Information Security Risk Management: VIC Government Case Study Report
VerifiedAdded on 2020/03/04
|14
|3441
|46
Report
AI Summary
This report presents a case study on information security risk management within the VIC Government. It begins with an illustration of current security risks and concerns, followed by an explanation of the diagram and an analysis of deliberate and accidental threats, ranking them in order of importance. The report then delves into the challenges of security/risk management, differentiating between risk and uncertainty. It discusses and evaluates various approaches available to the VIC government for risk control and mitigation, covering avoidance, loss prevention, loss reduction, and separation. The analysis highlights the importance of ISMS and the implementation of security configurations to protect against threats, emphasizing the higher impact of deliberate threats and the need for robust mitigation strategies. The report also underscores the challenges faced by the VIC government in selecting risk management approaches and emphasizes the crucial differences between risk and uncertainty in the context of information security.

Running head: INFORMATION SECURITY RISK MANAGEMENT
Information Security Risk Management: A Case Study of
VIC Government
Name of the Student
Name of the University
Information Security Risk Management: A Case Study of
VIC Government
Name of the Student
Name of the University
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SECURITY RISK MANAGEMENT
Table of Contents
1. Illustration of Current Security Risks and Concerns Considered by the VIC through Diagram:2
2. Explanation of the Diagram:........................................................................................................2
3. Analysis of the Deliberate and Accidental Threats:....................................................................3
3.1 Accidental Threats:................................................................................................................3
3.2 Deliberate Threats:.................................................................................................................4
3.3 Ranking of threats in order of importance.............................................................................4
3.4 Justification of the rankings...................................................................................................5
4. Challenges of Security/Risk Management Internally or Externally:...........................................5
5. Difference between Risk and Uncertainty:..................................................................................6
6. Discuss and Evaluation of Different Approaches Available to the VIC for Risk Control and
Mitigation:.......................................................................................................................................8
6.1 Risk Control Approaches:......................................................................................................8
6.2 Risk Mitigation Approaches:...............................................................................................10
Reference List:...............................................................................................................................11
Table of Contents
1. Illustration of Current Security Risks and Concerns Considered by the VIC through Diagram:2
2. Explanation of the Diagram:........................................................................................................2
3. Analysis of the Deliberate and Accidental Threats:....................................................................3
3.1 Accidental Threats:................................................................................................................3
