Information Security Risk Management
14 Pages3276 Words39 Views
Charles Sturt University
IT Risk Management (ITC596)
Added on 2020-03-07
About This Document
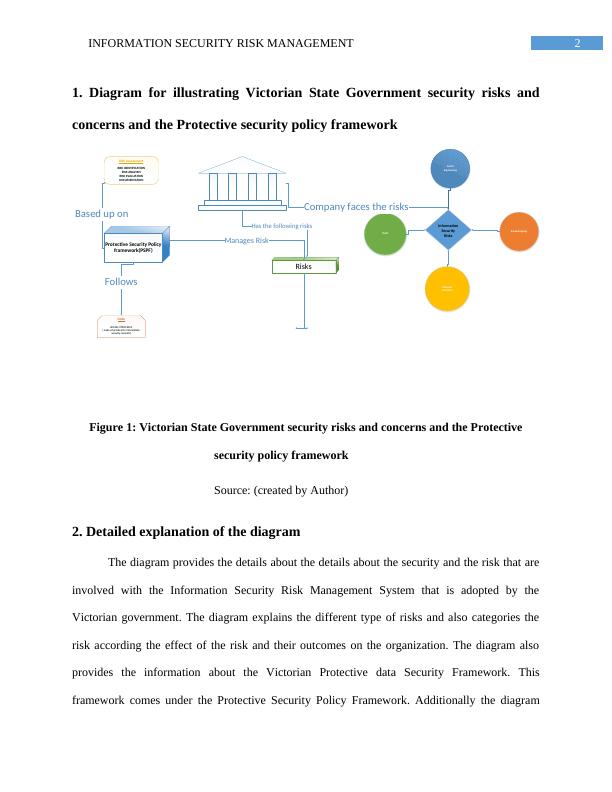
The framework is based on the risk assessment technique. There are many reasons that cause information security risks, among them is theft, malware infection, and eavesdropping. We will discuss a case study of Victorian State Government about identification of Security Risk Management, Ranking of threats in order of importance, Comparative analysis of the Deliberate and Accidental Threats, Justification of the rankings.
Information Security Risk Management
Charles Sturt University
IT Risk Management (ITC596)
Added on 2020-03-07
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
(solved) IT Risk Management PDF
|15
|3652
|47
IT Risk Management Security System
|17
|3744
|61
Victorian Protective Data Security Framework - ICT 303
|18
|3857
|81
Detailed Explanation of Risk Exposure Area 5 4. Analysis of Deliberate and Accidental Threats in Victoria Government
|15
|2687
|458
IT Risk Management & Security In Victorian Government
|17
|3721
|49
itc596 - Risk faced by VIC Government - Report
|15
|2864
|45