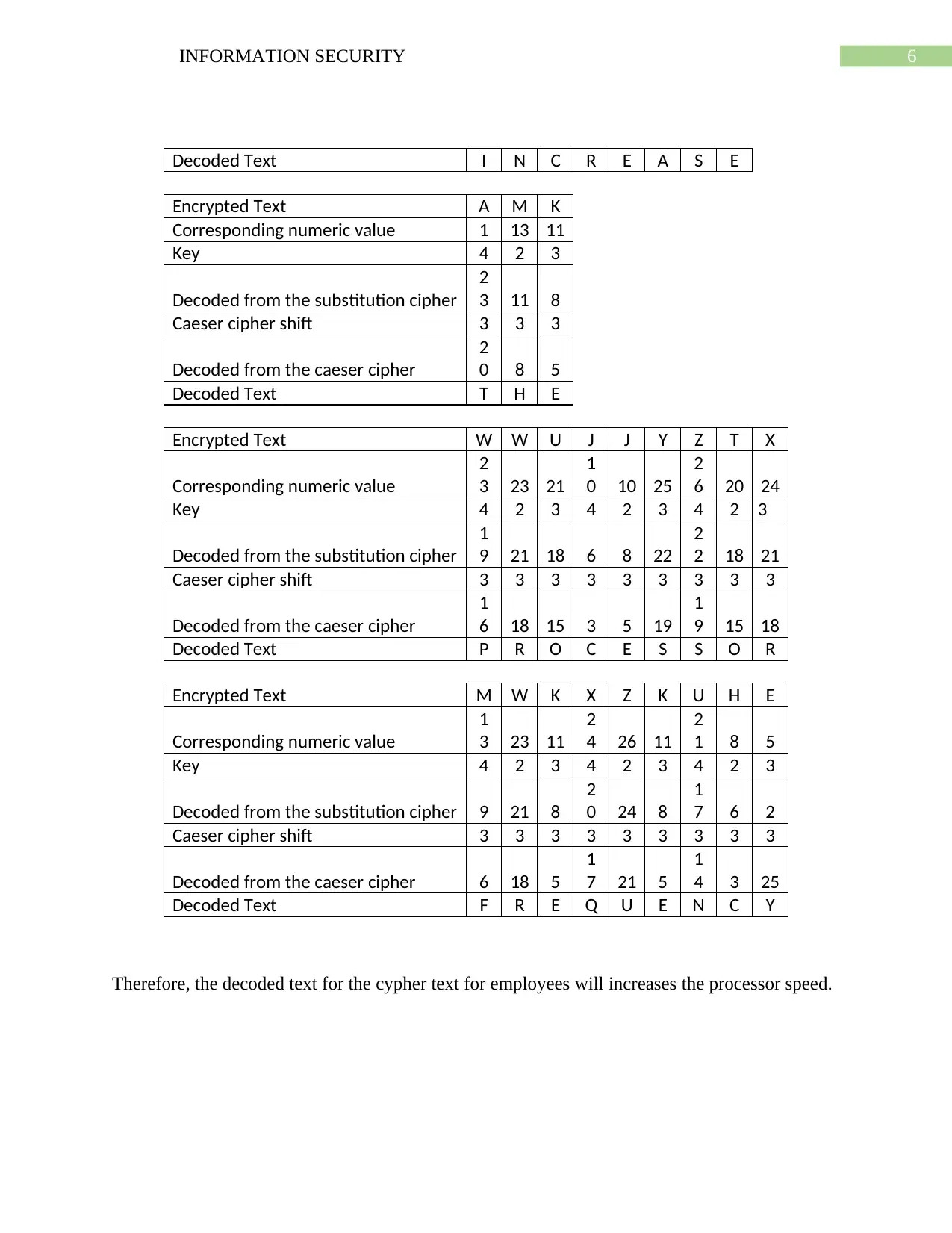
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decoded text for the cypher text for employees will increases the processor speed.
Decoded Text I N C R E A S E
Encrypted Text A M K
Corresponding numeric value 1 13 11
Key 4 2 3
Decoded from the substitution cipher
2
3 11 8
Caeser cipher shift 3 3 3
Decoded from the caeser cipher
2
0 8 5
Decoded Text T H E
Encrypted Text W W U J J Y Z T X
Corresponding numeric value
2
3 23 21
1
0 10 25
2
6 20 24
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher
1
9 21 18 6 8 22
2
2 18 21
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher
1
6 18 15 3 5 19
1
9 15 18
Decoded Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
Corresponding numeric value
1
3 23 11
2
4 26 11
2
1 8 5
Key 4 2 3 4 2 3 4 2 3
Decoded from the substitution cipher 9 21 8
2
0 24 8
1
7 6 2
Caeser cipher shift 3 3 3 3 3 3 3 3 3
Decoded from the caeser cipher 6 18 5
1
7 21 5
1
4 3 25
Decoded Text F R E Q U E N C Y
Therefore, the decoded text for the cypher text for employees will increases the processor speed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY
References
Hajare, U., Mahajan, R., Jadhav, S., Pingale, N., & Salunke, S. (2018). Efficient Cash
Withdrawal from ATM machine using Mobile Banking.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45, 390-
396.
Khan, R., Hasan, R., & Xu, J. (2015, March). SEPIA: Secure-PIN-authentication-as-a-service for
ATM using mobile and wearable devices. In Mobile Cloud Computing, Services, and
Engineering (MobileCloud), 2015 3rd IEEE International Conference on (pp. 41-50).
IEEE.
Koteswari, S., & Paul, P. J. (2017). A Survey: Fusion of Fingerprint and Iris for ATM services.
Onyesolu, M. O., & Okpala, A. C. (2017). Improving Security Using a Three-Tier
Authentication for Automated Teller Machine (ATM). International Journal of
Computer Network and Information Security, 9(10), 50.
Pathak, S. K., Pathak, S. K., Mishra, M. K., Kesharwani, L., & Gupta, A. K. (2015). Automated
Teller Machine (ATM) Frauds and Security. EDITORIAL BOARD, 192.
Singh, S., & Kaur, S. (2016). Enhancing ATM Security Using Fusion of Biometric
Techniques. IITM Journal of Management and IT, 7(1), 79-82.
References
Hajare, U., Mahajan, R., Jadhav, S., Pingale, N., & Salunke, S. (2018). Efficient Cash
Withdrawal from ATM machine using Mobile Banking.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45, 390-
396.
Khan, R., Hasan, R., & Xu, J. (2015, March). SEPIA: Secure-PIN-authentication-as-a-service for
ATM using mobile and wearable devices. In Mobile Cloud Computing, Services, and
Engineering (MobileCloud), 2015 3rd IEEE International Conference on (pp. 41-50).
IEEE.
Koteswari, S., & Paul, P. J. (2017). A Survey: Fusion of Fingerprint and Iris for ATM services.
Onyesolu, M. O., & Okpala, A. C. (2017). Improving Security Using a Three-Tier
Authentication for Automated Teller Machine (ATM). International Journal of
Computer Network and Information Security, 9(10), 50.
Pathak, S. K., Pathak, S. K., Mishra, M. K., Kesharwani, L., & Gupta, A. K. (2015). Automated
Teller Machine (ATM) Frauds and Security. EDITORIAL BOARD, 192.
Singh, S., & Kaur, S. (2016). Enhancing ATM Security Using Fusion of Biometric
Techniques. IITM Journal of Management and IT, 7(1), 79-82.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