3.2 Deliberate Threats:.................................................................................................................4
3.3 Ranking of threats in order of importance.............................................................................4
3.4 Justification of the rankings...................................................................................................5
4. Challenges of Security/Risk Management Internally or Externally:...........................................5
5. Difference between Risk and Uncertainty:..................................................................................6
6. Discuss and Evaluation of Different Approaches Available to the VIC for Risk Control and
Mitigation:.......................................................................................................................................8
6.1 Risk Control Approaches:......................................................................................................8
6.2 Risk Mitigation Approaches:...............................................................................................10
Reference List:...............................................................................................................................11
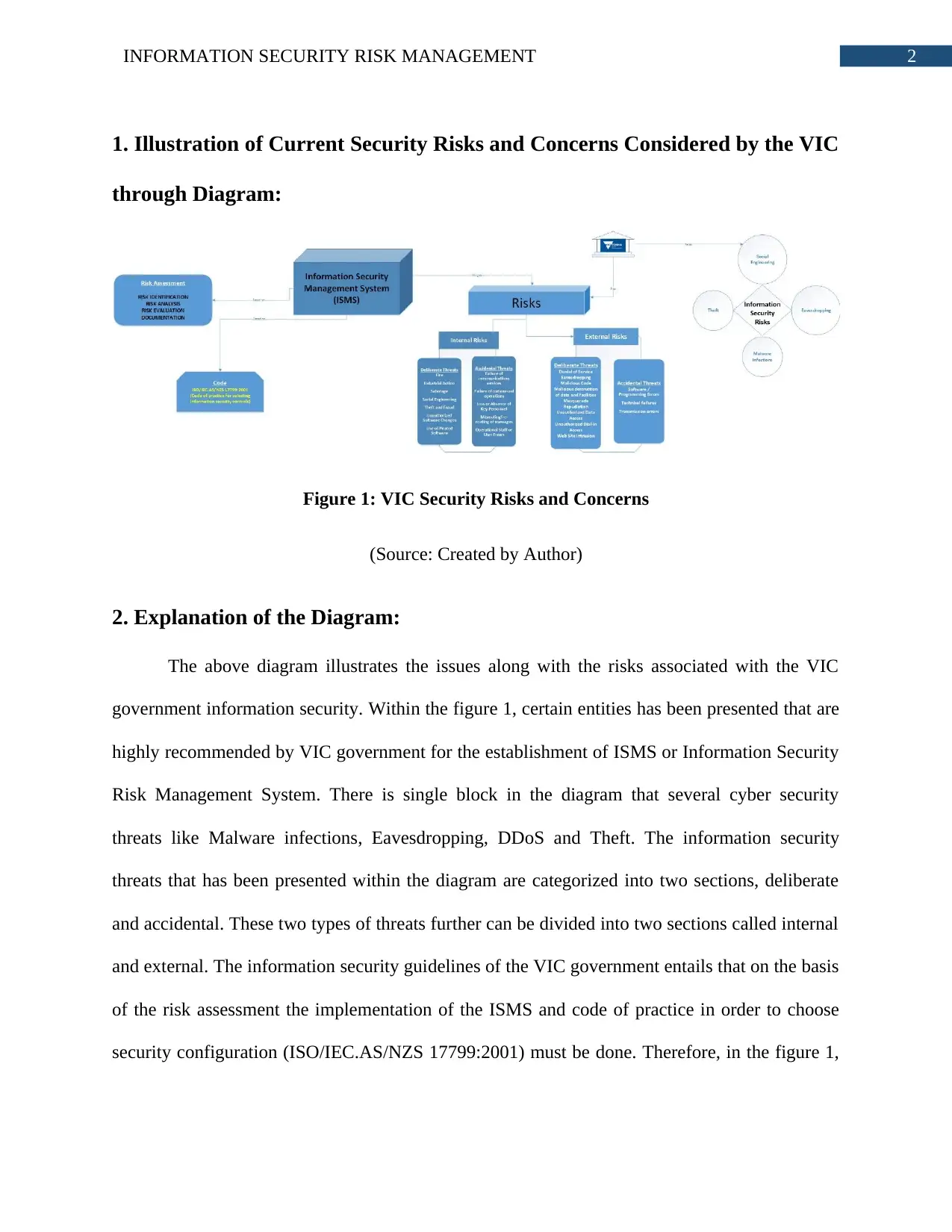
2INFORMATION SECURITY RISK MANAGEMENT
1. Illustration of Current Security Risks and Concerns Considered by the VIC
through Diagram:
Figure 1: VIC Security Risks and Concerns
(Source: Created by Author)
2. Explanation of the Diagram:
The above diagram illustrates the issues along with the risks associated with the VIC
government information security. Within the figure 1, certain entities has been presented that are
highly recommended by VIC government for the establishment of ISMS or Information Security
Risk Management System. There is single block in the diagram that several cyber security
threats like Malware infections, Eavesdropping, DDoS and Theft. The information security
threats that has been presented within the diagram are categorized into two sections, deliberate
and accidental. These two types of threats further can be divided into two sections called internal
and external. The information security guidelines of the VIC government entails that on the basis
of the risk assessment the implementation of the ISMS and code of practice in order to choose
security configuration (ISO/IEC.AS/NZS 17799:2001) must be done. Therefore, in the figure 1,
1. Illustration of Current Security Risks and Concerns Considered by the VIC
through Diagram:
Figure 1: VIC Security Risks and Concerns
(Source: Created by Author)
2. Explanation of the Diagram:
The above diagram illustrates the issues along with the risks associated with the VIC
government information security. Within the figure 1, certain entities has been presented that are
highly recommended by VIC government for the establishment of ISMS or Information Security
Risk Management System. There is single block in the diagram that several cyber security
threats like Malware infections, Eavesdropping, DDoS and Theft. The information security
threats that has been presented within the diagram are categorized into two sections, deliberate
and accidental. These two types of threats further can be divided into two sections called internal
and external. The information security guidelines of the VIC government entails that on the basis
of the risk assessment the implementation of the ISMS and code of practice in order to choose
security configuration (ISO/IEC.AS/NZS 17799:2001) must be done. Therefore, in the figure 1,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3INFORMATION SECURITY RISK MANAGEMENT
the risk assessment procedure has been described as way of dealing with the risks with the stages
like Risk Recognition, Investigation, Evaluation and Documentation.
3. Analysis of the Deliberate and Accidental Threats:
3.1 Accidental Threats:
Accidental threats are generated because of the mistakes and negligence. The issues in
the working behavior of the internal stakeholders can be the reason behind the occurrence of
data security risk (Jouini, Rabai & Aissa, 2014). The mistakes, can be considered as risks such as
programming error leads to system crash, may also lead to vulnerability such as a PC screen left
unattended might be abused by an unapproved client.
It is specifically a significant threat that occurs due to the weekly configured security
features and configurations and exploit the gaps in the programming. Taken as an example, the
running systems and databases that are not updated or patched with current version are
vulnerable to new security threats. Such threats may be the result of double dealing yet are well
while in transit to be accidental errors or rejections (Kaaniche, 2015).
The threats can affect in the following way:
Improper decision making process;
Harming the business capability;
The possibility of losing the open picture;
Financial misfortune (Jouini, Rabai & Aissa, 2014)
Legal liabilities;
Fall of Consideration’s obligation ;
The cost of business maintenance will rise tremendously.
the risk assessment procedure has been described as way of dealing with the risks with the stages
like Risk Recognition, Investigation, Evaluation and Documentation.
3. Analysis of the Deliberate and Accidental Threats:
3.1 Accidental Threats:
Accidental threats are generated because of the mistakes and negligence. The issues in
the working behavior of the internal stakeholders can be the reason behind the occurrence of
data security risk (Jouini, Rabai & Aissa, 2014). The mistakes, can be considered as risks such as
programming error leads to system crash, may also lead to vulnerability such as a PC screen left
unattended might be abused by an unapproved client.
It is specifically a significant threat that occurs due to the weekly configured security
features and configurations and exploit the gaps in the programming. Taken as an example, the
running systems and databases that are not updated or patched with current version are
vulnerable to new security threats. Such threats may be the result of double dealing yet are well
while in transit to be accidental errors or rejections (Kaaniche, 2015).
The threats can affect in the following way:
Improper decision making process;
Harming the business capability;
The possibility of losing the open picture;
Financial misfortune (Jouini, Rabai & Aissa, 2014)
Legal liabilities;
Fall of Consideration’s obligation ;
The cost of business maintenance will rise tremendously.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SECURITY RISK MANAGEMENT
3.2 Deliberate Threats:
These kinds of threats incorporate the continuous extermination or control over the data
or application. The possible sources of this threat is consisting of improper staff or
predetermined staff, coders, experts, consumers, cyber attackers, mobile operators and many
more (Jouini, Rabai & Aissa, 2014). Deliberate threats can result into the loss of privacy,
unauthorized access, loss of loyalty between organization and third party, dependability, loss of
information and many more. The following list represents the types of outcome of deliberate
threats:
Financial breakdown;
The possibility of losing the open picture;
Improper decision making process (Pettit, Croxton & Fiksel, 2013);
Legal liabilities;
Fall of consideration's obligation ;
Death or Injury toll;
Unauthorized access to the SLA to the Government of Public sector;
Losing the ability to perform the regular tasks.
3.3 Ranking of threats in order of importance
The impact of the deliberate threats are much higher than the accidental threats. This
makes the deliberate threat more significant to consider. The deliberate threats are uncontrollable
and these threats cannot be identified before its occurrence (Huth et al., 2013). It has been
recognized after conducting an analysis that the aim level can reasonably guide the risk within
the upcoming ten years span. The outcome of the impact on the ISMS for the occurrence of the
threats like deliberate and accidental has been presented in the following manner.
3.2 Deliberate Threats:
These kinds of threats incorporate the continuous extermination or control over the data
or application. The possible sources of this threat is consisting of improper staff or
predetermined staff, coders, experts, consumers, cyber attackers, mobile operators and many
more (Jouini, Rabai & Aissa, 2014). Deliberate threats can result into the loss of privacy,
unauthorized access, loss of loyalty between organization and third party, dependability, loss of
information and many more. The following list represents the types of outcome of deliberate
threats:
Financial breakdown;
The possibility of losing the open picture;
Improper decision making process (Pettit, Croxton & Fiksel, 2013);
Legal liabilities;
Fall of consideration's obligation ;
Death or Injury toll;
Unauthorized access to the SLA to the Government of Public sector;
Losing the ability to perform the regular tasks.
3.3 Ranking of threats in order of importance
The impact of the deliberate threats are much higher than the accidental threats. This
makes the deliberate threat more significant to consider. The deliberate threats are uncontrollable
and these threats cannot be identified before its occurrence (Huth et al., 2013). It has been
recognized after conducting an analysis that the aim level can reasonably guide the risk within
the upcoming ten years span. The outcome of the impact on the ISMS for the occurrence of the
threats like deliberate and accidental has been presented in the following manner.

5INFORMATION SECURITY RISK MANAGEMENT
Very High: In case of deliberate threat, it is being closely observed that it is international
in its level. Moreover, it has the capability of affecting the objective that are associated with
major occasions and people. It is also able to employ the risk that can destroy the risk and
position as needed.
High: Accidental threats are able of harming or weaken the objective of the collections
along with specific assisting point may be re-constructed up or convalesced. However, the cost
of mitigating the threats are irrational.
3.4 Justification of the rankings
The analysis that has been done about the threats made it clear that the method of
mitigating the threats must be able to protecting the VIC website as it is the source of
communication between the government and users. It categorizes a collection of criteria and
includes it into the security configuration to protect the ISMS from the threats. Deliberate threats
is located as high as it can be positioned for naturally controlling by the VIC government and
information recovery. Moreover, target is worrying as if there must be an event of accompanying
threat as well as target may be recuperated with particular expertise support.
4. Challenges of Security/Risk Management Internally or Externally:
There are various issues that the VIC government has to face for selecting whether the
risk management approach must be carried out from internally or externally (Webb et al., 2014).
The primary reason behind this challenge is the nonexistence of any Information Security
Management System. The risk management has proved itself as a high recommendable approach
even for the most consolidated government organization. Irrespective of being able to handle
most of the risks through the risk management, the enterprises are working continuously to
Very High: In case of deliberate threat, it is being closely observed that it is international
in its level. Moreover, it has the capability of affecting the objective that are associated with
major occasions and people. It is also able to employ the risk that can destroy the risk and
position as needed.
High: Accidental threats are able of harming or weaken the objective of the collections
along with specific assisting point may be re-constructed up or convalesced. However, the cost
of mitigating the threats are irrational.
3.4 Justification of the rankings
The analysis that has been done about the threats made it clear that the method of
mitigating the threats must be able to protecting the VIC website as it is the source of
communication between the government and users. It categorizes a collection of criteria and
includes it into the security configuration to protect the ISMS from the threats. Deliberate threats
is located as high as it can be positioned for naturally controlling by the VIC government and
information recovery. Moreover, target is worrying as if there must be an event of accompanying
threat as well as target may be recuperated with particular expertise support.
4. Challenges of Security/Risk Management Internally or Externally:
There are various issues that the VIC government has to face for selecting whether the
risk management approach must be carried out from internally or externally (Webb et al., 2014).
The primary reason behind this challenge is the nonexistence of any Information Security
Management System. The risk management has proved itself as a high recommendable approach
even for the most consolidated government organization. Irrespective of being able to handle
most of the risks through the risk management, the enterprises are working continuously to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6INFORMATION SECURITY RISK MANAGEMENT
improve this approach. The threat filtering option provides the visibility within the possible
regions of the system that are needed to be improved. The challenges are presented in the
following section.
Arranging Requirements: Considering the demographic perspective, the VIC
government requires to assign higher effort for positioning the structure appropriately for the
financial enhancement (Pachauri, Srivastava & Trivedi, 2014). However, the government is not
able to do so adequately.
Information Propriety: It can be considered as another issue that the VIC government
come across due to nonexistence of information security management. The security level in the
government is not up to appropriate degree thus accelerating information is possible.
Foundation of VIC: The VIC does not use security that is updated properly as per
present situation.
5. The difference between Risk and Uncertainty:
In general, the risk can be considered as the outcome of activity done or not done, within
a particular situation that might be able to bring harm to the information framework (Beck et al.,
2016). The risk is also known as the outcome of threats. Threats can occur from various
situations such as internal and external and can be handled with proper risks management
technique.
Within the financial term, the significance of risk is not a unique entity. In another word
the risk can be considered as the result of a particular event that is arising (Park et al., 2013). The
outcome of the risks is dependent upon the frequency and likelihood of the event occurs within a
particular span of time. Through the identification of impact of the risk, how serious the risk is
improve this approach. The threat filtering option provides the visibility within the possible
regions of the system that are needed to be improved. The challenges are presented in the
following section.
Arranging Requirements: Considering the demographic perspective, the VIC
government requires to assign higher effort for positioning the structure appropriately for the
financial enhancement (Pachauri, Srivastava & Trivedi, 2014). However, the government is not
able to do so adequately.
Information Propriety: It can be considered as another issue that the VIC government
come across due to nonexistence of information security management. The security level in the
government is not up to appropriate degree thus accelerating information is possible.
Foundation of VIC: The VIC does not use security that is updated properly as per
present situation.
5. The difference between Risk and Uncertainty:
In general, the risk can be considered as the outcome of activity done or not done, within
a particular situation that might be able to bring harm to the information framework (Beck et al.,
2016). The risk is also known as the outcome of threats. Threats can occur from various
situations such as internal and external and can be handled with proper risks management
technique.
Within the financial term, the significance of risk is not a unique entity. In another word
the risk can be considered as the result of a particular event that is arising (Park et al., 2013). The
outcome of the risks is dependent upon the frequency and likelihood of the event occurs within a
particular span of time. Through the identification of impact of the risk, how serious the risk is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7INFORMATION SECURITY RISK MANAGEMENT
determined. Most of the time the risk matrix is used for identifying the severity of the risk. The
information risk is mainly associated with cyber threats. The internal threats are cyber hacks,
DDoS and much more (Dixit & Skeath, 2015). The internal risks are a physical attack, virus and
much more. Both the types of risks are very crucial to identify and mitigate. The process of
handling cyber threats are different for different risks.
Through the uncertainty phrase the absence of something that is unknown to the
organizations and users. It implies the existence of several alternatives in a particular situation
that achieve a particular result. However, the probability of occurrence and result cannot be
identified. This is considered to the outcome of low data presence or inability of recognizing the
current situation. This makes it hard to forecast the result of future occurrences (Heckmann,
Comes & Nickel, 2015). Ineffectiveness is calculable through quantitative conditions via the
previous models. Simultaneously, possibilities may not be linked with the possible results as the
probability of occurrence is not clear.
The essential differences between the risk and vulnerability are as follows.
i. The risk is distinguished as the situation of gaining or losing profit. The
uncertainty is the situation when a person has no clue regarding the
occurrences of the future.
ii. The hypothetical models are utilized by the responsible personnel for
identifying, calculating and analyzing the risks. There is no sense in
measuring the uncertainty quantitatively. It is because the forecasting the
future incidents are not measurable (Pinchoff et al., 2016).
iii. The negative result of an event is considered as risk, and the source of the
uncertainty is not identifiable
determined. Most of the time the risk matrix is used for identifying the severity of the risk. The
information risk is mainly associated with cyber threats. The internal threats are cyber hacks,
DDoS and much more (Dixit & Skeath, 2015). The internal risks are a physical attack, virus and
much more. Both the types of risks are very crucial to identify and mitigate. The process of
handling cyber threats are different for different risks.
Through the uncertainty phrase the absence of something that is unknown to the
organizations and users. It implies the existence of several alternatives in a particular situation
that achieve a particular result. However, the probability of occurrence and result cannot be
identified. This is considered to the outcome of low data presence or inability of recognizing the
current situation. This makes it hard to forecast the result of future occurrences (Heckmann,
Comes & Nickel, 2015). Ineffectiveness is calculable through quantitative conditions via the
previous models. Simultaneously, possibilities may not be linked with the possible results as the
probability of occurrence is not clear.
The essential differences between the risk and vulnerability are as follows.
i. The risk is distinguished as the situation of gaining or losing profit. The
uncertainty is the situation when a person has no clue regarding the
occurrences of the future.
ii. The hypothetical models are utilized by the responsible personnel for
identifying, calculating and analyzing the risks. There is no sense in
measuring the uncertainty quantitatively. It is because the forecasting the
future incidents are not measurable (Pinchoff et al., 2016).
iii. The negative result of an event is considered as risk, and the source of the
uncertainty is not identifiable

8INFORMATION SECURITY RISK MANAGEMENT
iv. The risks are controlled through various techniques that are based on the
theories (Chiu et al., 2014). It is possible because tracking the source of
the risk is possible. Moreover, the most severe risks are already known.
However, the uncertainty cannot be controlled in some predefined way. It
is best to improvise the control method as per the situation.
v. Minimization of risk should be possible, by avoiding potential risk.
Instead of the instability that cannot be limited.
6. Discuss, and Evaluation of Different Approaches Available to the VIC for
Risk Control and Mitigation:
6.1 Risk Control Approaches:
Avoidance: Avoidance is among best strategies for setback control. This is by, as the
name recommends, associations are avoiding the risk altogether. In case your attempts at keeping
up a vital separation from the hardship have been productive, by then there is a no probability
that associations will encounter the evil impacts of that particular threat factor, at any rate (Yang,
Shieh & Tzeng, 2013). This is the reason avoidance is the initial of the threat control approaches
that are focused upon. This is a method for systematically discarding a risk.
Loss Prevention: This control strategy is a framework that resolves of containment,
instead of slaughters. As opposed to keeping up a vital separation from a threat absolutely, this
framework identifies a risk but tries to restrict the threat as an outcome. Taken as an example,
securing stock within a scattering focus concludes that it is feeble to theft (Laudon & Laudon,
2016). Regardless, since there genuinely is no genuine approach to keep up a vital separation
iv. The risks are controlled through various techniques that are based on the
theories (Chiu et al., 2014). It is possible because tracking the source of
the risk is possible. Moreover, the most severe risks are already known.
However, the uncertainty cannot be controlled in some predefined way. It
is best to improvise the control method as per the situation.
v. Minimization of risk should be possible, by avoiding potential risk.
Instead of the instability that cannot be limited.
6. Discuss, and Evaluation of Different Approaches Available to the VIC for
Risk Control and Mitigation:
6.1 Risk Control Approaches:
Avoidance: Avoidance is among best strategies for setback control. This is by, as the
name recommends, associations are avoiding the risk altogether. In case your attempts at keeping
up a vital separation from the hardship have been productive, by then there is a no probability
that associations will encounter the evil impacts of that particular threat factor, at any rate (Yang,
Shieh & Tzeng, 2013). This is the reason avoidance is the initial of the threat control approaches
that are focused upon. This is a method for systematically discarding a risk.
Loss Prevention: This control strategy is a framework that resolves of containment,
instead of slaughters. As opposed to keeping up a vital separation from a threat absolutely, this
framework identifies a risk but tries to restrict the threat as an outcome. Taken as an example,
securing stock within a scattering focus concludes that it is feeble to theft (Laudon & Laudon,
2016). Regardless, since there genuinely is no genuine approach to keep up a vital separation
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9INFORMATION SECURITY RISK MANAGEMENT
from it, a disaster neutralizing activity application is configured for restricting the threat. This
application may join monitoring security ensures, safeguarded storerooms and camcorders.
Loss Reduction: This is a control strategy that recognizes risk, and in addition recognizes
the way that hardship may happen due to the threat. This framework will attempt to constrain the
setback if there should be an occurrence or something to that effect of a threat. For example, an
association may need to store ignitable material in a dispersion focus (Pinchoff et al., 2015).
Association organization comprehends this is a basic threat and presents best manufactured water
sprinklers within the movement effort. In case of a fire occurs, measure of the event will be
compelled.
Separation: This is a control approach that includes disseminating primary resources. It
makes sure that if anything irrelevant happens at a region, the influence to the organization is
restricted to the benefits particularly at that area. Alternatively, in case of all advantages would
present in that area, by then the organization would escalate in contradiction of a liberally better
test (Laudon & Laudon, 2016). An instance of this is the time when an association uses a
geologically upgraded staff.
Duplication: This risk control approach fundamentally includes the creation of a
provision plan. It is as frequently as possible basic with implementation. A disaster within an
information system’s server ought not to pass on the whole business to a stop. Or maybe, a
fortification over server should be instantly available for getting to if the fundamental server
crashes and burns. Another duplication example as a threat control method is the time while an
organization utilizes the benefits of a disaster recovery strategy.
from it, a disaster neutralizing activity application is configured for restricting the threat. This
application may join monitoring security ensures, safeguarded storerooms and camcorders.
Loss Reduction: This is a control strategy that recognizes risk, and in addition recognizes
the way that hardship may happen due to the threat. This framework will attempt to constrain the
setback if there should be an occurrence or something to that effect of a threat. For example, an
association may need to store ignitable material in a dispersion focus (Pinchoff et al., 2015).
Association organization comprehends this is a basic threat and presents best manufactured water
sprinklers within the movement effort. In case of a fire occurs, measure of the event will be
compelled.
Separation: This is a control approach that includes disseminating primary resources. It
makes sure that if anything irrelevant happens at a region, the influence to the organization is
restricted to the benefits particularly at that area. Alternatively, in case of all advantages would
present in that area, by then the organization would escalate in contradiction of a liberally better
test (Laudon & Laudon, 2016). An instance of this is the time when an association uses a
geologically upgraded staff.
Duplication: This risk control approach fundamentally includes the creation of a
provision plan. It is as frequently as possible basic with implementation. A disaster within an
information system’s server ought not to pass on the whole business to a stop. Or maybe, a
fortification over server should be instantly available for getting to if the fundamental server
crashes and burns. Another duplication example as a threat control method is the time while an
organization utilizes the benefits of a disaster recovery strategy.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10INFORMATION SECURITY RISK MANAGEMENT
Diversification: This threat control approach that apportions business assets regarding
different make lines of business that offer various things and additionally organizations in
diverse endeavours (Yang, Shieh & Tzeng, 2013). With expanding, a tremendous wage threat
from one line of business would not make miserable devilishness the association's essential
concern.
6.2 Risk Mitigation Approaches:
Risk Acceptance: The risk acceptance does not lead to a reduction in the impact of the
risk though it is considered as a strategy of mitigating risk. Within various projects, this strategy
can be seen as a regular option as the charge of the risk handling preferences such as limitation
or avoidance be greater than the risk (Pinchoff et al., 2015). The risk acceptance strategy will be
used by VIC if the impact of the risk is not severe.
Risk Avoidance: Risk avoidance can be considered as the opposite process of risk
acceptance. VIC will be using the risk avoidance strategy to avoid any coverage of the risk from
its information security. Among all the risk mitigation strategy, the risk avoidance is the most
expensive mitigation strategy.
Risk Limitation: Various business uses this risk limitation strategy in terms of most of
the cases. This implies that organizations must limit its exposure to taking some actions. Both the
risk acceptance and avoidance strategies (Flanagin et al., 2014). Taken as an example, the risk
limitation strategy which VIC will use for accepting that the magnetic tape that holds data may
fail and evade an extended span of failure through having backups
Risk Transference: The risk transference is considered to be processed which hands the
task over to a third party, willing to manage risk. Taken as an example, various organizations
Diversification: This threat control approach that apportions business assets regarding
different make lines of business that offer various things and additionally organizations in
diverse endeavours (Yang, Shieh & Tzeng, 2013). With expanding, a tremendous wage threat
from one line of business would not make miserable devilishness the association's essential
concern.
6.2 Risk Mitigation Approaches:
Risk Acceptance: The risk acceptance does not lead to a reduction in the impact of the
risk though it is considered as a strategy of mitigating risk. Within various projects, this strategy
can be seen as a regular option as the charge of the risk handling preferences such as limitation
or avoidance be greater than the risk (Pinchoff et al., 2015). The risk acceptance strategy will be
used by VIC if the impact of the risk is not severe.
Risk Avoidance: Risk avoidance can be considered as the opposite process of risk
acceptance. VIC will be using the risk avoidance strategy to avoid any coverage of the risk from
its information security. Among all the risk mitigation strategy, the risk avoidance is the most
expensive mitigation strategy.
Risk Limitation: Various business uses this risk limitation strategy in terms of most of
the cases. This implies that organizations must limit its exposure to taking some actions. Both the
risk acceptance and avoidance strategies (Flanagin et al., 2014). Taken as an example, the risk
limitation strategy which VIC will use for accepting that the magnetic tape that holds data may
fail and evade an extended span of failure through having backups
Risk Transference: The risk transference is considered to be processed which hands the
task over to a third party, willing to manage risk. Taken as an example, various organizations

11INFORMATION SECURITY RISK MANAGEMENT
outsource particular activities such as payroll services, customer services and much more. This
may be advantageous regarding an organization on the basis of the fact that the risk not
associated with the core aspects of the organization.
outsource particular activities such as payroll services, customer services and much more. This
may be advantageous regarding an organization on the basis of the fact that the risk not
associated with the core aspects of the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





